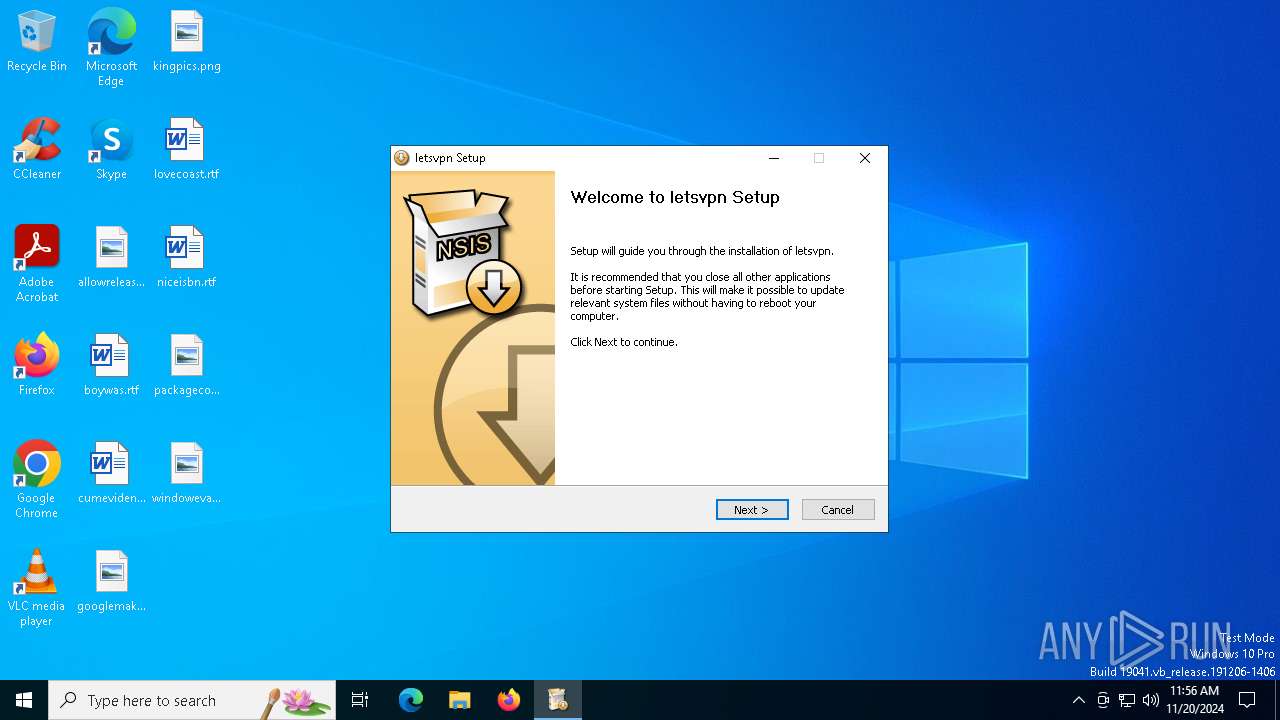
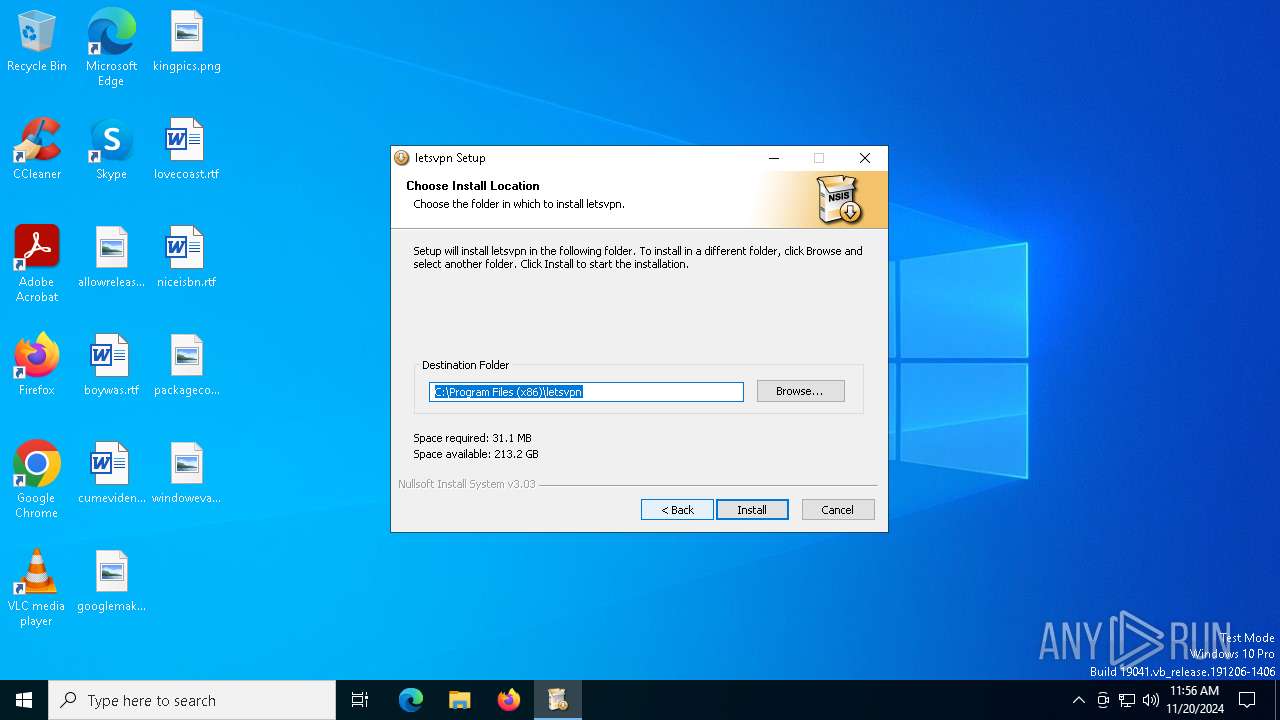
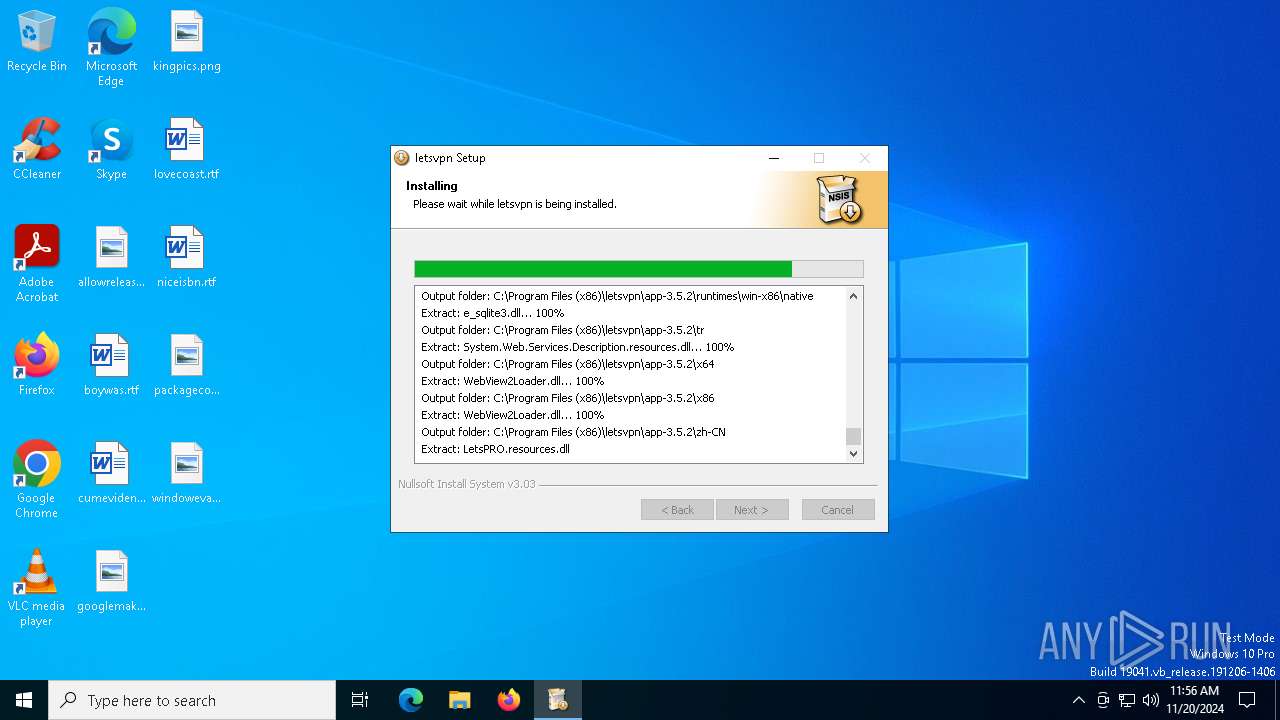
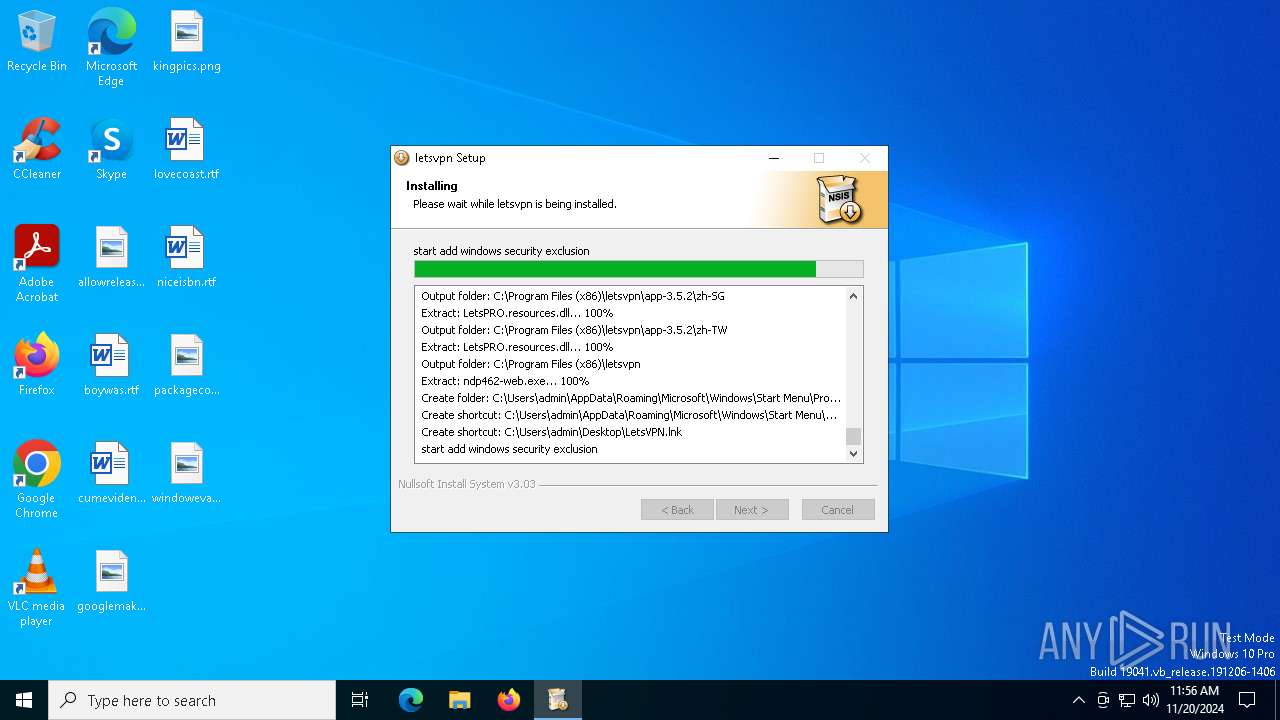
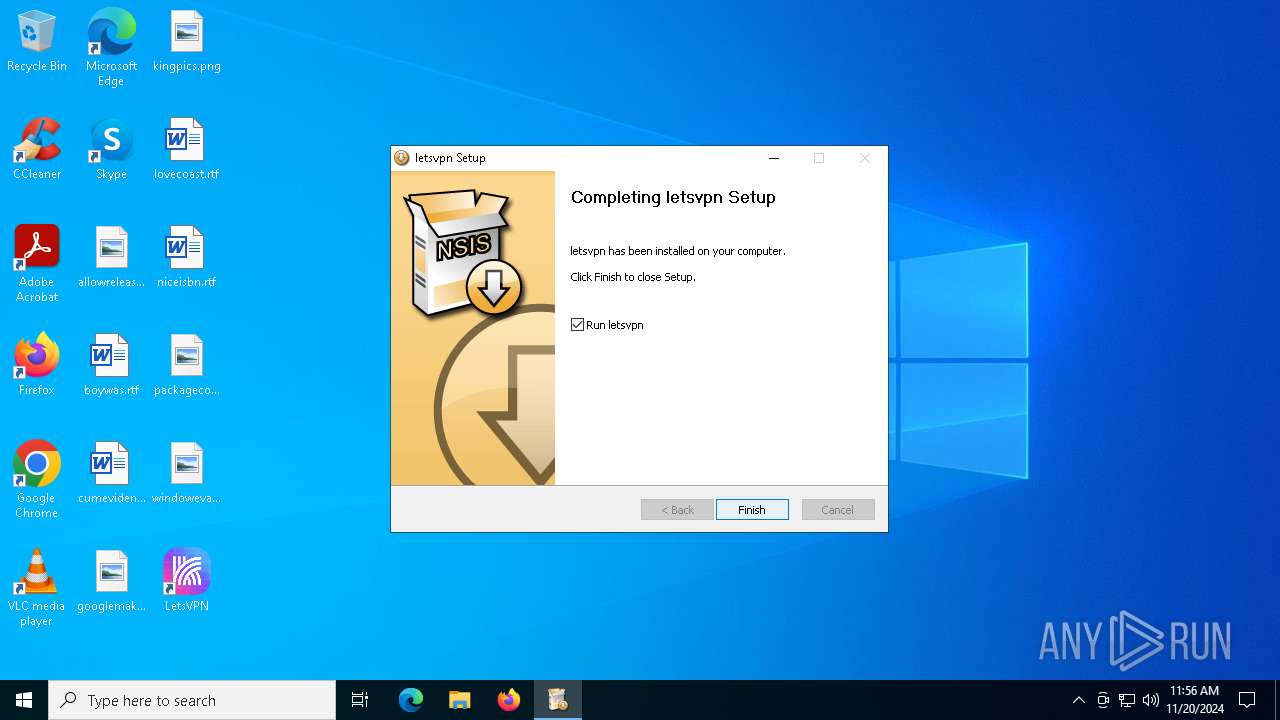
| File name: | letsvpn-latest.exe |
| Full analysis: | https://app.any.run/tasks/836d686c-850c-44f9-9b0e-937f0d57eab9 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2024, 11:56:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | E680B7E43F6FB7DAB7FCD9A07F0B9367 |
| SHA1: | E29C59617F8AAFCDE20E06542510C087EF1892A9 |
| SHA256: | 185B11B4952AA5A8BD4AB83B8FEADE5224AD5823F002FF2381F74E184B9F0A25 |
| SSDEEP: | 196608:+VR8YtUe4JmHP7zI58mb3YxRog8AtpH3H+2:+VftUVJm/Ik3og8MHXl |
MALICIOUS
Changes powershell execution policy (Bypass)
- letsvpn-latest.exe (PID: 5856)
Bypass execution policy to execute commands
- powershell.exe (PID: 3928)
- powershell.exe (PID: 1224)
SUSPICIOUS
Executable content was dropped or overwritten
- letsvpn-latest.exe (PID: 5856)
- tapinstall.exe (PID: 6448)
- drvinst.exe (PID: 6568)
- drvinst.exe (PID: 6604)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-latest.exe (PID: 5856)
The process creates files with name similar to system file names
- letsvpn-latest.exe (PID: 5856)
Starts POWERSHELL.EXE for commands execution
- letsvpn-latest.exe (PID: 5856)
Checks processor architecture
- powershell.exe (PID: 3928)
Manipulates environment variables
- powershell.exe (PID: 3928)
Drops a system driver (possible attempt to evade defenses)
- letsvpn-latest.exe (PID: 5856)
- tapinstall.exe (PID: 6448)
- drvinst.exe (PID: 6568)
- drvinst.exe (PID: 6604)
Process drops legitimate windows executable
- letsvpn-latest.exe (PID: 5856)
- LetsPRO.exe (PID: 6240)
The process executes Powershell scripts
- letsvpn-latest.exe (PID: 5856)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6660)
- cmd.exe (PID: 6872)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 6984)
Starts CMD.EXE for commands execution
- letsvpn-latest.exe (PID: 5856)
- LetsPRO.exe (PID: 6240)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 6884)
Executes as Windows Service
- WmiApSrv.exe (PID: 6788)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6904)
Process uses ARP to discover network configuration
- cmd.exe (PID: 7076)
Suspicious use of NETSH.EXE
- LetsPRO.exe (PID: 6240)
INFO
Checks supported languages
- letsvpn-latest.exe (PID: 5856)
Create files in a temporary directory
- letsvpn-latest.exe (PID: 5856)
Reads the computer name
- letsvpn-latest.exe (PID: 5856)
Creates files in the program directory
- letsvpn-latest.exe (PID: 5856)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 7060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 03:57:48+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
166
Monitored processes
40
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe" | C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | powershell -inputformat none -ExecutionPolicy Bypass -File "C:\Program Files (x86)\letsvpn\AddWindowsSecurityExclusion.ps1" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3928 | powershell.exe -inputformat none -ExecutionPolicy Bypass -Command "If ($env:PROCESSOR_ARCHITEW6432) { $env:PROCESSOR_ARCHITEW6432 } Else { $env:PROCESSOR_ARCHITECTURE }" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | C:\WINDOWS\System32\netsh interface ipv4 set dnsservers \"LetsTAP\" source=dhcp validate=no | C:\Windows\SysWOW64\netsh.exe | — | LetsPRO.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5680 | "C:\Program Files (x86)\letsvpn\LetsPRO.exe" | C:\Program Files (x86)\letsvpn\LetsPRO.exe | — | letsvpn-latest.exe | |||||||||||
User: admin Integrity Level: HIGH Description: LetsVPN Exit code: 0 Version: 3.5.2 Modules
| |||||||||||||||
| 5856 | "C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe" | C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5936 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
19 606
Read events
19 531
Write events
60
Delete events
15
Modification events
| (PID) Process: | (6448) tapinstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.dev.log |
Value: 4096 | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\tap0901 |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Setup\PnpLockdownFiles\%SystemRoot%/System32/drivers/tap0901.sys |
| Operation: | write | Name: | Owners |
Value: oem1.inf | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Configuration |
Value: tap0901.ndi | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Manufacturer |
Value: %provider% | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Descriptors\tap0901 |
| Operation: | write | Name: | Description |
Value: %devicedescription% | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | Service |
Value: tap0901 | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi |
| Operation: | write | Name: | ConfigScope |
Value: 5 | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi\Driver\Ndi |
| Operation: | write | Name: | Service |
Value: tap0901 | |||
| (PID) Process: | (6604) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\DRIVERS\DriverDatabase\DriverPackages\oemvista.inf_amd64_662fd96dfdced4ae\Configurations\tap0901.ndi\Driver\Ndi\Interfaces |
| Operation: | write | Name: | UpperRange |
Value: ndis5 | |||
Executable files
221
Suspicious files
28
Text files
23
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5856 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nsx9B52.tmp\System.dll | executable | |
MD5:75ED96254FBF894E42058062B4B4F0D1 | SHA256:A632D74332B3F08F834C732A103DAFEB09A540823A2217CA7F49159755E8F1D7 | |||
| 3928 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:8B46660FDE91A9F4DB735DD0A82E5263 | SHA256:CA07628A7D5289D040B31DE422DD237A5B3DE9179740F39BFF573A7EC019FDF5 | |||
| 3928 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bpo5crg0.mk3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3928 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i3nbuedt.oyu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5856 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nsx9B52.tmp\modern-wizard.bmp | image | |
MD5:7F8E1969B0874C8FB9AB44FC36575380 | SHA256:076221B4527FF13C3E1557ABBBD48B0CB8E5F7D724C6B9171C6AADADB80561DD | |||
| 5856 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nsx9B52.tmp\modern-header.bmp | image | |
MD5:5ACF495828FEAE7F85E006B7774AF497 | SHA256:6CFEBB59F0BA1B9F1E8D7AA6387F223A468EB2FF74A9ED3C3F4BB688C2B6455E | |||
| 5856 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nsx9B52.tmp\nsExec.dll | executable | |
MD5:3D366250FCF8B755FCE575C75F8C79E4 | SHA256:8BDD996AE4778C6F829E2BCB651C55EFC9EC37EEEA17D259E013B39528DDDBB6 | |||
| 5856 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.5.2\DeltaCompressionDotNet.MsDelta.dll | executable | |
MD5:6EB5A461CBA6957BE4E53D8408D57809 | SHA256:696F6C221387E8FB346C318456E63850BEDD416645958766E6AE32013C4F7BC2 | |||
| 5856 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.5.2\DeltaCompressionDotNet.PatchApi.dll | executable | |
MD5:7DAC119CD44D302EA7B56BFE42B29C38 | SHA256:F351B18C751023737AF45E5067503207023079C5260B9BB8173BF611F4CDA1A3 | |||
| 5856 | letsvpn-latest.exe | C:\Program Files (x86)\letsvpn\app-3.5.2\CommunityToolkit.Mvvm.dll | executable | |
MD5:9F710A9615E03883AA6B3AF05E03037D | SHA256:CDB8C60FFFDEE7E5FC5231BBC673D263C97E09742E050F939AB73AC756BA0285 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
33
DNS requests
31
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5732 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 101 | 52.76.189.10:80 | http://ws-ap1.pusher.com/app/4fc436ef36f4026102d7?protocol=5&client=pusher-dotnet-client&version=1.1.2 | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4932 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5660 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4932 | svchost.exe | 2.16.164.113:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4932 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.171:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |