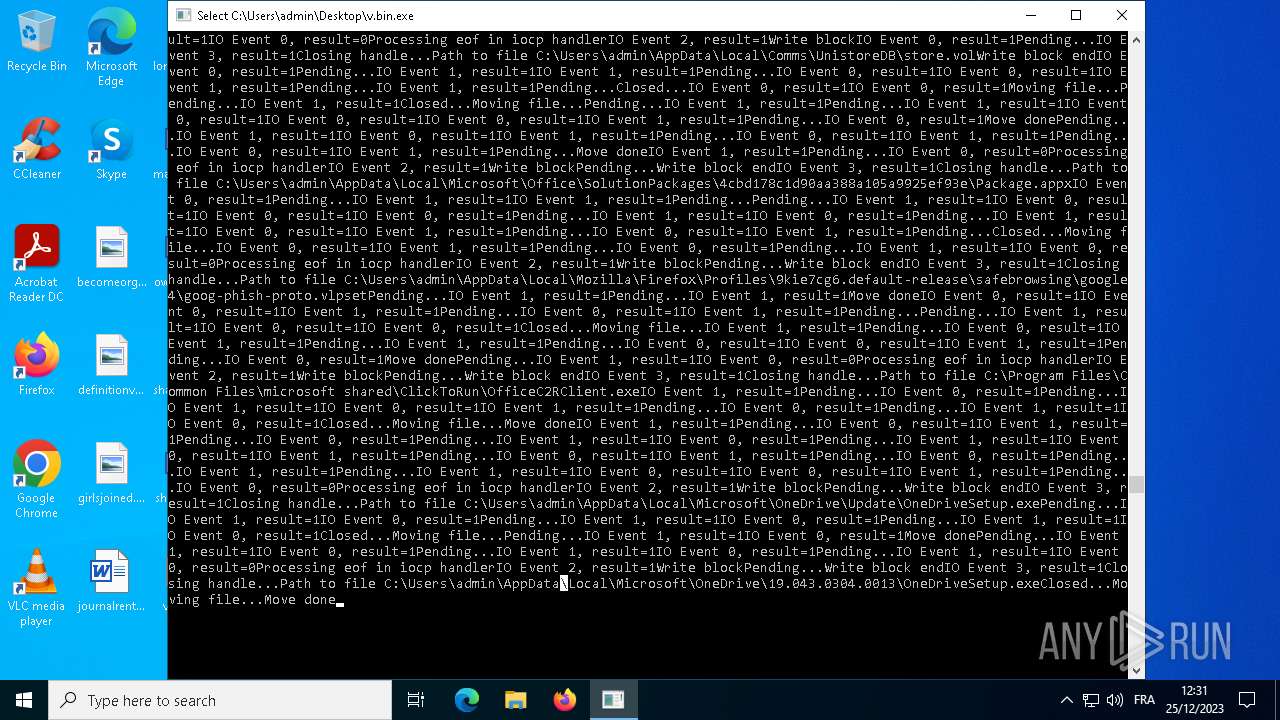
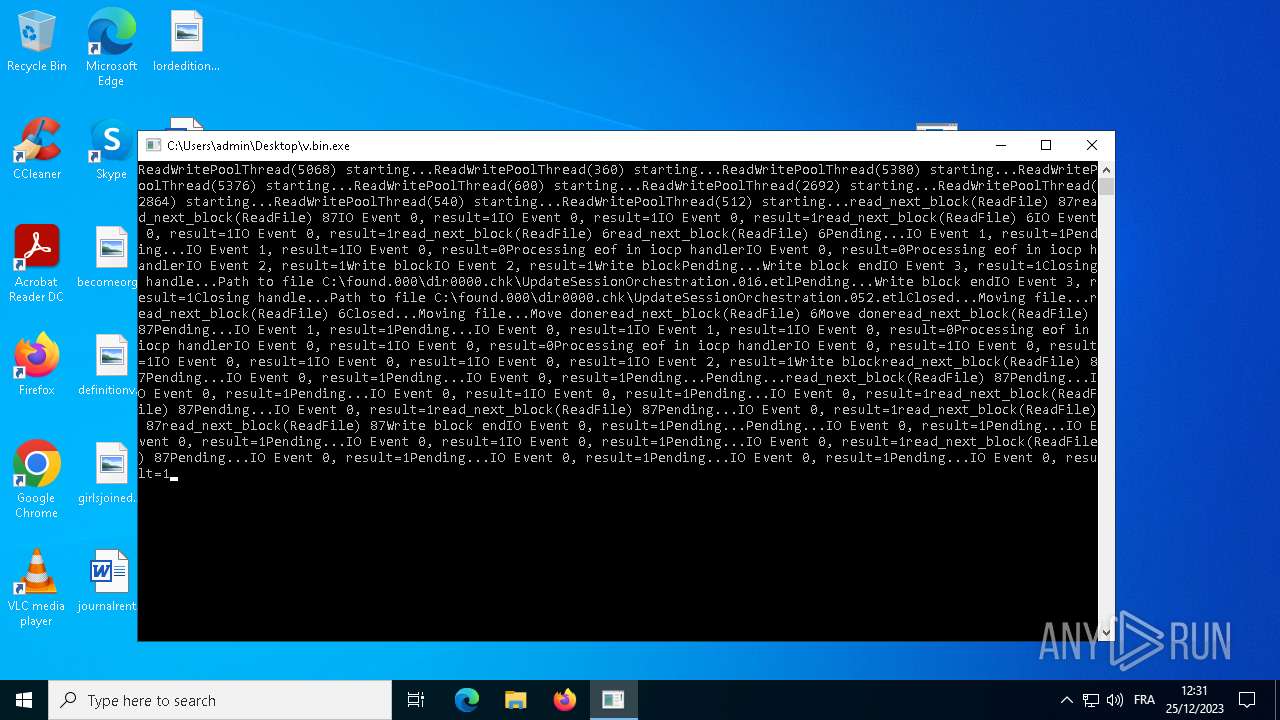
| File name: | v.bin |
| Full analysis: | https://app.any.run/tasks/bb854506-c655-4f02-a36d-5197536dc576 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2023, 11:29:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 85A3936612C12269B47F33930F990E8A |
| SHA1: | 2762209E26E7DA7FA4FAF2359366B835639159EA |
| SHA256: | 189EB8CF2EF8043E6438A8618710A07A7C020E77D6BCDD2D561BC50E073BCD83 |
| SSDEEP: | 3072:po28gotMjuneUUWM5M/j45mtjv7TpSc6ne98jqFZEIViH0EOxvR4HpMfpRnR+6hg:a28lMajU2j45mN7TpSc6O86VE0XBFrg |
MALICIOUS
Actions looks like stealing of personal data
- v.bin.exe (PID: 3680)
SUSPICIOUS
No suspicious indicators.INFO
Drops the executable file immediately after the start
- v.bin.exe (PID: 3680)
- v.bin.exe (PID: 2268)
Checks supported languages
- v.bin.exe (PID: 3680)
- v.bin.exe (PID: 2268)
Process drops legitimate windows executable
- v.bin.exe (PID: 3680)
Manual execution by a user
- v.bin.exe (PID: 2268)
- mspaint.exe (PID: 3892)
Checks proxy server information
- slui.exe (PID: 2032)
Reads the software policy settings
- slui.exe (PID: 2584)
- slui.exe (PID: 2032)
Dropped object may contain TOR URL's
- v.bin.exe (PID: 3680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:25 10:53:39+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 76288 |
| InitializedDataSize: | 85504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x403e |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
131
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\Desktop\v.bin.exe" | C:\Users\admin\Desktop\v.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2584 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3680 | "C:\Users\admin\Desktop\v.bin.exe" | C:\Users\admin\Desktop\v.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | v.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3892 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\sharewrote.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | v.bin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5396 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.1202 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 098
Read events
1 097
Write events
0
Delete events
1
Modification events
| (PID) Process: | (3892) mspaint.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Applets\Paint\Recent File List |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
14
Suspicious files
5 076
Text files
22
Unknown types
72
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-localization-l1-2-0.dll | binary | |
MD5:70477361CDAD452712691640C43695F2 | SHA256:2BCF8BADACDB918B3964124C1FCDB0F928D35A18A42D7C899CE3634E554A3C4D | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-processthreads-l1-1-1.dll | binary | |
MD5:17A6913CEC82CD2579DBE39AABFEB438 | SHA256:D8119907F93B3096B36FD1A05D969E9DB920BFD47D8A9187BB6A5C79CC93F2DB | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-timezone-l1-1-0.dll | binary | |
MD5:5E03A7EC1B4954DEEA27A30300D41755 | SHA256:73D6E9D924627FCE936169ABFA14BC2B28D0BC3024F659D9FB1C2BC4D94C5A8E | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-filesystem-l1-1-0.dll | binary | |
MD5:C2C5E072AE0CAFC7A8DB85129B05A3B8 | SHA256:1A2812DEF725B88BFB88F60CA2507E6EFC13373F26EED8A3A692C648FF4E4998 | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-conio-l1-1-0.dll | binary | |
MD5:DD48B950C20E5AD0EE08EC29C5ED6280 | SHA256:DC117C4AB3A560BFED05E5787EA0F9B3B815FD766BB5F9E33056D31A518605BC | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-xstate-l2-1-0.dll | binary | |
MD5:1472E750119DF244AE65AFCFCF92FDD6 | SHA256:6F94E9541CE252A35DCFC24A0E24AB356B0F41A73FA82D50A77FB8646FD365F0 | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-file-l2-1-0.dll | binary | |
MD5:C37FF25CA90FC501C7806D6AEA254A61 | SHA256:70581808141EC655CCBBAAAD97108470D7EAE7EBE6C2E711BA493F78912546DA | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-heap-l1-1-0.dll | binary | |
MD5:78CFC608260497B0846E97134A40A860 | SHA256:2AB7293694DCBB5BF74F24032C3534B46D21C4CC857C54C30C76E95678940B72 | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-crt-time-l1-1-0.dll | binary | |
MD5:245D4618BDECD1659D1B7CA7E4E5B1E1 | SHA256:AAD60FE2067D31F664B6BC16C6E14E5858BED2F4B40D749B9F8740D23F0E3F57 | |||
| 3680 | v.bin.exe | C:\Program Files\Common Files\microsoft shared\ClickToRun\api-ms-win-core-synch-l1-2-0.dll | binary | |
MD5:7CFE2A0423BA9C5CBAEB201A89CE17FA | SHA256:9E8231903717CA8320113BE8C7DEE97DF7F5C88A5B05BF5666C4172CA7A32640 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
39
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
3016 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
3016 | SIHClient.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
2908 | svchost.exe | GET | 200 | 92.123.17.153:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2644 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
1092 | svchost.exe | POST | — | 20.231.121.79:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1232 | svchost.exe | 40.126.32.140:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1092 | svchost.exe | 184.30.17.189:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
1092 | svchost.exe | 20.231.121.79:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5612 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5612 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3016 | SIHClient.exe | 40.68.123.157:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3016 | SIHClient.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1092 | svchost.exe | 138.91.171.81:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3016 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |