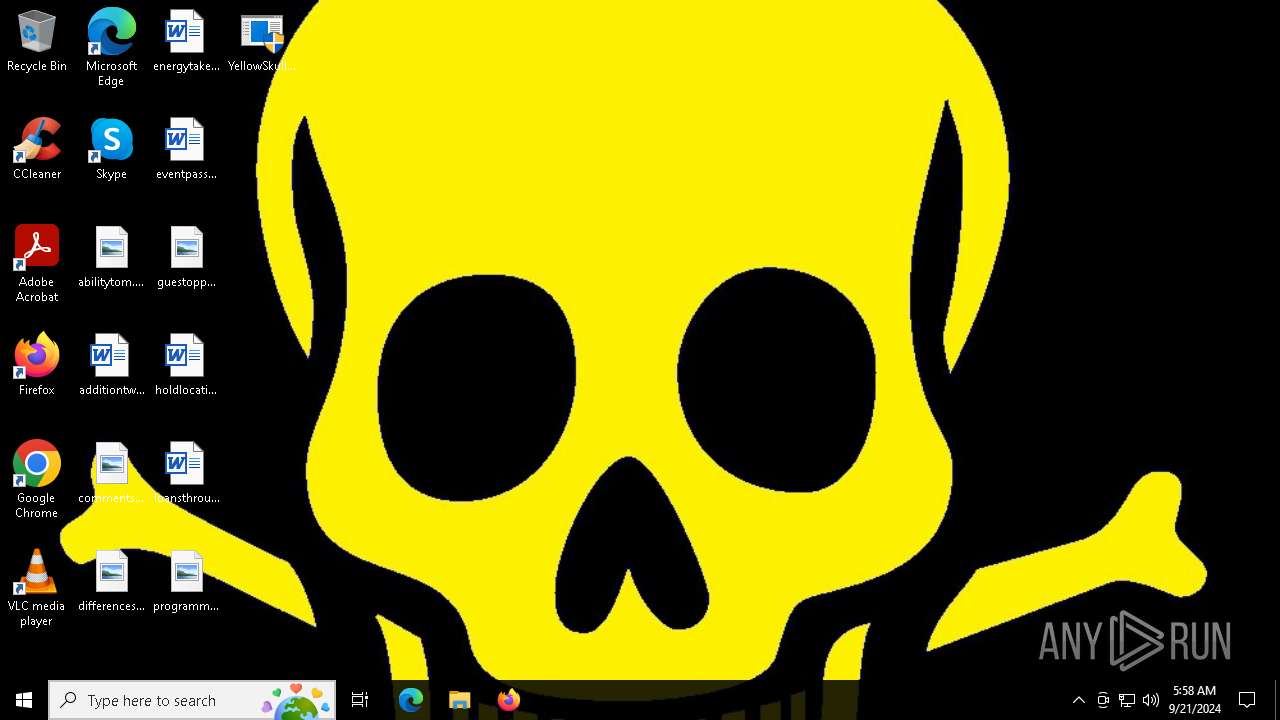
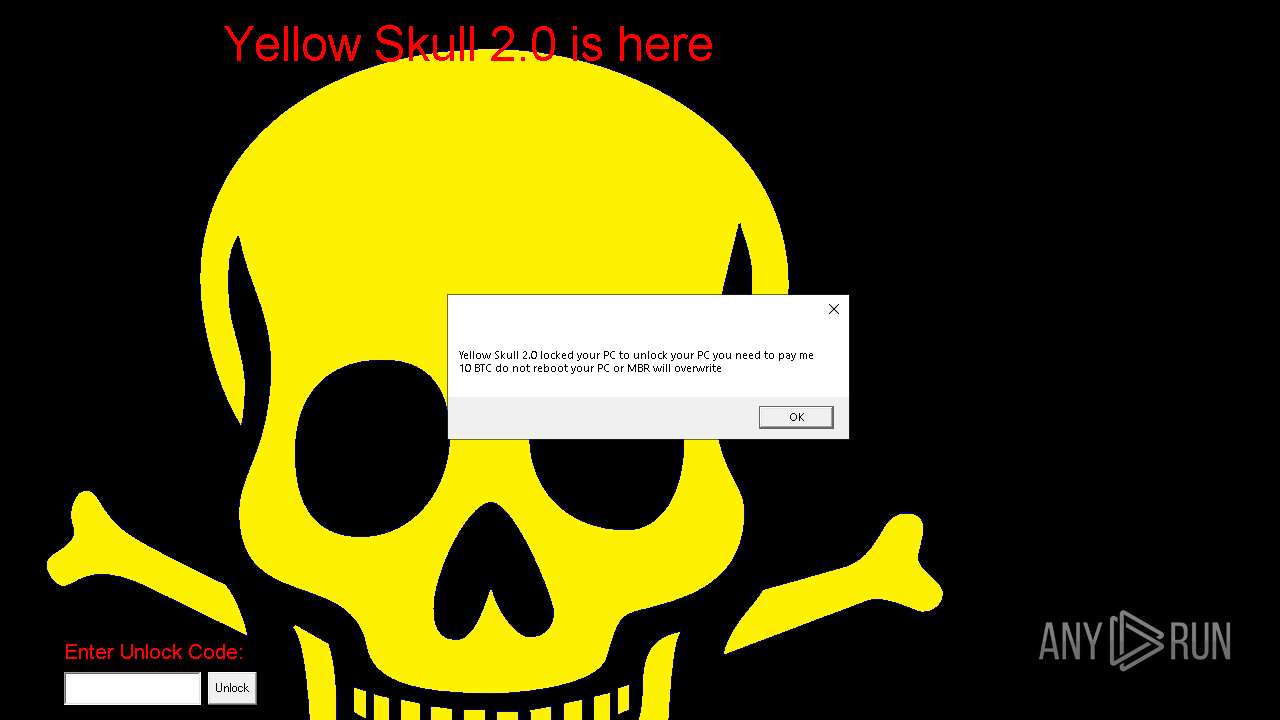
| File name: | YellowSkull2.0.exe |
| Full analysis: | https://app.any.run/tasks/f76385b1-1aed-4c4f-a201-ec94f39d0181 |
| Verdict: | Malicious activity |
| Analysis date: | September 21, 2024, 05:58:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 660E26001A8891E78135A09D3EC2623F |
| SHA1: | BD95C1955BE08EAECEFA7B3DD1CBDAC7387B6D06 |
| SHA256: | 1811C7B5DDCC6637A782BF32DB70B60BD0BF3EC2B3498716591F718CDA25FD14 |
| SSDEEP: | 49152:cCEz1VWQraflEcY8GSFJ2CBUm5htDRvG0JuH0Xv6GVO8UKlo6:cn14QilESfFim15rtxUuo6 |
MALICIOUS
Disables the LogOff the Start menu
- reg.exe (PID: 6256)
UAC/LUA settings modification
- reg.exe (PID: 6364)
Changes the autorun value in the registry
- reg.exe (PID: 2932)
SUSPICIOUS
Executable content was dropped or overwritten
- YellowSkull2.0.exe (PID: 6768)
- cmd.exe (PID: 3768)
Reads security settings of Internet Explorer
- YellowSkull2.0.exe (PID: 6768)
Executing commands from a ".bat" file
- YellowSkull2.0.exe (PID: 6768)
Creates file in the systems drive root
- cmd.exe (PID: 3768)
Starts CMD.EXE for commands execution
- YellowSkull2.0.exe (PID: 6768)
Changes the desktop background image
- reg.exe (PID: 6148)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3768)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3768)
The executable file from the user directory is run by the CMD process
- bg.exe (PID: 1920)
- YSkullLock.exe (PID: 5548)
The process executes VB scripts
- cmd.exe (PID: 3768)
INFO
Checks supported languages
- YellowSkull2.0.exe (PID: 6768)
- bg.exe (PID: 1920)
- YSkullLock.exe (PID: 5548)
Create files in a temporary directory
- YellowSkull2.0.exe (PID: 6768)
Process checks computer location settings
- YellowSkull2.0.exe (PID: 6768)
Reads the computer name
- YellowSkull2.0.exe (PID: 6768)
- bg.exe (PID: 1920)
- YSkullLock.exe (PID: 5548)
The process uses the downloaded file
- YellowSkull2.0.exe (PID: 6768)
- cmd.exe (PID: 3768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 2592768 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 7725056 |
| EntryPoint: | 0x9d66b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | Yellow Skull Virus 2.0 |
| FileVersion: | 2,0,0,0 |
| ProductVersion: | 2,0,0,0 |
Total processes
174
Monitored processes
52
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 884 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | reg.exe ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v ConsentPromptBehaviorAdmin /t REG_DWORD /d 0 /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | taskkill /f /im explorer.exe | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1920 | bg.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\bg.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2324 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2472 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\SysWOW64\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 398
Read events
4 388
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3768) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6148) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: c:\yellowskull.bmp | |||
| (PID) Process: | (6648) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (6332) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | HideFastUserSwitching |
Value: 1 | |||
| (PID) Process: | (3448) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableChangePassword |
Value: 1 | |||
| (PID) Process: | (4180) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableLockWorkstation |
Value: 1 | |||
| (PID) Process: | (6256) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoLogoff |
Value: 1 | |||
| (PID) Process: | (1184) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (6364) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (2932) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | YellowSkull2 Special Program |
Value: C:\YSkullMBRSetup.exe | |||
Executable files
4
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\bg.wav | wav | |
MD5:832B350B50A07906C630A2B8819FD209 | SHA256:94E1CECF8ED740EA45C87927DE31005C3B2F9DB261AAE04FE56A81E337D1E8DA | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\YellowSkull.bmp | image | |
MD5:11BCDA64D254AD8DC591B41F8FCEB04D | SHA256:84C5DAD2D4CEC5B636C1FAE6F1E1482ADA9F62363DCF269B4A86F6070D5B50FC | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\bg.cpp | text | |
MD5:A4F885352ED45CF37331BD01EC5B838A | SHA256:7032FD15B3B95CC3F0637BB8F8463E0848B5C2767C1CF4109EC34D7E2861322C | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\YellowSkull2.bat | text | |
MD5:4671D5895D88BC19645CAB0FC7CA398A | SHA256:DD8AA9F7955674A7A1B5B222D7C1809C583C705DAE8BF476CDD42EFCC0AFABB5 | |||
| 3768 | cmd.exe | C:\YellowSkull.bmp | image | |
MD5:11BCDA64D254AD8DC591B41F8FCEB04D | SHA256:84C5DAD2D4CEC5B636C1FAE6F1E1482ADA9F62363DCF269B4A86F6070D5B50FC | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\YSkullMBRSetup.cpp | text | |
MD5:47E463410CB8131ADACC9DCC7259D18B | SHA256:4A72771CA59099094242F733D396F775946ED59E03C2AD680517530CA8A070B7 | |||
| 3768 | cmd.exe | C:\YSkullMBRSetup.exe | executable | |
MD5:220303EB72EBDE4605116640FB719B26 | SHA256:F081C913488C3F22B62F906DAC2A82A38D085EBE1D28701F0059DFDFBF1CCF42 | |||
| 3768 | cmd.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\k.vbs | text | |
MD5:08121EA7E3B2EB7EDFC85252B937AAEB | SHA256:31CD4463ECC62DC846DBAEE0A5446D4BF11100BEFF1B01AE88E234B6C29329C2 | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\YSkullLock.exe | executable | |
MD5:2191C3A14B53531E82726B17DD331CEF | SHA256:3B2ABD3773E4678100F197F53A886EC833FD2E26AA9A94D780A2D22BEFDF7D44 | |||
| 6768 | YellowSkull2.0.exe | C:\Users\admin\AppData\Local\Temp\B5EB.tmp\YSkullMBRSetup.exe | executable | |
MD5:220303EB72EBDE4605116640FB719B26 | SHA256:F081C913488C3F22B62F906DAC2A82A38D085EBE1D28701F0059DFDFBF1CCF42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6176 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1848 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6176 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1848 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.189.173.24:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6176 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1848 | RUXIMICS.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |