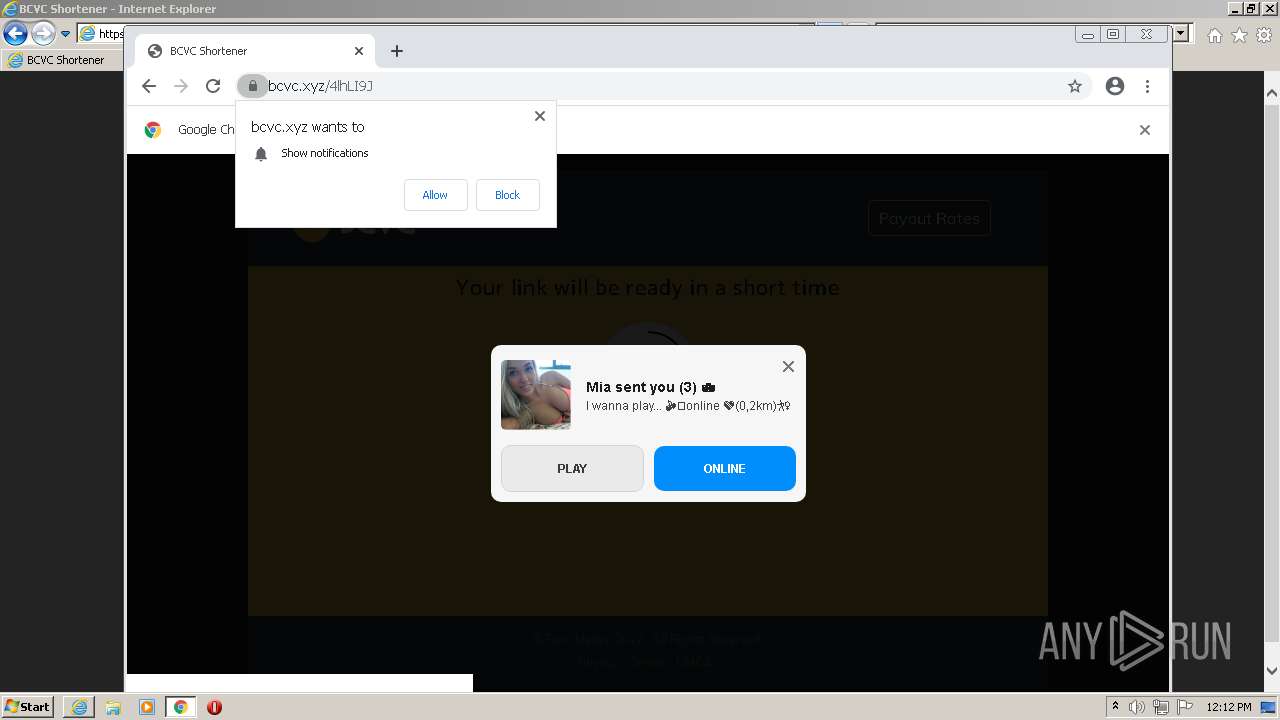
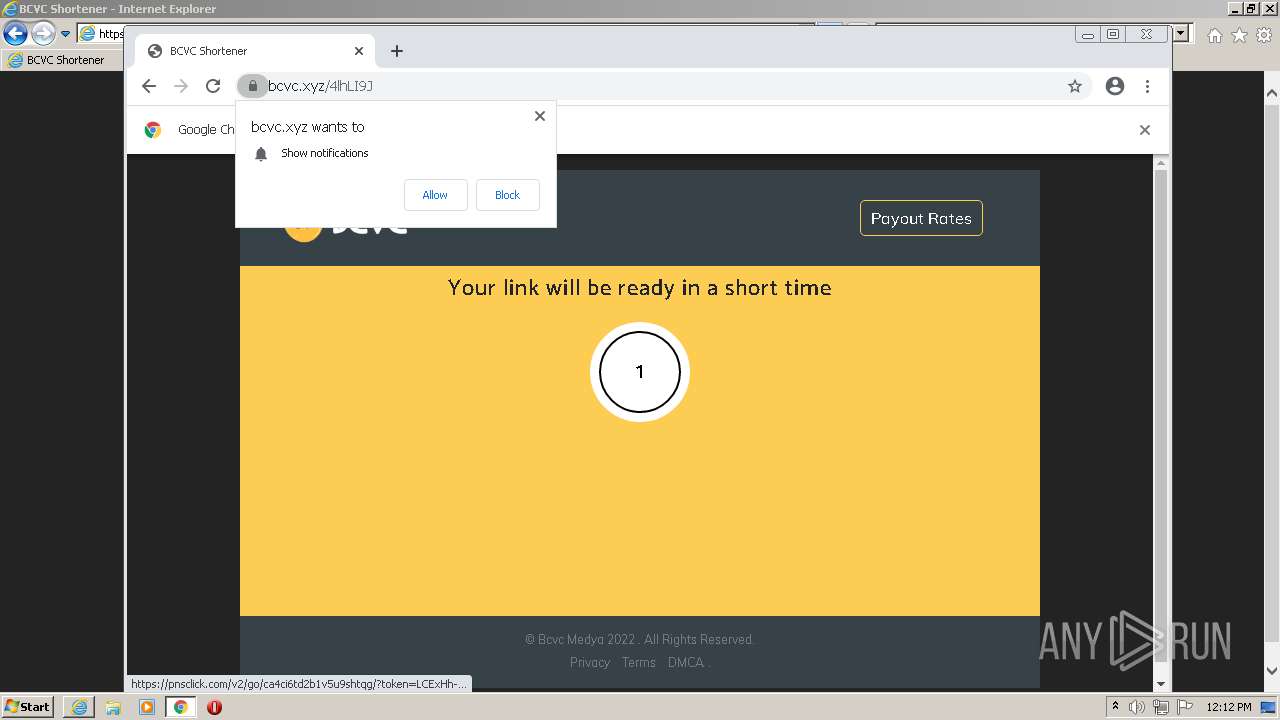
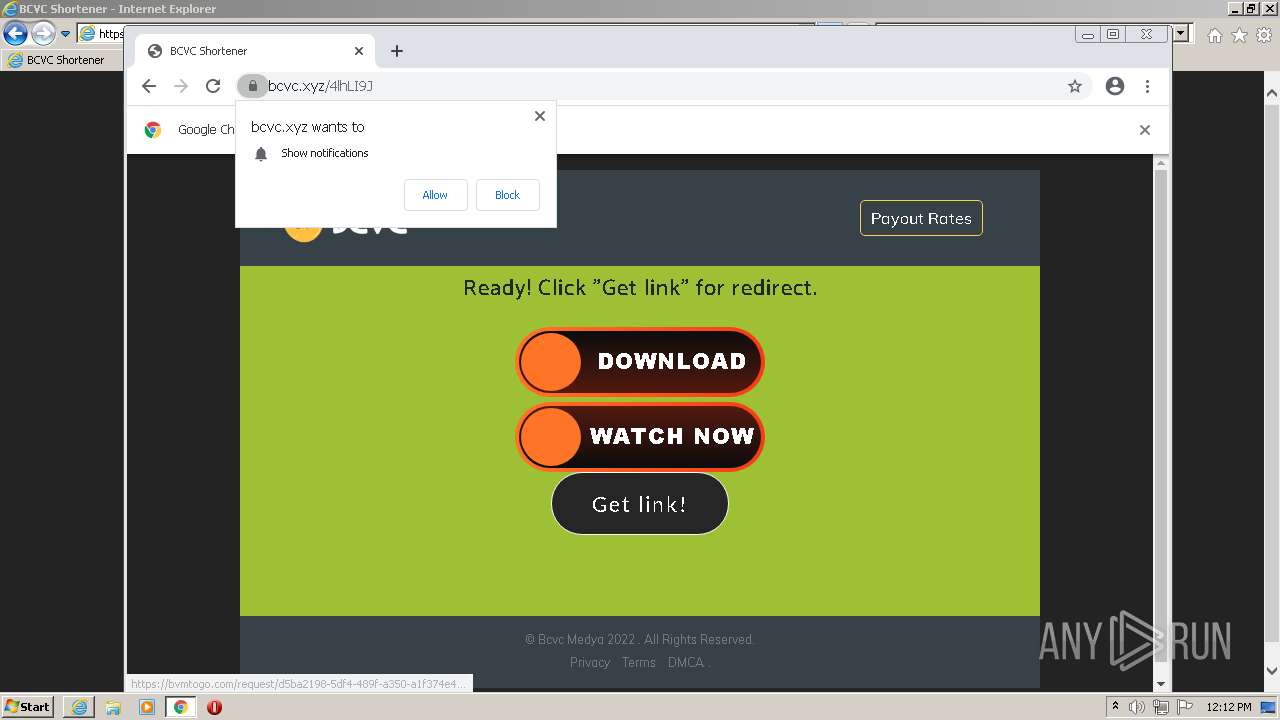
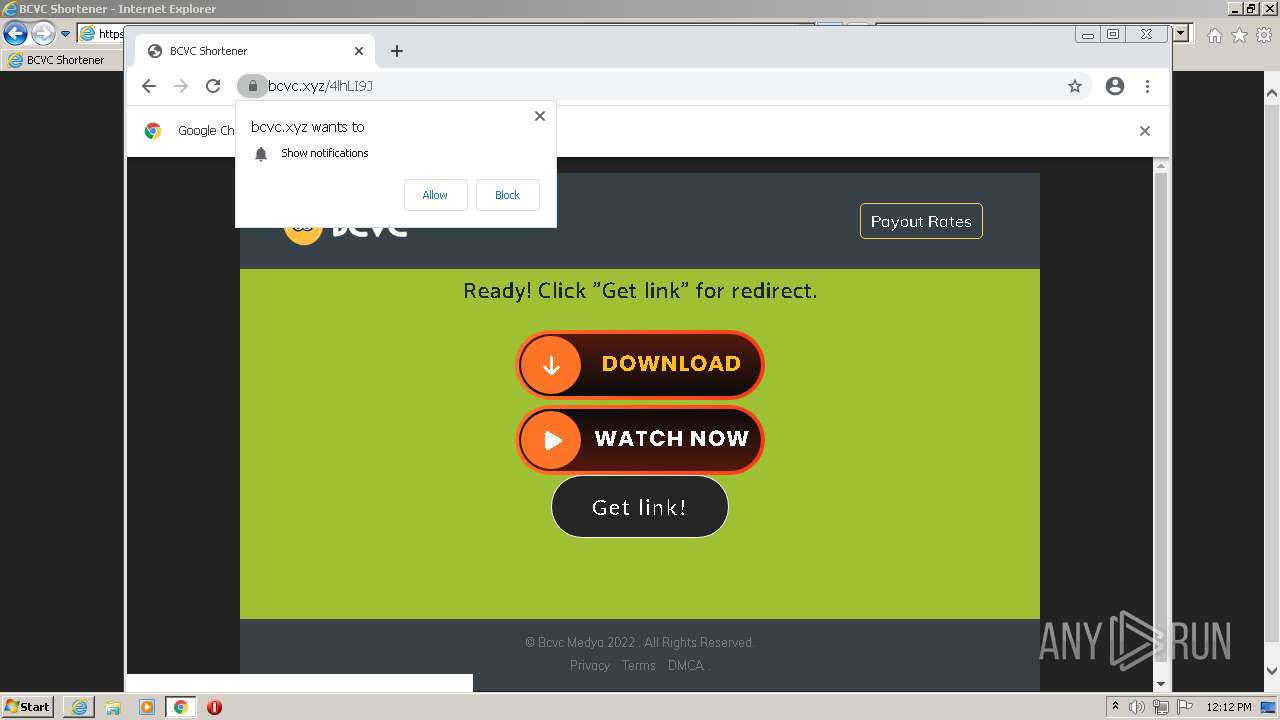
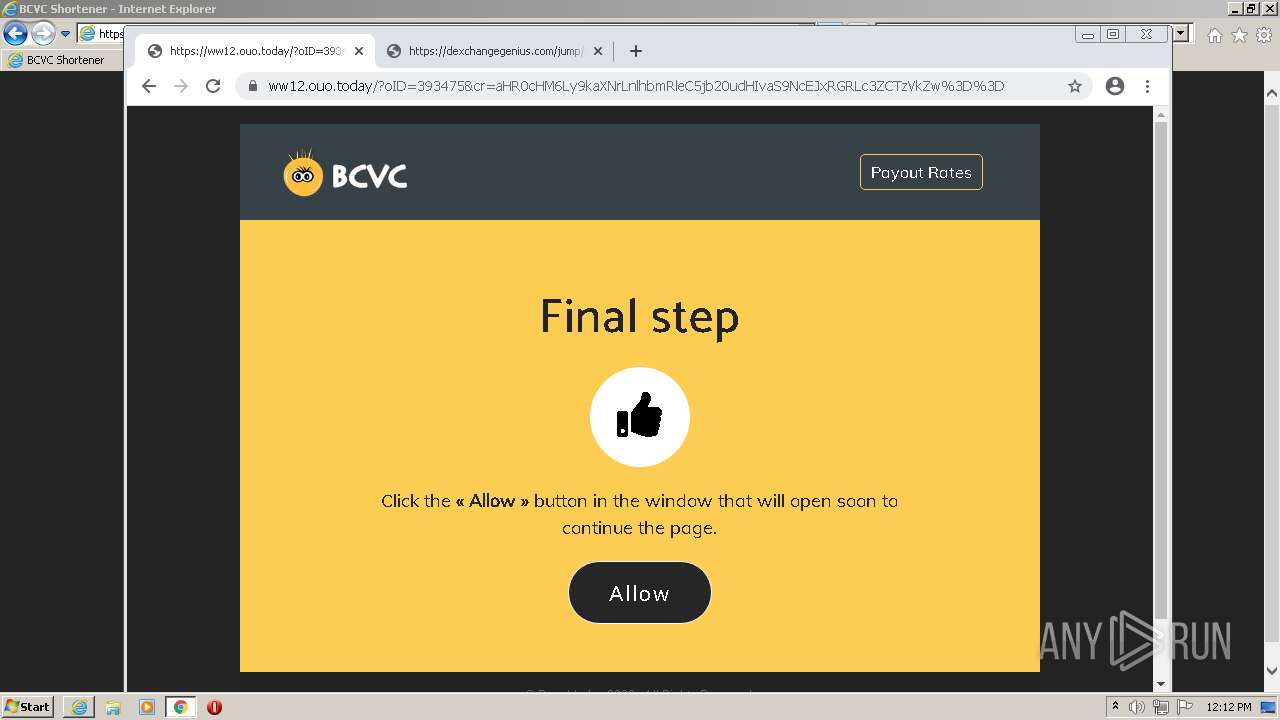
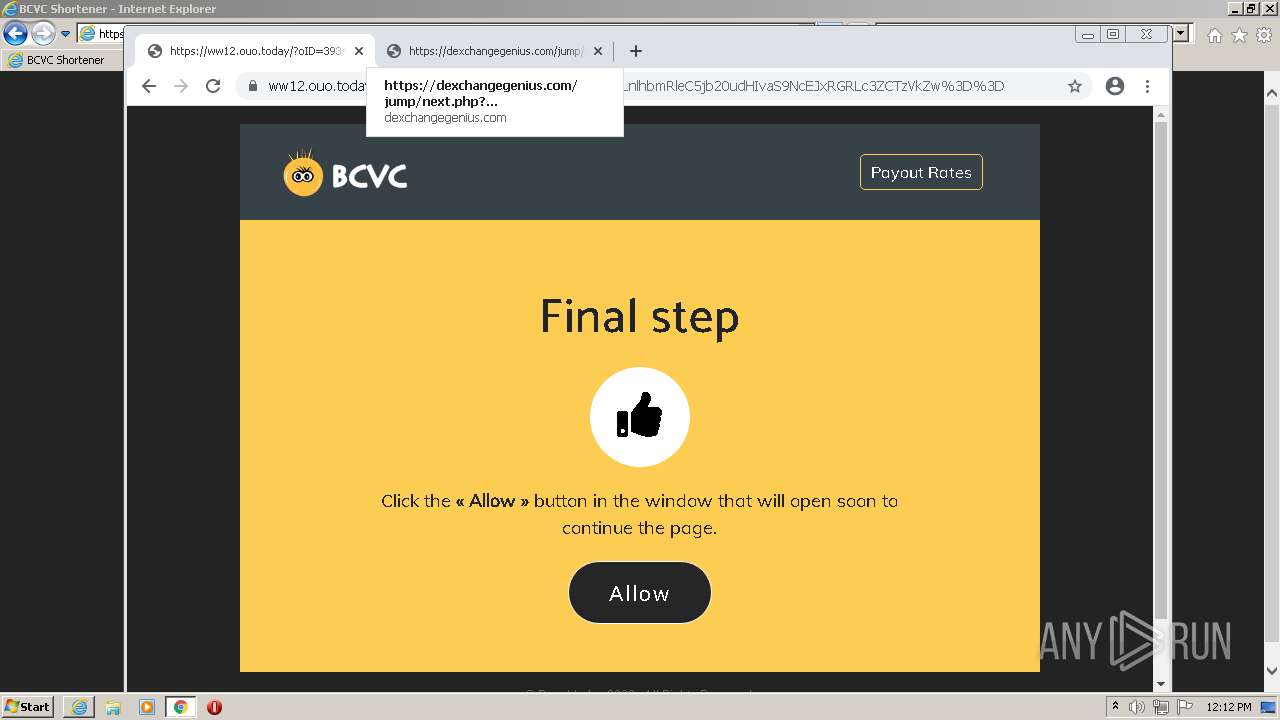
| URL: | http://bc.vc/4lhLI9J |
| Full analysis: | https://app.any.run/tasks/bd8e624d-e097-4fc2-9764-6bd1b5a76507 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 11:12:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CB0DDA9E24623F55520F874EF5ED0C30 |
| SHA1: | FE62CAF3F411CDD14F13EA572096A8A49DF8466D |
| SHA256: | 178485B0B778C3FE54BE2DA8424867E9ED181D251AF2DD7FCE8306AF0C1E9553 |
| SSDEEP: | 3:N1KccRDse:CcUN |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 2804)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2136)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3232)
Drops a file with a compile date too recent
- chrome.exe (PID: 2804)
Executable content was dropped or overwritten
- chrome.exe (PID: 2804)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1976)
Application launched itself
- iexplore.exe (PID: 1976)
- chrome.exe (PID: 3232)
Reads the computer name
- iexplore.exe (PID: 2136)
- iexplore.exe (PID: 1976)
- chrome.exe (PID: 3232)
- chrome.exe (PID: 2272)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 1260)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 552)
Reads settings of System Certificates
- iexplore.exe (PID: 2136)
- iexplore.exe (PID: 1976)
- chrome.exe (PID: 2288)
Checks supported languages
- iexplore.exe (PID: 1976)
- iexplore.exe (PID: 2136)
- chrome.exe (PID: 3232)
- chrome.exe (PID: 3384)
- chrome.exe (PID: 2272)
- chrome.exe (PID: 476)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 1520)
- chrome.exe (PID: 3028)
- chrome.exe (PID: 684)
- chrome.exe (PID: 2412)
- chrome.exe (PID: 300)
- chrome.exe (PID: 2152)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 4052)
- chrome.exe (PID: 3572)
- chrome.exe (PID: 992)
- chrome.exe (PID: 2228)
- chrome.exe (PID: 2672)
- chrome.exe (PID: 3272)
- chrome.exe (PID: 1780)
- chrome.exe (PID: 3588)
- chrome.exe (PID: 1260)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 3196)
- chrome.exe (PID: 2660)
- chrome.exe (PID: 552)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 2676)
- chrome.exe (PID: 2992)
- chrome.exe (PID: 1616)
- chrome.exe (PID: 2804)
- chrome.exe (PID: 2712)
- chrome.exe (PID: 2096)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 412)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 2692)
Reads internet explorer settings
- iexplore.exe (PID: 2136)
Checks Windows Trust Settings
- iexplore.exe (PID: 2136)
- iexplore.exe (PID: 1976)
Changes settings of System certificates
- iexplore.exe (PID: 1976)
Creates files in the user directory
- iexplore.exe (PID: 2136)
- chrome.exe (PID: 3232)
- iexplore.exe (PID: 1976)
Manual execution by user
- chrome.exe (PID: 3232)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1976)
Reads the hosts file
- chrome.exe (PID: 2288)
- chrome.exe (PID: 3232)
Reads the date of Windows installation
- chrome.exe (PID: 4088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
40
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1864 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2208 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1584 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1728 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1780 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,3747593904236955651,13363404856935905949,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2308 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
39 924
Read events
39 681
Write events
232
Delete events
11
Modification events
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960899 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960899 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
248
Text files
240
Unknown types
70
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar567F.tmp | cat | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab567E.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab56CE.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar56DF.tmp | cat | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | der | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
188
DNS requests
107
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adxv4tdkogkso3qjkj3bzwpvgyya_7350/hfnkpimlhhgieaddgfemjhofmfblmnib_7350_all_dip22yeoiod4ktdgnrsrbpono4.crx3 | US | — | — | whitelisted |
2136 | iexplore.exe | GET | 200 | 92.123.224.113:80 | http://e1.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTvkAFw3ViPKmUeIVEf3NC7b1ErqwQUWvPtK%2Fw2wjd5uVIw6lRvz1XLLqwCEgMnCufLLrHBjN%2FBOZ2g77c%2BnQ%3D%3D | unknown | der | 344 b | whitelisted |
1976 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
2136 | iexplore.exe | GET | 200 | 104.90.178.254:80 | http://x2.c.lencr.org/ | NL | der | 299 b | whitelisted |
1976 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2136 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2136 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCdUrA%2FwvrytArhIvu6cF3d | US | der | 472 b | whitelisted |
2136 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2136 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG3aTvFLTYzNCmxS2fUJutw%3D | US | der | 471 b | whitelisted |
2136 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0d6970c7831bbe12 | US | compressed | 60.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2136 | iexplore.exe | 104.21.3.156:80 | bc.vc | Cloudflare Inc | US | unknown |
2136 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2136 | iexplore.exe | 104.21.3.156:443 | bc.vc | Cloudflare Inc | US | unknown |
2136 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2136 | iexplore.exe | 104.26.8.148:443 | bcvc.xyz | Cloudflare Inc | US | suspicious |
1976 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1976 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2136 | iexplore.exe | 92.123.224.113:80 | e1.o.lencr.org | Akamai International B.V. | — | suspicious |
2136 | iexplore.exe | 104.17.24.14:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
2136 | iexplore.exe | 142.250.186.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bc.vc |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bcvc.xyz |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
e1.o.lencr.org |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2136 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2136 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
1976 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
1976 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |