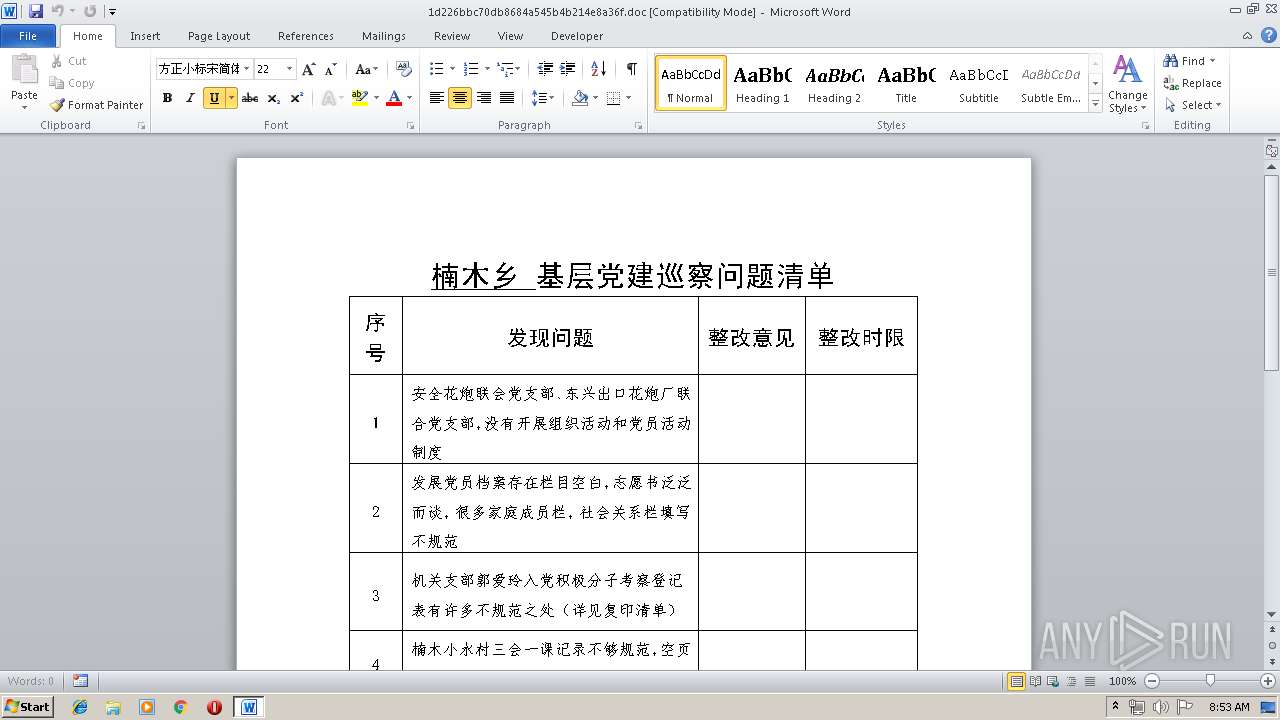
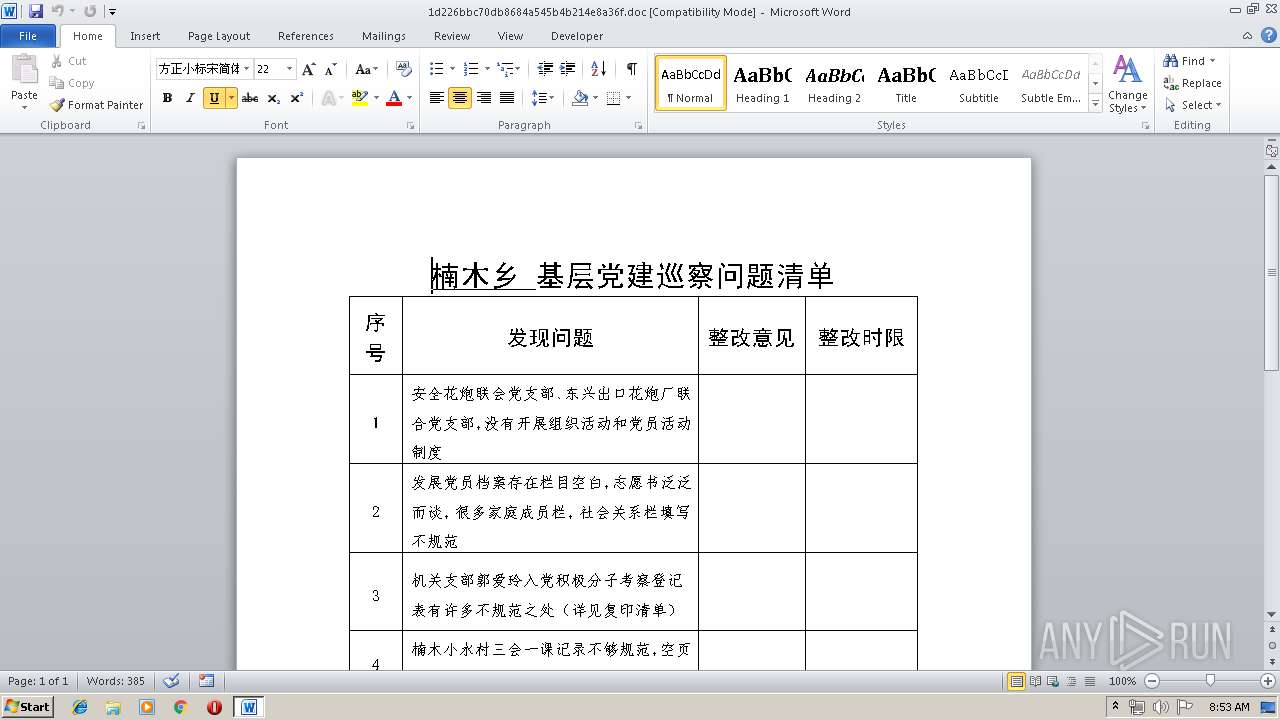
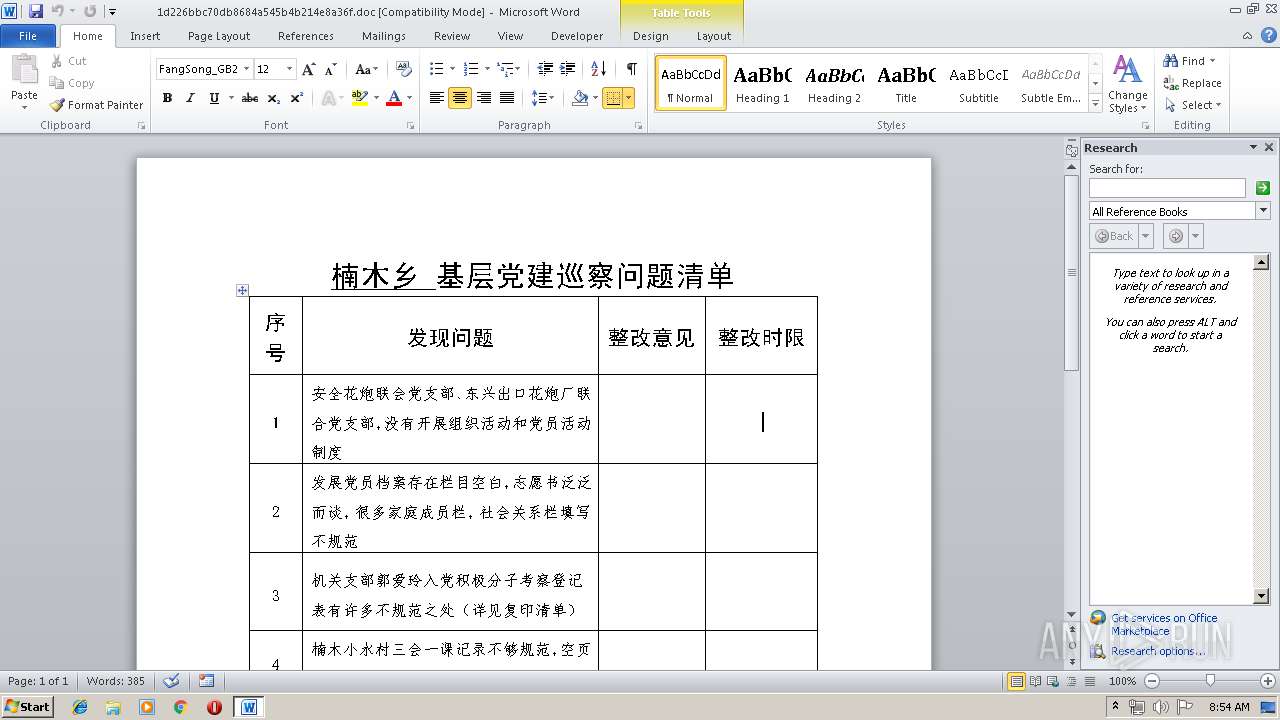
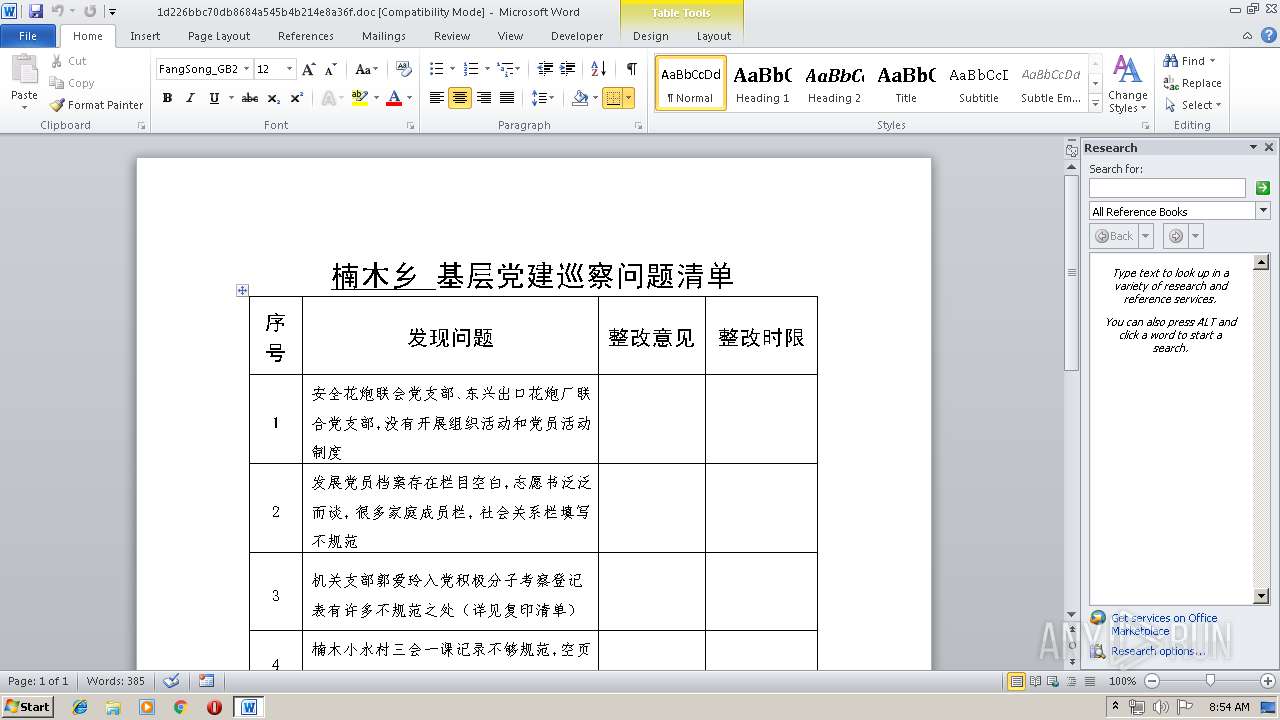
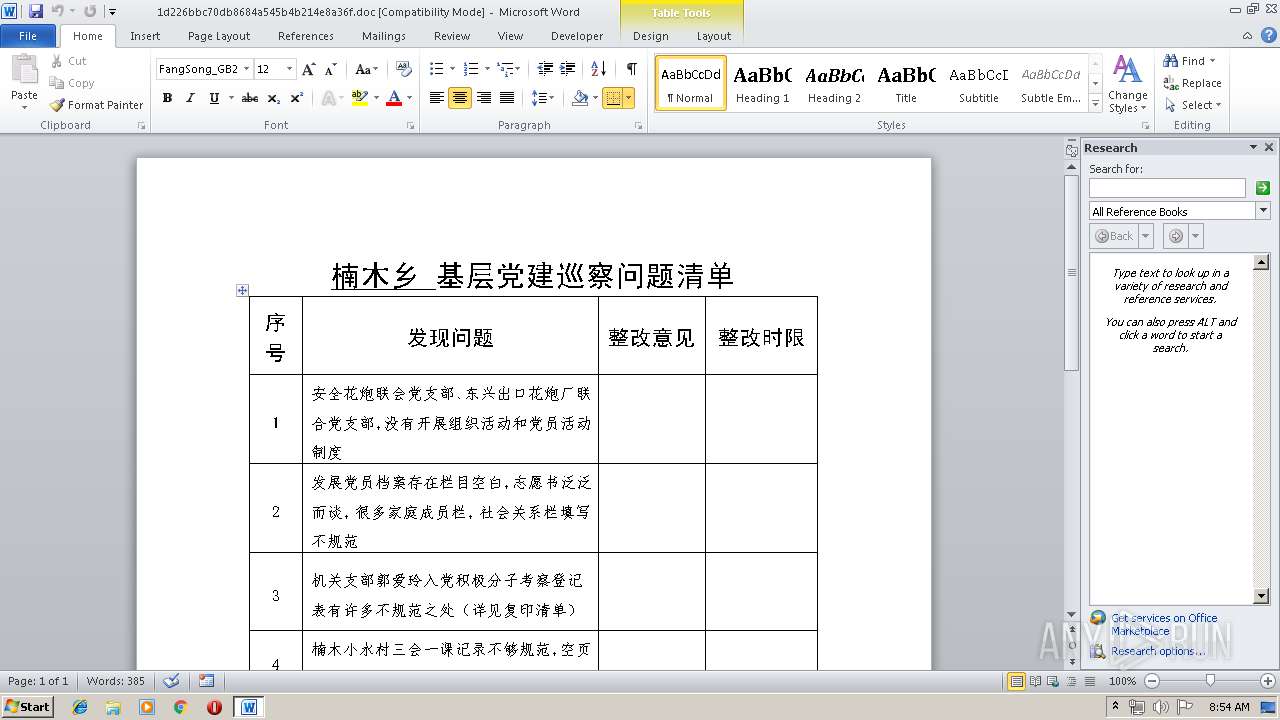
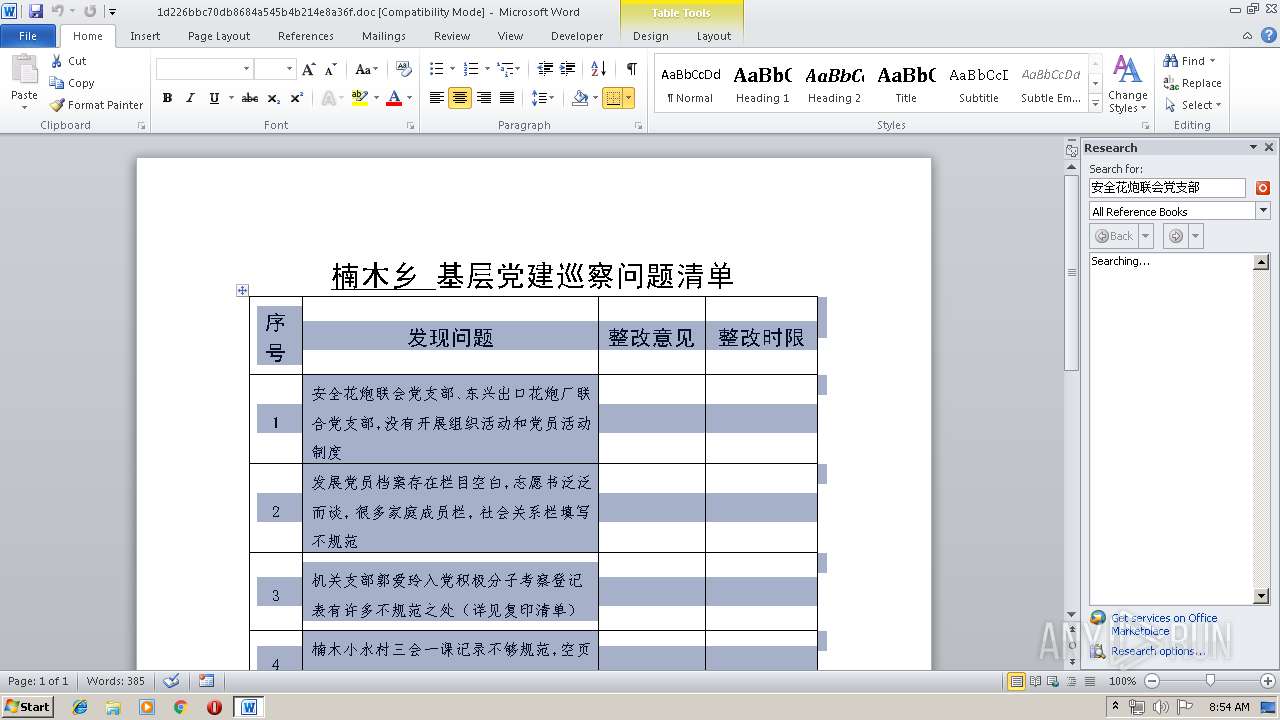
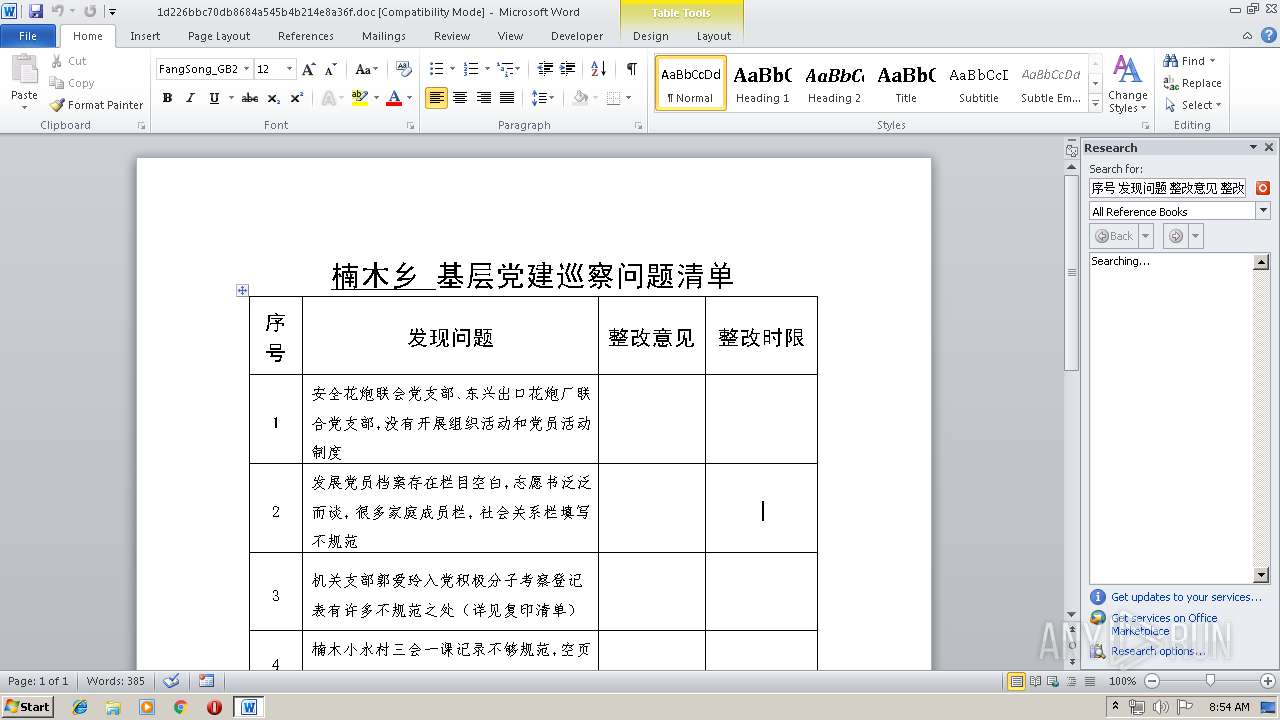
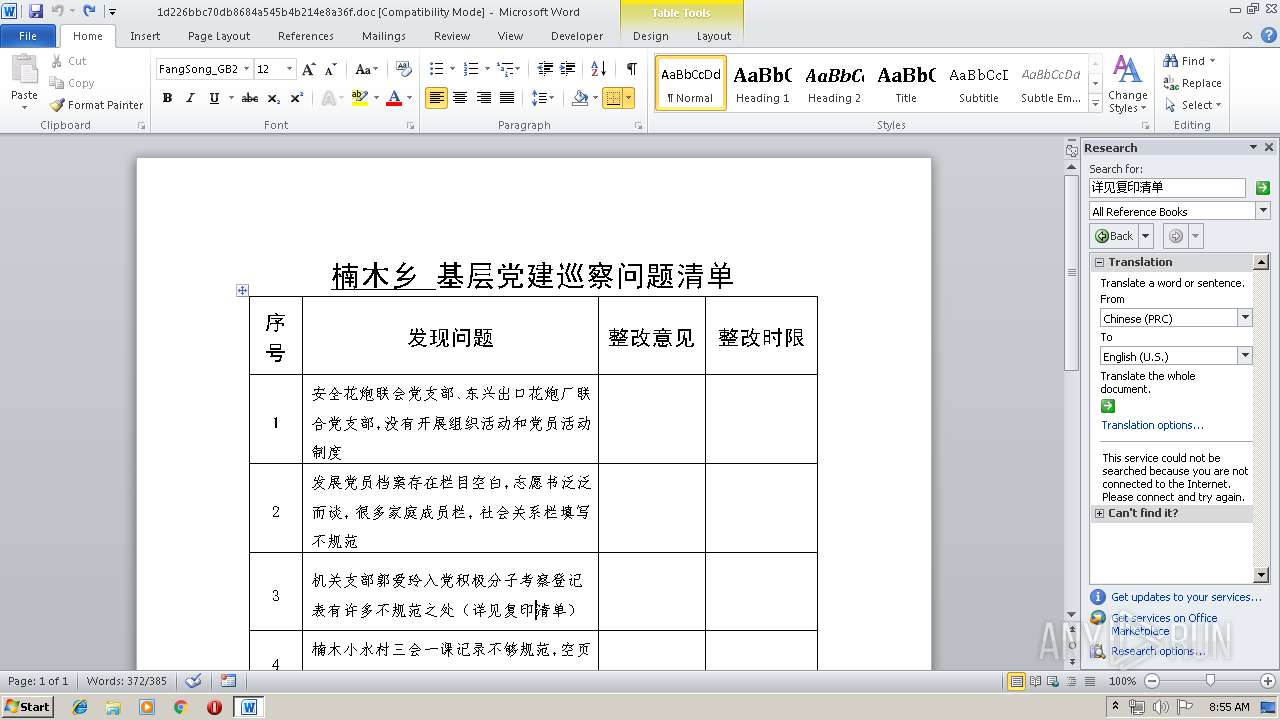
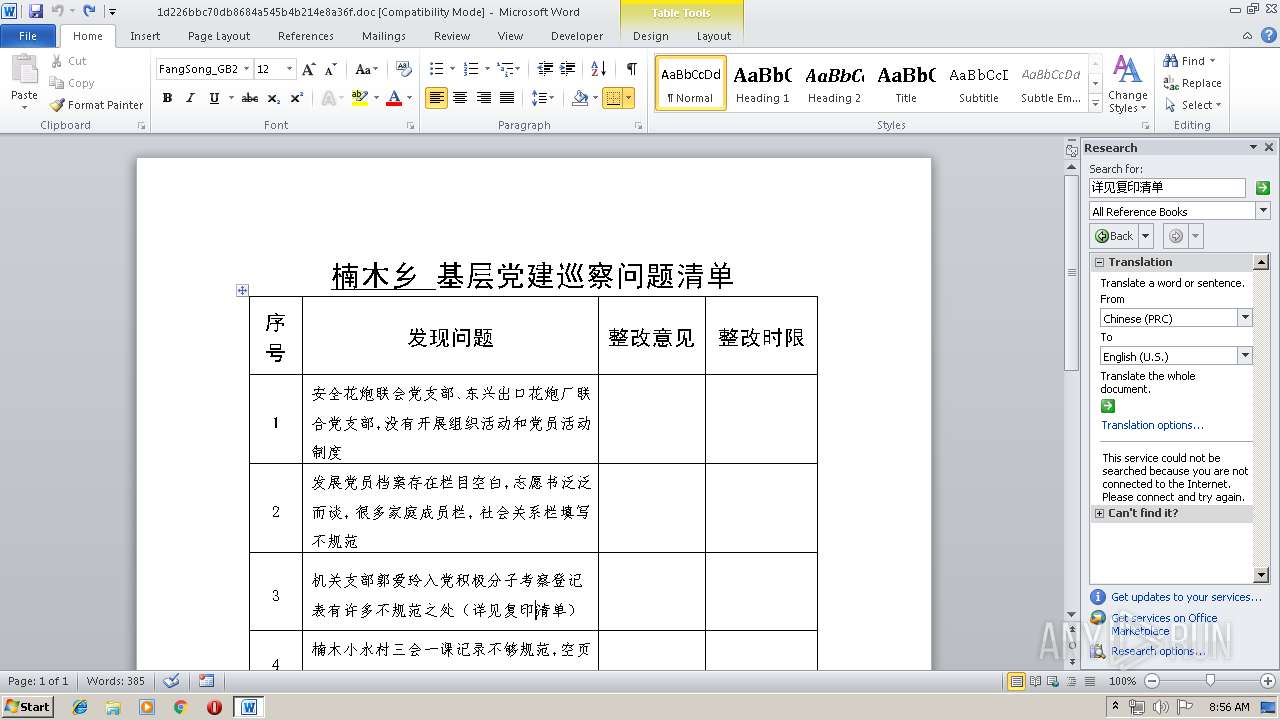
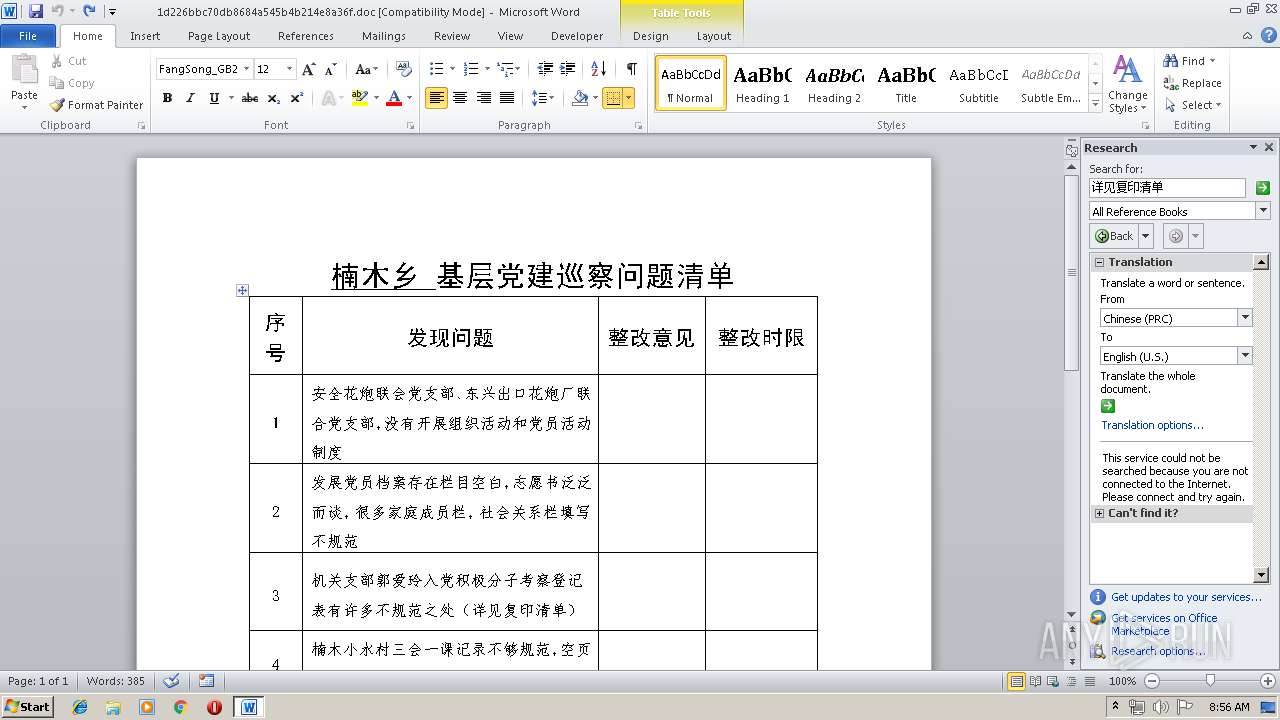
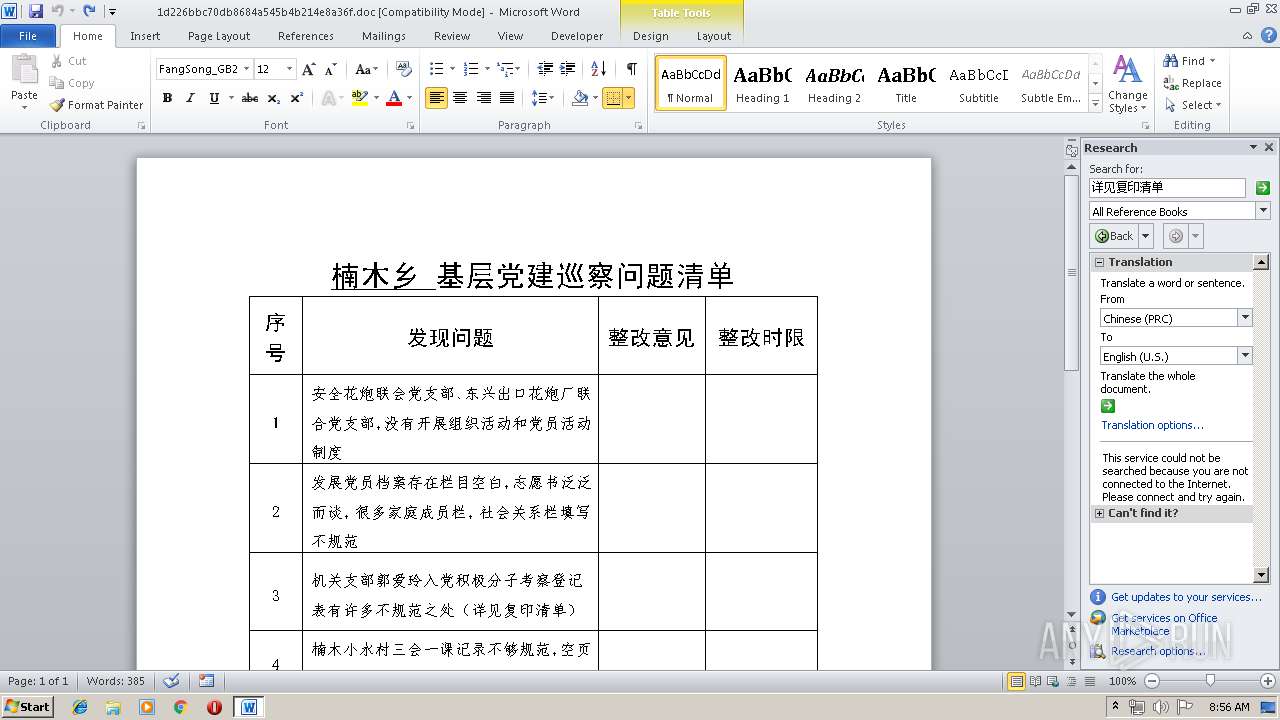
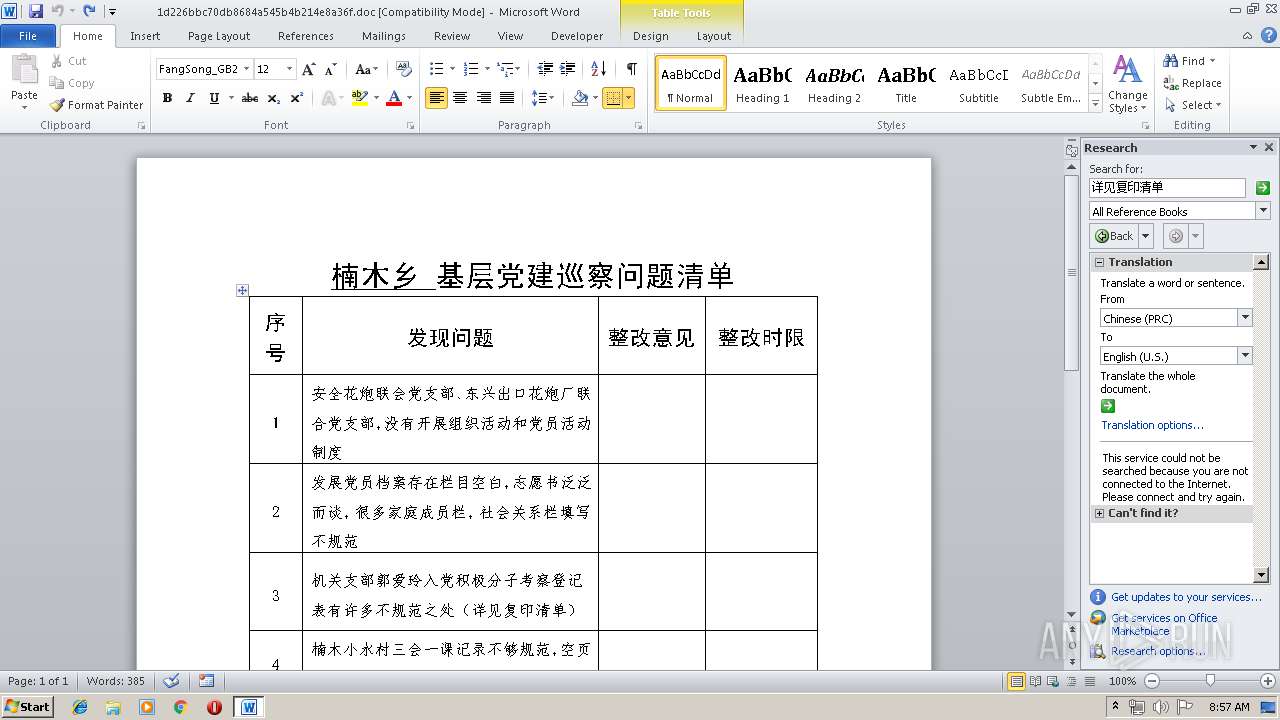
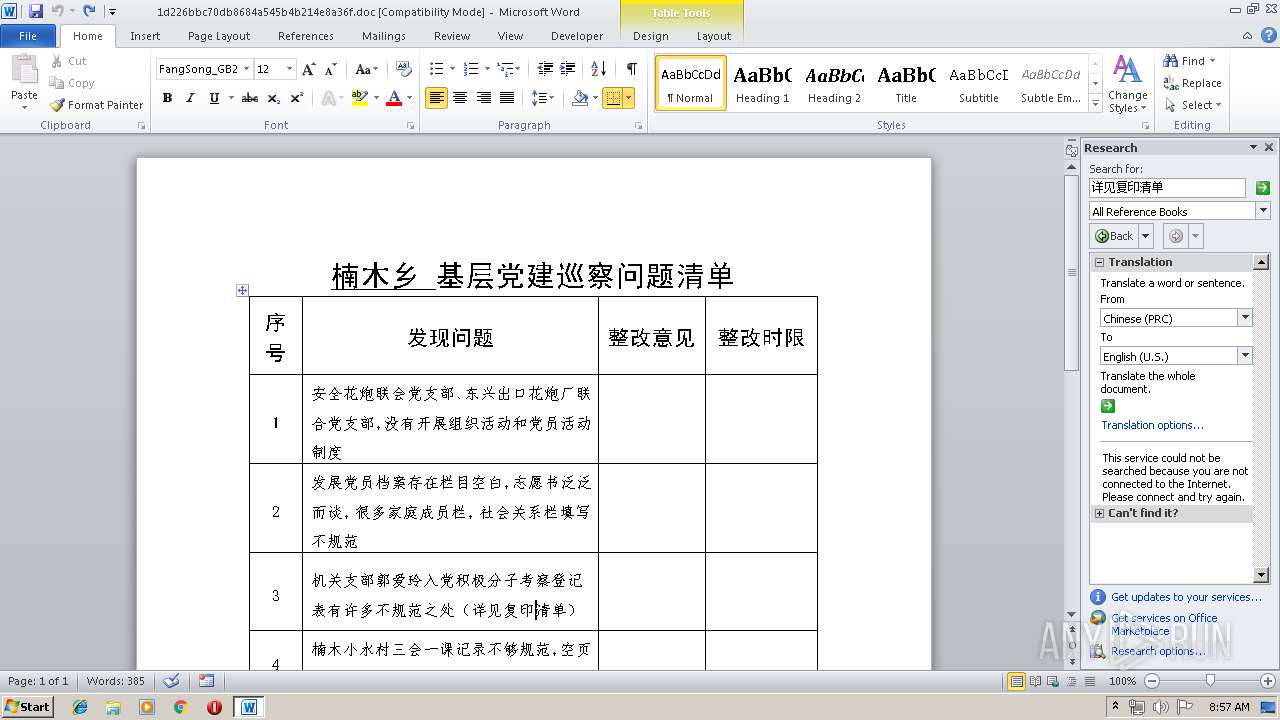
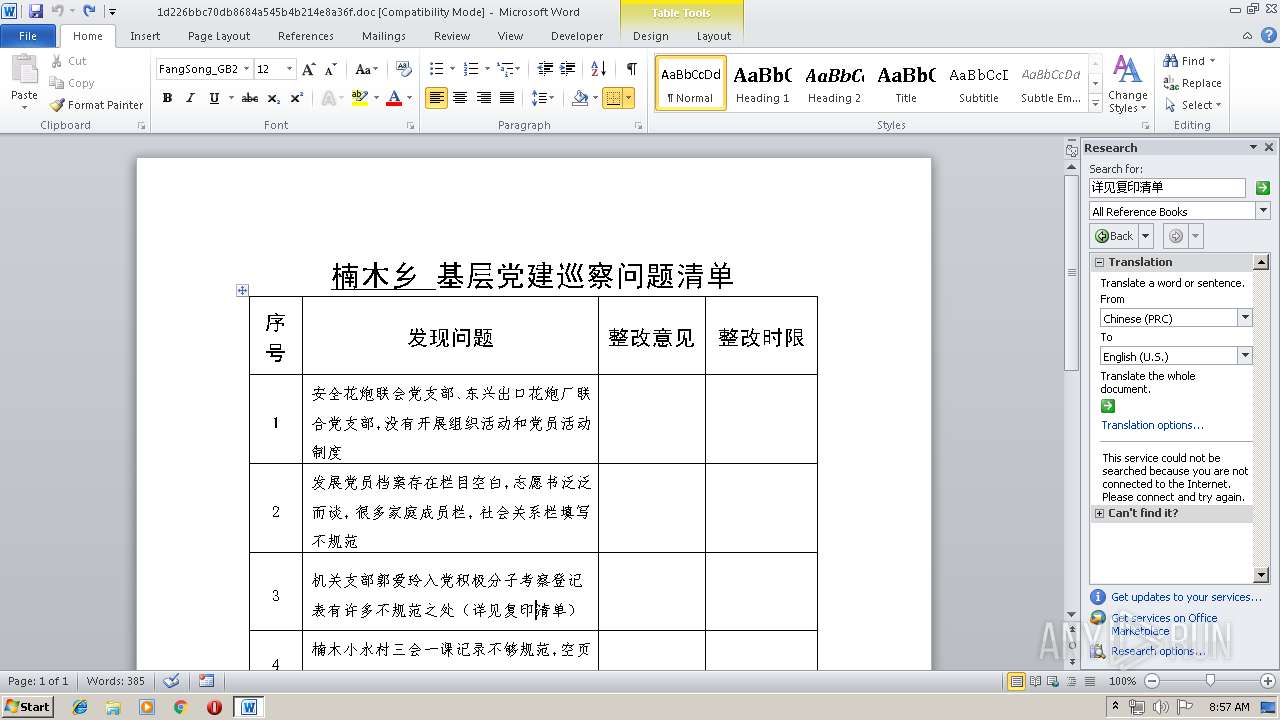
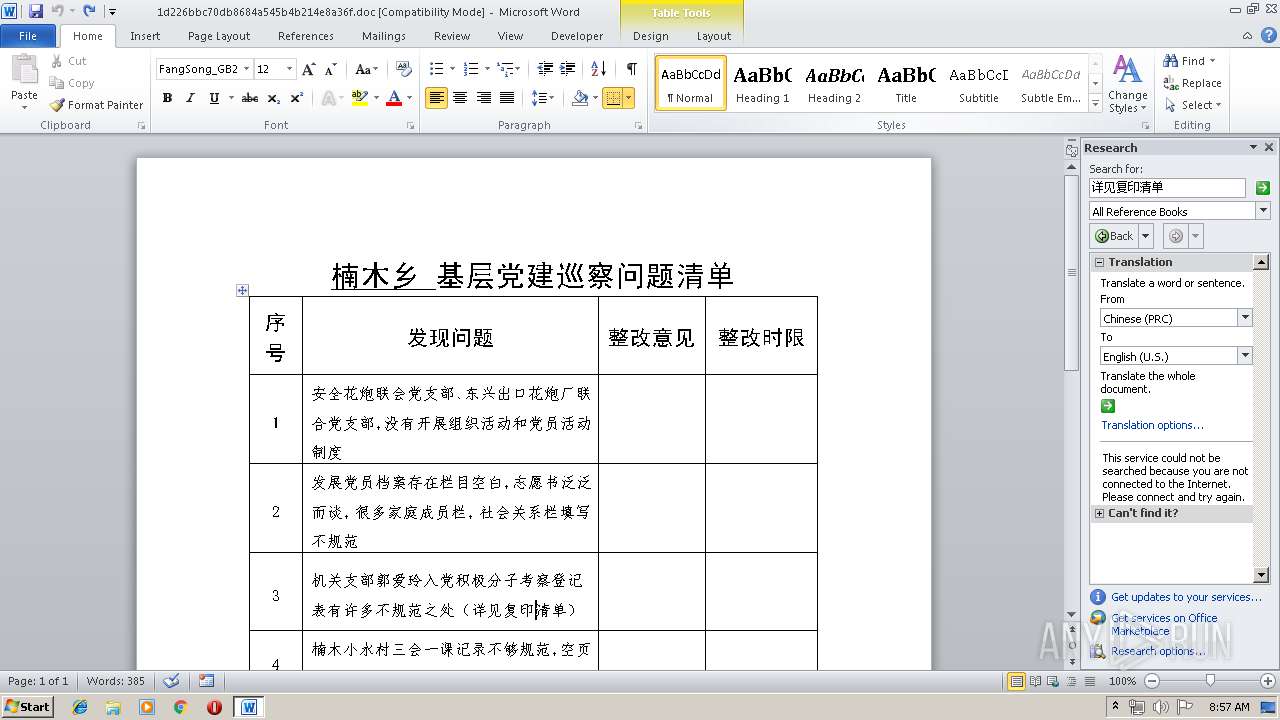
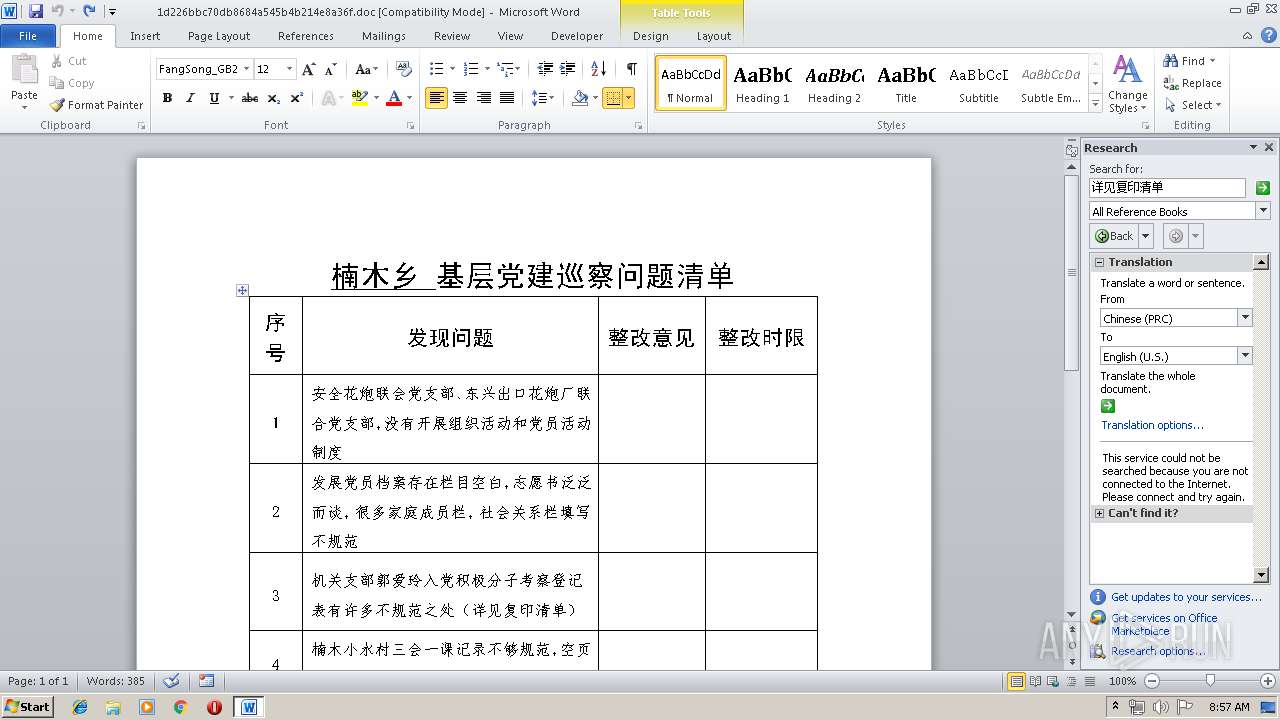
| File name: | 1d226bbc70db8684a545b4b214e8a36f.doc |
| Full analysis: | https://app.any.run/tasks/ae8646a1-ce50-4ac4-a9fd-dc559a33cc07 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 07:53:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 936, Author: Administrator, Template: Normal, Last Saved By: lenovo, Revision Number: 3, Name of Creating Application: Microsoft Office Word, Total Editing Time: 05:00, Last Printed: Mon Dec 10 10:41:00 2018, Create Time/Date: Mon Dec 10 10:42:00 2018, Last Saved Time/Date: Fri Jan 11 02:30:00 2019, Number of Pages: 1, Number of Words: 67, Number of Characters: 386, Security: 0 |
| MD5: | 1D226BBC70DB8684A545B4B214E8A36F |
| SHA1: | 849773545C96311F8A5521A558D2055BF51406A2 |
| SHA256: | 185DC7D7C27F0EE765D76097FD067C4230A2FF36A83DEE3E0FDD82786D743755 |
| SSDEEP: | 12288:/q/xonVVCb7ofbrQXw0jc5be3ZGA3iju9+eOj:MonfCbsnyRpGAyC9+vj |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2360)
Application was injected by another process
- explorer.exe (PID: 2044)
Application was dropped or rewritten from another process
- bk_2BA2.tmp (PID: 1536)
Runs injected code in another process
- bk_2BA2.tmp (PID: 1536)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2360)
Changes the login/logoff helper path in the registry
- bk_2BA2.tmp (PID: 1536)
SUSPICIOUS
Starts application with an unusual extension
- WINWORD.EXE (PID: 2360)
Reads Internet Cache Settings
- explorer.exe (PID: 2044)
Creates files in the user directory
- explorer.exe (PID: 2044)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2360)
- EXCEL.EXE (PID: 1364)
Starts Microsoft Office Application
- explorer.exe (PID: 2044)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2324)
- EXCEL.EXE (PID: 1364)
- WINWORD.EXE (PID: 3516)
- WINWORD.EXE (PID: 2360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Administrator |
| Keywords: | - |
| Template: | Normal |
| LastModifiedBy: | lenovo |
| RevisionNumber: | 3 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 5.0 minutes |
| LastPrinted: | 2018:12:10 10:41:00 |
| CreateDate: | 2018:12:10 10:42:00 |
| ModifyDate: | 2019:01:11 02:30:00 |
| Pages: | 1 |
| Words: | 67 |
| Characters: | 386 |
| Security: | None |
| Company: | Microsoft |
| Lines: | 3 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 452 |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| CodePage: | Windows Simplified Chinese (PRC, Singapore) |
| KSOProductBuildVer: | 2052-10.1.0.7697 |
| CompObjUserTypeLen: | 35 |
| CompObjUserType: | Microsoft Office Word 97-2003 ?ĵ? |
Total processes
36
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /automation -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1536 | C:\Users\admin\AppData\Local\Temp\bk_2BA2.tmp | C:\Users\admin\AppData\Local\Temp\bk_2BA2.tmp | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2044 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /automation -Embedding | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\1d226bbc70db8684a545b4b214e8a36f.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3516 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Automation -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
26 781
Read events
8 753
Write events
18 002
Delete events
26
Modification events
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 8n2 |
Value: 386E320038090000010000000000000000000000 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1318649886 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318650000 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1318650001 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 380900000EFD67013CFBD40100000000 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /p2 |
Value: 2F7032003809000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | /p2 |
Value: 2F7032003809000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2360) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
7
Text files
4
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR22B8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF24E9EB021459BE50.TMP | — | |
MD5:— | SHA256:— | |||
| 2360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF59CC0B7920717CB0.TMP | — | |
MD5:— | SHA256:— | |||
| 2360 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 2324 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR2F6A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\query[1].asmx | — | |
MD5:— | SHA256:— | |||
| 1364 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR8460.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1364 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Excel\XLSTART\06811000 | — | |
MD5:— | SHA256:— | |||
| 1364 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Excel\XLSTART\F6811000 | — | |
MD5:— | SHA256:— | |||
| 1364 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF51999BD543D30DF8.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2360 | WINWORD.EXE | GET | 200 | 52.109.88.8:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | NL | xml | 1.99 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2360 | WINWORD.EXE | 65.55.108.4:443 | ssl.translatoruser.net | Microsoft Corporation | US | whitelisted |
2360 | WINWORD.EXE | 52.109.8.27:443 | rr.office.microsoft.com | Microsoft Corporation | US | whitelisted |
2360 | WINWORD.EXE | 52.109.88.8:80 | office14client.microsoft.com | Microsoft Corporation | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fmtwld.zj.com |
| unknown |
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
ssl.translatoruser.net |
| suspicious |
dns.msftncsi.com |
| shared |
fmtwld.vicp.net |
| unknown |