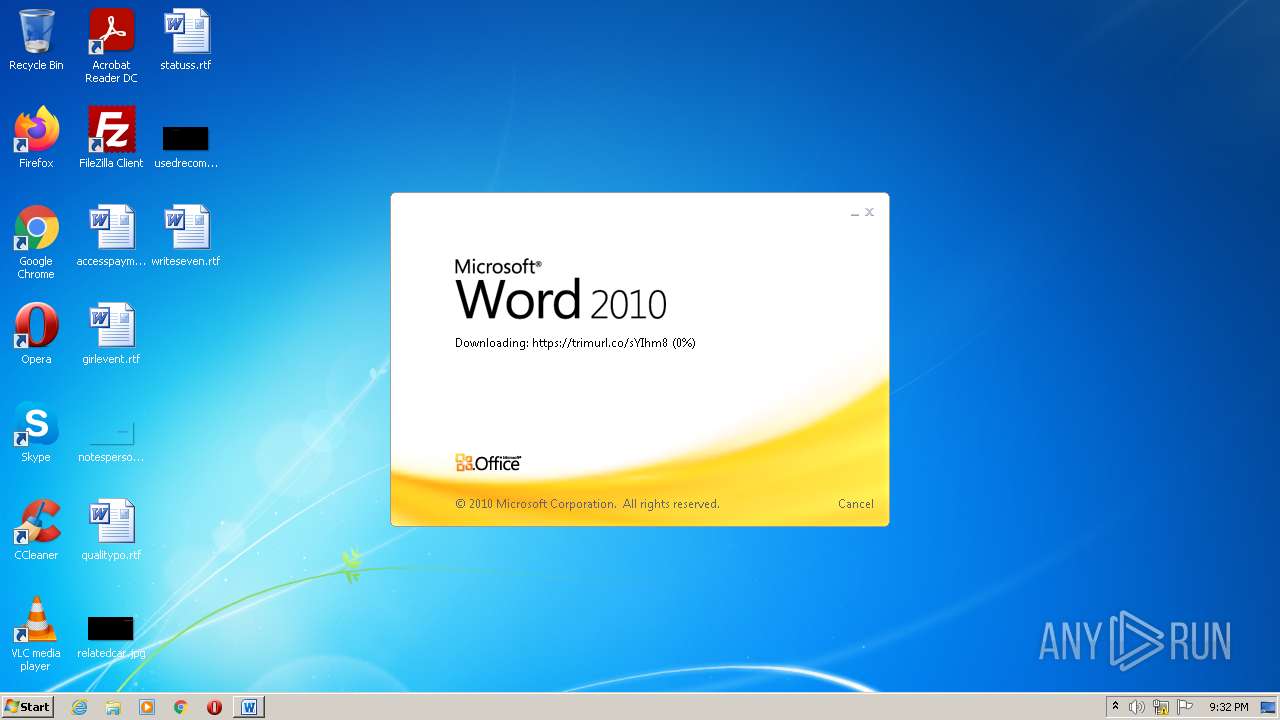
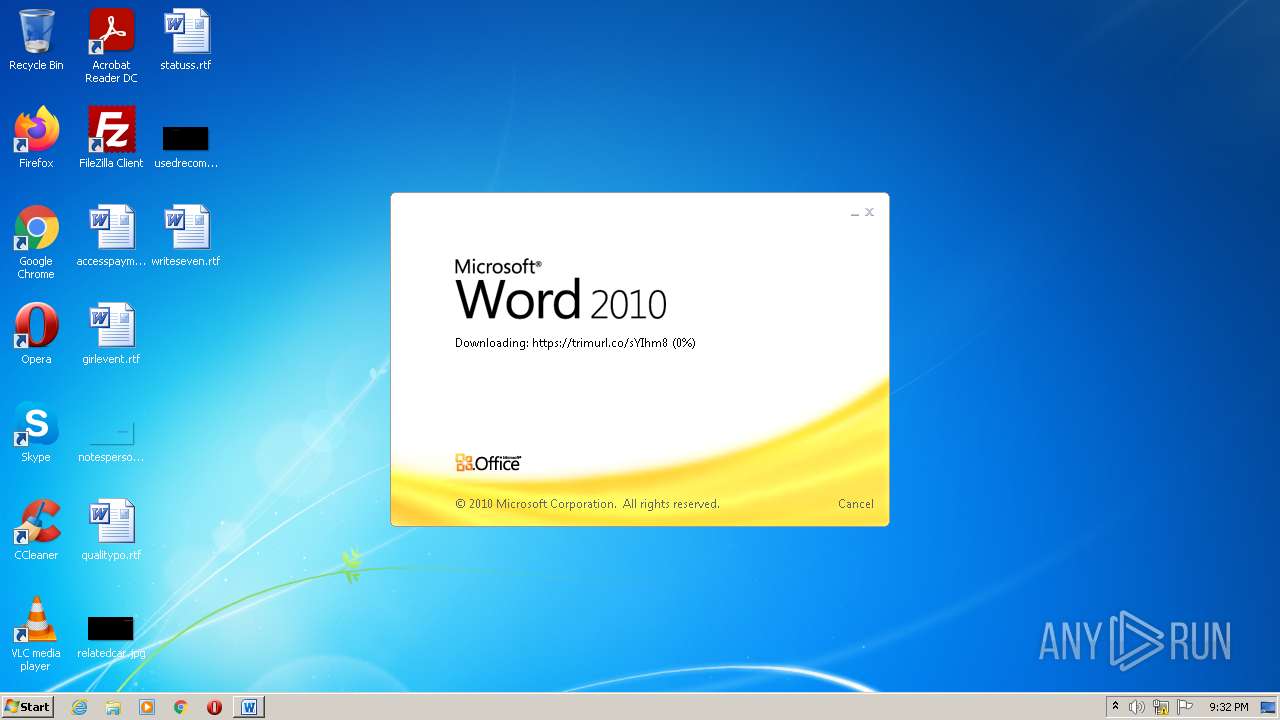
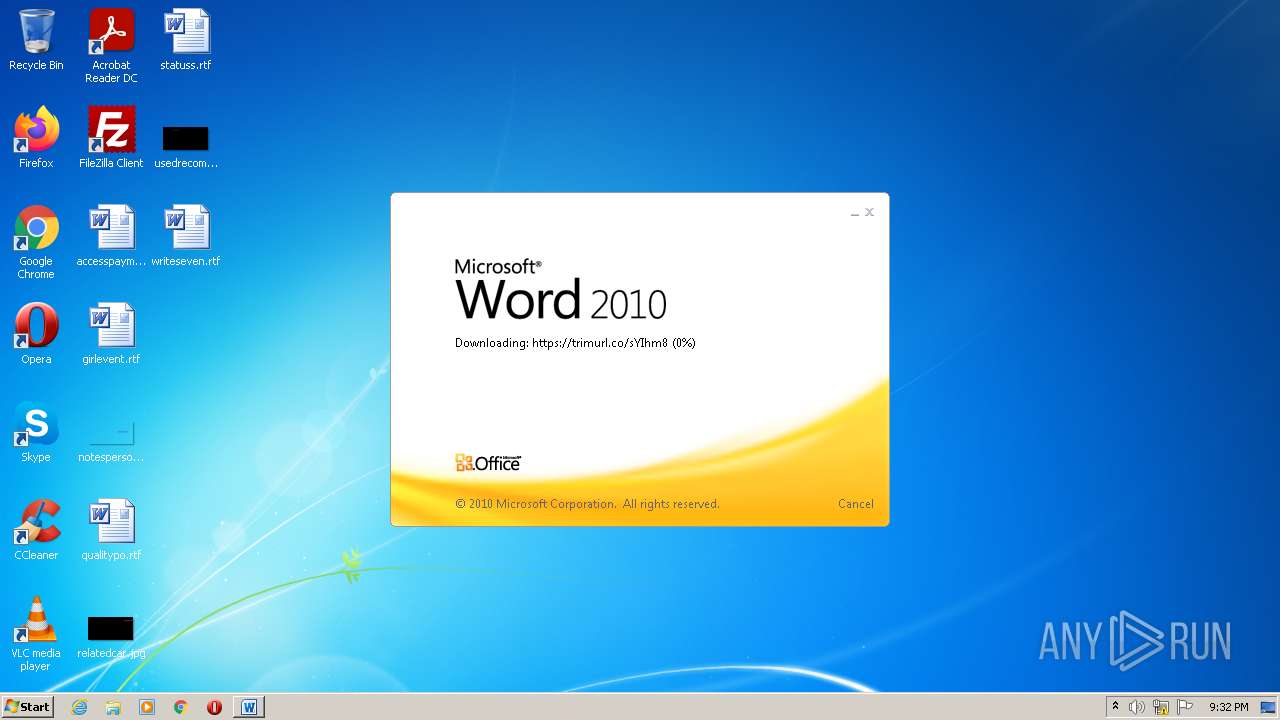
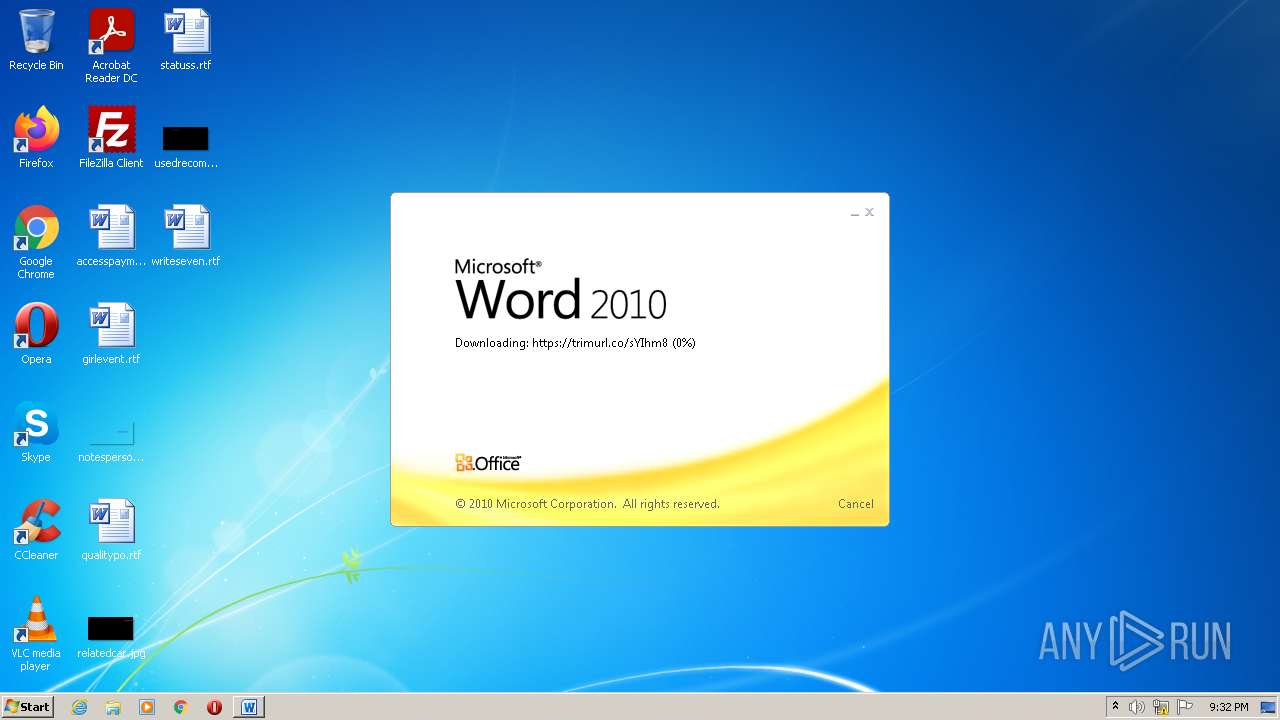
| File name: | 51dd25a5.docx |
| Full analysis: | https://app.any.run/tasks/a90dbfed-d572-483d-80d5-bfaabf2efc91 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 20:32:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 671CC6C3F279ED83BC75325626BFFA05 |
| SHA1: | 8C2F3A8180DB828A7D6EA302C12DB7094DFEB86A |
| SHA256: | 183AD1907F32FE5E280A6B25BCD4E177C51A3D0003A40EEF4823339907570EBB |
| SSDEEP: | 192:ScIMmtPpAAtG/bYRK5topOo7zlYFRV3Lt:SPXeZ5aOo7zlYFRx5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- WINWORD.EXE (PID: 1420)
Reads the computer name
- WINWORD.EXE (PID: 1420)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
XMP
| Creator: | HP 15 |
|---|
XML
| ModifyDate: | 2022:08:03 18:15:00Z |
|---|---|
| CreateDate: | 2018:03:07 09:39:00Z |
| RevisionNumber: | 1 |
| LastModifiedBy: | 91974 |
| AppVersion: | 12 |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| CharactersWithSpaces: | 5 |
| LinksUpToDate: | No |
| Company: | Grizli777 |
| ScaleCrop: | No |
| Paragraphs: | 1 |
| Lines: | 1 |
| DocSecurity: | None |
| Application: | Microsoft Office Word |
| Characters: | 5 |
| Words: | - |
| Pages: | 1 |
| TotalEditTime: | - |
| Template: | Normal.dotm |
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1312 |
| ZipCompressedSize: | 358 |
| ZipCRC: | 0x3795fcdd |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
38
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1420 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\51dd25a5.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 058
Read events
995
Write events
61
Delete events
2
Modification events
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | $29 |
Value: 243239008C050000010000000000000000000000 | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1420) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
8
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9674.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{E479647D-398F-4C24-9456-20EBD2349508}.FSD | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{37FA45F1-CFCD-452D-A709-02F76C16B295} | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$dd25a5.docx | pgc | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{F1EFC4A0-2A72-4DF0-A969-32C6FFEF48CA}.FSD | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{EEE7300E-AFE9-49C4-8DB2-E8E95E360330} | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 1420 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
1
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
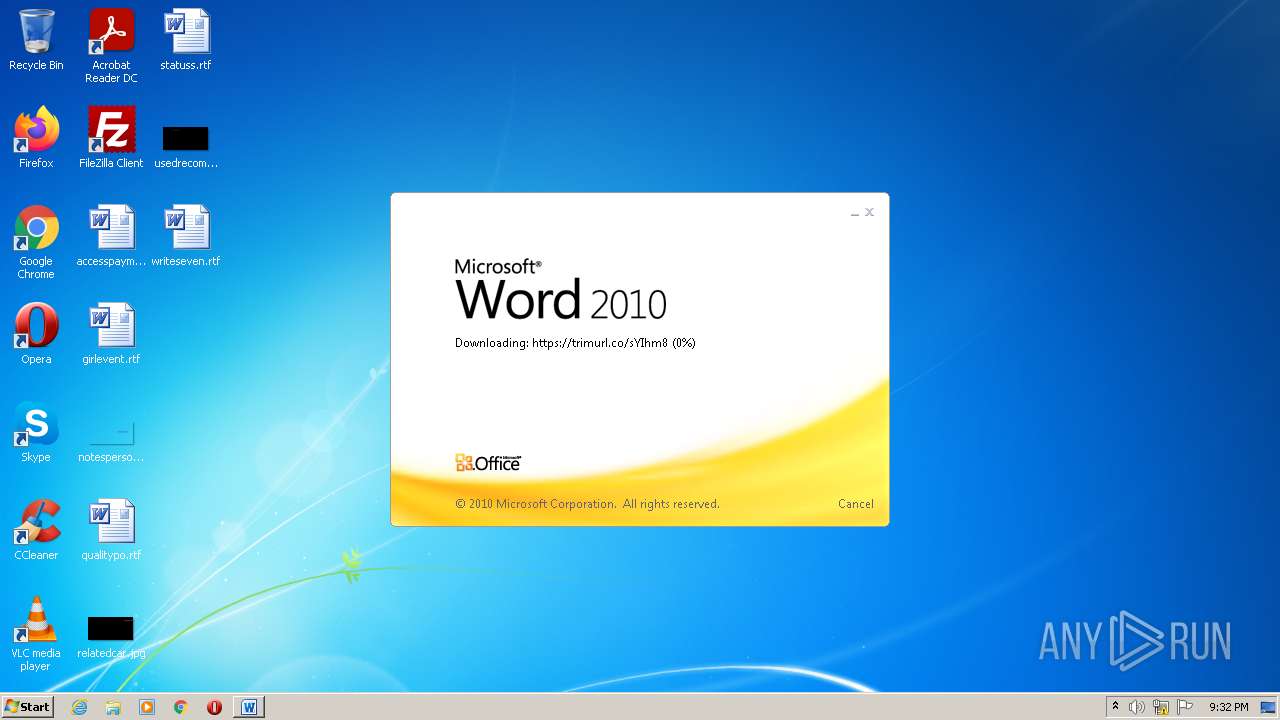
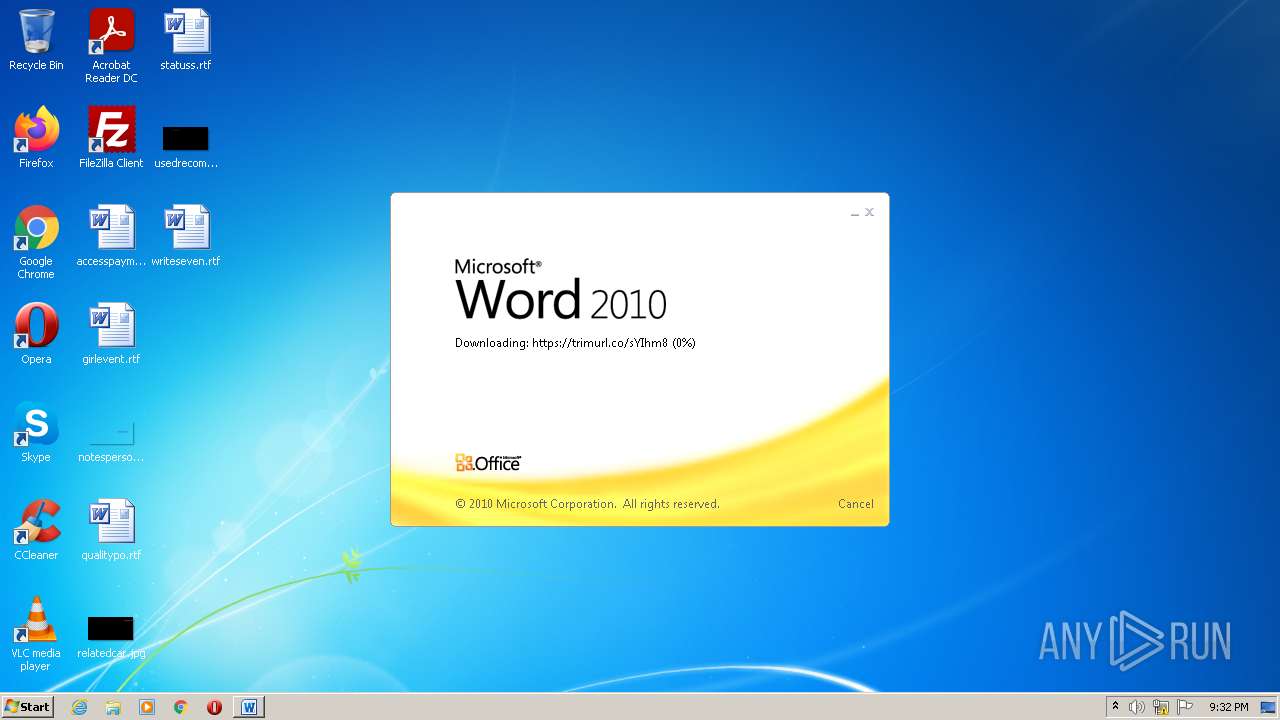
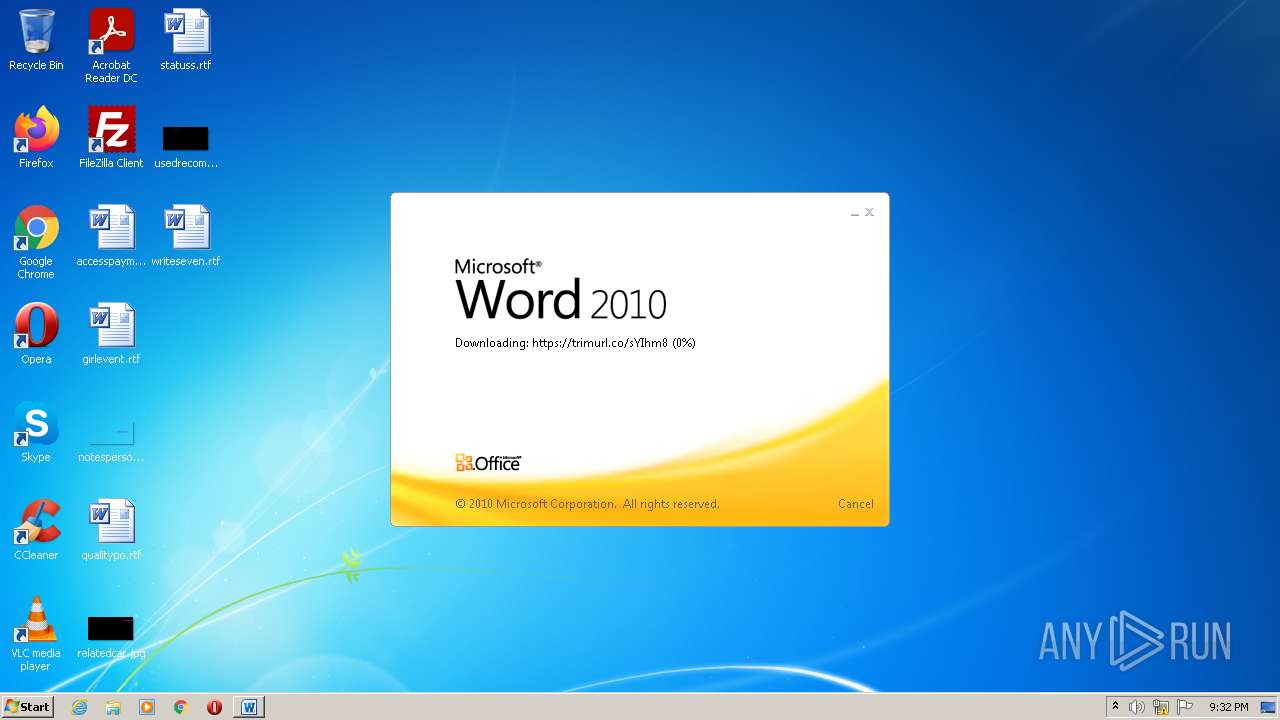
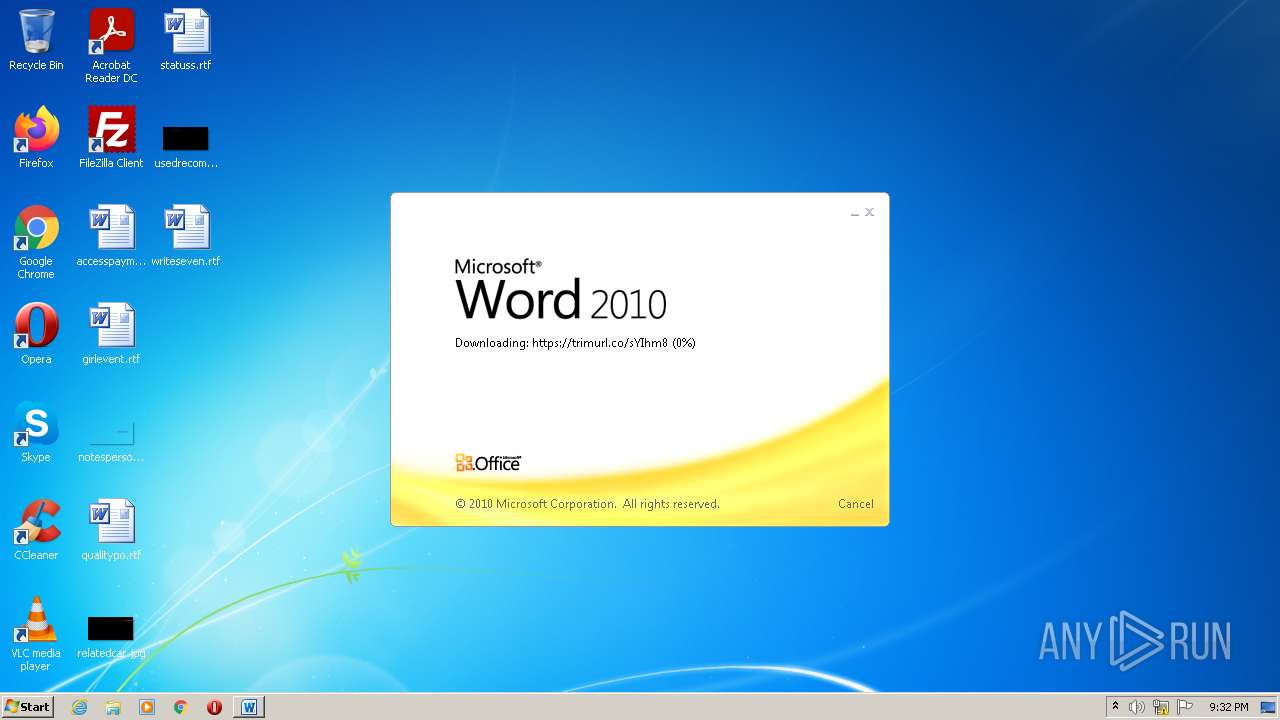
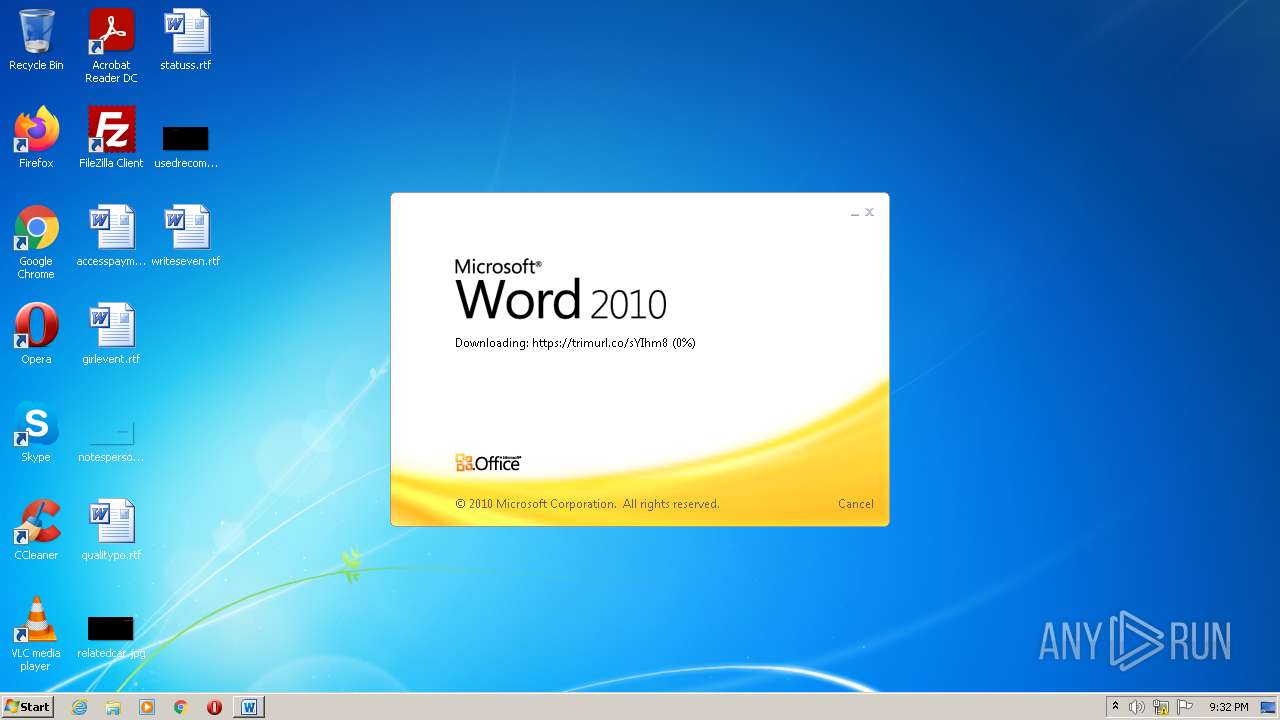
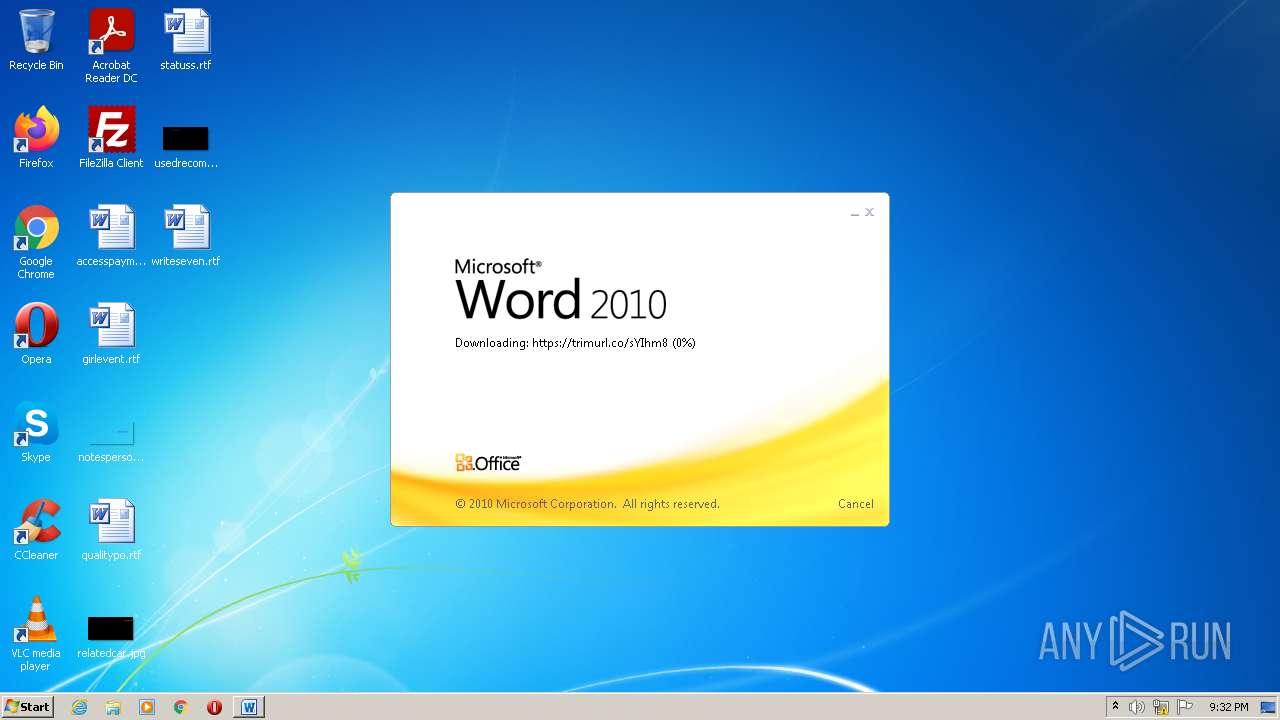
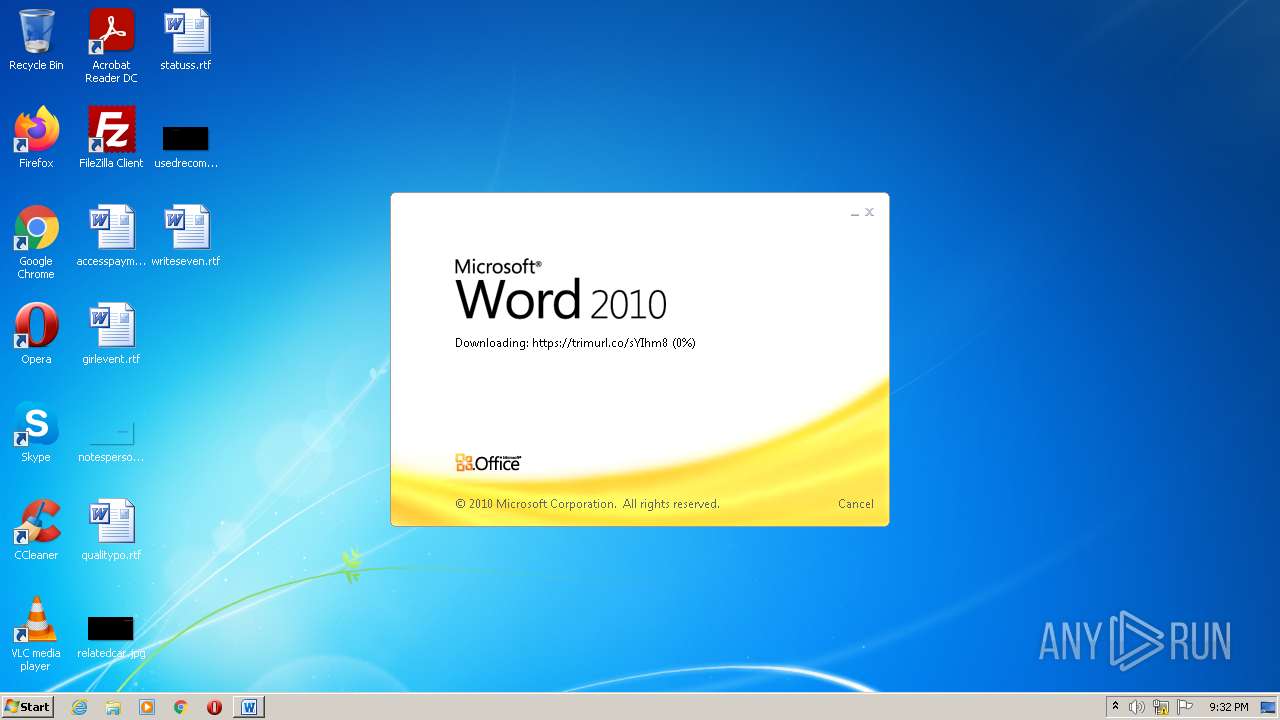
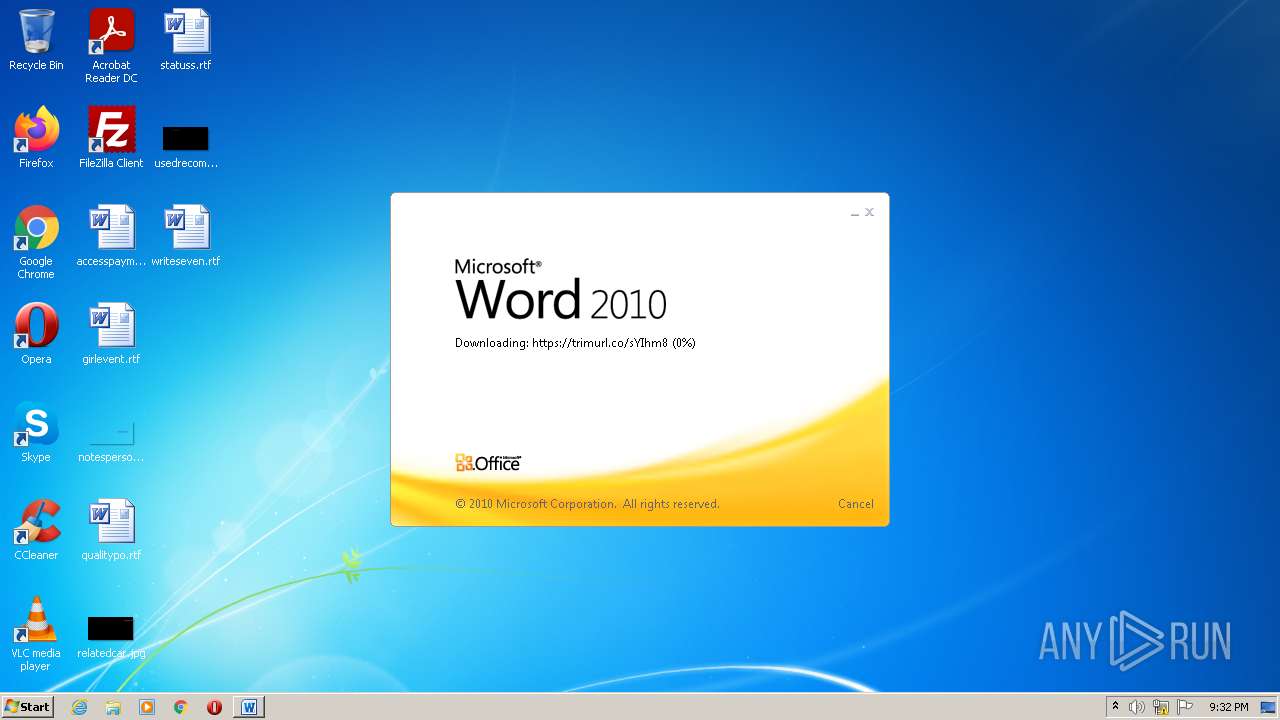
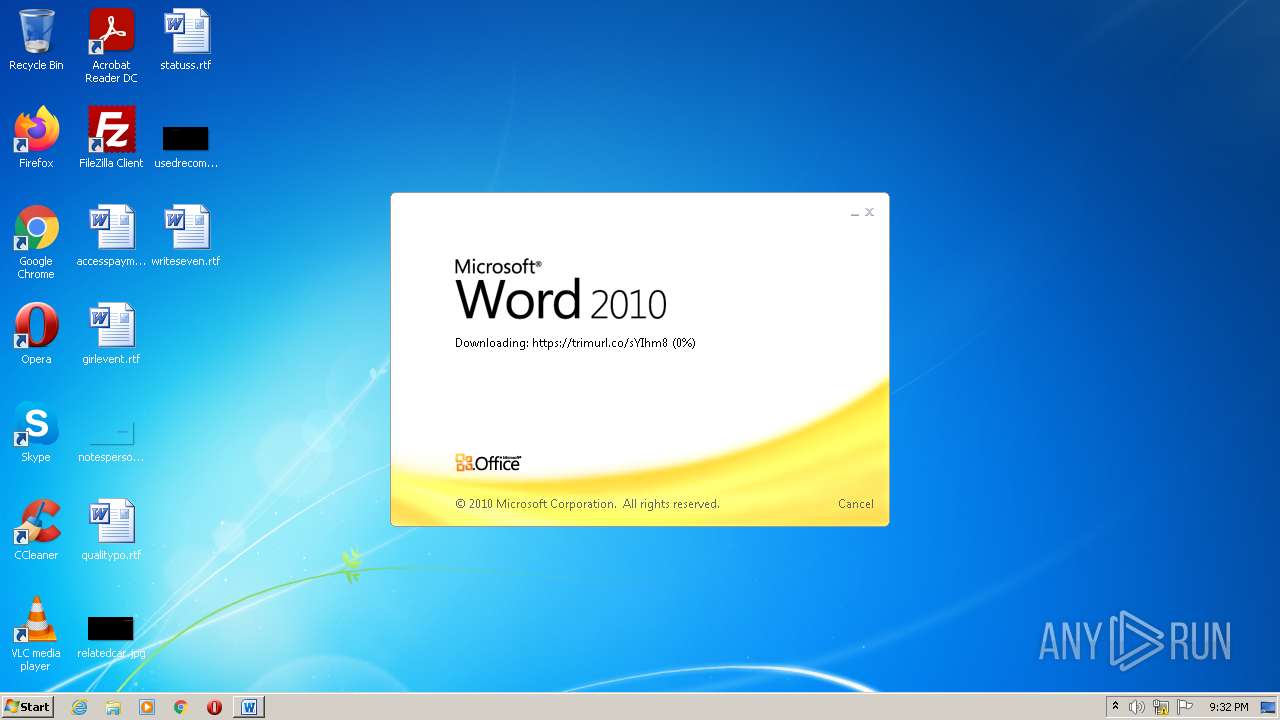
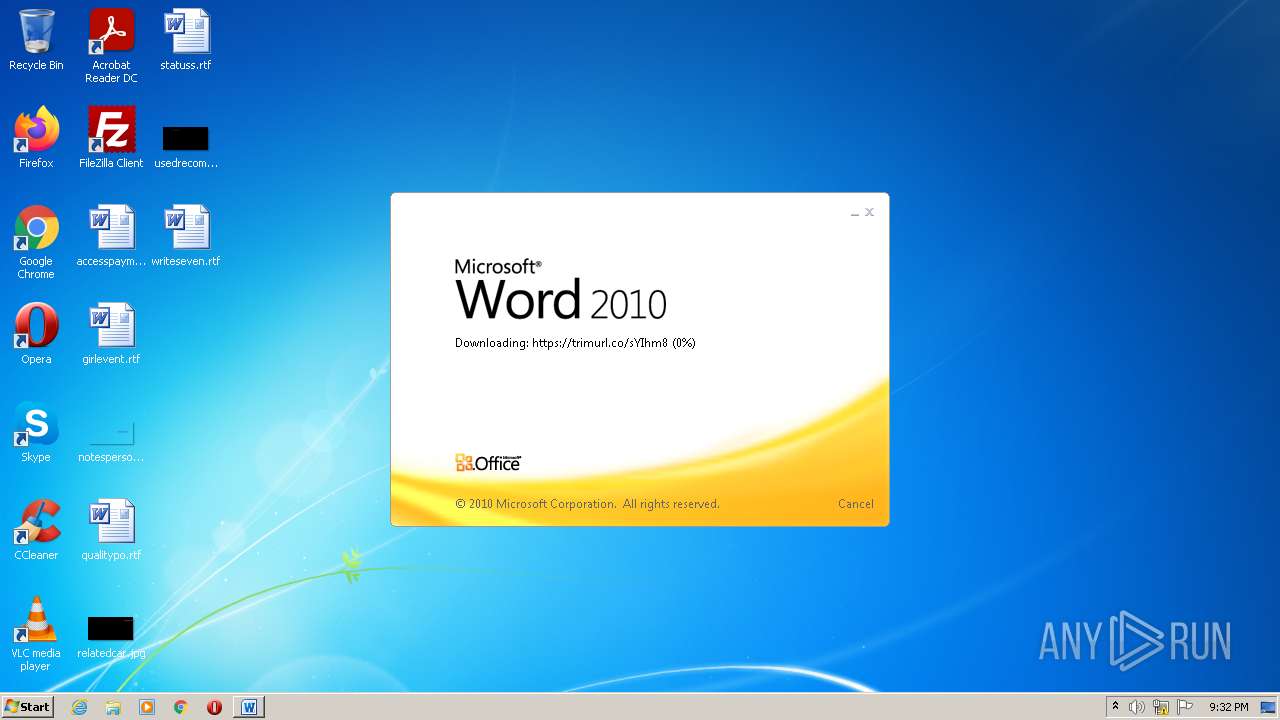
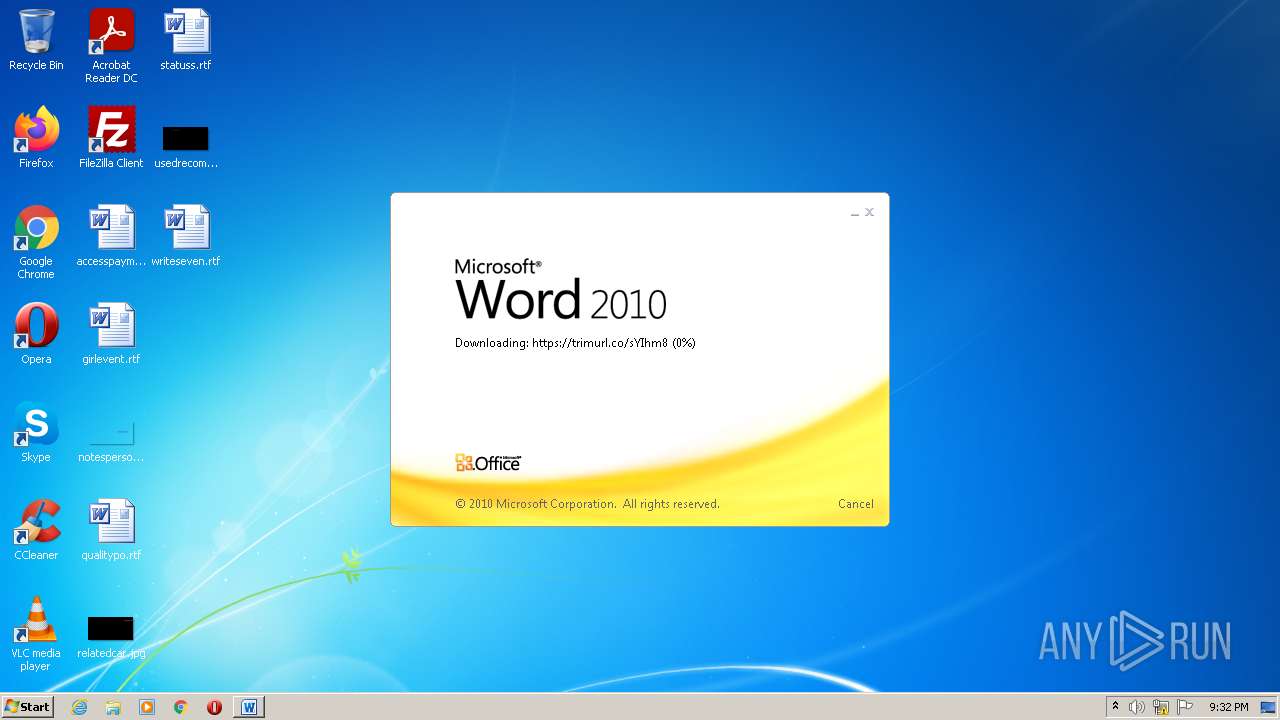
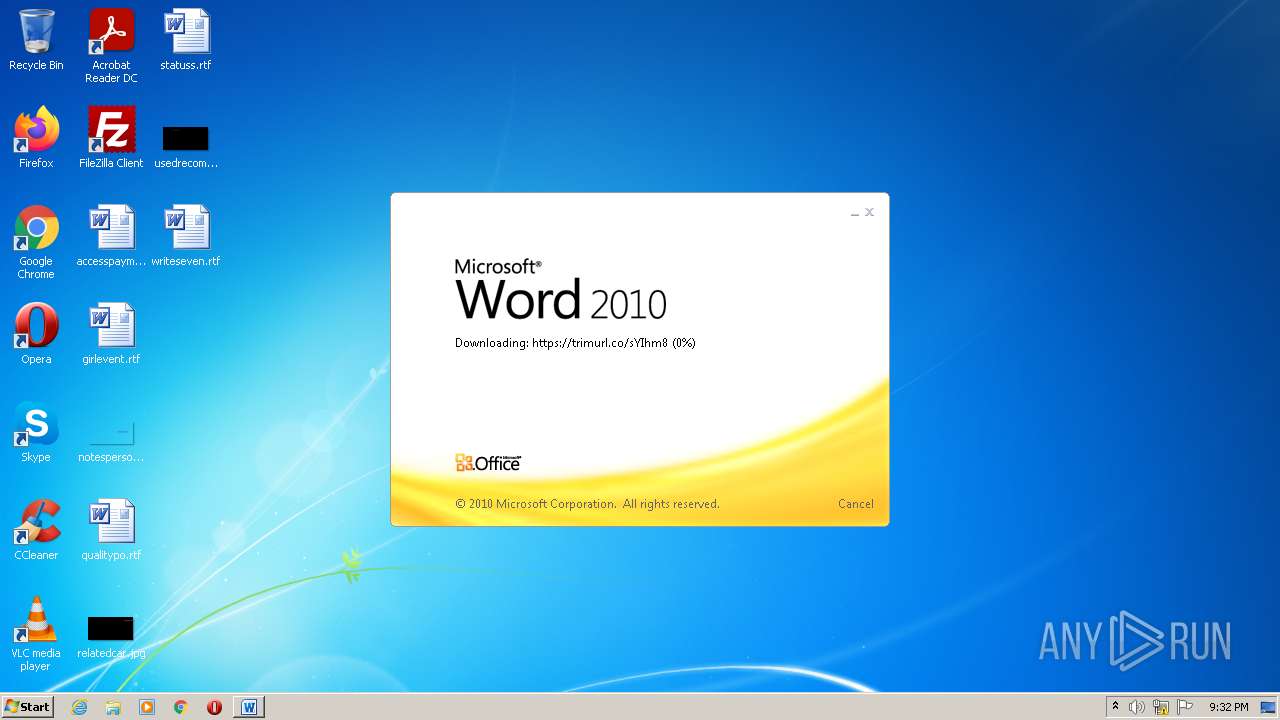
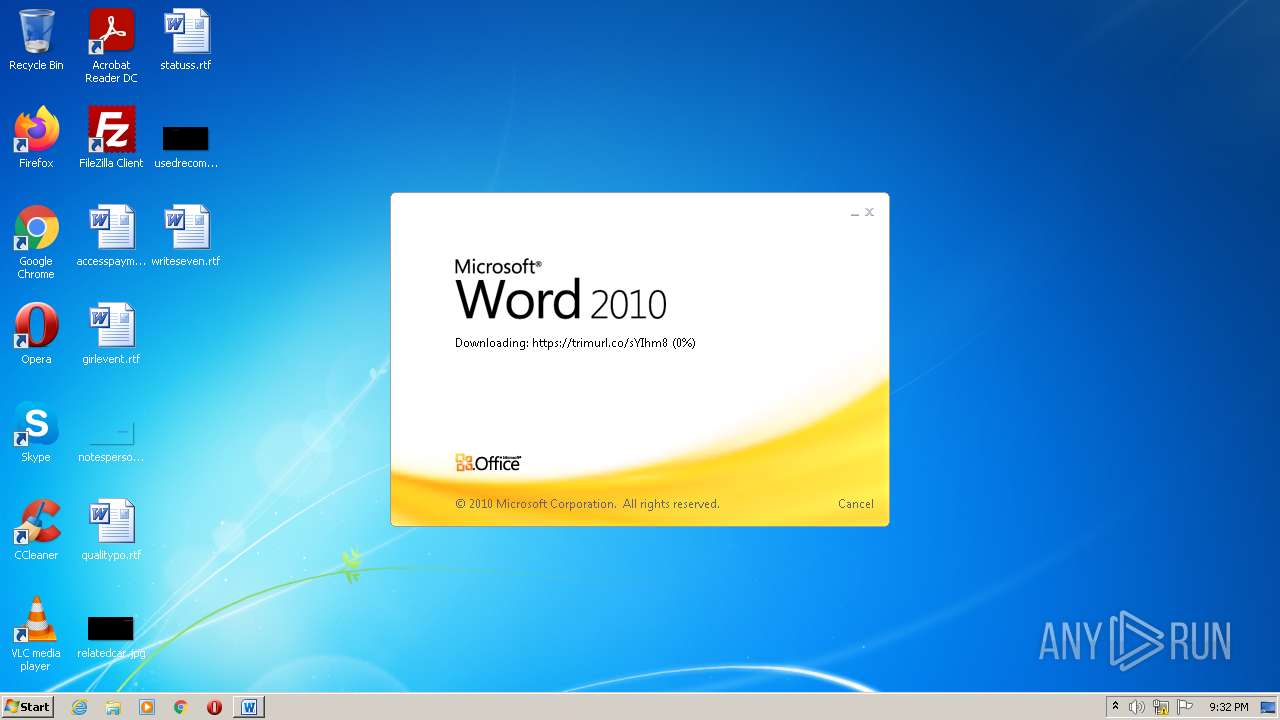
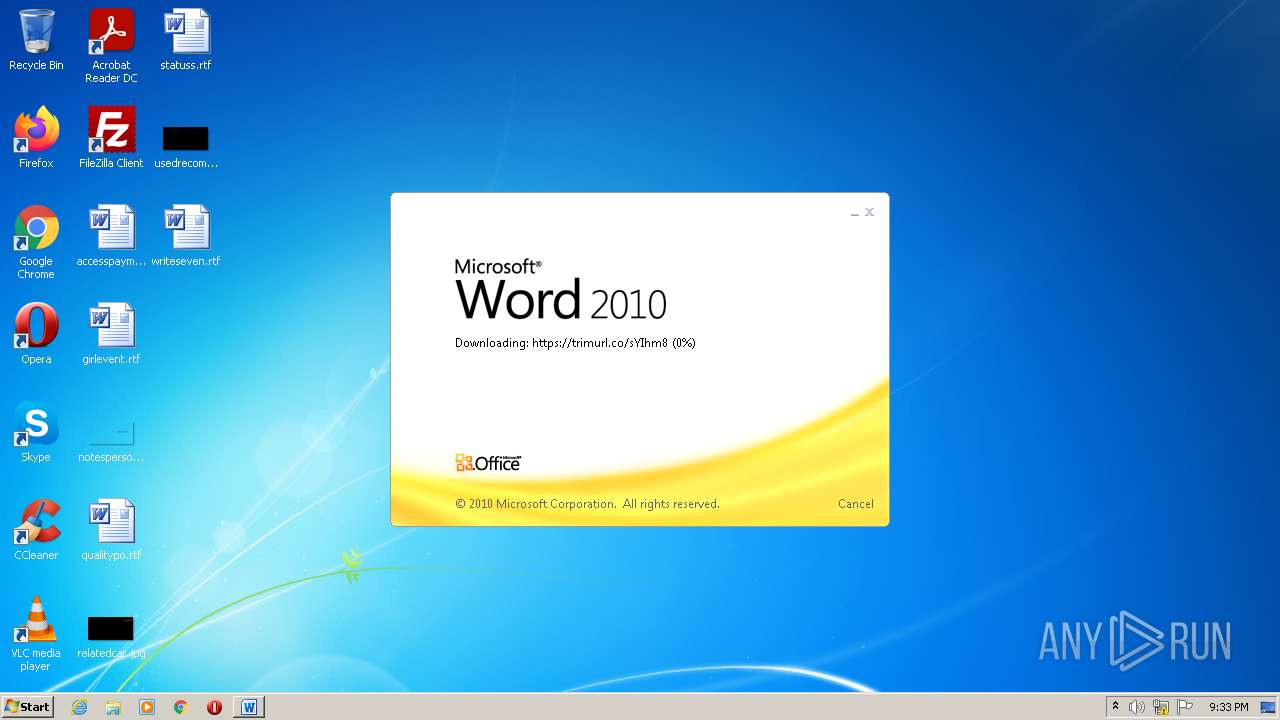
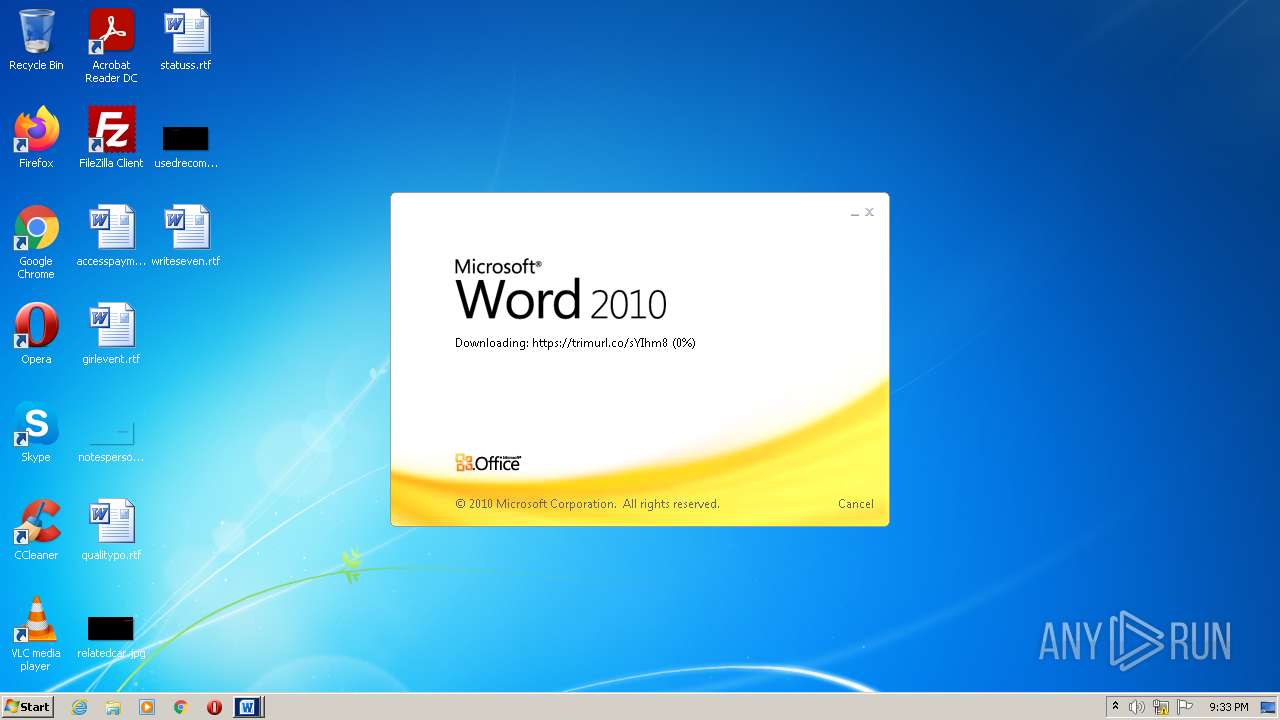
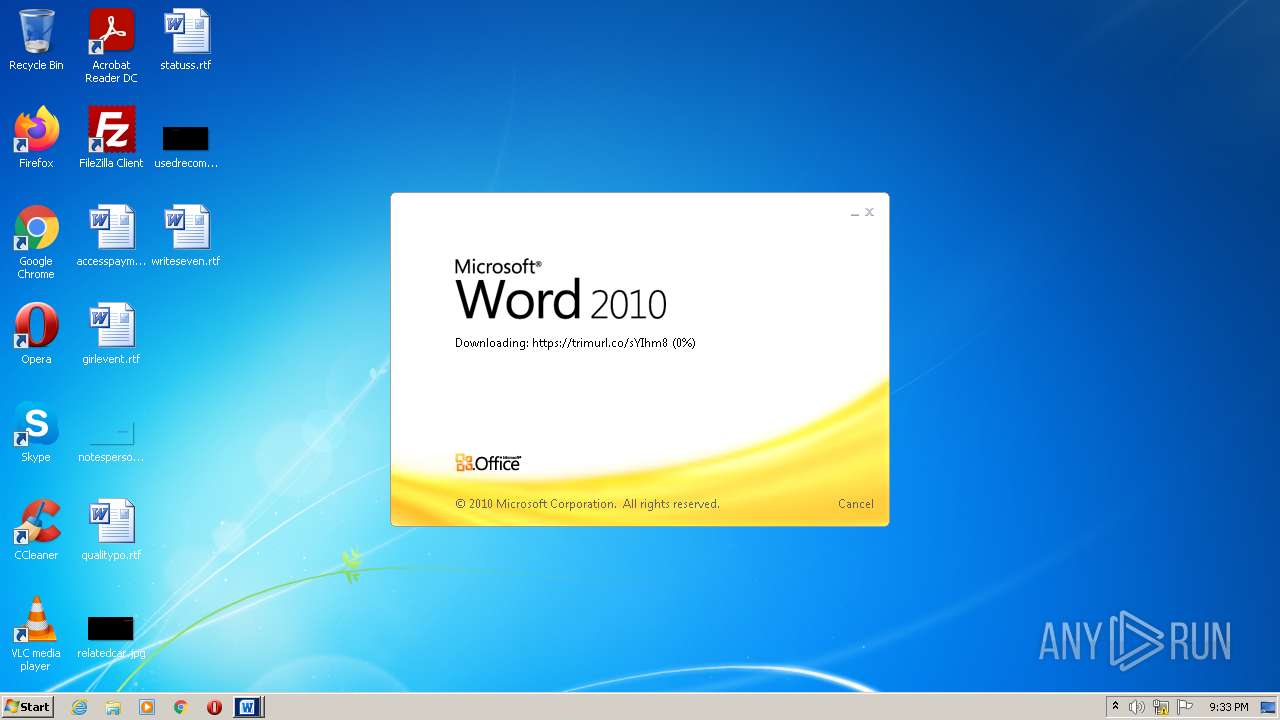
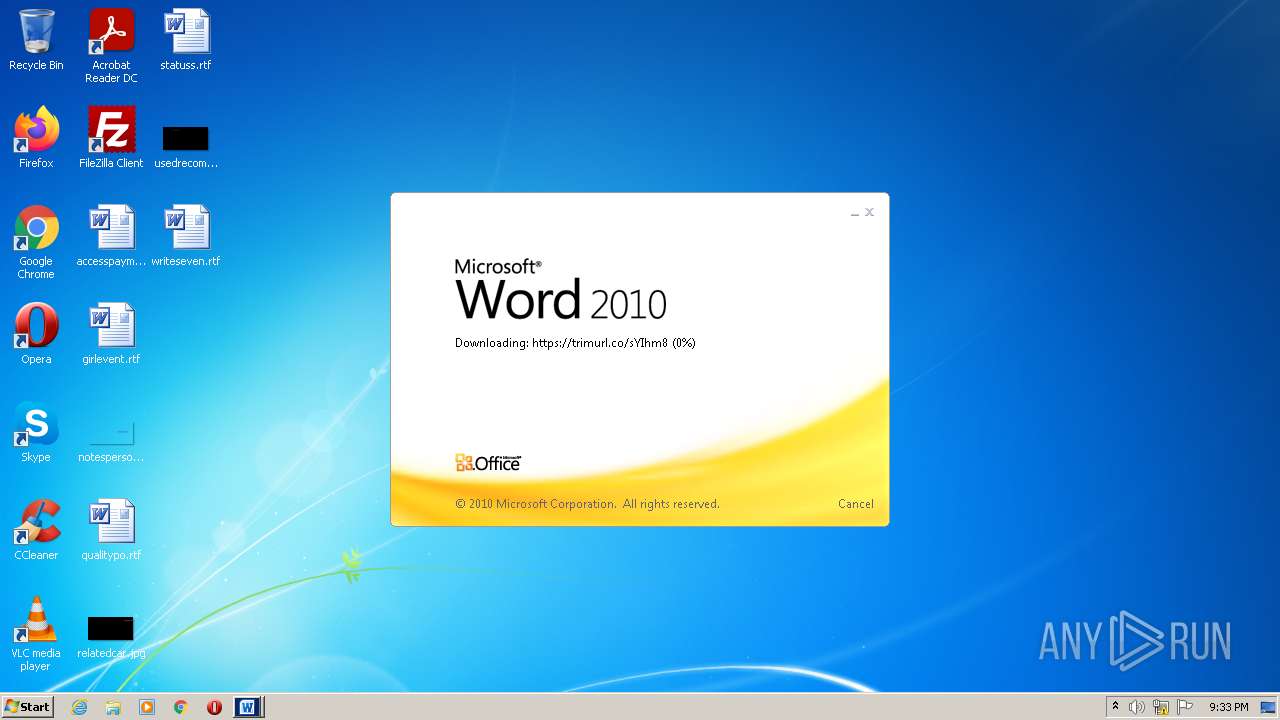
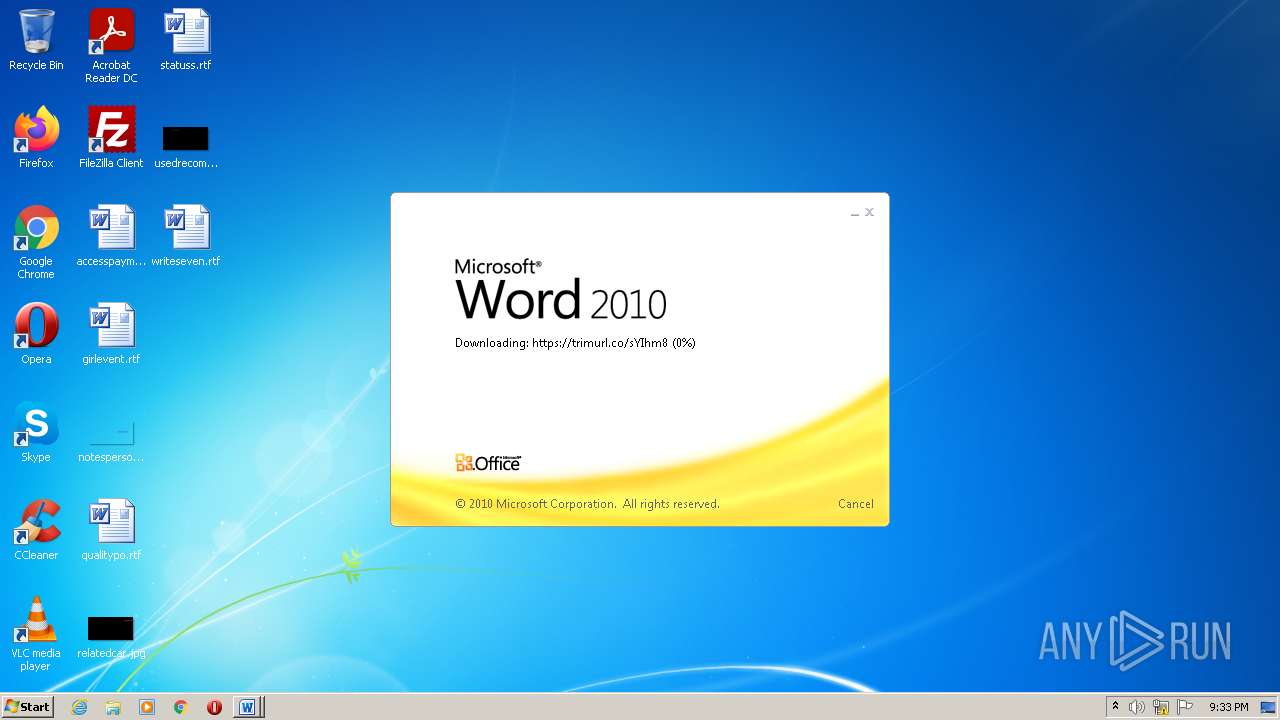
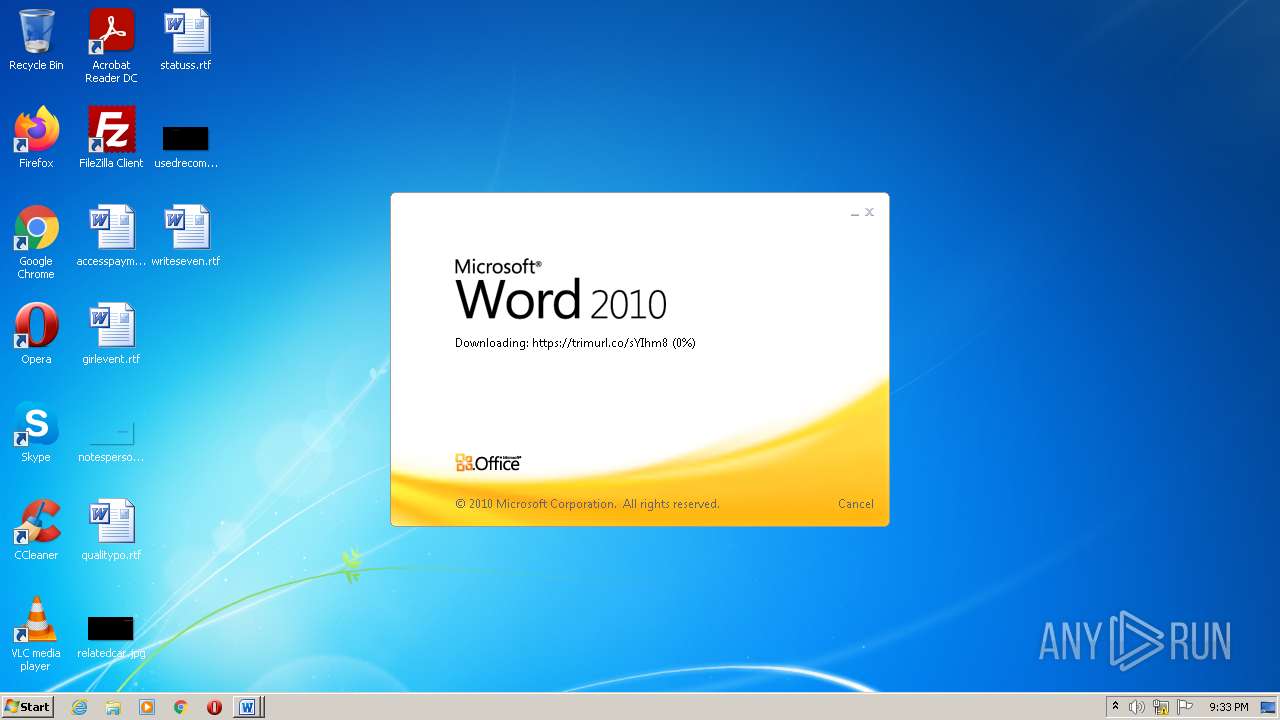
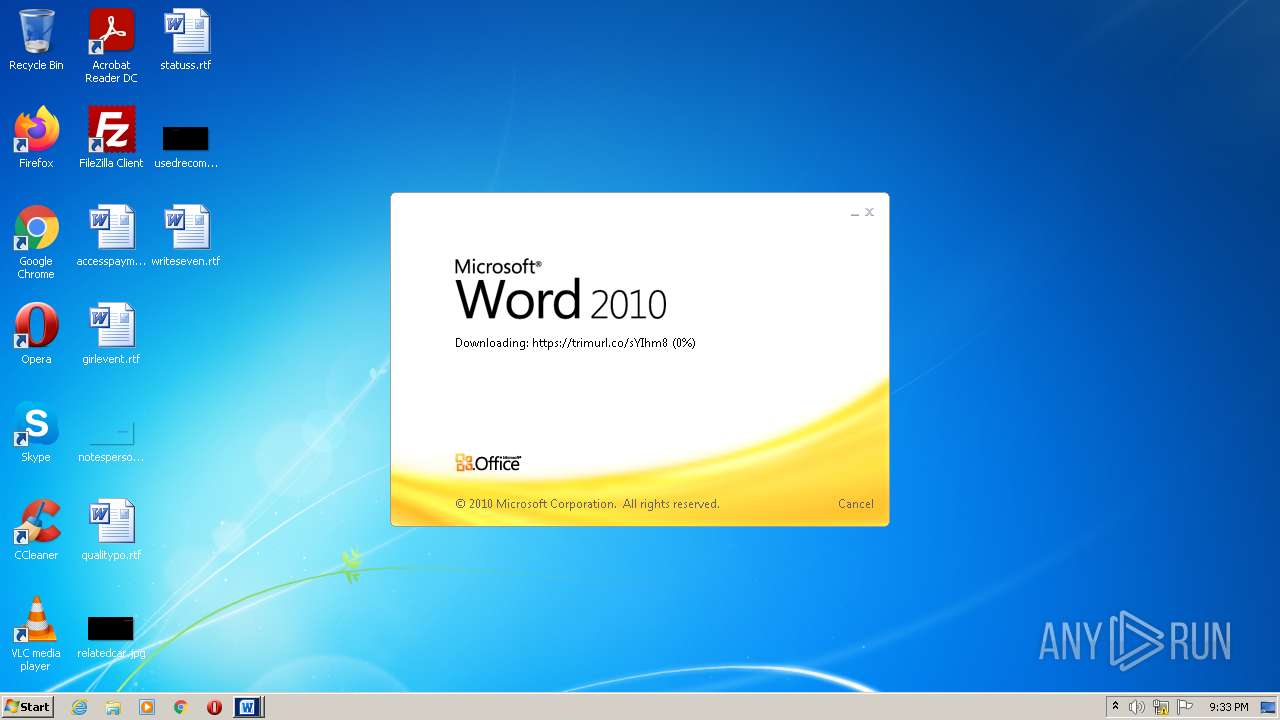
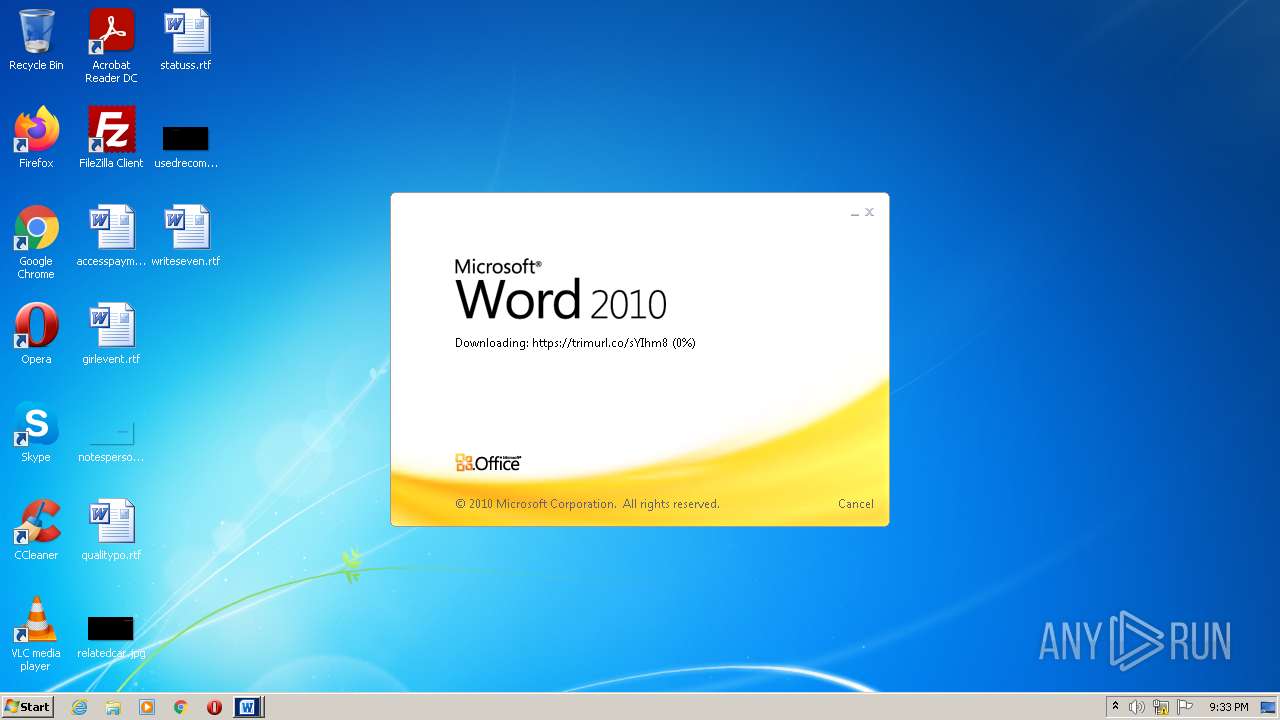
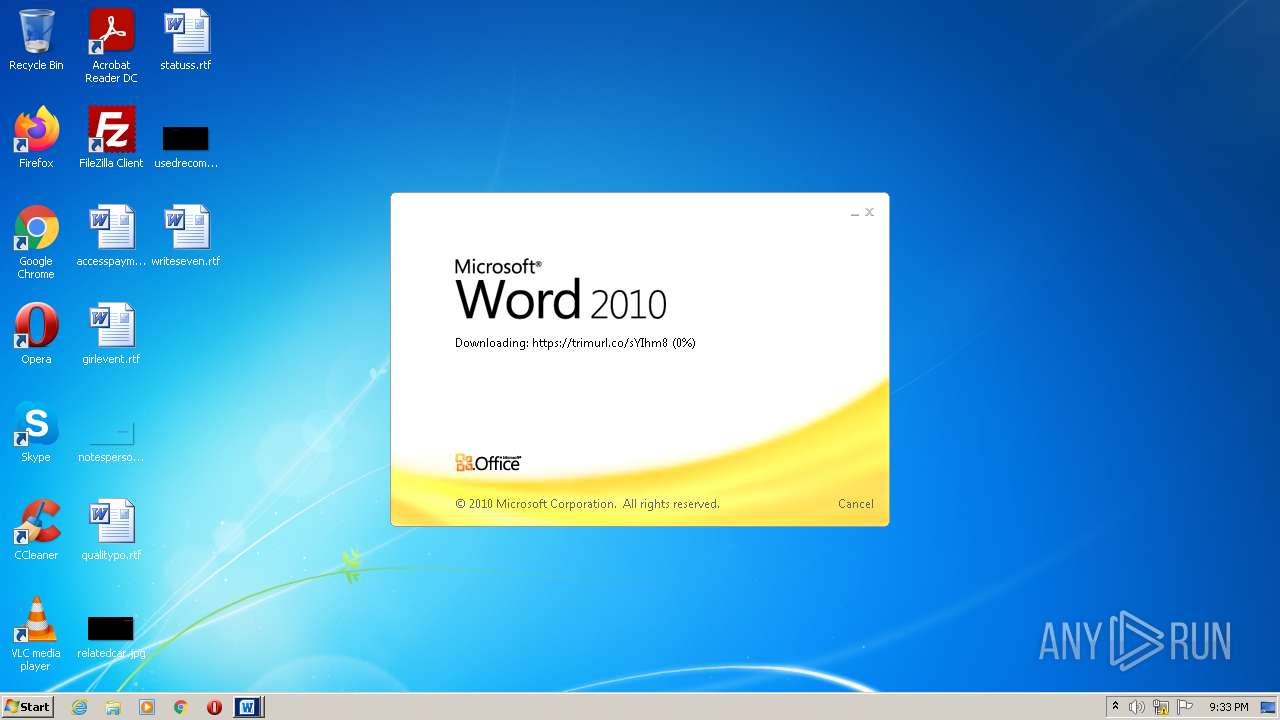
708 | svchost.exe | OPTIONS | 301 | 34.231.84.230:80 | http://trimurl.co/ | US | html | 162 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1420 | WINWORD.EXE | 34.231.84.230:443 | trimurl.co | Amazon.com, Inc. | US | suspicious |
— | — | 34.231.84.230:443 | trimurl.co | Amazon.com, Inc. | US | suspicious |
708 | svchost.exe | 34.231.84.230:443 | trimurl.co | Amazon.com, Inc. | US | suspicious |
708 | svchost.exe | 34.231.84.230:80 | trimurl.co | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
trimurl.co |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
708 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |