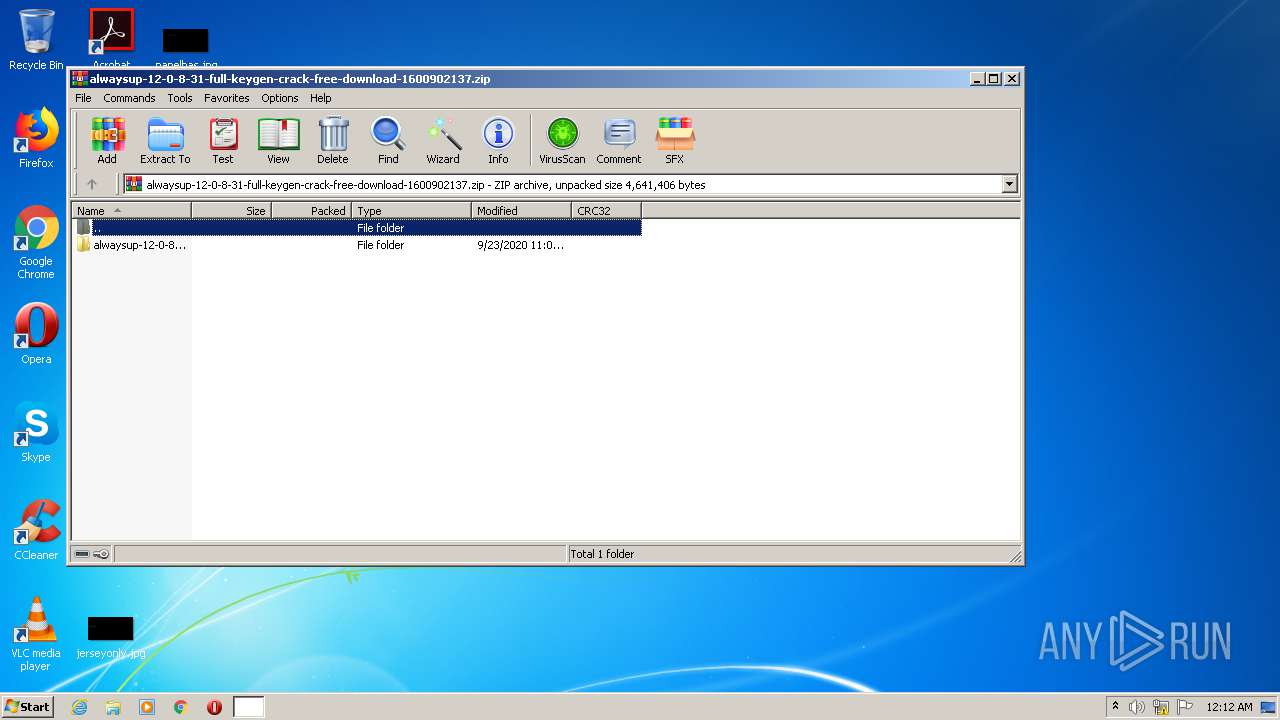
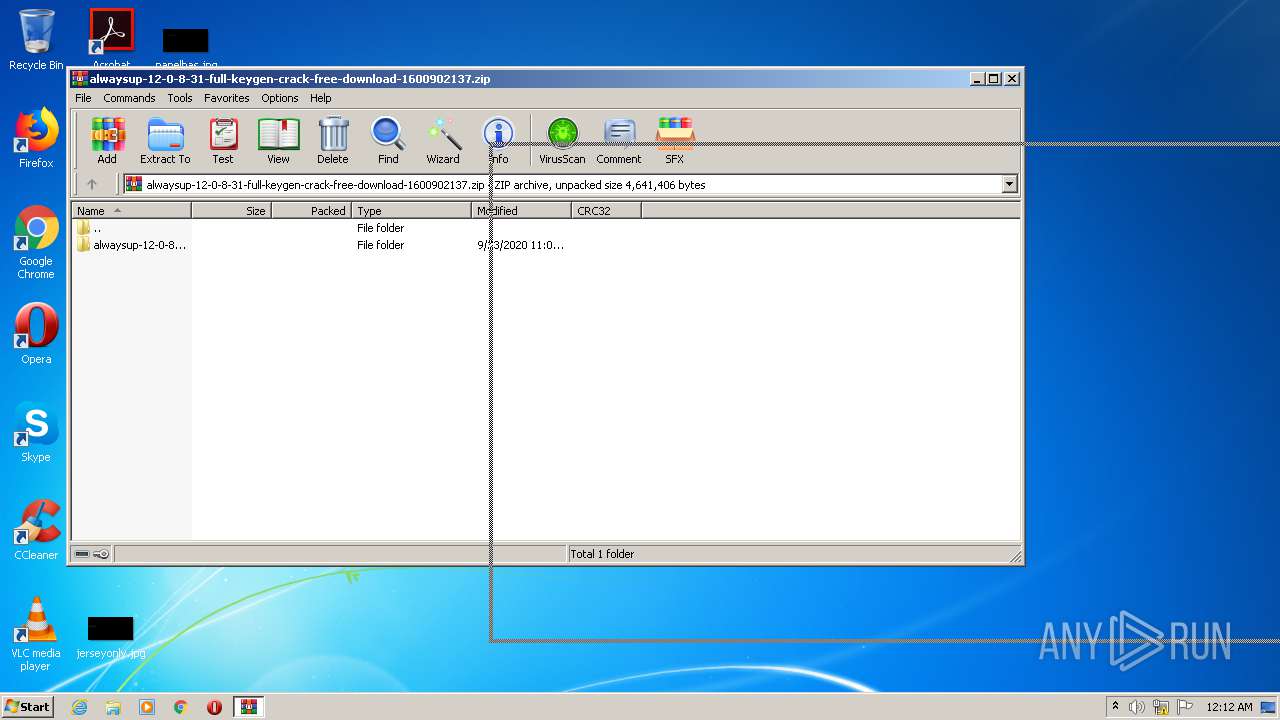
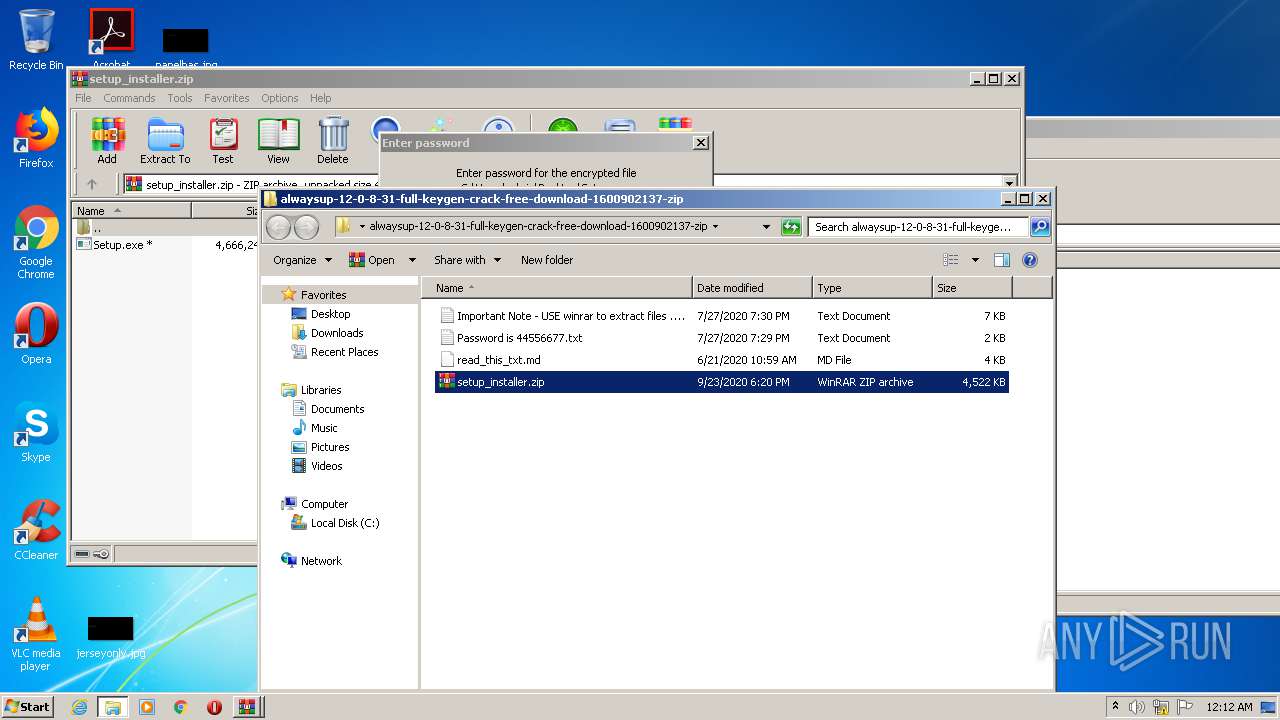
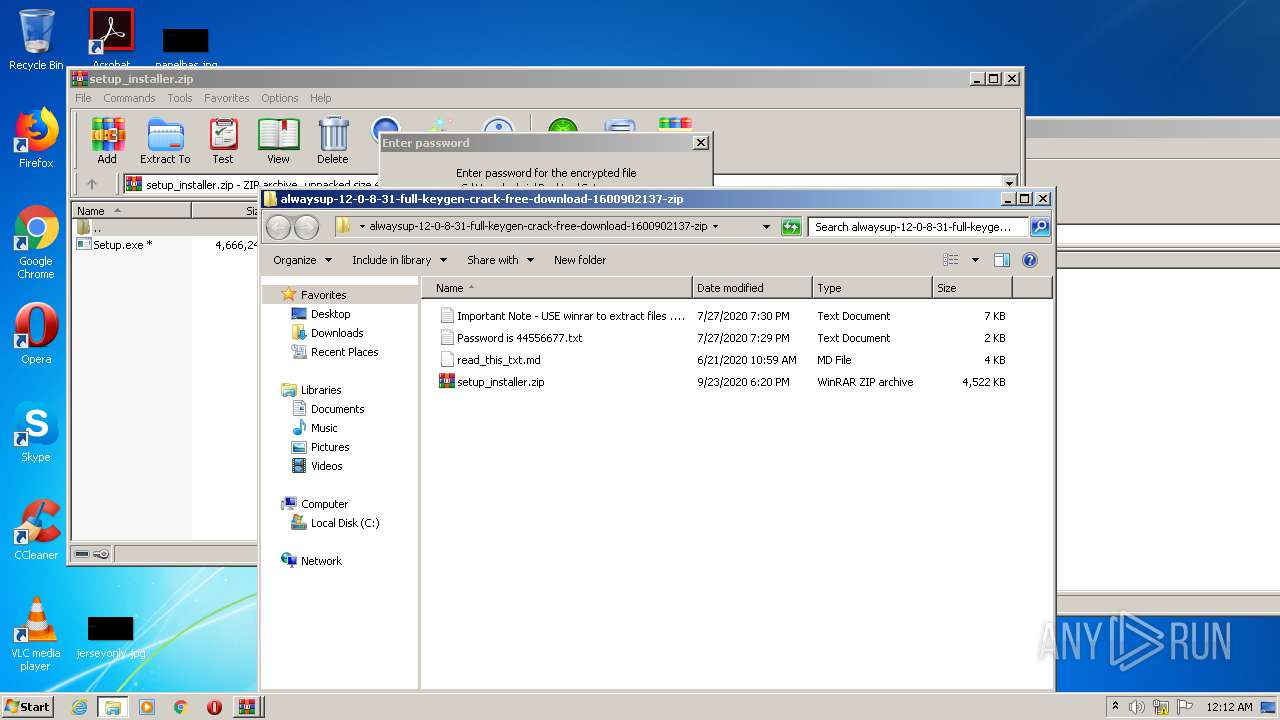
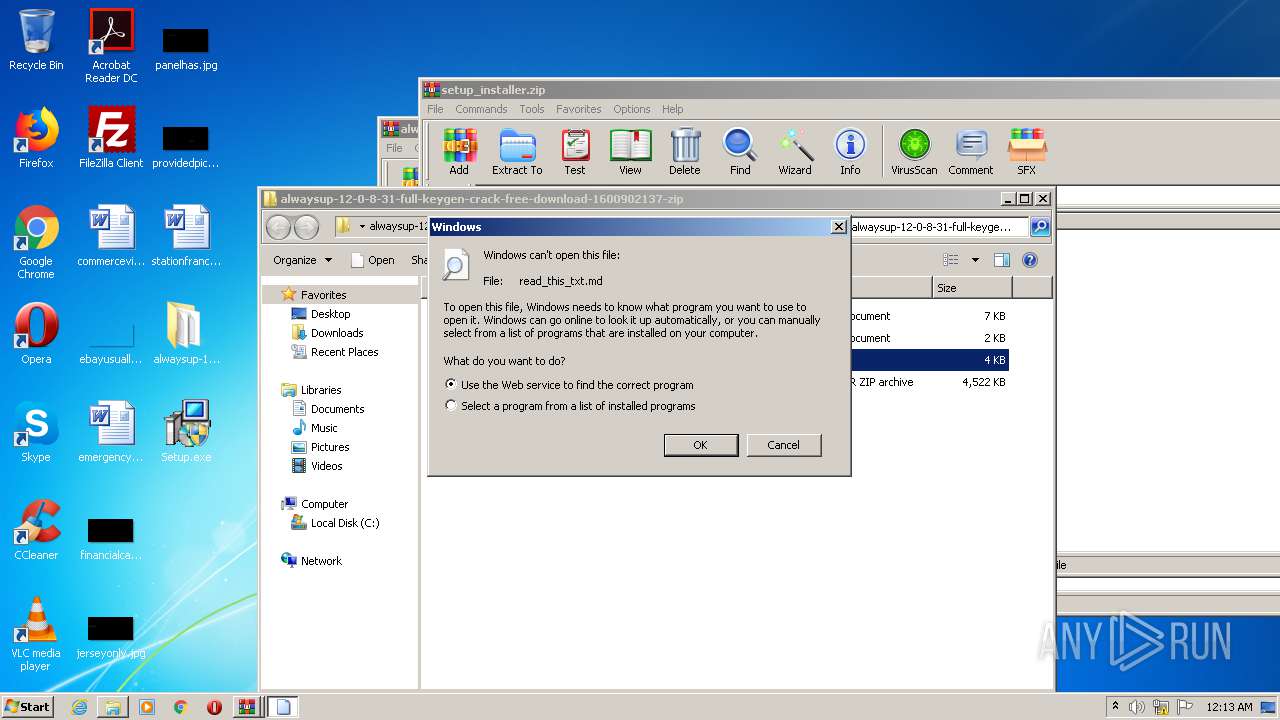
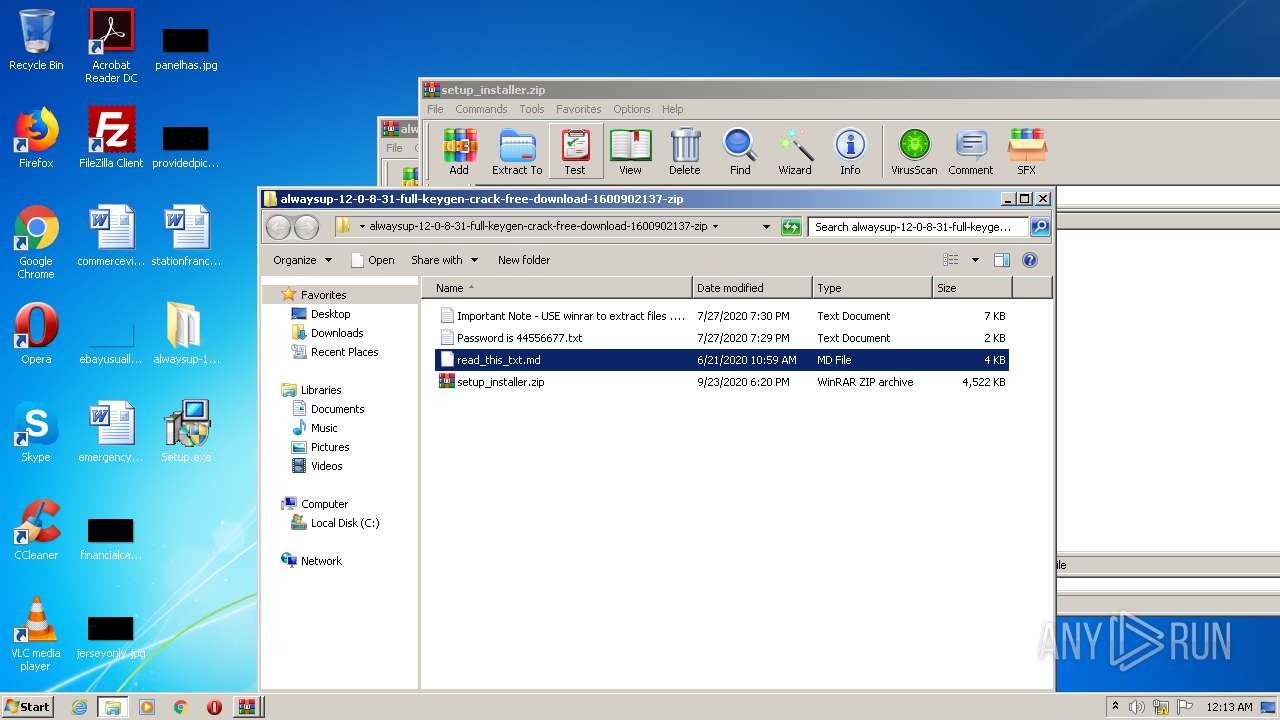
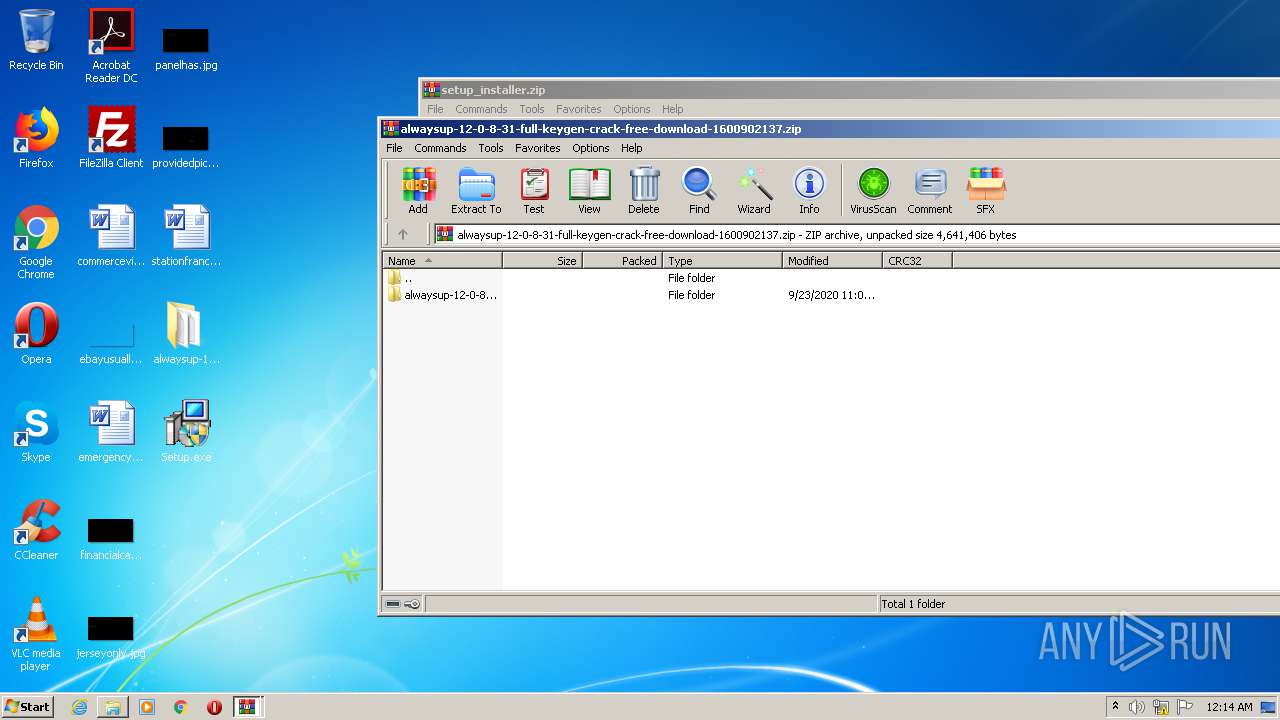
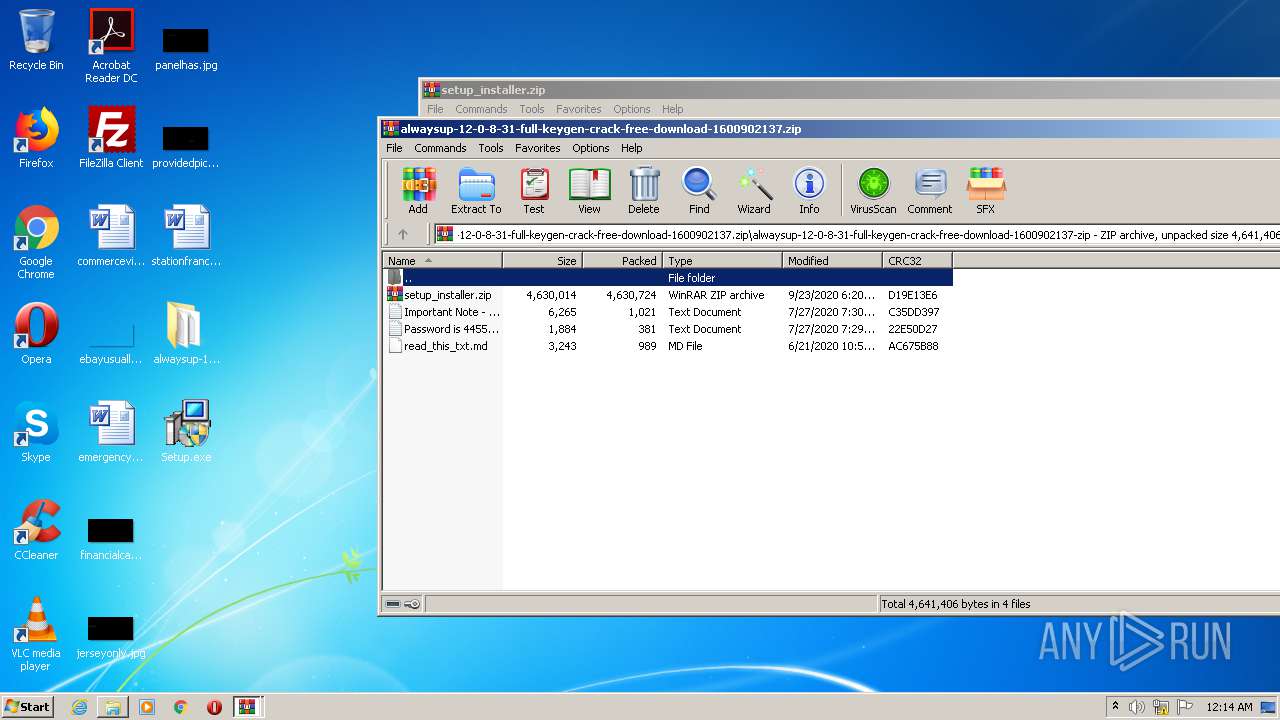
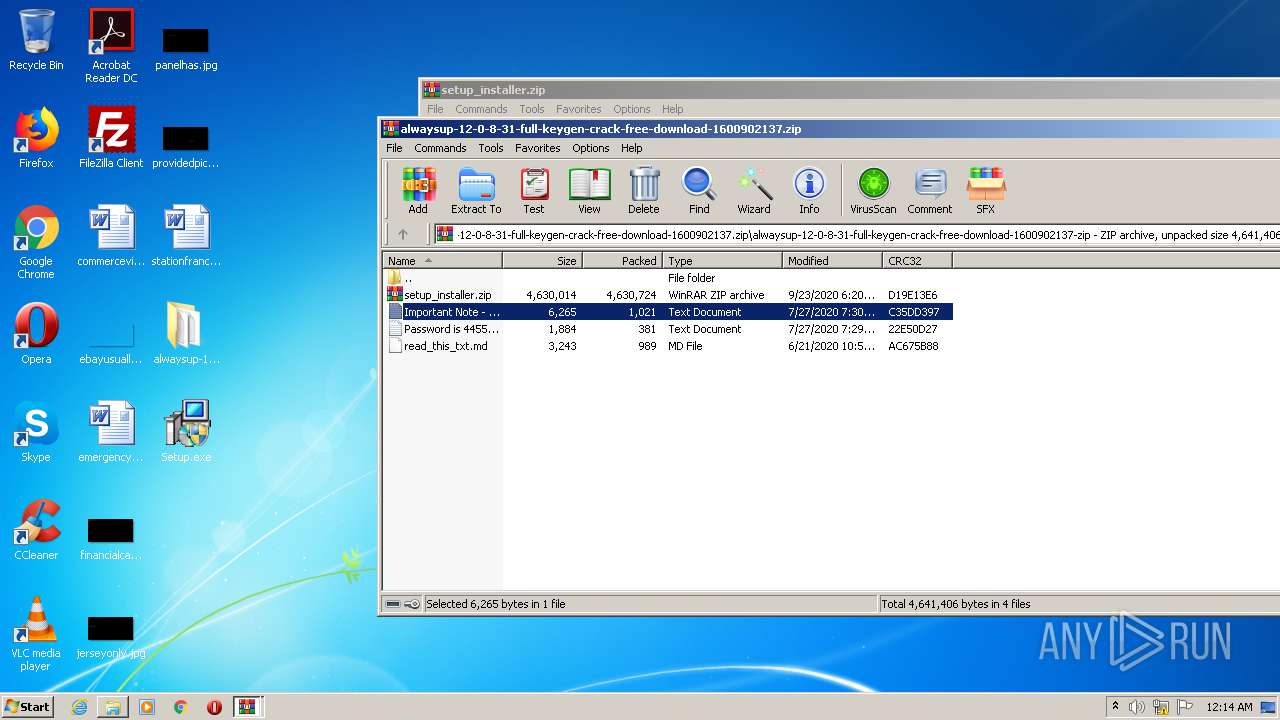
| File name: | alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137.zip |
| Full analysis: | https://app.any.run/tasks/85d19971-4045-4ec9-b221-a59d9b3ec10b |
| Verdict: | Malicious activity |
| Analysis date: | September 23, 2020, 23:11:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A70EBC90BDDB63D42AD22C47E718D950 |
| SHA1: | E693EFFEEE9DB0834408BFD9662AFF3A4270DEA5 |
| SHA256: | 18F806AD1738BAD221984A9D4636AD55FDC230359E34B2F1D232B28AD1698062 |
| SSDEEP: | 98304:MBdeAj8/7EyWHSX1vVt/bNIgpi6DhWOOwEdlUVsiJu1zROo4LX:MBwAjA7ExyXXtxIgg6DhJkLUm/aX |
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 2420)
- Setup.exe (PID: 3688)
- nsB7EF.tmp (PID: 3416)
- Setup.exe (PID: 3756)
- Setup.exe (PID: 3568)
- nsDFF9.tmp (PID: 1980)
- Setup.exe (PID: 292)
- Setup.exe (PID: 3000)
- ns617D.tmp (PID: 3984)
- Setup.exe (PID: 1820)
- Setup.exe (PID: 656)
- nsEA5.tmp (PID: 2868)
Loads dropped or rewritten executable
- Setup.exe (PID: 3756)
- Setup.exe (PID: 3688)
- Setup.exe (PID: 3000)
- Setup.exe (PID: 656)
Changes settings of System certificates
- CScript.exe (PID: 772)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3564)
- Setup.exe (PID: 3688)
- Setup.exe (PID: 3756)
- Setup.exe (PID: 3000)
- Setup.exe (PID: 656)
Starts application with an unusual extension
- Setup.exe (PID: 3688)
- Setup.exe (PID: 3756)
- Setup.exe (PID: 3000)
- Setup.exe (PID: 656)
Creates files in the program directory
- Setup.exe (PID: 3688)
- Setup.exe (PID: 3756)
- Setup.exe (PID: 3000)
- Setup.exe (PID: 656)
Reads Internet Cache Settings
- CScript.exe (PID: 772)
- CScript.exe (PID: 480)
- CScript.exe (PID: 2936)
- CScript.exe (PID: 3488)
Executes scripts
- nsDFF9.tmp (PID: 1980)
- nsB7EF.tmp (PID: 3416)
- ns617D.tmp (PID: 3984)
- nsEA5.tmp (PID: 2868)
Adds / modifies Windows certificates
- CScript.exe (PID: 772)
INFO
Manual execution by user
- Setup.exe (PID: 2420)
- Setup.exe (PID: 3688)
- Setup.exe (PID: 3568)
- rundll32.exe (PID: 2132)
- Setup.exe (PID: 292)
- Setup.exe (PID: 3756)
- Setup.exe (PID: 1820)
- Setup.exe (PID: 656)
- Setup.exe (PID: 3000)
- WinRAR.exe (PID: 3564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:09:23 23:02:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip/ |
Total processes
76
Monitored processes
20
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
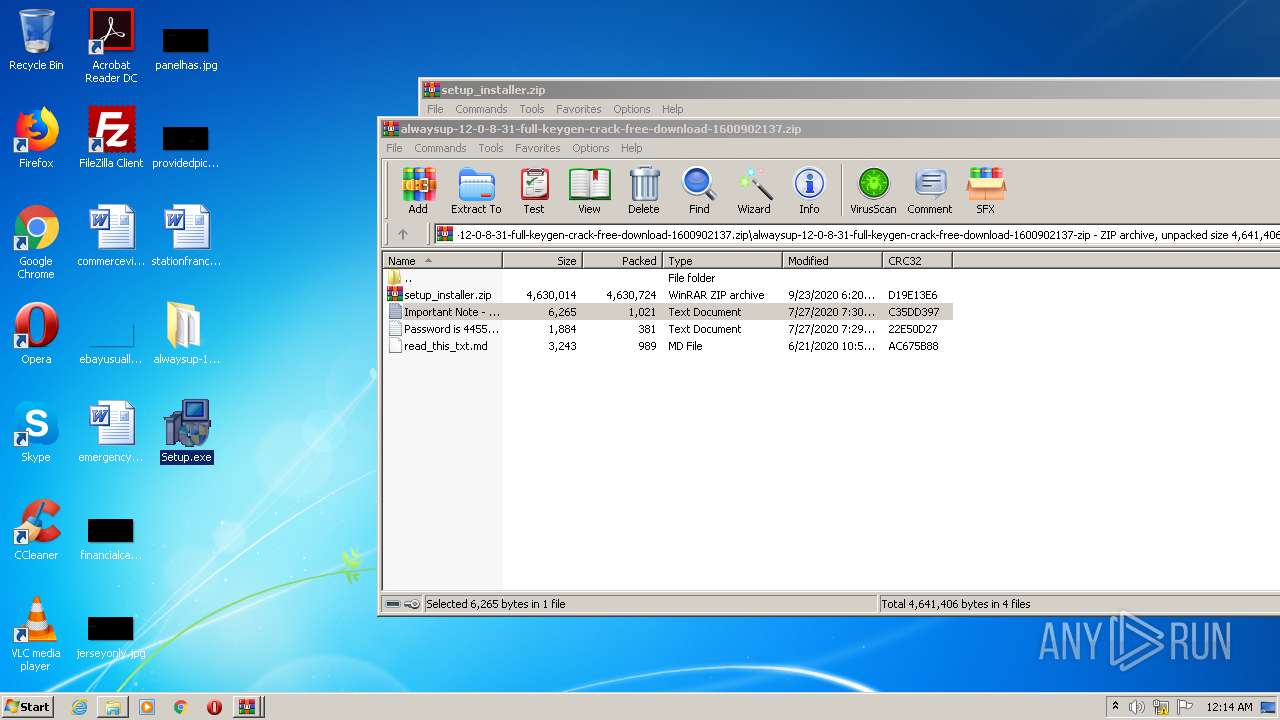
| 292 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 4.2.0.0 Modules
| |||||||||||||||
| 480 | "C:\Windows\system32\CScript.exe" "C:\Program Files\Jaoler\kader\Setup3.vbs" //e:vbscript //B //NOLOGO | C:\Windows\system32\CScript.exe | nsDFF9.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
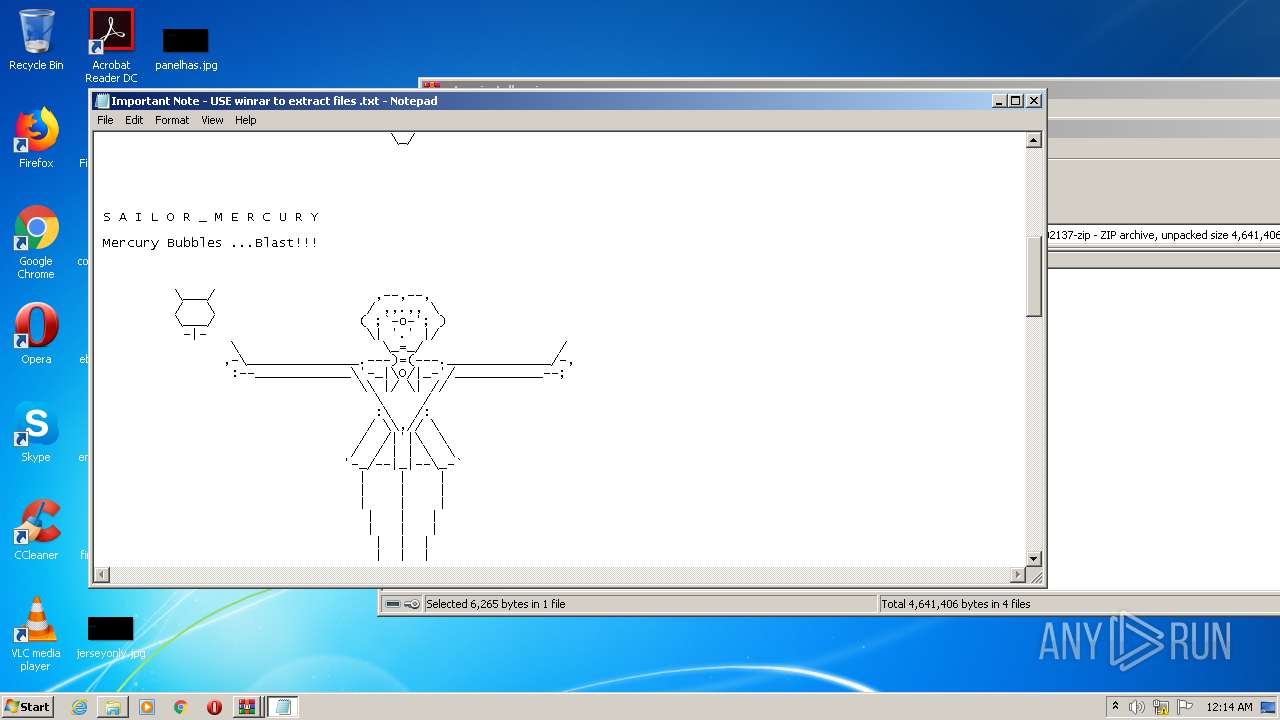
| 540 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa1704.18261\Important Note - USE winrar to extract files .txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Version: 4.2.0.0 Modules
| |||||||||||||||
| 772 | "C:\Windows\system32\CScript.exe" "C:\Program Files\Jaoler\kader\Setup3.vbs" //e:vbscript //B //NOLOGO | C:\Windows\system32\CScript.exe | nsB7EF.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
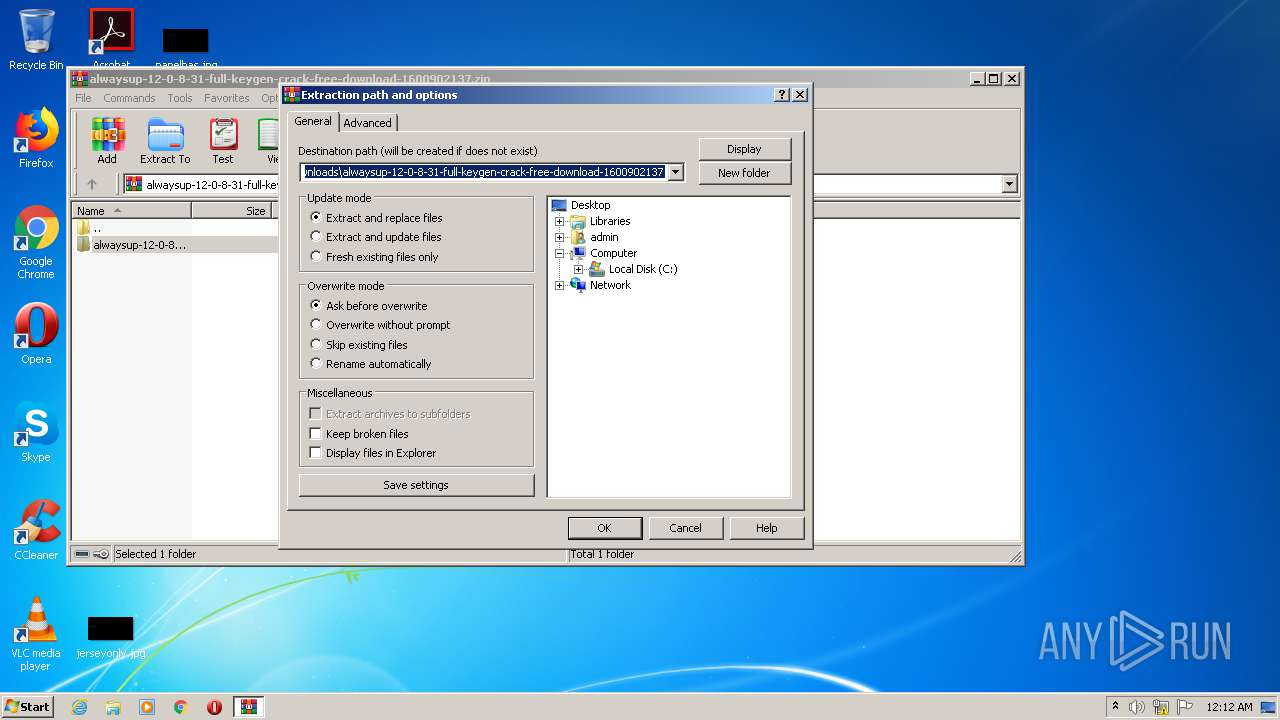
| 1704 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 4.2.0.0 Modules
| |||||||||||||||
| 1980 | "C:\Users\admin\AppData\Local\Temp\nsvDF9A.tmp\nsDFF9.tmp" "C:\Windows\system32\CScript.exe" "C:\Program Files\Jaoler\kader\Setup3.vbs" //e:vbscript //B //NOLOGO | C:\Users\admin\AppData\Local\Temp\nsvDF9A.tmp\nsDFF9.tmp | — | Setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2132 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip\read_this_txt.md | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 4.2.0.0 Modules
| |||||||||||||||
Total events
1 112
Read events
1 007
Write events
105
Delete events
0
Modification events
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137.zip | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1704) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (3564) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
21
Suspicious files
5
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 772 | CScript.exe | C:\Users\admin\AppData\Local\Temp\CabBC03.tmp | — | |
MD5:— | SHA256:— | |||
| 772 | CScript.exe | C:\Users\admin\AppData\Local\Temp\TarBC04.tmp | — | |
MD5:— | SHA256:— | |||
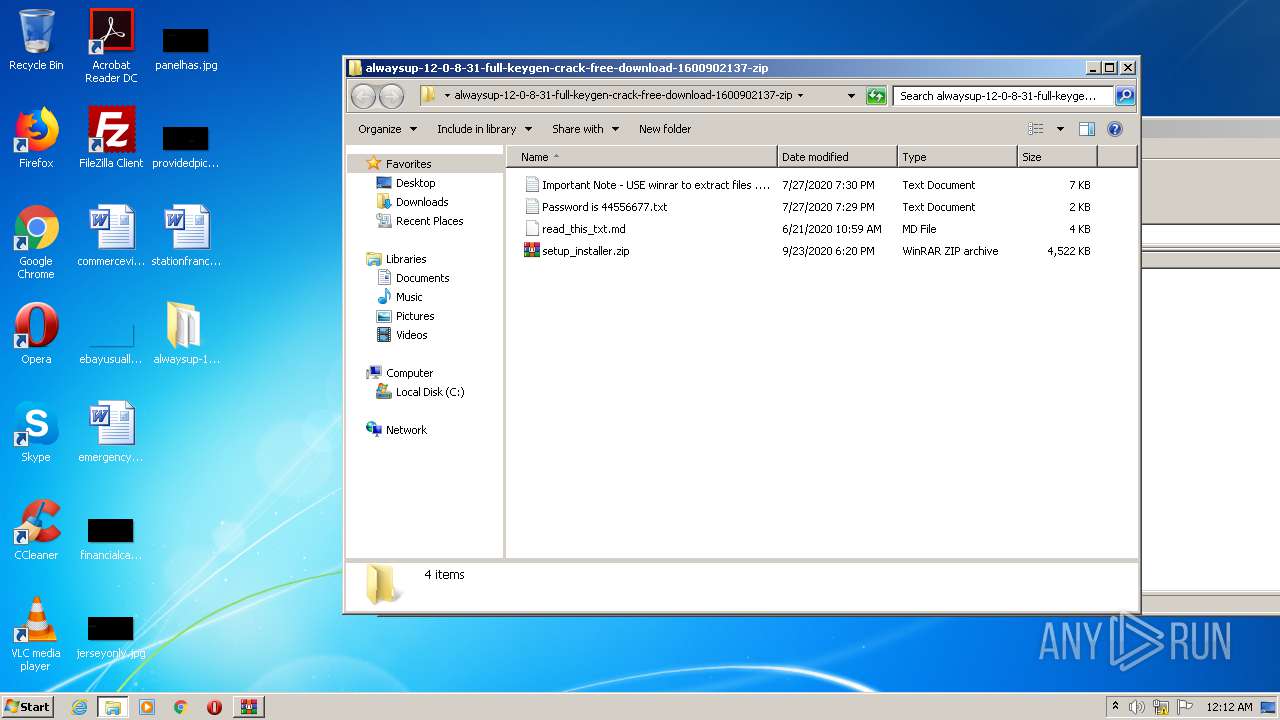
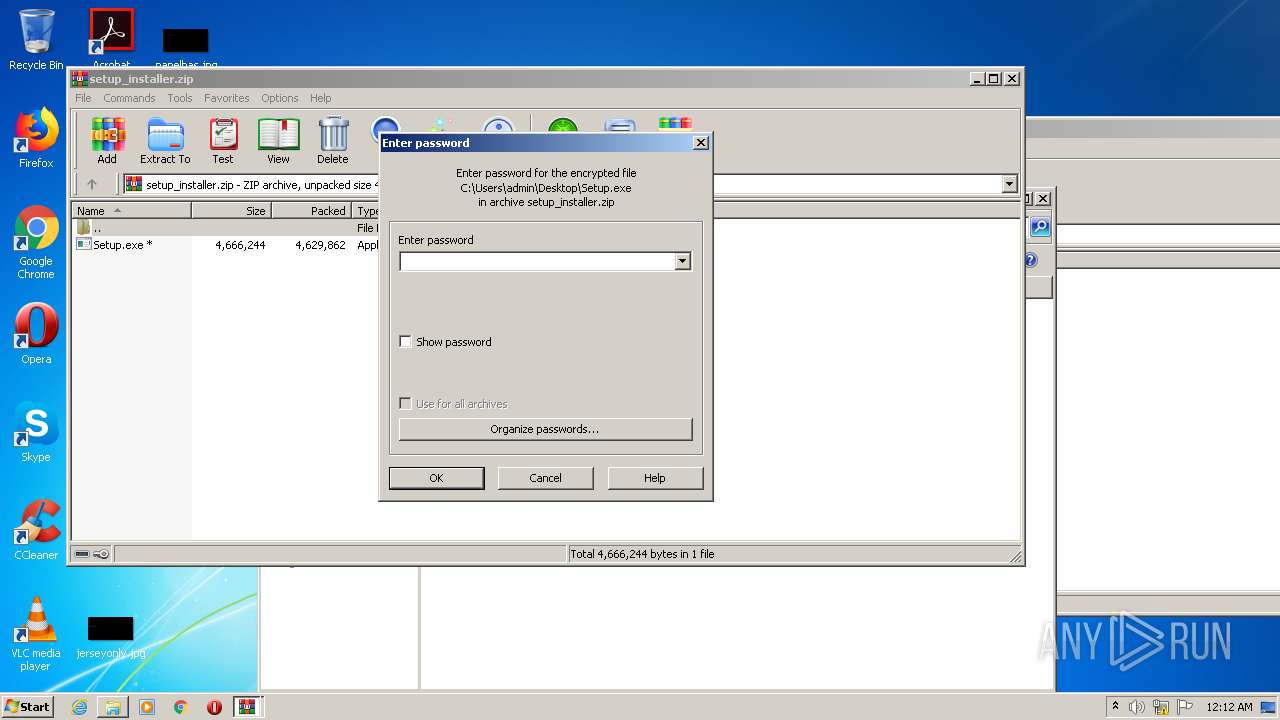
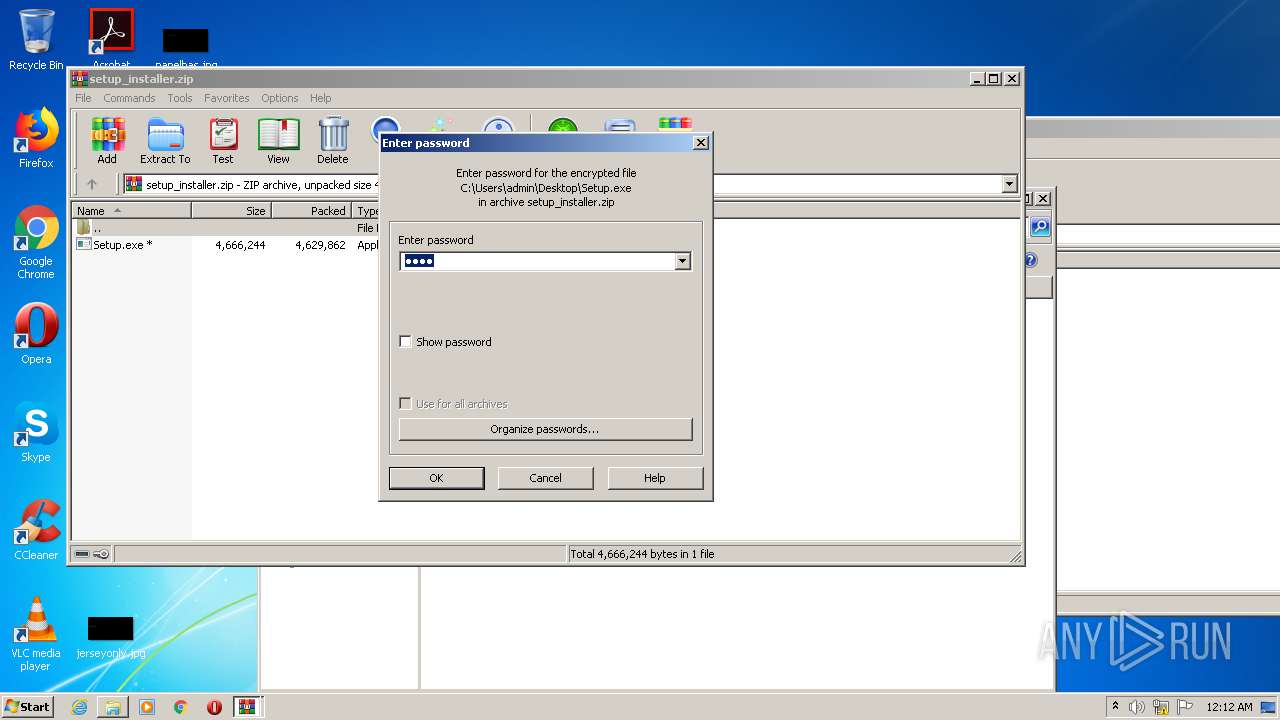
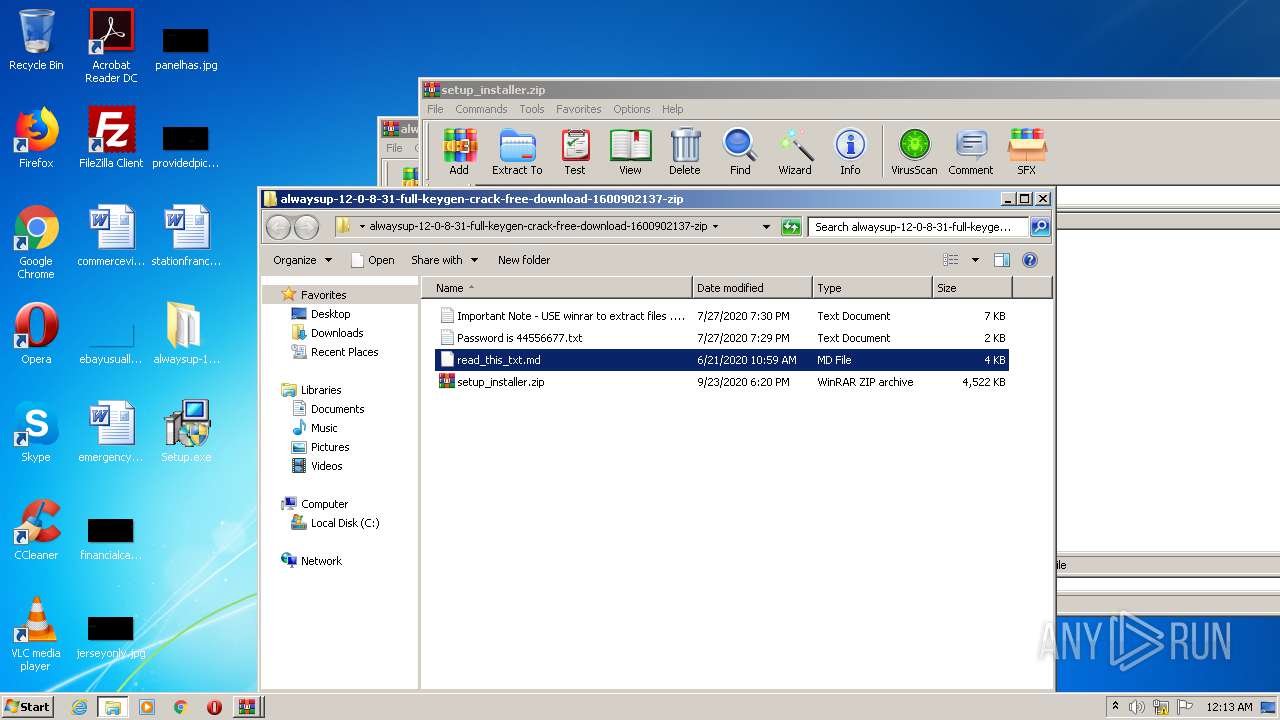
| 1704 | WinRAR.exe | C:\Users\admin\Desktop\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip\Important Note - USE winrar to extract files .txt | text | |
MD5:— | SHA256:— | |||
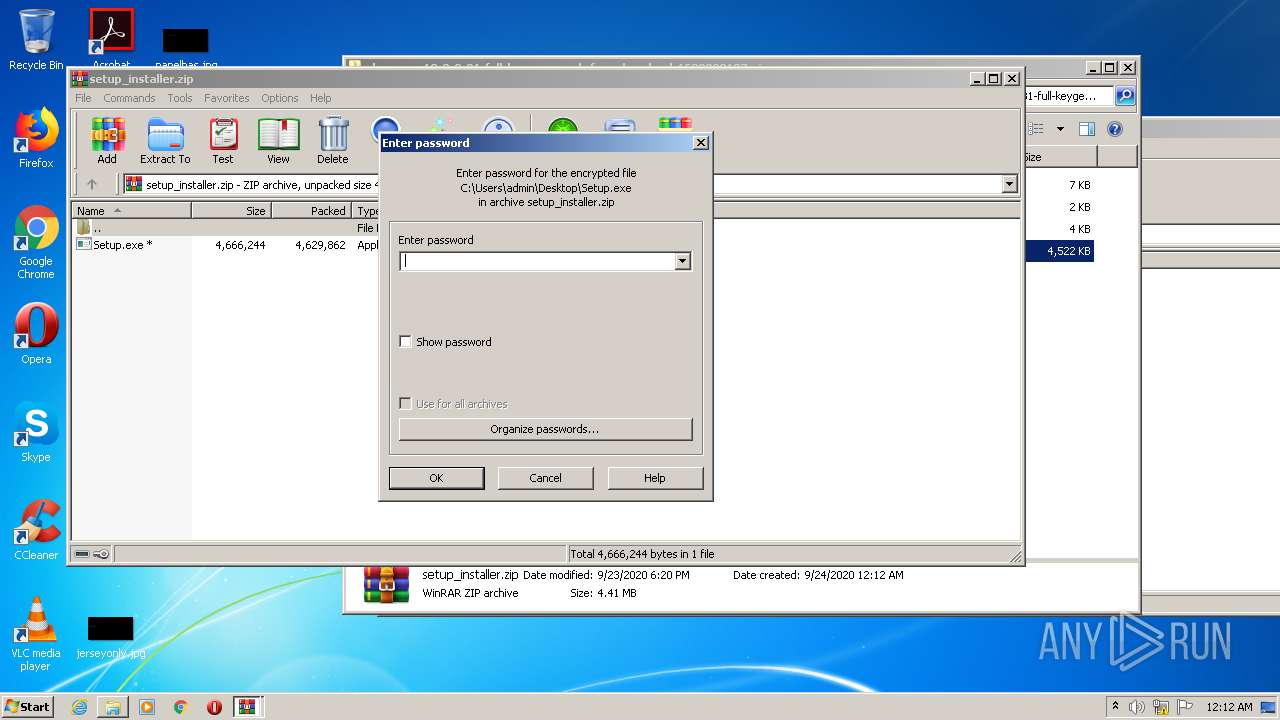
| 1704 | WinRAR.exe | C:\Users\admin\Desktop\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip\Password is 44556677.txt | text | |
MD5:— | SHA256:— | |||
| 480 | CScript.exe | C:\Users\admin\AppData\Local\Temp\CabE287.tmp | — | |
MD5:— | SHA256:— | |||
| 480 | CScript.exe | C:\Users\admin\AppData\Local\Temp\TarE288.tmp | — | |
MD5:— | SHA256:— | |||
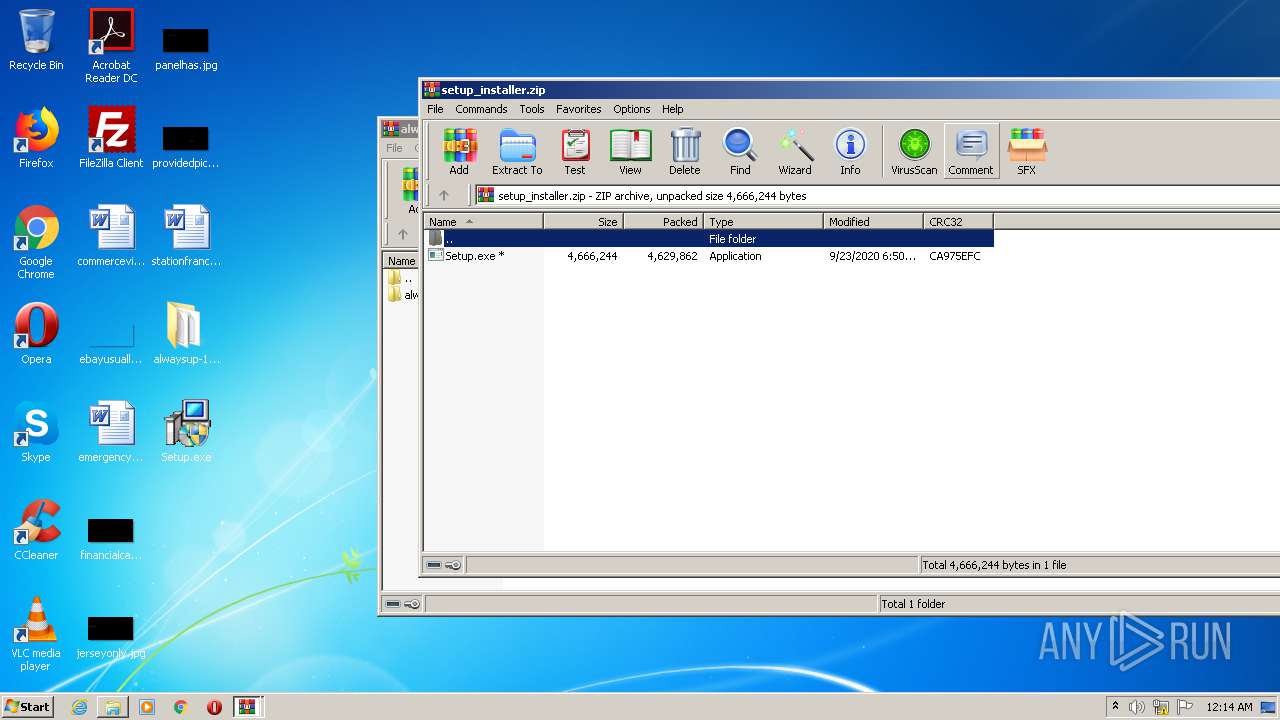
| 3564 | WinRAR.exe | C:\Users\admin\Desktop\Setup.exe | executable | |
MD5:— | SHA256:— | |||
| 1704 | WinRAR.exe | C:\Users\admin\Desktop\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip\read_this_txt.md | text | |
MD5:— | SHA256:— | |||
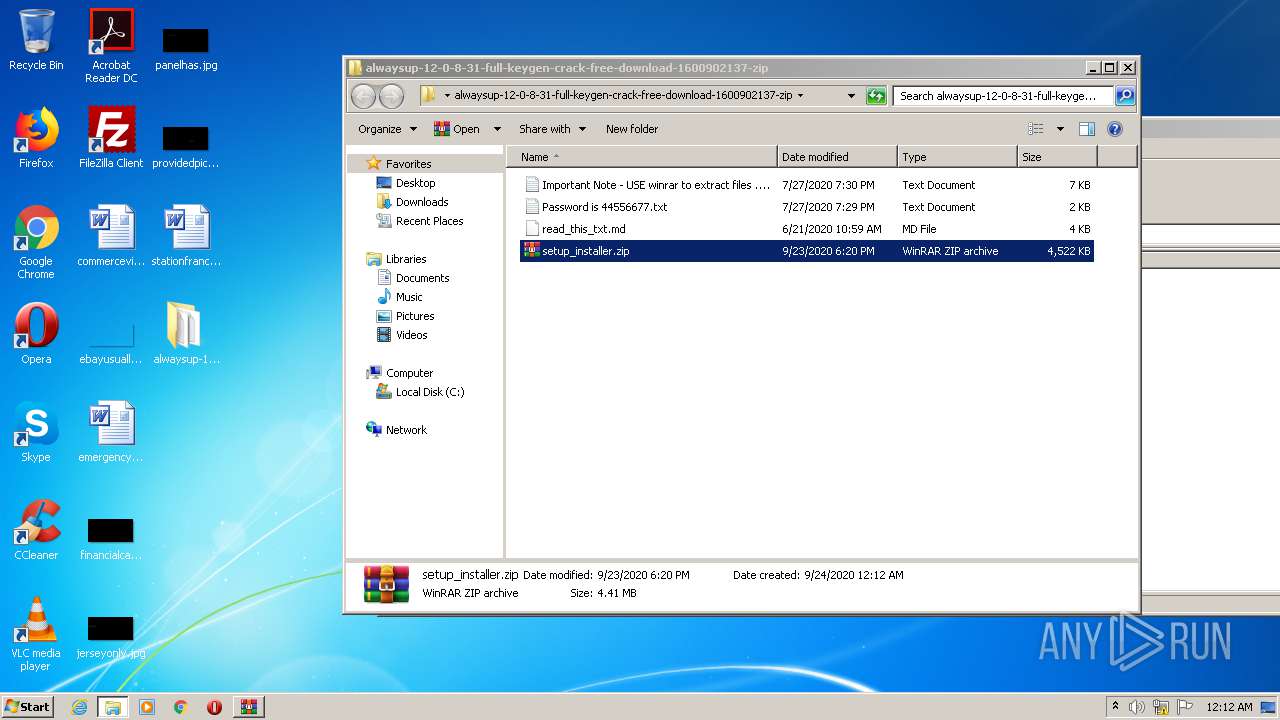
| 1704 | WinRAR.exe | C:\Users\admin\Desktop\alwaysup-12-0-8-31-full-keygen-crack-free-download-1600902137-zip\setup_installer.zip | compressed | |
MD5:— | SHA256:— | |||
| 3688 | Setup.exe | C:\Program Files\Jaoler\kader\Setup3.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
4
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
772 | CScript.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
772 | CScript.exe | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgOFvRj973rrPO3ypqcX4igUEQ%3D%3D | unknown | der | 527 b | whitelisted |
1048 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
772 | CScript.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
772 | CScript.exe | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
772 | CScript.exe | 2.16.186.27:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
480 | CScript.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
2936 | CScript.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
1048 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3488 | CScript.exe | 88.99.66.31:443 | iplogger.org | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
iplogger.org |
| shared |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
772 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
772 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
480 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
480 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2936 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2936 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
3488 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
3488 | CScript.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
9 ETPRO signatures available at the full report