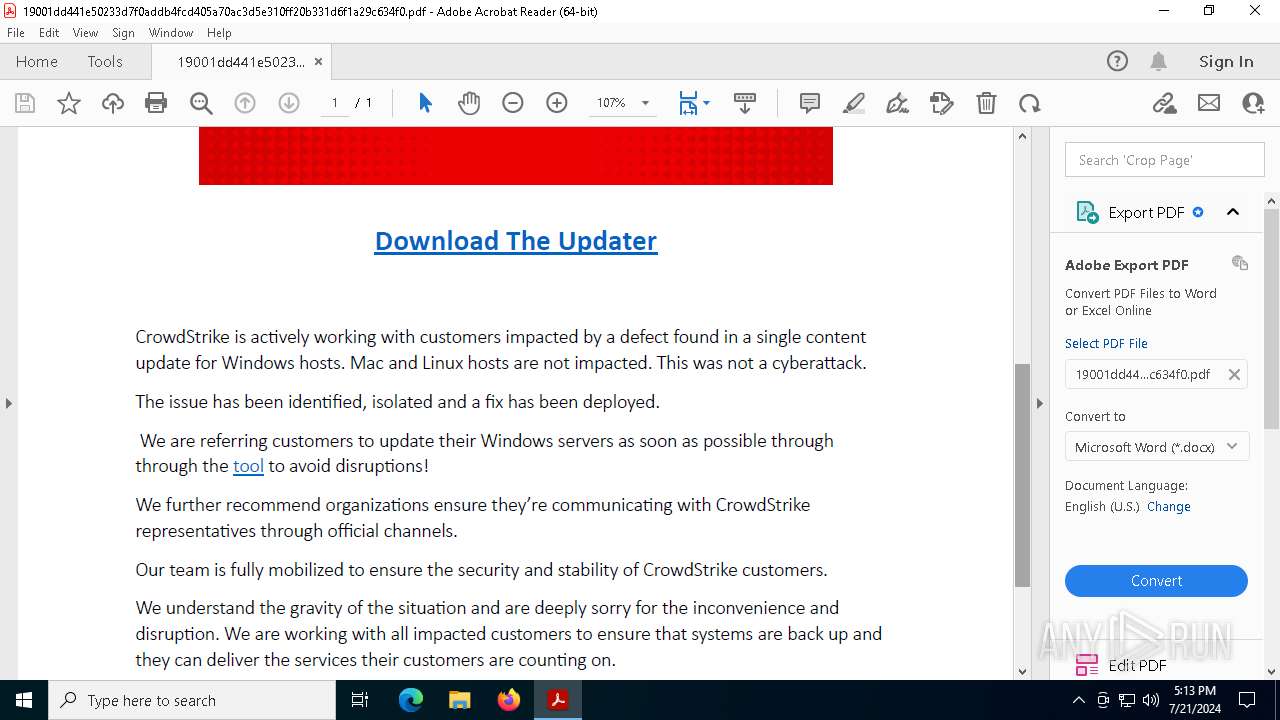
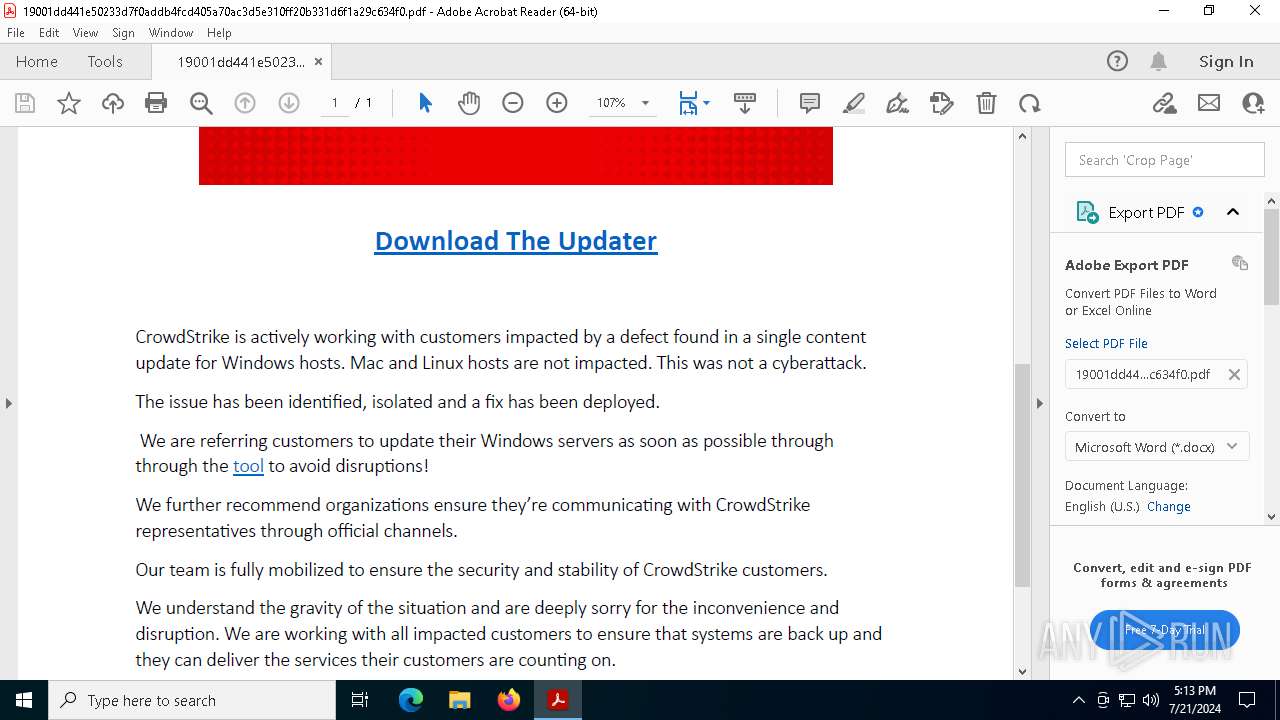
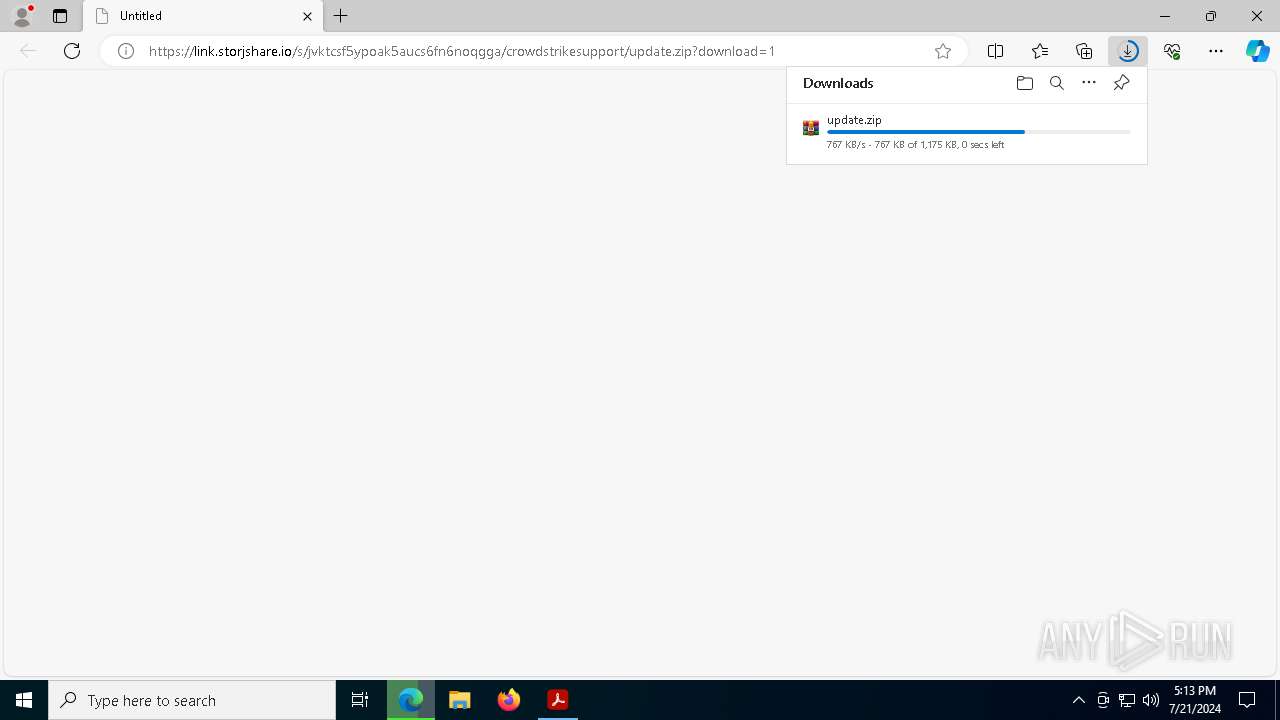
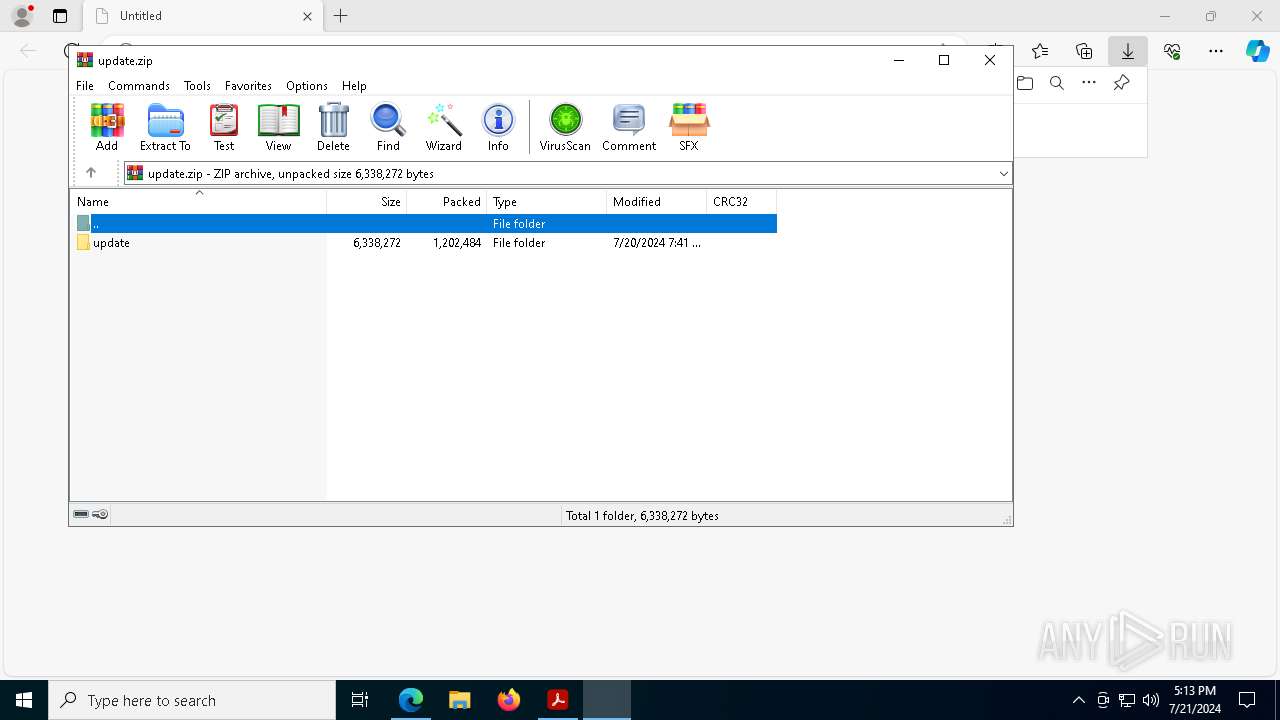
| File name: | 19001dd441e50233d7f0addb4fcd405a70ac3d5e310ff20b331d6f1a29c634f0.pdf |
| Full analysis: | https://app.any.run/tasks/2c0ffc87-4059-4d6f-8306-1258cf33aa54 |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2024, 17:12:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7, 1 pages |
| MD5: | 22E9135A650CD674EB330CBB4A7329C3 |
| SHA1: | CDFA4966D7A859B09A411F0D90EFBF822B2D6671 |
| SHA256: | 19001DD441E50233D7F0ADDB4FCD405A70AC3D5E310FF20B331D6F1A29C634F0 |
| SSDEEP: | 3072:0acAmbHcWJZ6HjAndhEsWfJnOmsXfrRkPBKkeR8H80znno1pFpQcM:0acAmbHKAnXDqPBKks8H3ToLrBM |
MALICIOUS
Drops the executable file immediately after the start
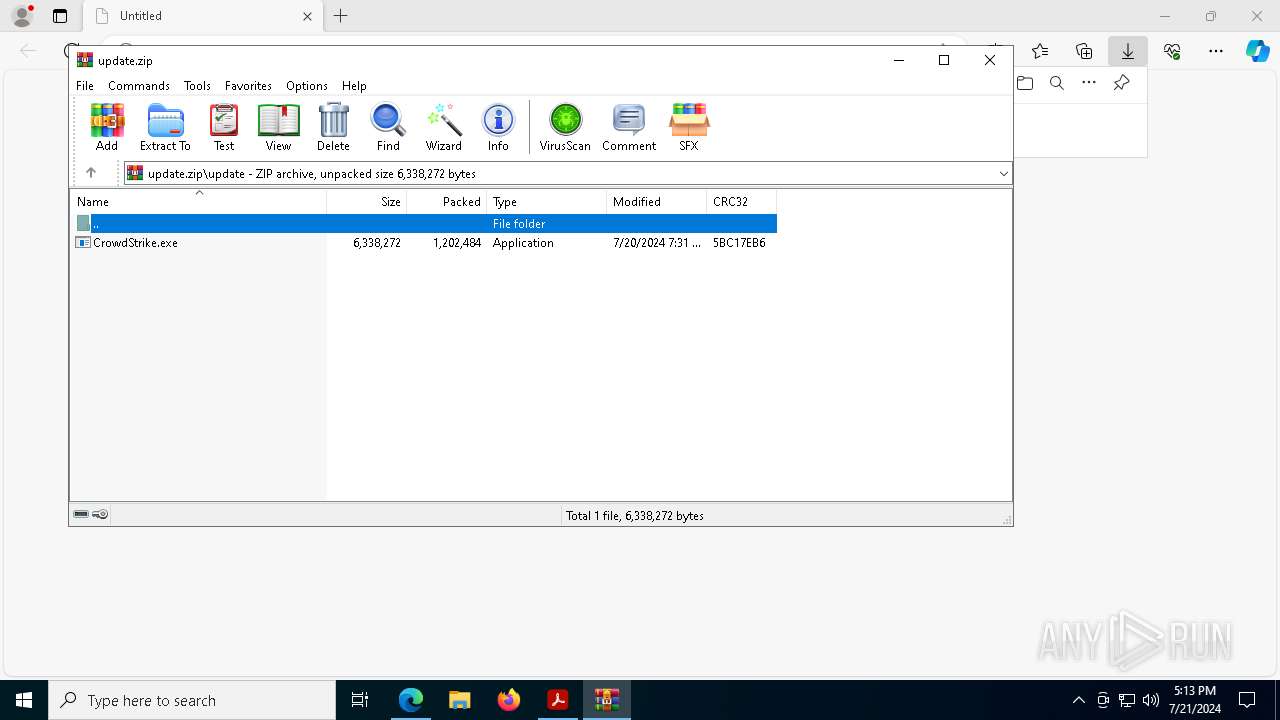
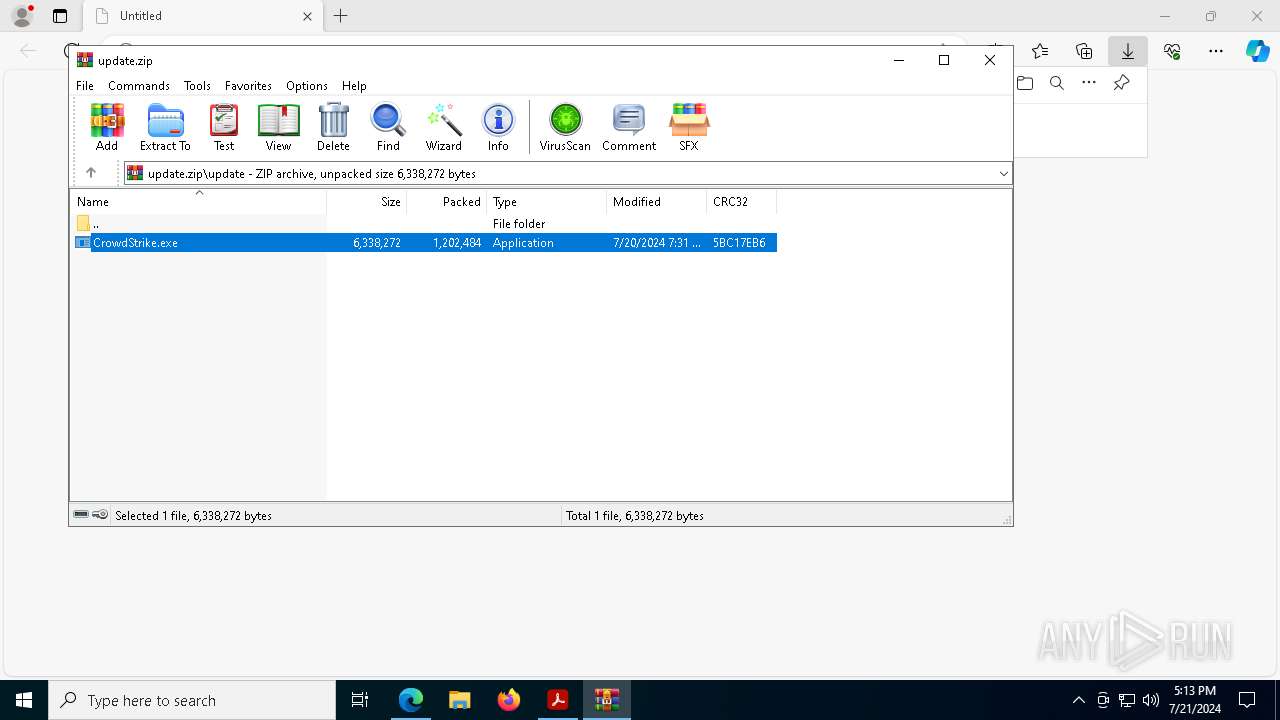
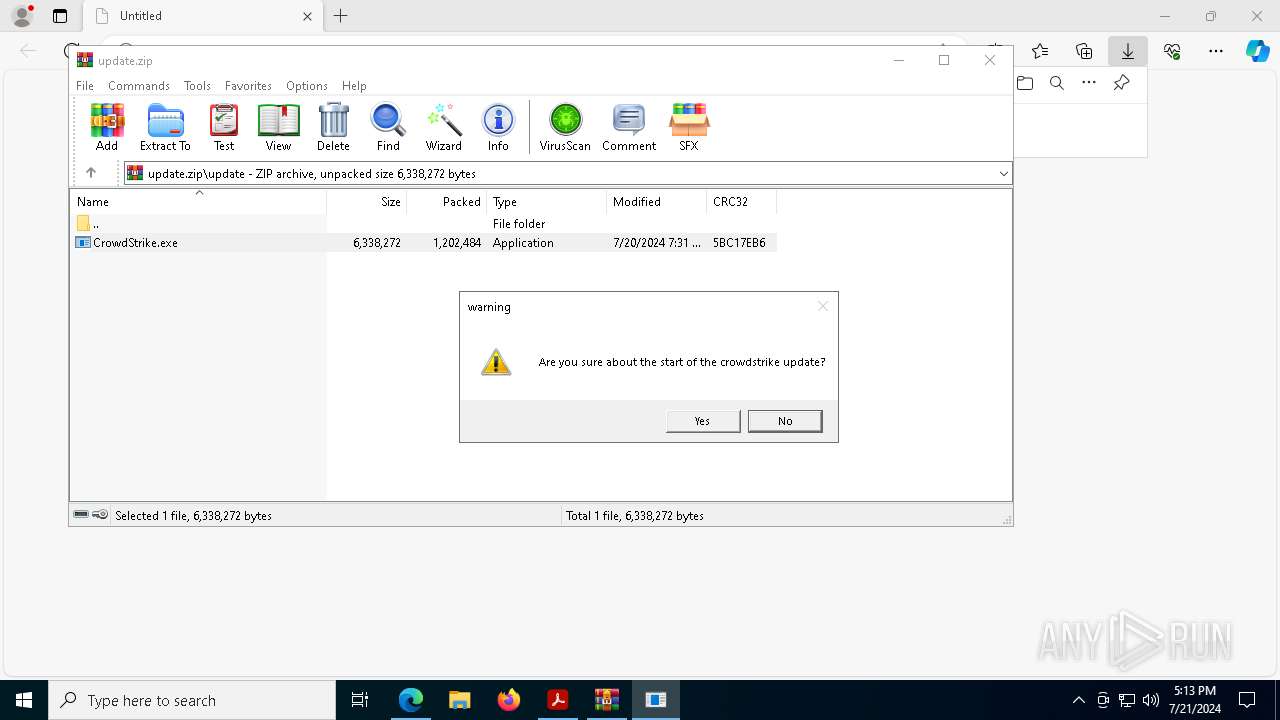
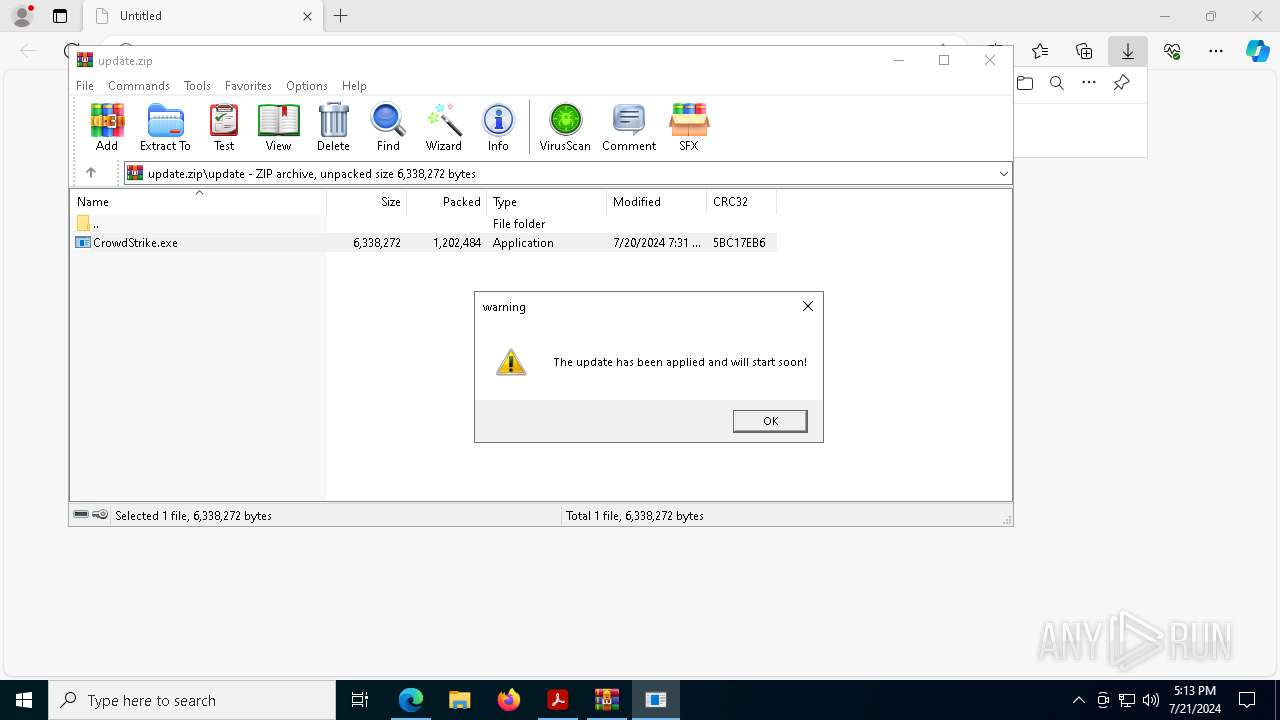
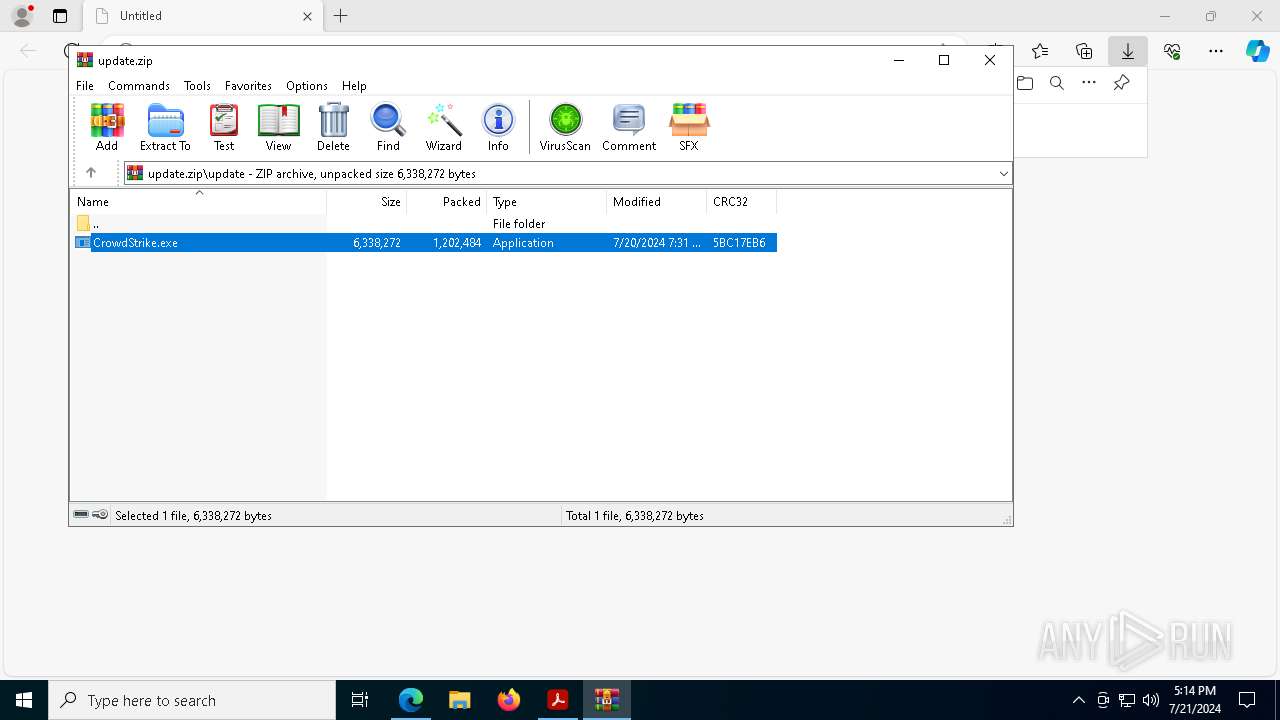
- CrowdStrike.exe (PID: 8936)
- cmd.exe (PID: 9092)
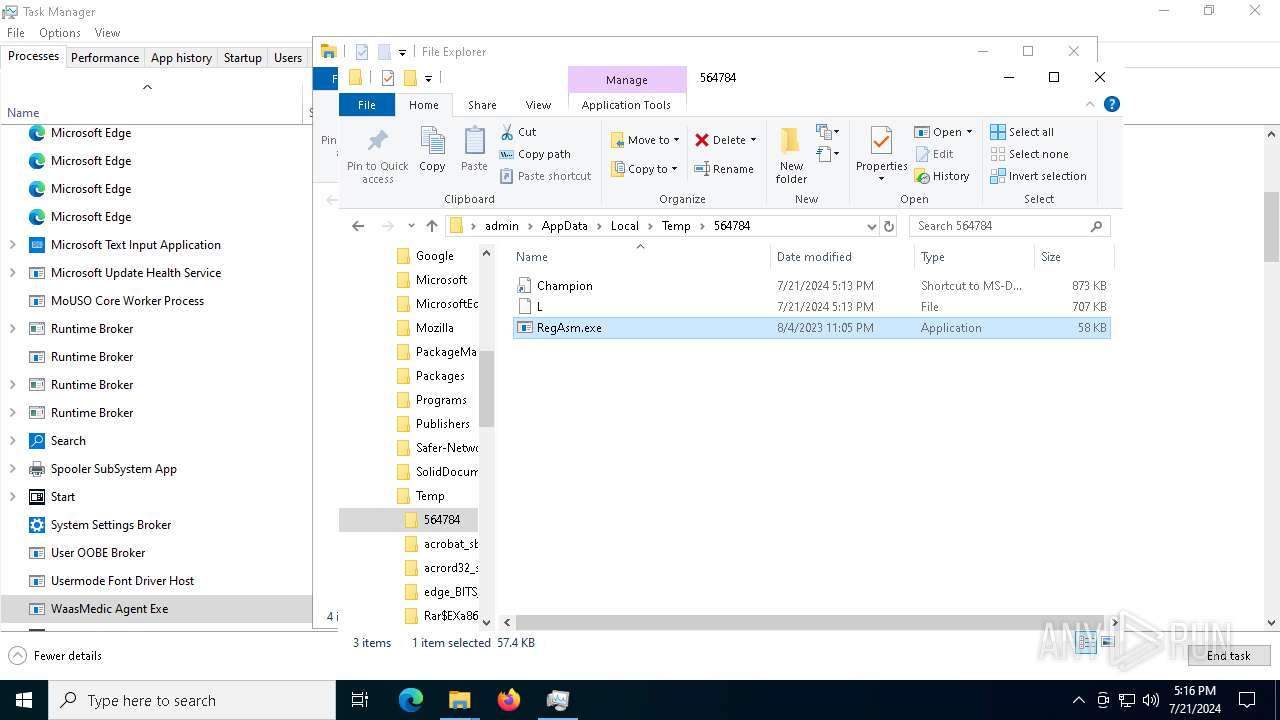
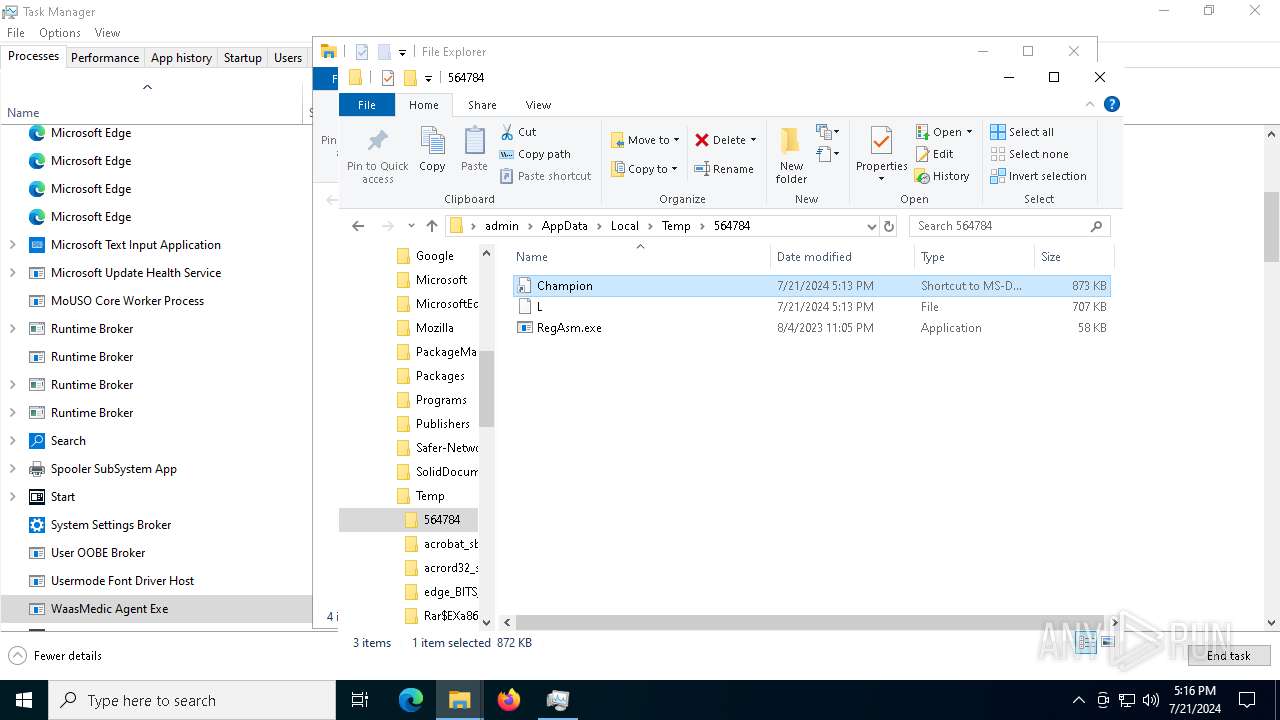
- Champion.pif (PID: 6396)
- RegAsm.exe (PID: 8896)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 8976)
- findstr.exe (PID: 9060)
- findstr.exe (PID: 9052)
- findstr.exe (PID: 8504)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 8896)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8604)
- CrowdStrike.exe (PID: 8936)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
Starts CMD.EXE for commands execution
- CrowdStrike.exe (PID: 8936)
- cmd.exe (PID: 9092)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
- cmd.exe (PID: 9004)
Executing commands from ".cmd" file
- CrowdStrike.exe (PID: 8936)
- CrowdStrike.exe (PID: 5244)
Reads the date of Windows installation
- CrowdStrike.exe (PID: 8936)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
Get information on the list of running processes
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9004)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9004)
The executable file from the user directory is run by the CMD process
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
- Champion.pif (PID: 6396)
Application launched itself
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9004)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 9092)
Executable content was dropped or overwritten
- cmd.exe (PID: 9092)
- RegAsm.exe (PID: 8896)
- Champion.pif (PID: 6396)
Suspicious file concatenation
- cmd.exe (PID: 1164)
- cmd.exe (PID: 9168)
Starts application with an unusual extension
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9004)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9004)
The process creates files with name similar to system file names
- Champion.pif (PID: 6396)
Process drops legitimate windows executable
- Champion.pif (PID: 6396)
Starts a Microsoft application from unusual location
- RegAsm.exe (PID: 8896)
- RegAsm.exe (PID: 7232)
Drops a system driver (possible attempt to evade defenses)
- RegAsm.exe (PID: 8896)
Checks for external IP
- RegAsm.exe (PID: 8896)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegAsm.exe (PID: 8896)
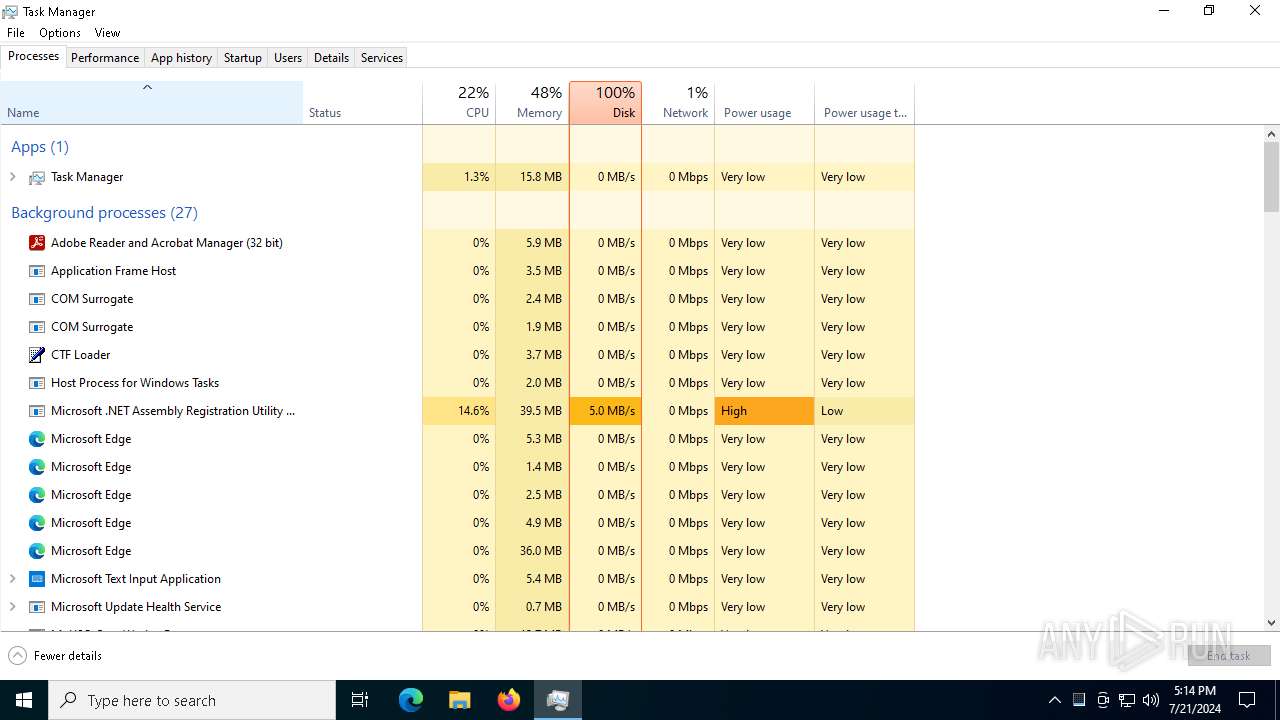
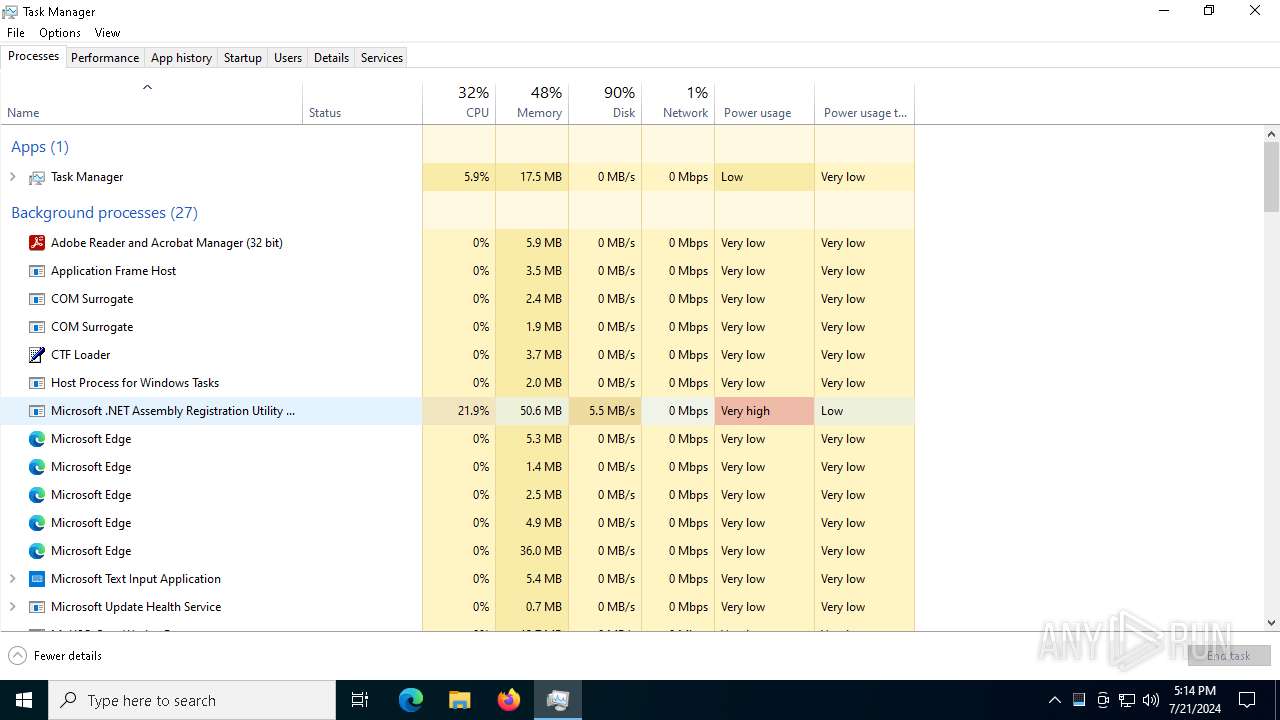
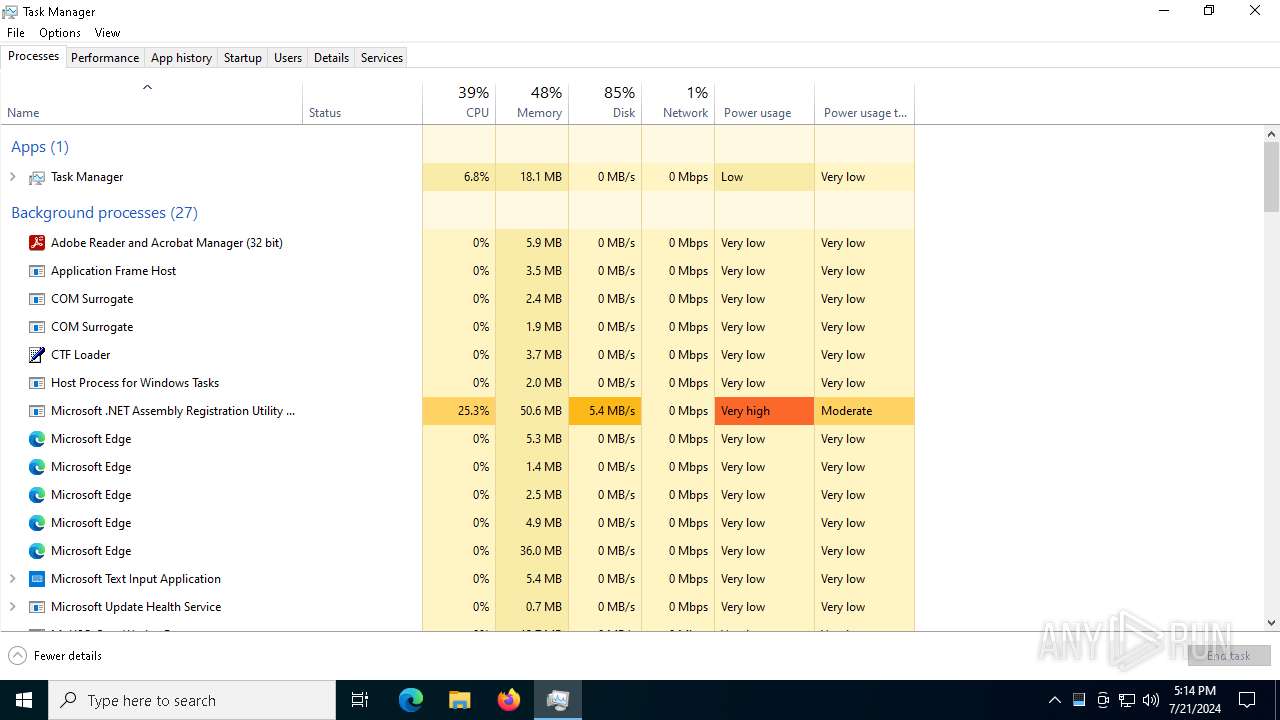
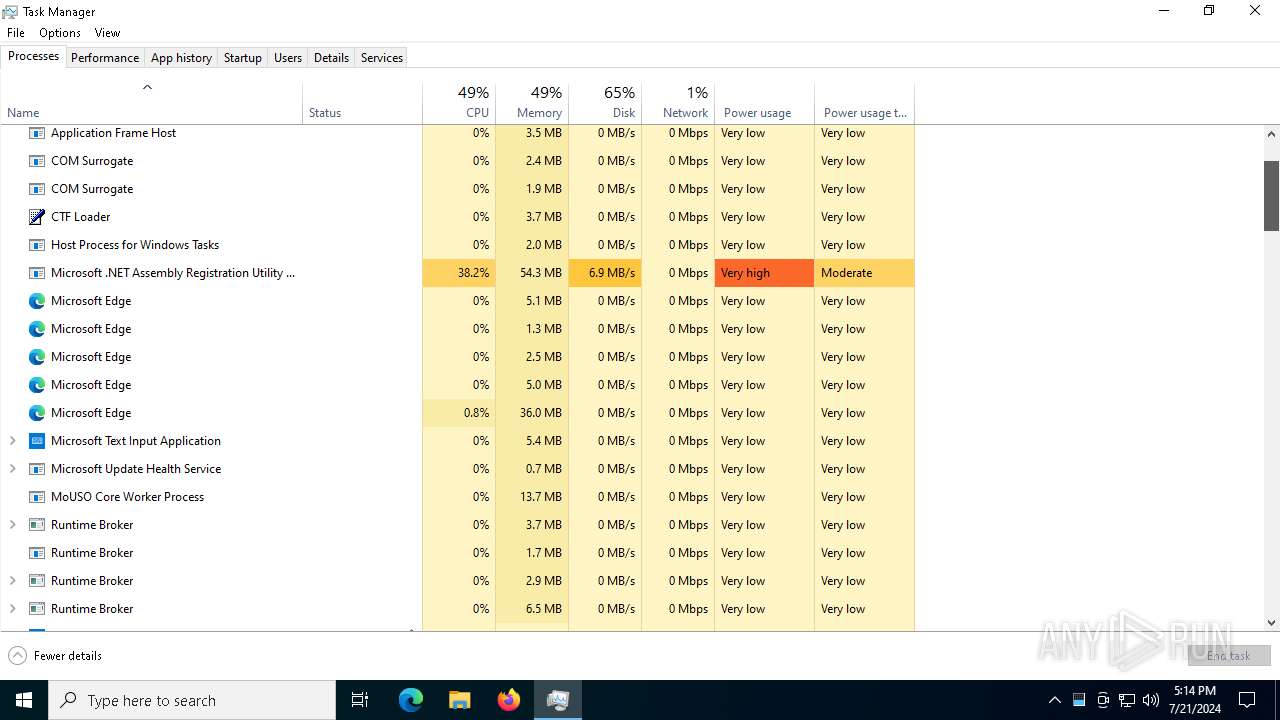
Executes application which crashes
- Taskmgr.exe (PID: 2204)
INFO
Checks supported languages
- acrobat_sl.exe (PID: 7336)
- identity_helper.exe (PID: 8844)
- CrowdStrike.exe (PID: 8936)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
- Champion.pif (PID: 6396)
- RegAsm.exe (PID: 8896)
- identity_helper.exe (PID: 9196)
Application launched itself
- Acrobat.exe (PID: 7628)
- AcroCEF.exe (PID: 7608)
- msedge.exe (PID: 7972)
- msedge.exe (PID: 8832)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7972)
- Acrobat.exe (PID: 7628)
- msedge.exe (PID: 8832)
Drops the executable file immediately after the start
- msedge.exe (PID: 7972)
- msedge.exe (PID: 5848)
- WinRAR.exe (PID: 8604)
- AdobeARM.exe (PID: 8124)
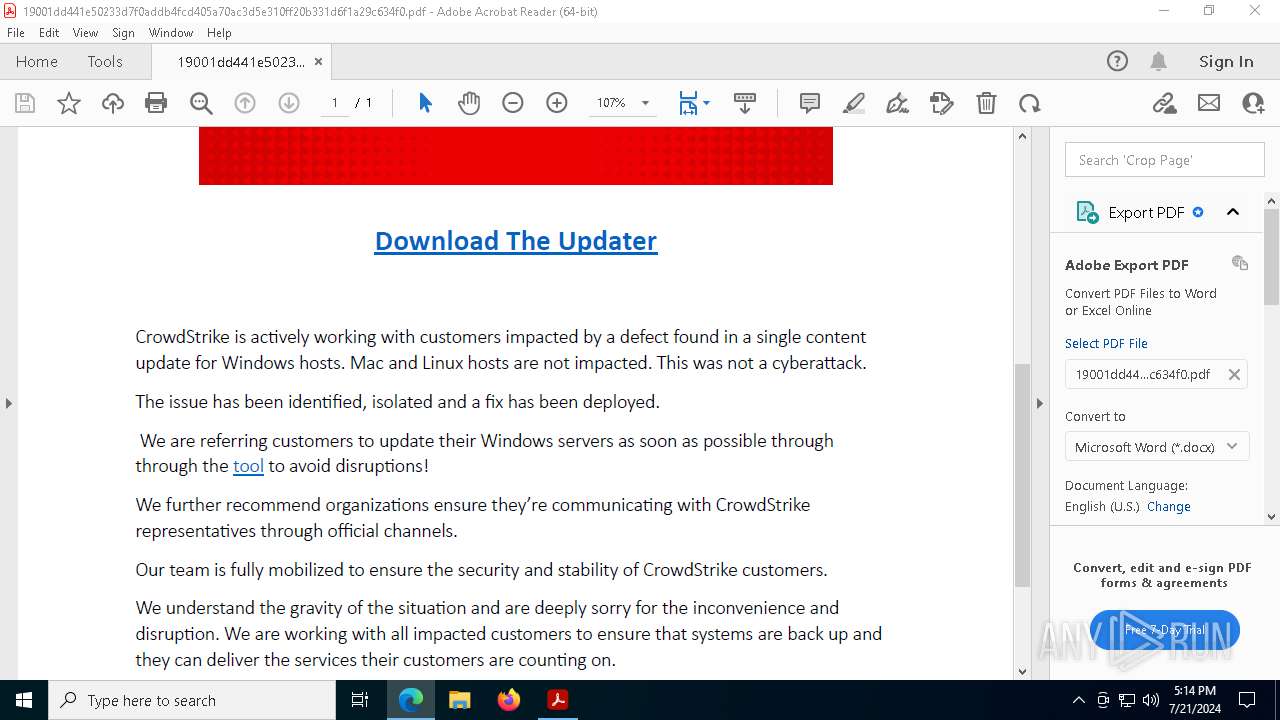
An automatically generated document
- Acrobat.exe (PID: 7628)
Reads the computer name
- identity_helper.exe (PID: 8844)
- CrowdStrike.exe (PID: 8936)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
- Champion.pif (PID: 6396)
- RegAsm.exe (PID: 8896)
- identity_helper.exe (PID: 9196)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 8124)
- WinRAR.exe (PID: 8604)
The process uses the downloaded file
- msedge.exe (PID: 9188)
- msedge.exe (PID: 7972)
- WinRAR.exe (PID: 8604)
Create files in a temporary directory
- CrowdStrike.exe (PID: 8936)
- CrowdStrike.exe (PID: 5244)
- Champion.pif (PID: 6396)
- RegAsm.exe (PID: 8896)
Process checks computer location settings
- CrowdStrike.exe (PID: 8936)
- Champion.pif (PID: 8380)
- CrowdStrike.exe (PID: 5244)
Reads mouse settings
- Champion.pif (PID: 8380)
- Champion.pif (PID: 6396)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 8896)
Checks proxy server information
- RegAsm.exe (PID: 8896)
Manual execution by a user
- Taskmgr.exe (PID: 5312)
- Taskmgr.exe (PID: 2204)
- RegAsm.exe (PID: 7232)
- notepad++.exe (PID: 3672)
- WerFault.exe (PID: 7520)
- Taskmgr.exe (PID: 968)
- Taskmgr.exe (PID: 6780)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 2204)
Reads the software policy settings
- RegAsm.exe (PID: 8896)
Attempting to use instant messaging service
- RegAsm.exe (PID: 8896)
Reads Environment values
- RegAsm.exe (PID: 8896)
Disables trace logs
- RegAsm.exe (PID: 8896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.7 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en |
| TaggedPDF: | Yes |
| Author: | Eliza |
| Creator: | Microsoft® Word LTSC |
| CreateDate: | 2024:07:20 11:35:24+03:30 |
| ModifyDate: | 2024:07:20 11:35:24+03:30 |
| Producer: | Microsoft® Word LTSC |
XMP
| XMPToolkit: | 3.1-701 |
|---|---|
| Producer: | Microsoft® Word LTSC |
| Creator: | Eliza |
| CreatorTool: | Microsoft® Word LTSC |
| CreateDate: | 2024:07:20 11:35:24+03:30 |
| ModifyDate: | 2024:07:20 11:35:24+03:30 |
| DocumentID: | uuid:B47B247B-A057-44E2-B84D-C9DB82B7E26A |
| InstanceID: | uuid:B47B247B-A057-44E2-B84D-C9DB82B7E26A |
Total processes
275
Monitored processes
105
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2516 --field-trial-handle=1600,i,4431285975096472131,570738573696107412,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2504 --field-trial-handle=1600,i,4431285975096472131,570738573696107412,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 796 | "C:\WINDOWS\SysWOW64\cmd.exe" /c C:\Users\admin\AppData\Local\Temp\Rar$EXa8604.31388\update\CrowdStrike.exe | C:\Windows\SysWOW64\cmd.exe | Champion.pif | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1068 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6704 --field-trial-handle=2388,i,12835060206259354787,14366823388722948944,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | cmd /c copy /b Treating + Viagra + Vision + Jul + Str 564784\L | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 3221225477 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2748 | C:\WINDOWS\system32\WerFault.exe -u -p 2204 -s 1776 | C:\Windows\System32\WerFault.exe | — | Taskmgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3128 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2136 --field-trial-handle=1600,i,4431285975096472131,570738573696107412,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3548 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
58 170
Read events
57 658
Write events
498
Delete events
14
Modification events
| (PID) Process: | (7628) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | aDefaultRHPViewMode_L |
Value: Expanded | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 3 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumUserDockUndockHUD |
Value: 0 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (4372) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ToolsSearch |
| Operation: | write | Name: | iSearchHintIndex |
Value: 0 | |||
Executable files
14
Suspicious files
1 177
Text files
320
Unknown types
125
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF42bae2.TMP | text | |
MD5:B875B798FCFA464DB41DDC9789BDB161 | SHA256:F6259A0B5E546CB737118D559D0FBDFFDCEC68AD4F7B95451FED263058606B13 | |||
| 4372 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF42b8df.TMP | text | |
MD5:E26AF4B6A1AD62E54D67510EEFE20B2C | SHA256:BF001234CF5F261254DEA1EA459BBFD4A35D15166C765CA3ED9B56D49A04BE1B | |||
| 4372 | Acrobat.exe | C:\USERS\ADMIN\APPDATA\LOCAL\ADOBE\ACROBAT\DC\SOPHIA\ACROBAT\SOPHIA.JSON | binary | |
MD5:79270D9595B259B53E39403366436A8E | SHA256:AD0552A8B392315C512F6DC945F318AD83B98FB64415C0CED694843A3C5D2083 | |||
| 8124 | AdobeARM.exe | C:\Users\admin\AppData\Local\Temp\ArmUI.ini | text | |
MD5:B0DF20BAA9DEE27BDBC3285C7D6D4C57 | SHA256:76362509A8CA3E4A9FDC854C56674083EF77CA2C53628CE0ACF4BB4C42D73894 | |||
| 8124 | AdobeARM.exe | C:\WINDOWS\Temp\ArmReport.ini | text | |
MD5:C4DBB5797C48D30597D78B6277E06350 | SHA256:0AAF07A70C53FB0918539B8CDDE43645CE1E88BC100D899B0718352971F06BCA | |||
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:6894162069E758321B7EA361EC3F15DE | SHA256:FCB3D6E792B5487B105710333488CEA123BE9D3718F647FBD9B453D745467A7D | |||
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:B733E9F7527E6B1C22E22FB1BA3F3CB3 | SHA256:73D209866F38BF4BBCE43696D6CEAB1374EFD861482AD4962001CEC9702DB45D | |||
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:181D7651FBB224ABCC4D367B9FEF4C92 | SHA256:C4C4C964170723490759387679B26386E4888959280802A9FB6430A7E5BCDEB5 | |||
| 7608 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:23FCFB07C75CE7191DD51CBD9DC29AE9 | SHA256:D6E6776431C280214C0C9CCCFF50C44A133D96FE76CEB57BFB4EB6145E15997F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
83
DNS requests
72
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8124 | AdobeARM.exe | GET | 304 | 2.19.126.143:80 | http://acroipm2.adobe.com/assets/Owner/arm/ReportOwner.txt | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 404 | 2.19.126.143:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/OwnerAPI/Rdr.txt | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 304 | 2.19.126.143:80 | http://acroipm2.adobe.com/assets/Owner/arm/ProcessMAU.txt | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 404 | 2.19.126.143:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/UC/Other.txt | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 404 | 2.19.126.143:80 | http://acroipm2.adobe.com/assets/Owner/arm/29/adnme/NoValidReasonForAdnme.txt | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA0aNA9419AA4In9uq1lIt8%3D | unknown | — | — | whitelisted |
7628 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
8124 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
8896 | RegAsm.exe | GET | 200 | 104.16.185.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4716 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2760 | svchost.exe | 40.113.103.199:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4984 | AcroCEF.exe | 184.28.88.176:443 | geo2.adobe.com | AKAMAI-AS | US | unknown |
8124 | AdobeARM.exe | 2.19.126.143:80 | acroipm2.adobe.com | Akamai International B.V. | DE | unknown |
7108 | svchost.exe | 88.221.168.141:443 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
4984 | AcroCEF.exe | 34.237.241.83:443 | p13n.adobe.io | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
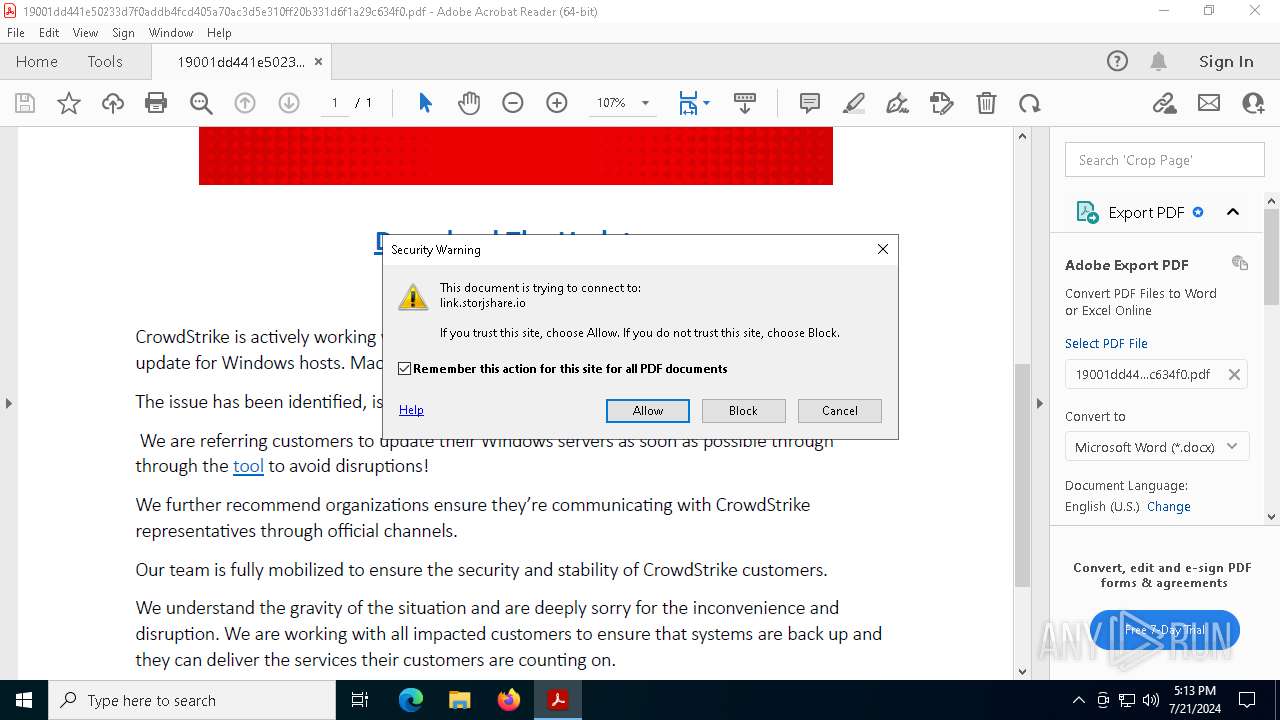
2168 | svchost.exe | Potentially Bad Traffic | ET INFO File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
5848 | msedge.exe | Potentially Bad Traffic | ET INFO File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
5848 | msedge.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Domain (link .storjshare .io in TLS SNI) |
5848 | msedge.exe | Potentially Bad Traffic | ET INFO File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
8896 | RegAsm.exe | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
8896 | RegAsm.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2168 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
8896 | RegAsm.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
8896 | RegAsm.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |