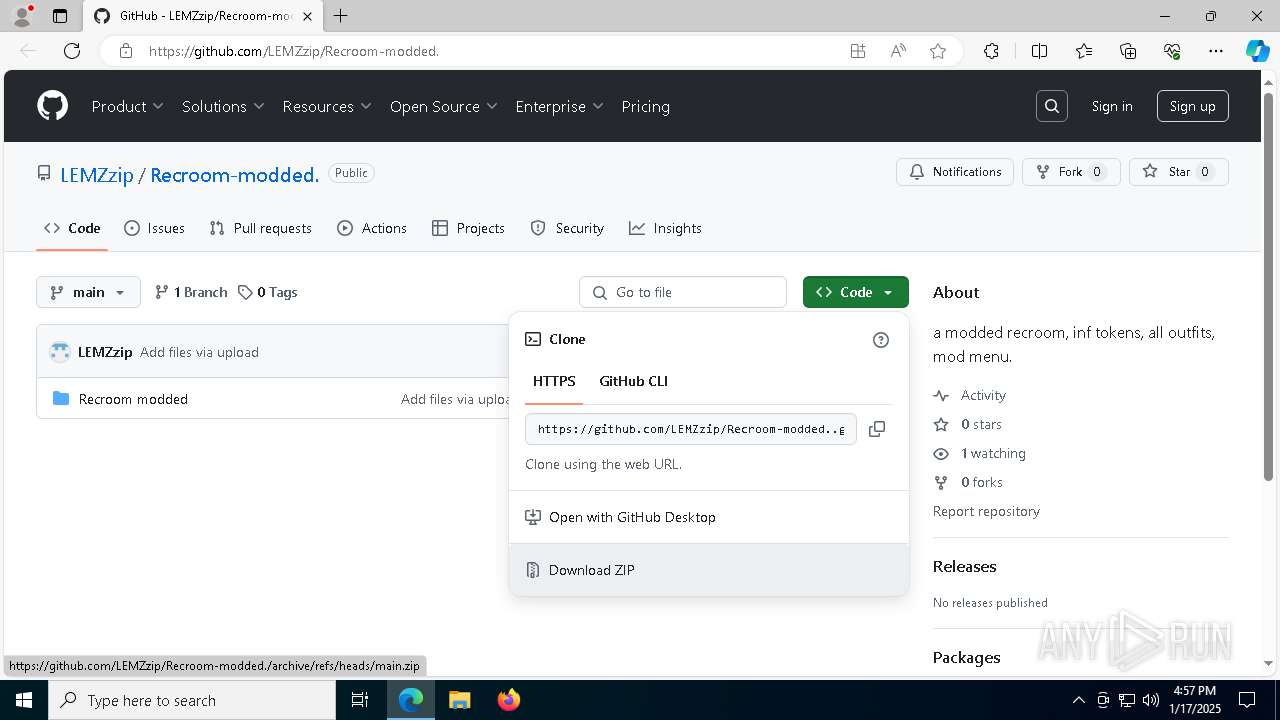
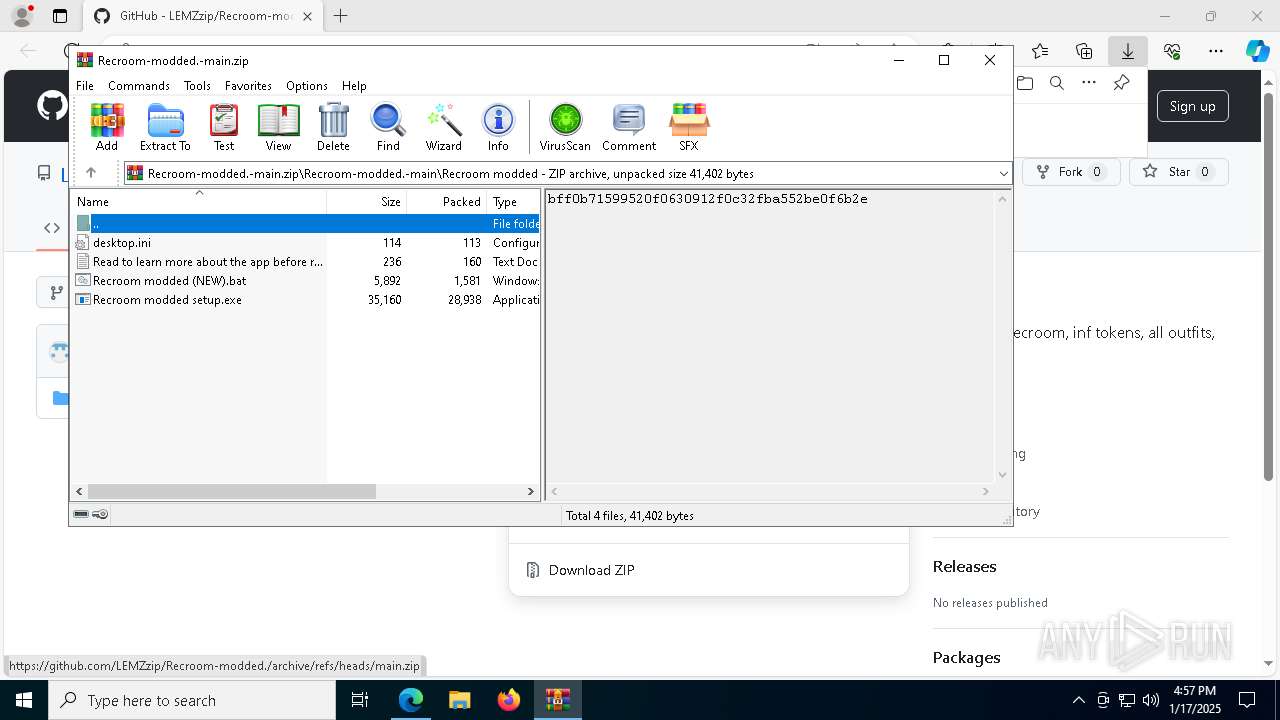
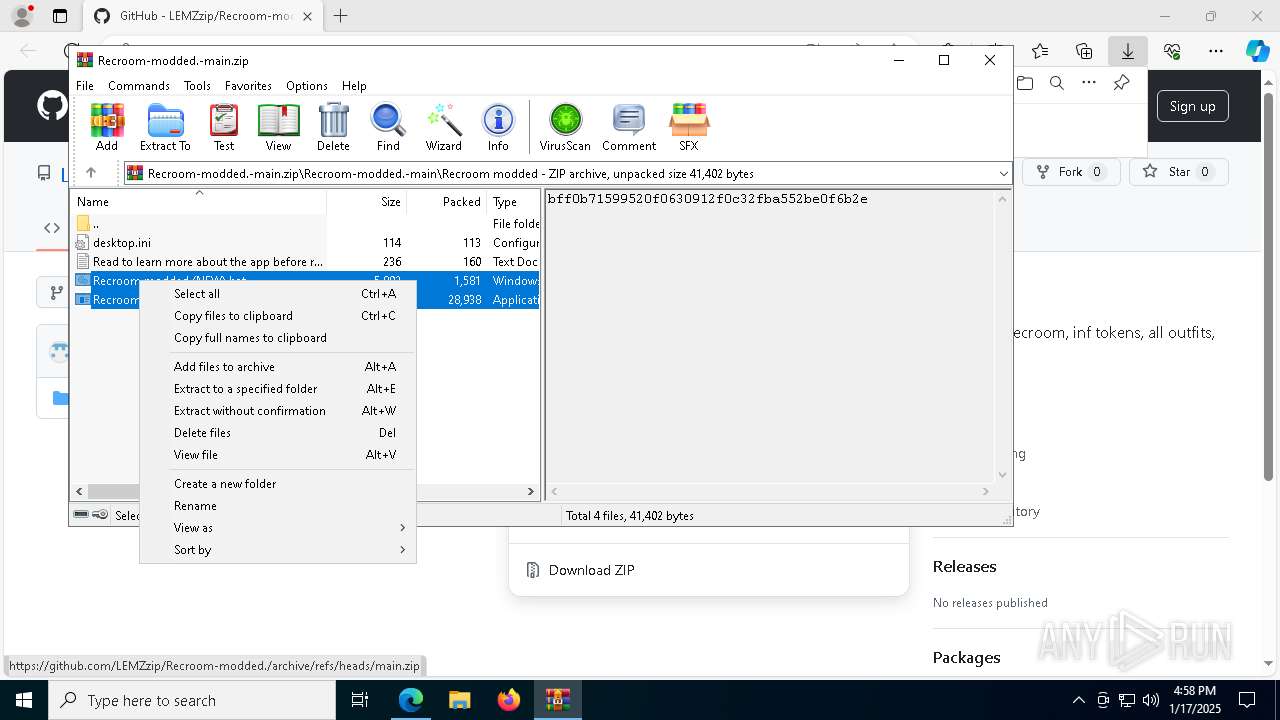
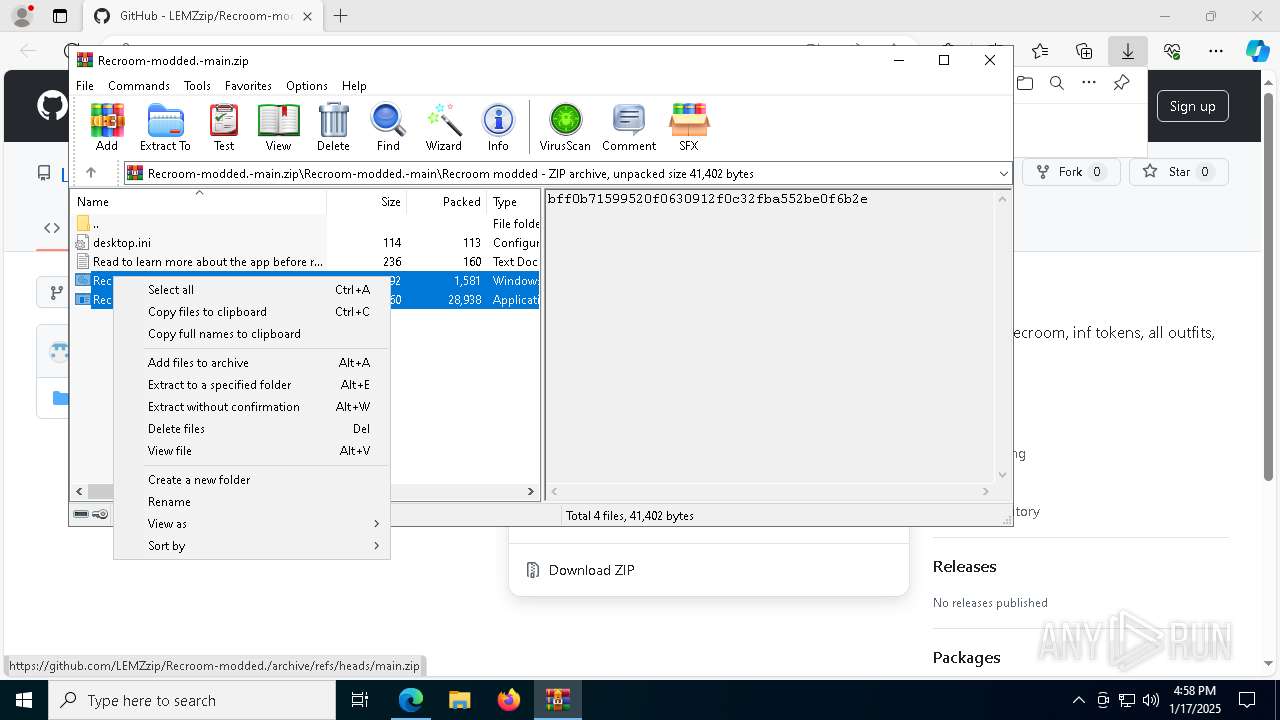
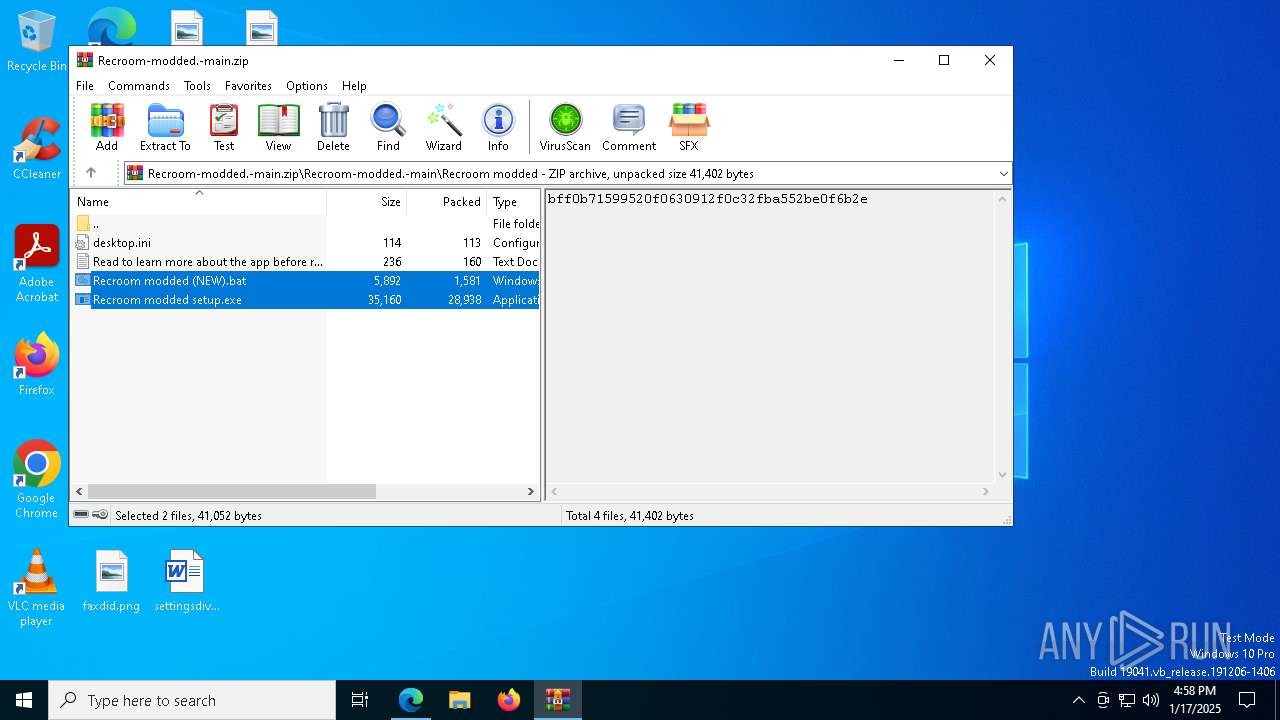
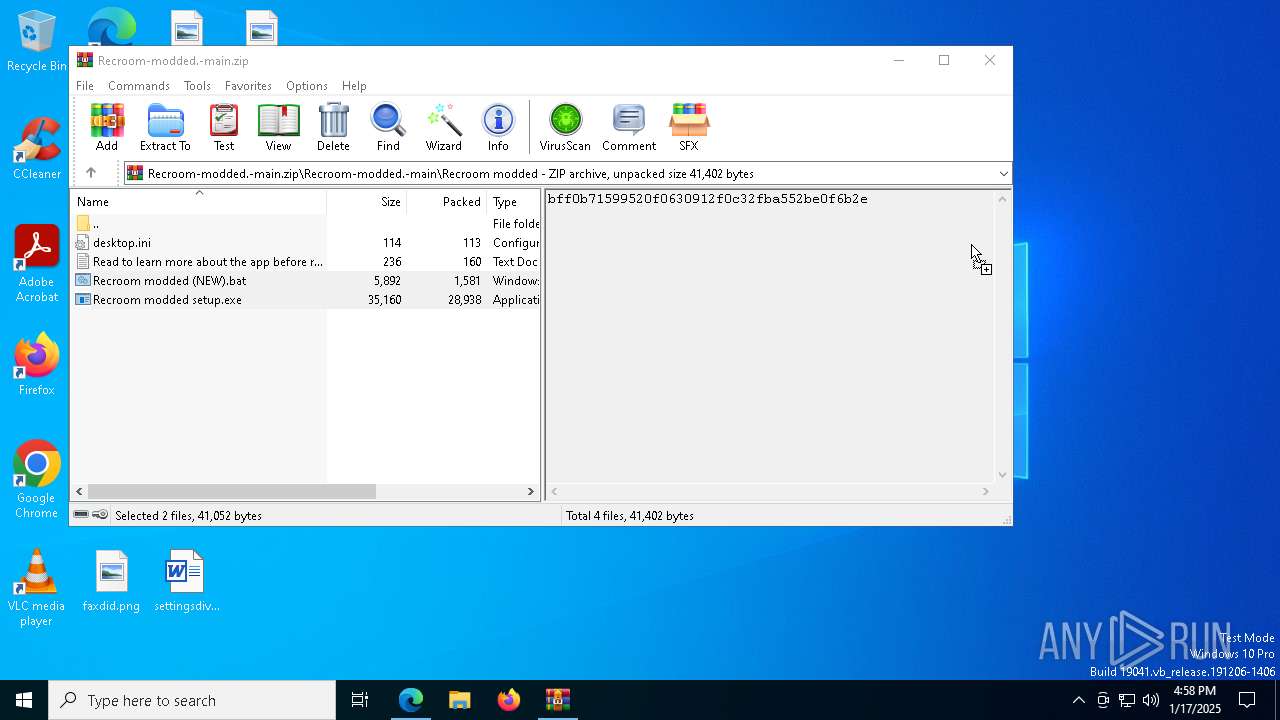
| URL: | https://github.com/LEMZzip/Recroom-modded. |
| Full analysis: | https://app.any.run/tasks/37d83c06-c9fe-456f-8c2e-4321458b3e9b |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 16:57:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2E7BB4775930FC6CE4B1B3AFFBF7DD40 |
| SHA1: | 155E51BC429F4833E01AD5C3E51E0B2F8DCD79B8 |
| SHA256: | 18E9661FF358647EACCFEF2733EAF81B03DE6D3D347495734ABA2B7E4821CC60 |
| SSDEEP: | 3:N8tEdPfTz4KC:2u+R |
MALICIOUS
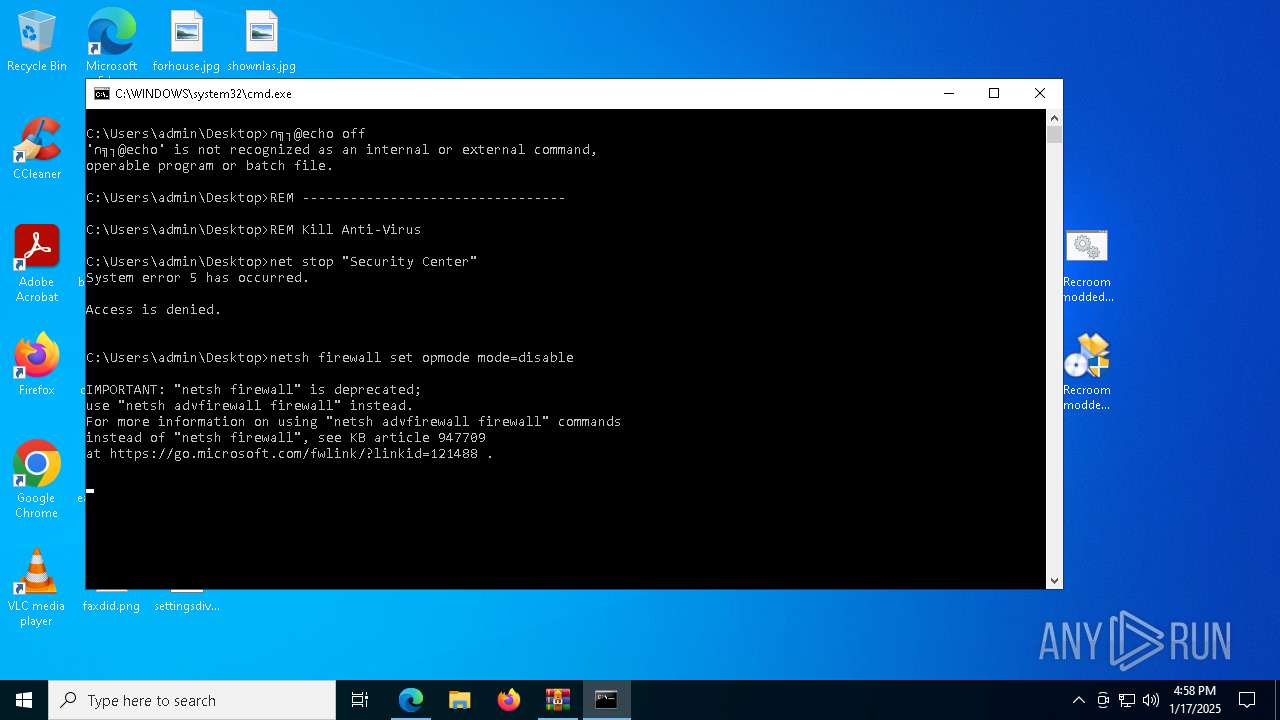
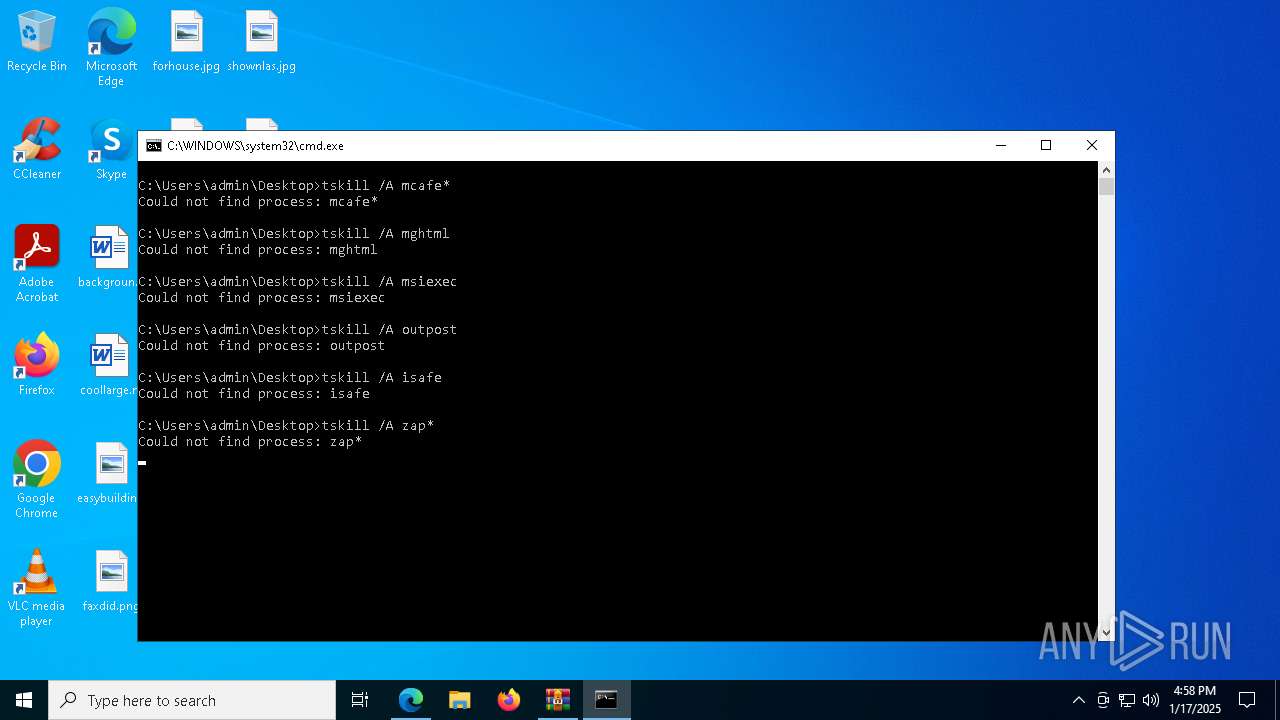
Starts NET.EXE to view/add/change user profiles
- recroom.exe.exe (PID: 8136)
- net.exe (PID: 2144)
Starts NET.EXE for service management
- cmd.exe (PID: 2132)
- net.exe (PID: 6016)
- cmd.exe (PID: 6016)
- net.exe (PID: 5572)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 6188)
- msedge.exe (PID: 6600)
- WinRAR.exe (PID: 5788)
- Recroom modded setup.exe (PID: 7396)
- recroom.exe.exe (PID: 8136)
Executable content was dropped or overwritten
- Recroom modded setup.exe (PID: 7396)
- recroom.exe.exe (PID: 8136)
Starts itself from another location
- Recroom modded setup.exe (PID: 7396)
Starts a Microsoft application from unusual location
- recroom.exe.exe (PID: 8136)
- Recroom modded setup.exe (PID: 7396)
- Recroom modded setup.exe (PID: 5268)
- Recroom modded setup.exe (PID: 3144)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2132)
- cmd.exe (PID: 6016)
Creates file in the systems drive root
- recroom.exe.exe (PID: 8136)
INFO
Checks supported languages
- identity_helper.exe (PID: 8060)
- Recroom modded setup.exe (PID: 7396)
- recroom.exe.exe (PID: 8136)
Reads Environment values
- identity_helper.exe (PID: 8060)
Reads the computer name
- identity_helper.exe (PID: 8060)
The sample compiled with english language support
- msedge.exe (PID: 6600)
- msedge.exe (PID: 6188)
- WinRAR.exe (PID: 5788)
- Recroom modded setup.exe (PID: 7396)
- recroom.exe.exe (PID: 8136)
The process uses the downloaded file
- msedge.exe (PID: 6188)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5788)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6188)
Manual execution by a user
- Recroom modded setup.exe (PID: 5268)
- Recroom modded setup.exe (PID: 7396)
- cmd.exe (PID: 2132)
- Recroom modded setup.exe (PID: 3144)
- cmd.exe (PID: 6016)
Process checks computer location settings
- recroom.exe.exe (PID: 8136)
Application launched itself
- msedge.exe (PID: 6188)
UPX packer has been detected
- recroom.exe.exe (PID: 8136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
281
Monitored processes
149
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | tskill /A sweep* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | tskill /A zauinst | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | tskill /A cc* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | tskill /A aswupdsv | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | tskill /A realm* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | tskill /A nisum* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | tskill /A ewid* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3536 --field-trial-handle=2280,i,2183815091422401222,9576104982713914363,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | tskill /A virus* | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 175
Read events
9 149
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393898 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B58D219F-070E-43A4-BD3A-676A47D114BA} | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393898 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C84F6906-CCE1-4D6A-A0C4-DD49C76D2038} | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3C198317808A2F00 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8EF28C17808A2F00 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 973ADE17808A2F00 | |||
| (PID) Process: | (6188) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
11
Suspicious files
338
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135a29.TMP | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135a39.TMP | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135a39.TMP | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135a39.TMP | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135a39.TMP | — | |
MD5:— | SHA256:— | |||
| 6188 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
78
DNS requests
71
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7316 | svchost.exe | HEAD | 200 | 84.201.210.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1737475196&P2=404&P3=2&P4=H%2fr7vyJrEiUzN%2fqSLcWXilLnjbw0U4D2Y9nZPWGnGcErfpJg1NFJM0SyGaDlMGhj%2fOvvrYWOqMxsU6ARLN4ZNg%3d%3d | unknown | — | — | whitelisted |
648 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7476 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7316 | svchost.exe | GET | — | 84.201.210.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1737475196&P2=404&P3=2&P4=H%2fr7vyJrEiUzN%2fqSLcWXilLnjbw0U4D2Y9nZPWGnGcErfpJg1NFJM0SyGaDlMGhj%2fOvvrYWOqMxsU6ARLN4ZNg%3d%3d | unknown | — | — | whitelisted |
7476 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7316 | svchost.exe | GET | 206 | 84.201.210.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8699fac5-cf38-4f97-a2f8-fb1e47f5e54e?P1=1737475196&P2=404&P3=2&P4=H%2fr7vyJrEiUzN%2fqSLcWXilLnjbw0U4D2Y9nZPWGnGcErfpJg1NFJM0SyGaDlMGhj%2fOvvrYWOqMxsU6ARLN4ZNg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.61:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5564 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |