| File name: | 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625 |
| Full analysis: | https://app.any.run/tasks/d906e8bb-783e-4efa-8391-32c3d0cbb3e5 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 16:38:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 30FF054F2AB48237349FB4B392679E3A |
| SHA1: | 80FE1B23C8F08F94E089A1BB46C399AB7B93C556 |
| SHA256: | 18FB7256EF9A19551C2639F8014C9680CA85782FB3D0787C4BB04116D143E625 |
| SSDEEP: | 12288:S7nBJhGs7R9YTToJjG/qXQE+wvDYOoj4nO5ihKnoAK:8BJhlR9YTMJjGgCm0OoB58 |
MALICIOUS
Drops executable file immediately after starts
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
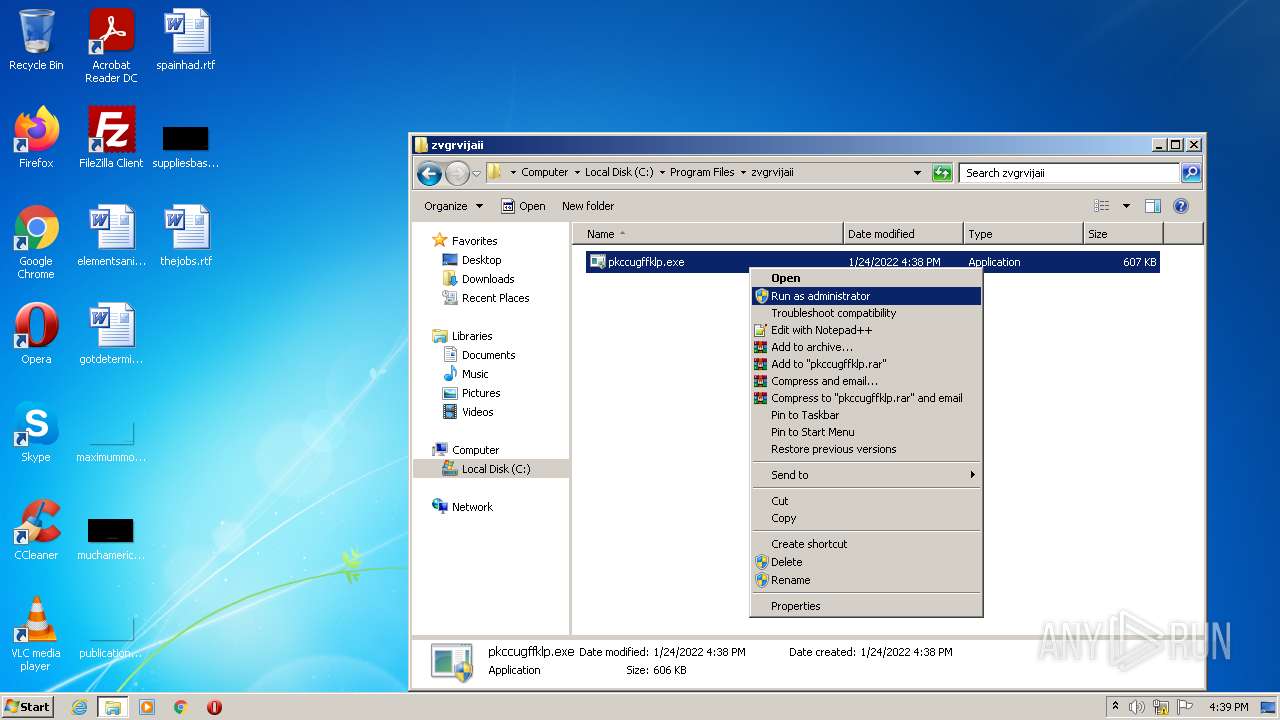
- pkccugffklp.exe (PID: 2932)
- pkccugffklp.exe (PID: 3840)
- zekxrpxhhou.exe (PID: 1700)
- lx.exe (PID: 3068)
- cmhavyeamxvtv.exe (PID: 3964)
SUSPICIOUS
Checks supported languages
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2348)
- pkccugffklp.exe (PID: 2932)
- zekxrpxhhou.exe (PID: 2780)
- pkccugffklp.exe (PID: 3840)
- zekxrpxhhou.exe (PID: 1700)
- lx.exe (PID: 2308)
- iazfgwyjc.exe (PID: 3352)
- cmhavyeamxvtv.exe (PID: 3252)
- cmhavyeamxvtv.exe (PID: 3964)
- lx.exe (PID: 3068)
- litt.exe (PID: 3704)
Starts itself from another location
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2932)
- zekxrpxhhou.exe (PID: 1700)
- pkccugffklp.exe (PID: 3840)
- lx.exe (PID: 3068)
- cmhavyeamxvtv.exe (PID: 3964)
Executable content was dropped or overwritten
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2932)
- pkccugffklp.exe (PID: 3840)
- zekxrpxhhou.exe (PID: 1700)
- lx.exe (PID: 3068)
- cmhavyeamxvtv.exe (PID: 3964)
Creates files in the program directory
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2932)
- zekxrpxhhou.exe (PID: 1700)
- pkccugffklp.exe (PID: 3840)
- lx.exe (PID: 3068)
- cmhavyeamxvtv.exe (PID: 3964)
Drops a file with too old compile date
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2932)
- pkccugffklp.exe (PID: 3840)
- lx.exe (PID: 3068)
- zekxrpxhhou.exe (PID: 1700)
- cmhavyeamxvtv.exe (PID: 3964)
Creates a directory in Program Files
- 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe (PID: 3948)
- pkccugffklp.exe (PID: 2932)
- zekxrpxhhou.exe (PID: 1700)
- pkccugffklp.exe (PID: 3840)
- lx.exe (PID: 3068)
- cmhavyeamxvtv.exe (PID: 3964)
INFO
Manual execution by user
- pkccugffklp.exe (PID: 2844)
- pkccugffklp.exe (PID: 2932)
- pkccugffklp.exe (PID: 3840)
- zekxrpxhhou.exe (PID: 1700)
- cmhavyeamxvtv.exe (PID: 3964)
- cmhavyeamxvtv.exe (PID: 3608)
- lx.exe (PID: 464)
- lx.exe (PID: 3068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x778f1 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 18432 |
| CodeSize: | 86528 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 9 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x000150E8 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
DATA | 0x00017000 | 0x000005C8 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
BSS | 0x00018000 | 0x0000089D | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00019000 | 0x00000D6A | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.tls | 0x0001A000 | 0x0000000C | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x0001B000 | 0x00000018 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 0 |
.vmp0 | 0x0001C000 | 0x0002A606 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.vmp1 | 0x00047000 | 0x00044B3F | 0x00044C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.94294 |
.rsrc | 0x0008C000 | 0x000016B4 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_SHARED | 4.44896 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.13025 | 702 | UNKNOWN | Russian - Russia | RT_MANIFEST |
4090 | 5.72373 | 624 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 7.44362 | 428 | UNKNOWN | UNKNOWN | RT_STRING |
4092 | 7.12712 | 236 | UNKNOWN | UNKNOWN | RT_STRING |
4093 | 7.53235 | 484 | UNKNOWN | UNKNOWN | RT_STRING |
4094 | 7.7906 | 1012 | UNKNOWN | UNKNOWN | RT_STRING |
4095 | 7.70433 | 820 | UNKNOWN | UNKNOWN | RT_STRING |
4096 | 7.71491 | 692 | UNKNOWN | UNKNOWN | RT_STRING |
DVCLAL | 3.875 | 16 | UNKNOWN | UNKNOWN | RT_RCDATA |
PACKAGEINFO | 6.93736 | 188 | UNKNOWN | UNKNOWN | RT_RCDATA |
Imports
advapi32.dll |
kernel32.dll |
oleaut32.dll |
user32.dll |
Total processes
73
Monitored processes
16
Malicious processes
0
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 464 | "C:\Program Files\gylwt\lx.exe" | C:\Program Files\gylwt\lx.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1700 | "C:\Program Files\rxzfrdme\zekxrpxhhou.exe" | C:\Program Files\rxzfrdme\zekxrpxhhou.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\gylwt\lx.exe" | C:\Program Files\gylwt\lx.exe | — | zekxrpxhhou.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\zvgrvijaii\pkccugffklp.exe" | C:\Program Files\zvgrvijaii\pkccugffklp.exe | — | 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2780 | "C:\Program Files\rxzfrdme\zekxrpxhhou.exe" | C:\Program Files\rxzfrdme\zekxrpxhhou.exe | — | pkccugffklp.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\zvgrvijaii\pkccugffklp.exe" | C:\Program Files\zvgrvijaii\pkccugffklp.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\zvgrvijaii\pkccugffklp.exe" | C:\Program Files\zvgrvijaii\pkccugffklp.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3068 | "C:\Program Files\gylwt\lx.exe" | C:\Program Files\gylwt\lx.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3144 | "C:\Users\admin\AppData\Local\Temp\18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe" | C:\Users\admin\AppData\Local\Temp\18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3252 | "C:\Program Files\sneebebm\cmhavyeamxvtv.exe" | C:\Program Files\sneebebm\cmhavyeamxvtv.exe | — | lx.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
108
Read events
108
Write events
0
Delete events
0
Modification events
Executable files
6
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | lx.exe | C:\Program Files\sneebebm\cmhavyeamxvtv.exe | executable | |
MD5:— | SHA256:— | |||
| 3948 | 18fb7256ef9a19551c2639f8014c9680ca85782fb3d0787c4bb04116d143e625.exe | C:\Program Files\zvgrvijaii\pkccugffklp.exe | executable | |
MD5:— | SHA256:— | |||
| 3840 | pkccugffklp.exe | C:\Program Files\zxglwtrbma\iazfgwyjc.exe | executable | |
MD5:— | SHA256:— | |||
| 1700 | zekxrpxhhou.exe | C:\Program Files\gylwt\lx.exe | executable | |
MD5:— | SHA256:— | |||
| 3964 | cmhavyeamxvtv.exe | C:\Program Files\fnige\litt.exe | executable | |
MD5:— | SHA256:— | |||
| 2932 | pkccugffklp.exe | C:\Program Files\rxzfrdme\zekxrpxhhou.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report