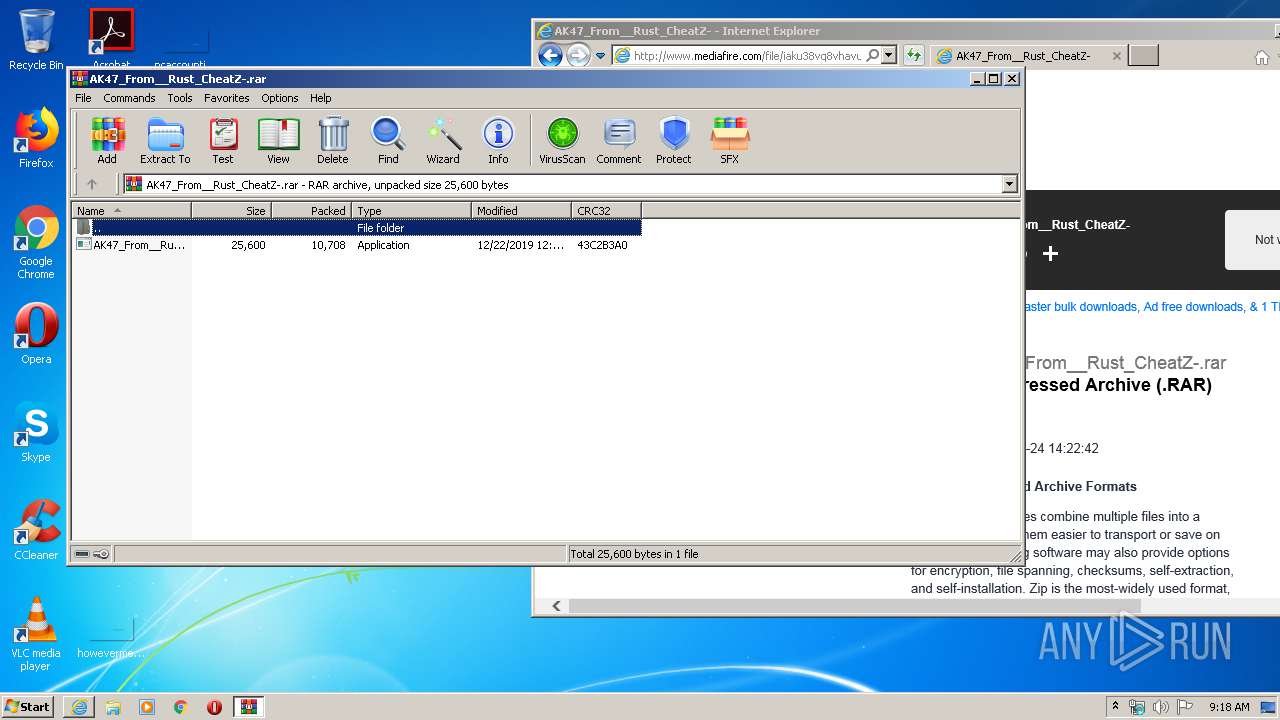
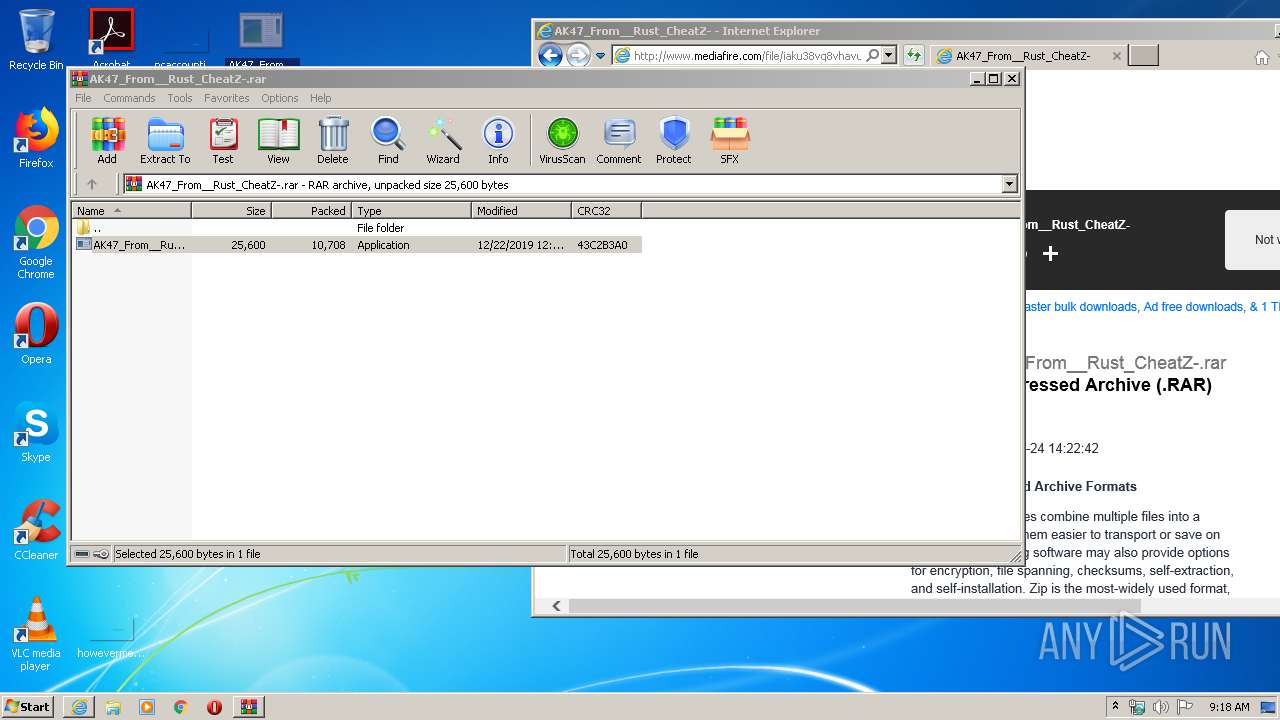
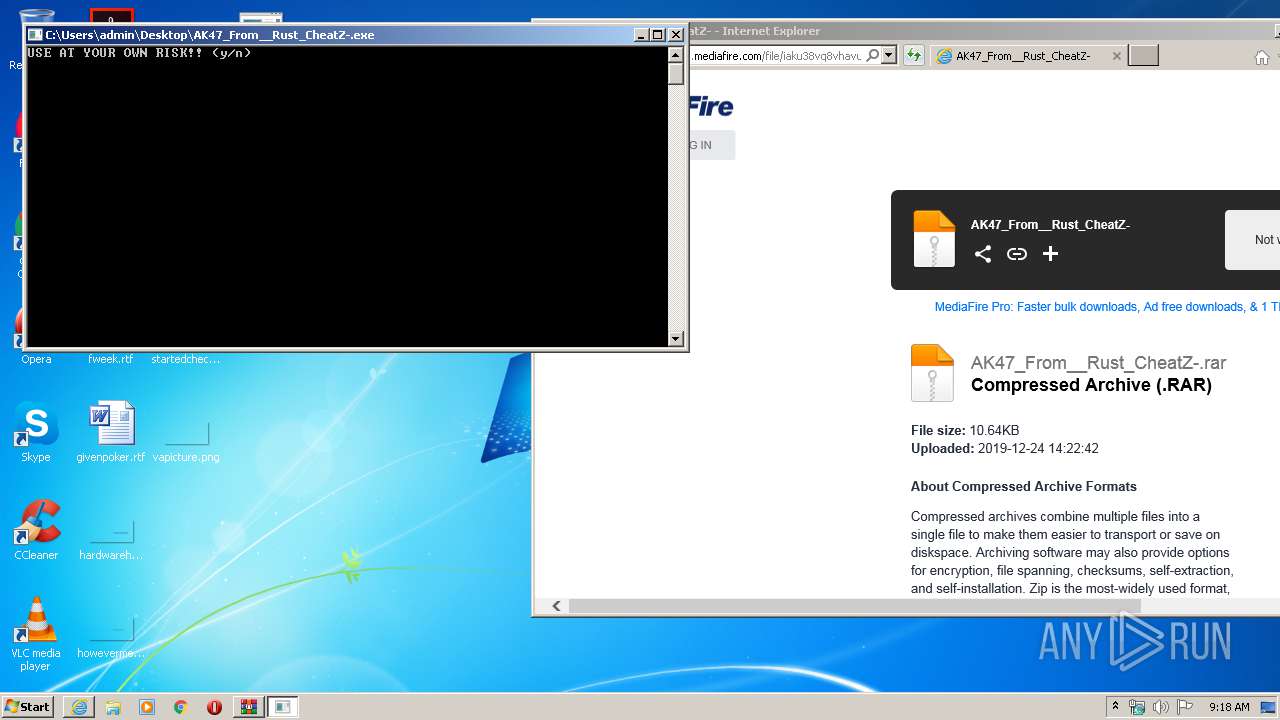
| URL: | http://www.mediafire.com/file/iaku38vq8vhavuk/AK47_From__Rust_CheatZ-.rar/file |
| Full analysis: | https://app.any.run/tasks/5241044c-0b26-4da3-a257-7dfc5e8e51fc |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2020, 09:17:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 126FA3DA5151721725CC8605A00E71A1 |
| SHA1: | DDD8C1B311BBEE2229D577858B523ADFA72FA15E |
| SHA256: | 18CB8C6A3C8B145FB72C1A207636B3DB524192A2F5077AF5458C25558586E70D |
| SSDEEP: | 3:N1KJS4w3eGUoF/aYdyeSxHhWN3sUXKcA:Cc4w3eGcYQeSVhE3rfA |
MALICIOUS
Application was dropped or rewritten from another process
- AK47_From__Rust_CheatZ-.exe (PID: 3160)
SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1696)
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2732)
Changes internet zones settings
- iexplore.exe (PID: 1696)
Application launched itself
- iexplore.exe (PID: 1696)
Reads internet explorer settings
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2732)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1696)
Reads settings of System Certificates
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 1696)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1696)
Creates files in the user directory
- iexplore.exe (PID: 4092)
- iexplore.exe (PID: 2732)
Changes settings of System certificates
- iexplore.exe (PID: 1696)
Manual execution by user
- AK47_From__Rust_CheatZ-.exe (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1696 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.mediafire.com/file/iaku38vq8vhavuk/AK47_From__Rust_CheatZ-.rar/file | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2236 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B4FOPVAU\AK47_From__Rust_CheatZ-.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:1185049 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\Desktop\AK47_From__Rust_CheatZ-.exe" | C:\Users\admin\Desktop\AK47_From__Rust_CheatZ-.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 4092 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
1 573
Read events
1 441
Write events
130
Delete events
2
Modification events
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 4202901472 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30790093 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A0000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
122
Text files
81
Unknown types
55
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1696 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1161MORM.txt | — | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\f[1].txt | text | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\U28VXOT3.txt | text | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\apps_list_sprite-v4[1].png | image | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\file[1].htm | html | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\O4RJPM80.txt | text | |
MD5:— | SHA256:— | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabC1FA.tmp | — | |
MD5:— | SHA256:— | |||
| 1696 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\EP2NOZAO\favicon[1].ico | image | |
MD5:9FB559A691078558E77D6848202F6541 | SHA256:6D8A01DC7647BC218D003B58FE04049E24A9359900B7E0CEBAE76EDF85B8B914 | |||
| 4092 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\infinity.js[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
154
DNS requests
60
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4092 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/images/icons/svg_light/icons_sprite.svg | US | image | 8.12 Kb | shared |
4092 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
4092 | iexplore.exe | GET | 200 | 2.16.186.80:80 | http://b.scorecardresearch.com/beacon.js?c1=8&c2=18203330&c3=1 | unknown | text | 902 b | whitelisted |
4092 | iexplore.exe | GET | 200 | 104.16.202.237:80 | http://static.mediafire.com/images/backgrounds/download/apps_list_sprite-v4.png | US | image | 6.78 Kb | shared |
4092 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
4092 | iexplore.exe | GET | 200 | 104.19.214.37:80 | http://cdn.otnolatrnup.com/Scripts/infinity.js.aspx?guid=5ff0fb62-0643-4ff1-aaee-c737f9ffc0e0 | US | text | 73.0 Kb | whitelisted |
4092 | iexplore.exe | GET | 200 | 104.19.214.37:80 | http://otnolatrnup.com/Tag.engine?time=0&id=5ff0fb62-0643-4ff1-aaee-c737f9ffc0e0&rand=11396&ver=async&referrerUrl=&fingerPrint=123&abr=false&stdTime=0&fpe=3&bw=1280&bh=644&res=1280x720&curl=http%3A%2F%2Fwww.mediafire.com%2Ffile%2Fiaku38vq8vhavuk%2FAK47_From__Rust_CheatZ-.rar%2Ffile&kw=online%20storage%2Cfree%20storage%2Ccloud%20storage%2Ccollaboration%2Cbackup%20file%20sharing%2Cshare%20files%2Cphoto%20backup%2Cphoto%20sharing%2Cftp%20replacement%2Ccross%20platform%2Cremote%20access%2Cmobile%20access%2Csend%20large%20files%2Crecover%20files%2Cfile%20versioning%2Cundelete%2Cwindows%2Cpc%2Cmac%2Cos%20x%2Clinux%2Ciphone | US | text | 2.66 Kb | whitelisted |
4092 | iexplore.exe | GET | 200 | 23.66.27.225:80 | http://c.aaxads.com/aax.js?pub=AAX3221EY&hst=www.mediafire.com&ver=1.2 | NL | text | 102 Kb | whitelisted |
4092 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
4092 | iexplore.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4092 | iexplore.exe | 104.16.203.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
1696 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4092 | iexplore.exe | 104.16.202.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
4092 | iexplore.exe | 172.217.21.200:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 216.58.208.34:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 23.66.27.225:80 | c.aaxads.com | Akamai Technologies, Inc. | NL | whitelisted |
4092 | iexplore.exe | 172.217.18.174:80 | translate.google.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 104.19.214.37:80 | cdn.otnolatrnup.com | Cloudflare Inc | US | shared |
4092 | iexplore.exe | 172.217.22.106:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
4092 | iexplore.exe | 2.16.186.80:80 | b.scorecardresearch.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
translate.google.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
c.aaxads.com |
| whitelisted |
cdn.otnolatrnup.com |
| whitelisted |
translate.googleapis.com |
| whitelisted |
static.mediafire.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4092 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |