| URL: | https://www.windows7download.com/win7-bonzi-buddy/download-rxcxenfb.html |
| Full analysis: | https://app.any.run/tasks/2d1f965f-a534-4426-903a-fe589feb5064 |
| Verdict: | Malicious activity |
| Analysis date: | February 28, 2024, 10:43:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 674EC784EB6C5B3E4FE522C4C2FC48C9 |
| SHA1: | D6C50A4835BE84214EDC6CD2BEE3036B27670088 |
| SHA256: | 189904E6DF9571B06F6B07636FDA19B3A711F47B75369C6BD7B633DED5DD95E3 |
| SSDEEP: | 3:N8DSLjFnKCmHv4kX0uDQJ:2OLdKvutJ |
MALICIOUS
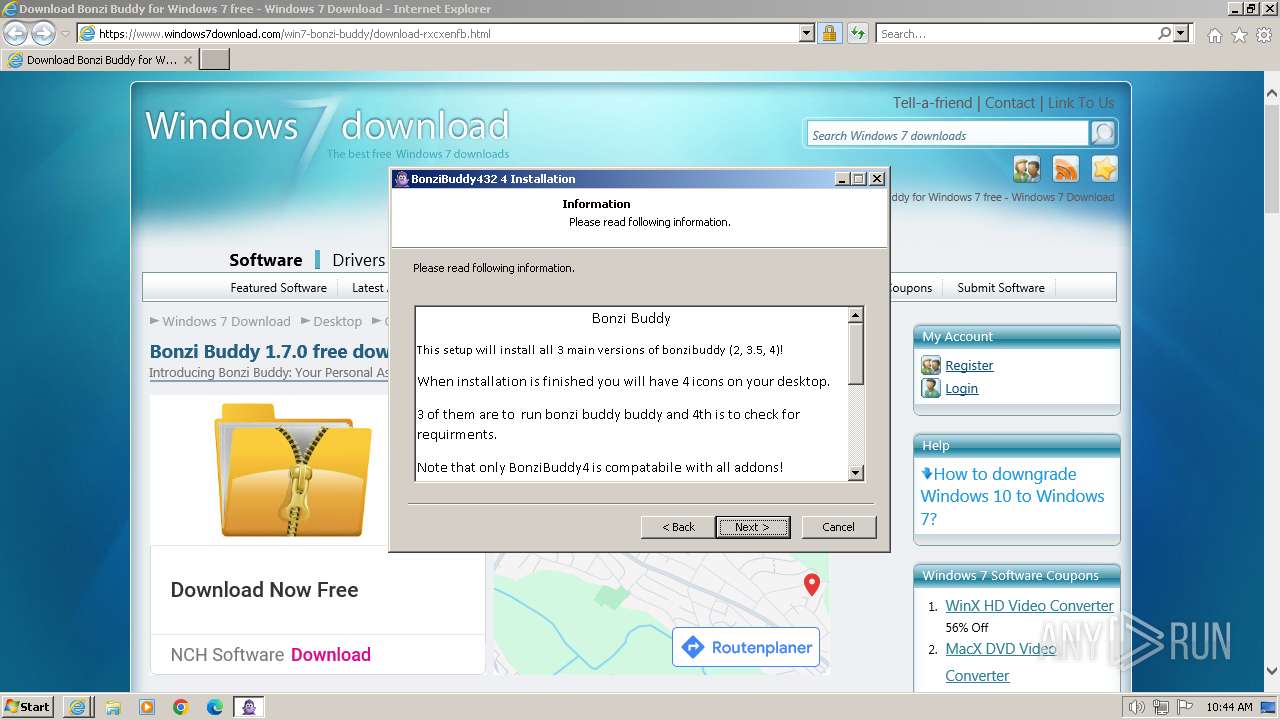
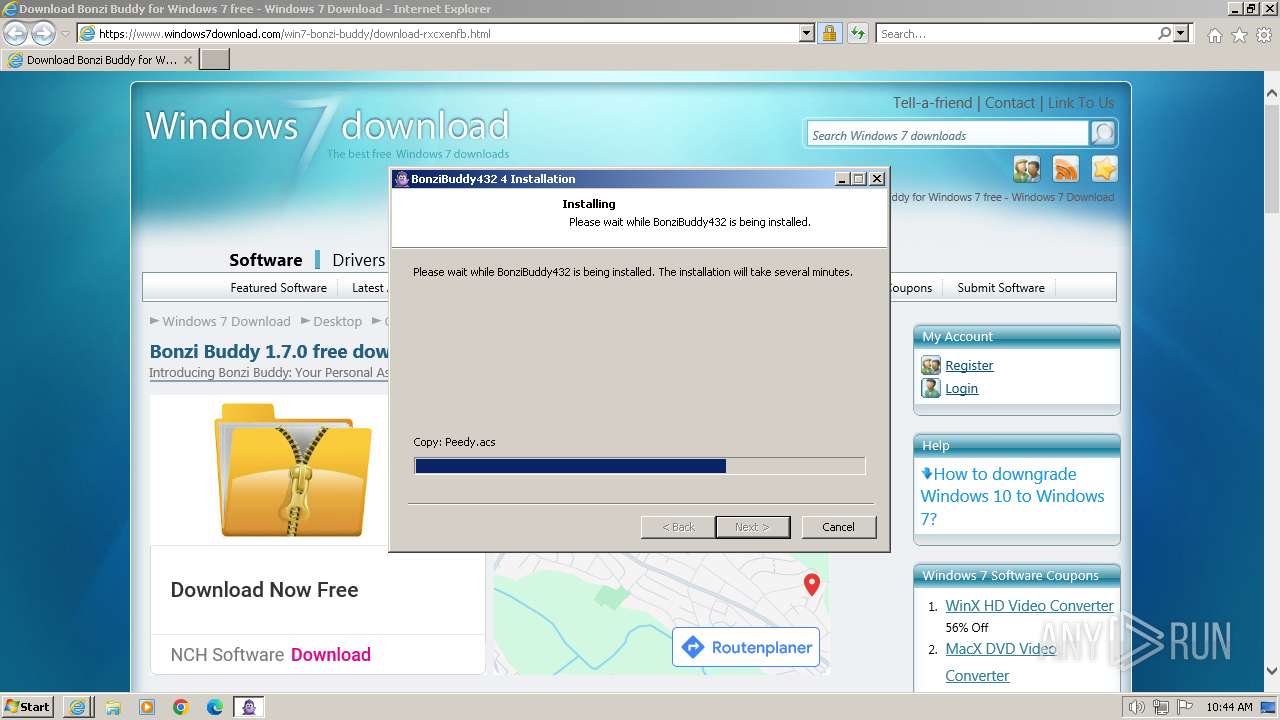
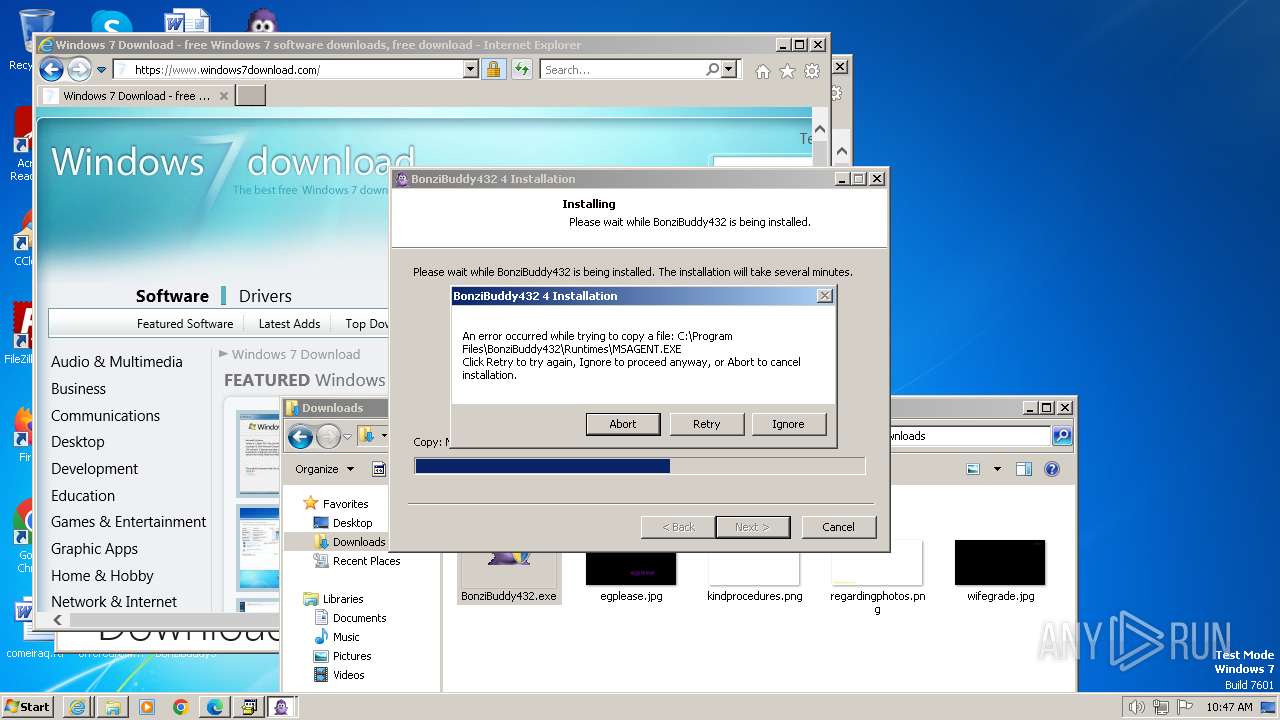
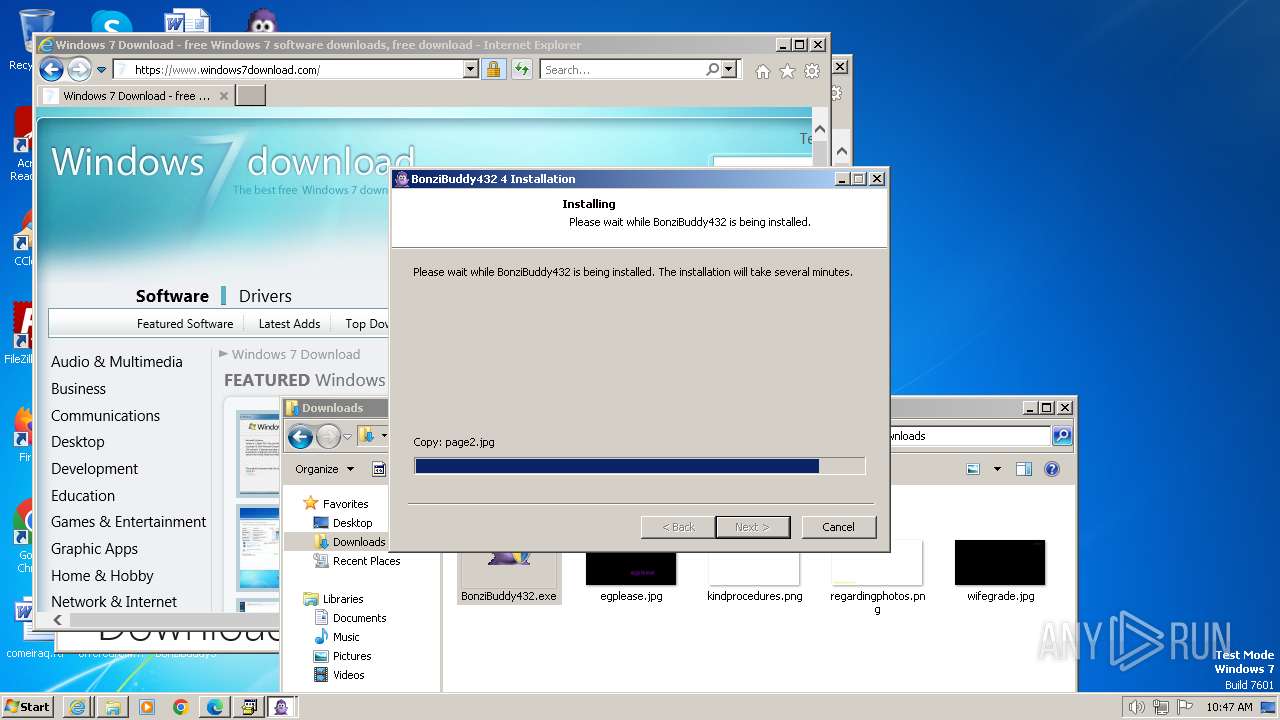
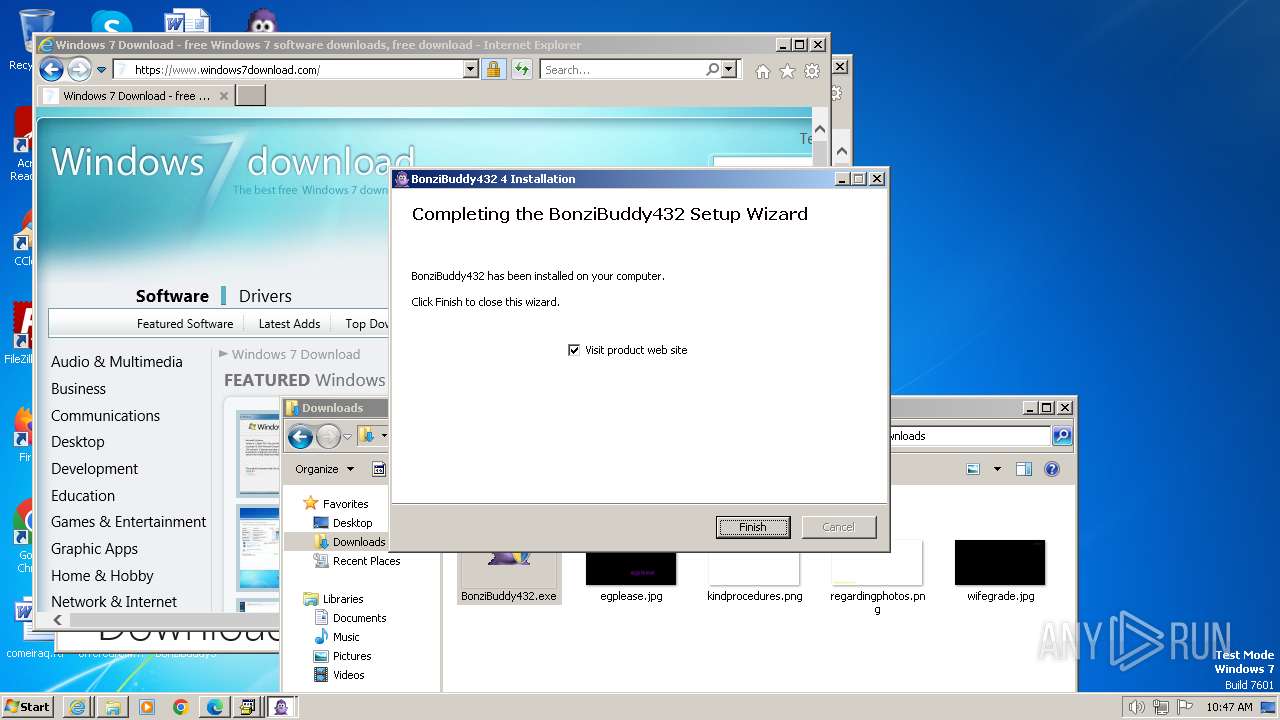
Drops the executable file immediately after the start
- BonziBuddy432.exe (PID: 3980)
- tv_enua.exe (PID: 2128)
- BonziBuddy432.exe (PID: 1728)
Registers / Runs the DLL via REGSVR32.EXE
- tv_enua.exe (PID: 2128)
Creates a writable file in the system directory
- tv_enua.exe (PID: 2128)
Changes the autorun value in the registry
- tv_enua.exe (PID: 2128)
SUSPICIOUS
Reads the Internet Settings
- BonziBuddy432.exe (PID: 3980)
- wmplayer.exe (PID: 1596)
- setup_wm.exe (PID: 1812)
- BonziBuddy432.exe (PID: 1728)
Process drops legitimate windows executable
- BonziBuddy432.exe (PID: 3980)
- tv_enua.exe (PID: 2128)
- BonziBuddy432.exe (PID: 1728)
Starts CMD.EXE for commands execution
- BonziBuddy432.exe (PID: 3980)
- BonziBuddy432.exe (PID: 1728)
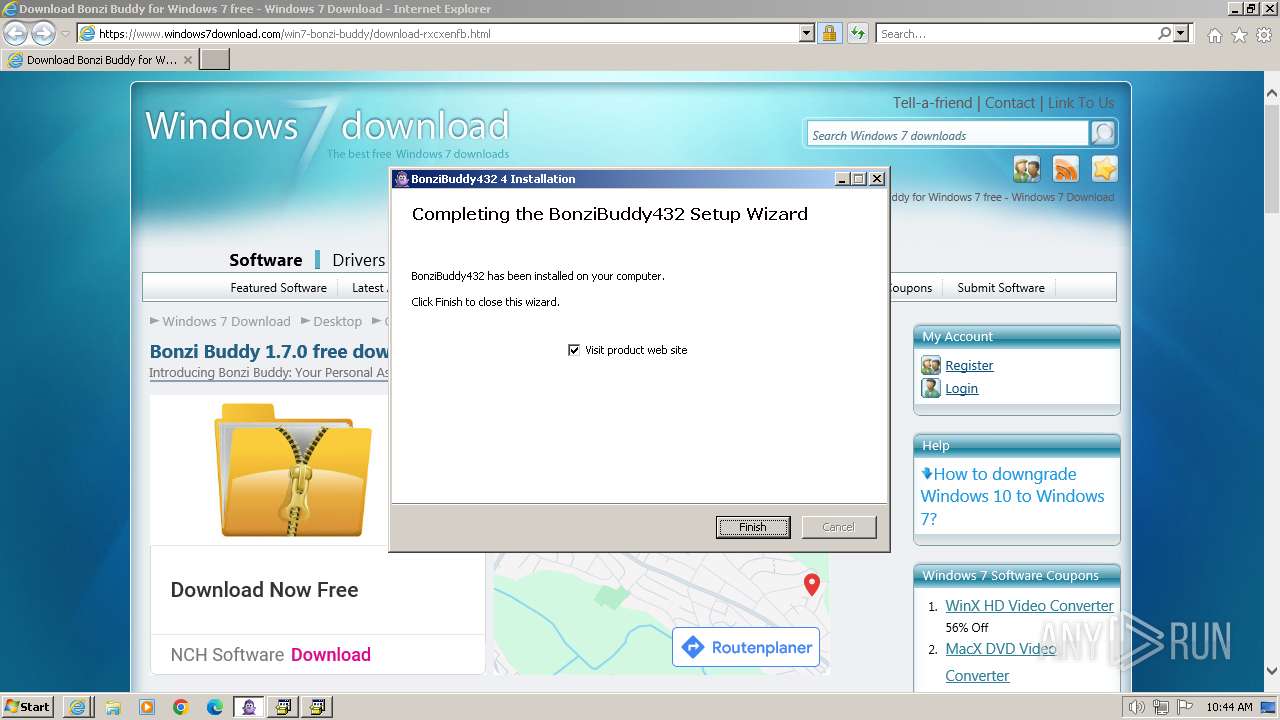
Creates a software uninstall entry
- BonziBuddy432.exe (PID: 3980)
- BonziBuddy432.exe (PID: 1728)
- tv_enua.exe (PID: 2128)
Executable content was dropped or overwritten
- BonziBuddy432.exe (PID: 3980)
- tv_enua.exe (PID: 2128)
- BonziBuddy432.exe (PID: 1728)
Creates/Modifies COM task schedule object
- BonziBuddy432.exe (PID: 3980)
- regsvr32.exe (PID: 2120)
- regsvr32.exe (PID: 2940)
- BonziBuddy432.exe (PID: 1728)
Reads security settings of Internet Explorer
- BonziBuddy432.exe (PID: 3980)
- wmplayer.exe (PID: 1596)
- setup_wm.exe (PID: 1812)
- BonziBuddy432.exe (PID: 1728)
Executing commands from a ".bat" file
- BonziBuddy432.exe (PID: 3980)
- BonziBuddy432.exe (PID: 1728)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3708)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3708)
Application launched itself
- iexplore.exe (PID: 3348)
- msedge.exe (PID: 3940)
- msedge.exe (PID: 1608)
- msedge.exe (PID: 3260)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3348)
Reads the computer name
- BonziBuddy432.exe (PID: 3980)
- wmplayer.exe (PID: 1596)
- setup_wm.exe (PID: 1812)
- BonziBuddy432.exe (PID: 2016)
- BonziBuddy432.exe (PID: 1728)
- tv_enua.exe (PID: 2128)
The process uses the downloaded file
- iexplore.exe (PID: 3348)
Create files in a temporary directory
- BonziBuddy432.exe (PID: 3980)
- tv_enua.exe (PID: 2128)
- setup_wm.exe (PID: 1812)
- BonziBuddy432.exe (PID: 2016)
- BonziBuddy432.exe (PID: 1728)
Checks supported languages
- BonziBuddy432.exe (PID: 3980)
- tv_enua.exe (PID: 2128)
- MSAGENT.EXE (PID: 3444)
- wmplayer.exe (PID: 1596)
- setup_wm.exe (PID: 1812)
- BonziBuddy432.exe (PID: 2016)
- BonziBuddy432.exe (PID: 1728)
- MSAGENT.EXE (PID: 3932)
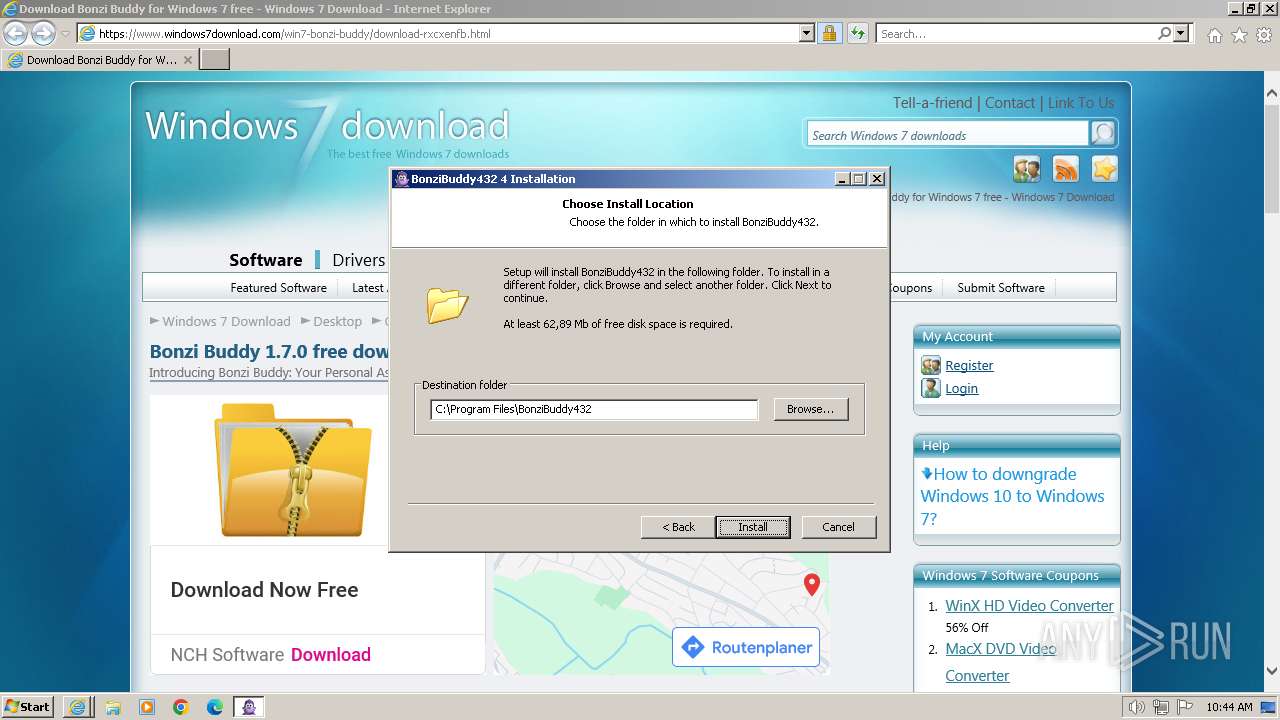
Creates files in the program directory
- BonziBuddy432.exe (PID: 3980)
- BonziBuddy432.exe (PID: 1728)
Reads mouse settings
- BonziBuddy432.exe (PID: 3980)
- BonziBuddy432.exe (PID: 1728)
Manual execution by a user
- msedge.exe (PID: 3260)
- wmplayer.exe (PID: 1596)
- explorer.exe (PID: 296)
- BonziBuddy432.exe (PID: 2128)
- BonziBuddy432.exe (PID: 2016)
- BonziBuddy432.exe (PID: 2348)
- BonziBuddy432.exe (PID: 1728)
Reads the machine GUID from the registry
- setup_wm.exe (PID: 1812)
Process checks computer location settings
- setup_wm.exe (PID: 1812)
Reads Environment values
- setup_wm.exe (PID: 1812)
Checks proxy server information
- setup_wm.exe (PID: 1812)
Creates files or folders in the user directory
- BonziBuddy432.exe (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
102
Monitored processes
46
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3348 CREDAT:988441 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1196 --field-trial-handle=1268,i,12317205874989256796,7929829615632782821,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1172 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1248 --field-trial-handle=1316,i,18319293847973100622,5998117851974374878,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3784 --field-trial-handle=1316,i,18319293847973100622,5998117851974374878,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3544 --field-trial-handle=1316,i,18319293847973100622,5998117851974374878,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1592 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1428 --field-trial-handle=1268,i,12317205874989256796,7929829615632782821,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\wmplayer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Exit code: 0 Version: 12.0.7601.23517 (win7sp1_ldr.160812-0732) Modules
| |||||||||||||||
| 1608 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://bonzibuddy.tk/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | BonziBuddy432.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
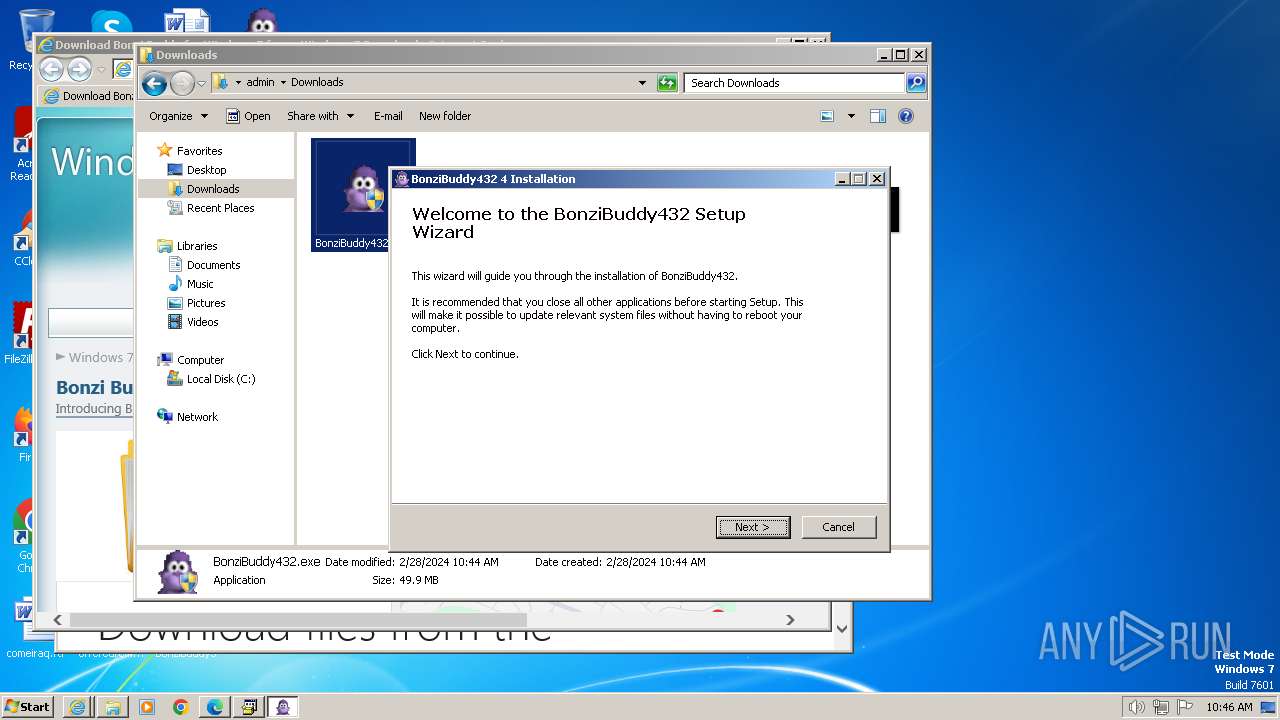
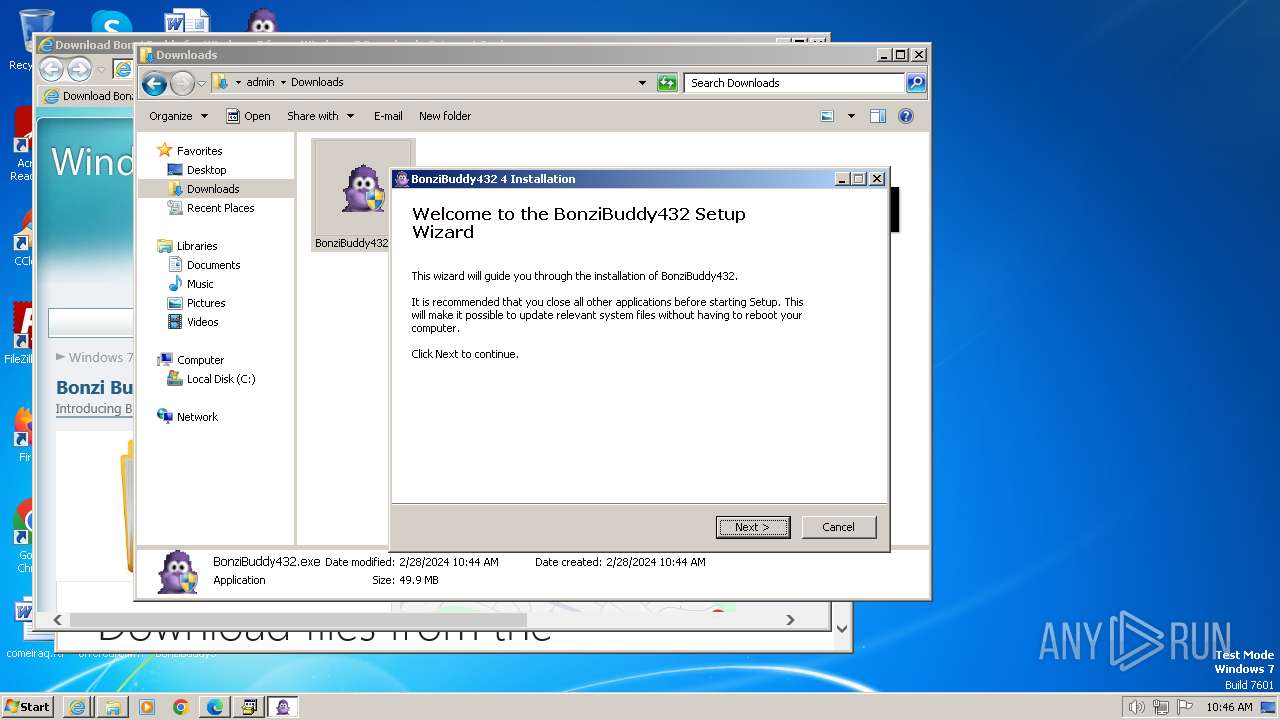
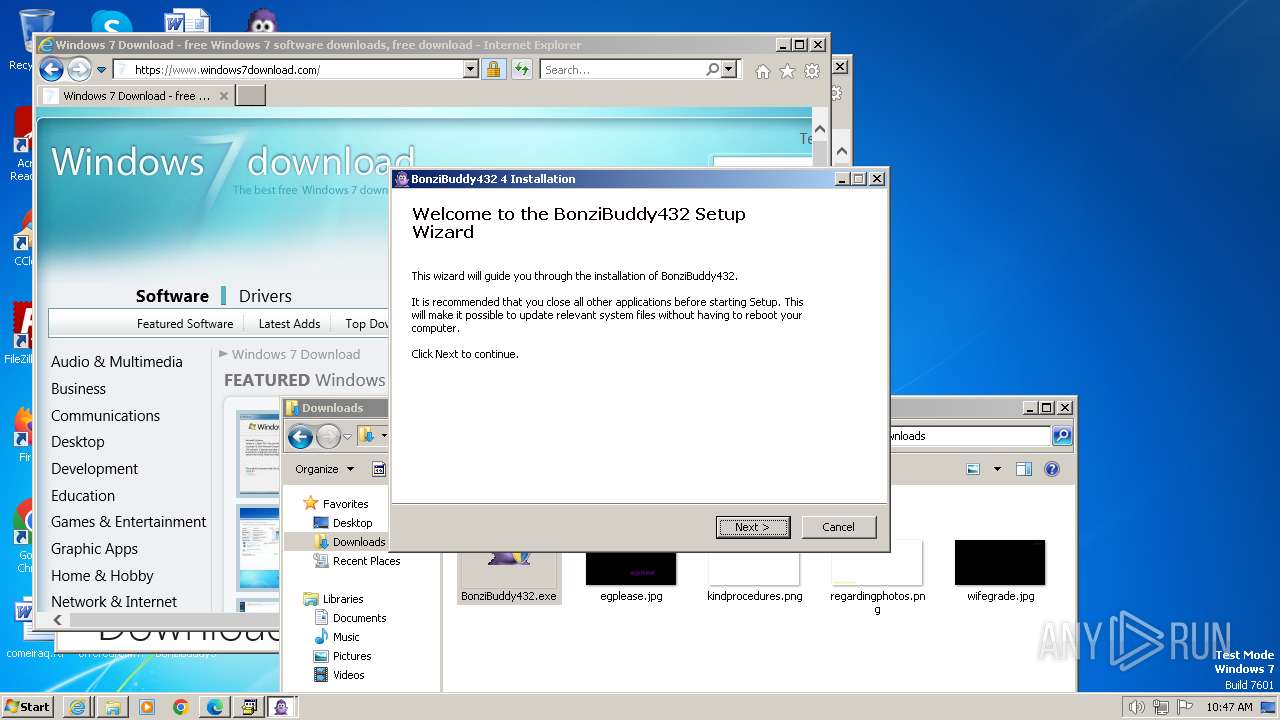
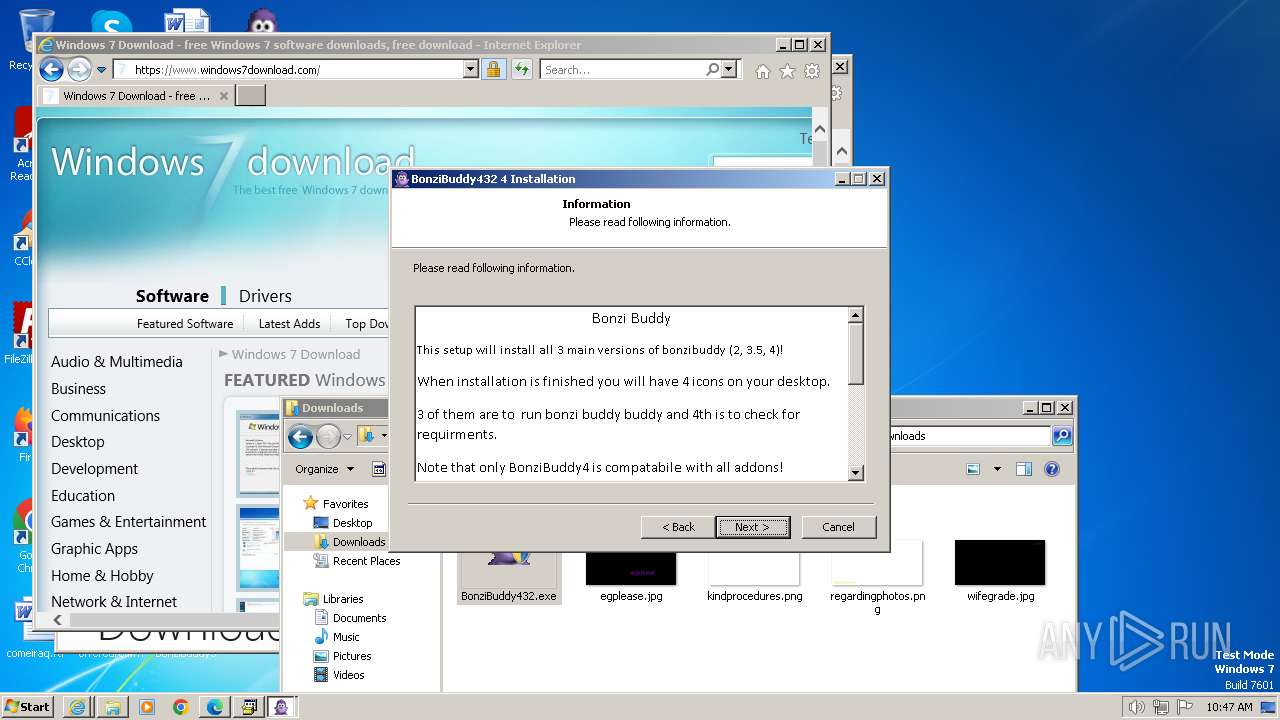
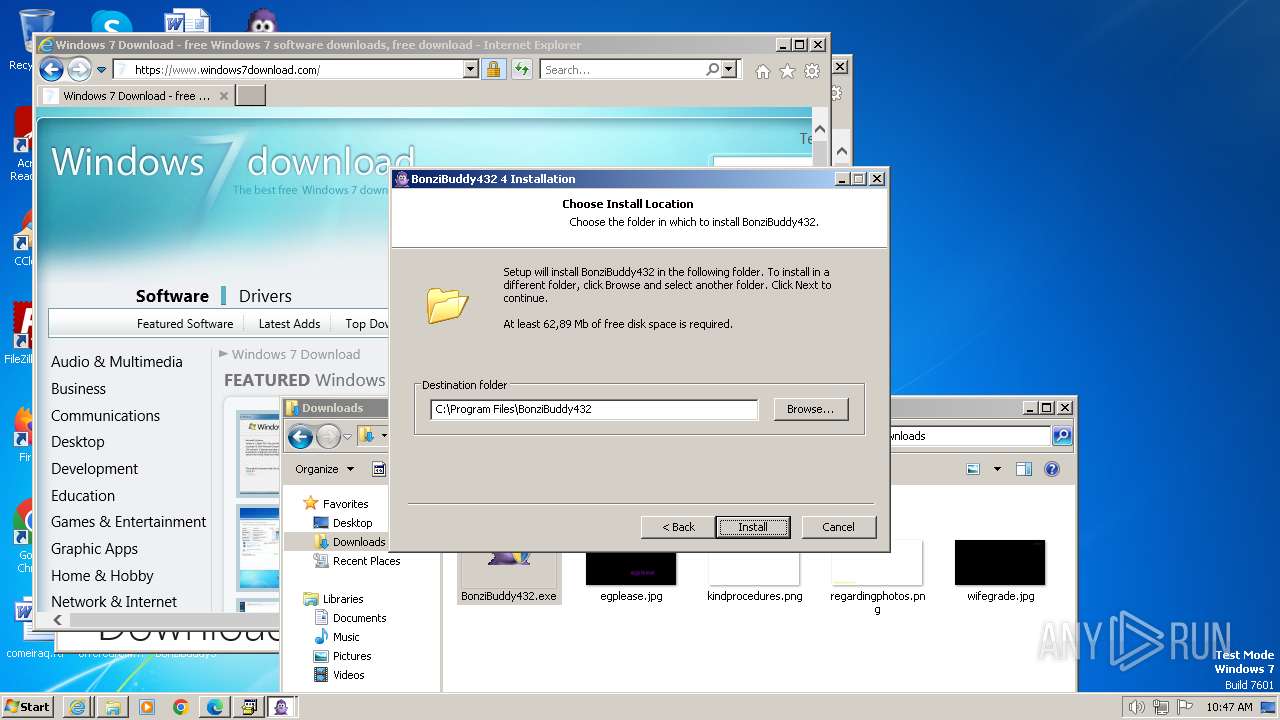
| 1728 | "C:\Users\admin\Downloads\BonziBuddy432.exe" | C:\Users\admin\Downloads\BonziBuddy432.exe | explorer.exe | ||||||||||||
User: admin Company: Bonzi Software Integrity Level: HIGH Description: BonziBuddy432 4 Installation Exit code: 3221225547 Version: 4 Modules
| |||||||||||||||
Total events
61 551
Read events
60 350
Write events
767
Delete events
434
Modification events
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 123992704 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31091251 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 424155204 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31091251 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
80
Suspicious files
118
Text files
578
Unknown types
107
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3708 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\rating[1].css | text | |
MD5:FDDFBEB5892D4F867112A989EDF187A1 | SHA256:4F861DE38EF4934745376B48CB698DB4C6ACB156378D0AEAF6778FE15185B787 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:1D0C9D388488E25BA9660FF4D68EC83B | SHA256:6B8FC7A10DB214DB80A37642273573D65DD78B75B26B311D1DE77F207A97D403 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:CAA11E25E05806D8291BB6AA9922D368 | SHA256:871C385776C3EF94D3B09C9A6C982480A33FFF198FA3C106047C3DB492AF087C | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:36FAC61743E405273BC3E5C76F30993B | SHA256:7C7BD64AC168CD144F3B5F5109452715E1A66A7D5222E83B0B3E8E543B437DED | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_E8AB3F6B94D563A8B6A387168D3E7B81 | der | |
MD5:46247F9C00A942FC36A3F62DCABB4FC5 | SHA256:3E1373616AF8355A42B7BCBBCD6481F238454A72F79AA820658EF2D6C66A33D9 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\widgets[1].js | text | |
MD5:824BEB891744DB98CCBD3A456E59E0F7 | SHA256:173460E89E6A7244218BADAE2016F65C48A3EAE9D400802273EECA18B07336F1 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\rating.min[1].js | text | |
MD5:62E26B280B315443633D2FA612D4E082 | SHA256:941C07FB2B8EC3872D52F6FD7ECB4BD341B97476C7E77C5245E1C6169F338CF8 | |||
| 3708 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:9ACA8F0EE5703E18CAE6D688F2E8568B | SHA256:9C8F46157735768028AD87C590B1C9BE7CA320891668D11F6BE1BA27EC7D032F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
202
DNS requests
99
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3708 | iexplore.exe | GET | 304 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9f2b763ba05a2db | unknown | — | — | unknown |
3708 | iexplore.exe | GET | 200 | 23.192.153.142:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3708 | iexplore.exe | GET | 304 | 173.222.108.147:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?14266dff8470122f | unknown | — | — | unknown |
3708 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3708 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
3708 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGHsycmQas7CCZXEOfu%2B%2Bqs%3D | unknown | binary | 471 b | unknown |
3708 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDWcu1vhm%2F7Dgq%2BMnSH3EBn | unknown | binary | 472 b | unknown |
3708 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | binary | 471 b | unknown |
3708 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEALeSdKlLJXCFLT6KOkng0s%3D | unknown | binary | 471 b | unknown |
3708 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDDidhelLJLaQnsKqlsZYpa | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3708 | iexplore.exe | 193.203.165.208:443 | www.windows7download.com | — | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3708 | iexplore.exe | 173.222.108.147:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3708 | iexplore.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
3708 | iexplore.exe | 23.192.153.142:80 | x1.c.lencr.org | AKAMAI-AS | GB | unknown |
3708 | iexplore.exe | 216.58.212.132:443 | www.google.com | GOOGLE | US | whitelisted |
3708 | iexplore.exe | 142.250.186.34:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
3708 | iexplore.exe | 93.184.220.66:443 | platform.twitter.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.windows7download.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.google.com |
| whitelisted |
platform.twitter.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3988 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3988 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3988 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3988 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
3988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
3988 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
Process | Message |
|---|---|
msedge.exe | [0228/104801.979:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|