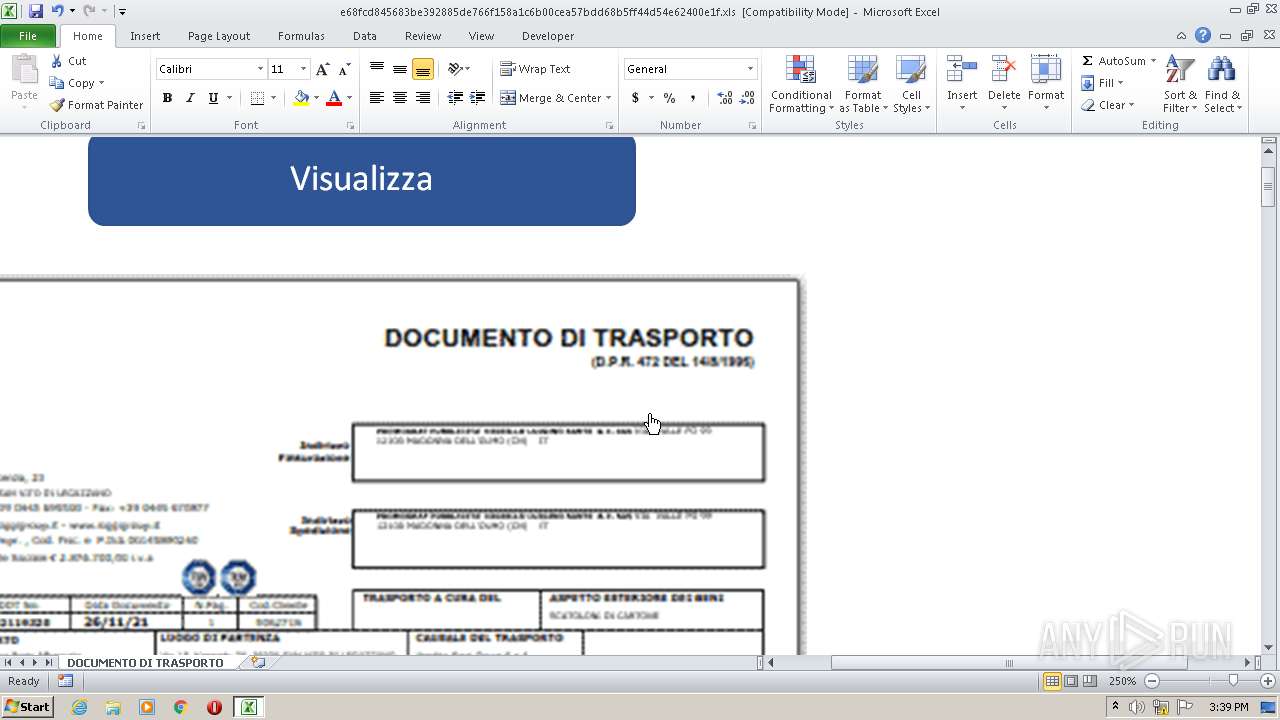
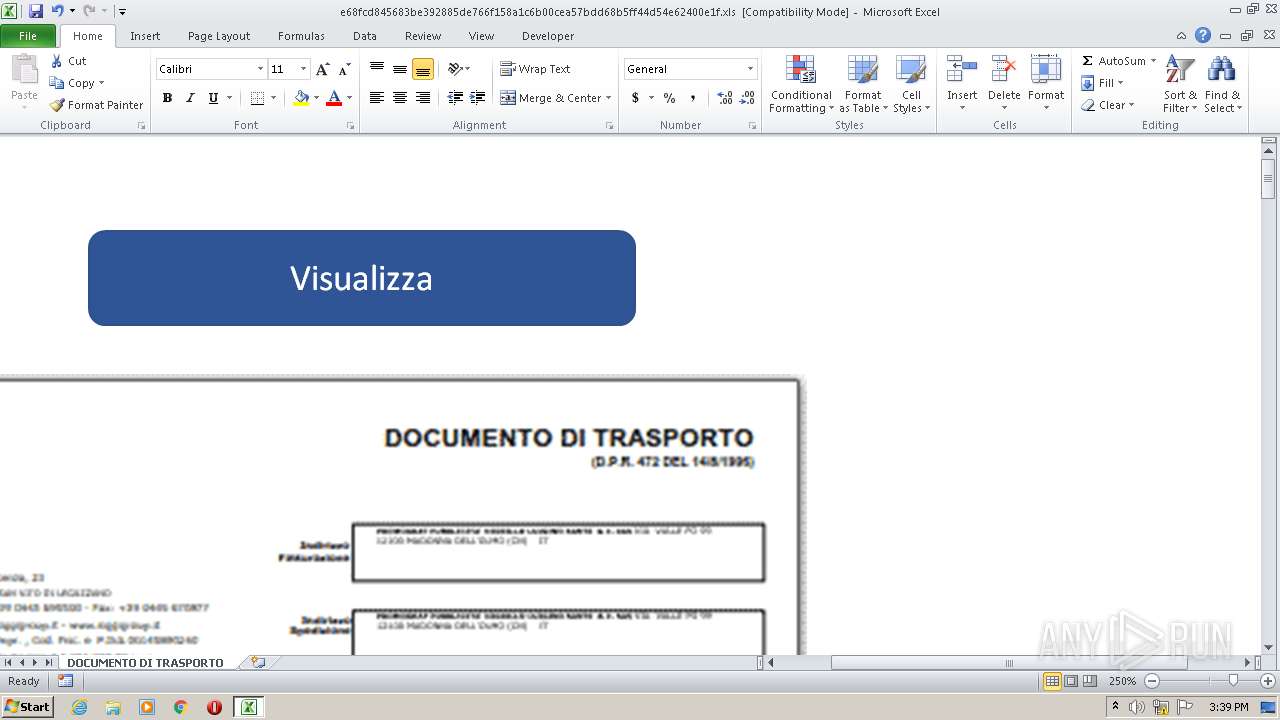
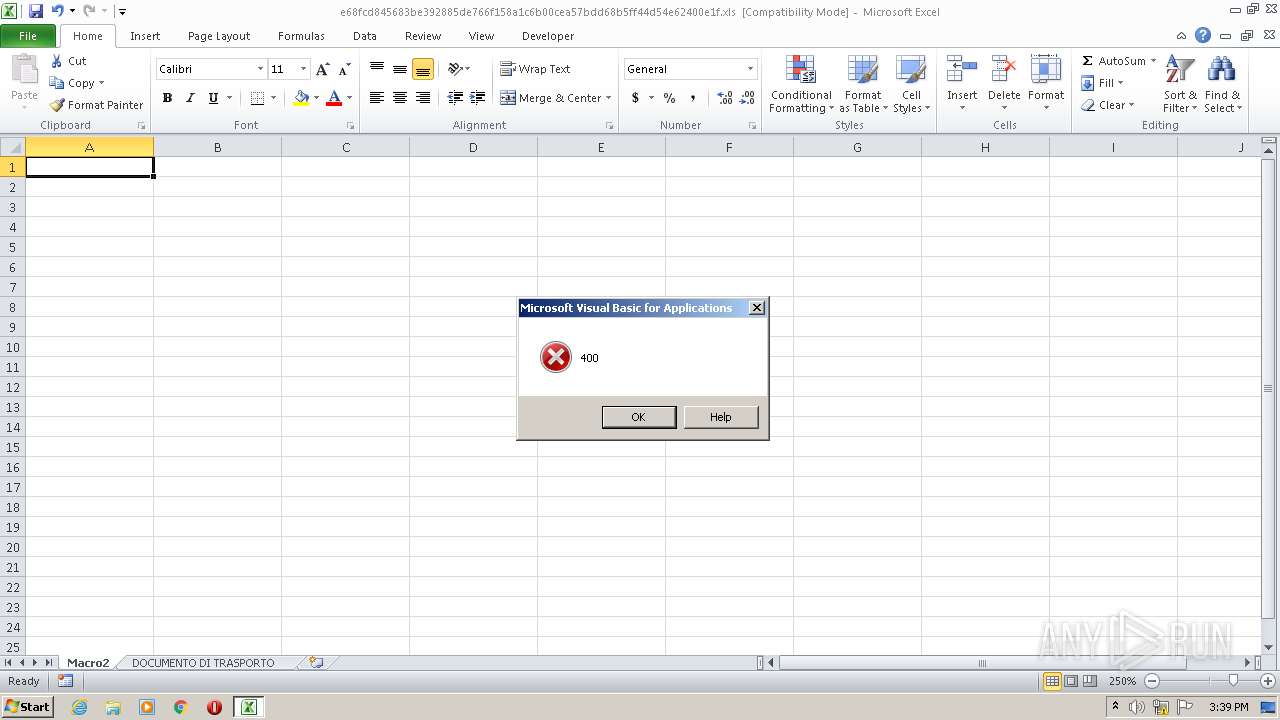
| File name: | e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.zip |
| Full analysis: | https://app.any.run/tasks/4bbd60cc-35f3-449e-8023-66ce958241be |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 15:38:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 9D6F277E7F90A5B67F4D6DEB56F15DAA |
| SHA1: | D1F97B078DCBEE9EA39F1BB171E768FB573F21A6 |
| SHA256: | 18B99BBD5DB40BFC3B5655989D7F53A2F646F0877FC38272E959B0C0B99EBBA4 |
| SSDEEP: | 384:nQpmX/+gmnZCl1jjDbogQtRbzA/PbuufsNURzcXhehBnepC46j7Wbpini73:nImvkrRtB4FFPh5eJ6j7WgS3 |
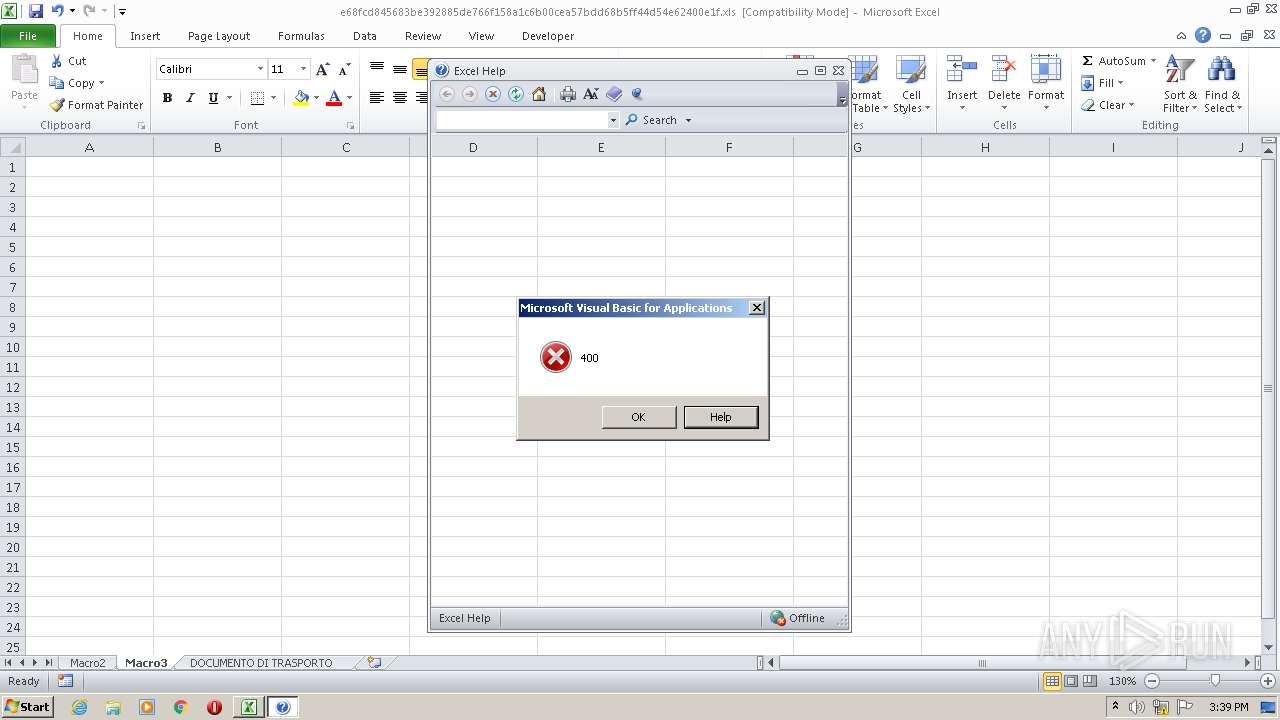
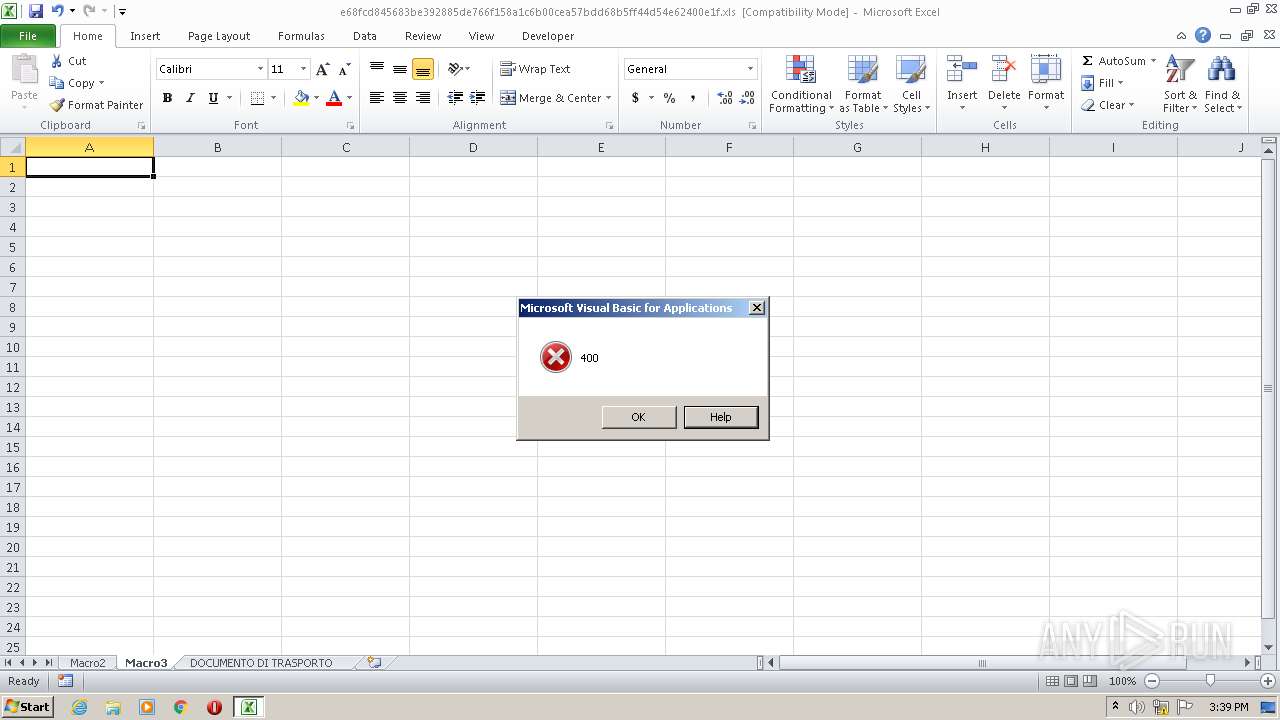
MALICIOUS
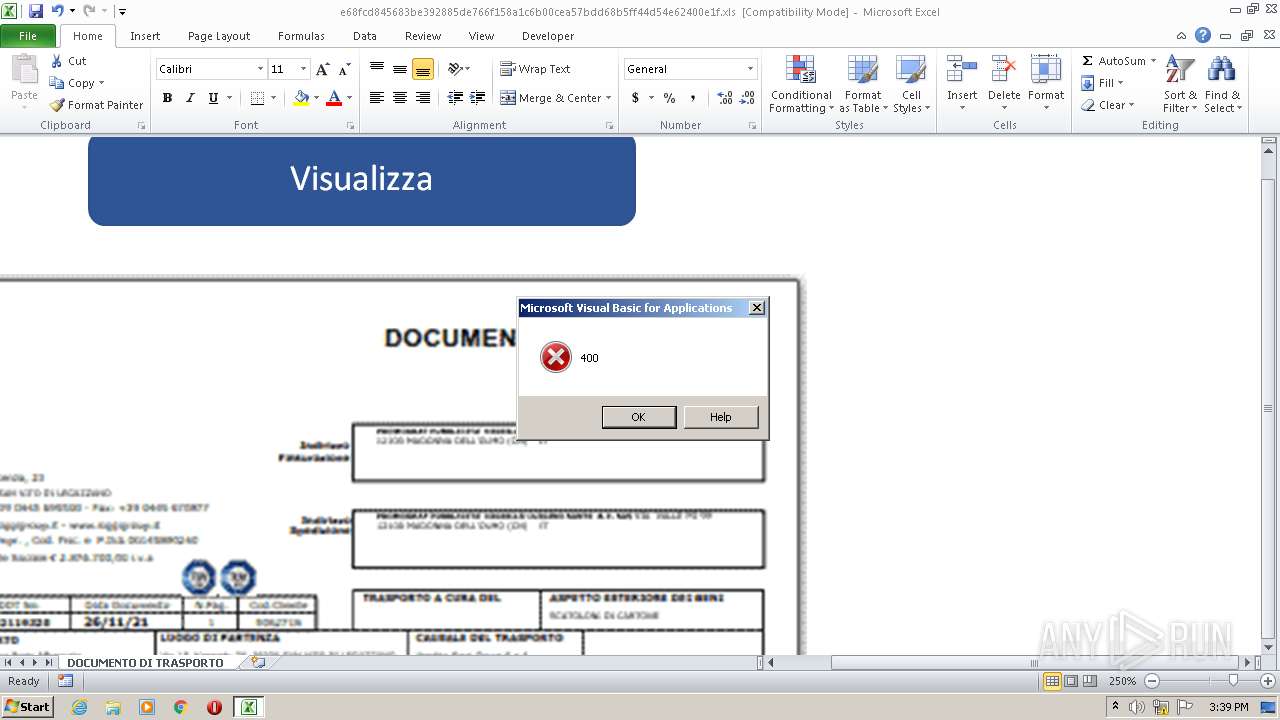
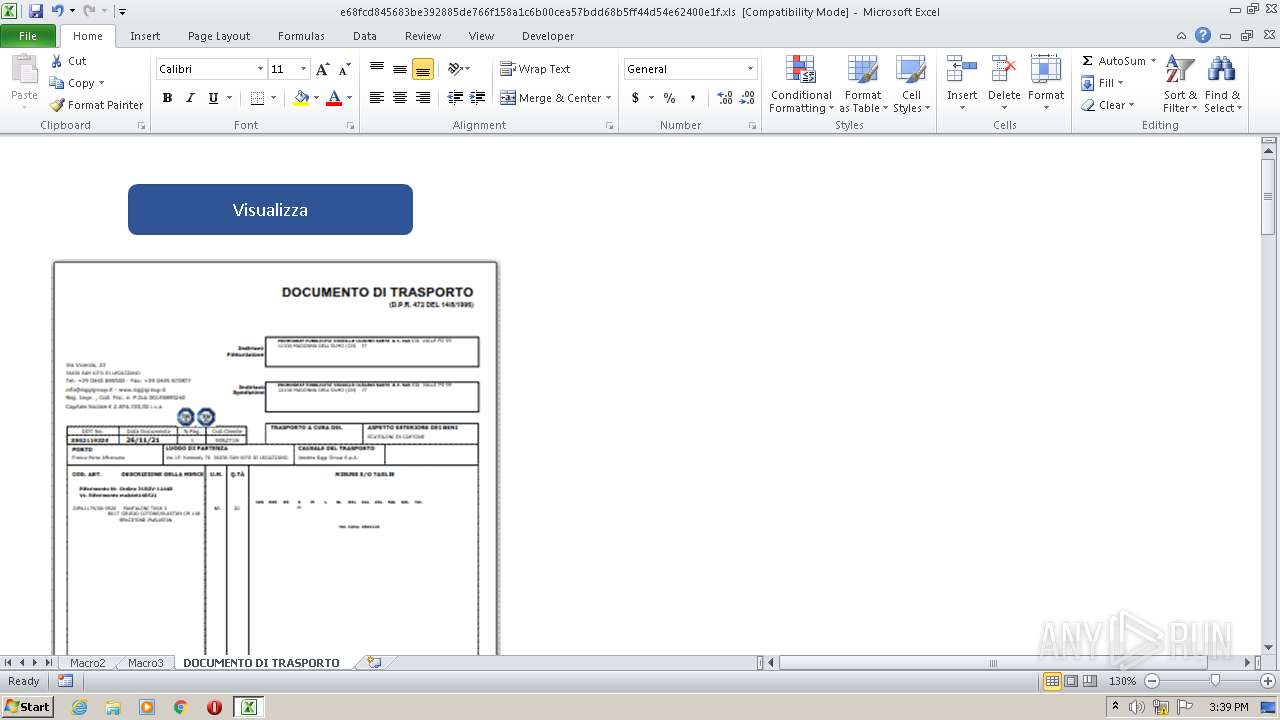
Drops known malicious document
- WinRAR.exe (PID: 3220)
SUSPICIOUS
Reads default file associations for system extensions
- WinRAR.exe (PID: 3220)
- EXCEL.EXE (PID: 2696)
Checks supported languages
- WinRAR.exe (PID: 3220)
Reads the computer name
- WinRAR.exe (PID: 3220)
Starts Microsoft Office Application
- EXCEL.EXE (PID: 2696)
INFO
Checks supported languages
- EXCEL.EXE (PID: 2696)
- CLVIEW.EXE (PID: 1020)
Reads the computer name
- EXCEL.EXE (PID: 2696)
- CLVIEW.EXE (PID: 1020)
Manual execution by user
- EXCEL.EXE (PID: 2696)
Creates files in the user directory
- EXCEL.EXE (PID: 2696)
Reads Microsoft Outlook installation path
- CLVIEW.EXE (PID: 1020)
Reads Microsoft Office registry keys
- CLVIEW.EXE (PID: 1020)
- EXCEL.EXE (PID: 2696)
Reads internet explorer settings
- CLVIEW.EXE (PID: 1020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.xls |
|---|---|
| ZipUncompressedSize: | 51200 |
| ZipCompressedSize: | 24571 |
| ZipCRC: | 0x951501f8 |
| ZipModifyDate: | 2022:01:24 15:38:18 |
| ZipCompression: | Unknown (99) |
| ZipBitFlag: | 0x0003 |
| ZipRequiredVersion: | 51 |
Total processes
38
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | "C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE" "EXCEL" "Microsoft Excel" | C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Help Viewer Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
| 2696 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3220 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 229
Read events
4 084
Write events
124
Delete events
21
Modification events
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.zip | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
105
Text files
76
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRE893.tmp.cvr | — | |
MD5:— | SHA256:— | |||
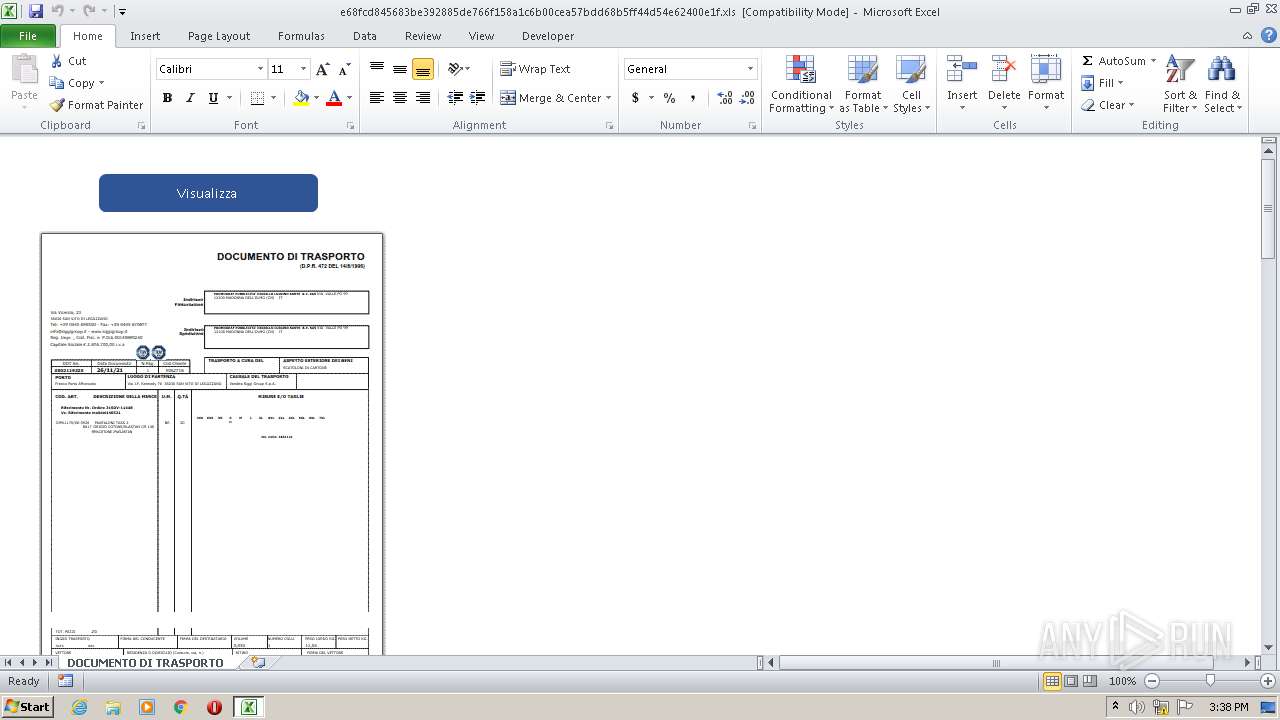
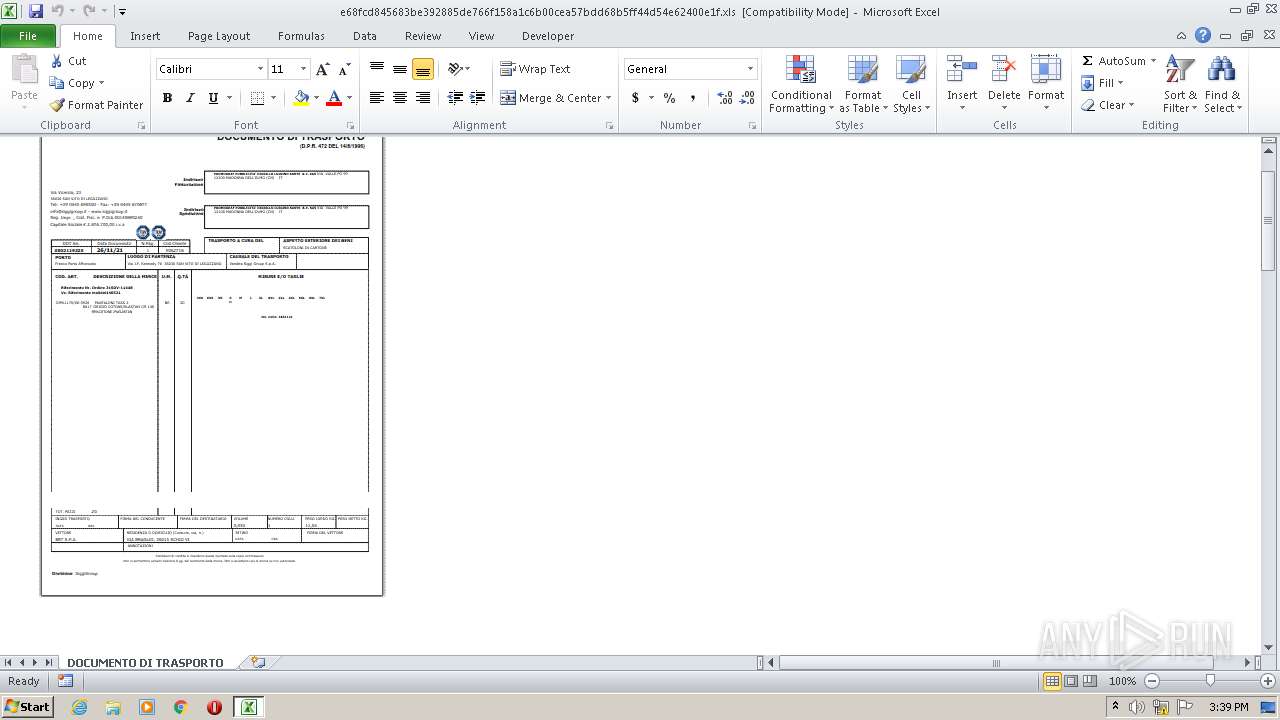
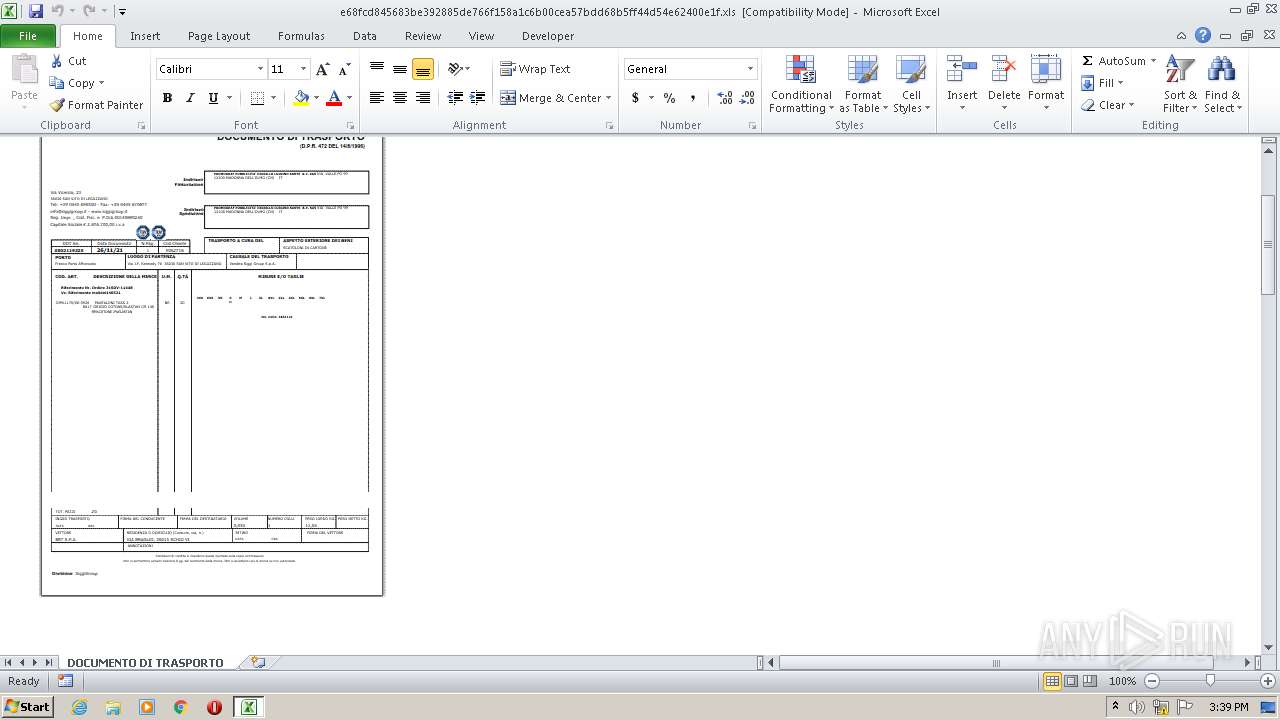
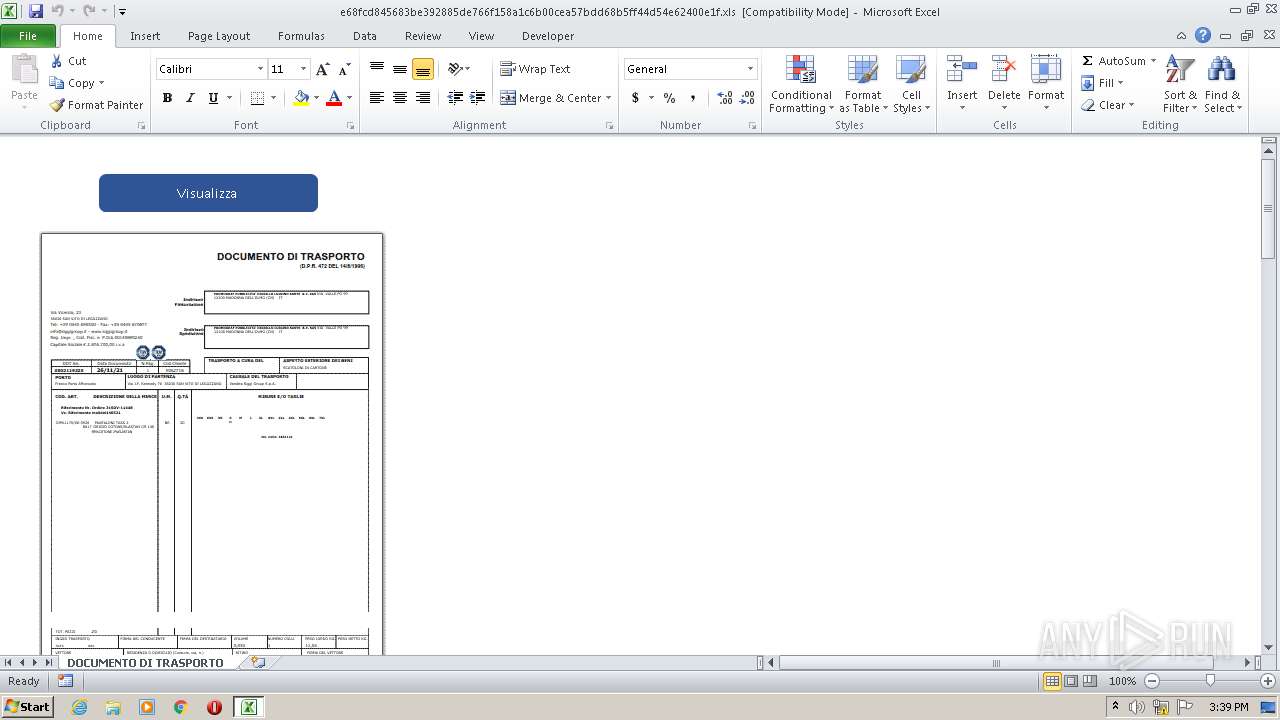
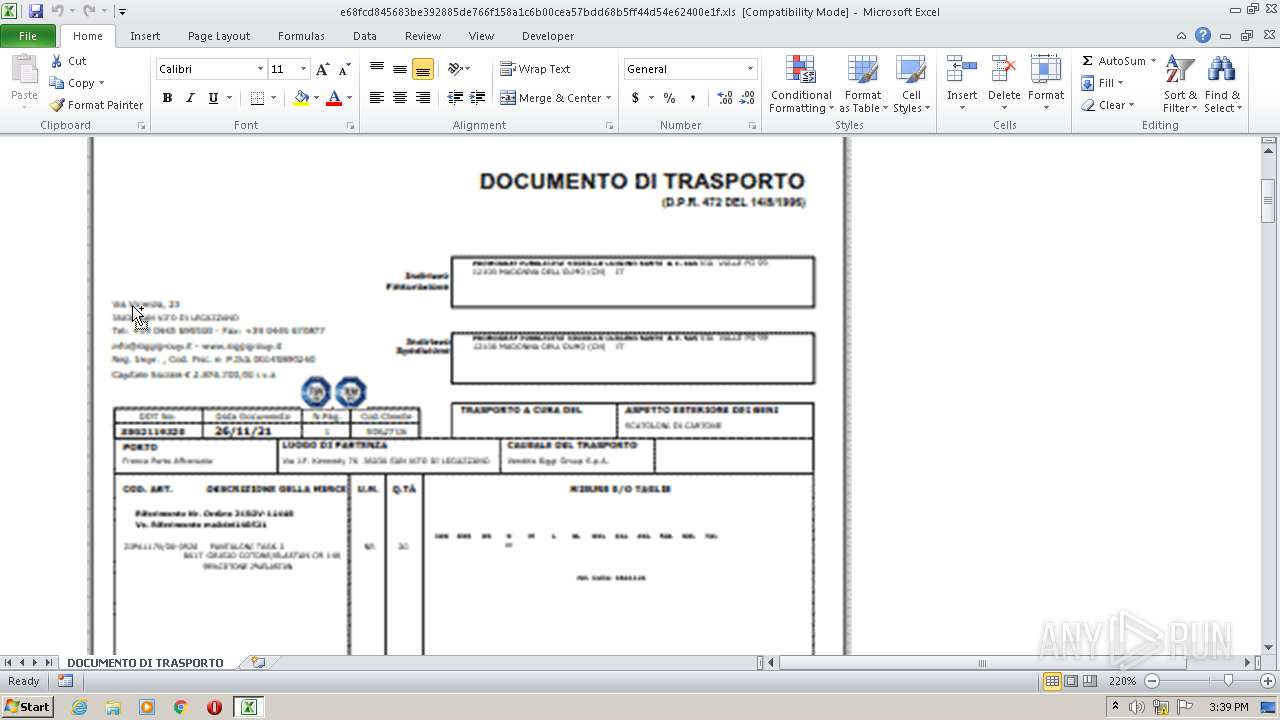
| 3220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3220.38810\e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.xls | document | |
MD5:— | SHA256:— | |||
| 2696 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\e68fcd845683be392885de766f158a1c6b00cea57bdd68b5ff44d54e62400e1f.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT3883.tmp | binary | |
MD5:— | SHA256:— | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT3882.tmp | binary | |
MD5:— | SHA256:— | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Microsoft Help\MS.EXCEL.14.1033_1033_MTOC_EXCEL_COL.HxH | binary | |
MD5:— | SHA256:— | |||
| 2696 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT386B.tmp | binary | |
MD5:4BE2AEDDA24E0539C95564B48CA9D8BA | SHA256:E4D153F74AC21D4212A83FE030EE7A407B5FDFE2D3A8145F3E826532BD796893 | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT386D.tmp | binary | |
MD5:7E8B24EECB300B45B19F534EFF40AD54 | SHA256:DAA96DDB007D4387E35263890F76F3CE91EE276D6AE85B0BBF1D9BCB97FCF85B | |||
| 1020 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT3880.tmp | binary | |
MD5:4BD1EB83BB26A0192FE6465187600F4A | SHA256:375732431D8AB7B81AD6BA6F53FBB291BBA95614171A52B4BA281B628A69E061 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report