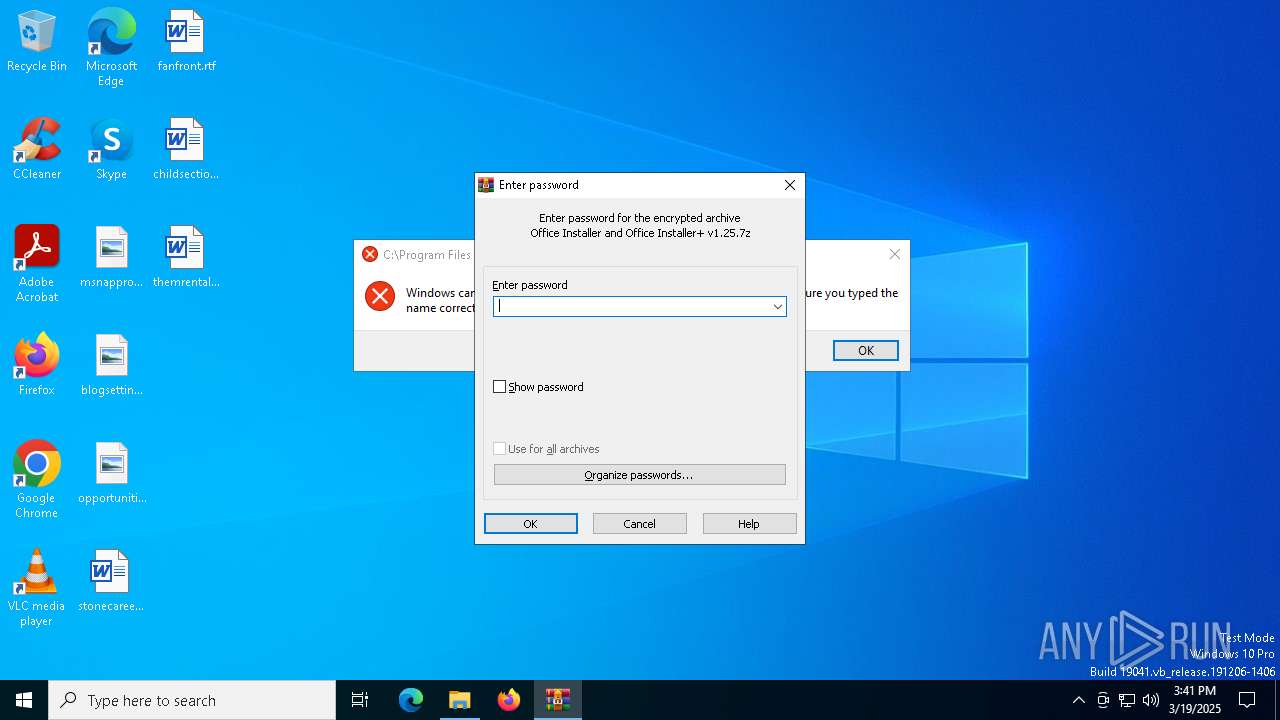
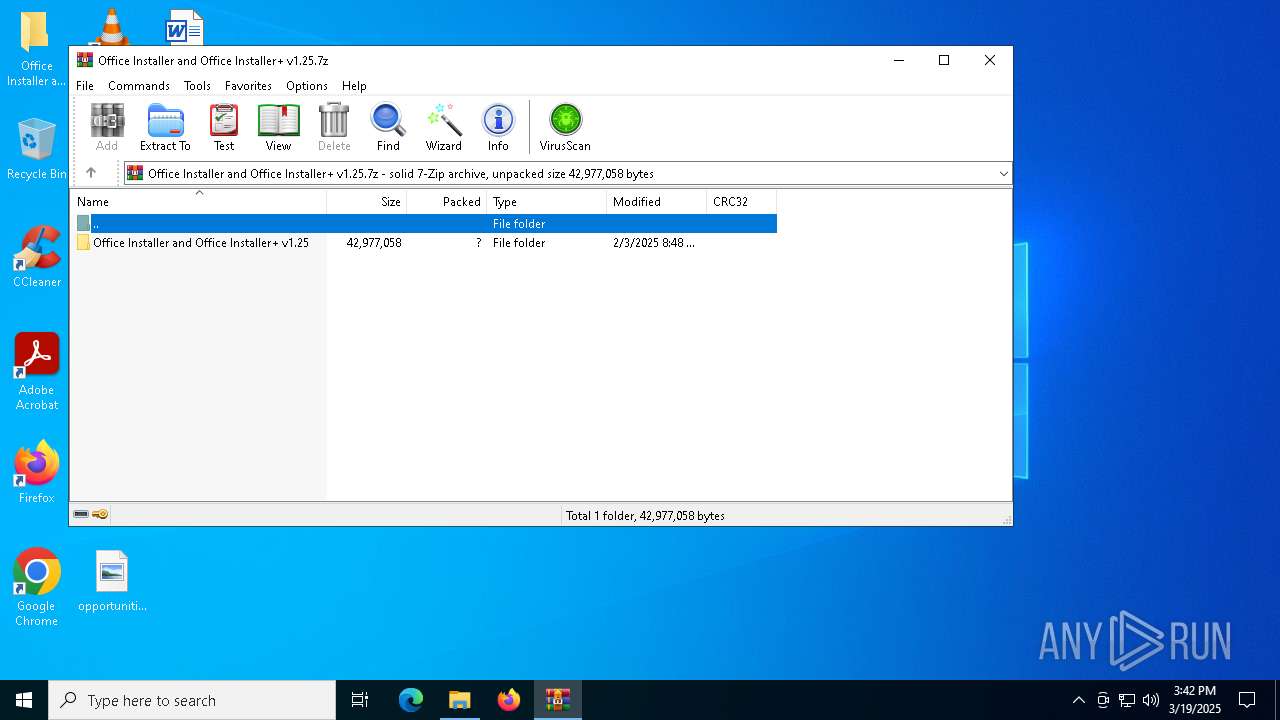
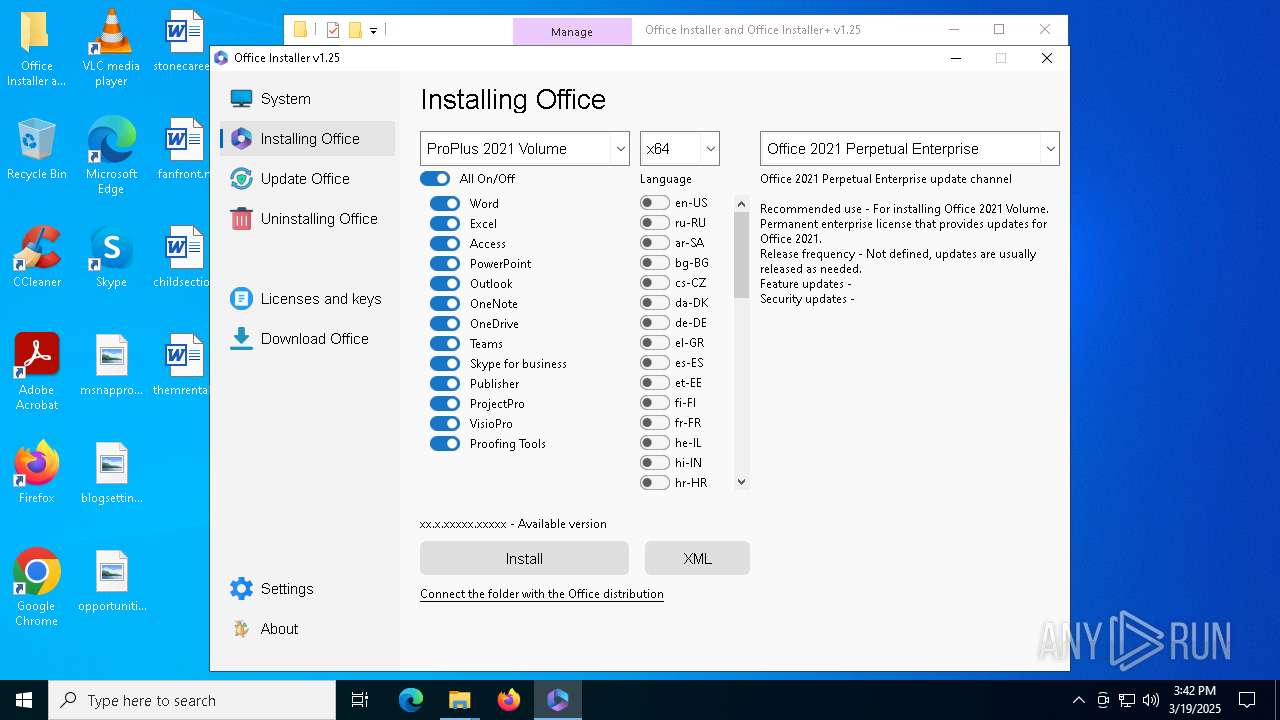
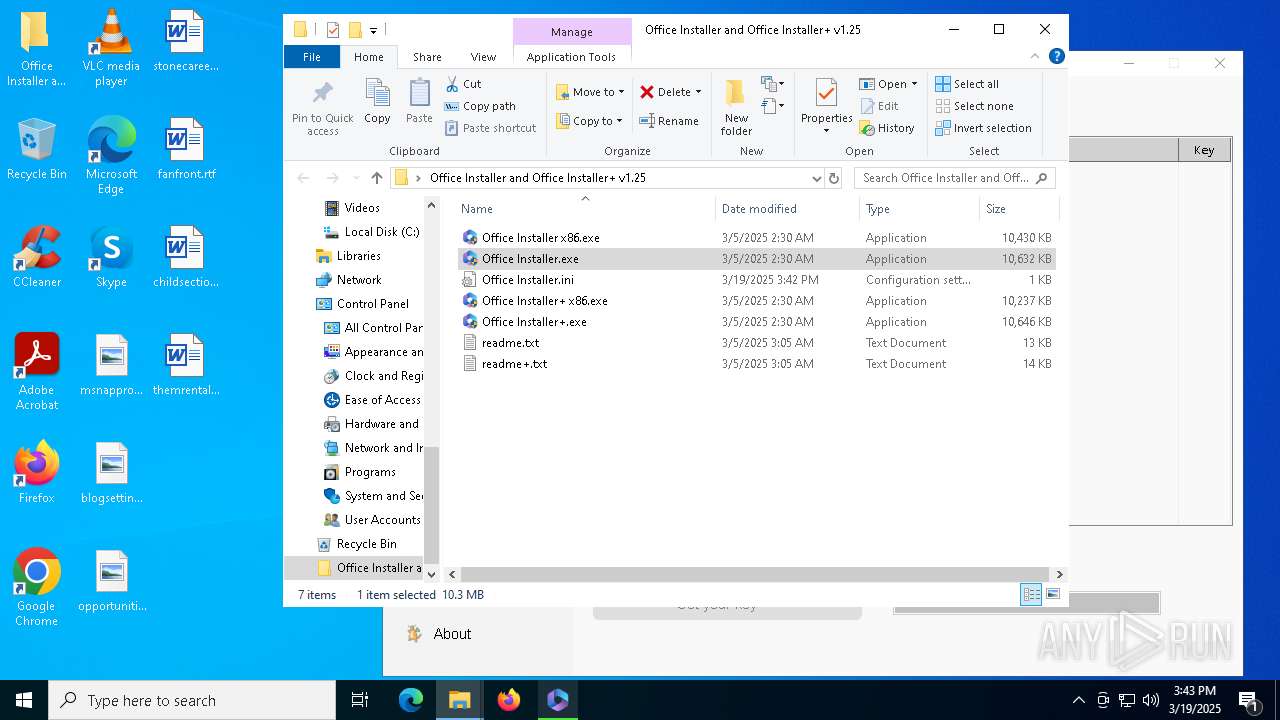
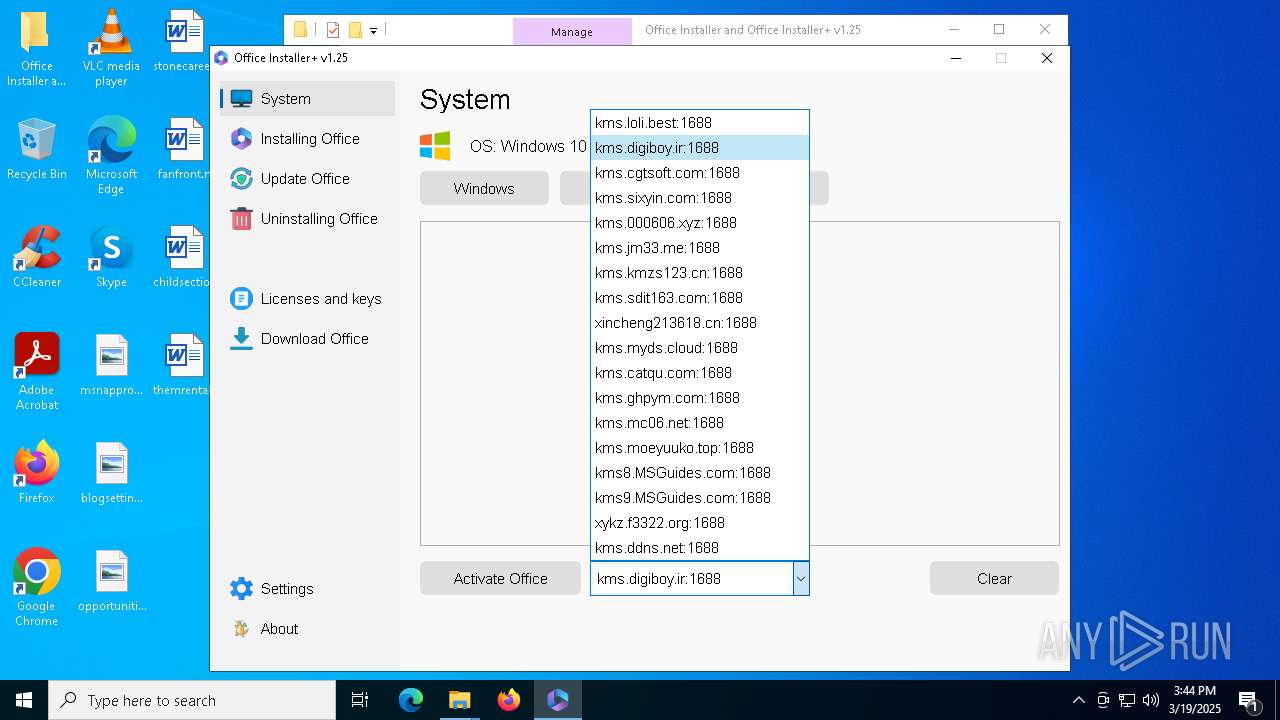
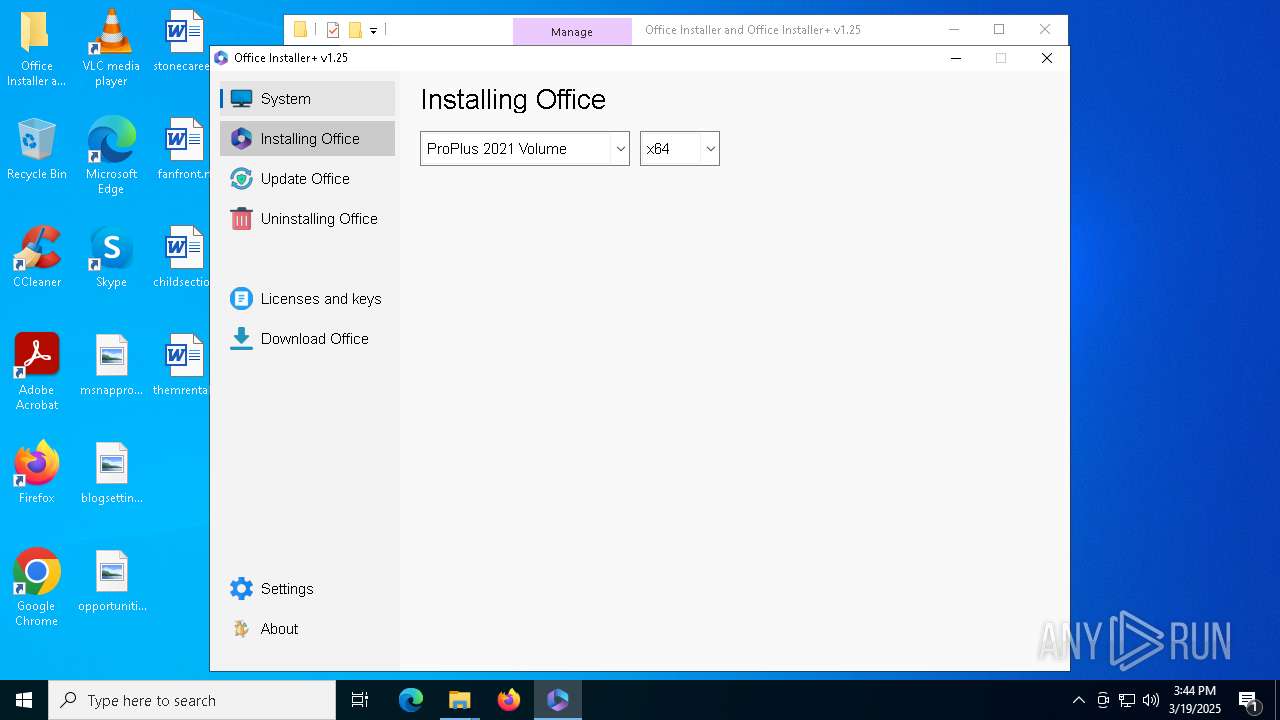
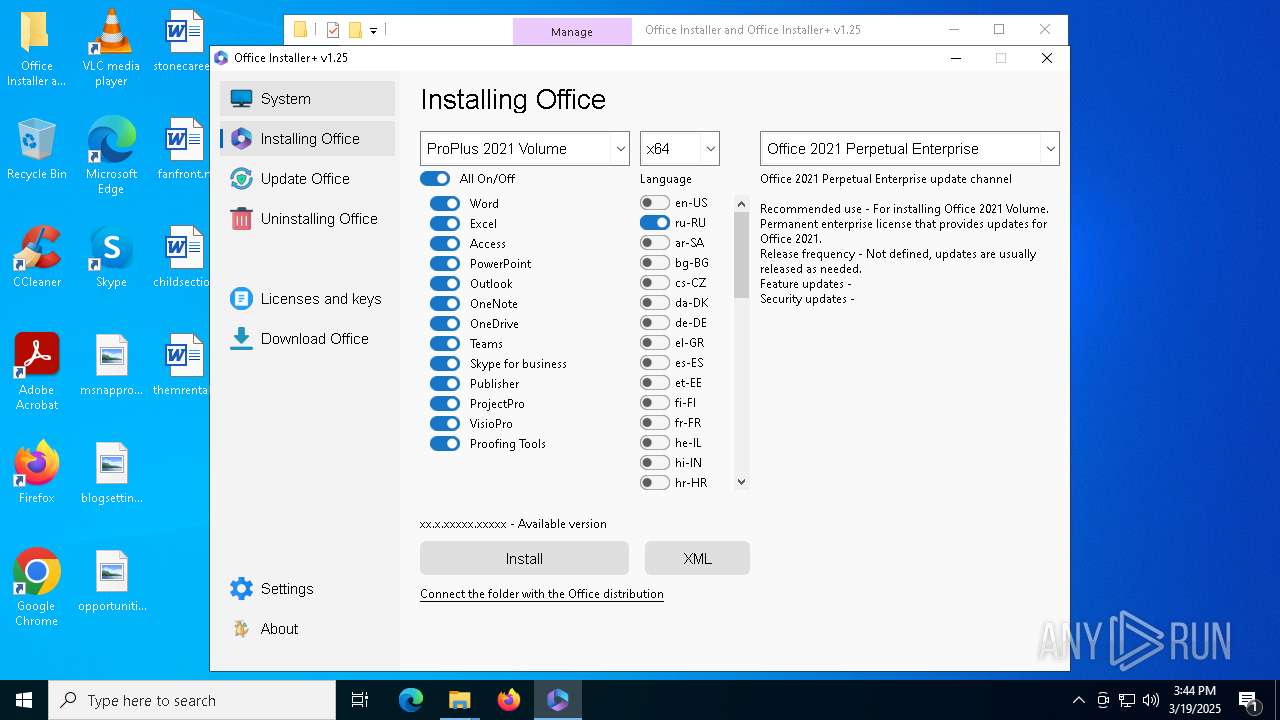
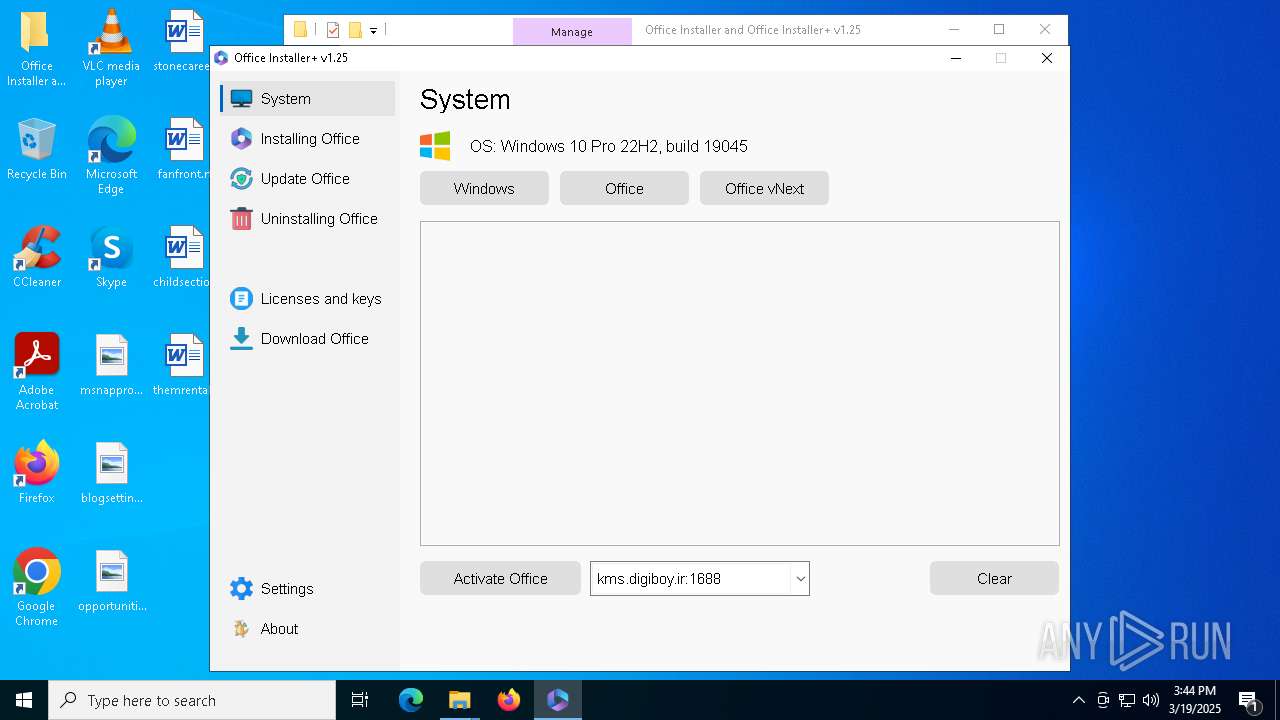
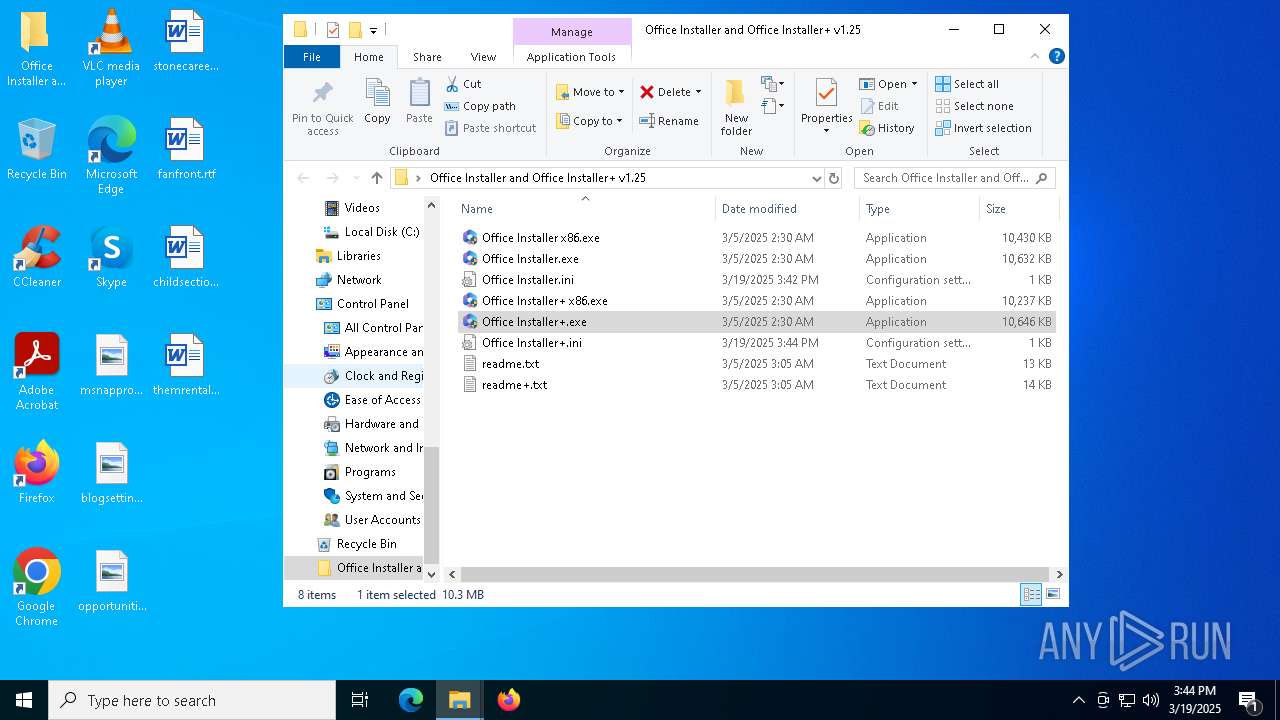
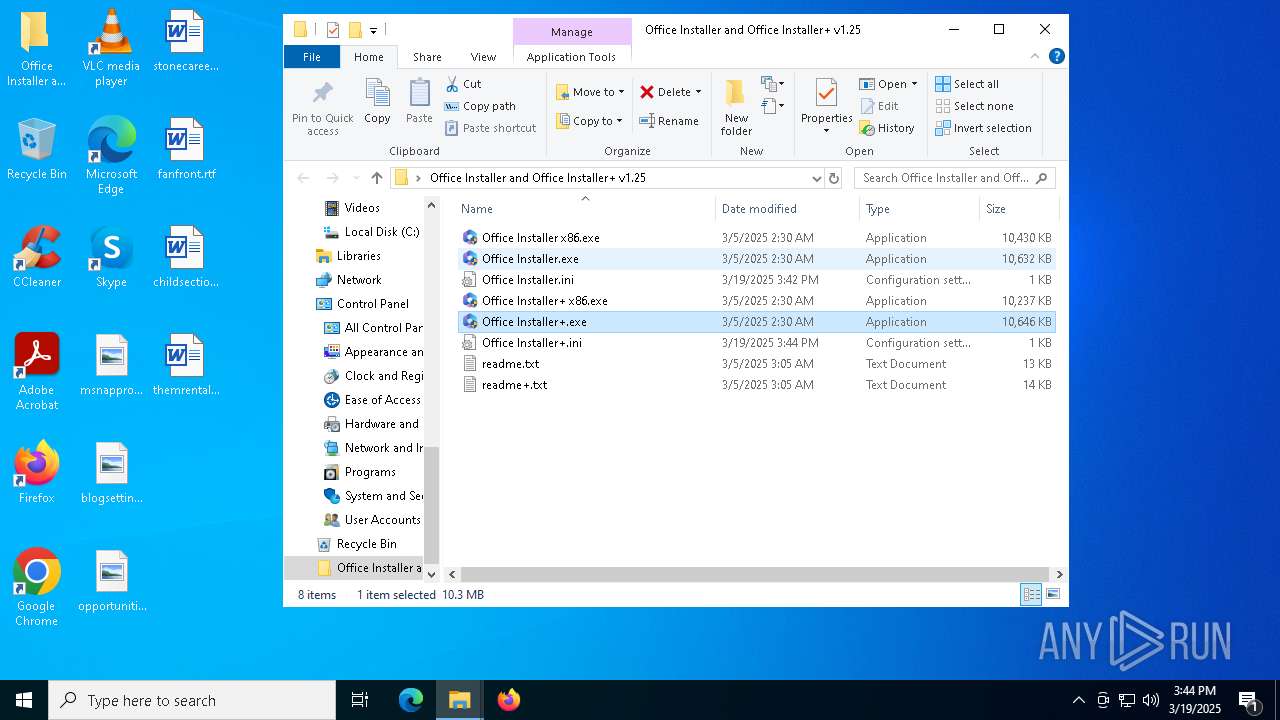
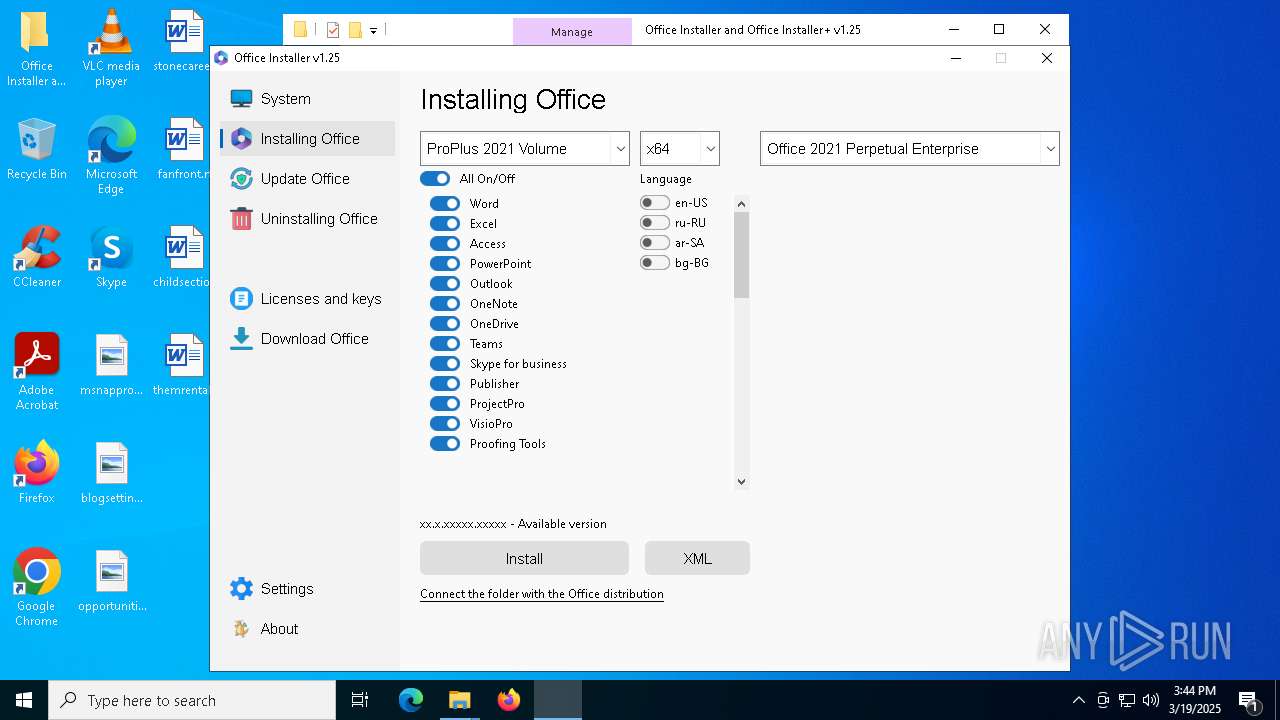
| File name: | Office Installer and Office Installer+ v1.25.7z |
| Full analysis: | https://app.any.run/tasks/7cdc2fde-07ef-44c9-95b8-e8b20d29cf06 |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2025, 15:41:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 349192E852F520412B616FFC391DFA6E |
| SHA1: | 03F30A8D15E1A01AD13C054737479DB10F92E687 |
| SHA256: | 176B4A7ED15CAD31EF6644CD2859B788AF3BAE365D152B535D9F5DA42A558B86 |
| SSDEEP: | 98304:ZpI6D0YCSFwH/l9TWWWb5yNiyLLMJjic1OQDYxM7T0lRwVUsG6yc/RW8Hi4m8KCF:tTo+o3r5yp4aQyJsjl6/ |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3008)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 668)
SUSPICIOUS
Starts CMD.EXE for commands execution
- Office Installer.exe (PID: 5528)
- Office Installer.exe (PID: 1672)
Uses REG/REGEDIT.EXE to modify registry
- Office Installer.exe (PID: 5528)
The process bypasses the loading of PowerShell profile settings
- Office Installer.exe (PID: 5528)
- Office Installer+.exe (PID: 4424)
- Office Installer.exe (PID: 1672)
Probably download files using WebClient
- Office Installer.exe (PID: 5528)
- Office Installer+.exe (PID: 4424)
- Office Installer.exe (PID: 1672)
Starts application with an unusual extension
- cmd.exe (PID: 5796)
- cmd.exe (PID: 4200)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 6264)
- files.dat (PID: 2432)
Starts POWERSHELL.EXE for commands execution
- Office Installer+.exe (PID: 4424)
- Office Installer.exe (PID: 1672)
- Office Installer.exe (PID: 5528)
Executes script without checking the security policy
- powershell.exe (PID: 3008)
- powershell.exe (PID: 6456)
- powershell.exe (PID: 668)
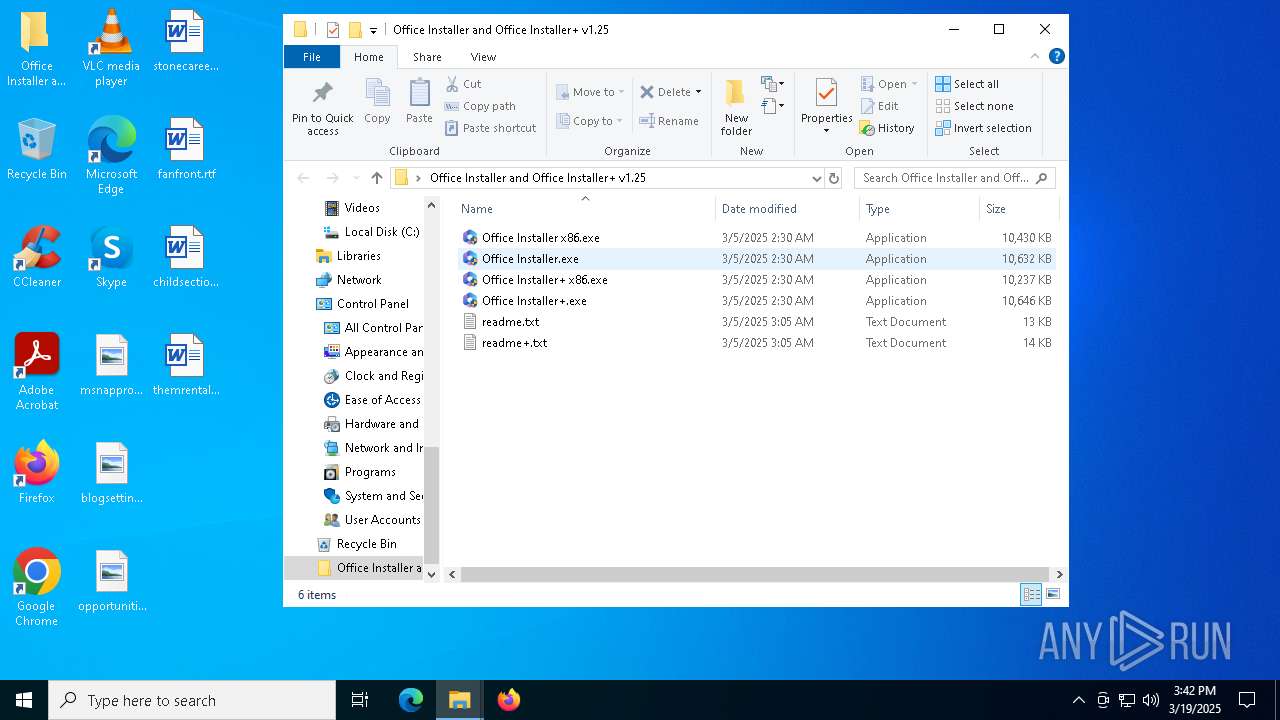
Executable content was dropped or overwritten
- Office Installer.exe (PID: 5528)
Drops 7-zip archiver for unpacking
- Office Installer.exe (PID: 5528)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1056)
- BackgroundTransferHost.exe (PID: 6800)
- BackgroundTransferHost.exe (PID: 2104)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 6800)
The sample compiled with english language support
- Office Installer.exe (PID: 5528)
Manual execution by a user
- Office Installer.exe (PID: 5164)
- Office Installer.exe (PID: 5528)
- Taskmgr.exe (PID: 1164)
- Taskmgr.exe (PID: 4108)
- Office Installer+.exe (PID: 2796)
- Office Installer+.exe (PID: 4424)
- Office Installer.exe (PID: 6068)
- Office Installer.exe (PID: 1672)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5428)
Reads the computer name
- ShellExperienceHost.exe (PID: 6476)
Checks supported languages
- Office Installer+.exe (PID: 4424)
Create files in a temporary directory
- files.dat (PID: 6264)
- files.dat (PID: 2432)
- Office Installer.exe (PID: 5528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
172
Monitored processes
33
Malicious processes
1
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "powershell" -nop -command "& { (New-Object Net.WebClient).DownloadFile('https://mrodevicemgr.officeapps.live.com/mrodevicemgrsvc/api/v2/C2RReleaseData', 'C:\Users\admin\AppData\Local\Temp\files\ver.txt') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | Office Installer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.25\Office Installer.exe" | C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.25\Office Installer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2104 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 432
Read events
23 376
Write events
42
Delete events
14
Modification events
| (PID) Process: | (1056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1056) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2104) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2104) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2104) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
8
Suspicious files
6
Text files
2 110
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\539fa696-9fb9-4fef-8574-a955c50f3673.down_data | — | |
MD5:— | SHA256:— | |||
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\539fa696-9fb9-4fef-8574-a955c50f3673.e85bfc38-a4d7-4de4-b56e-b96390c2cab3.down_meta | binary | |
MD5:9516AB92E326A780260F55539C5FEC56 | SHA256:BEFEFEF4CCDE6F7200026299DA059C265C7A2B9BC0764C29633658195245501E | |||
| 5428 | WinRAR.exe | C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.25\readme+.txt | text | |
MD5:509DB22BF8D2518B97D647FE3E85A622 | SHA256:C9DE1237F6C6E1A6320460991C5222E8308716E5CE58B11E29EC9956281C6FA4 | |||
| 5528 | Office Installer.exe | C:\Users\admin\AppData\Local\Temp\files.dat | executable | |
MD5:7E8CD9731305E426446E4D433DC79D74 | SHA256:7AB974CC7DDE723698D92401AB7E5EC997D57C3C6CF375B4BAB2AF4A6E4B1CA2 | |||
| 5428 | WinRAR.exe | C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.25\Office Installer x86.exe | executable | |
MD5:741D25BAFBD80CDB3A7179E00A409689 | SHA256:BE96A882503392D3BAA2217874BCF37FCAEC4EB971BEA868D8E2CA7E6187F2C8 | |||
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C8AF25AA60A073D8DCEA106CD46D1073 | SHA256:ECE1E0D365A6A4F49DD6700870A17DC3225812E0260FECB63169CC23F7960612 | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_k2kkpowj.2lx.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 668 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:47DB822222632BD01071831DEAD952FF | SHA256:B4F213CF0FE234BCDF3BB004038274627736C52EACF6C1A90E6A957516979E37 | |||
| 5528 | Office Installer.exe | C:\Users\admin\Desktop\Office Installer and Office Installer+ v1.25\Office Installer.ini | text | |
MD5:2A8204CFB0C0B6B7D73880F70FF4DCE7 | SHA256:9A3CCCA43D3BFE395820E58E478A1CFC1A5D9CF606B7F63000E03C8EF63C81C9 | |||
| 6264 | files.dat | C:\Users\admin\AppData\Local\Temp\o16files\Access2019R_Grace-ul-oob.xrm-ms | xml | |
MD5:A922C21504F108638BDAF12A9C96AB6D | SHA256:7A3804333CBF64CF3AC115E06533BD139E50E96B68089EBC452A34A6C931ABDA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5304 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6800 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6980 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6980 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5304 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5304 | backgroundTaskHost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
664 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |