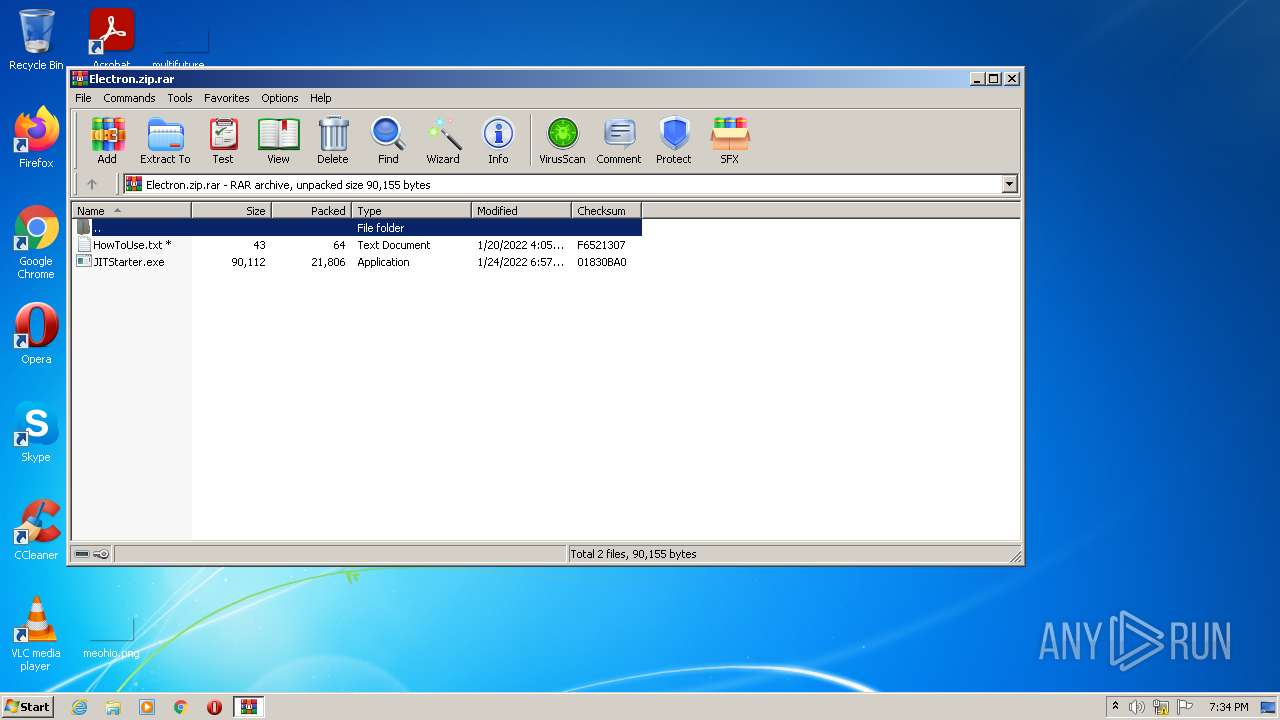
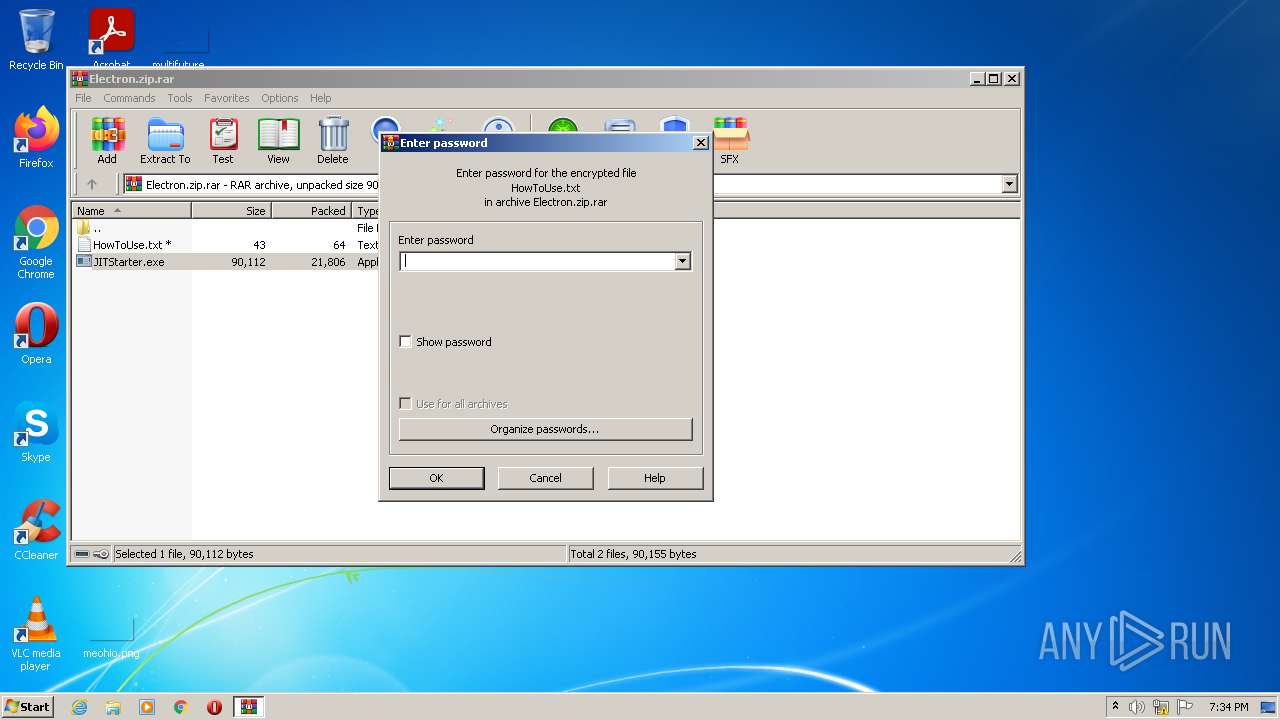
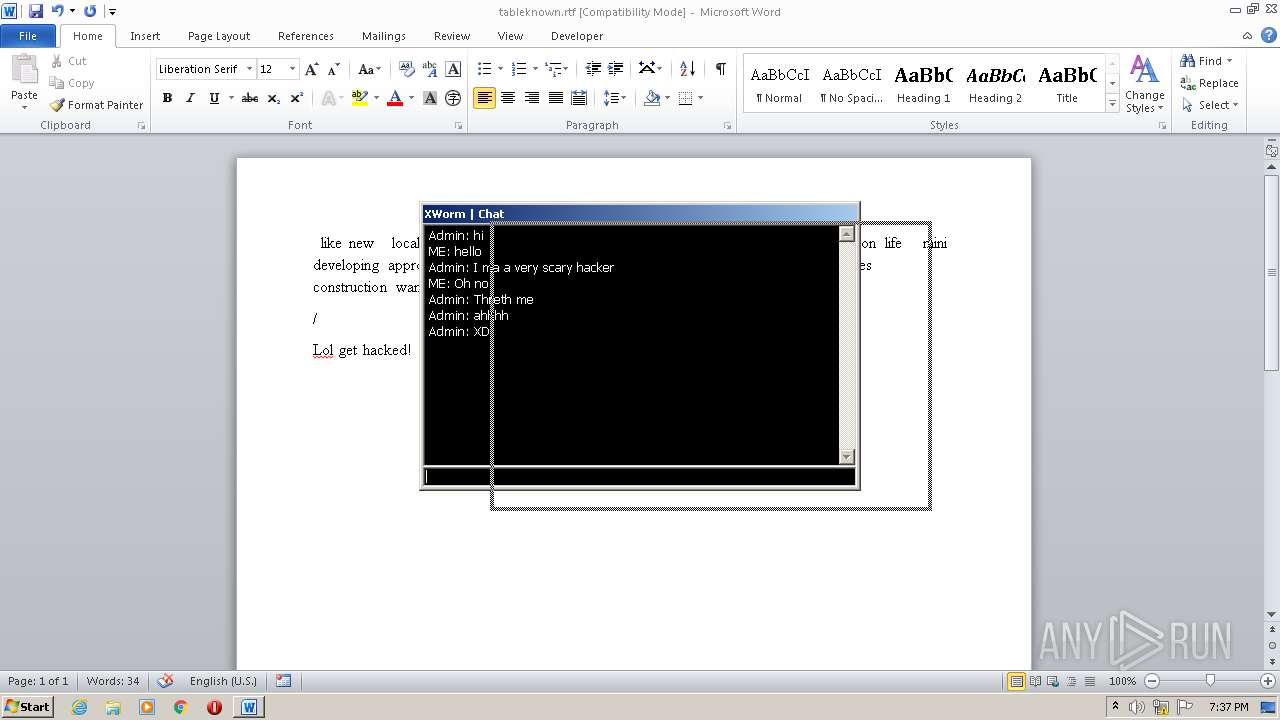
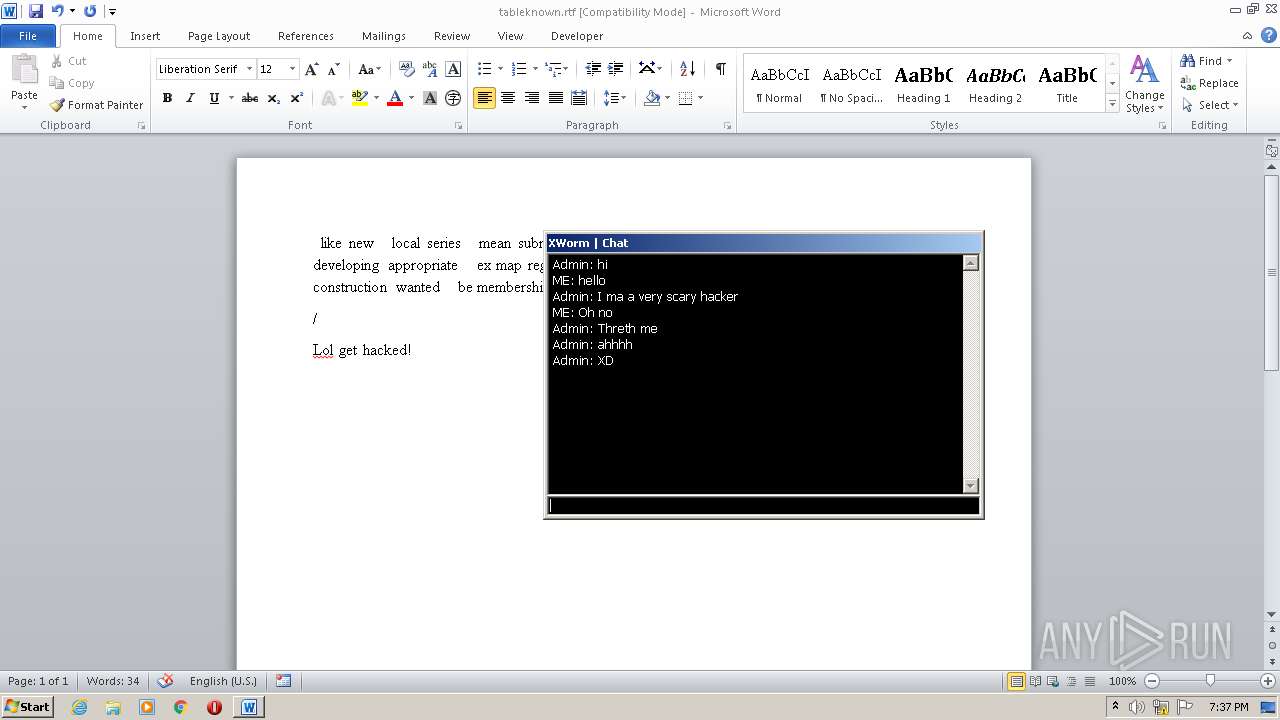
| File name: | Electron.zip |
| Full analysis: | https://app.any.run/tasks/5c160ca8-bc1b-4a75-8997-6e42a6aed6f2 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 19:33:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 607F027700DC670D72FF5F781CA0A562 |
| SHA1: | 82742F9458871814CB666EB3DBE04B645AF49DC2 |
| SHA256: | 17EA4D8A811BB37FB14F0508875A5EEC31AA7734C95E4BBE583FB256D7D1A6CB |
| SSDEEP: | 384:IMdKzZ64j4N0vDxlbZmWwjN6767wUQwBgkNQELpqpkOCIw8uGa3GKB:zKIN4Zmhjw767wOBgUxx5Gq |
MALICIOUS
Application was dropped or rewritten from another process
- JITStarter.exe (PID: 3160)
- JITStarter.exe (PID: 3492)
- JITStarter.exe (PID: 2812)
- JITStarter.exe (PID: 3224)
- JITStarter.exe (PID: 3164)
Writes to a start menu file
- JITStarter.exe (PID: 3160)
Changes the autorun value in the registry
- JITStarter.exe (PID: 3160)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1268)
Uses Task Scheduler to run other applications
- JITStarter.exe (PID: 3160)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2484)
- JITStarter.exe (PID: 3160)
- JITStarter.exe (PID: 3492)
- JITStarter.exe (PID: 2812)
- JITStarter.exe (PID: 3224)
- JITStarter.exe (PID: 3164)
Reads the computer name
- WinRAR.exe (PID: 2484)
- JITStarter.exe (PID: 3492)
- JITStarter.exe (PID: 2812)
- JITStarter.exe (PID: 3224)
- JITStarter.exe (PID: 3164)
- JITStarter.exe (PID: 3160)
Reads Environment values
- JITStarter.exe (PID: 3160)
Creates files in the user directory
- JITStarter.exe (PID: 3160)
Executed via Task Scheduler
- JITStarter.exe (PID: 3492)
- JITStarter.exe (PID: 2812)
- JITStarter.exe (PID: 3224)
- JITStarter.exe (PID: 3164)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2484)
- JITStarter.exe (PID: 3160)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2484)
- JITStarter.exe (PID: 3160)
Checks for external IP
- JITStarter.exe (PID: 3160)
INFO
Reads settings of System Certificates
- JITStarter.exe (PID: 3160)
Checks supported languages
- schtasks.exe (PID: 1268)
- WINWORD.EXE (PID: 3544)
- opera.exe (PID: 2120)
Reads the computer name
- schtasks.exe (PID: 1268)
- WINWORD.EXE (PID: 3544)
- opera.exe (PID: 2120)
Manual execution by user
- WINWORD.EXE (PID: 3544)
- opera.exe (PID: 2120)
Creates files in the user directory
- WINWORD.EXE (PID: 3544)
- opera.exe (PID: 2120)
Check for Java to be installed
- opera.exe (PID: 2120)
Dropped object may contain Bitcoin addresses
- opera.exe (PID: 2120)
Reads the date of Windows installation
- opera.exe (PID: 2120)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
48
Monitored processes
9
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1268 | "C:\Windows\System32\schtasks.exe" /create /sc minute /mo 1 /tn "JITStarter" /tr "C:\Users\admin\AppData\Roaming\JITStarter.exe" | C:\Windows\System32\schtasks.exe | — | JITStarter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Electron.zip.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2812 | C:\Users\admin\AppData\Roaming\JITStarter.exe | C:\Users\admin\AppData\Roaming\JITStarter.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2484.49997\JITStarter.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2484.49997\JITStarter.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3164 | C:\Users\admin\AppData\Roaming\JITStarter.exe | C:\Users\admin\AppData\Roaming\JITStarter.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3224 | C:\Users\admin\AppData\Roaming\JITStarter.exe | C:\Users\admin\AppData\Roaming\JITStarter.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3492 | C:\Users\admin\AppData\Roaming\JITStarter.exe | C:\Users\admin\AppData\Roaming\JITStarter.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
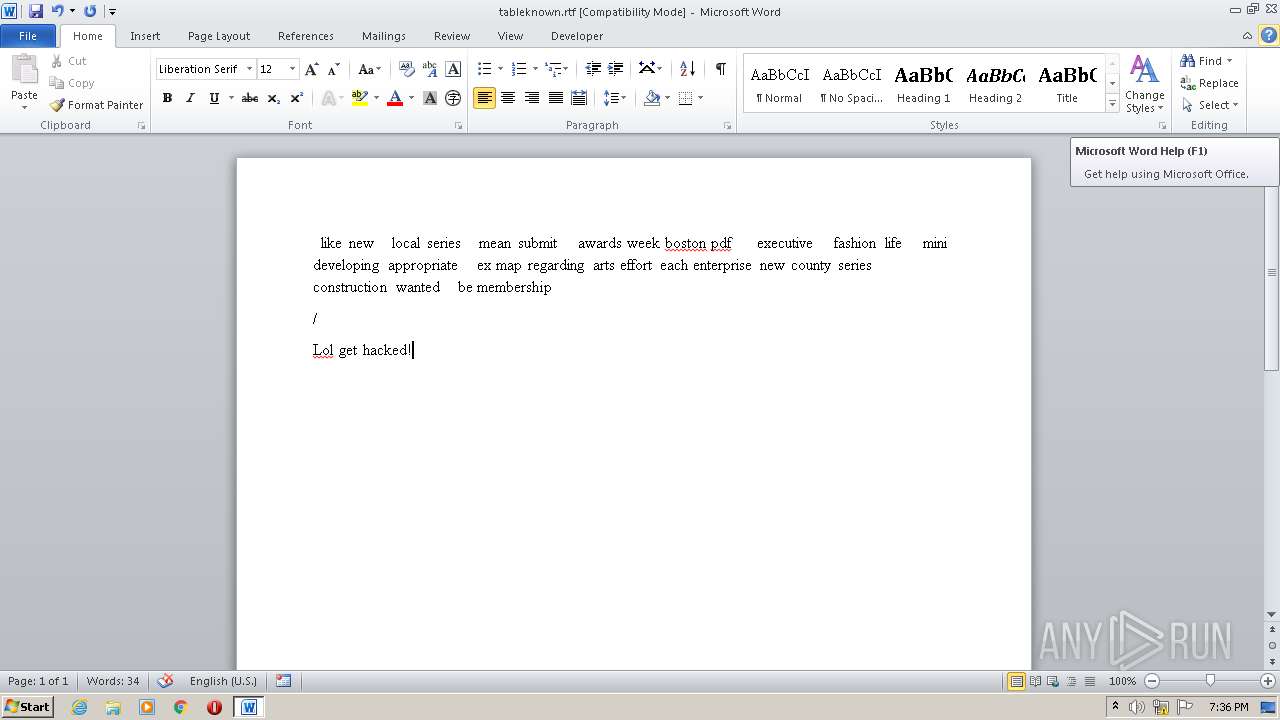
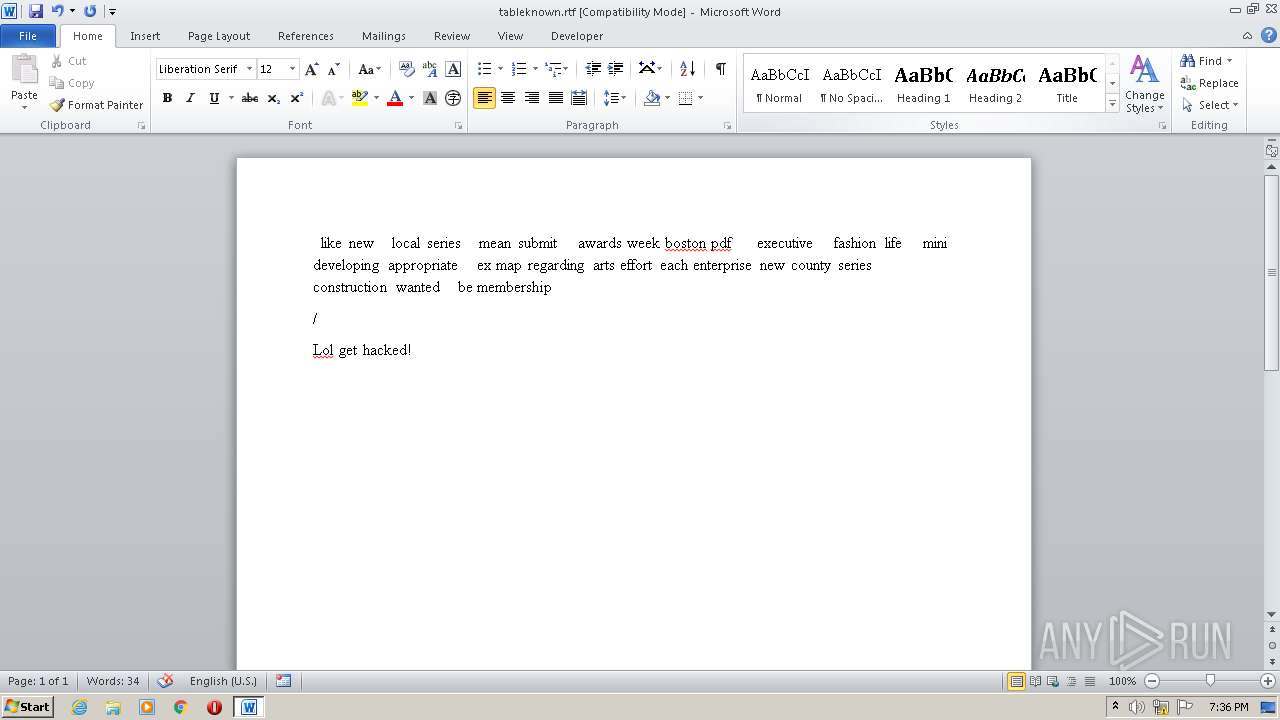
| 3544 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\tableknown.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
8 818
Read events
7 953
Write events
727
Delete events
138
Modification events
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Electron.zip.rar | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
26
Text files
18
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A80.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2484.49997\JITStarter.exe | executable | |
MD5:— | SHA256:— | |||
| 3160 | JITStarter.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\JITStarter.exe | executable | |
MD5:— | SHA256:— | |||
| 3160 | JITStarter.exe | C:\Users\admin\AppData\Roaming\JITStarter.exe | executable | |
MD5:— | SHA256:— | |||
| 3544 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3544 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 3544 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\tableknown.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2484.49997\HowToUse.txt | text | |
MD5:— | SHA256:— | |||
| 3544 | WINWORD.EXE | C:\Users\admin\Desktop\~$bleknown.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2120 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
7
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
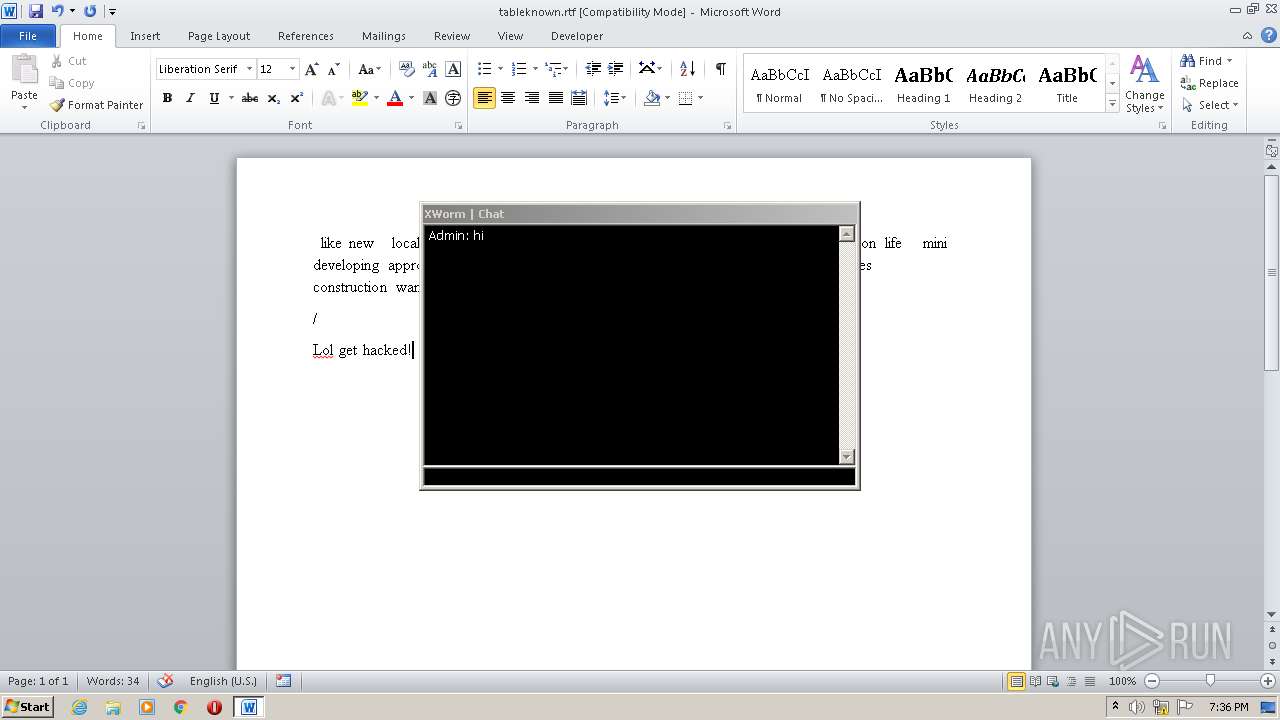
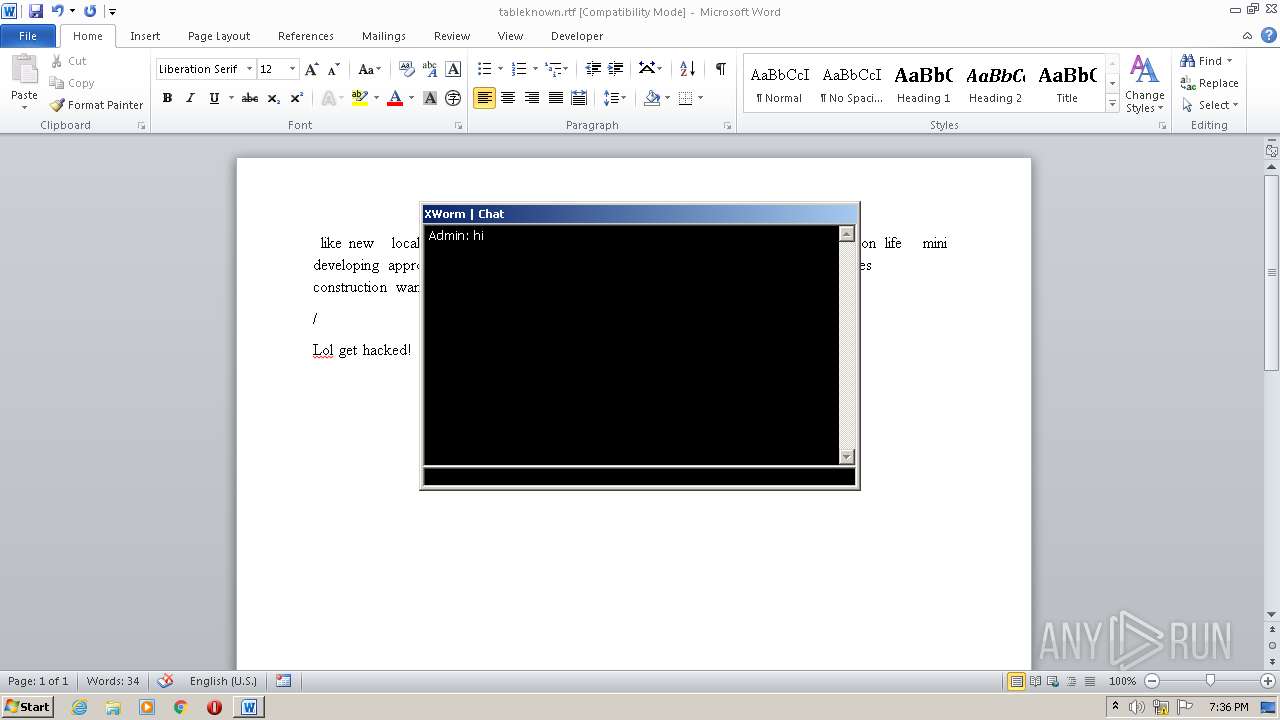
3160 | JITStarter.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | text | 6 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3160 | JITStarter.exe | 208.95.112.1:80 | ip-api.com | IBURST | — | malicious |
2120 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3160 | JITStarter.exe | 162.159.138.85:443 | sharetext.me | Cloudflare Inc | — | malicious |
3160 | JITStarter.exe | 3.138.180.119:13853 | 4.tcp.ngrok.io | — | US | malicious |
2120 | opera.exe | 93.184.220.29:80 | crl3.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
sharetext.me |
| malicious |
4.tcp.ngrok.io |
| malicious |
certs.opera.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3160 | JITStarter.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3160 | JITStarter.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query to a *.ngrok domain (ngrok.io) |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query to a *.ngrok domain (ngrok.io) |