| File name: | GjkeqZjxdJVq2K.rar |
| Full analysis: | https://app.any.run/tasks/2a4a7a5f-d2ab-48b7-ba4b-30257c3e279d |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 09:09:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5B639E895D8FD75E5CB3F2BD25811A41 |
| SHA1: | 774E54BCA857A3D5284910649F5901B7509FF955 |
| SHA256: | 18A14C770DC8D0679D2C22D35853F53C5B40EC7B10F098FEA57A38989929B525 |
| SSDEEP: | 49152:d7JF/7akKMurXK+4uVreB0cQyXusC2haQ7BhcwAhjIZJf+qiNpT4V9lpNrqTwwH:d7JN7ajXNBC0GC1QNhcDGf+qifkTlppO |
MALICIOUS
Application was dropped or rewritten from another process
- Vq2K$GjkeqZjxdJ.exe (PID: 2728)
- ztYw2y8tYw2N9yeRPFMT.exe (PID: 2004)
- NzmQfYnDsd.exe (PID: 2732)
- Vq2K$GjkeqZjxdJ.exe (PID: 2836)
SUSPICIOUS
Creates files in the driver directory
- Vq2K$GjkeqZjxdJ.exe (PID: 2836)
Application launched itself
- Vq2K$GjkeqZjxdJ.exe (PID: 2728)
Creates files in the Windows directory
- Vq2K$GjkeqZjxdJ.exe (PID: 2836)
Reads Internet Cache Settings
- NzmQfYnDsd.exe (PID: 2732)
Creates files in the user directory
- NzmQfYnDsd.exe (PID: 2732)
Reads internet explorer settings
- NzmQfYnDsd.exe (PID: 2732)
Executable content was dropped or overwritten
- Vq2K$GjkeqZjxdJ.exe (PID: 2836)
INFO
Manual execution by user
- Vq2K$GjkeqZjxdJ.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2004 | "C:\Windows\System32\drivers\ztYw2y8tYw2N9yeRPFMT.exe" | C:\Windows\System32\drivers\ztYw2y8tYw2N9yeRPFMT.exe | — | Vq2K$GjkeqZjxdJ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2452 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\GjkeqZjxdJVq2K.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\Desktop\Vq2K$GjkeqZjxdJ.exe" | C:\Users\admin\Desktop\Vq2K$GjkeqZjxdJ.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2732 | "C:\Windows\System32\drivers\NzmQfYnDsd.exe" | C:\Windows\System32\drivers\NzmQfYnDsd.exe | Vq2K$GjkeqZjxdJ.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: FluxLoader Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\Desktop\Vq2K$GjkeqZjxdJ.exe" -el -s2 "-dC:\Windows\System32\drivers" "-sp" | C:\Users\admin\Desktop\Vq2K$GjkeqZjxdJ.exe | Vq2K$GjkeqZjxdJ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
618
Read events
592
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GjkeqZjxdJVq2K.rar | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2728) Vq2K$GjkeqZjxdJ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2452.11447\Vq2K$GjkeqZjxdJ.exe | — | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Local\FluxLoader\DefaultDomain_Path_otxh1g3d2uhtlcxxtxzivz3e0bknhhgq\1.0.0.0\weg3olz3.newcfg | — | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\check[1].htm | html | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Local\FluxLoader\DefaultDomain_Path_otxh1g3d2uhtlcxxtxzivz3e0bknhhgq\1.0.0.0\wmd0suv0.newcfg | xml | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Local\FluxLoader\DefaultDomain_Path_otxh1g3d2uhtlcxxtxzivz3e0bknhhgq\1.0.0.0\user.config | xml | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\ECKJYRJ0.txt | text | |
MD5:— | SHA256:— | |||
| 2836 | Vq2K$GjkeqZjxdJ.exe | C:\Windows\System32\drivers\NzmQfYnDsd.exe | executable | |
MD5:— | SHA256:— | |||
| 2836 | Vq2K$GjkeqZjxdJ.exe | C:\Windows\System32\drivers\ztYw2y8tYw2N9yeRPFMT.exe | executable | |
MD5:— | SHA256:— | |||
| 2732 | NzmQfYnDsd.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\aes[1].js | text | |
MD5:78A66859739B0C9E18BC5B4538C03BF9 | SHA256:D2701C86A2A31A641520E72121749DBBABEED4B1A59AECE20BBF14F9C9DE82BC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
2
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
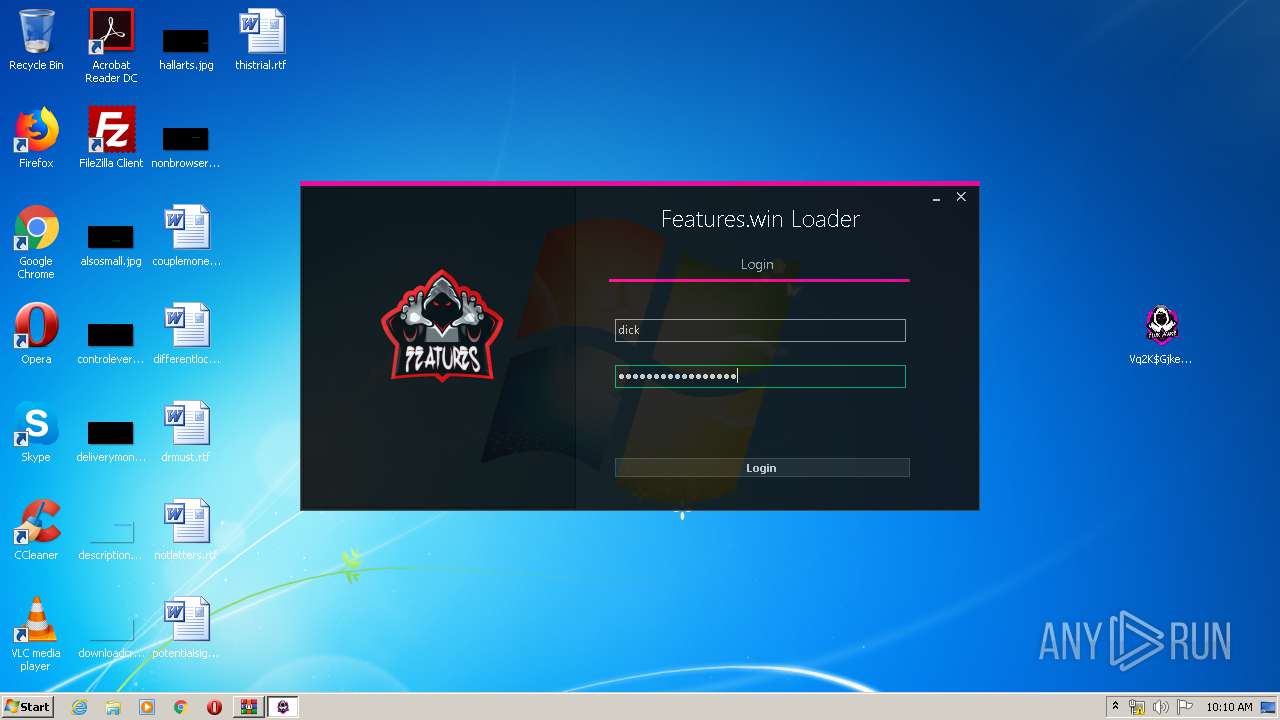
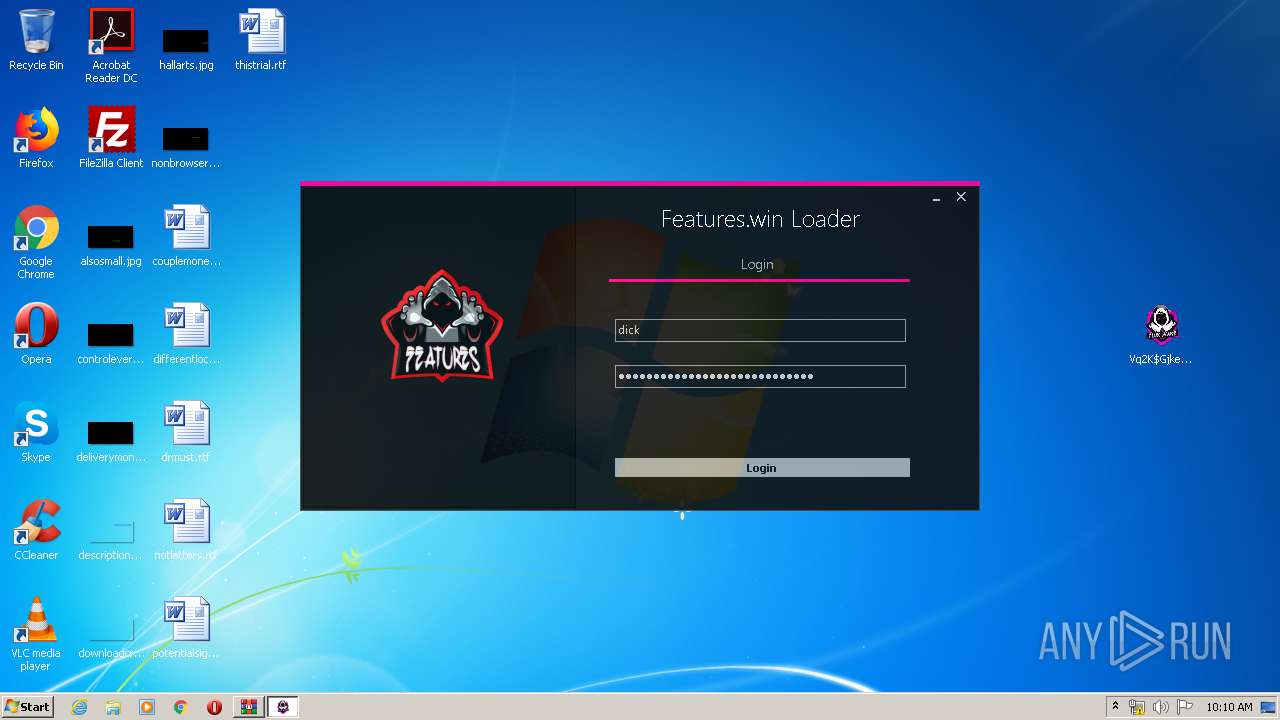
2732 | NzmQfYnDsd.exe | GET | 200 | 185.27.134.125:80 | http://fluxware.epizy.com/forums/check/check.php?username=dick&password=awdadawdawdawdwuaiawidaawdaw | GB | — | — | suspicious |
2732 | NzmQfYnDsd.exe | GET | 200 | 185.27.134.125:80 | http://fluxware.epizy.com/forums/check/check.php?username=dwadwad&password=awdadawdawdaw | GB | html | 593 b | suspicious |
2732 | NzmQfYnDsd.exe | GET | 200 | 185.27.134.125:80 | http://fluxware.epizy.com/forums/check/check.php?username=dwadwad&password=awdadawdawdaw&i=1 | GB | text | 30.4 Kb | suspicious |
2732 | NzmQfYnDsd.exe | GET | 200 | 185.27.134.125:80 | http://fluxware.epizy.com/aes.js | GB | text | 30.4 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2732 | NzmQfYnDsd.exe | 185.27.134.125:80 | fluxware.epizy.com | Wildcard UK Limited | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fluxware.epizy.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2732 | NzmQfYnDsd.exe | Misc activity | SUSPICIOUS [PTsecurity] Encryptor aes.js script (seen PedCont ransomware) |