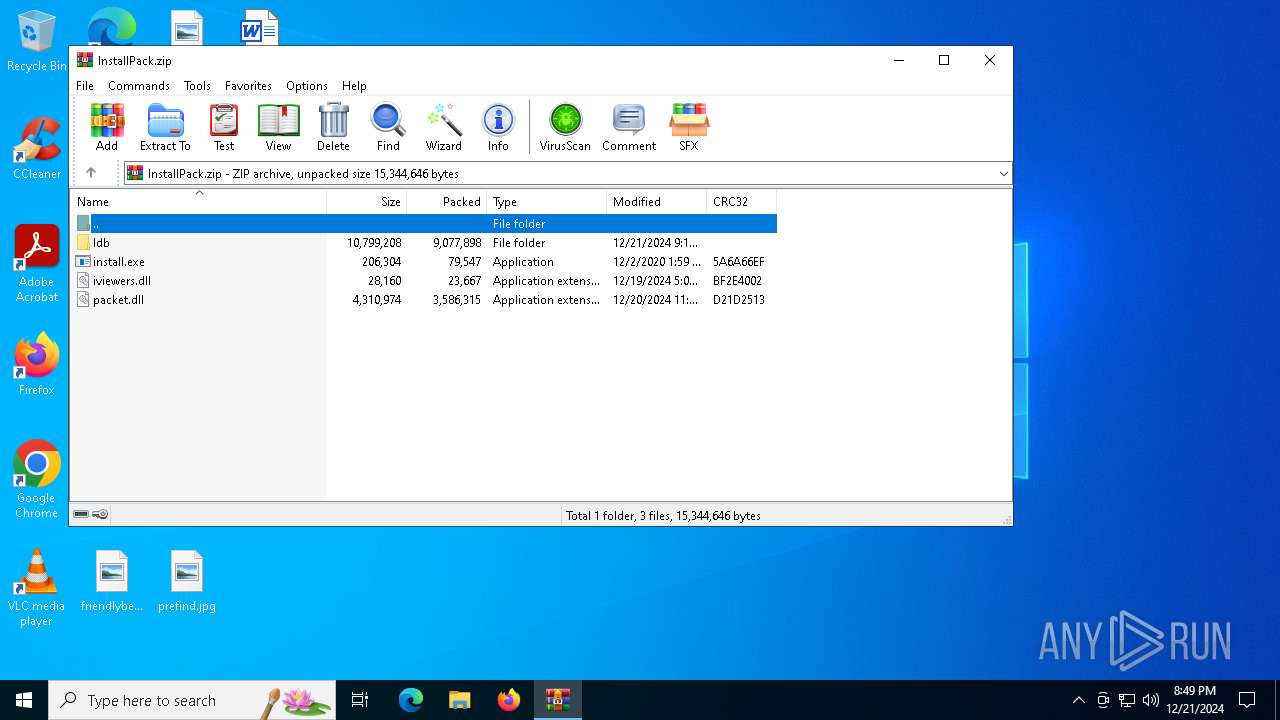
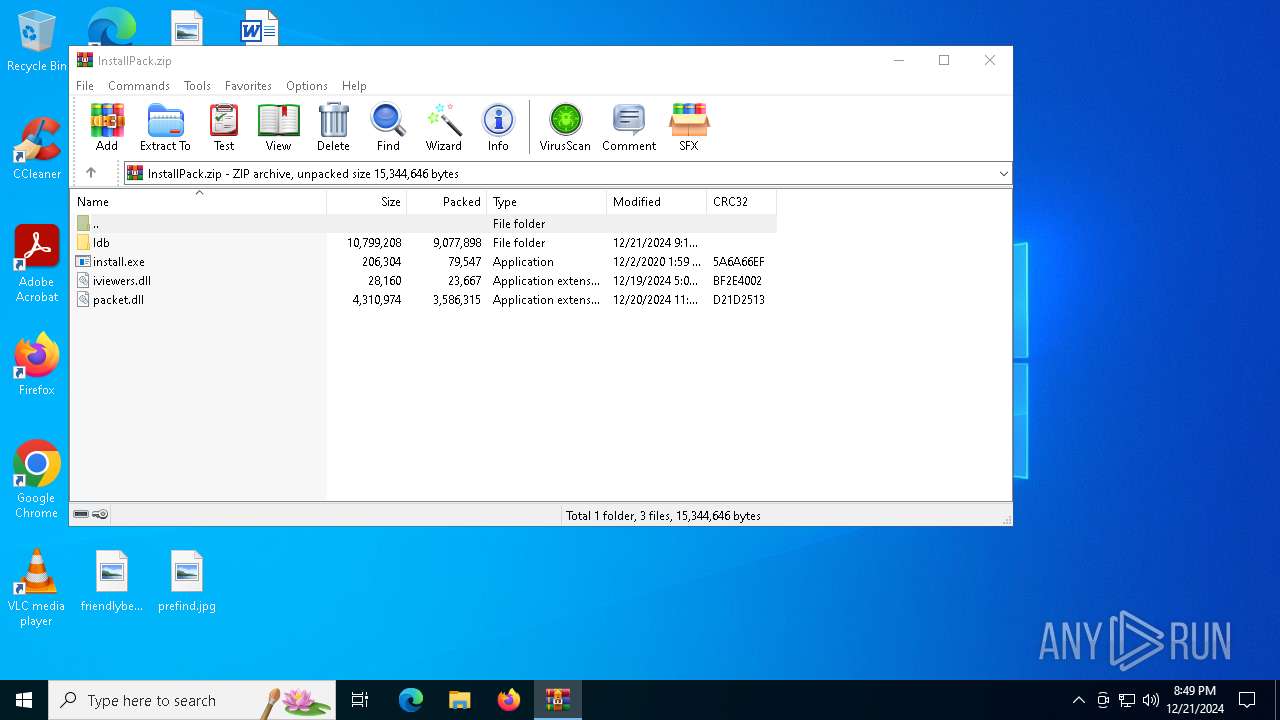
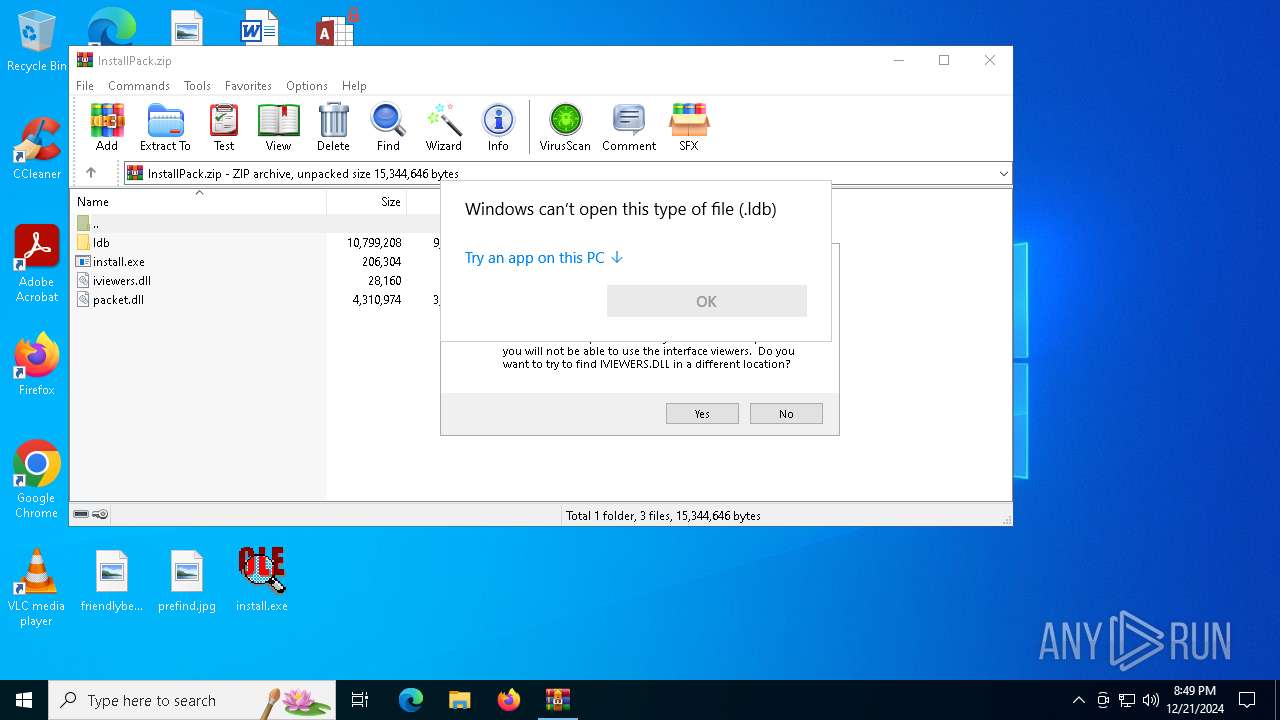
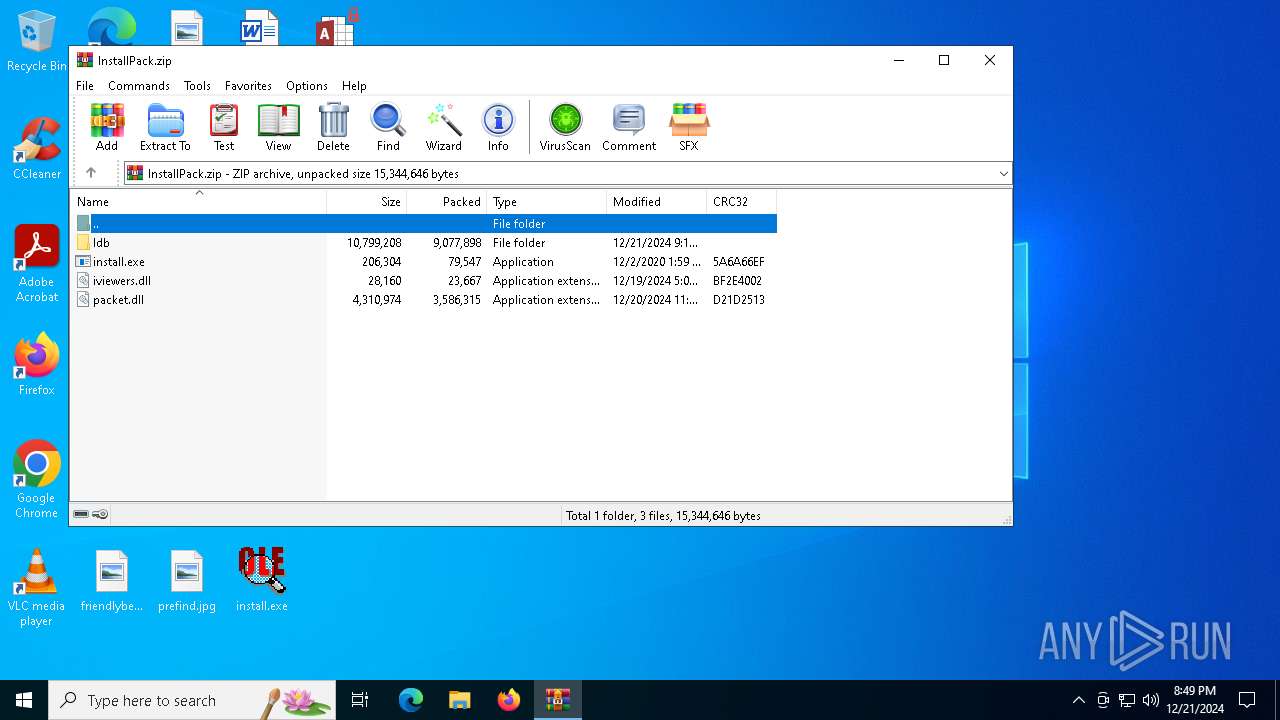
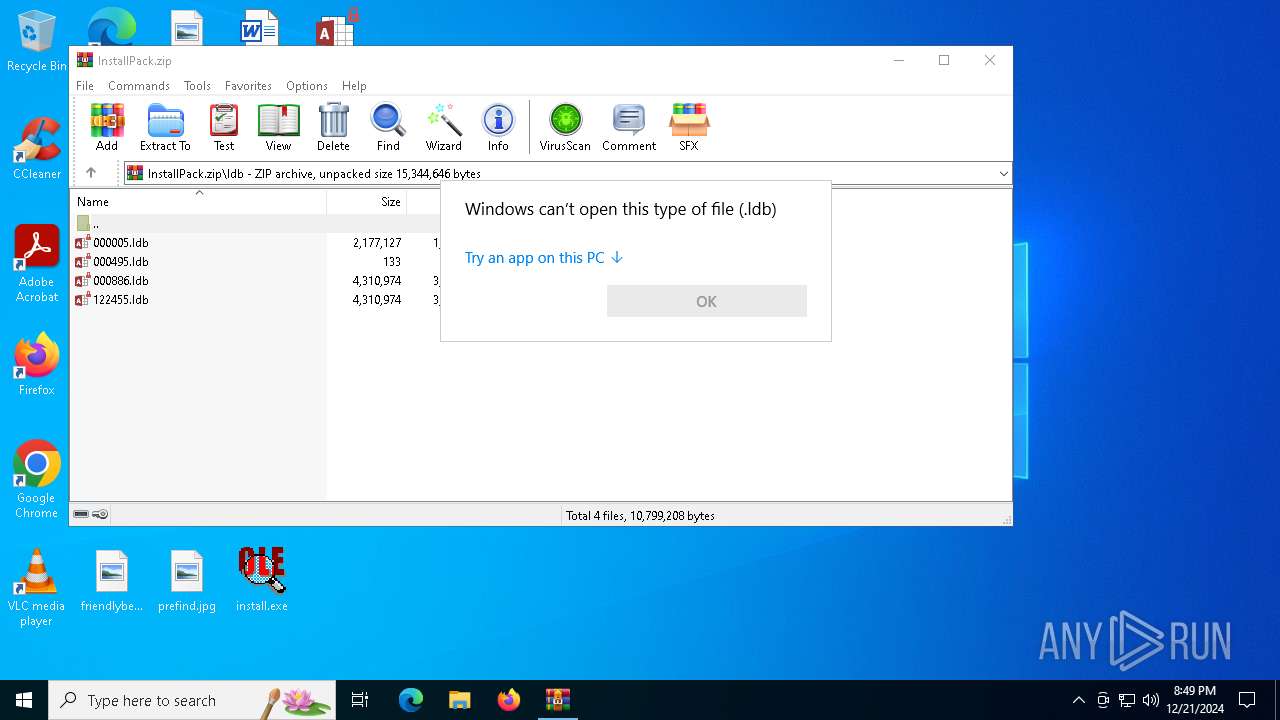
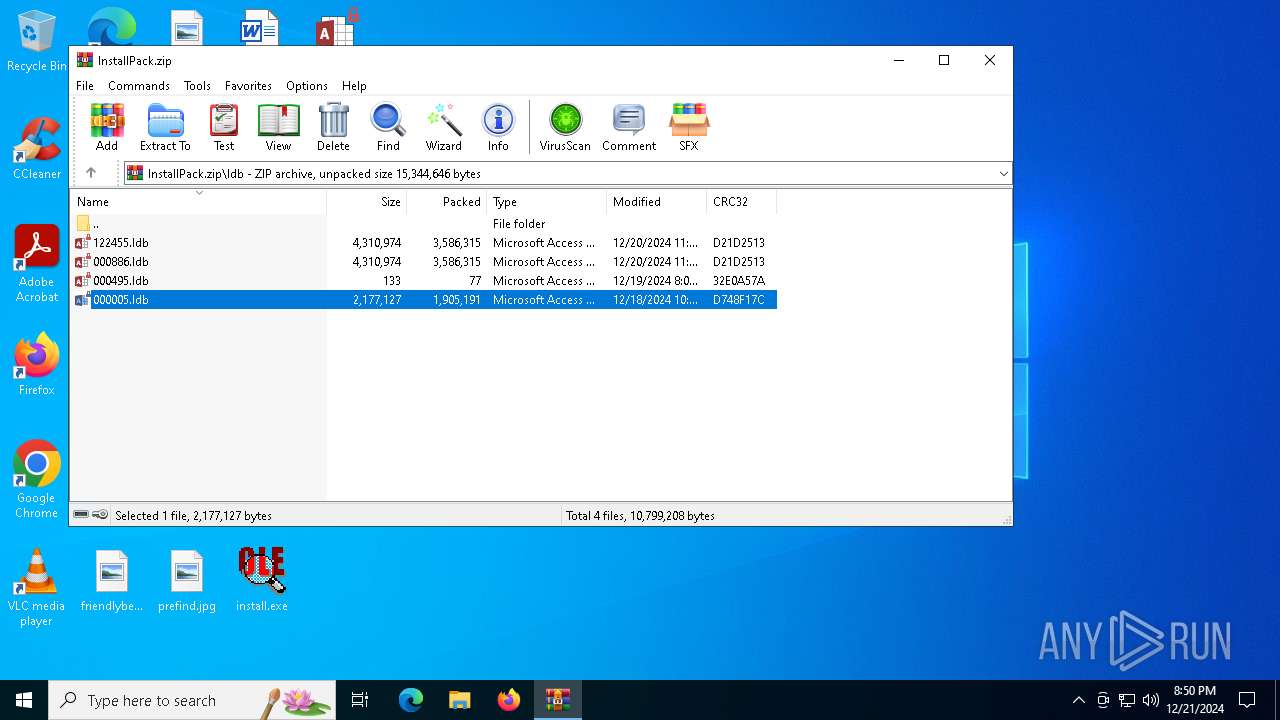
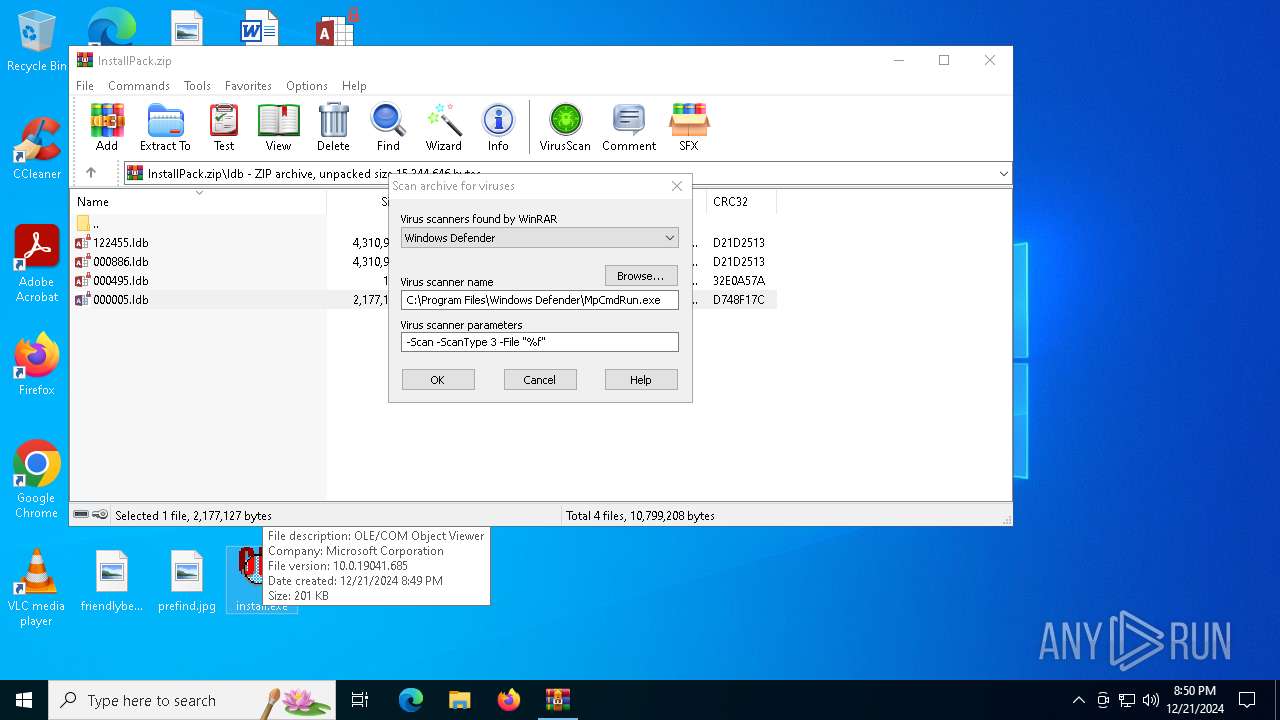
| File name: | InstallPack.zip |
| Full analysis: | https://app.any.run/tasks/aea14bdf-7092-4bbd-a571-e1143a4b6450 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2024, 20:49:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C37F0D9D6950E3E669D6348690882D3C |
| SHA1: | 300F404FBD2569A5257CC1C82B153A80A259B822 |
| SHA256: | 189FE42938DAFE1EFAA9624C55C0CAEC232C454B9B874D9EFB765F5A1BCB5EE2 |
| SSDEEP: | 98304:y/7s8iO4+96e0mdk16+OBl+dTqp+1HCOhGYGpzzpXMA2VYSYamKnlH23c5budfc9:0SwsS3GKopuQGVSwsS3GKESwsS3GKf |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4392)
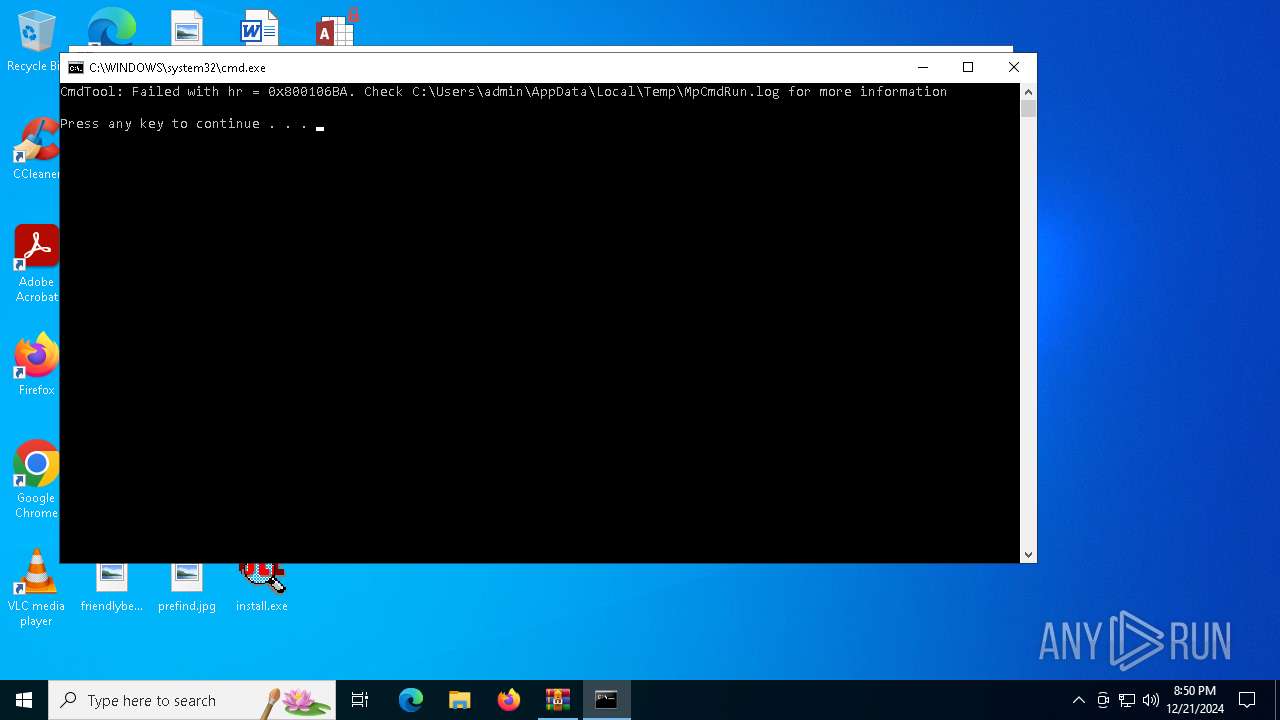
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 5256)
SUSPICIOUS
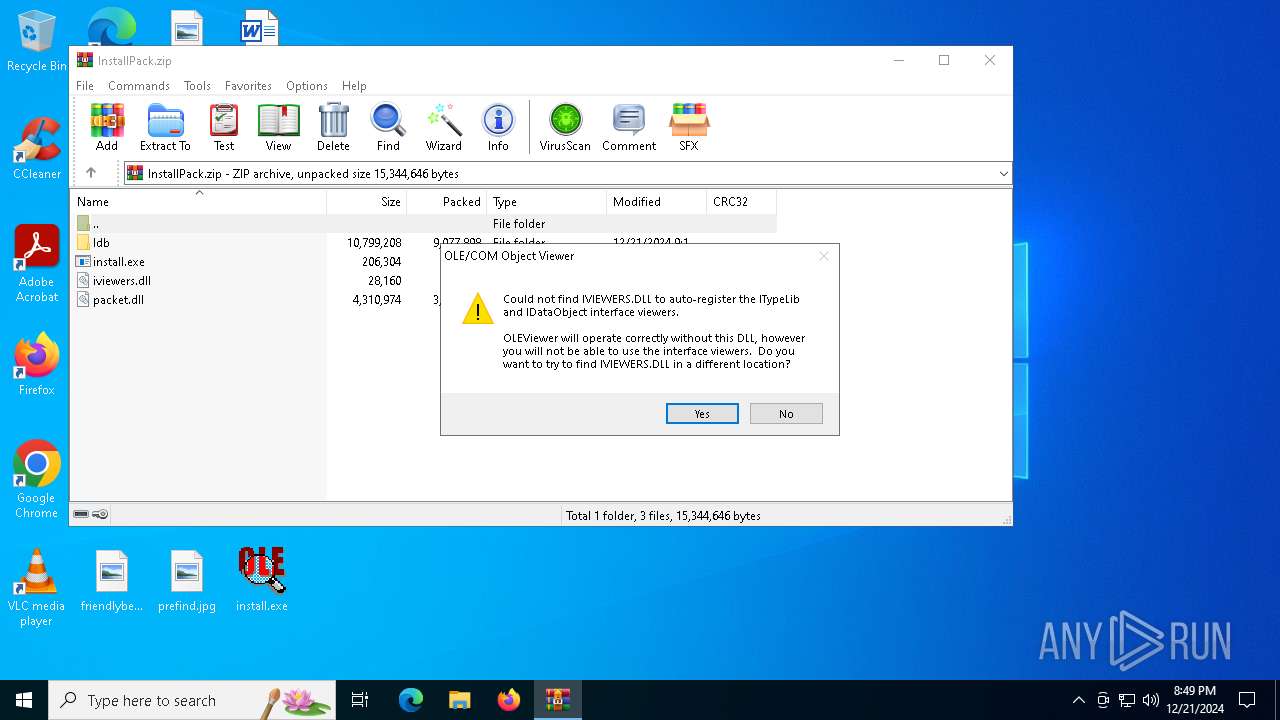
Starts a Microsoft application from unusual location
- install.exe (PID: 4980)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4392)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4392)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4392)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4392)
INFO
Manual execution by a user
- install.exe (PID: 4980)
- OpenWith.exe (PID: 4764)
- OpenWith.exe (PID: 4824)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4764)
- OpenWith.exe (PID: 4824)
Checks supported languages
- install.exe (PID: 4980)
- MpCmdRun.exe (PID: 5256)
Reads the computer name
- install.exe (PID: 4980)
- MpCmdRun.exe (PID: 5256)
The process uses the downloaded file
- WinRAR.exe (PID: 4392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4392)
The sample compiled with english language support
- WinRAR.exe (PID: 4392)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:12:02 04:59:12 |
| ZipCRC: | 0x5a6a66ef |
| ZipCompressedSize: | 79547 |
| ZipUncompressedSize: | 206304 |
| ZipFileName: | install.exe |
Total processes
123
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\InstallPack.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4764 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\000495.ldb | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\000005.ldb | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4980 | "C:\Users\admin\Desktop\install.exe" | C:\Users\admin\Desktop\install.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: OLE/COM Object Viewer Version: 10.0.19041.685 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\Rar$Scan51567.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5256 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 876
Read events
2 864
Write events
12
Delete events
0
Modification events
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\InstallPack.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4764) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ldb\OpenWithProgids |
| Operation: | write | Name: | Access.LockFile.16 |
Value: | |||
| (PID) Process: | (4824) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ldb\OpenWithProgids |
| Operation: | write | Name: | Access.LockFile.16 |
Value: | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\packet.dll | — | |
MD5:— | SHA256:— | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\ldb\000886.ldb | — | |
MD5:— | SHA256:— | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\ldb\122455.ldb | — | |
MD5:— | SHA256:— | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\install.exe | executable | |
MD5:2696D944FFBEF69510B0C826446FD748 | SHA256:A4F53964CDDDCCCBD1B46DA4D3F7F5F4292B5DD11C833D3DB3A1E7DEF36DA69A | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\ldb\000495.ldb | binary | |
MD5:F7971FB42F2AD20E488AEB4259885DC5 | SHA256:359165176B7FDCE424D3C0EA2B8AA9F73A07B1B2D4DE220A3904A14E85A60184 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\ldb\000005.ldb | binary | |
MD5:2F10108C3010C377E7456E8B24FE9141 | SHA256:1E8037CE6B26161D9363F90D1B1950E598AF860EEB2C9DC637CE6B8694322AEB | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\InstallPack.zip\iviewers.dll | executable | |
MD5:7A1F330D4D54B5259EB06A0E4E6D8E95 | SHA256:909B3E941DCD16485EB0D4518145E7B27423EB0C323CF2666151AF0076776611 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.4644\Rar$Scan51567.bat | text | |
MD5:8D729F2EC22DC5FCE23872DFFEBA0625 | SHA256:C8BC7485F075BFBC395A9043F80C2E983C0A0E030436F7FD3F6C0CBB01604A14 | |||
| 5256 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:5B233D14236DF0D382ED9AEB55481766 | SHA256:717F38FDE6A86C42FC7E52F57A57B113F314ED7E9BD40965952D63DC476D6746 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5448 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5448 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5448 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5448 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5448 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |