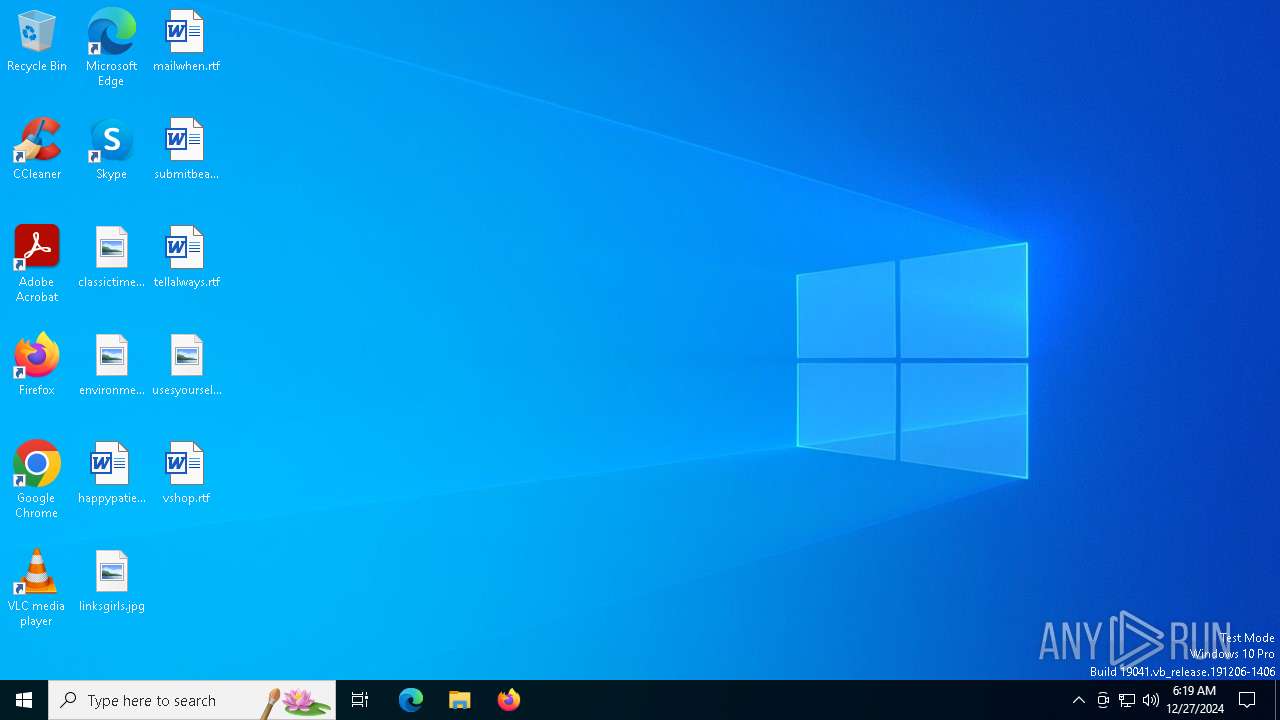
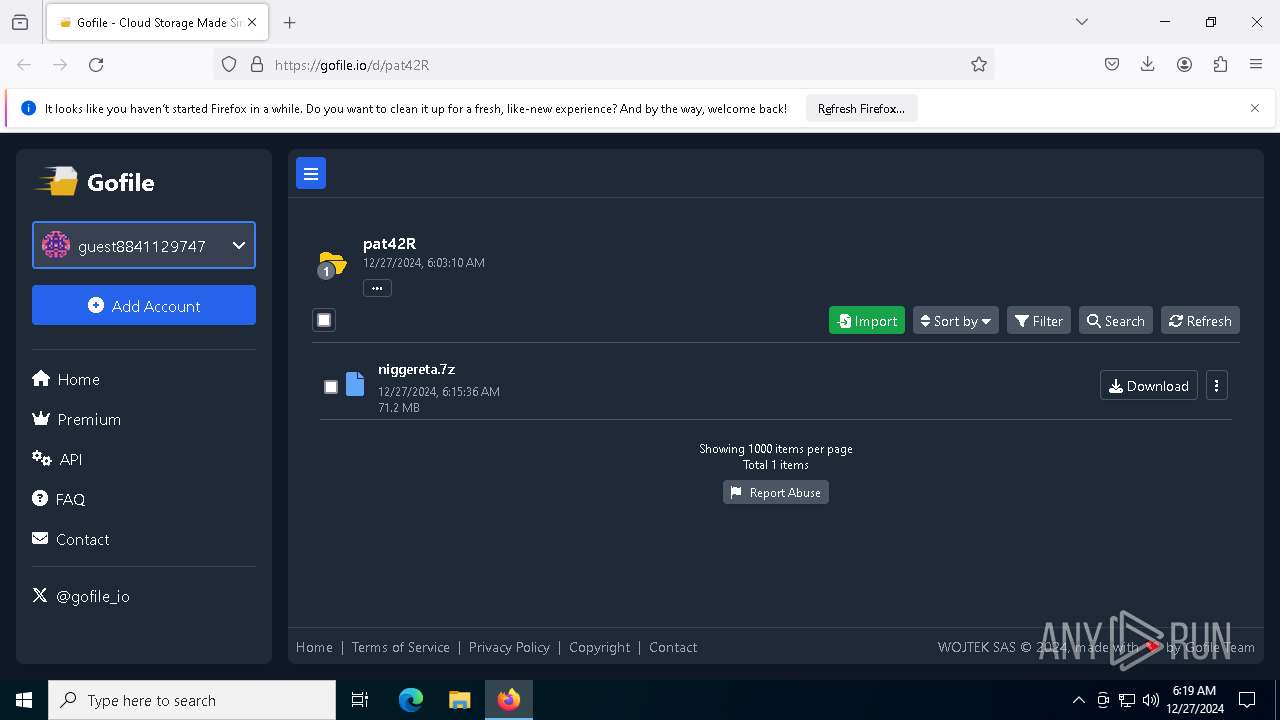
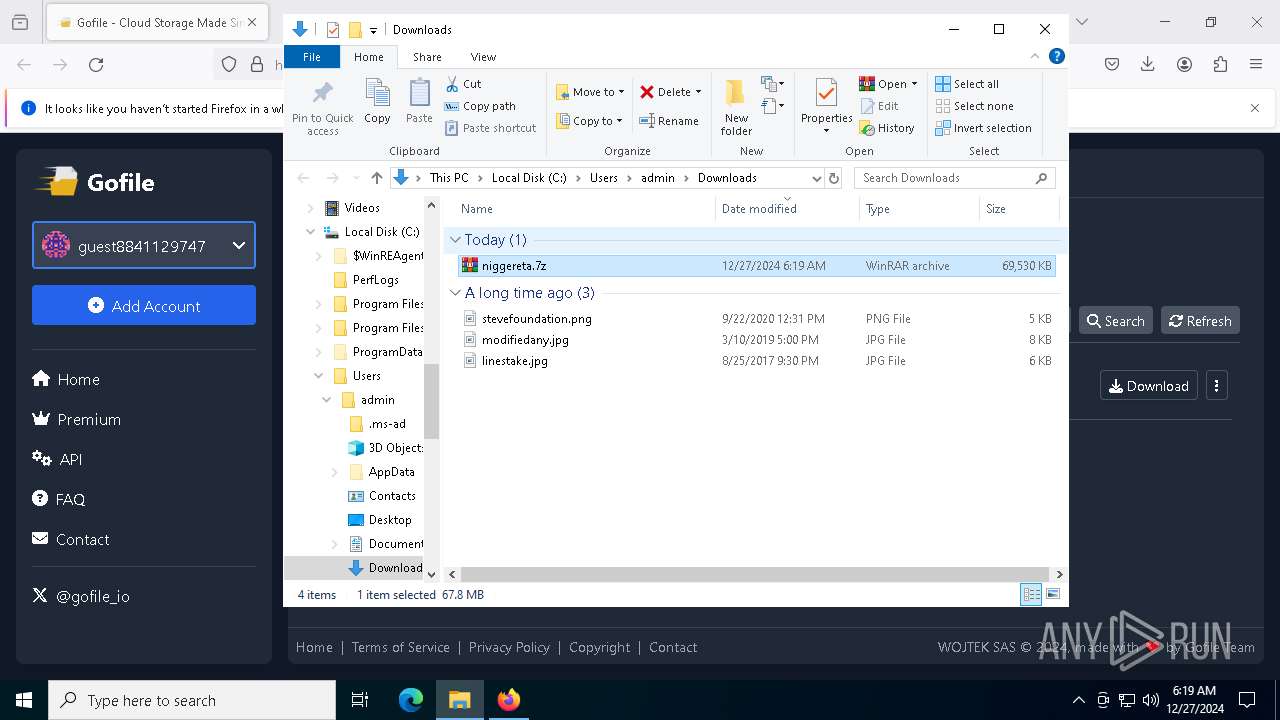
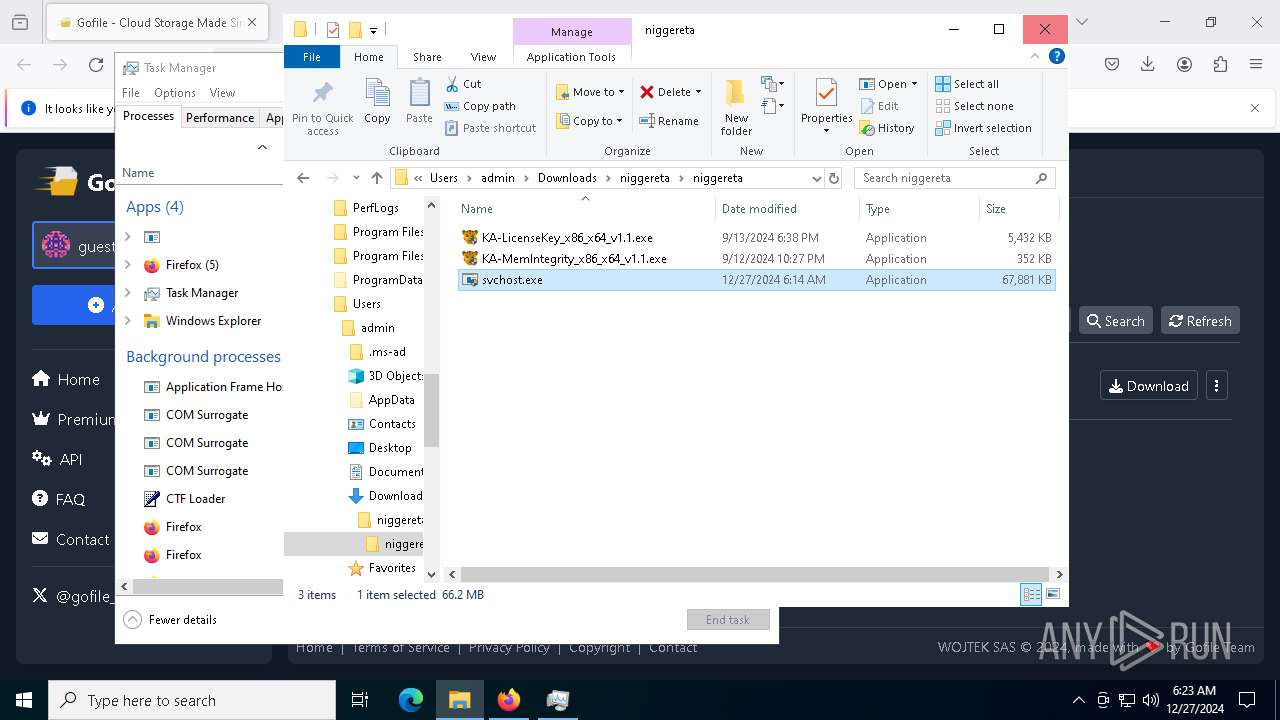
| URL: | https://gofile.io/d/pat42R |
| Full analysis: | https://app.any.run/tasks/fe7f8c91-46a8-4192-a4d9-d591ce8cc812 |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2024, 06:19:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9F2E0C0429D11322AC4AE4BD21299F1B |
| SHA1: | 4DB3DC347BAFD1DBC1F601FDEA68B9AFC8F5EE2F |
| SHA256: | 181D0076D0B29B91999100BFAA01306ADB59DA7CC983D3B7597C2A011B608F01 |
| SSDEEP: | 3:N8rxL1u3:2Zo |
MALICIOUS
Uses TASKKILL.EXE to kill security tools
- cmd.exe (PID: 7636)
- cmd.exe (PID: 6444)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 1076)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 7760)
SUSPICIOUS
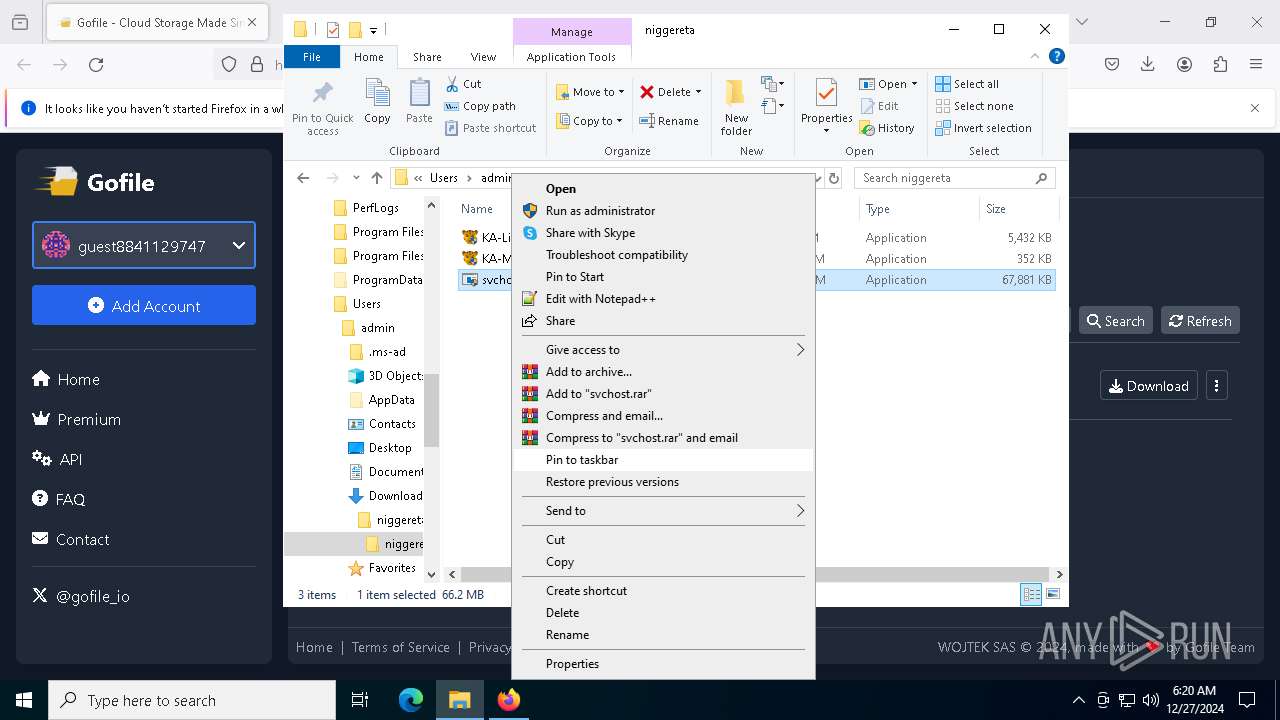
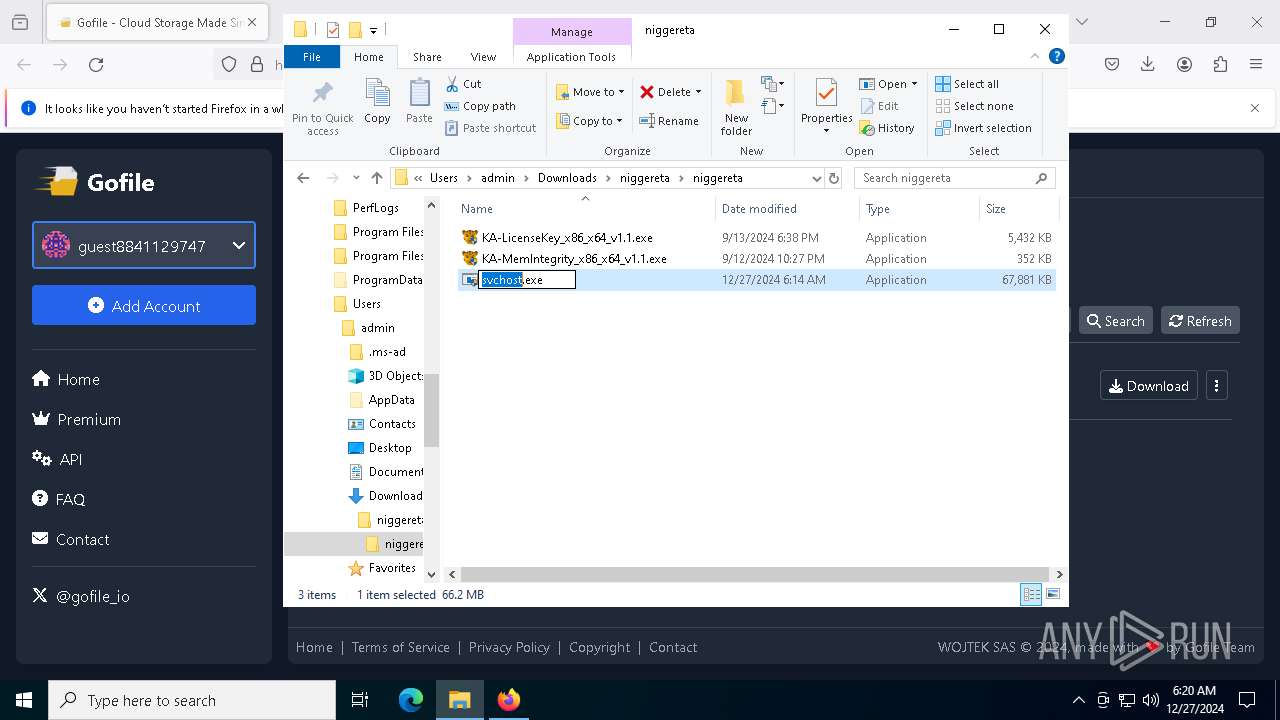
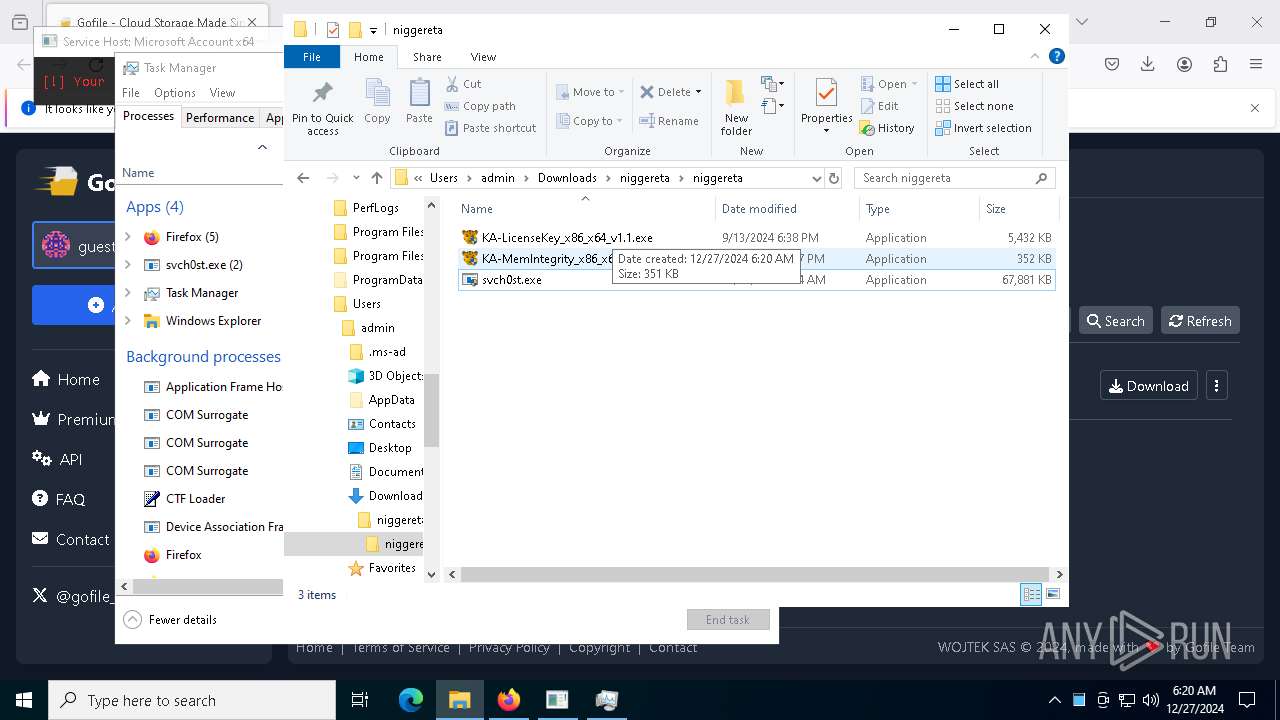
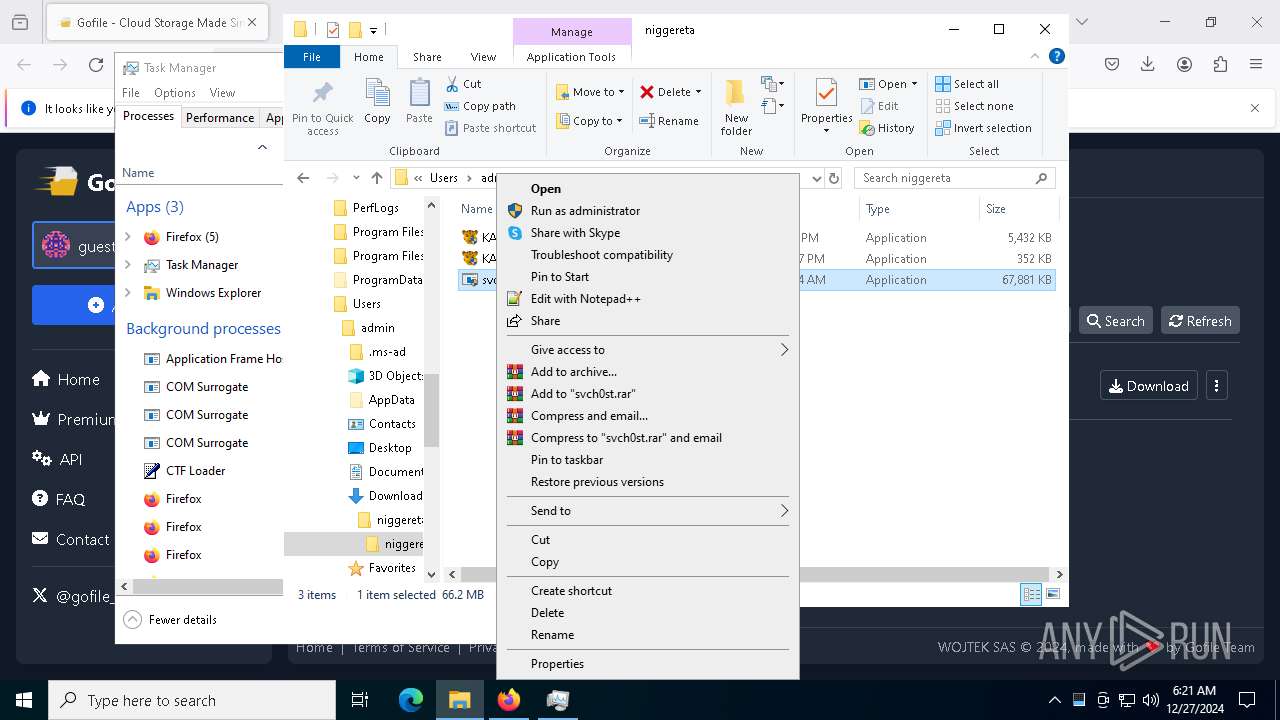
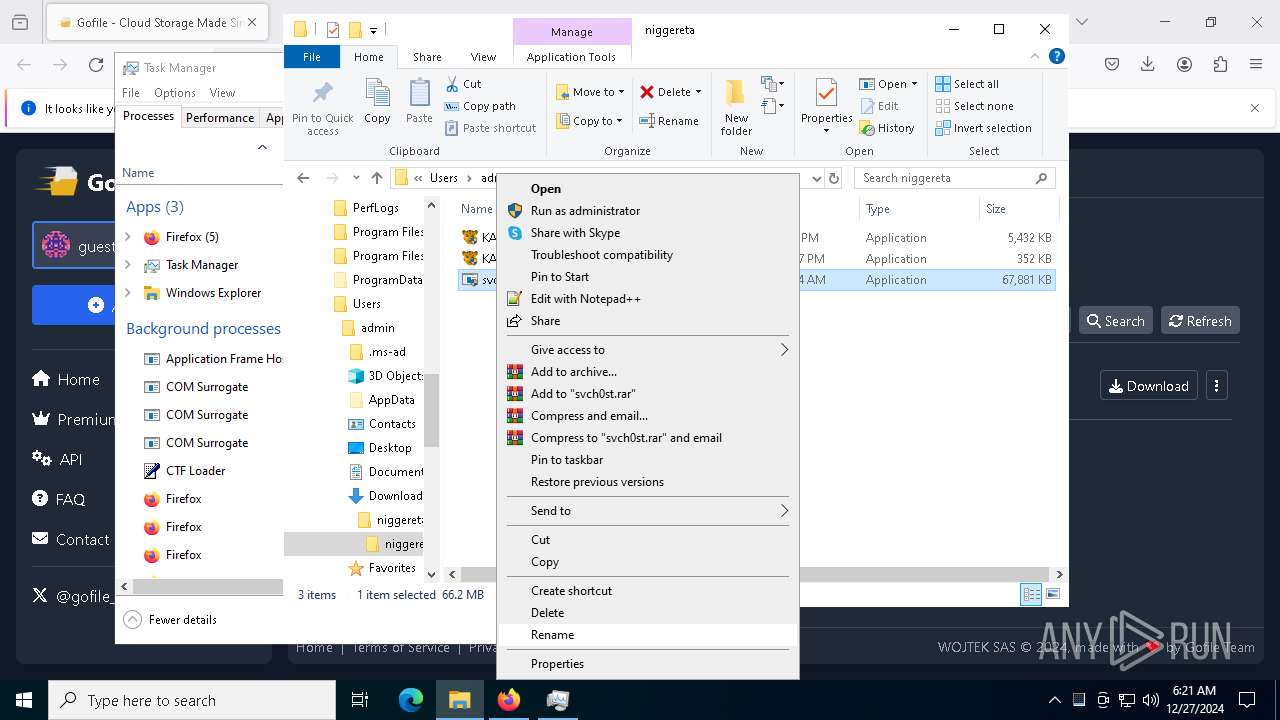
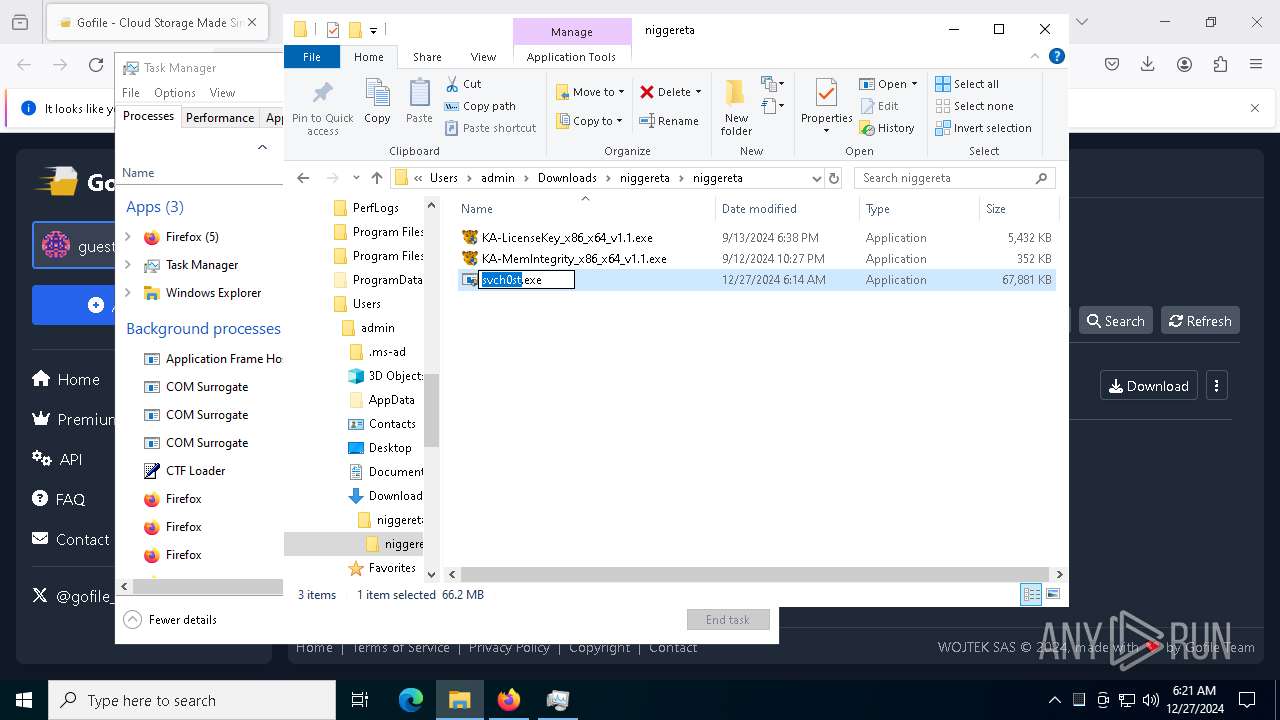
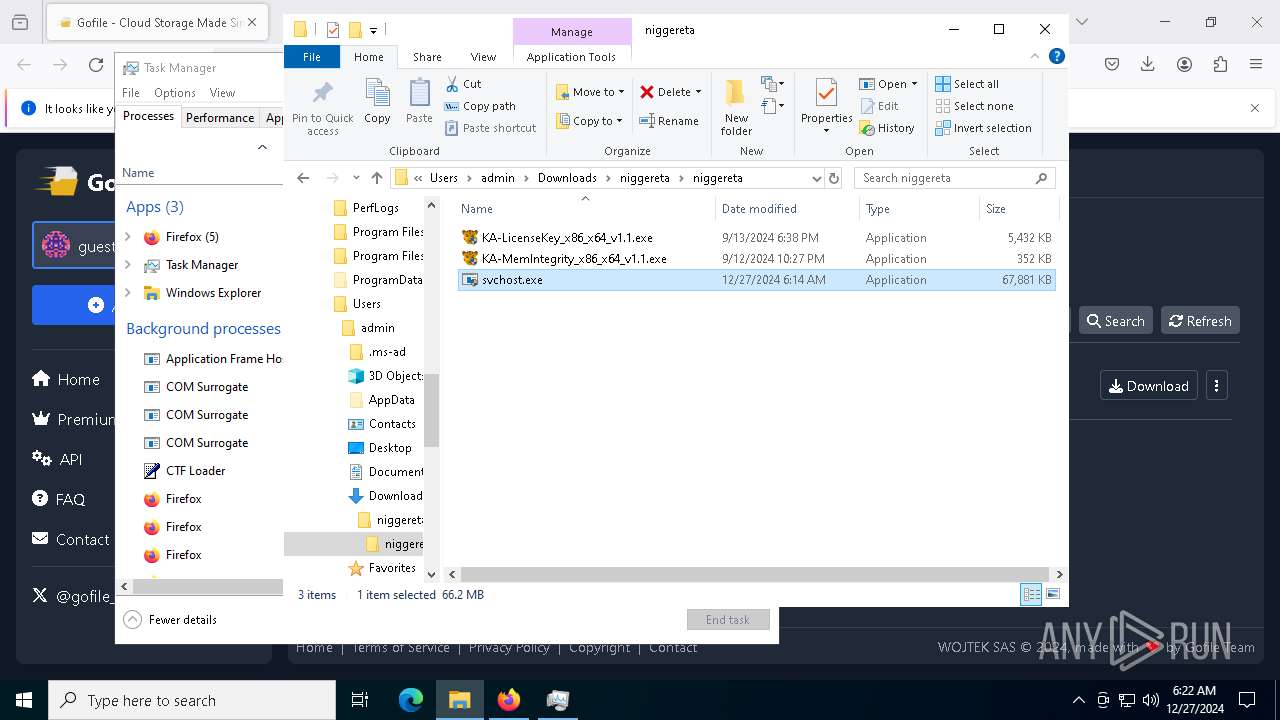
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3984)
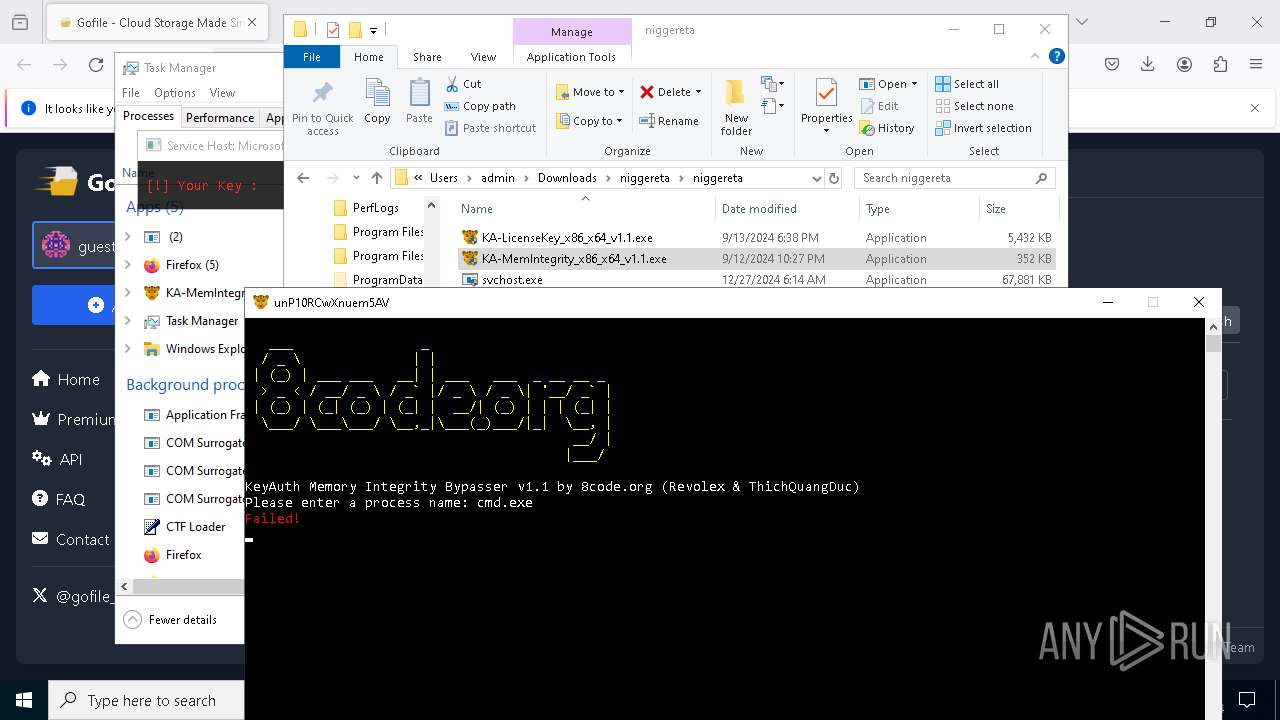
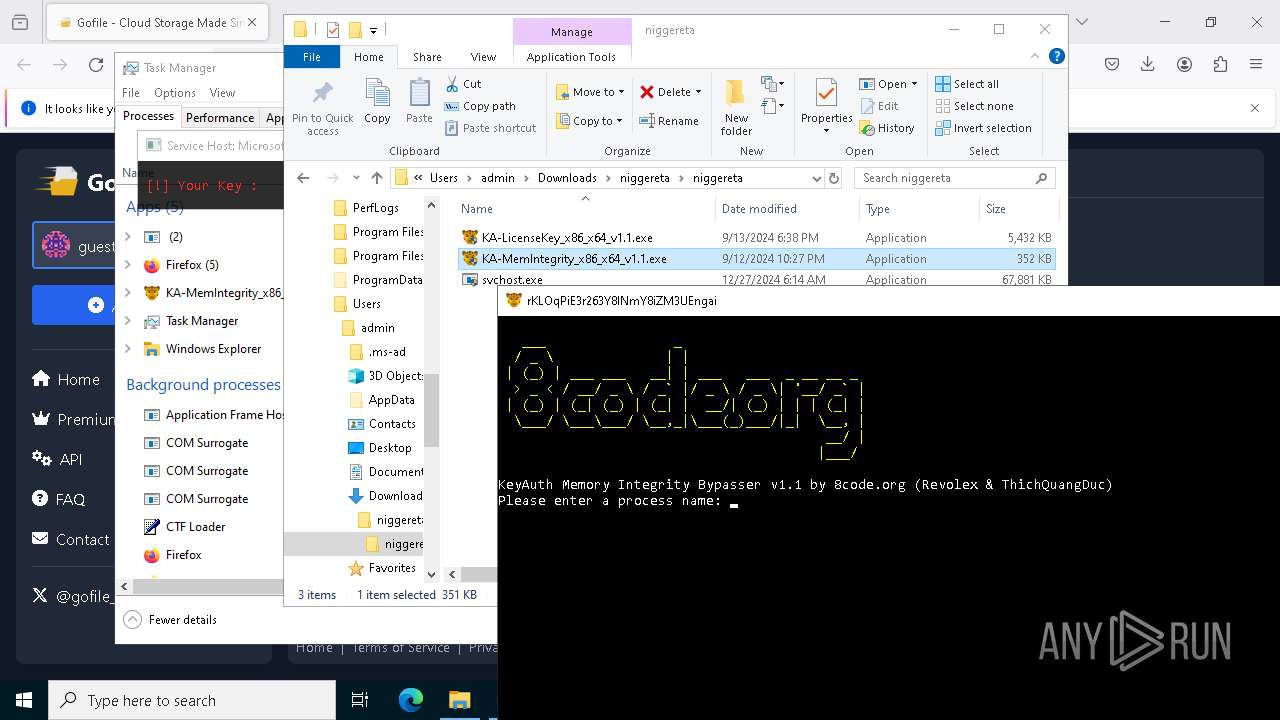
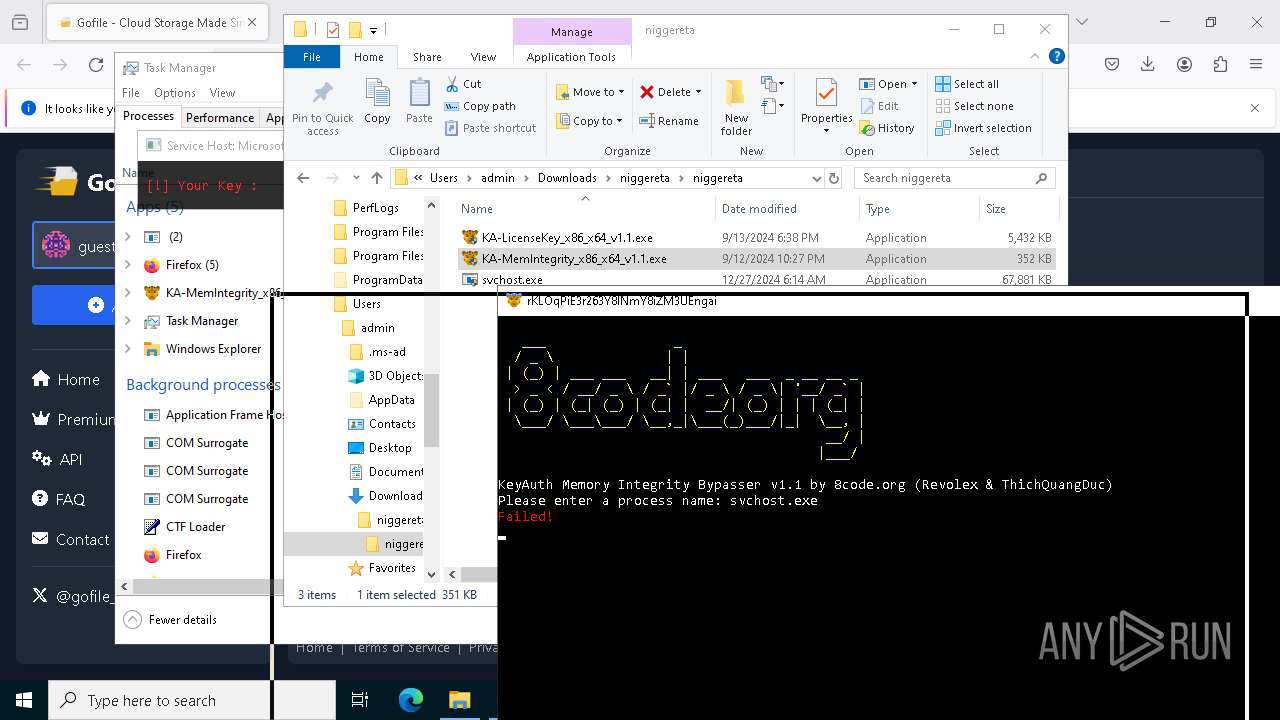
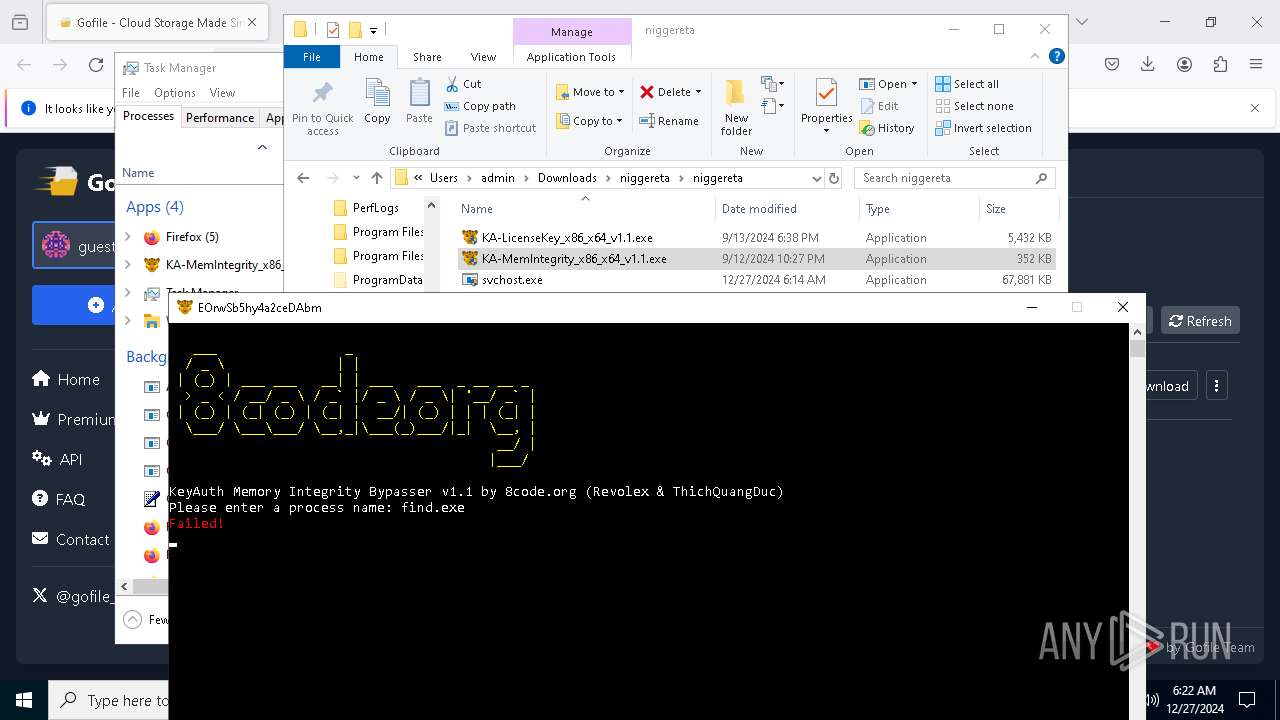
Starts CMD.EXE for commands execution
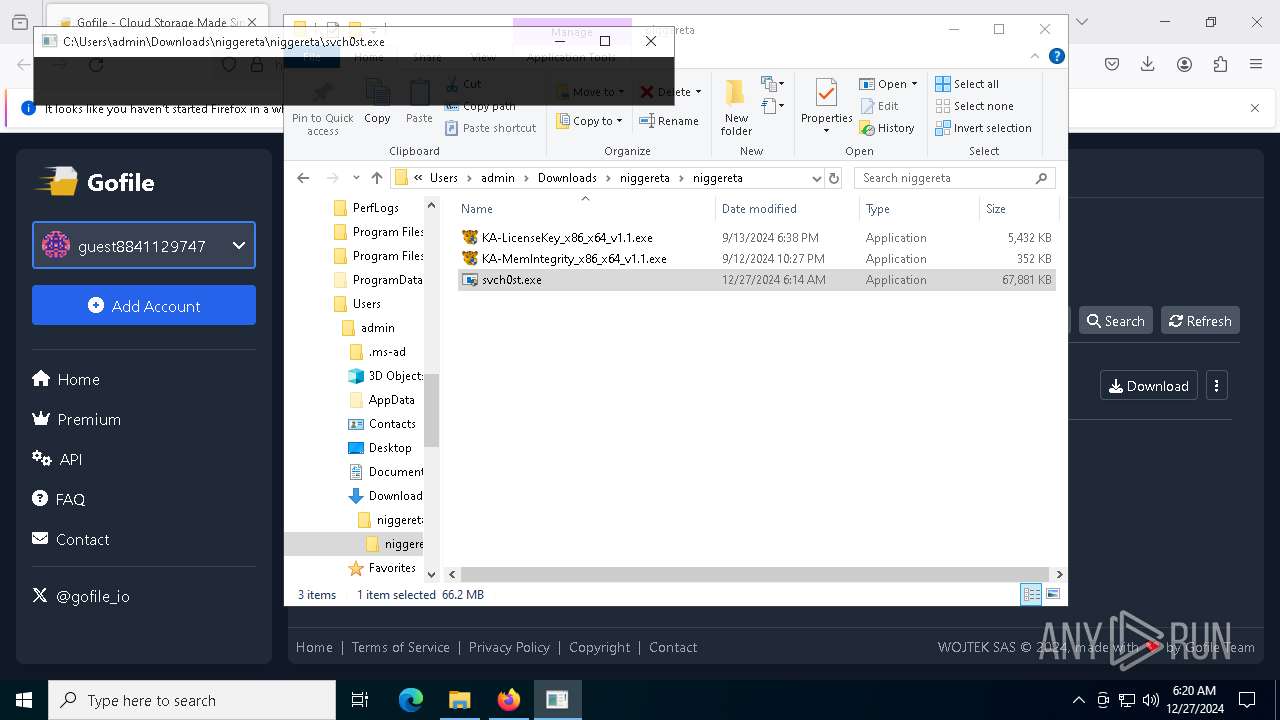
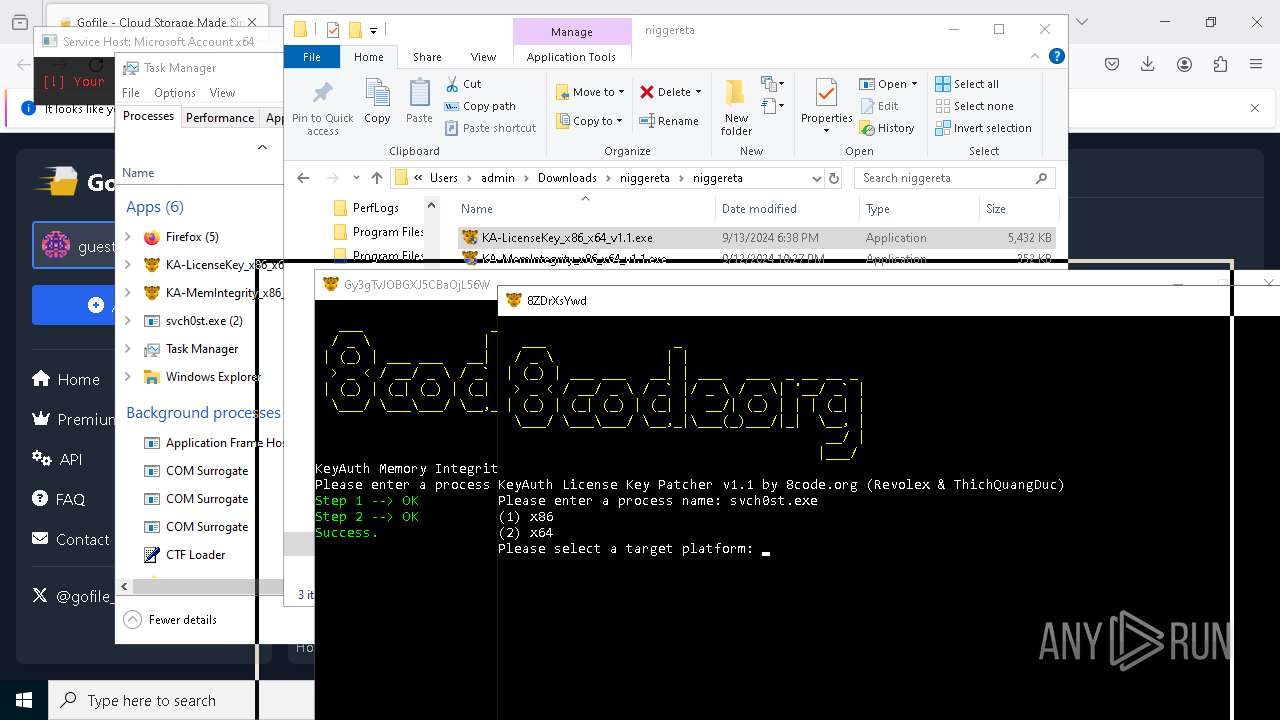
- svch0st.exe (PID: 5096)
- svchost.exe (PID: 6484)
- svchost.exe (PID: 624)
- svchost.exe (PID: 6636)
Hides command output
- cmd.exe (PID: 7628)
- cmd.exe (PID: 7636)
- cmd.exe (PID: 6444)
- cmd.exe (PID: 6608)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 5916)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 4932)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 4708)
- cmd.exe (PID: 6524)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 7088)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 1076)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7904)
- cmd.exe (PID: 6232)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 6424)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7628)
- cmd.exe (PID: 6608)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 7956)
- cmd.exe (PID: 5916)
- cmd.exe (PID: 6096)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 7088)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 3584)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 7904)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 6232)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 6424)
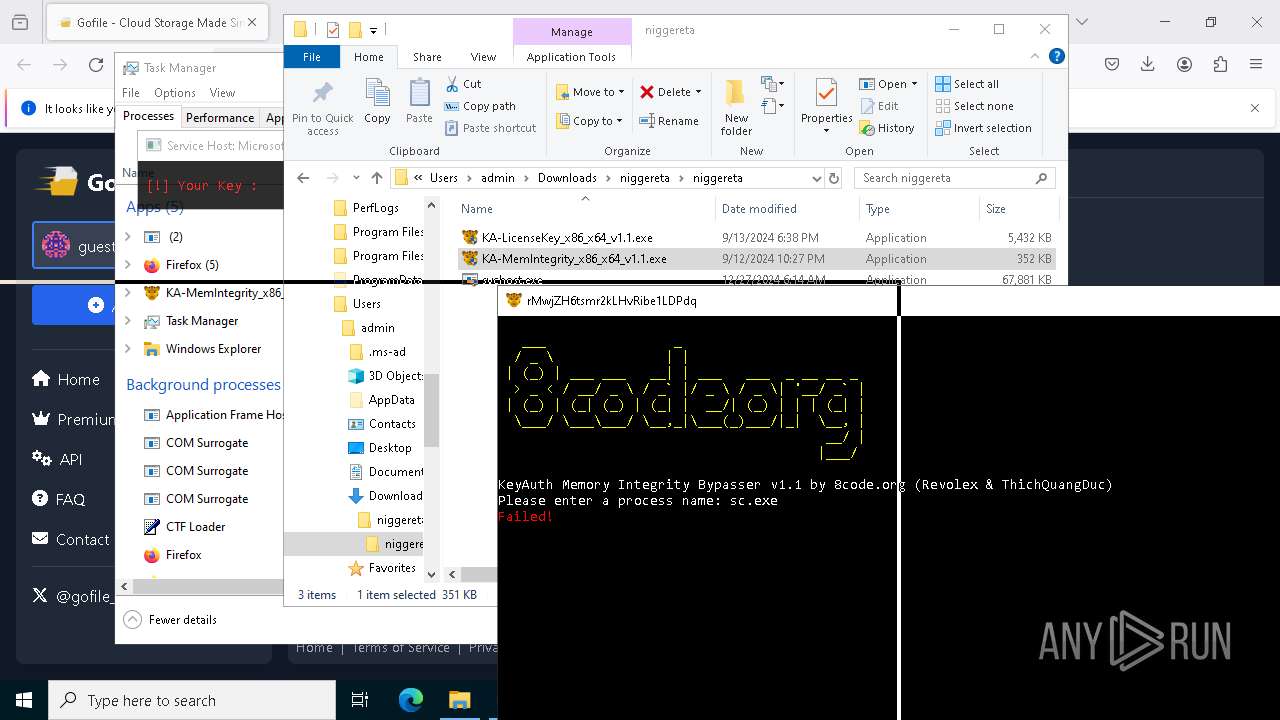
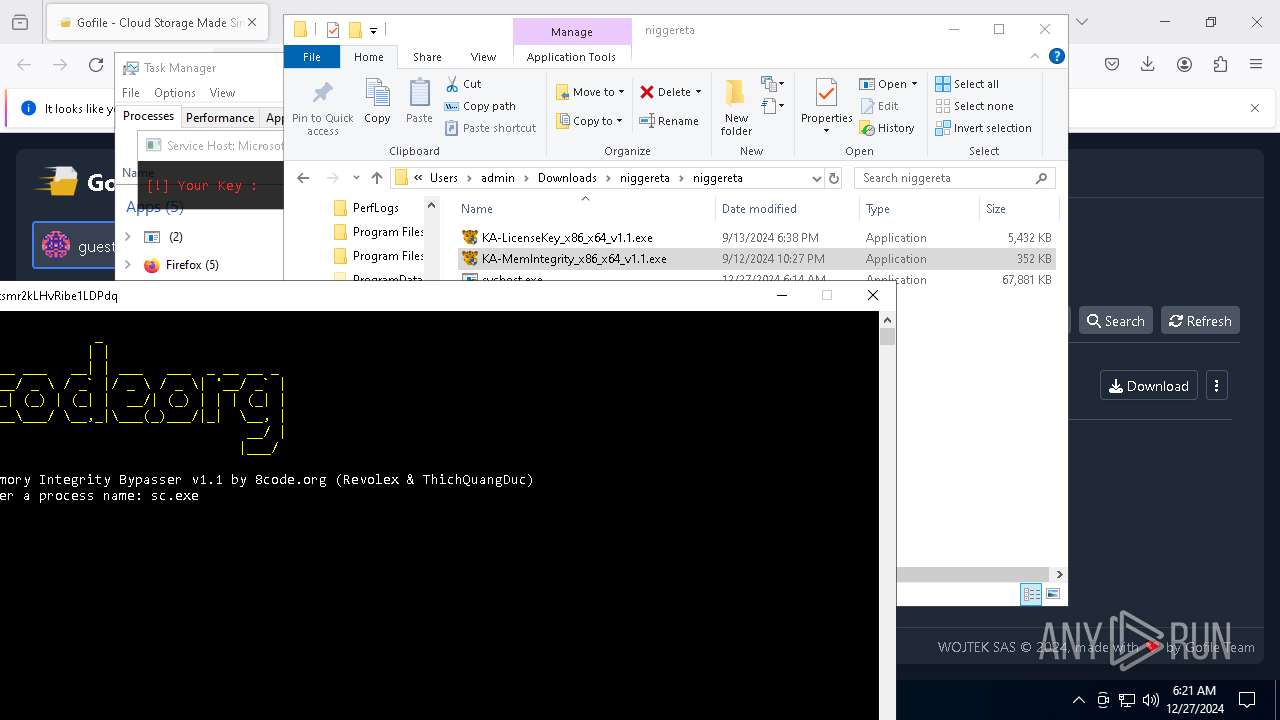
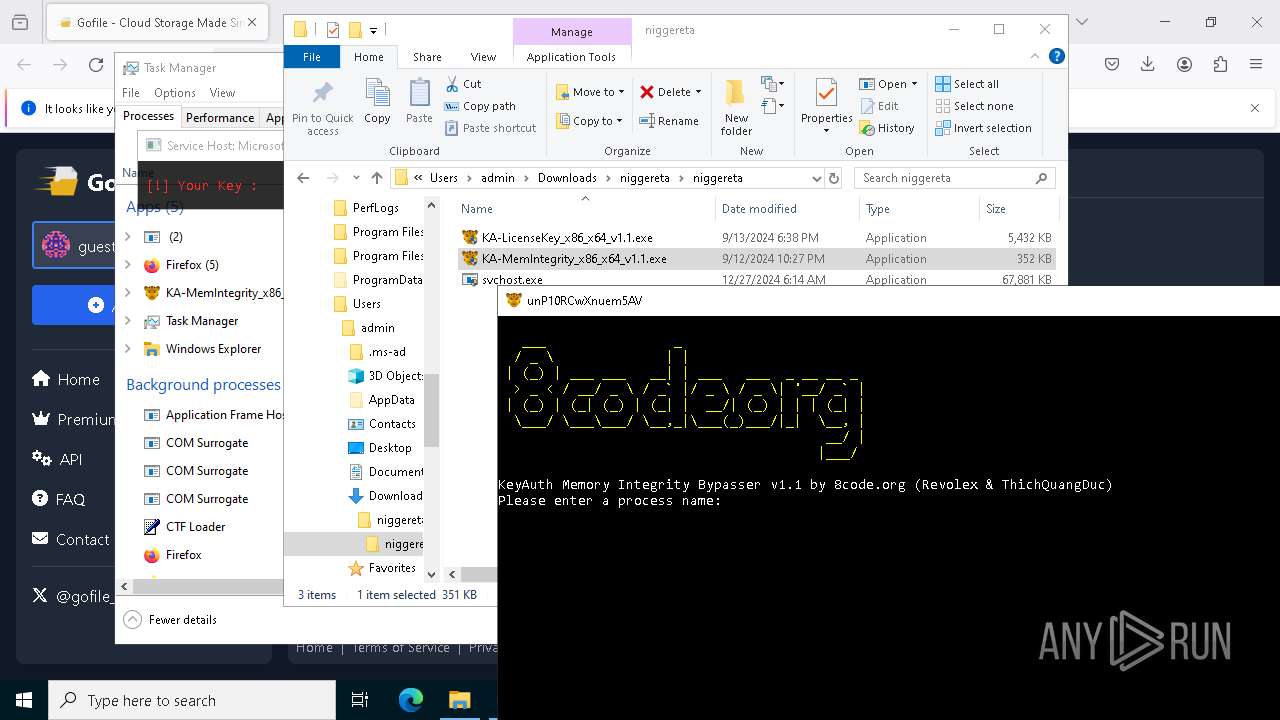
Starts SC.EXE for service management
- cmd.exe (PID: 2040)
- cmd.exe (PID: 6524)
- cmd.exe (PID: 8092)
Stops a currently running service
- sc.exe (PID: 5564)
- sc.exe (PID: 6632)
- sc.exe (PID: 2160)
Executes application which crashes
- svch0st.exe (PID: 5096)
INFO
Application launched itself
- firefox.exe (PID: 1668)
- firefox.exe (PID: 6176)
The process uses the downloaded file
- WinRAR.exe (PID: 3984)
- firefox.exe (PID: 6176)
Manual execution by a user
- WinRAR.exe (PID: 3984)
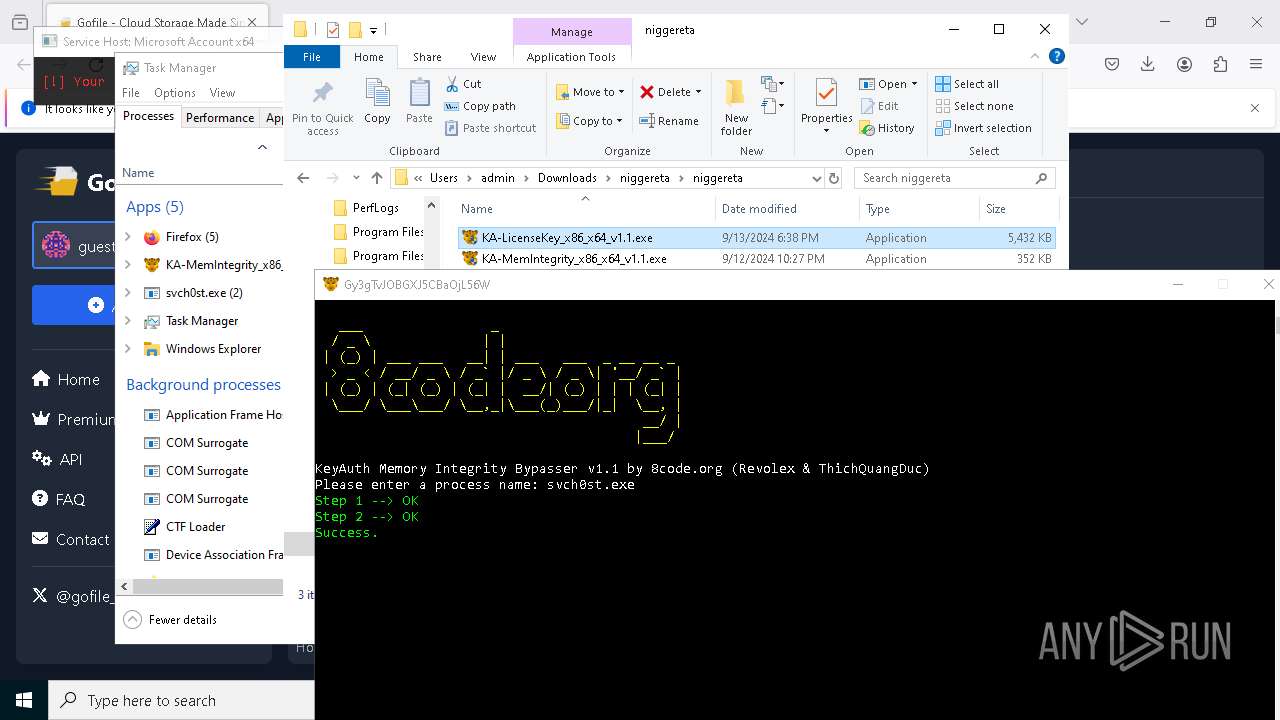
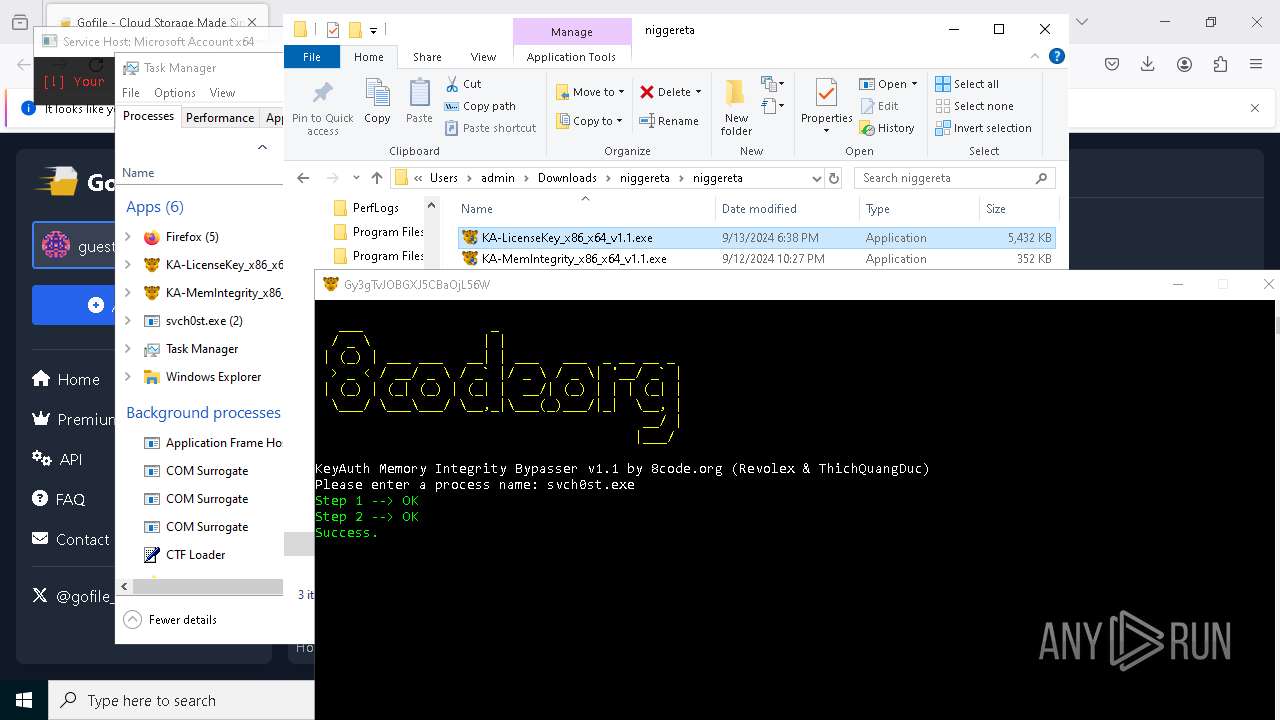
- svch0st.exe (PID: 4388)
- svch0st.exe (PID: 5096)
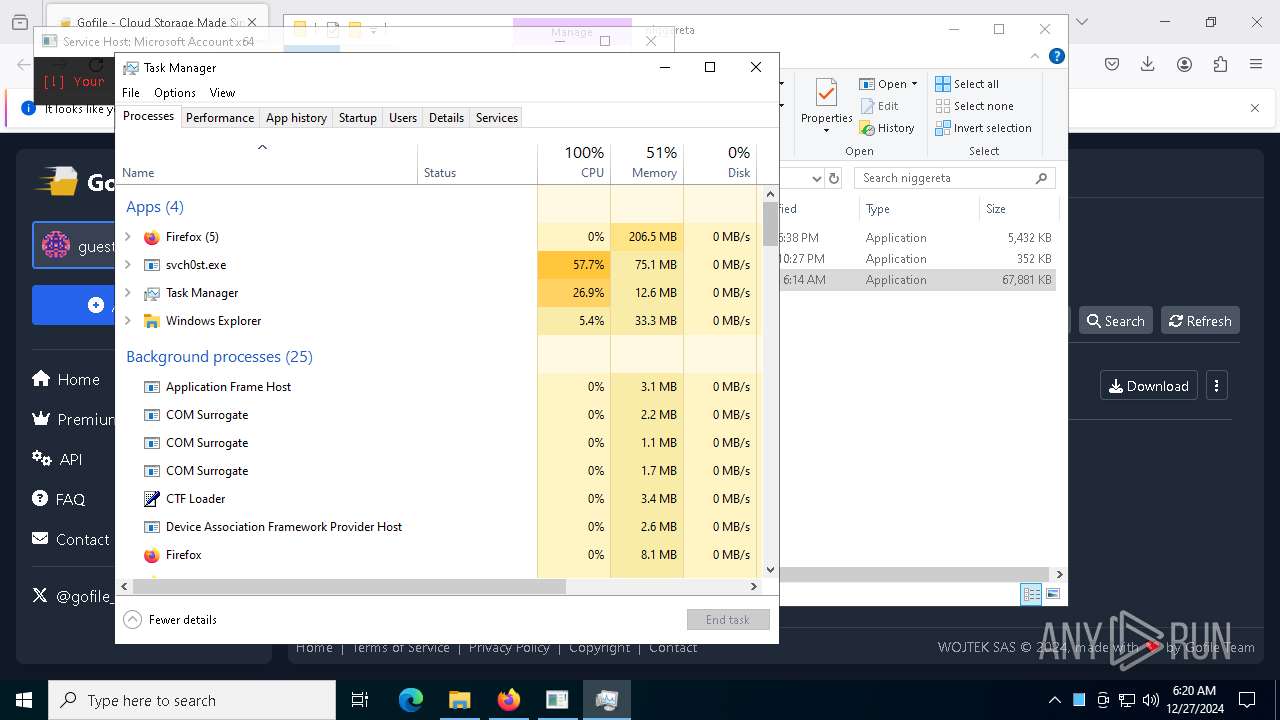
- Taskmgr.exe (PID: 3692)
- Taskmgr.exe (PID: 5200)
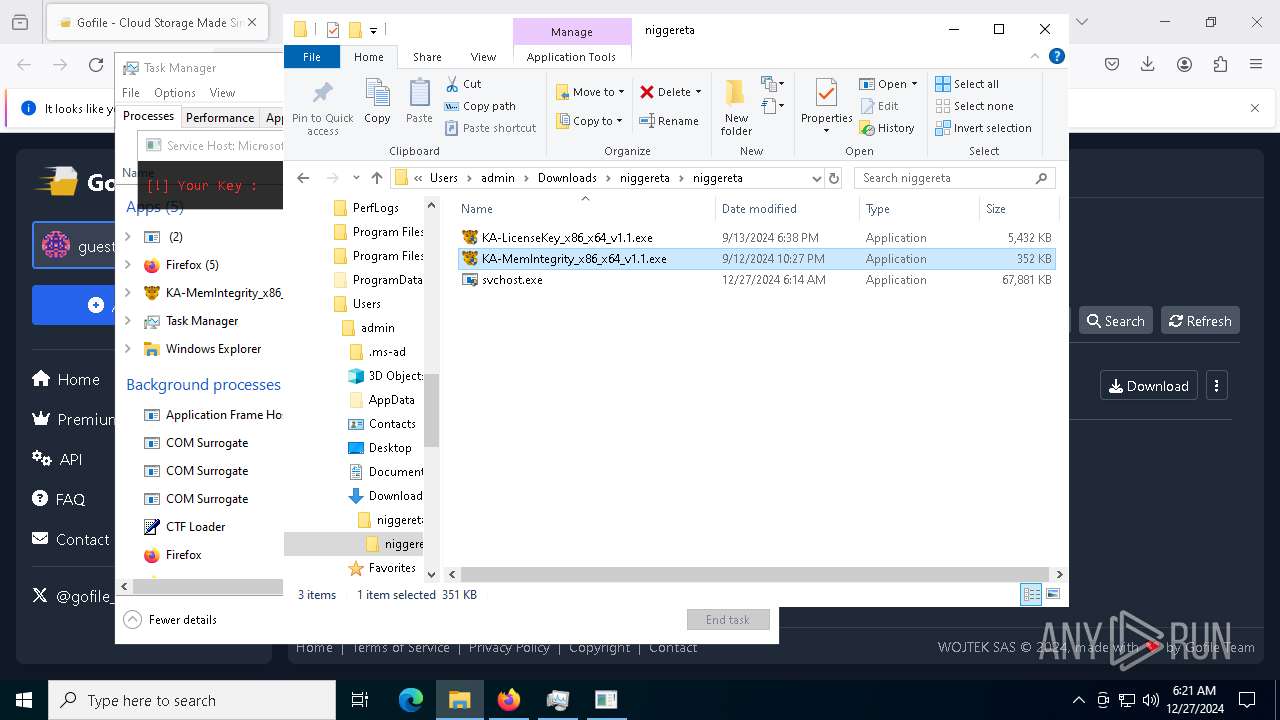
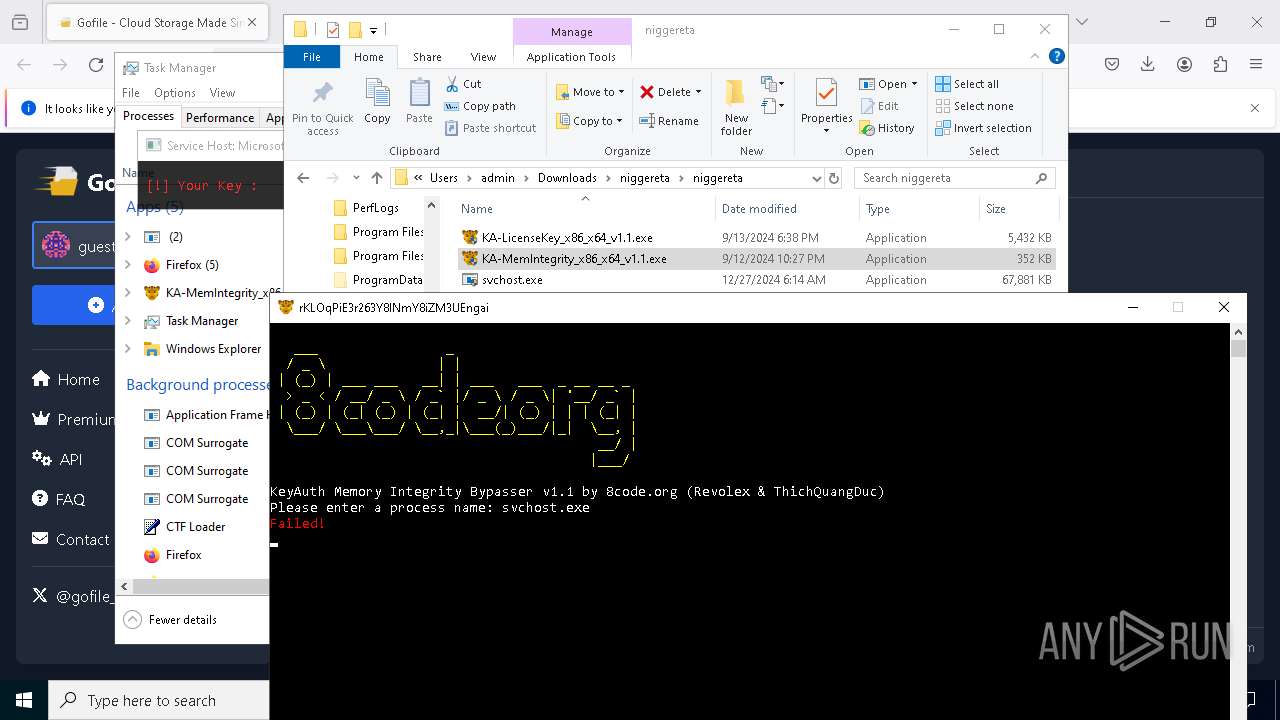
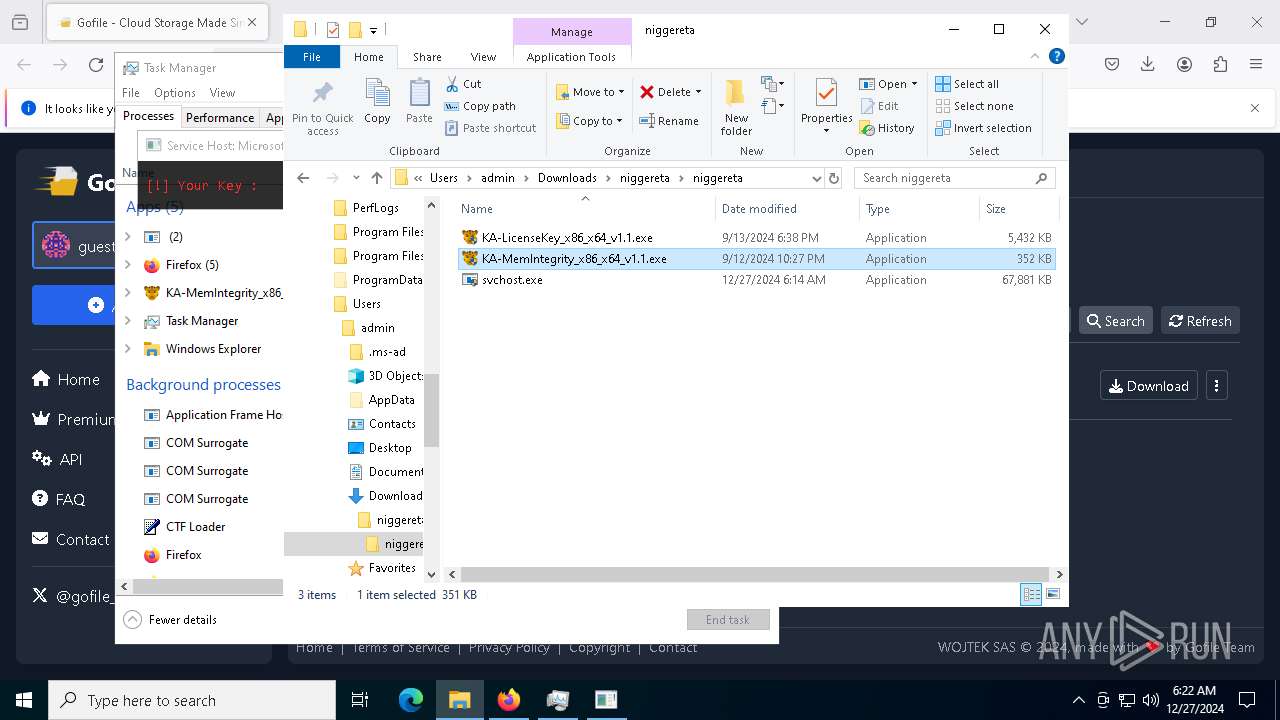
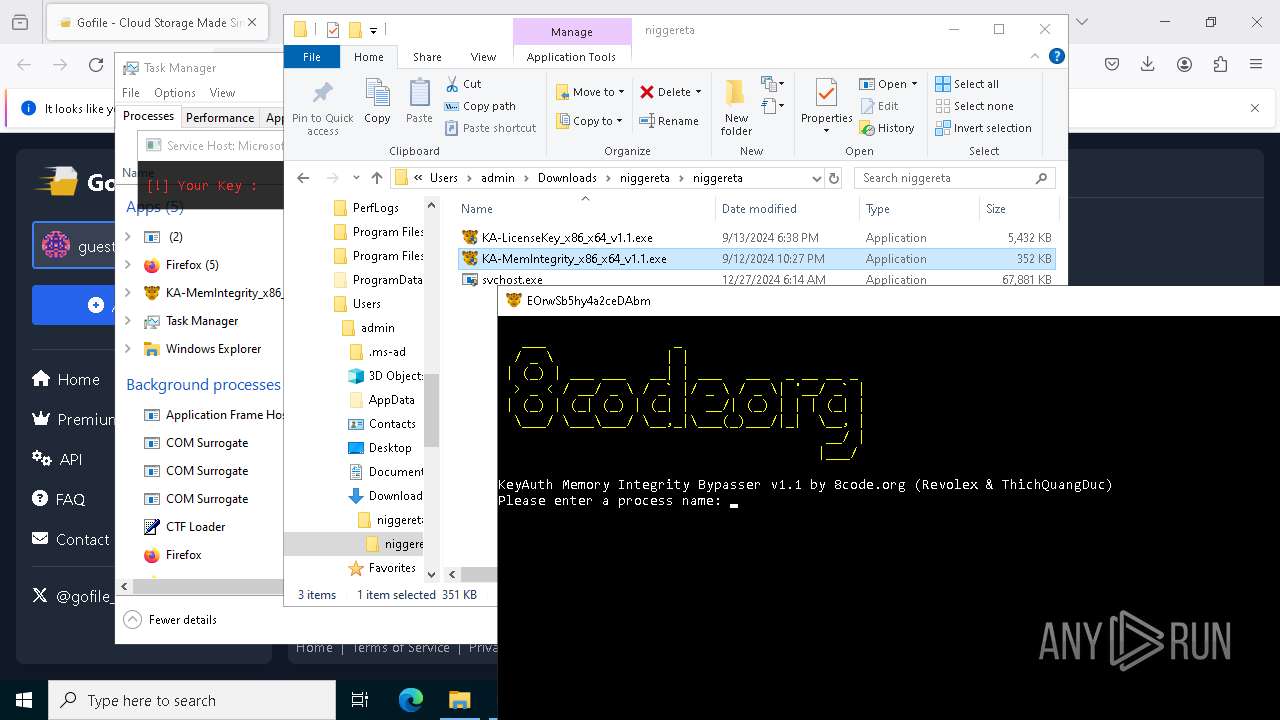
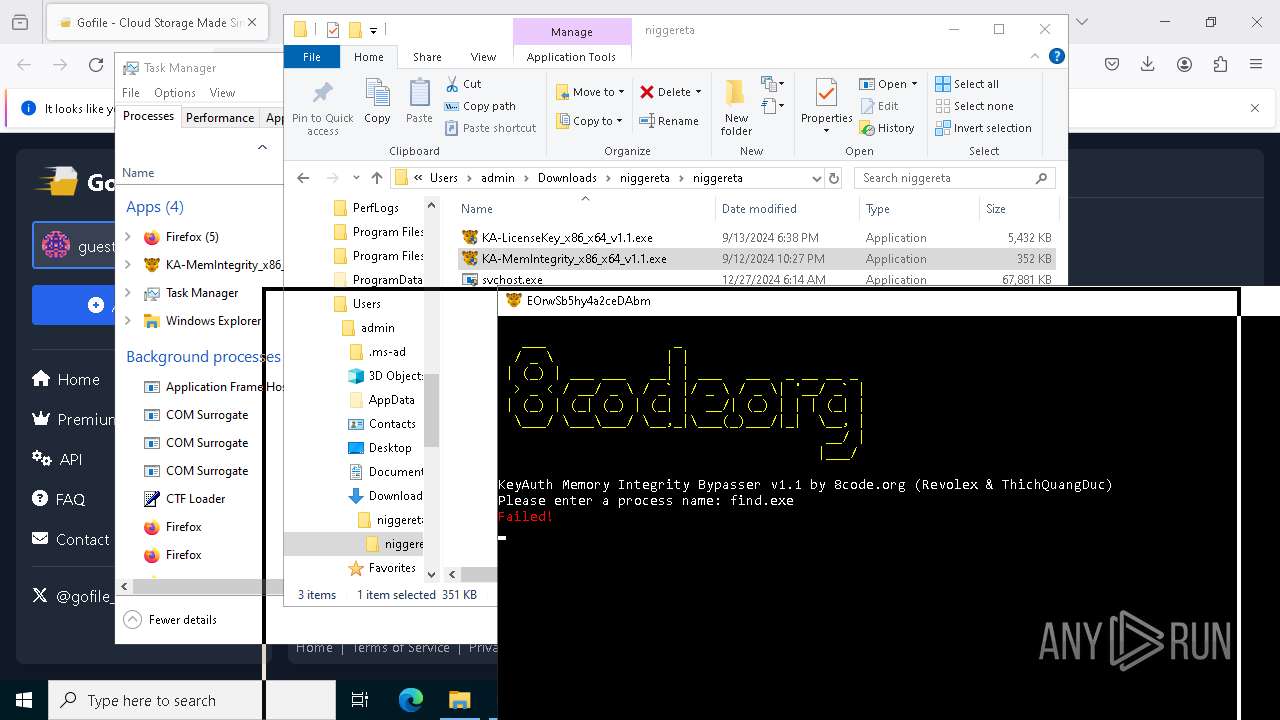
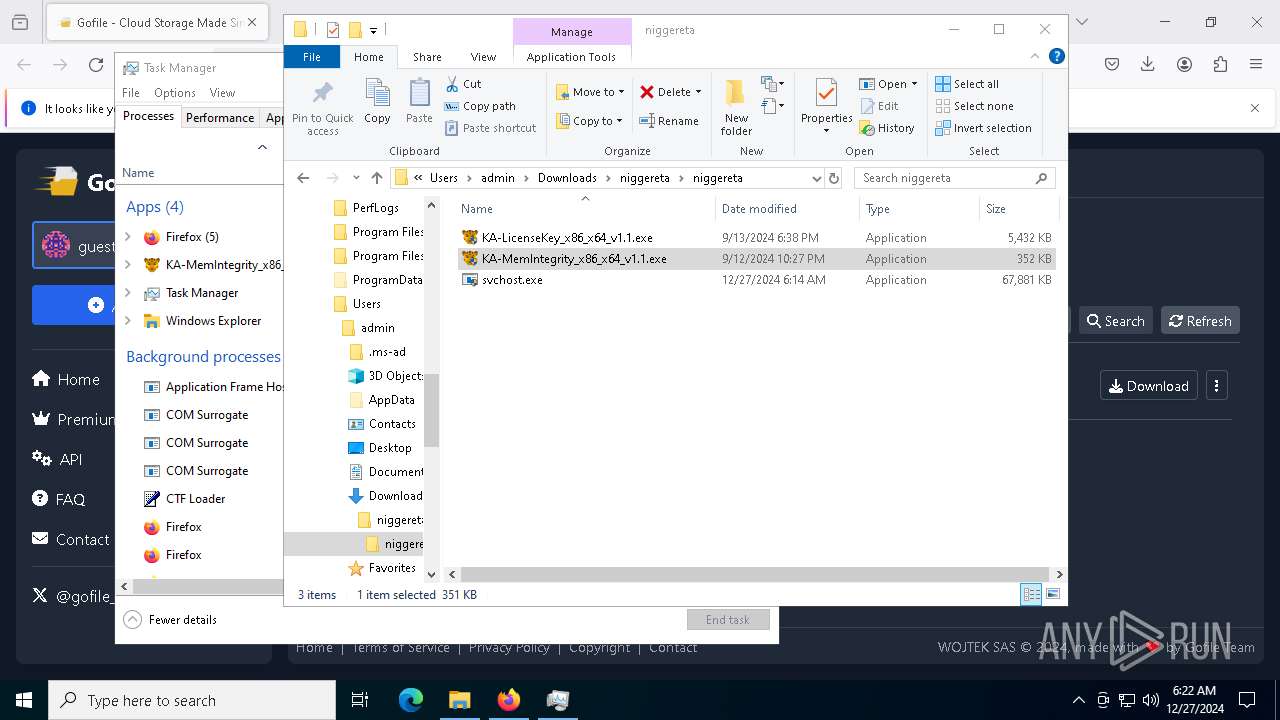
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 7608)
- svchost.exe (PID: 6588)
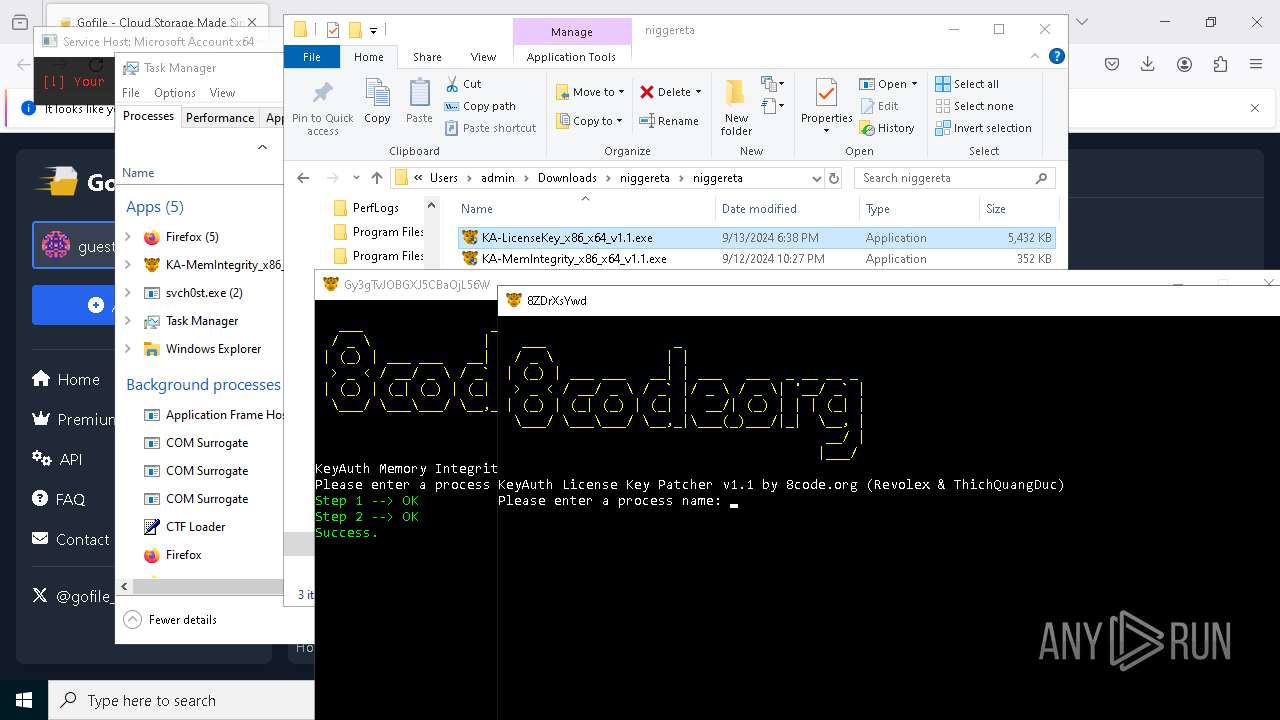
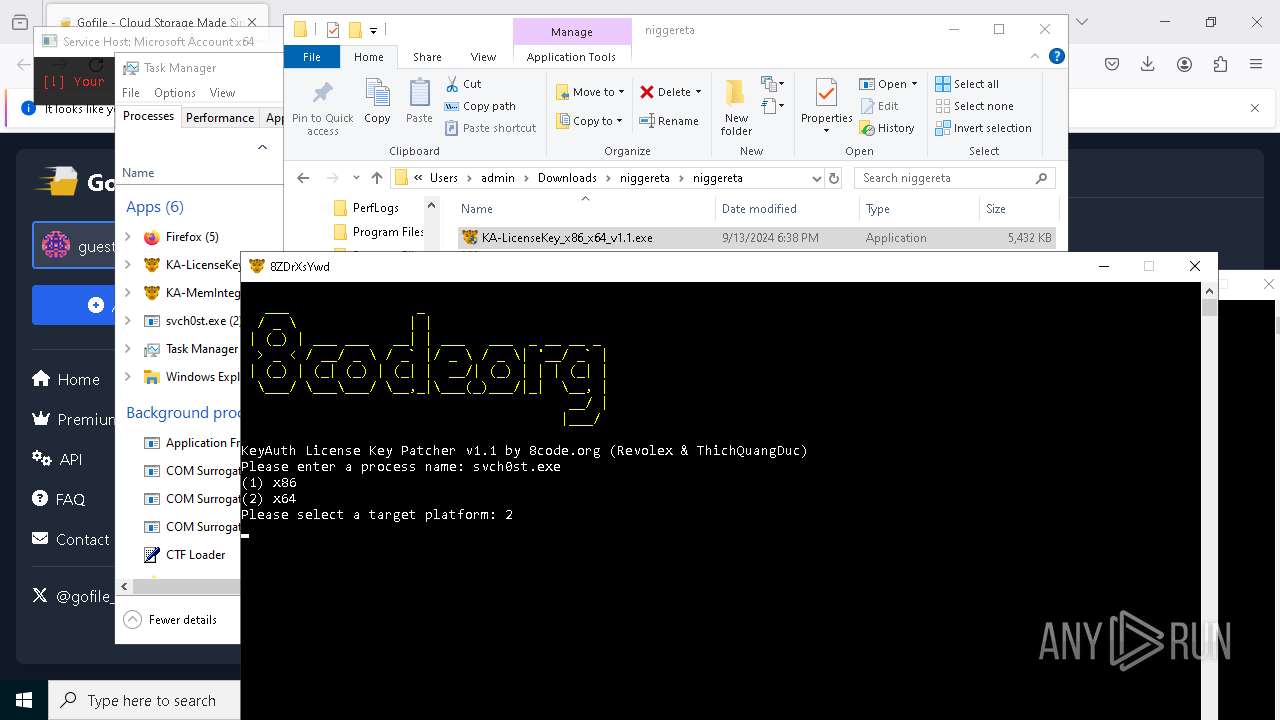
- KA-LicenseKey_x86_x64_v1.1.exe (PID: 1512)
- KA-LicenseKey_x86_x64_v1.1.exe (PID: 1536)
- svchost.exe (PID: 6484)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 7248)
- svchost.exe (PID: 2828)
- svchost.exe (PID: 624)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 6256)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 5876)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 4672)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 3884)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 6228)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 1140)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 4188)
- svchost.exe (PID: 6636)
- svchost.exe (PID: 8124)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 6456)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3984)
- firefox.exe (PID: 6176)
Sends debugging messages
- svch0st.exe (PID: 5096)
- svchost.exe (PID: 6484)
- svchost.exe (PID: 624)
- svchost.exe (PID: 6636)
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 5876)
- certutil.exe (PID: 1200)
- certutil.exe (PID: 6324)
- certutil.exe (PID: 4228)
Reads the computer name
- svch0st.exe (PID: 5096)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 7248)
- KA-LicenseKey_x86_x64_v1.1.exe (PID: 1536)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 6256)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 4188)
- svchost.exe (PID: 6636)
Checks supported languages
- mode.com (PID: 3544)
- svch0st.exe (PID: 5096)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 7248)
- KA-LicenseKey_x86_x64_v1.1.exe (PID: 1536)
- svchost.exe (PID: 6484)
- svchost.exe (PID: 624)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 6256)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 4672)
- KA-MemIntegrity_x86_x64_v1.1.exe (PID: 4188)
- svchost.exe (PID: 6636)
- mode.com (PID: 2152)
Starts MODE.COM to configure console settings
- mode.com (PID: 3544)
- mode.com (PID: 7760)
- mode.com (PID: 2152)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3692)
Creates files in the program directory
- svch0st.exe (PID: 5096)
- svchost.exe (PID: 6484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
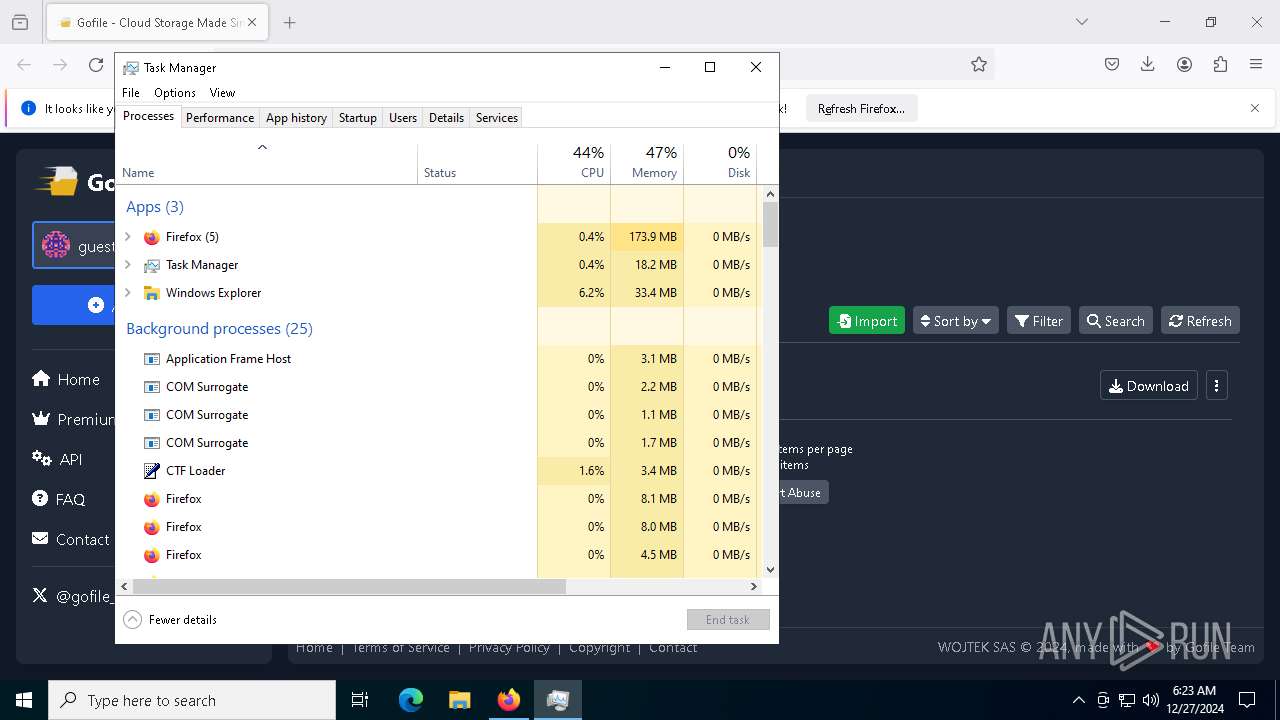
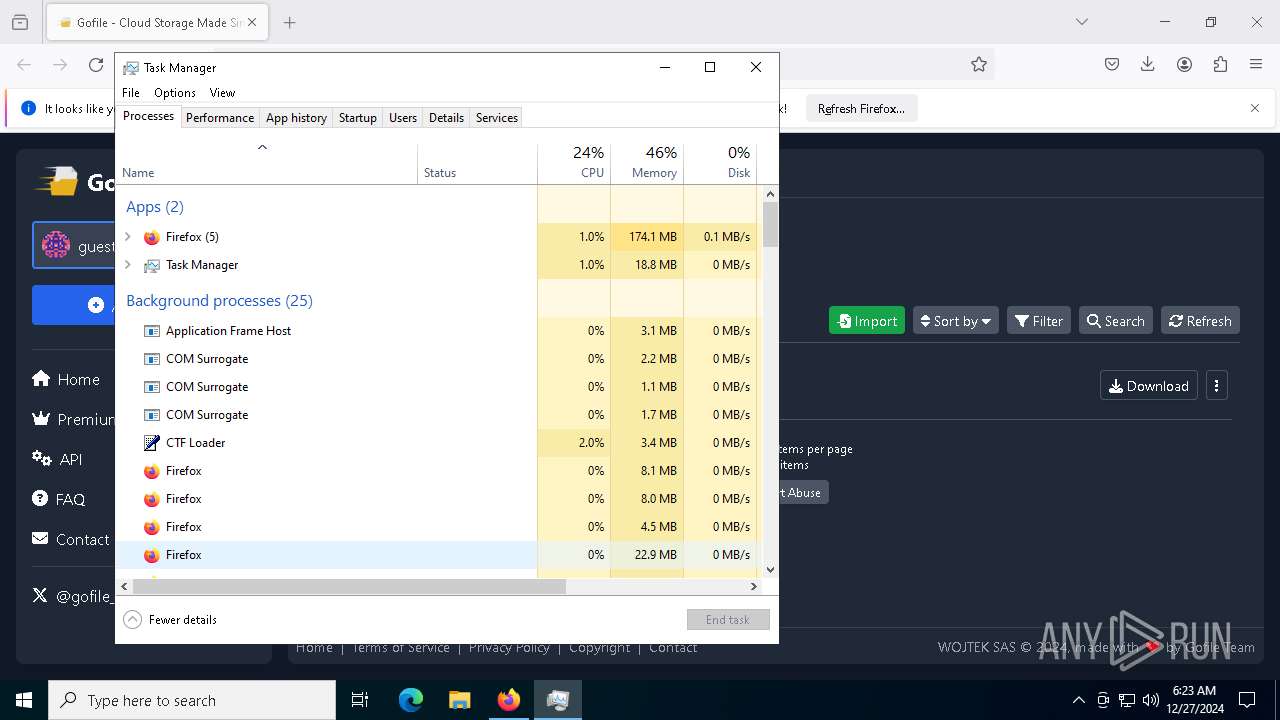
Total processes
268
Monitored processes
129
Malicious processes
3
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | taskkill /FI "IMAGENAME eq cheatengine*" /IM * /F /T | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | taskkill /FI "IMAGENAME eq processhacker*" /IM * /F /T | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
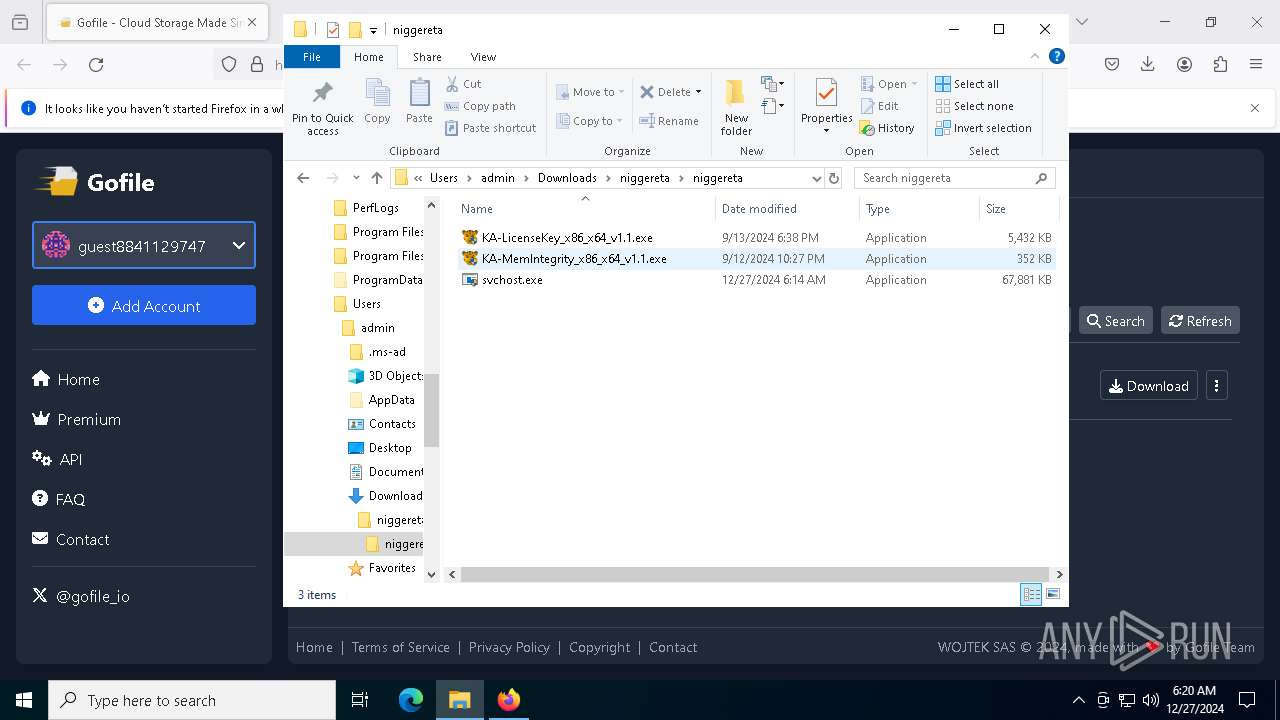
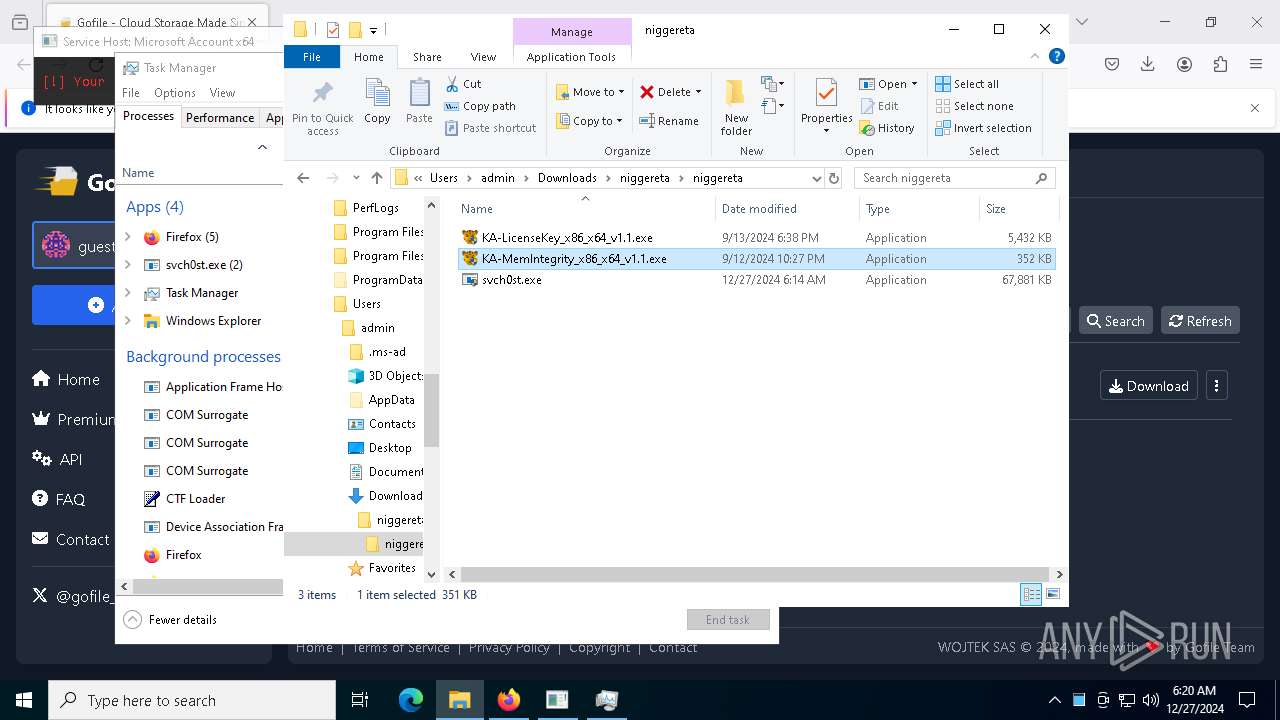
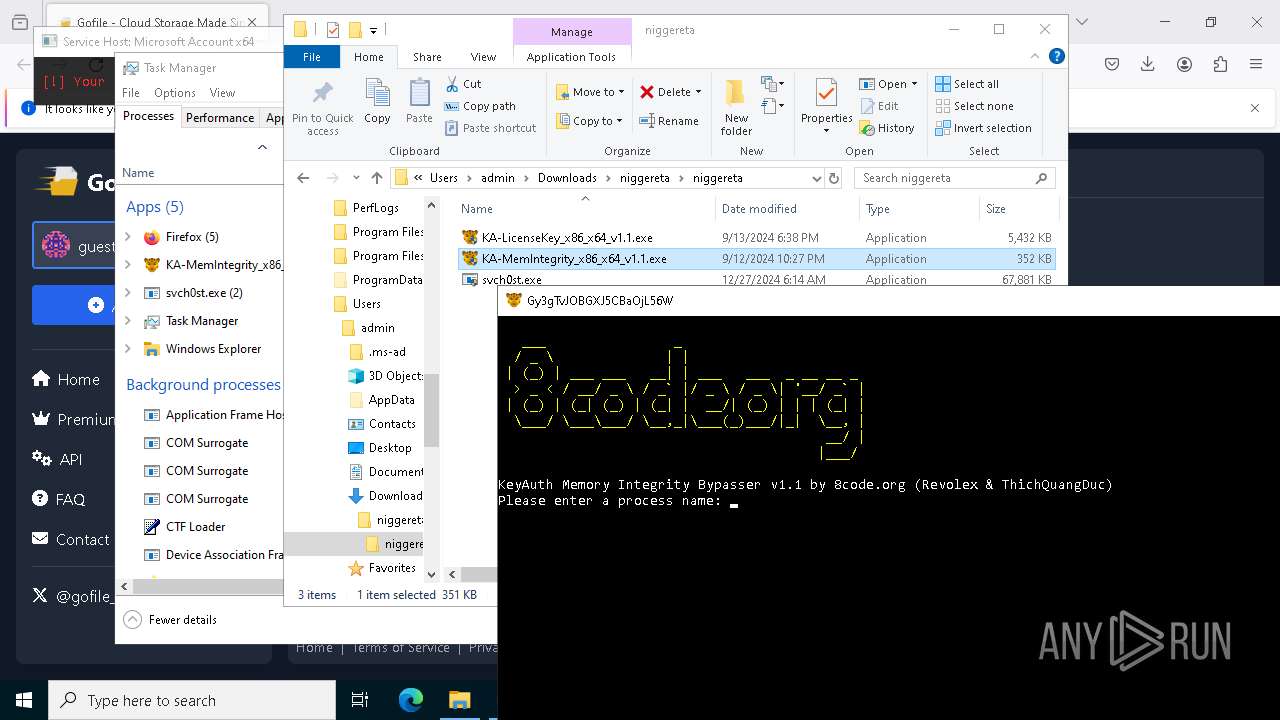
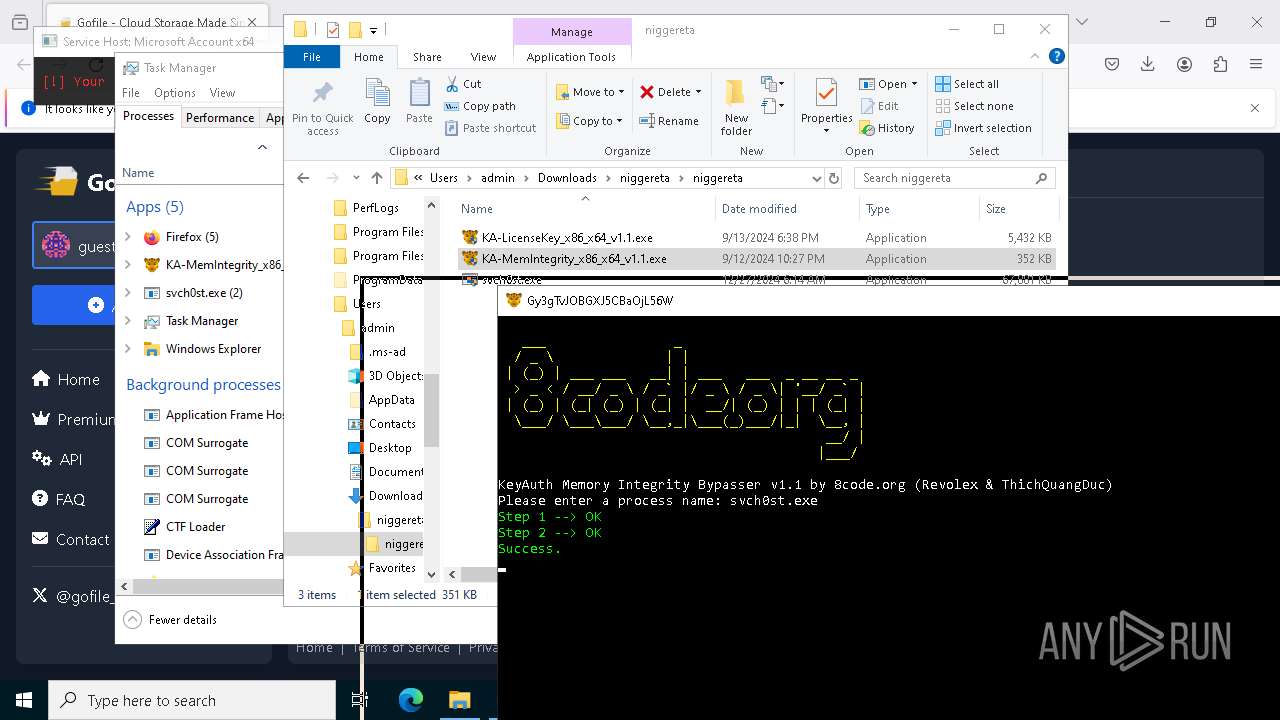
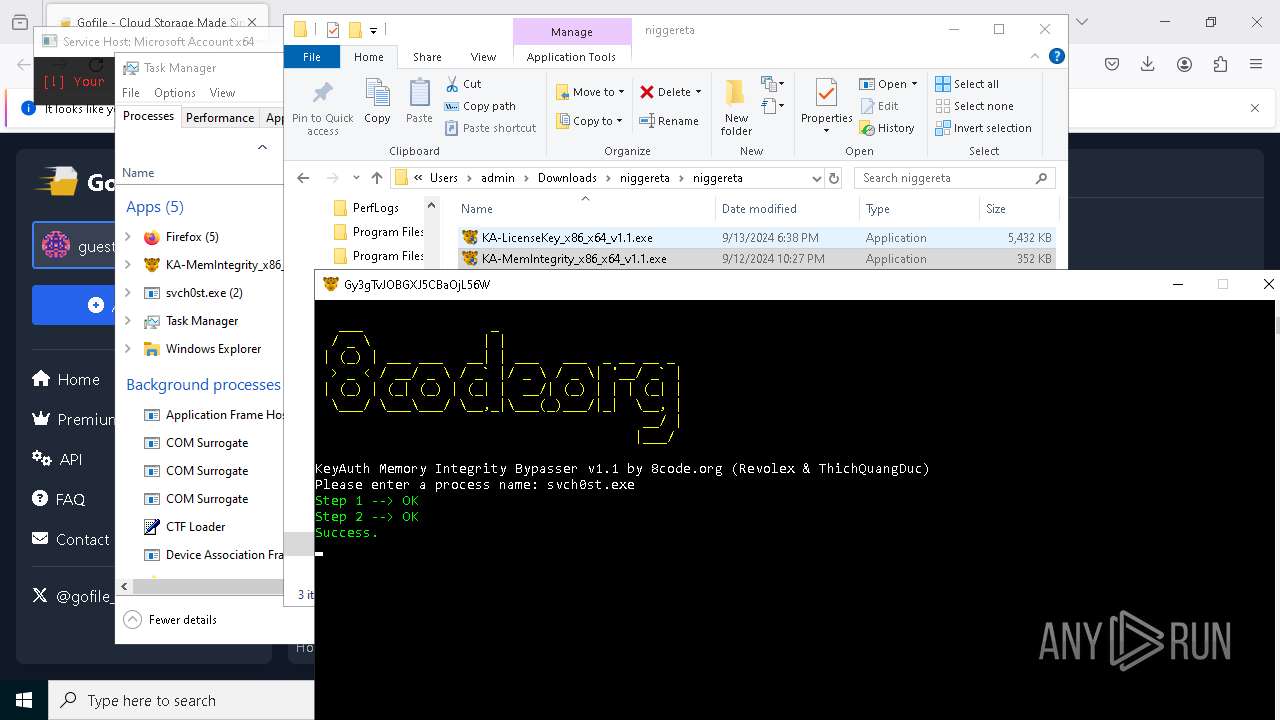
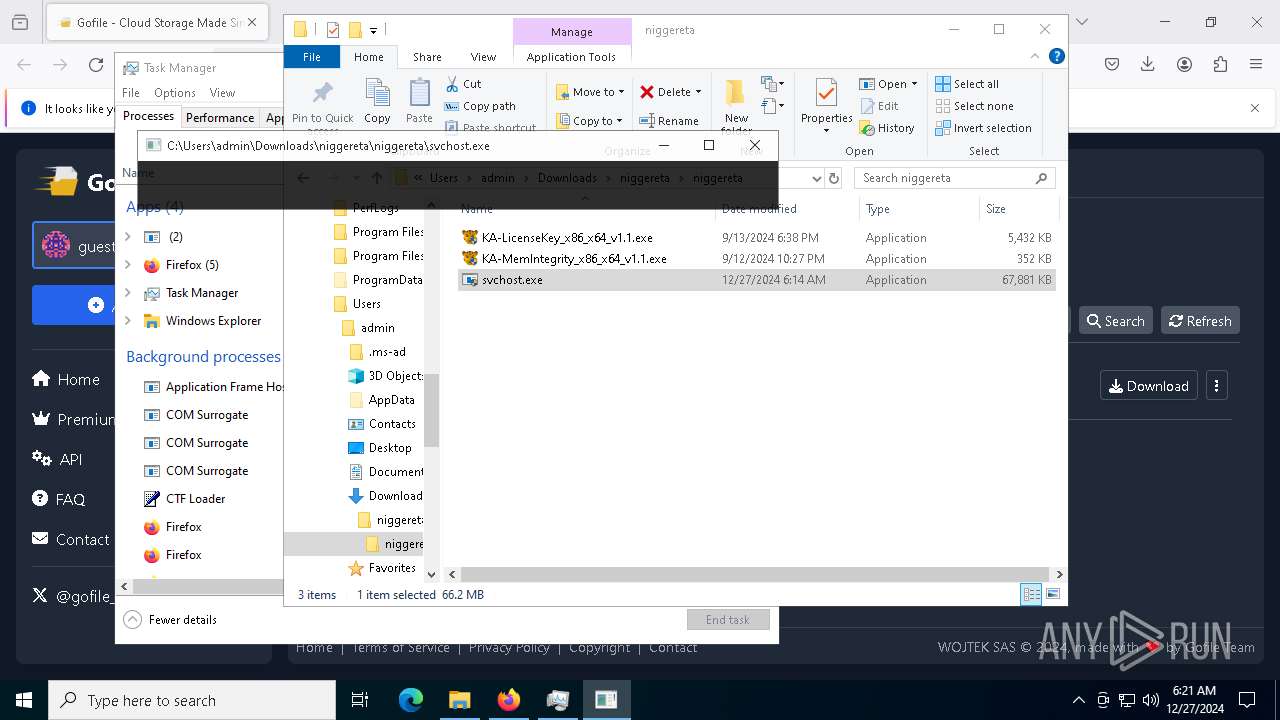
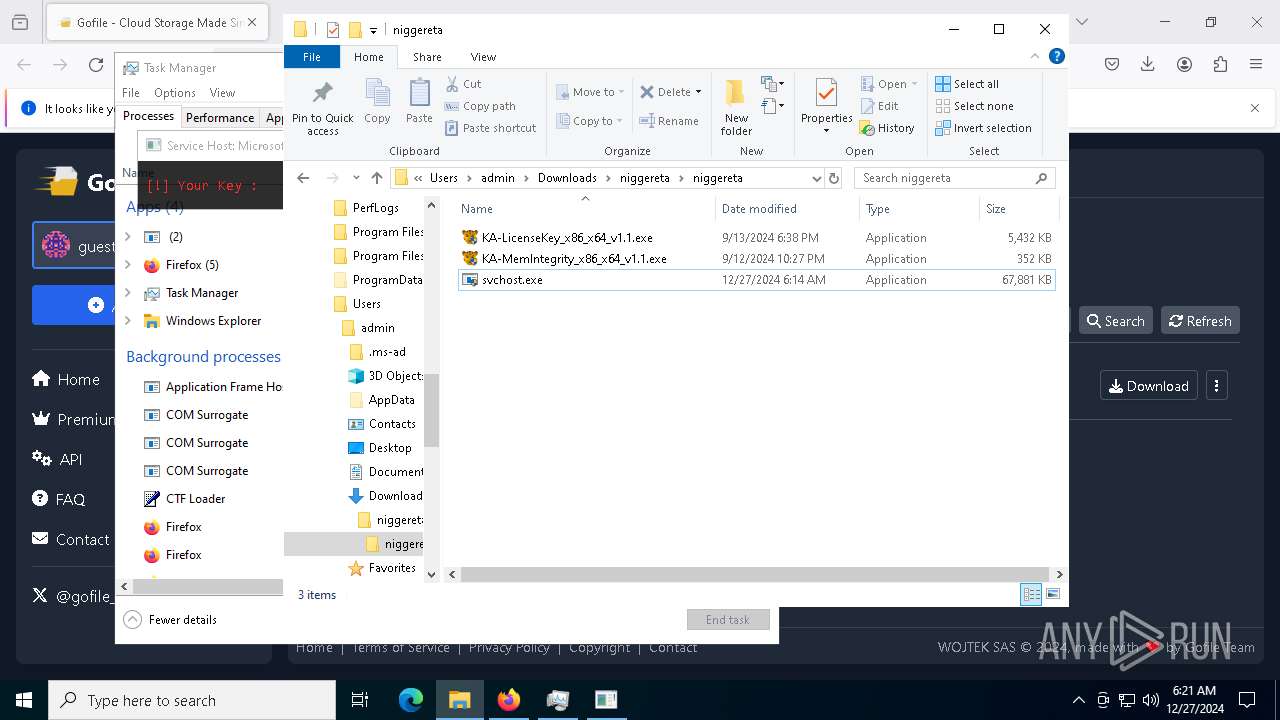
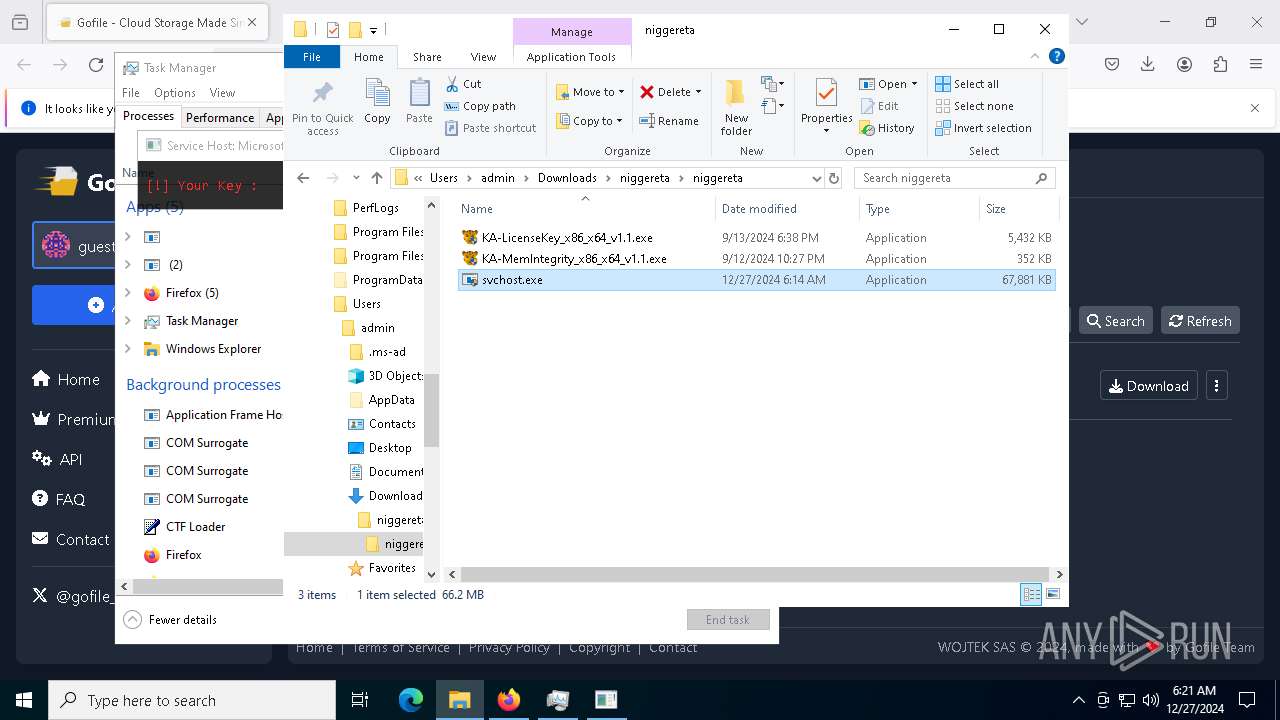
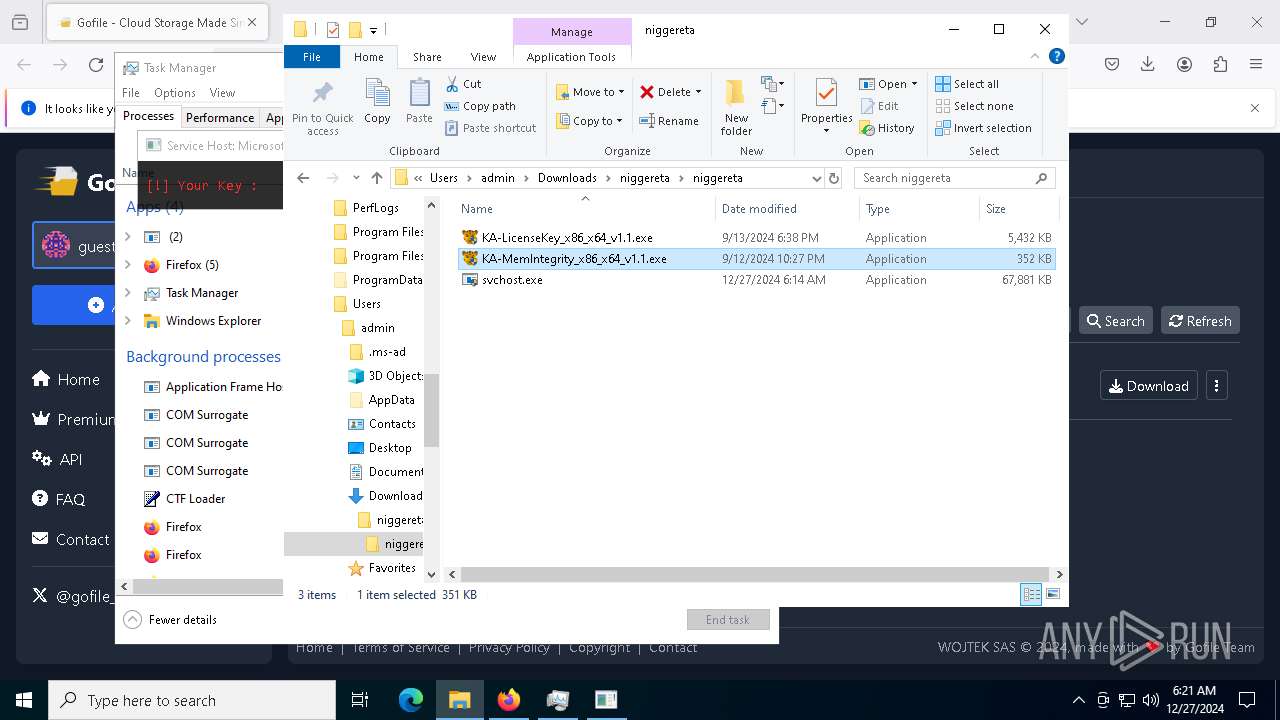
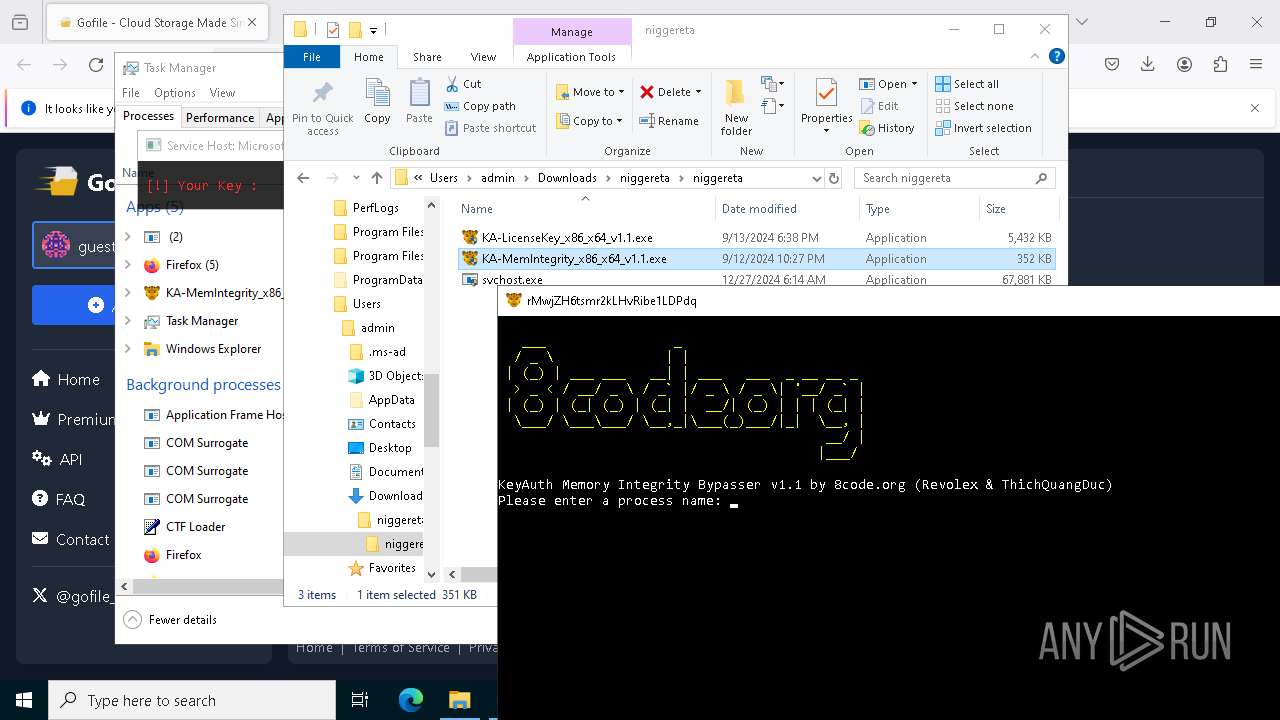
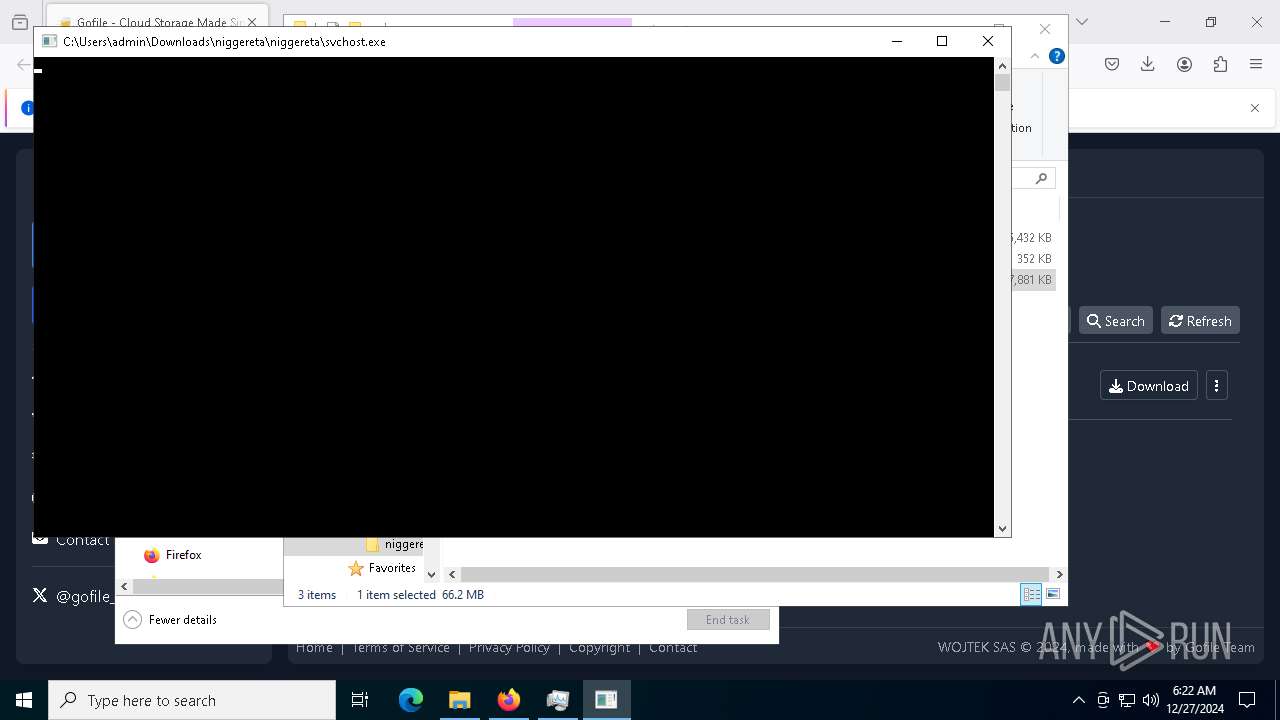
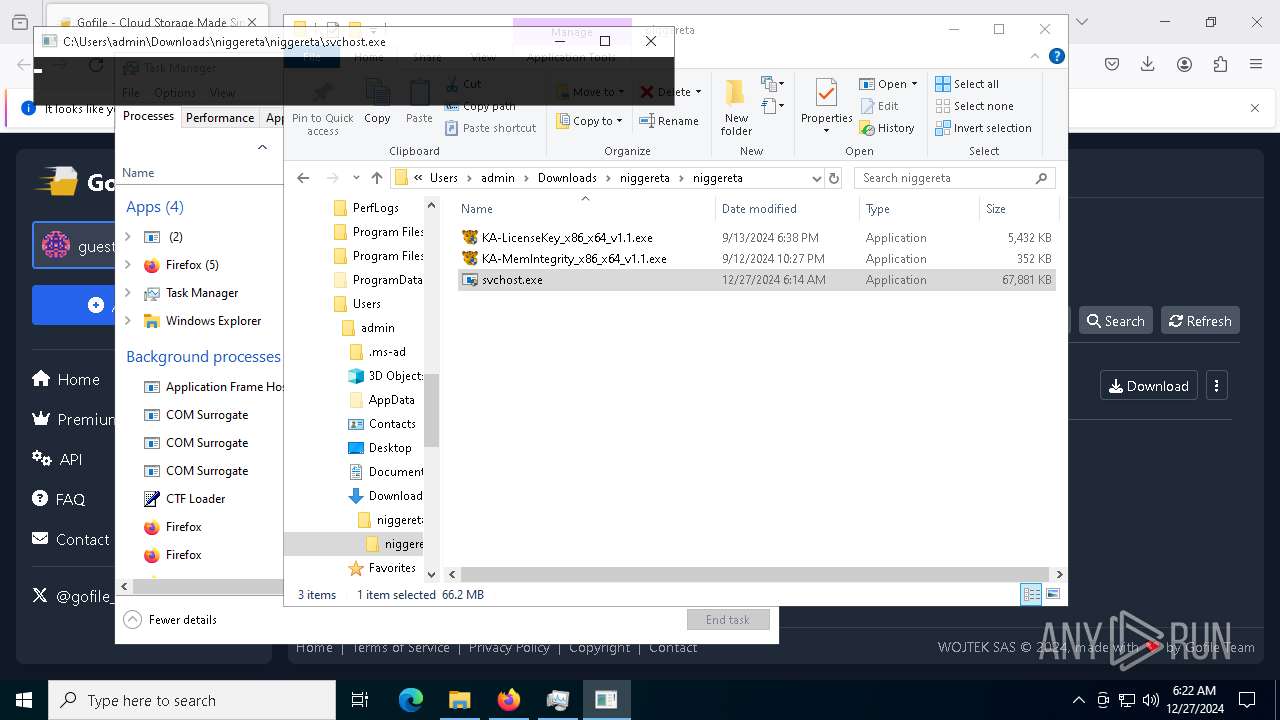
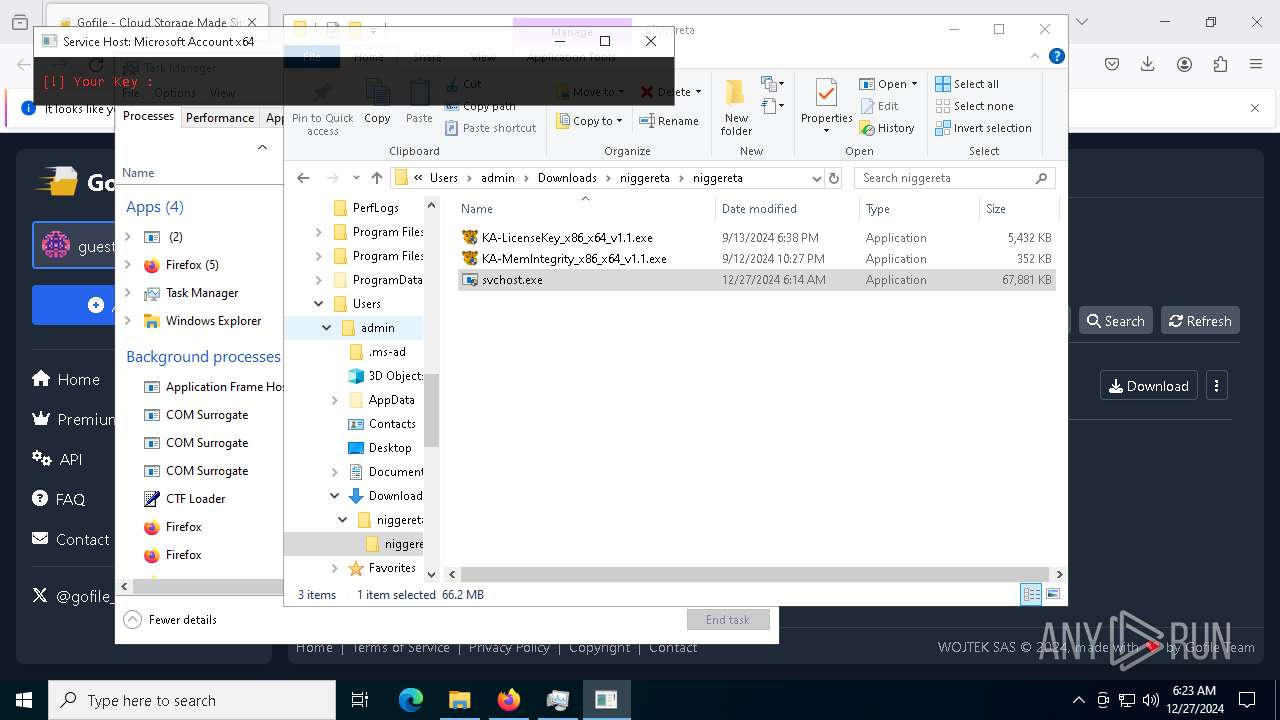
| 624 | "C:\Users\admin\Downloads\niggereta\niggereta\svchost.exe" | C:\Users\admin\Downloads\niggereta\niggereta\svchost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | KA-MemIntegrity_x86_x64_v1.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | taskkill /f /im HTTPDebuggerUI.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 932 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | svch0st.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1016 | taskkill /f /im HTTPDebuggerSvc.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\cmd.exe /c taskkill /f /im HTTPDebuggerUI.exe >nul 2>&1 | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\Downloads\niggereta\niggereta\KA-MemIntegrity_x86_x64_v1.1.exe" | C:\Users\admin\Downloads\niggereta\niggereta\KA-MemIntegrity_x86_x64_v1.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1172 | taskkill /FI "IMAGENAME eq httpdebugger*" /IM * /F /T | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 131
Read events
9 122
Write events
8
Delete events
1
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5876) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (5876) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (5876) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (3692) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (3692) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AA6C15F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AA6C15F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AA6C15F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000AB6C15F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028AB6C15F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050AB6C15F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AA6C15F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070AB6C15F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088AB6C15F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8AB6C15F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8AB6C15F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0AB6C15F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010AC6C15F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AA6C15F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040AC6C15F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068AC6C15F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090AC6C15F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8AC6C15F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8AC6C15F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8AC6C15F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028AB6C15F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AA6C15F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020AD6C15F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068AD6C15F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AA6C15F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050AB6C15F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AA6C15F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070AB6C15F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088AB6C15F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8AB6C15F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8AB6C15F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AA6C15F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0AD6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AE6C15F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AE6C15F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AE6C15F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
Executable files
4
Suspicious files
167
Text files
31
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6176 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | dbf | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:6134B34D6660F33DF298E2237D57CDA9 | SHA256:798625D952D0FBD47C85C6DB7A671649C70BAB0E3FF279F4F18AD1C108624934 | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:3B156E12141F8CBCE9D60CDCE2077617 | SHA256:E6287E44B44ABEA20E1B2E3F415D22B9E5E5FBBC155AD9DADBABA63951B2AF6F | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6176 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
116
DNS requests
122
Threats
51
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5340 | svchost.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5340 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
— | — | POST | 200 | 95.101.54.131:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 95.101.54.131:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
— | — | POST | 200 | 95.101.54.131:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5340 | svchost.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5340 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 142.250.185.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
— | — | 34.117.188.166:443 | contile.services.mozilla.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
gofile.io |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
Process | Message |
|---|---|
svch0st.exe | X Security |
svch0st.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
svchost.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
svchost.exe | X Security |
svchost.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
svchost.exe | X Security |
svchost.exe | X Security |
svchost.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |