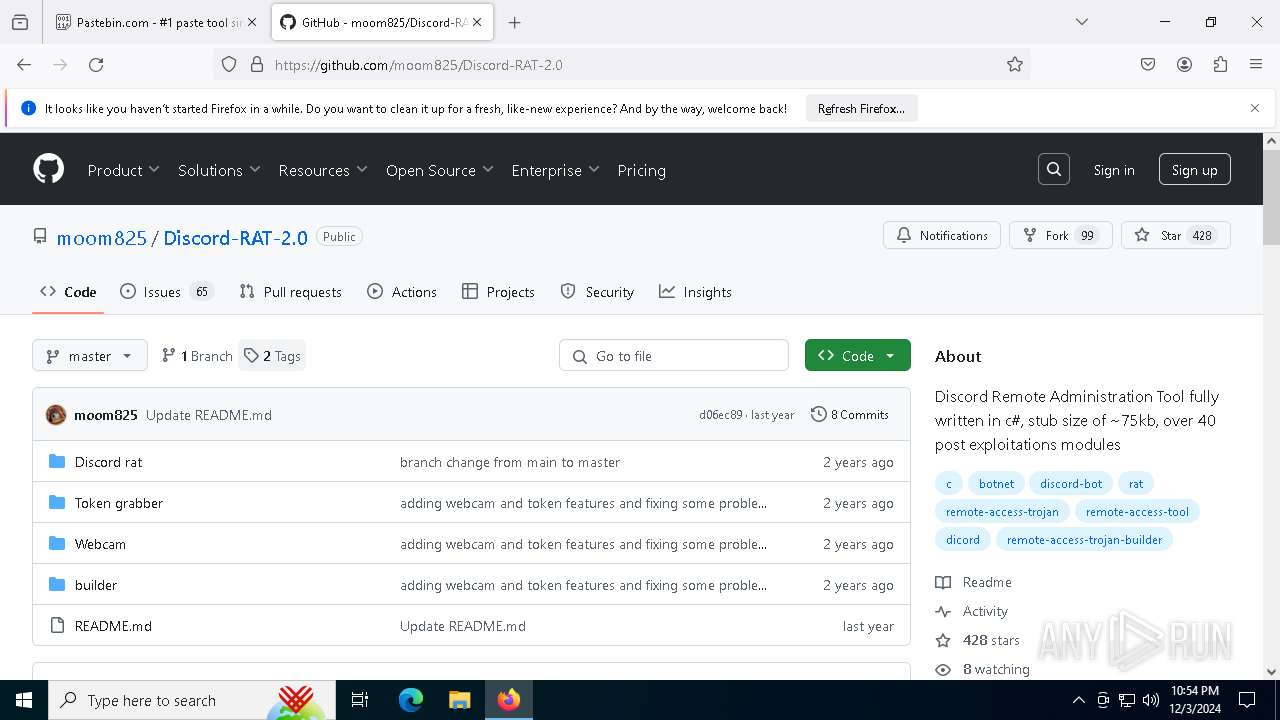
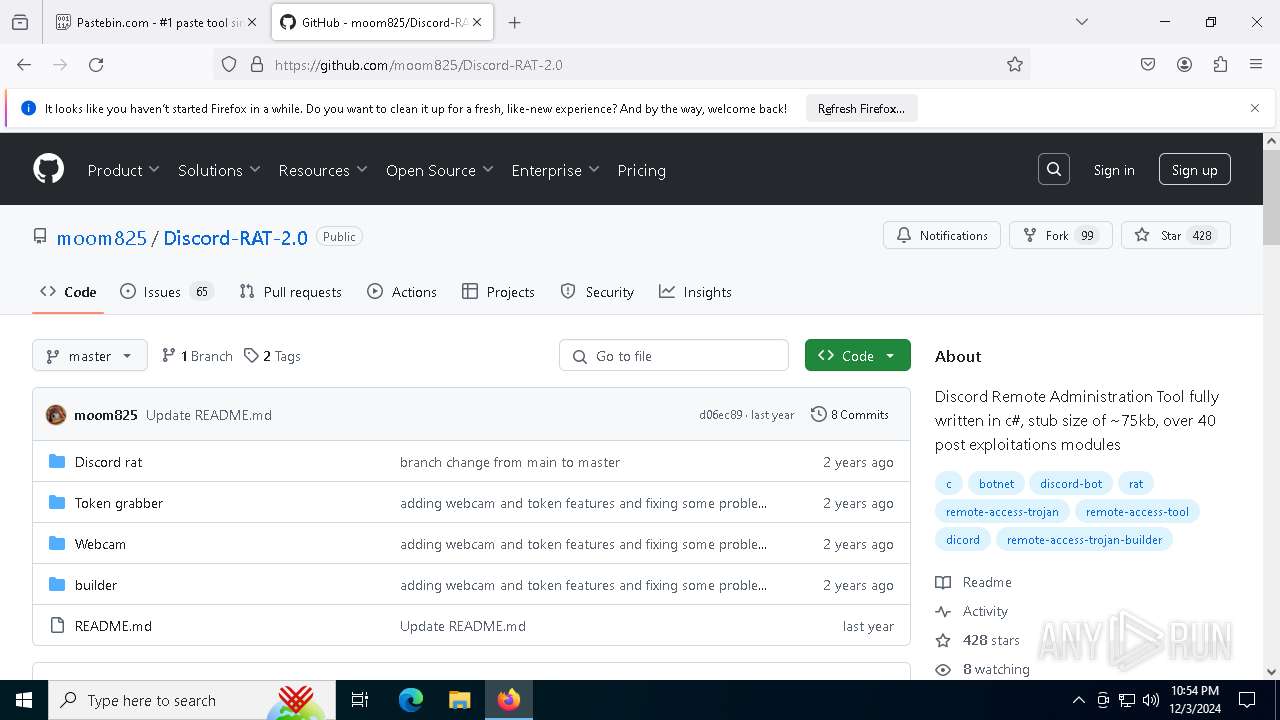
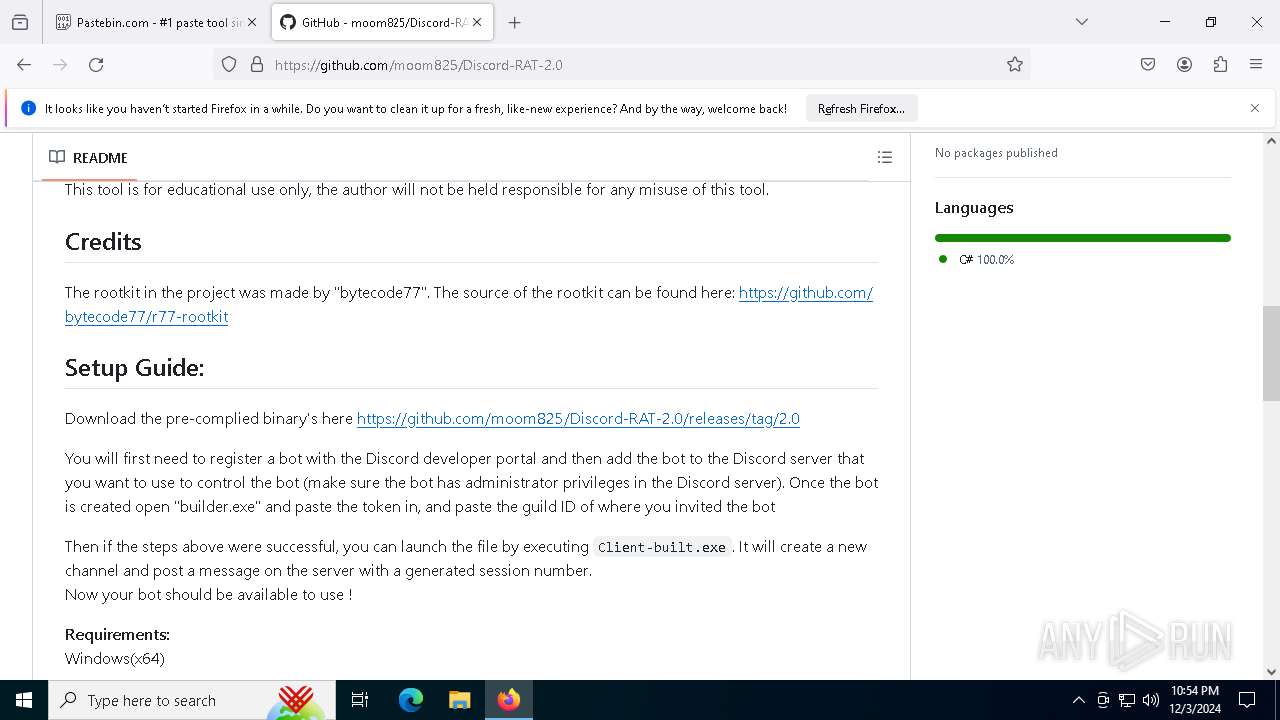
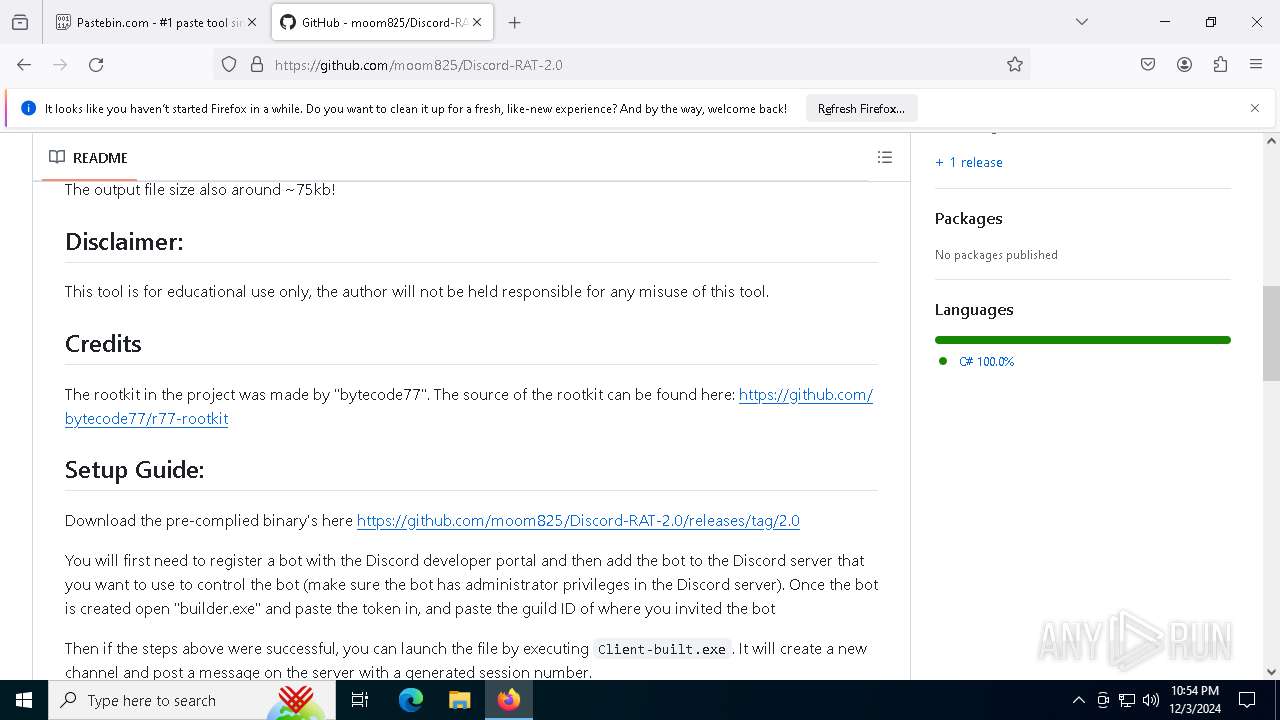
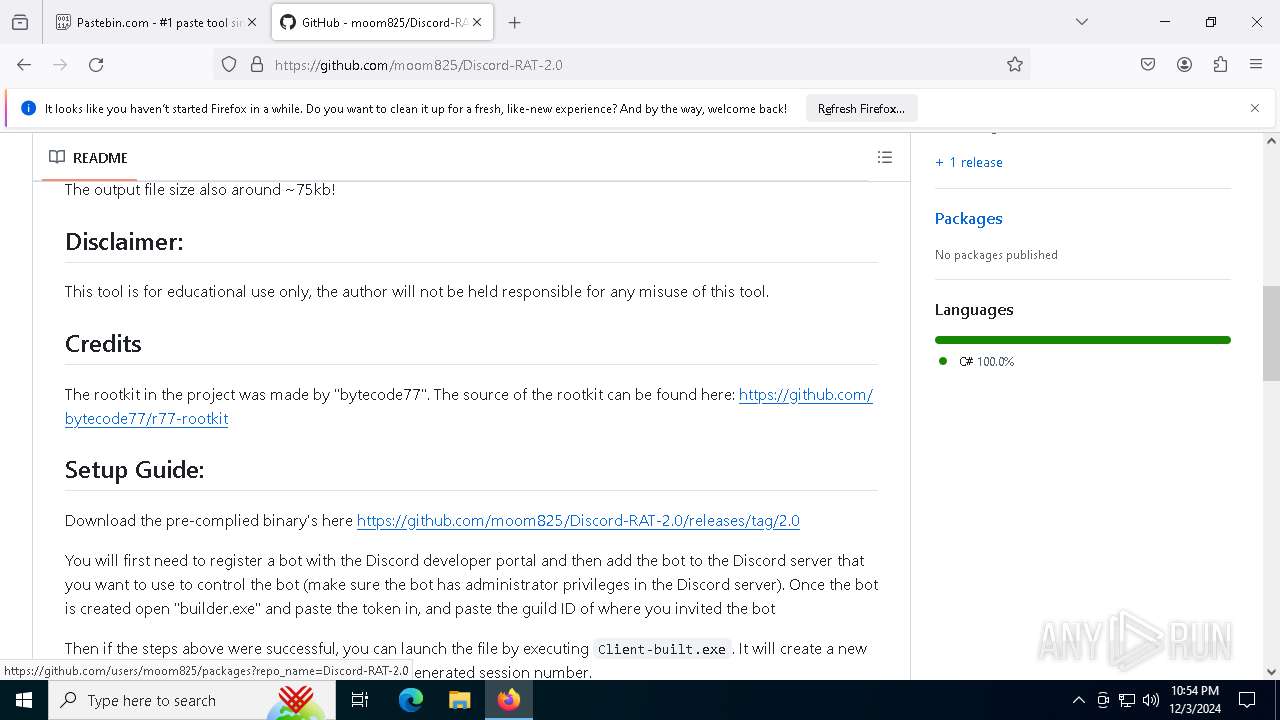
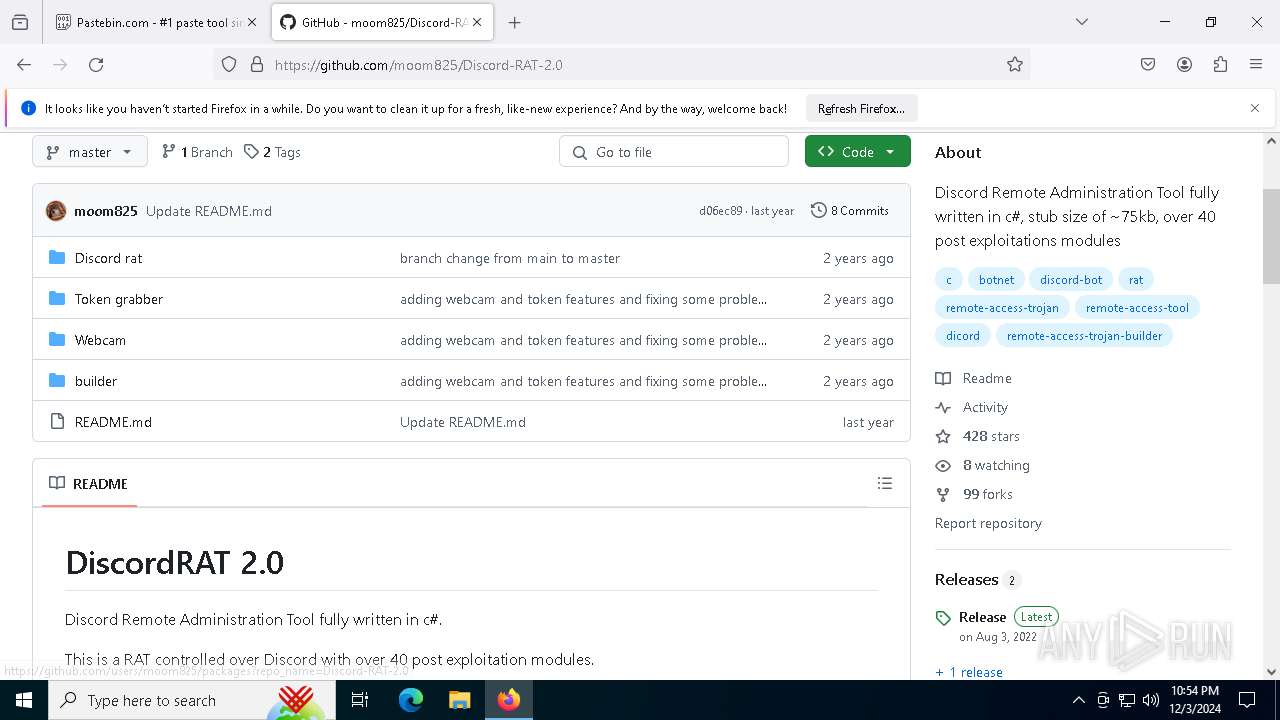
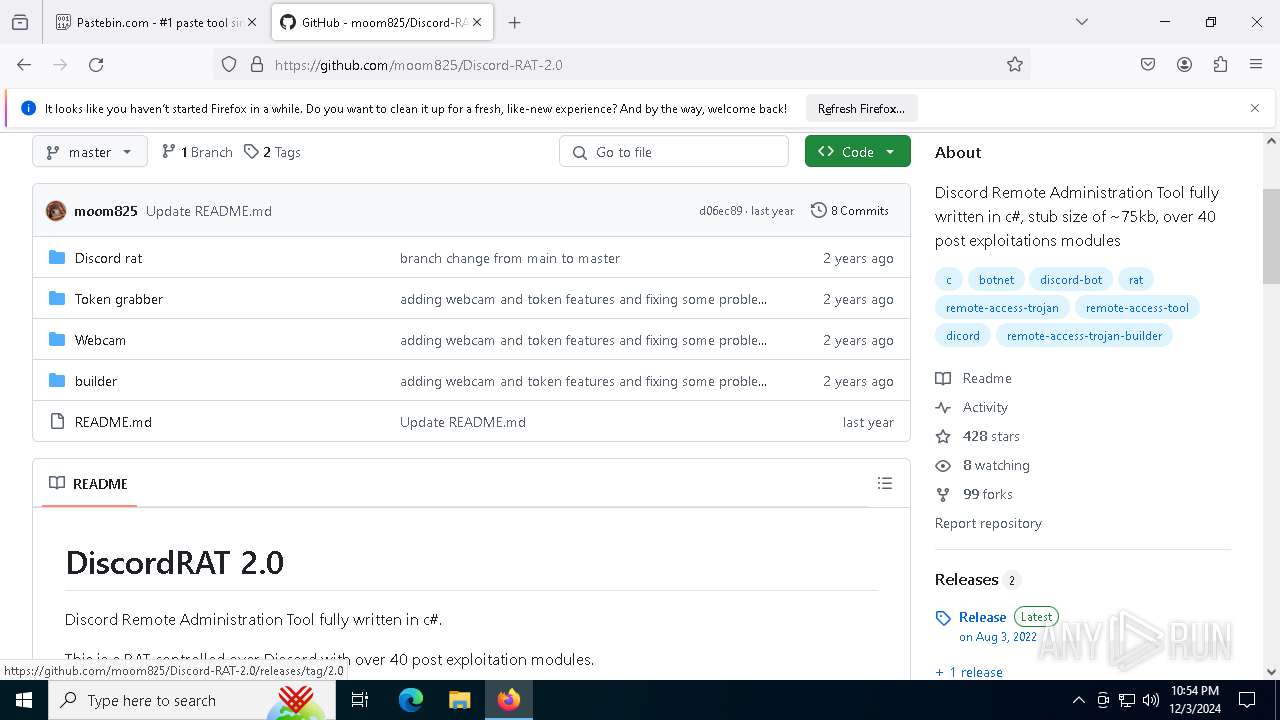
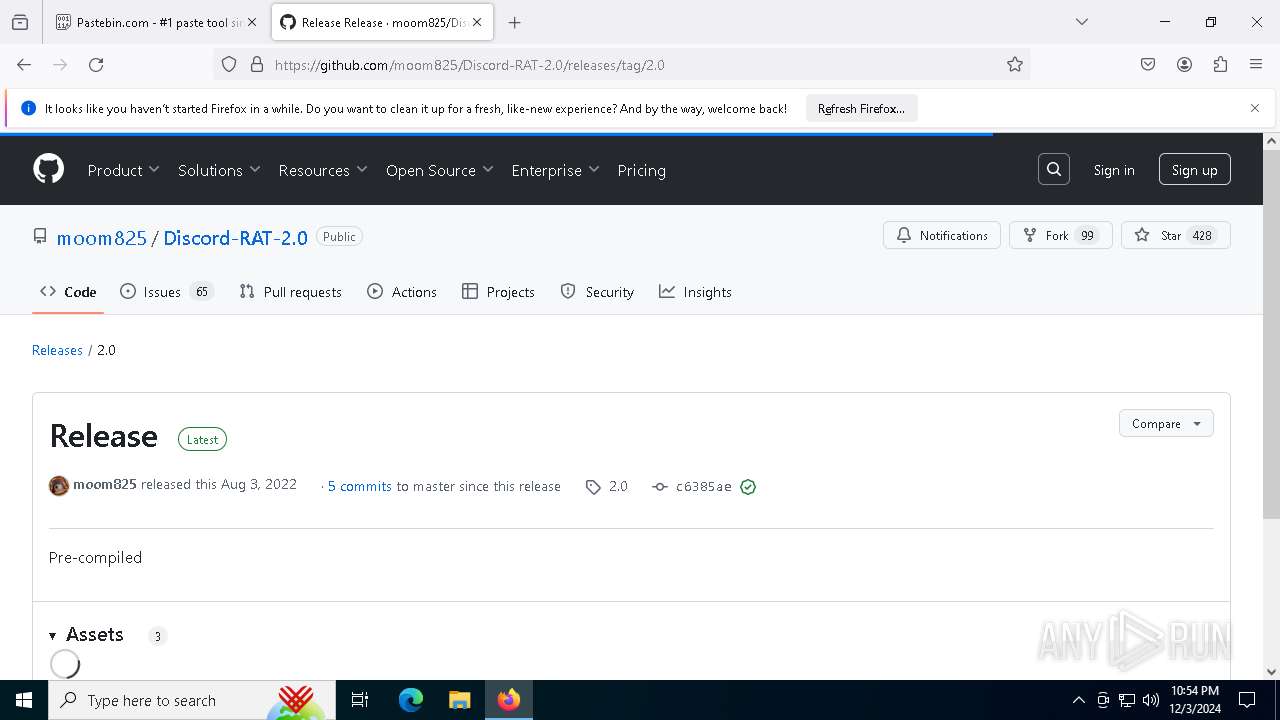
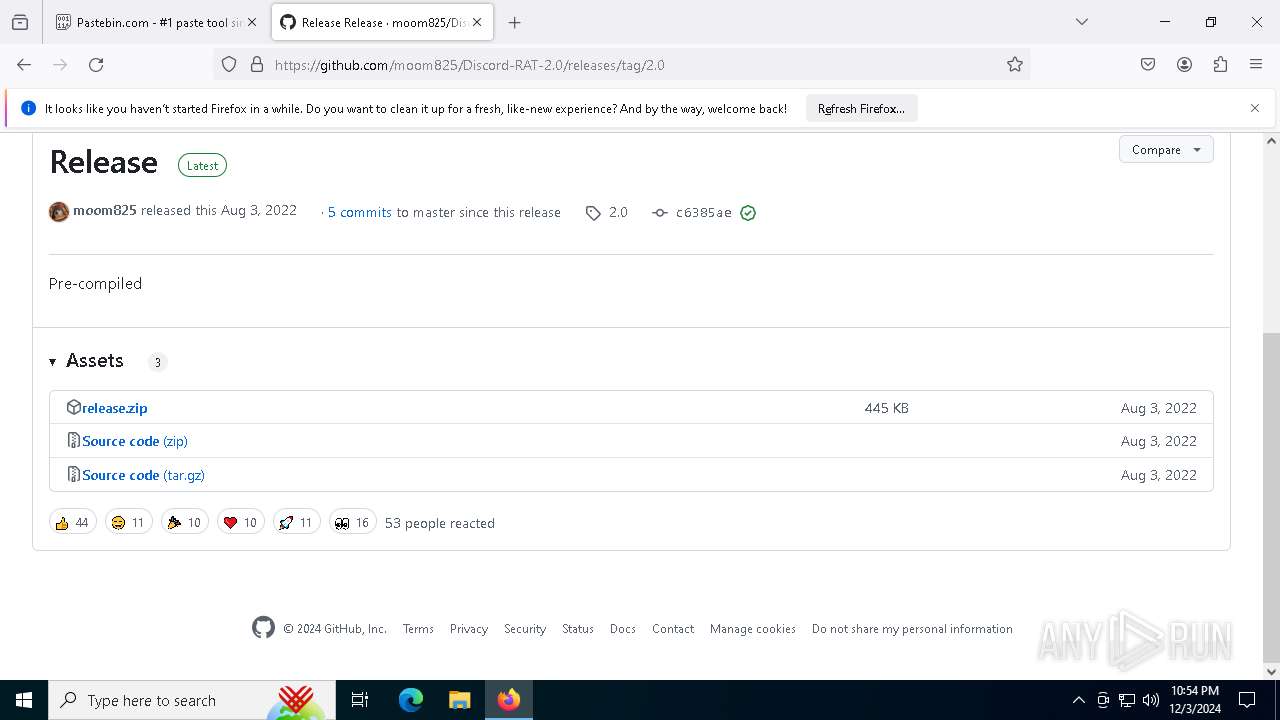
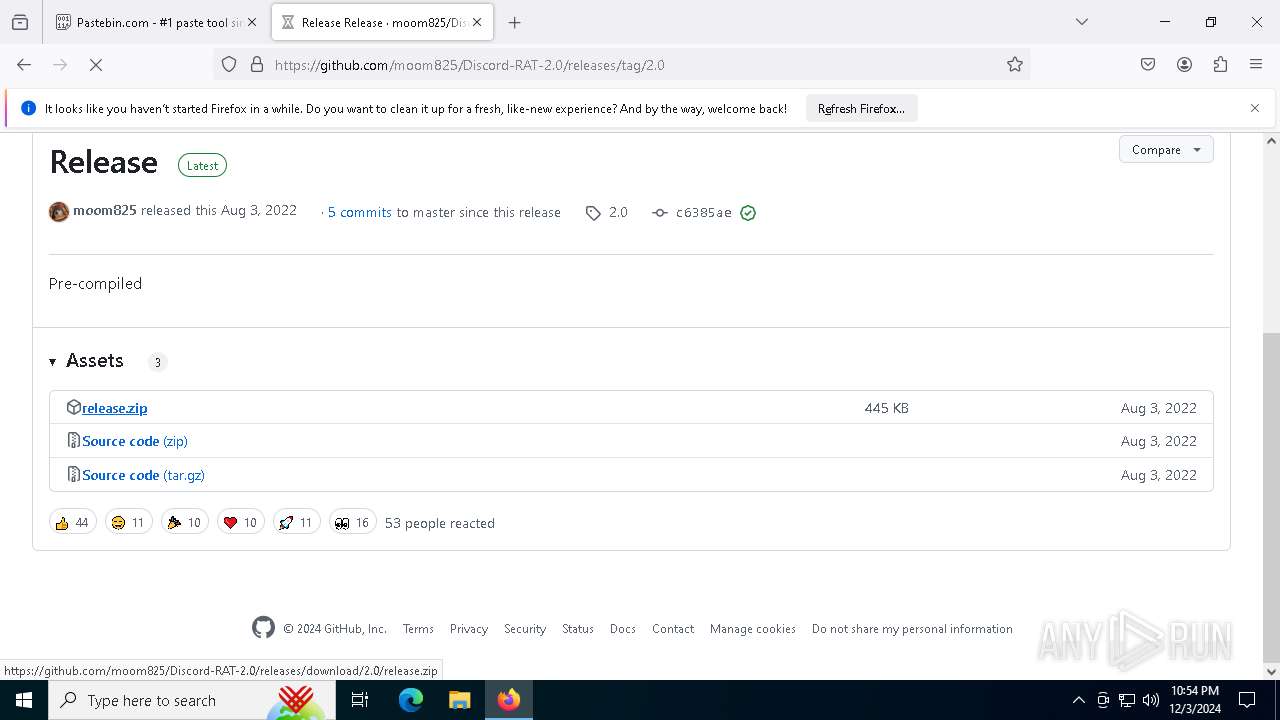
| download: | /moom825/Discord-RAT-2.0/releases/tag/2.0 |
| Full analysis: | https://app.any.run/tasks/1160a4d3-dc33-42f1-ab40-1976c5727c10 |
| Verdict: | Malicious activity |
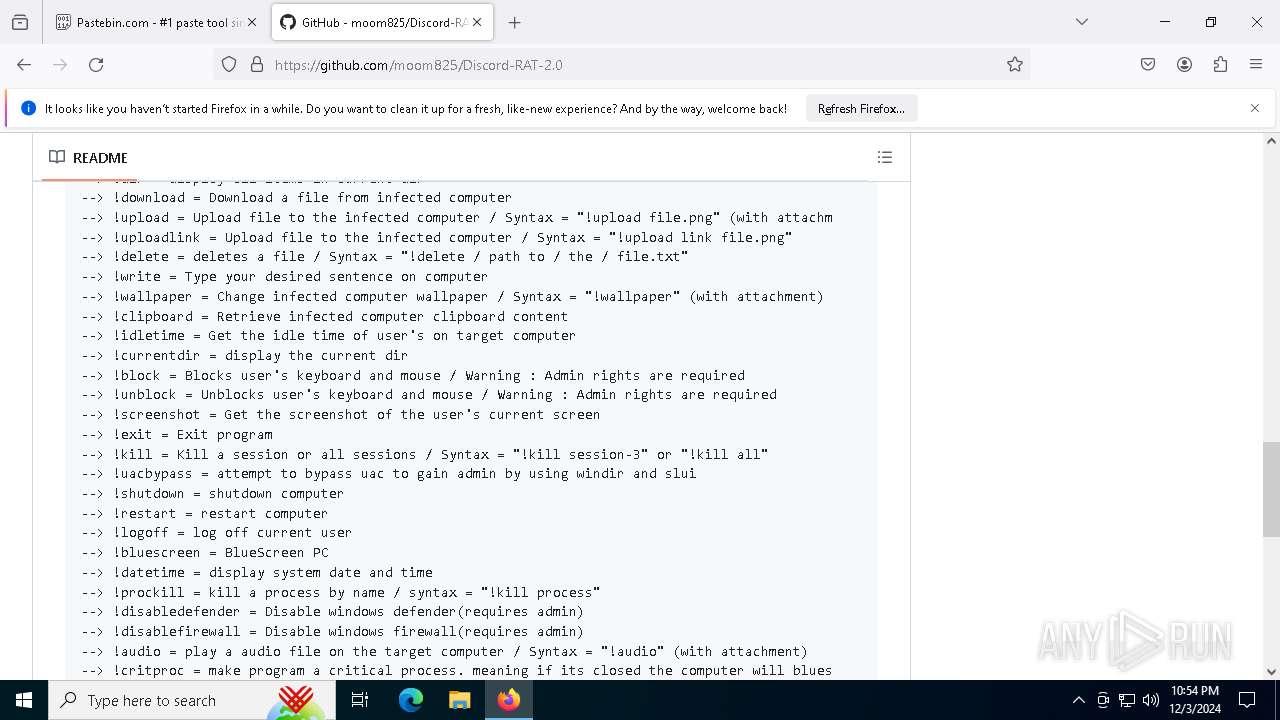
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | December 03, 2024, 22:52:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (1616) |
| MD5: | B846A39017A89CBBB077D4C481C6B866 |
| SHA1: | F9871534A7235C4A3ECD2E07946A1FE2810DE5D5 |
| SHA256: | 17B390173D9F001EE2F21BDB92ED2AEA18106A29371654B43B3E7AF39FCF4AF3 |
| SSDEEP: | 3072:tQGUmzeSVahcGRLIgX6UOeoSJzWmcUjFilMHjgj1GLhKWn+skgj1GLhKx0WspOL/:w+sHspOL/saqkPV9FemLtcsDSsmwC9Ob |
MALICIOUS
Stealers network behavior
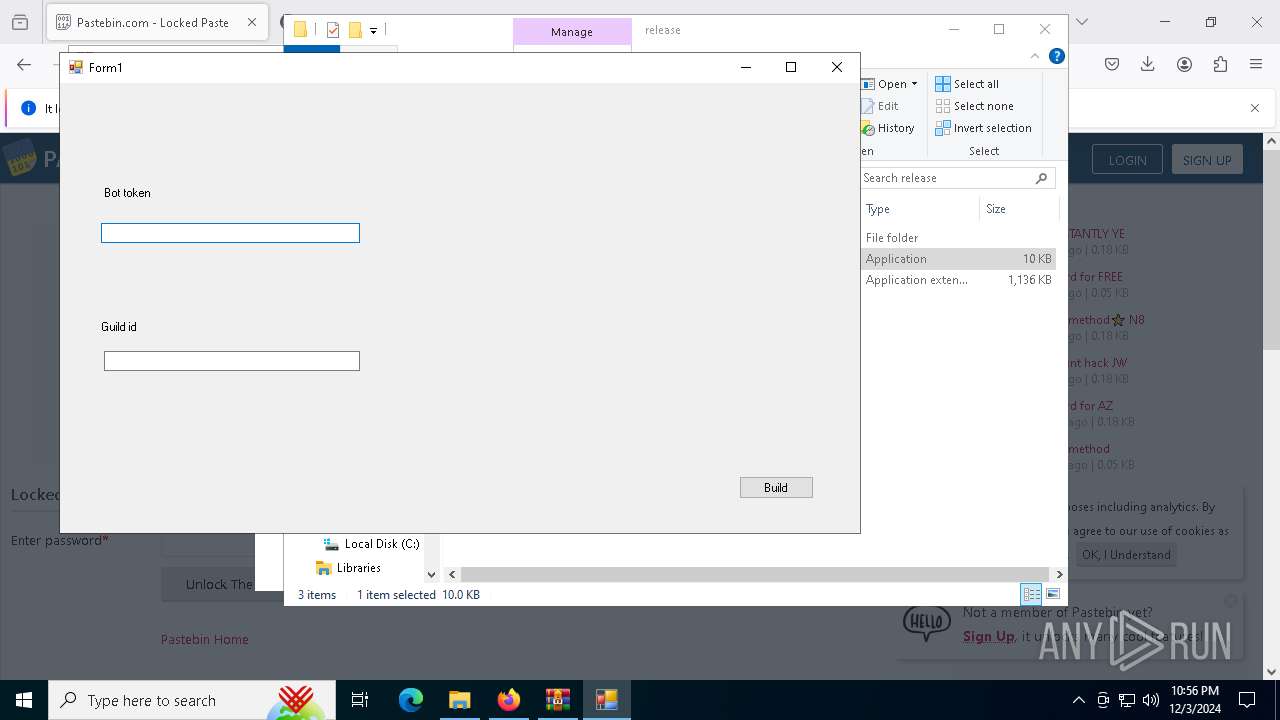
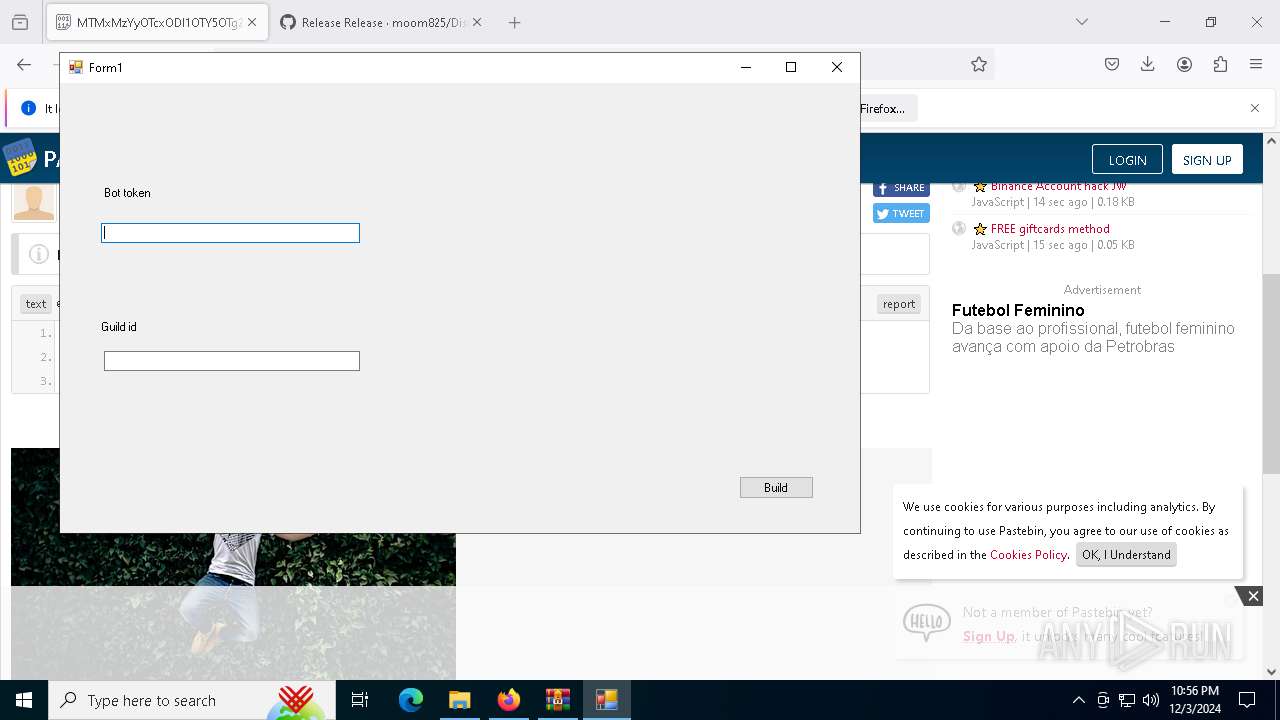
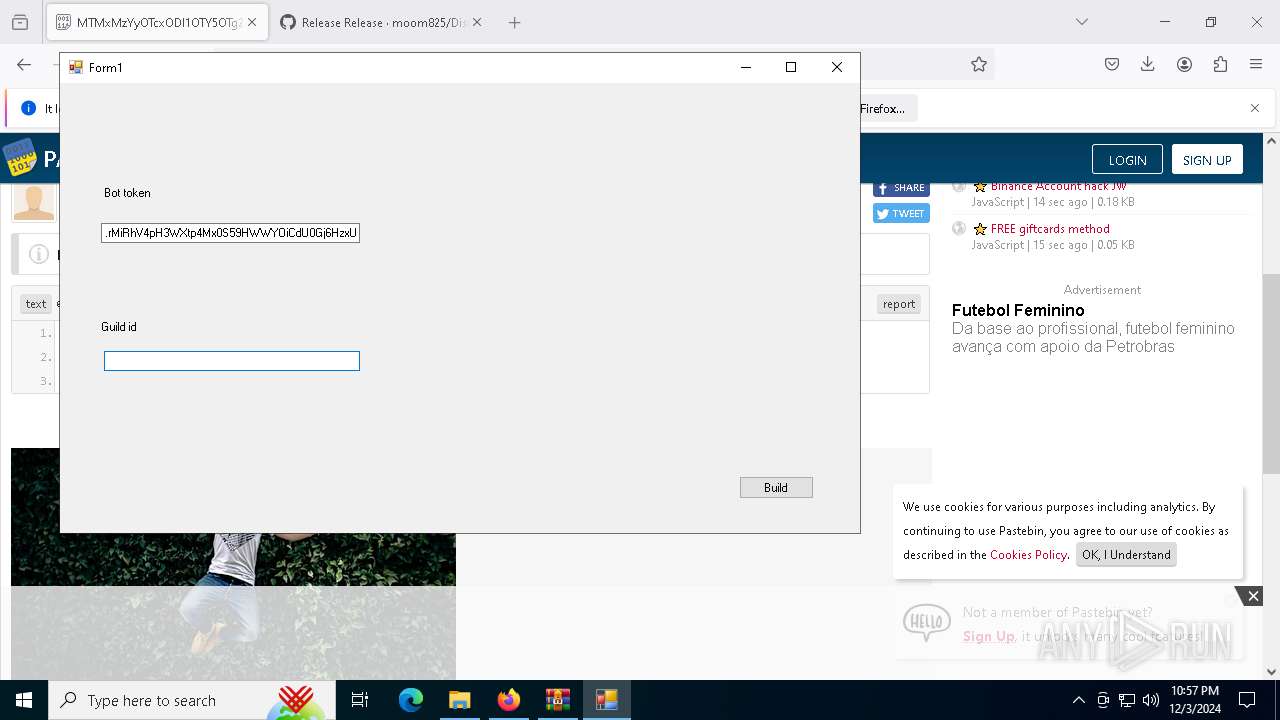
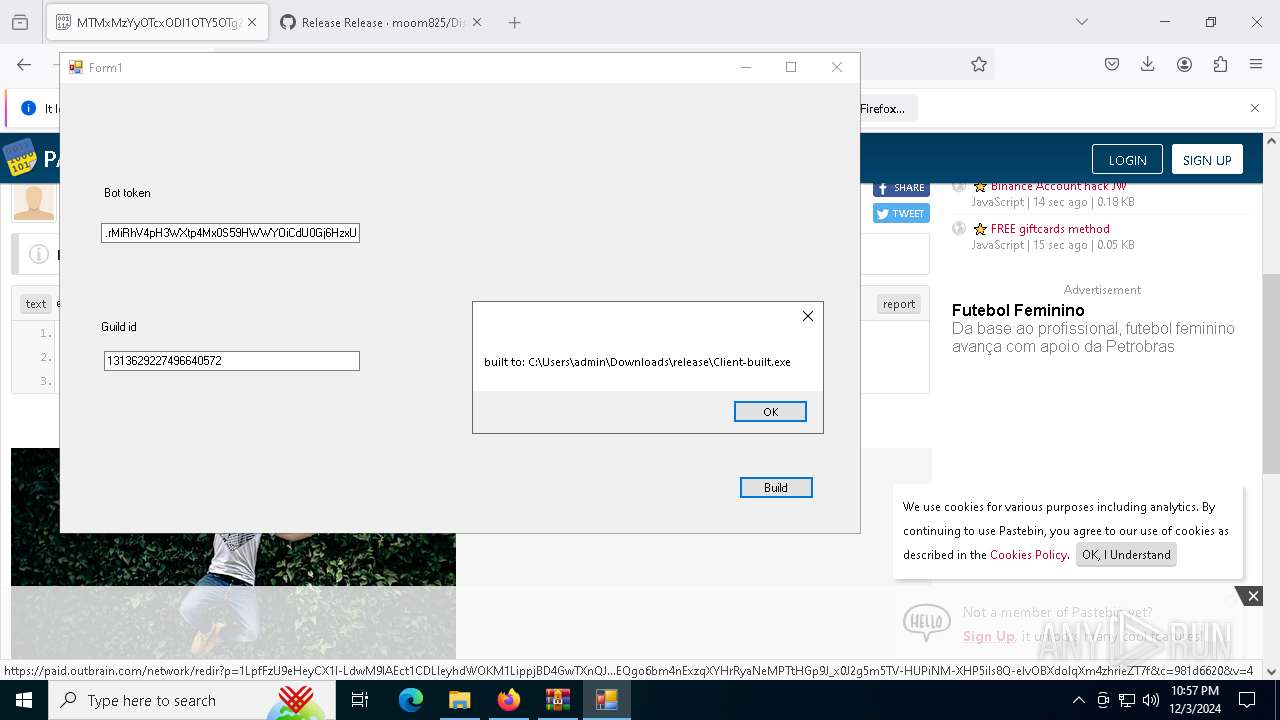
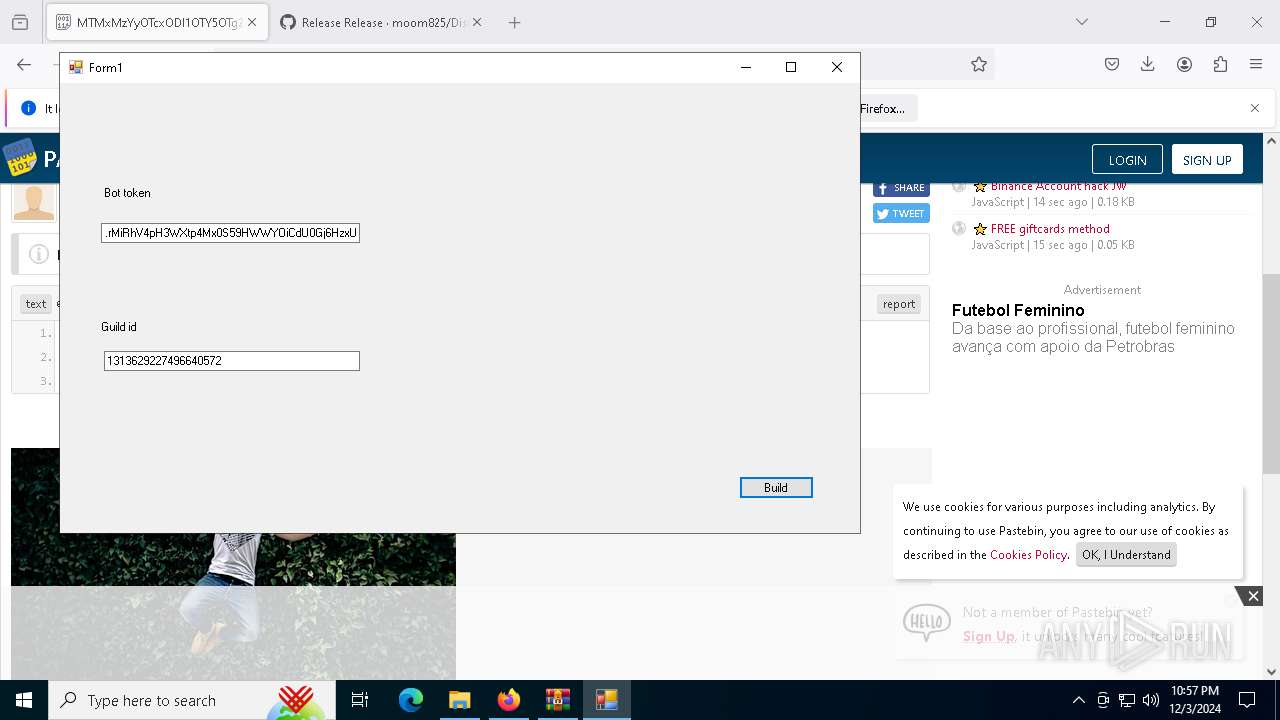
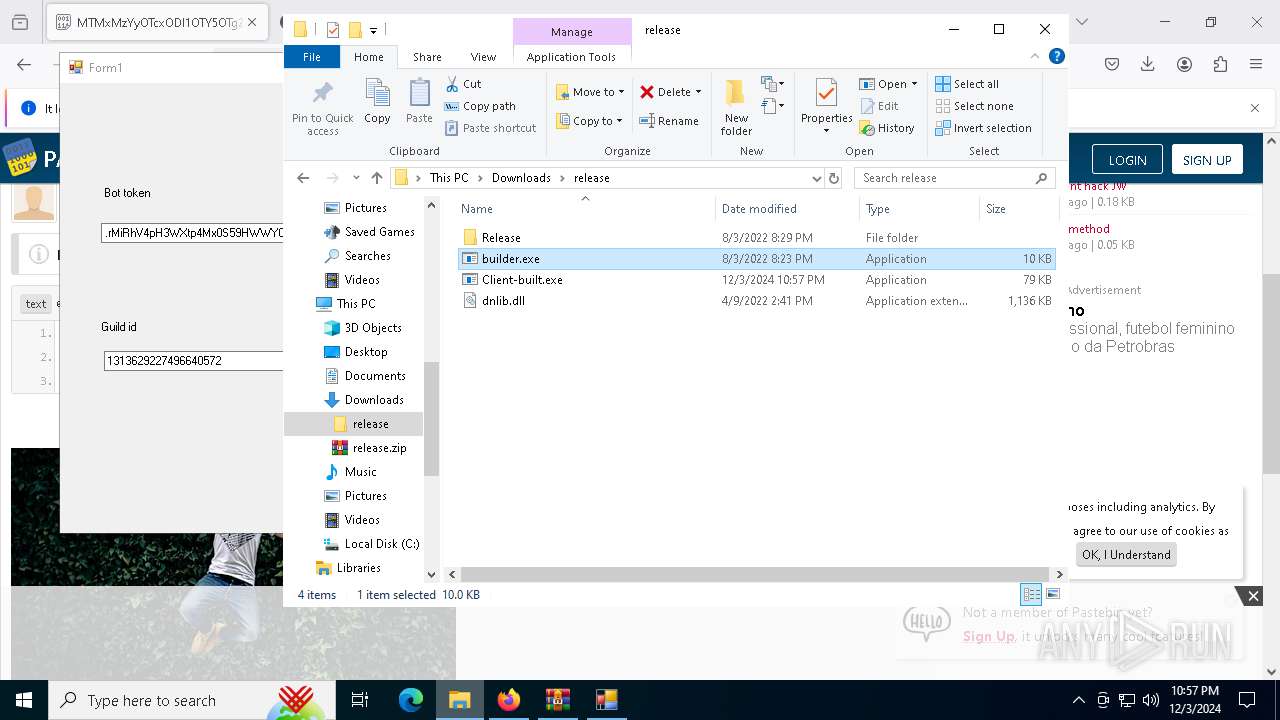
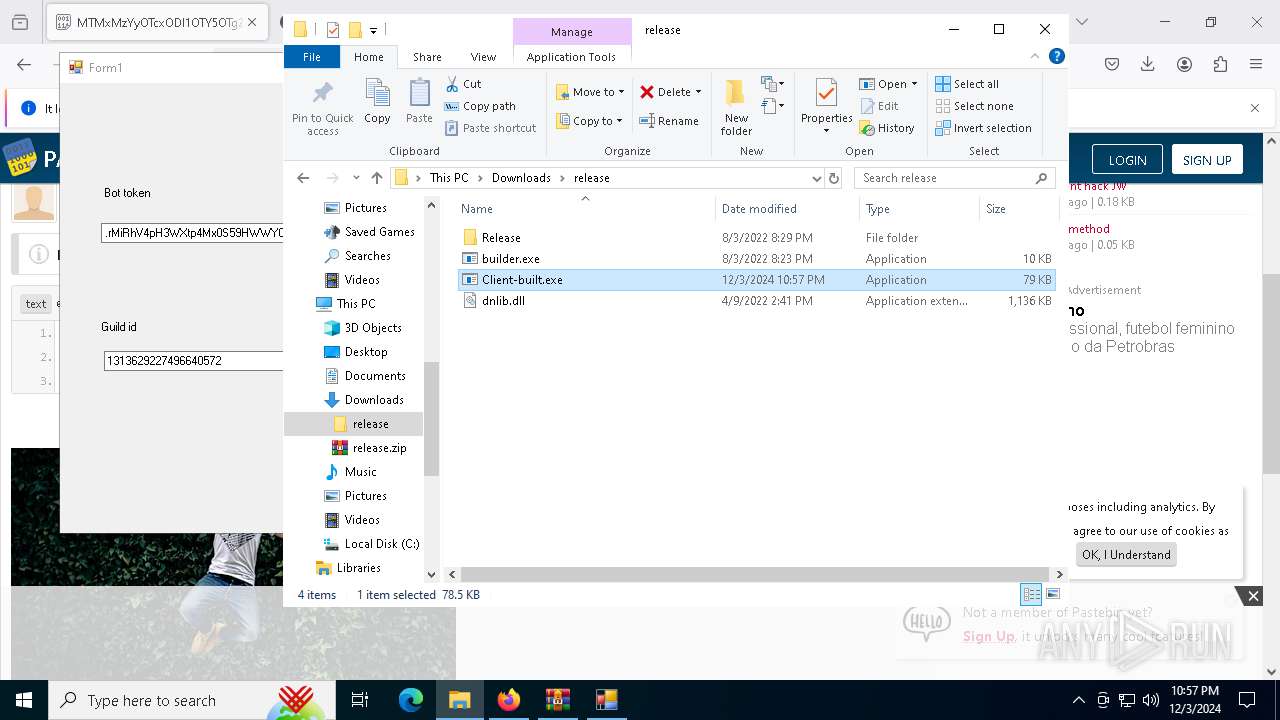
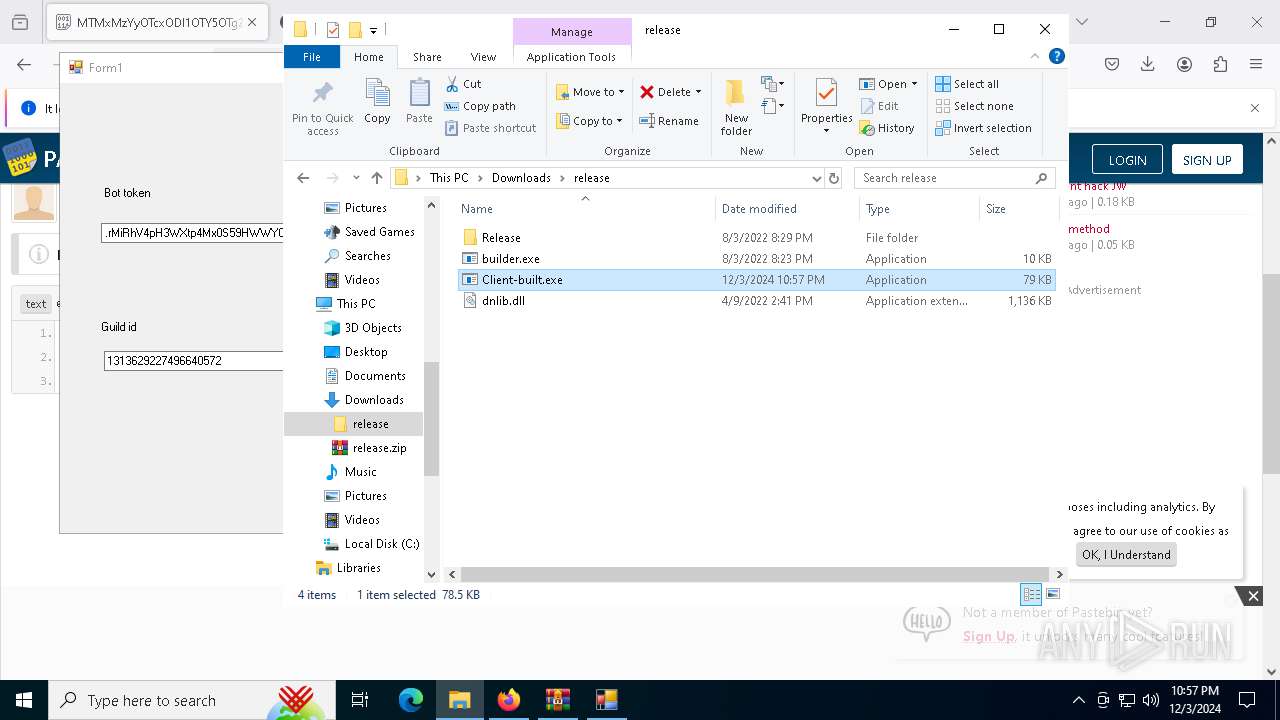
- Client-built.exe (PID: 4740)
Attempting to use instant messaging service
- Client-built.exe (PID: 4740)
DISCORDRAT has been detected (YARA)
- Client-built.exe (PID: 4740)
SUSPICIOUS
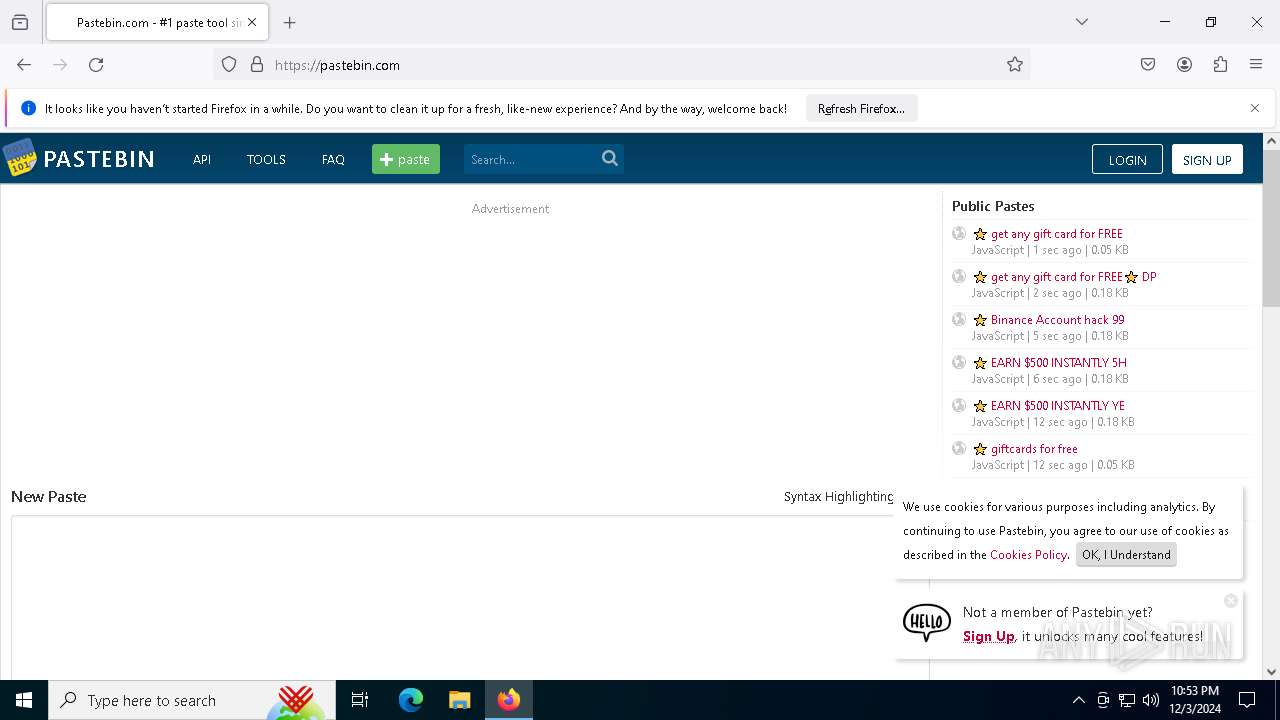
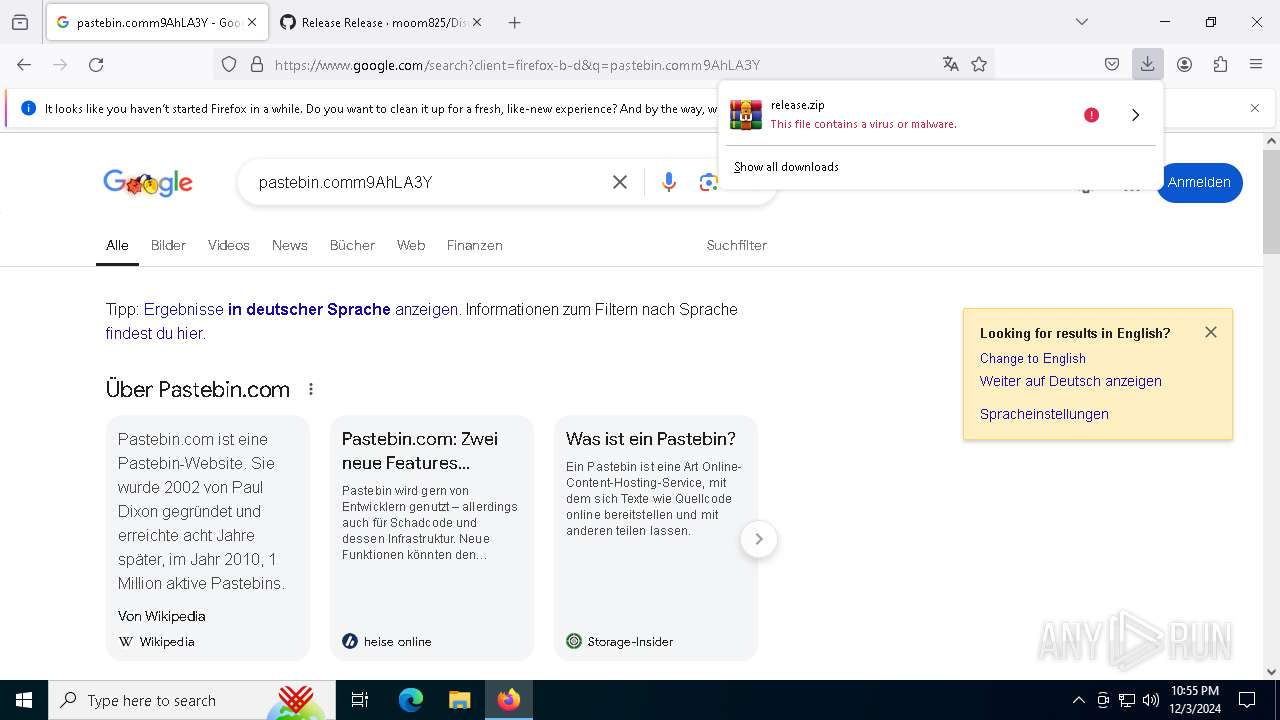
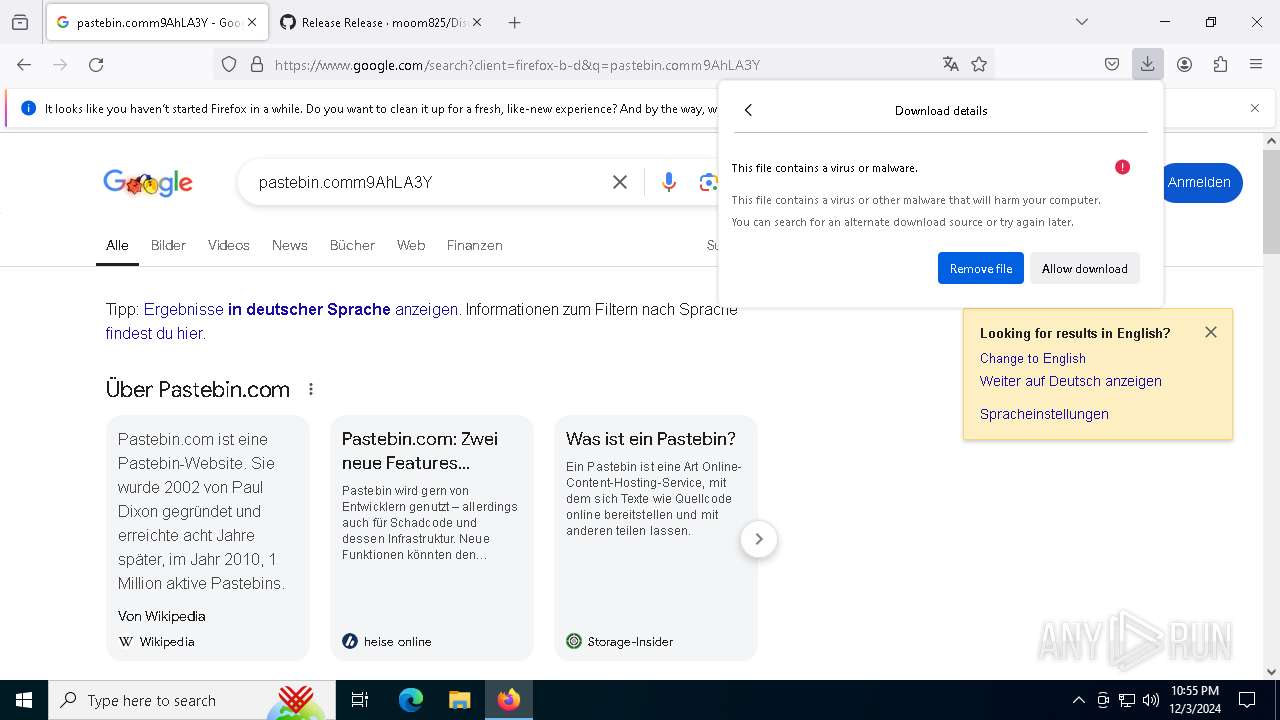
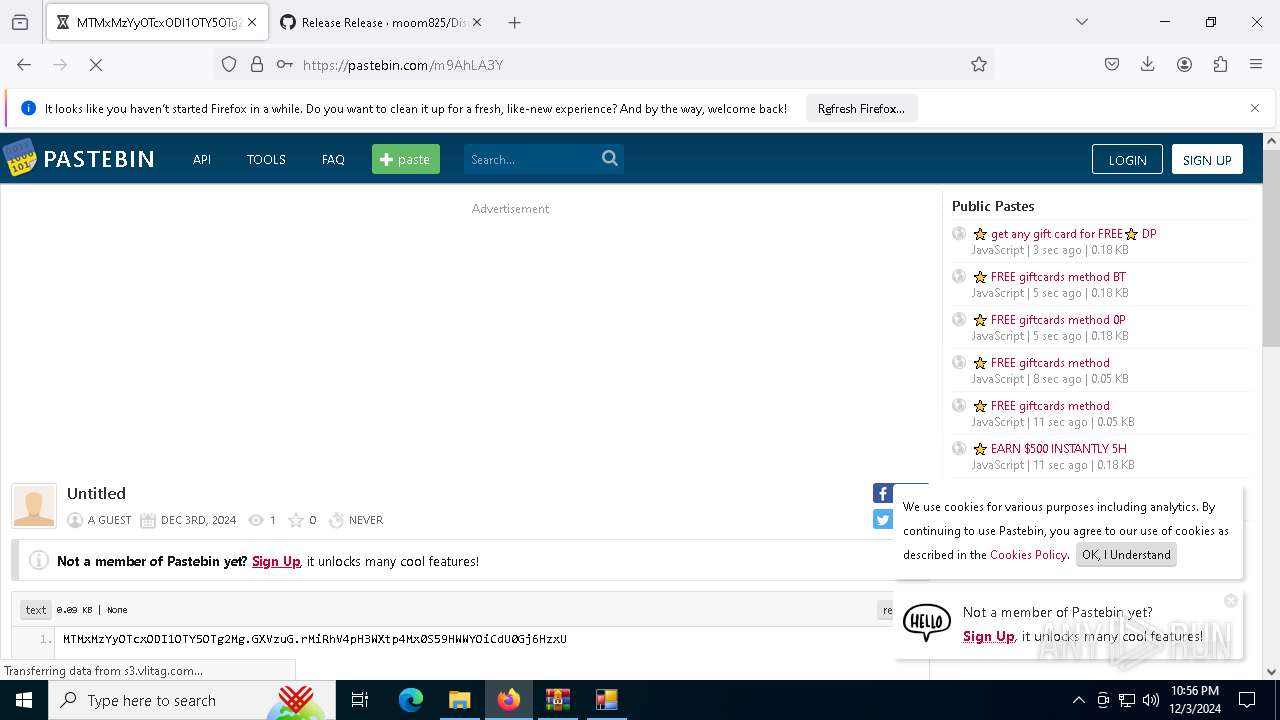
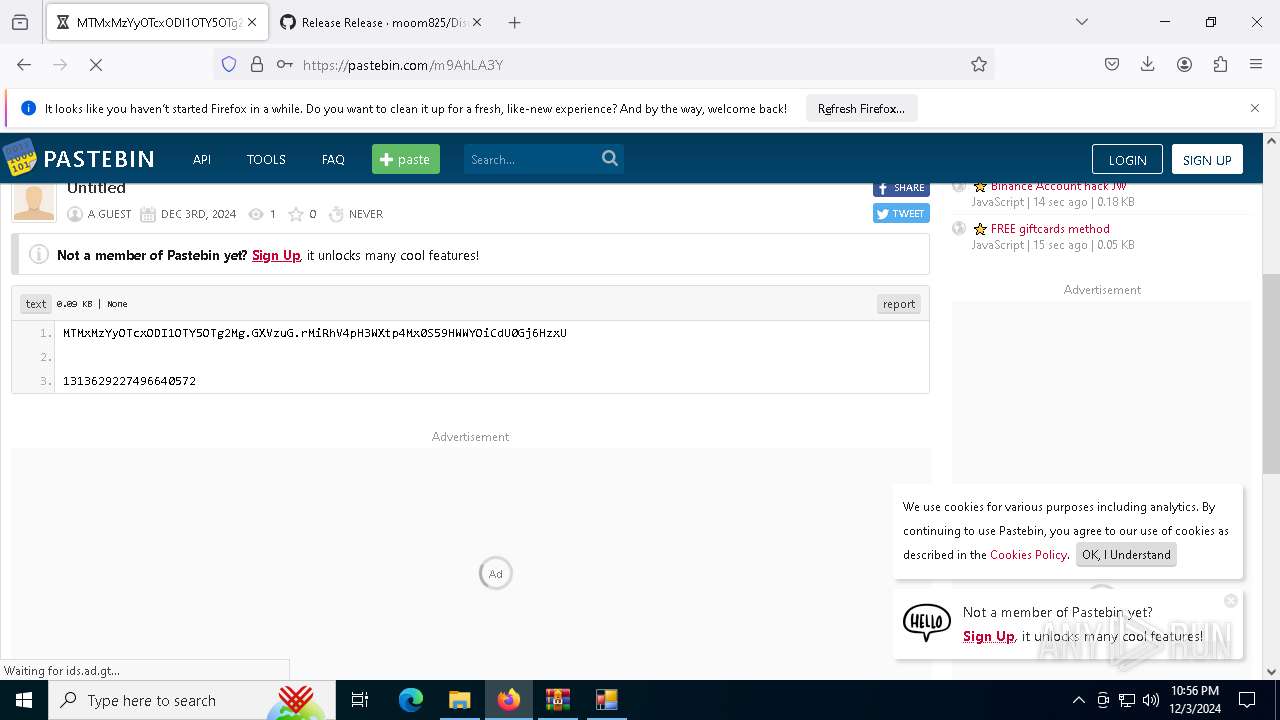
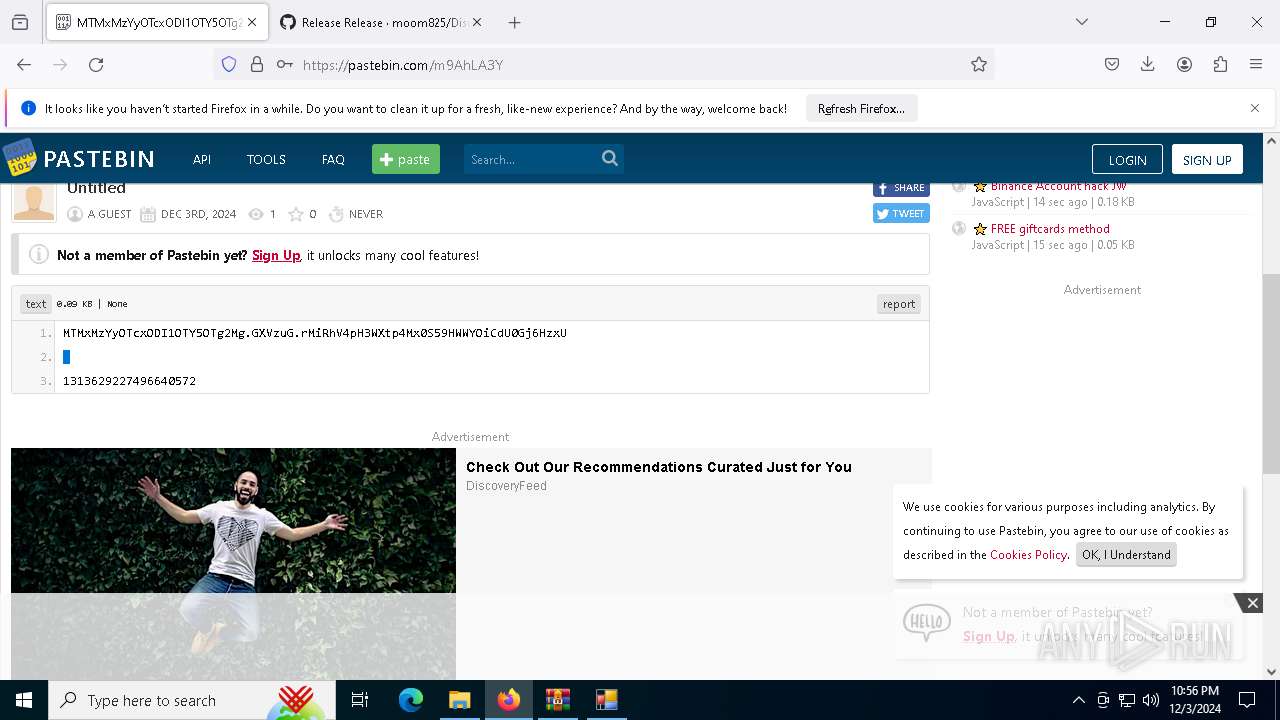
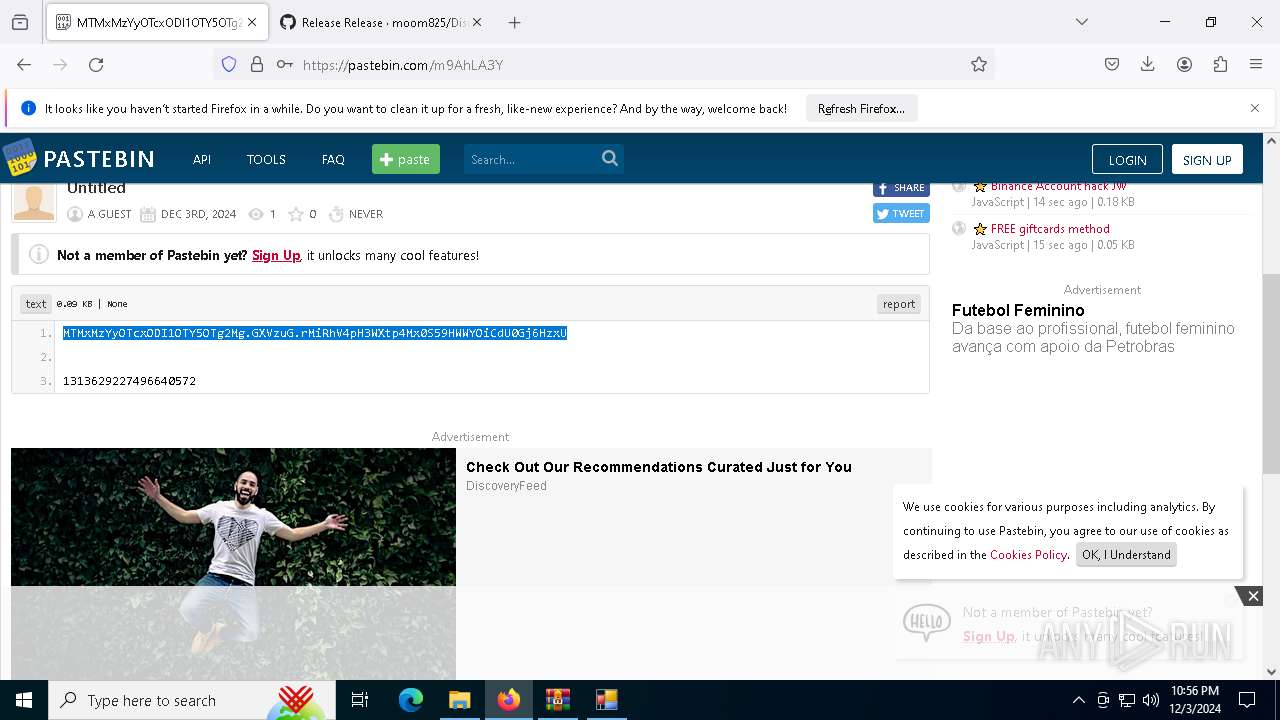
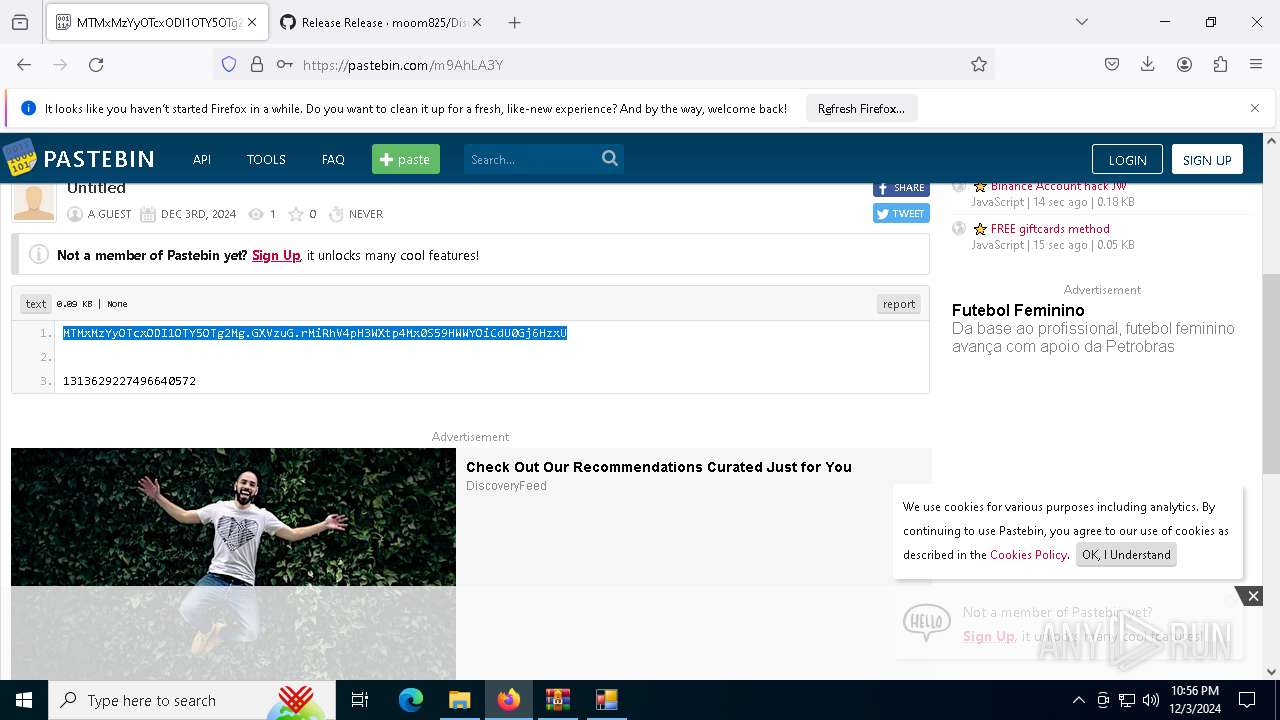
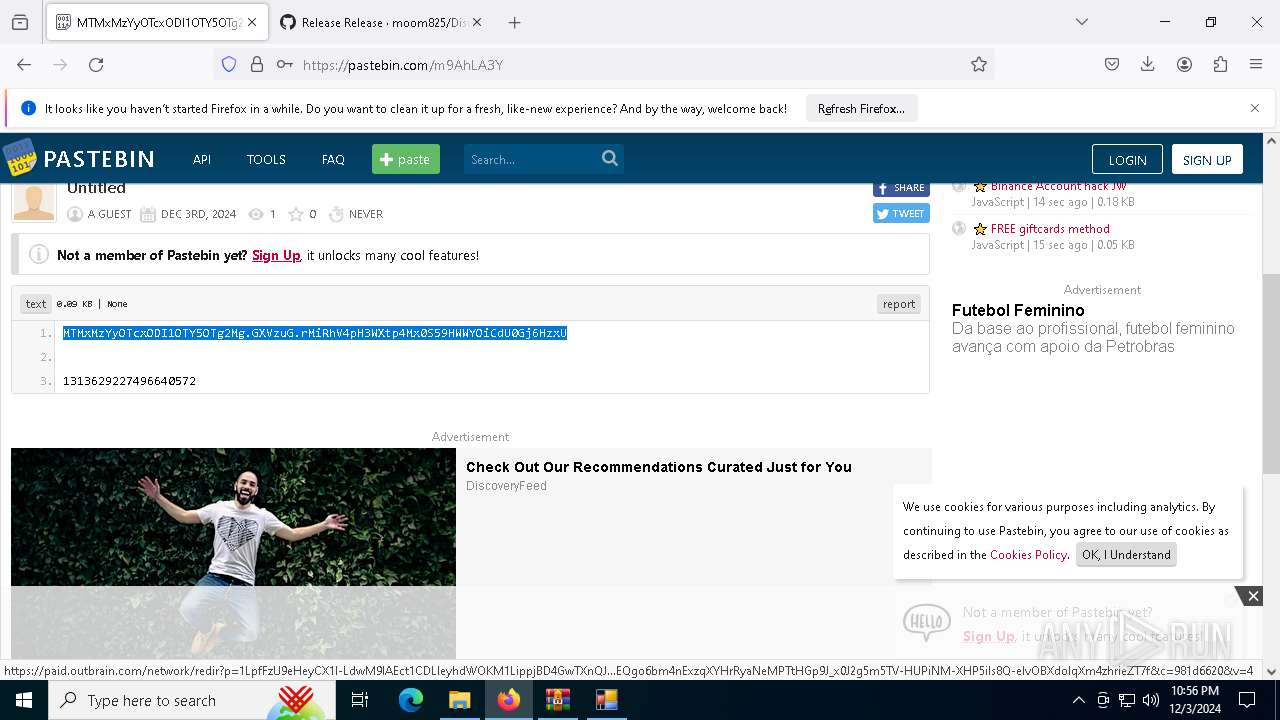
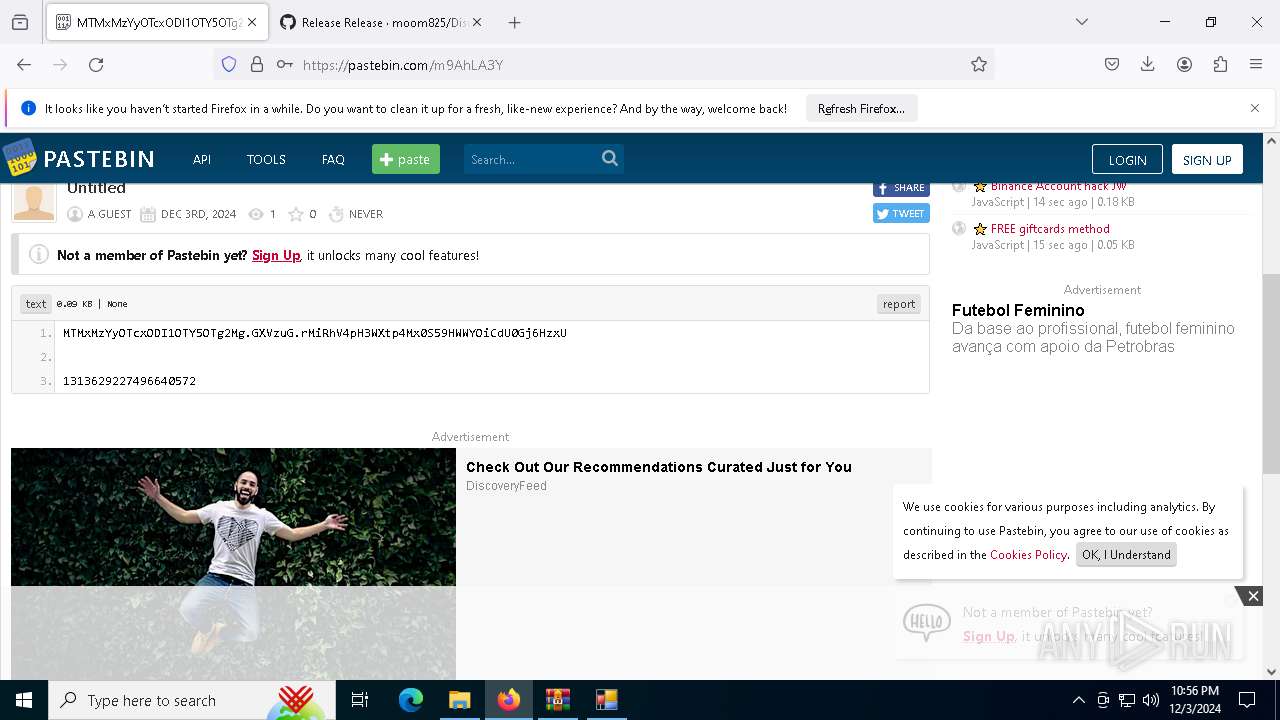
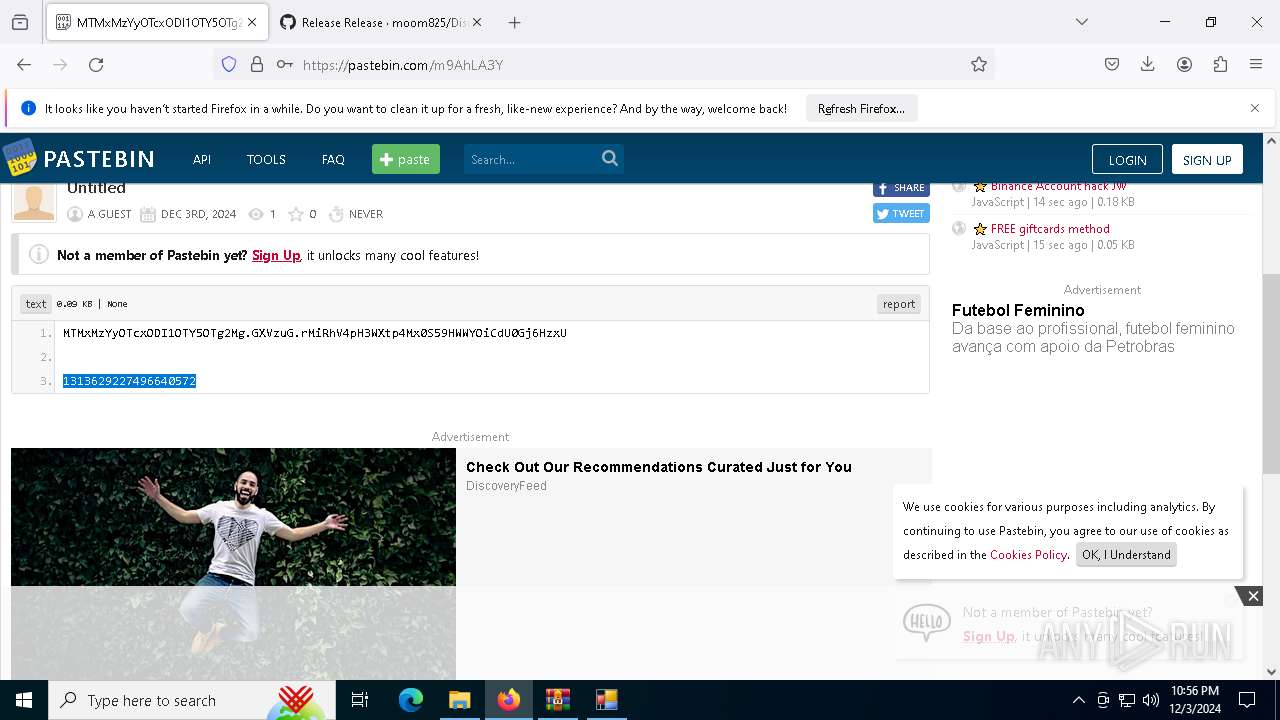
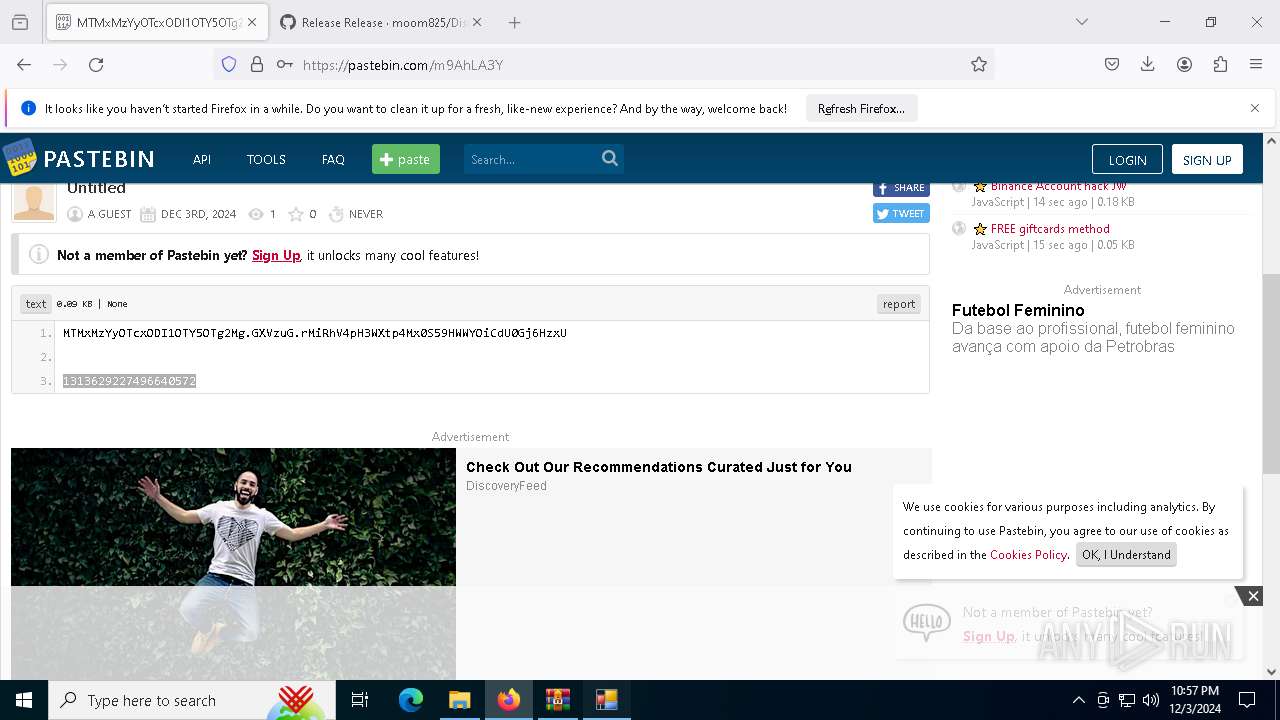
Requests information from PasteBin
- firefox.exe (PID: 4140)
Executable content was dropped or overwritten
- builder.exe (PID: 4188)
The process connected to a server suspected of theft
- Client-built.exe (PID: 4740)
Checks for external IP
- svchost.exe (PID: 2192)
- Client-built.exe (PID: 4740)
INFO
Manual execution by a user
- firefox.exe (PID: 4392)
- WinRAR.exe (PID: 5640)
- Client-built.exe (PID: 4740)
- builder.exe (PID: 4188)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6152)
Application launched itself
- firefox.exe (PID: 4392)
- firefox.exe (PID: 4140)
Attempting to use instant messaging service
- svchost.exe (PID: 2192)
- Client-built.exe (PID: 4740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | Release Release · moom825/Discord-RAT-2.0 · GitHub |
|---|---|
| RoutePattern: | /:user_id/:repository/releases/tag/*name |
| RouteController: | releases |
| RouteAction: | show |
| CurrentCatalogServiceHash: | 6f13f31f798a93a6b08d3be0727120e9af35851fac7b9c620d6cf9a70068c136 |
| RequestId: | 8AE8:327EBC:1E96F90:1F641DE:674F8BB3 |
| HtmlSafeNonce: | 79e0a74edf5a015da449c25c1aad094e4046aeff88d630de42890484f13eafea |
| VisitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4QUU4OjMyN0VCQzoxRTk2RjkwOjFGNjQxREU6Njc0RjhCQjMiLCJ2aXNpdG9yX2lkIjoiNTg0MjczMjY1MTg4Mzc1NDc1IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0= |
| VisitorHmac: | d2c16ea1efac35137efedb16cf6614550b5c71ce99dd276c042dc5fc588dab73 |
| HovercardSubjectTag: | repository:514392783 |
| GithubKeyboardShortcuts: | repository,copilot |
| GoogleSiteVerification: | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| OctolyticsUrl: | https://collector.github.com/github/collect |
| AnalyticsLocation: | /<user-name>/<repo-name>/releases/show |
| UserLogin: | - |
| Viewport: | width=device-width |
| Description: | Discord Remote Administration Tool fully written in c#, stub size of ~75kb, over 40 post exploitations modules - Release Release · moom825/Discord-RAT-2.0 |
| AppleItunesApp: | app-id=1477376905, app-argument=https://github.com/moom825/Discord-RAT-2.0/releases/tag/2.0 |
| TwitterImage: | https://opengraph.githubassets.com/e586f1df50993991c7c040bf64c4a26aed38e188d76f5a8325b5628d5c4b5b97/moom825/Discord-RAT-2.0/releases/tag/2.0 |
| TwitterSite: | @github |
| TwitterCard: | summary_large_image |
| TwitterTitle: | Release Release · moom825/Discord-RAT-2.0 |
| TwitterDescription: | Pre-compiled |
| Hostname: | github.com |
| ExpectedHostname: | github.com |
| HTTPEquivXPjaxVersion: | a3fccbbc47e59efe5da179856996add616f03e34d3398e2c6cd7ed1869365f99 |
| HTTPEquivXPjaxCspVersion: | ace39c3b6632770952207593607e6e0be0db363435a8b877b1f96abe6430f345 |
| HTTPEquivXPjaxCssVersion: | 3adbaefc258174e49a9472f62ba4ed262e7c0112f9e7266a3e927bd7b898716f |
| HTTPEquivXPjaxJsVersion: | 4beabdd0fbb99b09cd036910100c0444b454c234ffa1d1e7fa9530b1077bb7ab |
| TurboCacheControl: | no-preview |
| GoImport: | github.com/moom825/Discord-RAT-2.0 git https://github.com/moom825/Discord-RAT-2.0.git |
| OctolyticsDimensionUser_id: | 63253634 |
| OctolyticsDimensionUser_login: | moom825 |
| OctolyticsDimensionRepository_id: | 514392783 |
| OctolyticsDimensionRepository_nwo: | moom825/Discord-RAT-2.0 |
| OctolyticsDimensionRepository_public: | |
| OctolyticsDimensionRepository_is_fork: | - |
| OctolyticsDimensionRepository_network_root_id: | 514392783 |
| OctolyticsDimensionRepository_network_root_nwo: | moom825/Discord-RAT-2.0 |
| TurboBodyClasses: | logged-out env-production page-responsive |
| BrowserStatsUrl: | https://api.github.com/_private/browser/stats |
| BrowserErrorsUrl: | https://api.github.com/_private/browser/errors |
| ThemeColor: | #1e2327 |
| ColorScheme: | light dark |
Total processes
160
Monitored processes
32
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7792 -childID 20 -isForBrowser -prefsHandle 7888 -prefMapHandle 7884 -prefsLen 32110 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {fde9bb8d-d702-4eb2-8b14-ae0445031c38} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a6a97fc150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1136 -parentBuildID 20240213221259 -prefsHandle 1860 -prefMapHandle 1852 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {cf4b24a9-7255-4abb-8d15-ea808e4fcfe6} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a6a15f0610 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6292 -childID 16 -isForBrowser -prefsHandle 5144 -prefMapHandle 7296 -prefsLen 32110 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {ca1e8ee8-4d1b-4bc4-9f9f-becdf6c65760} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a6a563e690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3524 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2144 -prefMapHandle 2112 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f72933a2-3b8e-4a27-ac76-c2111004b22f} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a694682d10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3544 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6276 -childID 19 -isForBrowser -prefsHandle 7756 -prefMapHandle 5540 -prefsLen 32110 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {98cc8d84-5359-4310-aa66-ee5e9399b86c} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a6a9798a10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3920 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7116 -childID 11 -isForBrowser -prefsHandle 5132 -prefMapHandle 7024 -prefsLen 32060 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {1f125659-eec8-43c3-a447-a6551fd5f6a8} 4140 "\\.\pipe\gecko-crash-server-pipe.4140" 1a6a87d0850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 4140 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
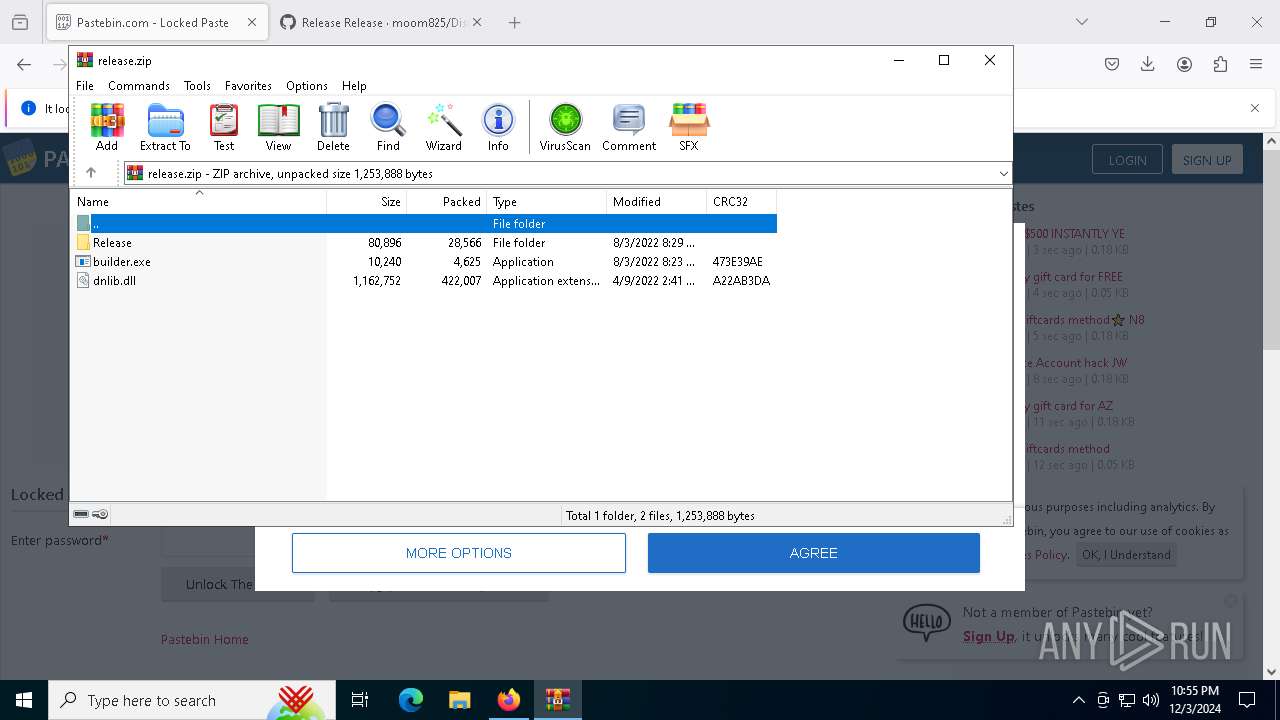
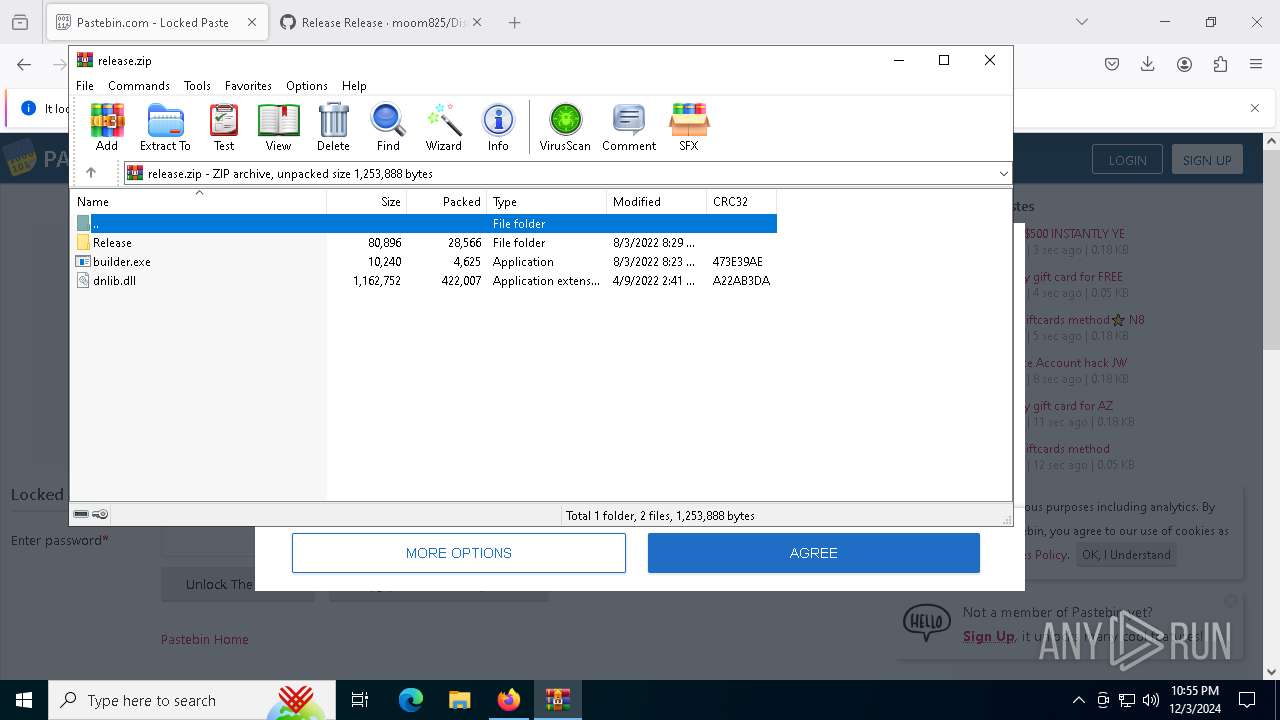
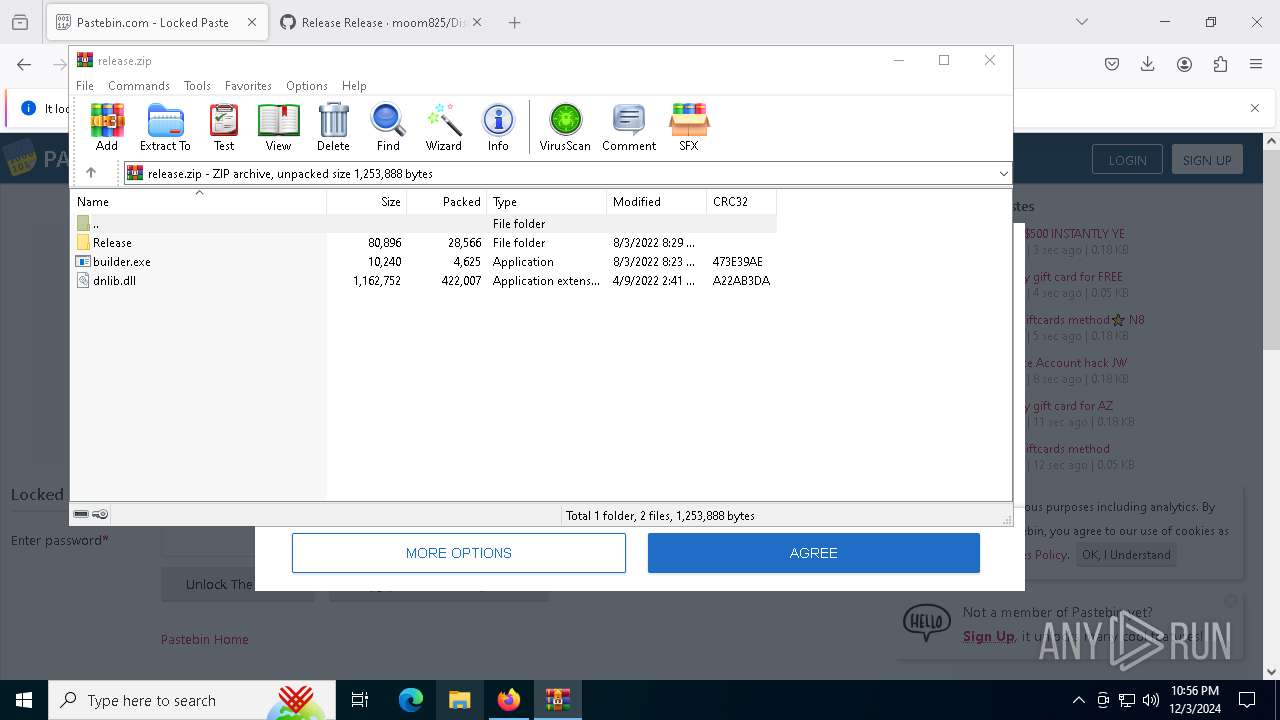
| 4188 | "C:\Users\admin\Downloads\release\builder.exe" | C:\Users\admin\Downloads\release\builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: builder Version: 1.0.0.0 Modules
| |||||||||||||||
| 4392 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
32 661
Read events
32 622
Write events
26
Delete events
13
Modification events
| (PID) Process: | (4140) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\release.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
4
Suspicious files
255
Text files
54
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:FD124C2980C886606A119AB3BC98033F | SHA256:725E927B44AA2DB61F6A6A2943DAE2D9B980C7C616D1BDF9DEEF18E8291A3492 | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
116
TCP/UDP connections
443
DNS requests
538
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4140 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5776 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5776 | svchost.exe | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.79.89.142:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.86.251.9:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2192 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2 ETPRO signatures available at the full report