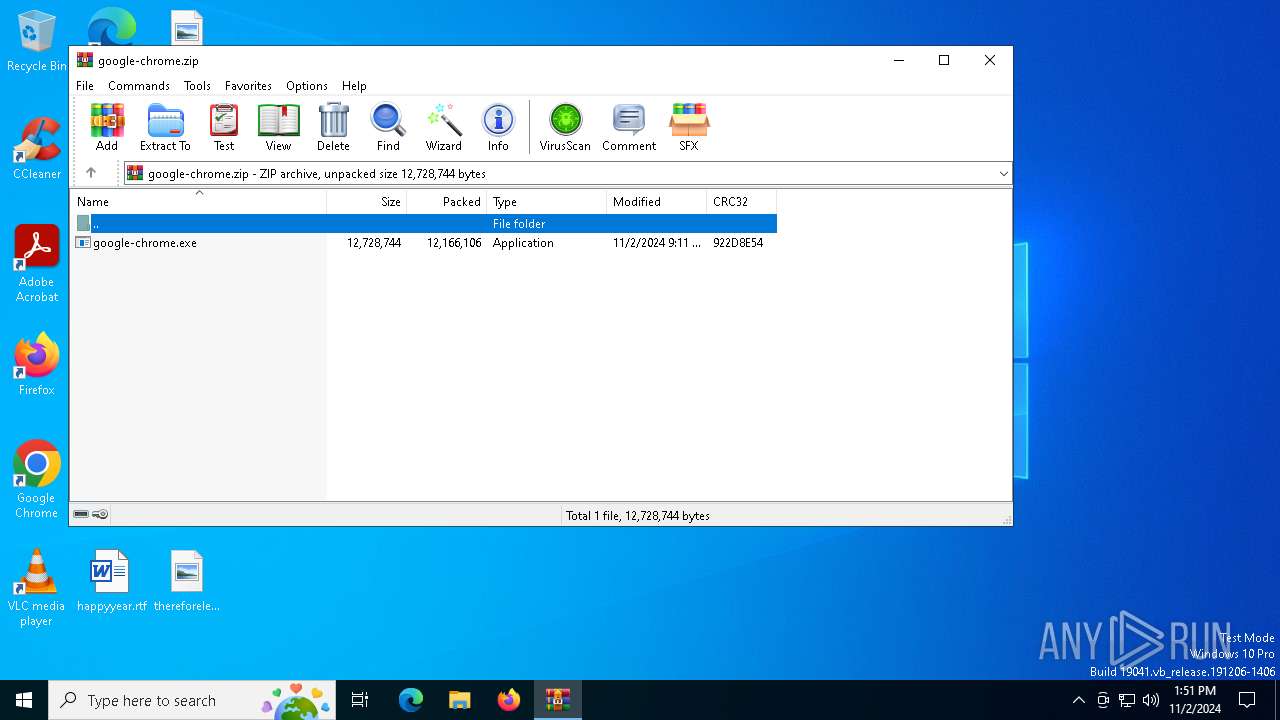
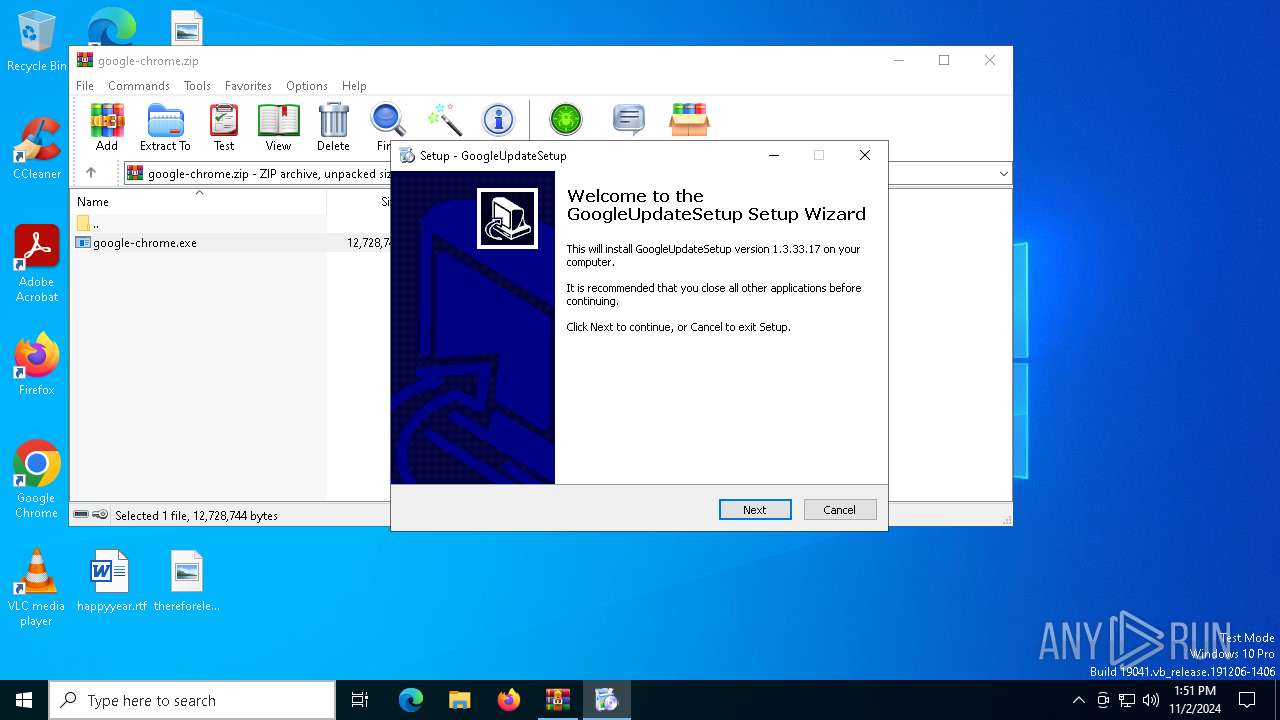
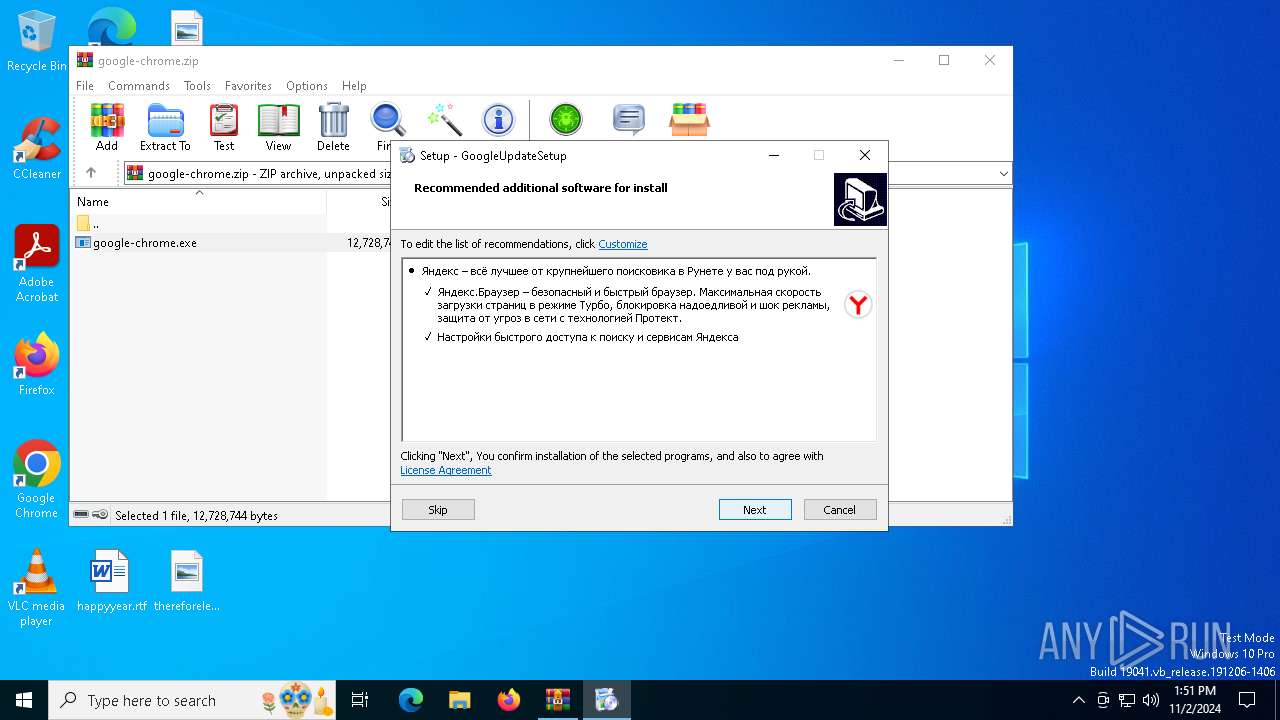
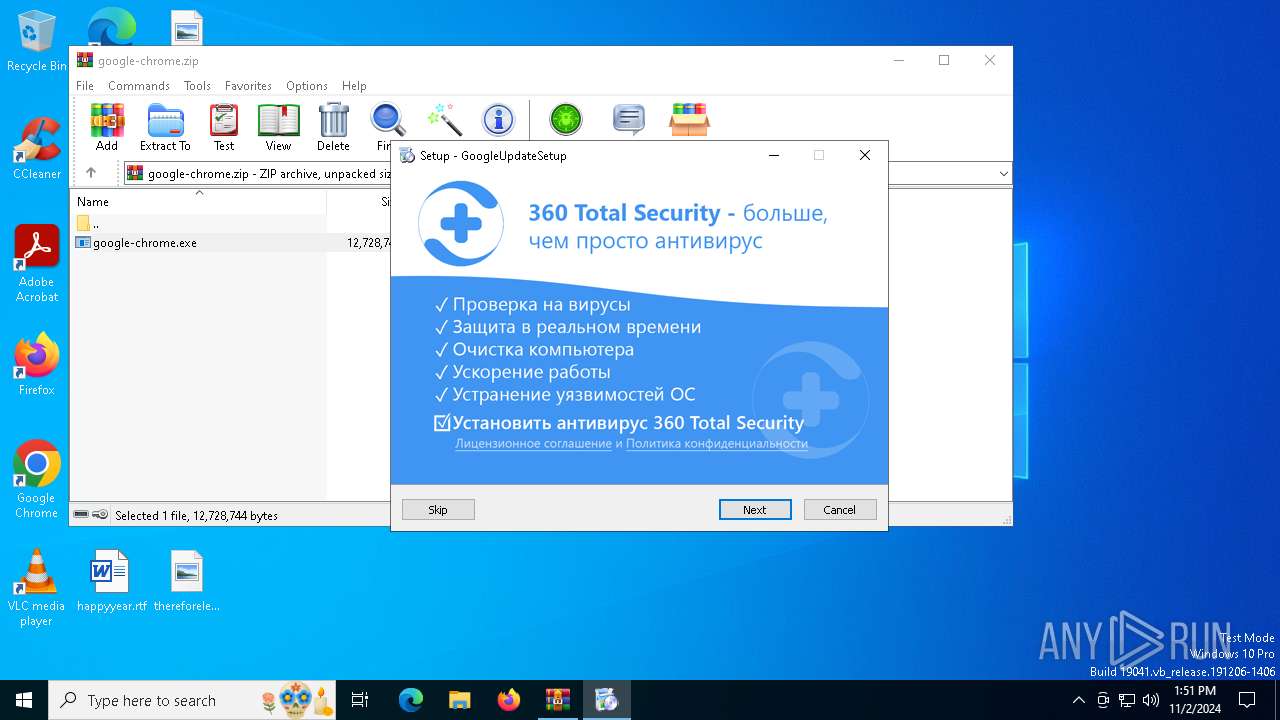
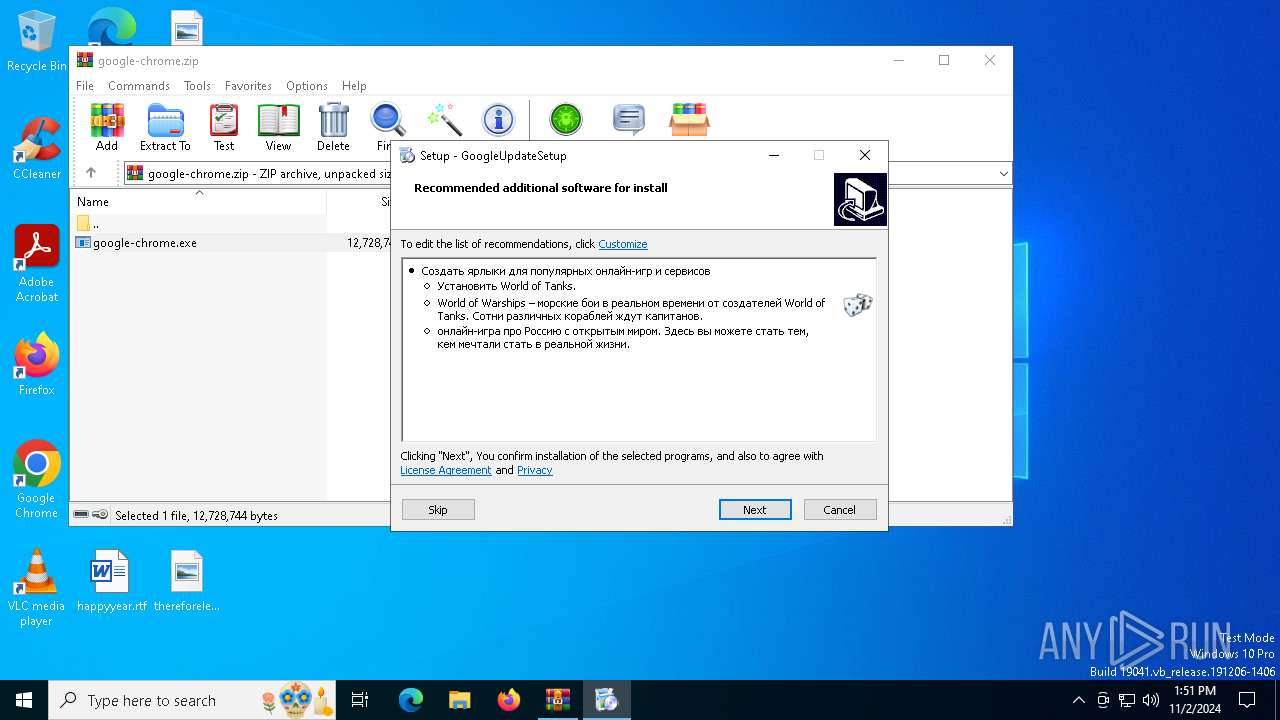
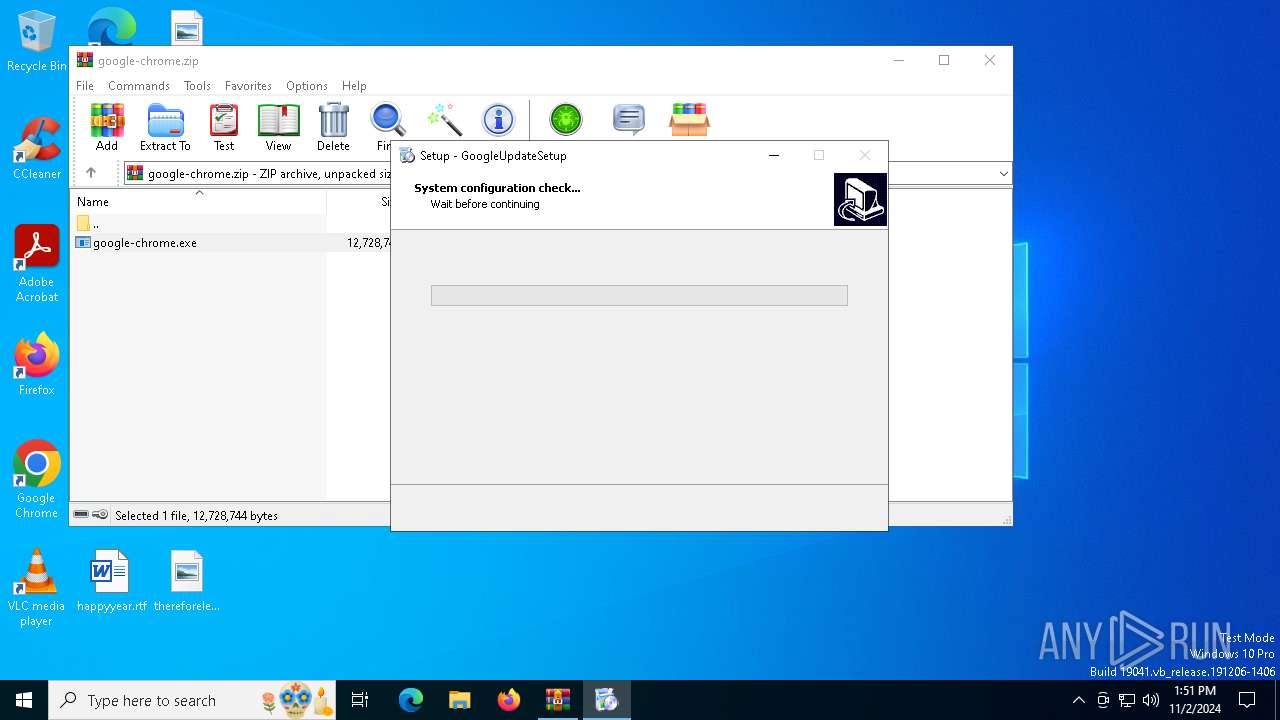
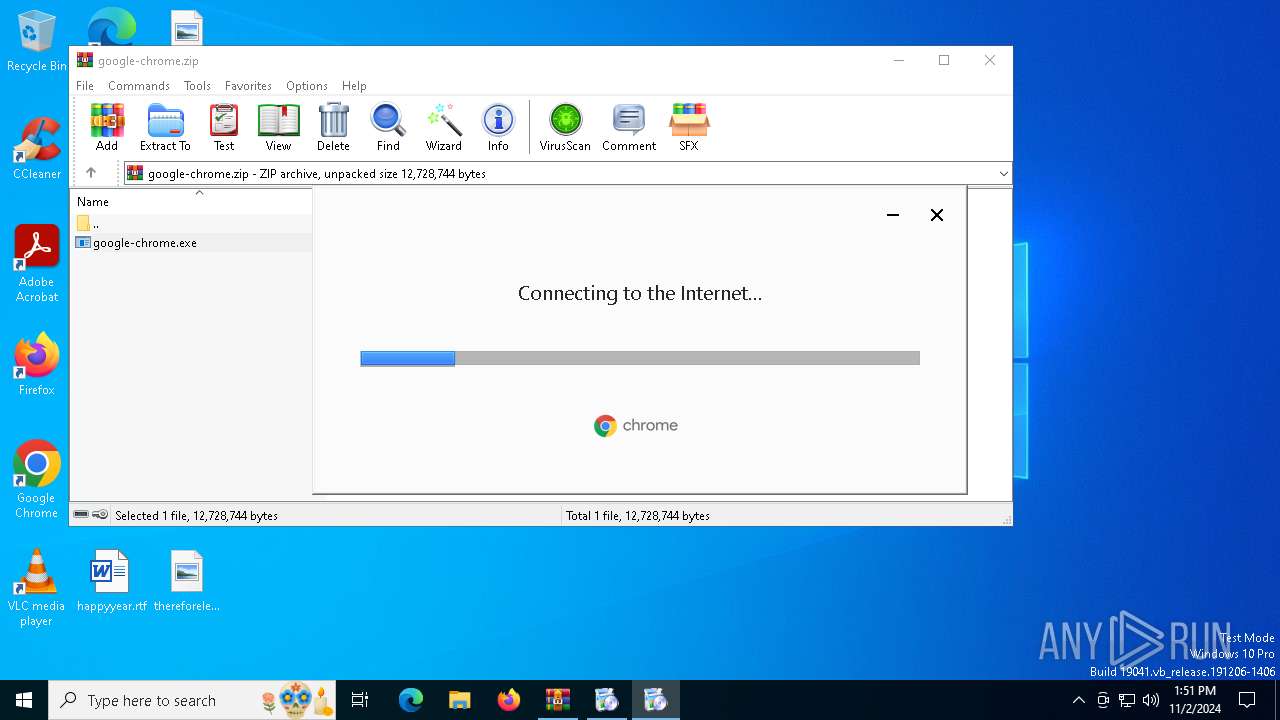
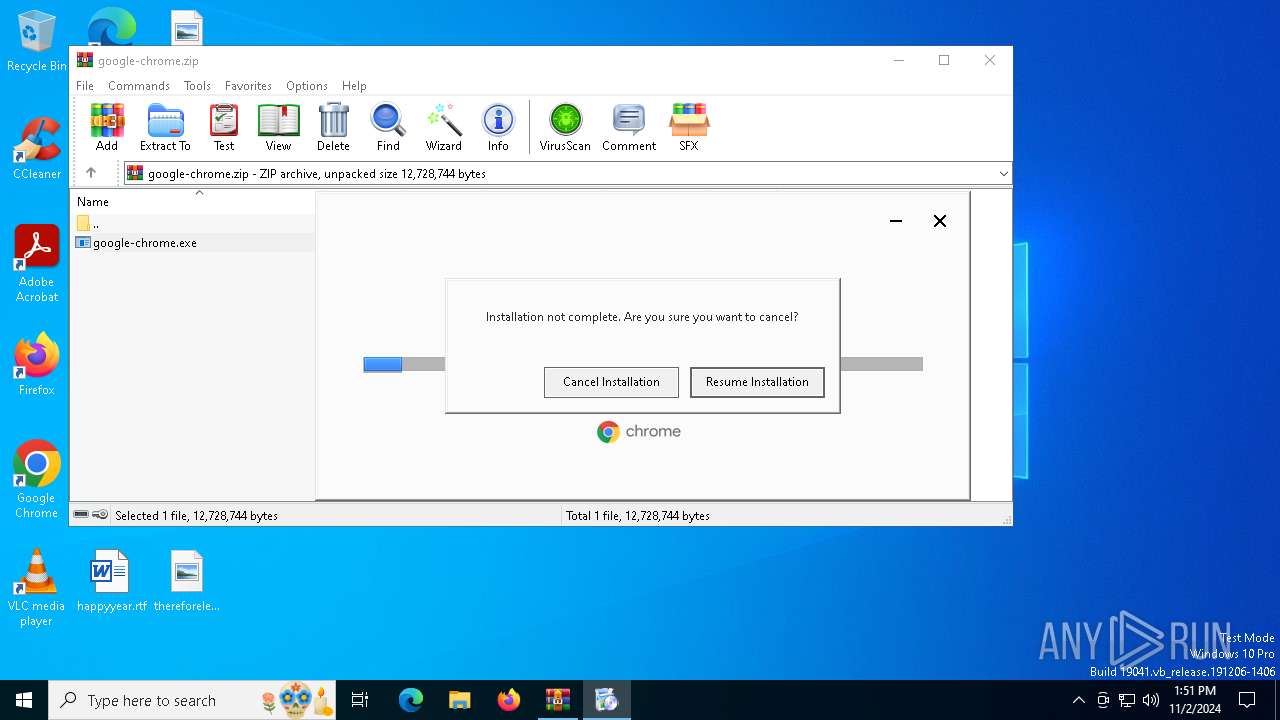
| File name: | google-chrome.zip |
| Full analysis: | https://app.any.run/tasks/9d3ba549-6e58-4882-98c5-fe2085e8d218 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2024, 13:51:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 496386B077989149A9928BE561F886AD |
| SHA1: | 2BCDD4D23B1BB14659F3704C27D68EF35C96EA2E |
| SHA256: | 17BD08BC03DBE4F65CD5AF24BA41F6A9673FFEE3282CF3AFD14C8F471C7793DA |
| SSDEEP: | 98304:j1TUjg7iNniSFMVq9YshxI8wrVb/zfUJbgArEdXuJ91hYNhe0NSR5LGcC4ASWwM2:UA9jjTAF2gMTUb4Ji2eP |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5100)
Application was injected by another process
- explorer.exe (PID: 4616)
Runs injected code in another process
- BWcfuV.exe (PID: 4208)
- BWcfuV.exe (PID: 4312)
- BWcfuV.exe (PID: 6956)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5100)
- google-chrome.tmp (PID: 6680)
- GoogleUpdate.exe (PID: 5068)
- GoogleUpdate.exe (PID: 7148)
Executable content was dropped or overwritten
- google-chrome.exe (PID: 6692)
- google-chrome.tmp (PID: 3568)
- google-chrome.exe (PID: 6276)
- google-chrome.exe (PID: 4548)
- 130.0.6723.92_chrome_installer.exe (PID: 6820)
Reads the Windows owner or organization settings
- google-chrome.tmp (PID: 3568)
Searches for installed software
- google-chrome.tmp (PID: 3568)
Checks Windows Trust Settings
- GoogleUpdate.exe (PID: 7148)
Potential Corporate Privacy Violation
- GoogleUpdate.exe (PID: 7148)
Process requests binary or script from the Internet
- GoogleUpdate.exe (PID: 7148)
Application launched itself
- setup.exe (PID: 6272)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 5100)
- google-chrome.tmp (PID: 6680)
Checks supported languages
- google-chrome.tmp (PID: 6680)
- google-chrome.exe (PID: 6692)
- google-chrome.tmp (PID: 3568)
- google-chrome.exe (PID: 6276)
- google-chrome.exe (PID: 4548)
- GoogleUpdate.exe (PID: 5356)
- GoogleUpdate.exe (PID: 6220)
- GoogleUpdate.exe (PID: 7148)
- BWcfuV.exe (PID: 4208)
- BWcfuV.exe (PID: 4312)
- BWcfuV.exe (PID: 6956)
- GoogleUpdate.exe (PID: 5068)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5100)
Create files in a temporary directory
- google-chrome.exe (PID: 6692)
- google-chrome.tmp (PID: 3568)
- google-chrome.exe (PID: 6276)
- GoogleUpdate.exe (PID: 7148)
Reads the computer name
- google-chrome.tmp (PID: 6680)
- google-chrome.tmp (PID: 3568)
- GoogleUpdate.exe (PID: 5068)
- GoogleUpdate.exe (PID: 5356)
- GoogleUpdate.exe (PID: 7148)
- GoogleUpdate.exe (PID: 6220)
Process checks computer location settings
- google-chrome.tmp (PID: 6680)
- GoogleUpdate.exe (PID: 5068)
Reads the software policy settings
- google-chrome.tmp (PID: 3568)
- GoogleUpdate.exe (PID: 6220)
- GoogleUpdate.exe (PID: 7148)
Creates files in the program directory
- google-chrome.exe (PID: 4548)
- GoogleUpdate.exe (PID: 5356)
- GoogleUpdate.exe (PID: 6220)
- GoogleUpdate.exe (PID: 7148)
Checks proxy server information
- GoogleUpdate.exe (PID: 6220)
- GoogleUpdate.exe (PID: 7148)
Reads the machine GUID from the registry
- GoogleUpdate.exe (PID: 7148)
Creates a software uninstall entry
- google-chrome.tmp (PID: 3568)
Creates files or folders in the user directory
- explorer.exe (PID: 4616)
- GoogleUpdate.exe (PID: 7148)
- google-chrome.tmp (PID: 3568)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:02 12:11:54 |
| ZipCRC: | 0x922d8e54 |
| ZipCompressedSize: | 12166106 |
| ZipUncompressedSize: | 12728744 |
| ZipFileName: | google-chrome.exe |
Total processes
147
Monitored processes
22
Malicious processes
3
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BWcfuV.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | "C:\Users\admin\AppData\Local\Temp\is-H08F7.tmp\google-chrome.tmp" /SL5="$6025E,11472340,826880,C:\Users\admin\AppData\Local\Temp\Rar$EXa5100.30653\google-chrome.exe" /SPAWNWND=$6023C /NOTIFYWND=$5024E | C:\Users\admin\AppData\Local\Temp\is-H08F7.tmp\google-chrome.tmp | google-chrome.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4208 | "C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\BWcfuV.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\World of Warships.lnk" 5386 | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\BWcfuV.exe | — | google-chrome.tmp | |||||||||||
User: admin Company: Technosys Corporation Integrity Level: MEDIUM Description: Pin To Taskbar Exit code: 0 Version: 0.99.9.1 Modules
| |||||||||||||||
| 4312 | "C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\BWcfuV.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\World of Tanks.lnk" 5386 | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\BWcfuV.exe | — | google-chrome.tmp | |||||||||||
User: admin Company: Technosys Corporation Integrity Level: MEDIUM Description: Pin To Taskbar Exit code: 0 Version: 0.99.9.1 Modules
| |||||||||||||||
| 4548 | "C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bupBWV0hOF3OvPPbix9\google-chrome.exe" | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bupBWV0hOF3OvPPbix9\google-chrome.exe | google-chrome.tmp | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Update Setup Version: 1.3.33.17 Modules
| |||||||||||||||
| 4616 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5068 | "C:\Program Files (x86)\GUMF238.tmp\GoogleUpdate.exe" /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={ADC5A877-2F2E-215F-6DAC-B2AB514017C7}&lang=en&browser=4&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=x64-stable-statsdef_1&installdataindex=empty" | C:\Program Files (x86)\GUMF238.tmp\GoogleUpdate.exe | — | google-chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Version: 1.3.33.17 Modules
| |||||||||||||||
| 5100 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\google-chrome.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5232 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5356 | "C:\Program Files (x86)\Google\Update\GoogleUpdate.exe" /healthcheck | C:\Program Files (x86)\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.36.51 Modules
| |||||||||||||||
Total events
10 047
Read events
9 896
Write events
139
Delete events
12
Modification events
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\google-chrome.zip | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000080238 |
| Operation: | write | Name: | VirtualDesktop |
Value: 100000003030445671D90A7D3588864C9F3CEA9EBAB7B4A7 | |||
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000060078 |
| Operation: | write | Name: | VirtualDesktop |
Value: 100000003030445671D90A7D3588864C9F3CEA9EBAB7B4A7 | |||
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000602E2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 100000003030445671D90A7D3588864C9F3CEA9EBAB7B4A7 | |||
| (PID) Process: | (5068) GoogleUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | delete value | Name: | usagestats |
Value: | |||
Executable files
82
Suspicious files
25
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5100.30653\google-chrome.exe | executable | |
MD5:BCB27180DA1B7527758BB86D4462AD6B | SHA256:3BBBF698C2CFB6796143FE061B316070827243A42718E95177B722468258C4F1 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\V4xEHL0ByrrwZkg7.dll | executable | |
MD5:D6F1BA0EEF05A82D2F3EF55DD3AE45B0 | SHA256:727B06710120B371183D68EF1C2D205E8C2968ADE93F8466DDEA4824B212B035 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\botva2.dll | executable | |
MD5:EF899FA243C07B7B82B3A45F6EC36771 | SHA256:DA7D0368712EE419952EB2640A65A7F24E39FB7872442ED4D2EE847EC4CFDE77 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\downloader.exe | executable | |
MD5:B9314504E592D42CB36534415A62B3AF | SHA256:C60C3A7D20B575FDEEB723E12A11C2602E73329DC413FC6D88F72E6F87E38B49 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\Accept_buttons_175.png | image | |
MD5:FCE8F803891426B137713E4595B05B42 | SHA256:0C48C8AF091A7602366631E35F1DEC2F31E17D6726707F1D51476EC0DB0CB9B5 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\Accept_buttons_200.png | image | |
MD5:66ED96978B9869BEA3AE689B265FC1FE | SHA256:65A8D030FC4508ACE386703F90455B98DCB042F9C8BB5A083C95436A2AC75E61 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\Background_125.png | image | |
MD5:F1CDF3F13B88927BD304F22A47EDB579 | SHA256:2CD9FDF6F4A04586D66F52A6625A9E5A8F734B8A15222FFC137F0C5B98EFF8A7 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\Accept_buttons_150.png | image | |
MD5:216480982115385689910C22155587BC | SHA256:E207A18366D9768595EEA3EDE3ACF9509071A964788037F3AA6BB6831A3BA51E | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\bs2g9b_m6WzN3j\Background_175.png | image | |
MD5:0F5A0ACCC4D2439307969A85E56443F4 | SHA256:77E77EAC9E15F20AF5DA2D6D1A7E843718109A6A6A02691FE9B64581C8322707 | |||
| 3568 | google-chrome.tmp | C:\Users\admin\AppData\Local\Temp\is-7S5D4.tmp\{app}\EKr0KN1vfOFpfiMJoEeu\bs2g9b_m6WzN3j | binary | |
MD5:670C3E49D8BBA4CA61D08937D2576CD8 | SHA256:0CA54D79192C4C31334514E35B60A67207F858D3EBF4A8DAC6DA9E596FCF2DF0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
48
DNS requests
27
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7148 | GoogleUpdate.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/o7tujekrb3s3ybnrwp5n2taize_130.0.6723.92/130.0.6723.92_chrome_installer.exe | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7148 | GoogleUpdate.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
7148 | GoogleUpdate.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1552 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
cfg.datarcv.ru |
| unknown |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7148 | GoogleUpdate.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
7148 | GoogleUpdate.exe | Misc activity | ET INFO EXE - Served Attached HTTP |