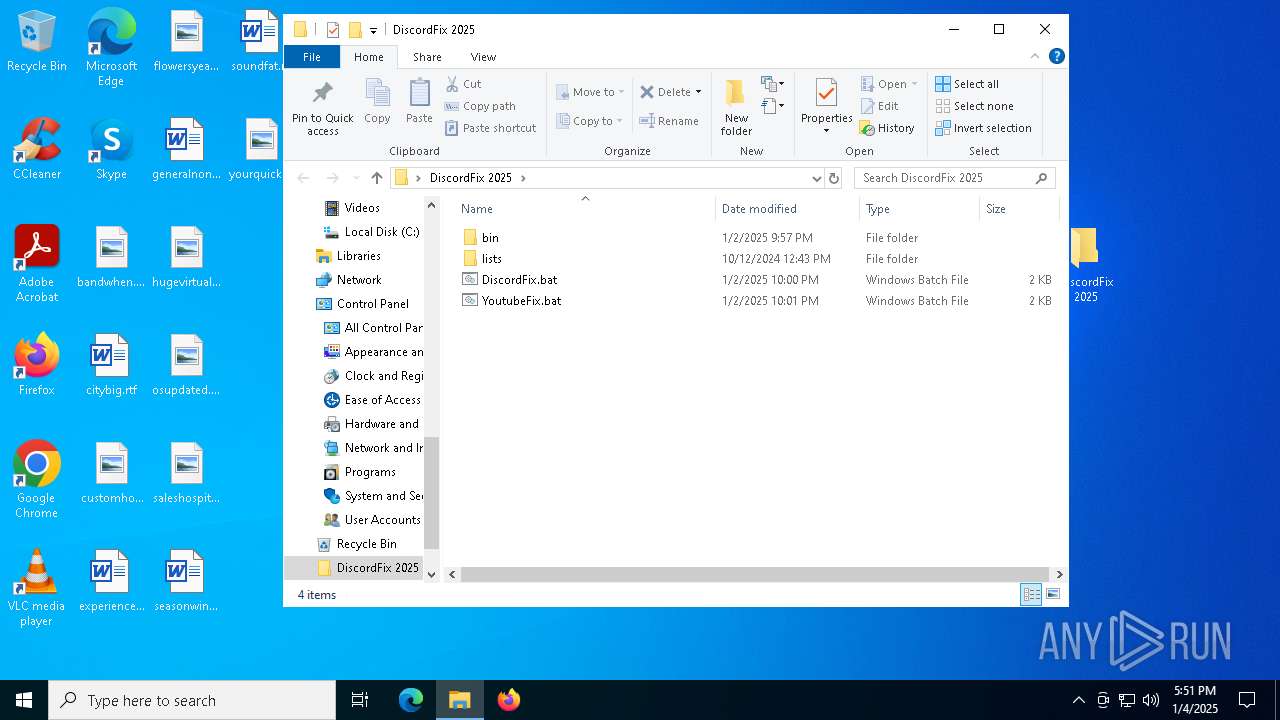
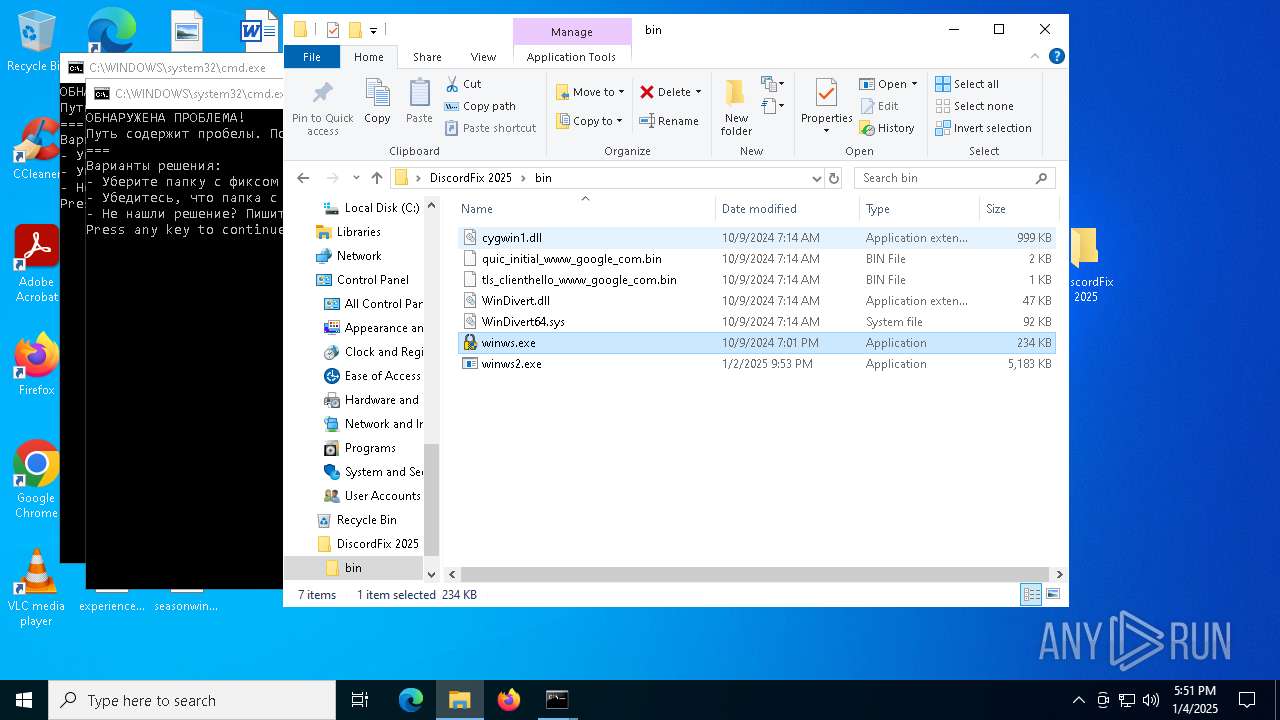
| File name: | DiscordFix 2025.rar |
| Full analysis: | https://app.any.run/tasks/b4d3ad9e-b310-4076-951f-99ee2b8ecd0b |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2025, 17:51:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 87EBAB96600629CF7CD192D298D25AAF |
| SHA1: | 13CA1BDBC1381E76045E535087FD2356F899F404 |
| SHA256: | 188AE5C7F44EB1719B7DF960FD77D3425FB658EC30222567D864FC3D9E501B65 |
| SSDEEP: | 98304:mcEZqli5RjzEGd5uaQ6vJCnYELJXhgfNjVIvBXfpY6NveYhqY60zPZDVCQU1Cy9/:3VFptymeCgF |
MALICIOUS
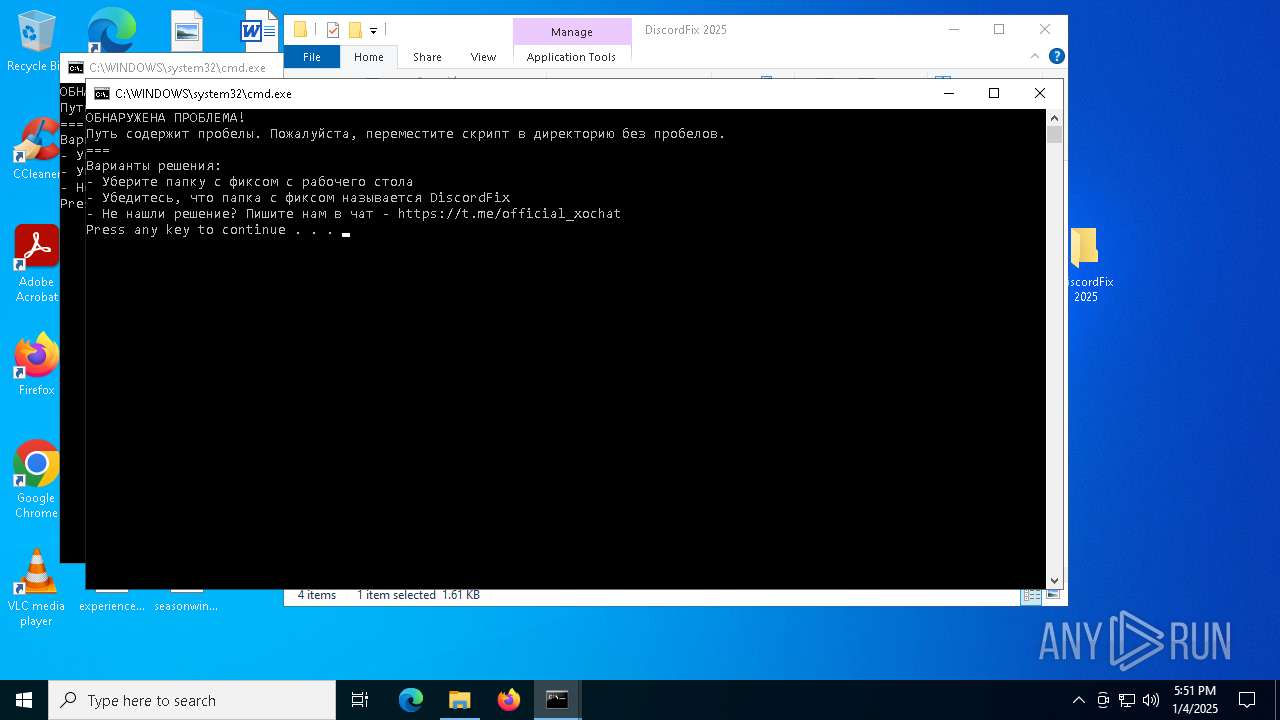
Detects Cygwin installation
- WinRAR.exe (PID: 6304)
Executing a file with an untrusted certificate
- winws2.exe (PID: 4128)
- winws2.exe (PID: 6456)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6304)
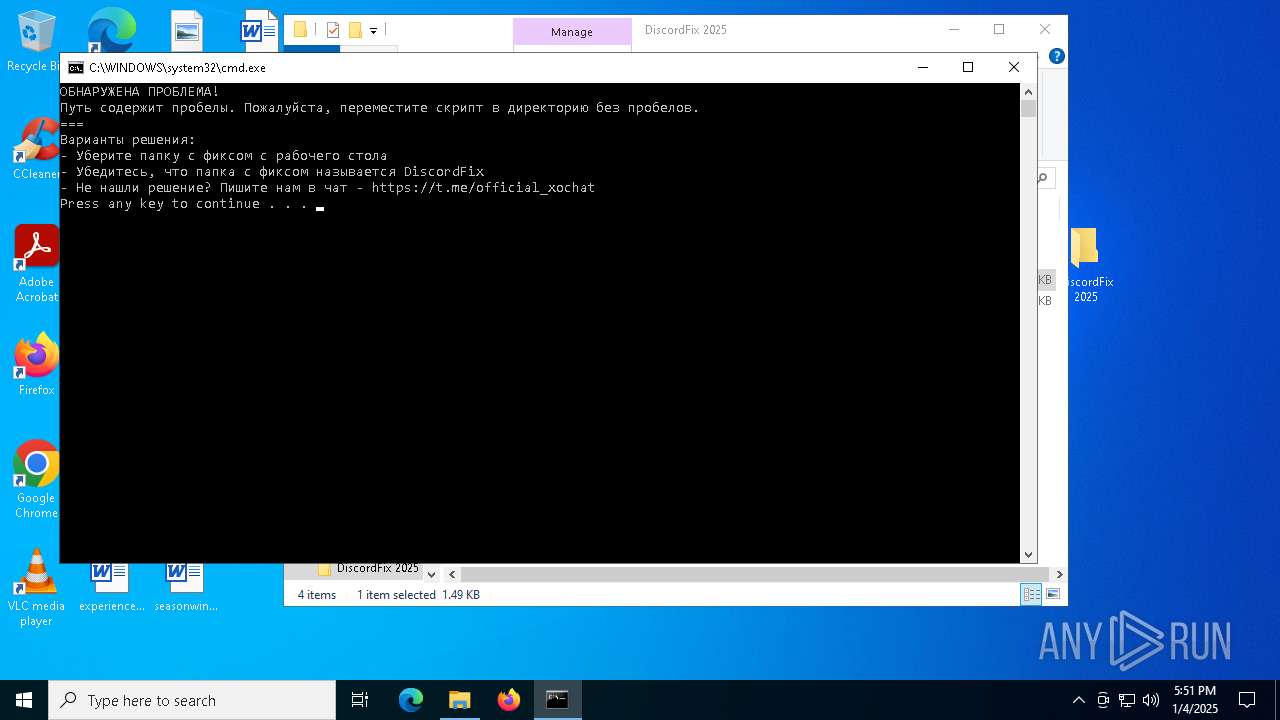
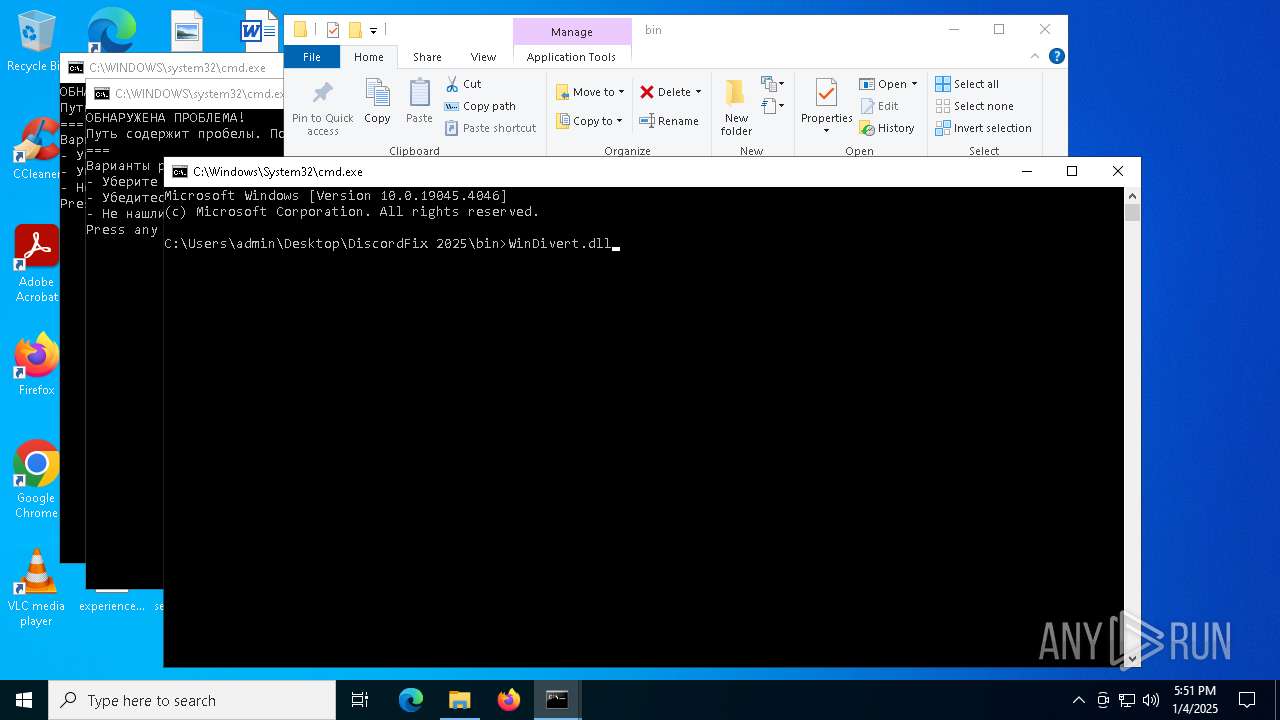
Starts application with an unusual extension
- cmd.exe (PID: 7160)
- cmd.exe (PID: 5920)
Starts POWERSHELL.EXE for commands execution
- winws2.exe (PID: 4128)
- winws2.exe (PID: 6456)
Starts process via Powershell
- powershell.exe (PID: 4160)
- powershell.exe (PID: 6468)
INFO
Changes the display of characters in the console
- cmd.exe (PID: 7160)
- cmd.exe (PID: 5920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6304)
The sample compiled with english language support
- WinRAR.exe (PID: 6304)
The process uses the downloaded file
- WinRAR.exe (PID: 6304)
- cmd.exe (PID: 1684)
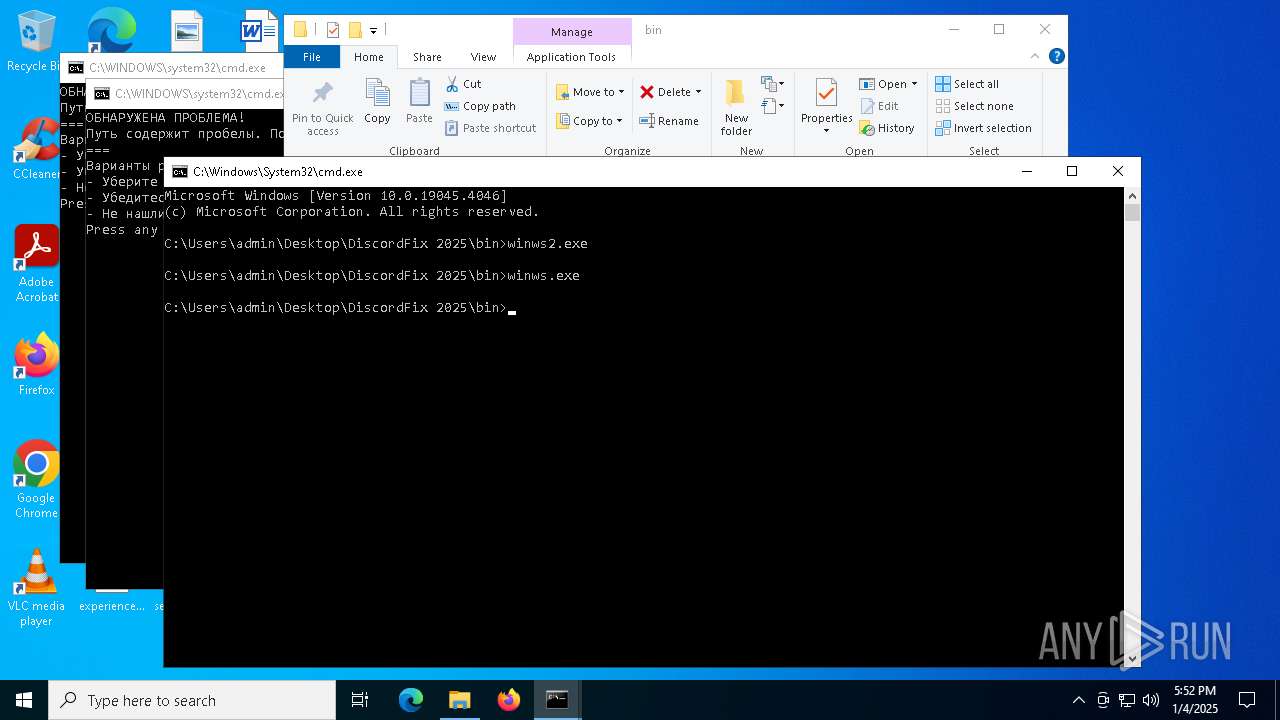
Manual execution by a user
- cmd.exe (PID: 7160)
- cmd.exe (PID: 5920)
- winws2.exe (PID: 4128)
- winws.exe (PID: 3532)
- winws.exe (PID: 3988)
- winws.exe (PID: 6824)
- cmd.exe (PID: 1684)
Checks supported languages
- chcp.com (PID: 6168)
- chcp.com (PID: 828)
- winws2.exe (PID: 4128)
- winws.exe (PID: 3988)
- winws.exe (PID: 6824)
- winws2.exe (PID: 6456)
- winws.exe (PID: 7156)
Reads the computer name
- winws.exe (PID: 3988)
- winws.exe (PID: 6824)
- winws.exe (PID: 7156)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 6468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 981636 |
| UncompressedSize: | 1022005 |
| OperatingSystem: | Win32 |
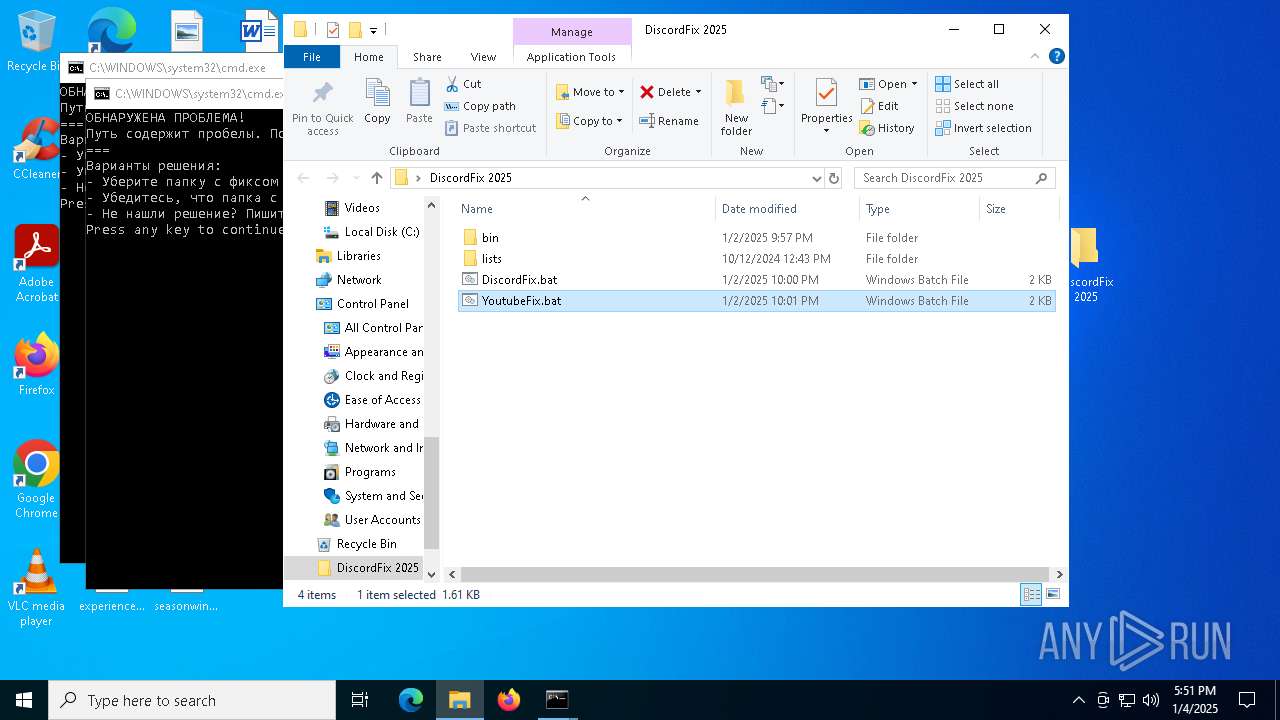
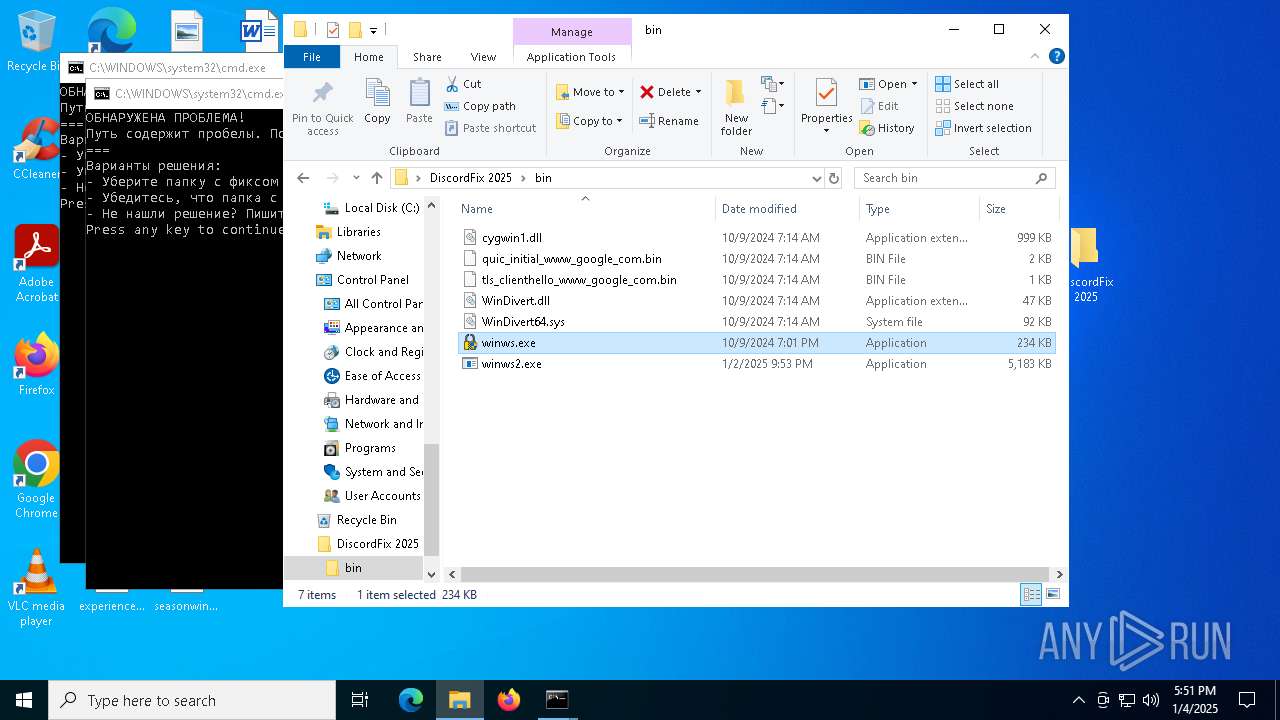
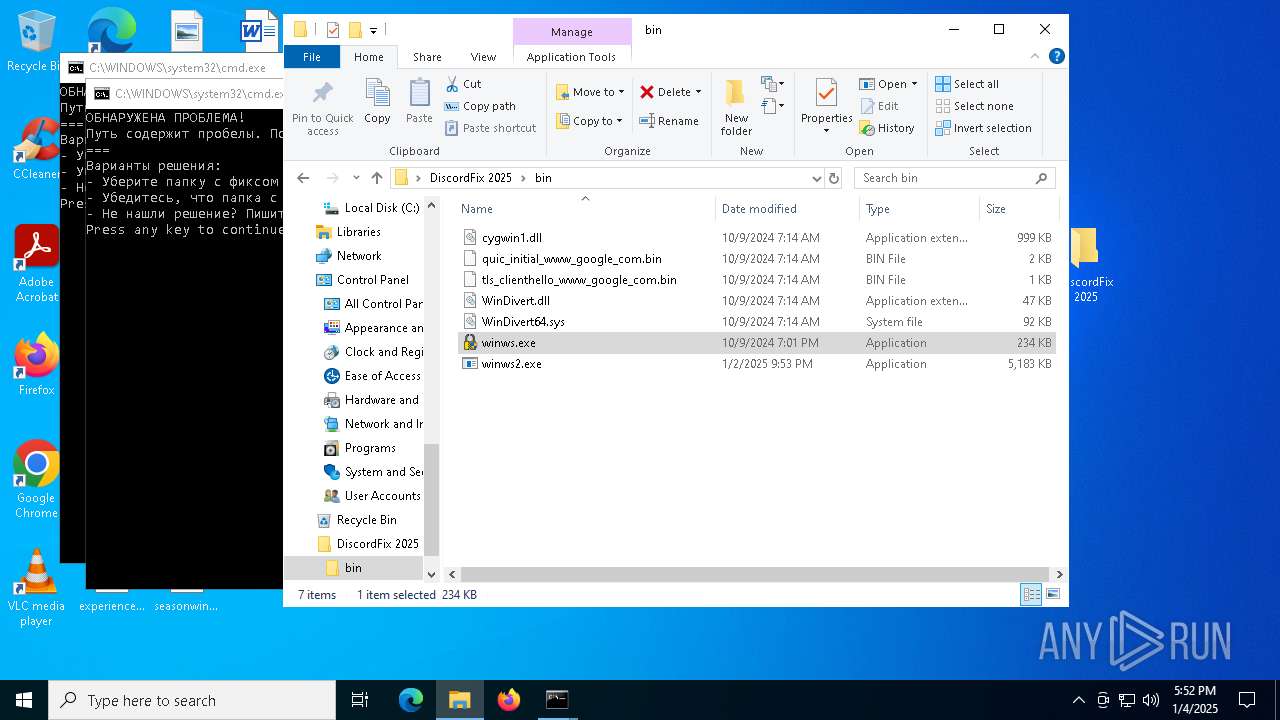
| ArchivedFileName: | DiscordFix 2025/bin/cygwin1.dll |
Total processes
153
Monitored processes
25
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
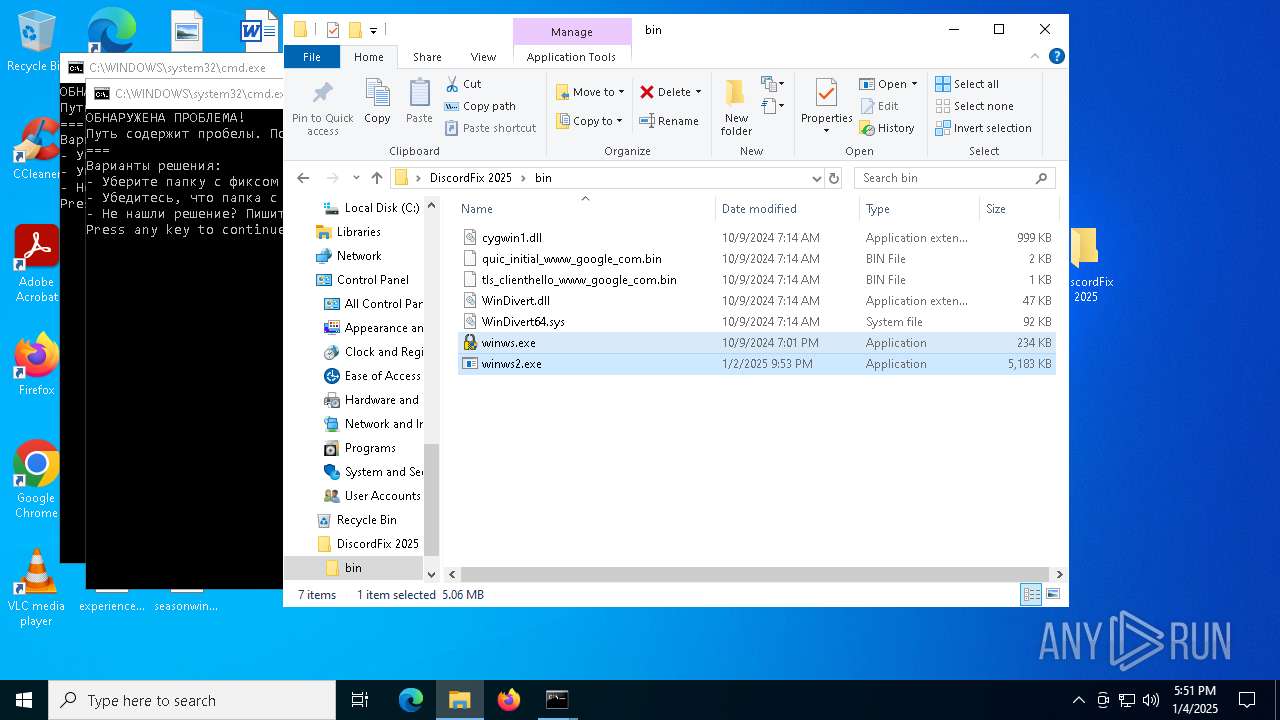
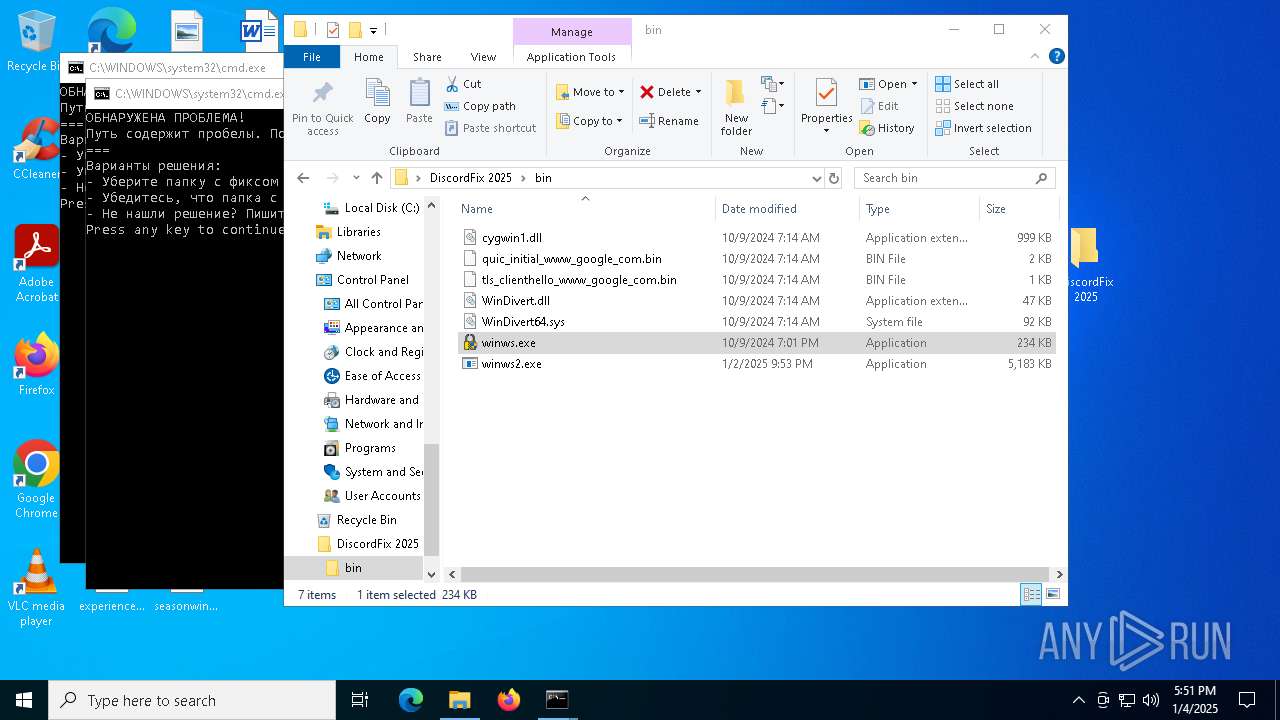
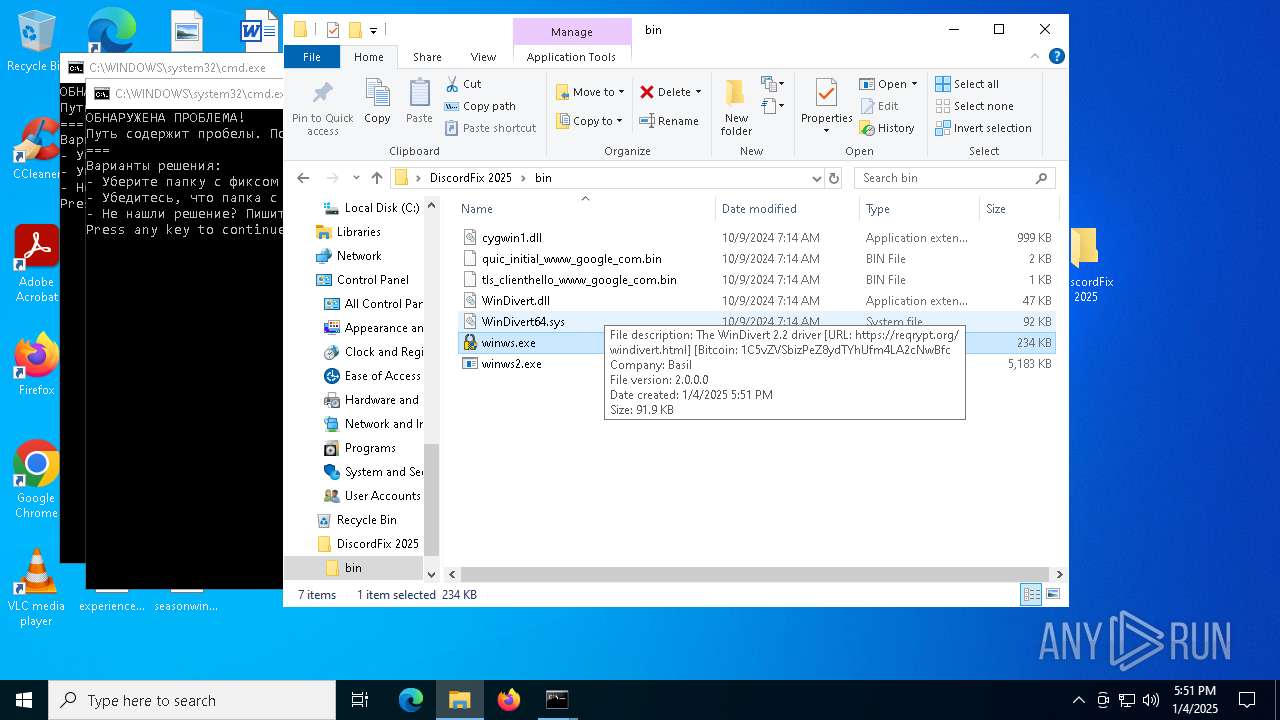
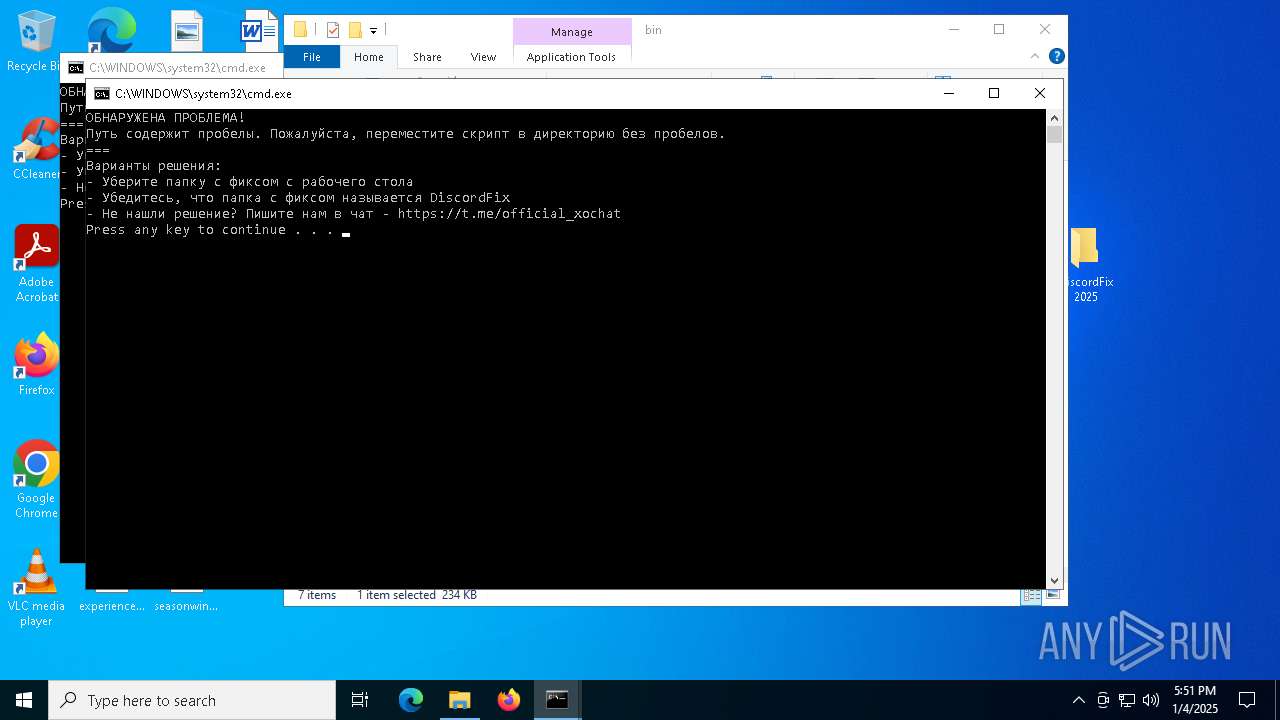
| 3532 | "C:\Users\admin\Desktop\DiscordFix 2025\bin\winws.exe" | C:\Users\admin\Desktop\DiscordFix 2025\bin\winws.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3988 | "C:\Users\admin\Desktop\DiscordFix 2025\bin\winws.exe" | C:\Users\admin\Desktop\DiscordFix 2025\bin\winws.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 4128 | "C:\Users\admin\Desktop\DiscordFix 2025\bin\winws2.exe" | C:\Users\admin\Desktop\DiscordFix 2025\bin\winws2.exe | — | explorer.exe | |||||||||||
User: admin Company: Discord - https://discord.com/ Integrity Level: MEDIUM Description: Discord - https://discord.com/ Exit code: 0 Version: 1,0,9163,0 Modules
| |||||||||||||||
| 4160 | C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe Start-Process "C:\Users\admin\Desktop\DiscordFix 2025\bin\winws2.exe" -Verb runAs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | winws2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 301
Read events
10 280
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DiscordFix 2025.rar | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
5
Suspicious files
3
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
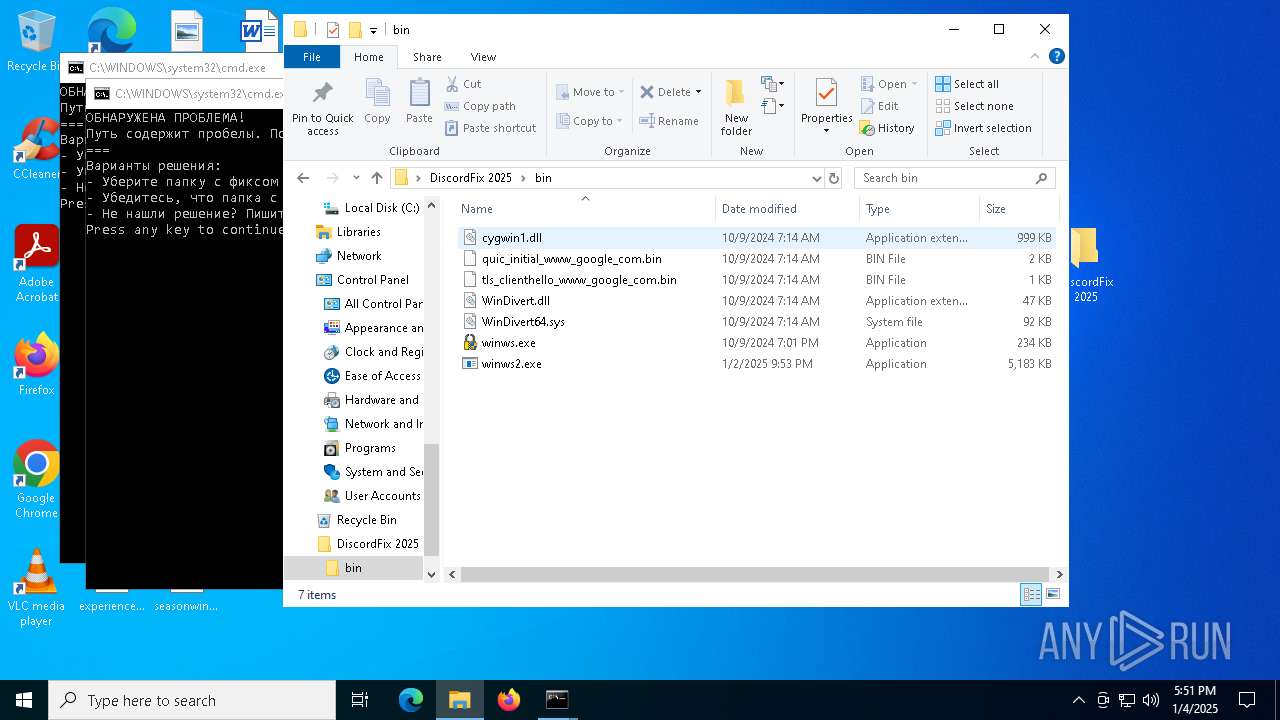
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\bin\winws.exe | executable | |
MD5:8C624E64742BC19447D52F61EDEC52DB | SHA256:13FD7A9C6F7C98239A61A212F69211A0F19159B2E8CDAE8B1EFC57D35CDCD5AD | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\bin\quic_initial_www_google_com.bin | binary | |
MD5:312526D39958D89B1F8AB67789AB985F | SHA256:F4589C57749F956BB30538197A521D7005F8B0A8723B4707E72405E51DDAC50A | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\bin\cygwin1.dll | executable | |
MD5:C50B50303FAE4AFE7248307339A00D13 | SHA256:712C39A069541AFA69CFCBE01B422BD67B4201EEE7E94CC1327D4ED8B4FA2167 | |||
| 6468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ccnezlre.kjt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\bin\tls_clienthello_www_google_com.bin | binary | |
MD5:7AB7AD857C5B8794FBDF1091B494DC94 | SHA256:E5938780152169F720383F80EABB309E9477369B83B5EC40CC137C397F862CDE | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\lists\list-discord.txt | text | |
MD5:D785A5A1158111A9DC32E6335BB192C3 | SHA256:501166C9358E344284B8A2FFC3AA23976397A1D751D1F1A47EA7A57F2BE68655 | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\YoutubeFix.bat | text | |
MD5:8C75FD441D54ED01551B3F816EE12828 | SHA256:3CC2E9A30E53DCC20556CE058551B13D99E312AD377FC37C3A3FCA1CC7F876EF | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\lists\list-ultimate.txt | text | |
MD5:3E907016966B64BC2D14F742F8EE8952 | SHA256:FDA178658096D92F409A390AFD6C1210F2F355BF82A7630A4942FC950F596468 | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\lists\list-youtube.txt | text | |
MD5:9B3D4A71610CC8D5385962D74B6D8424 | SHA256:A145674245BD30C06197234D1BE2104F9FDB161C546A9690E8E9EF3F52BF218A | |||
| 6304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6304.39160\DiscordFix 2025\bin\WinDivert64.sys | executable | |
MD5:89ED5BE7EA83C01D0DE33D3519944AA5 | SHA256:8DA085332782708D8767BCACE5327A6EC7283C17CFB85E40B03CD2323A90DDC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6552 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5244 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2040 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| unknown |