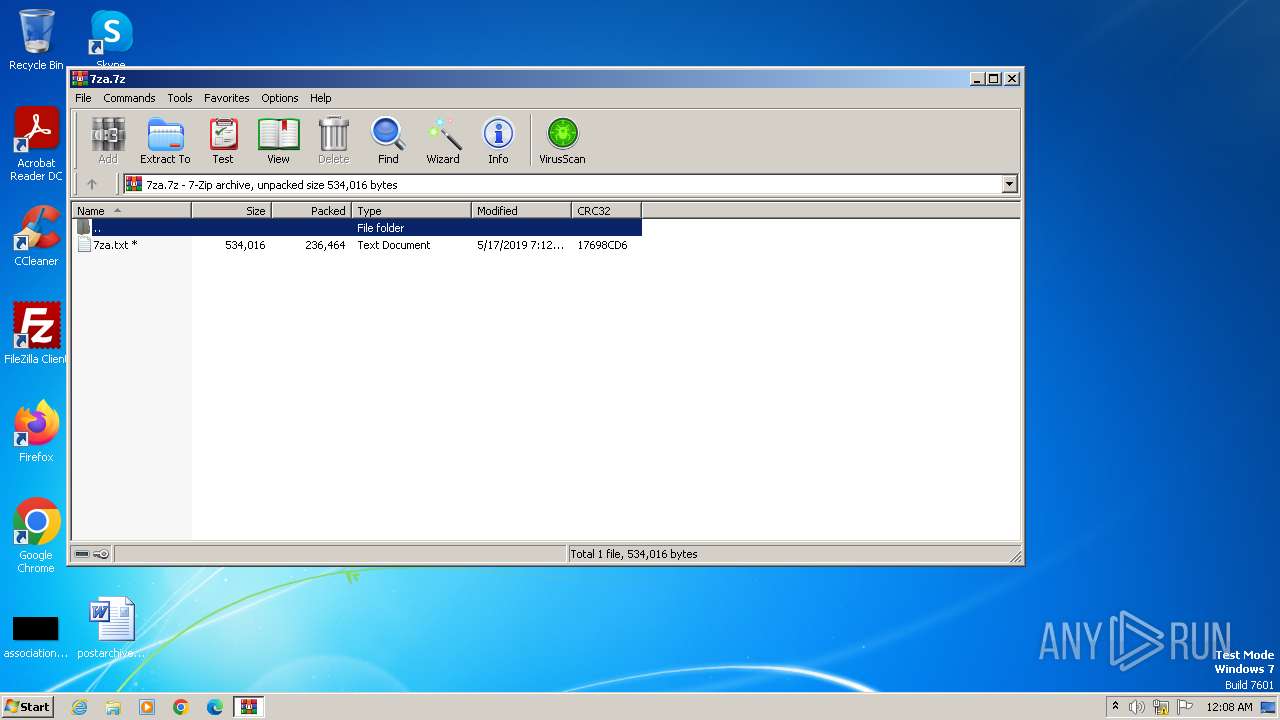
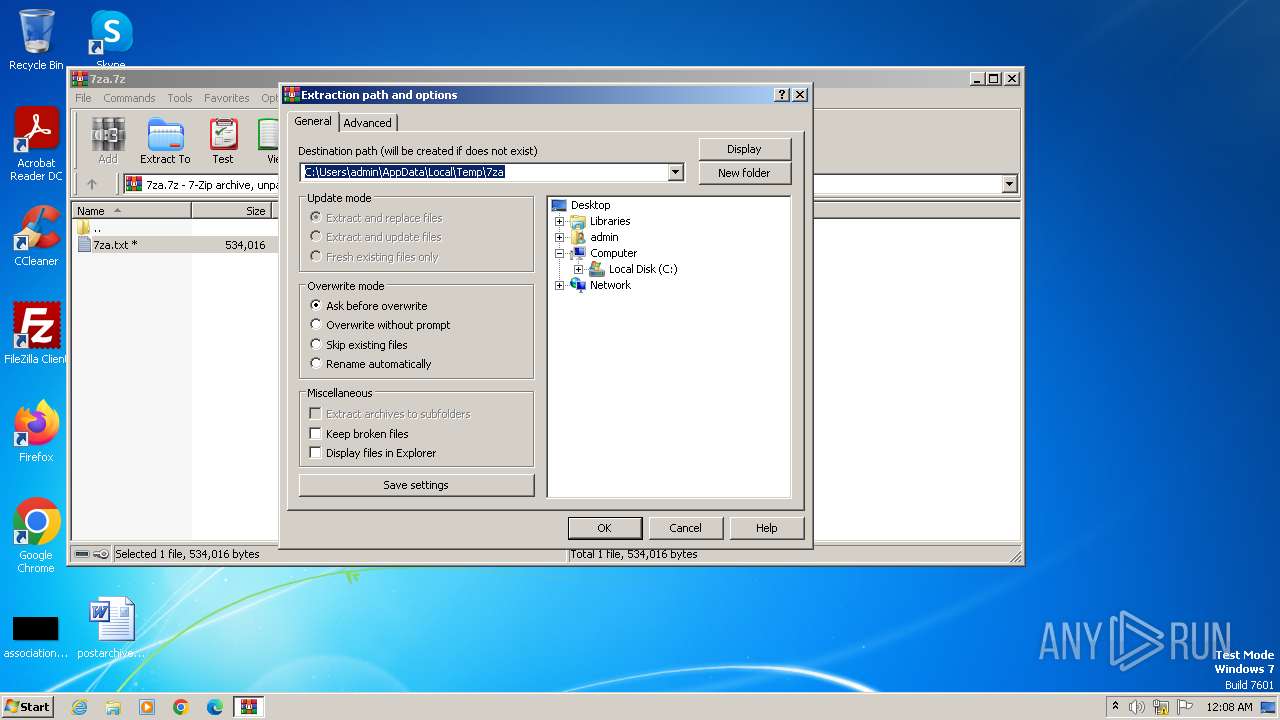
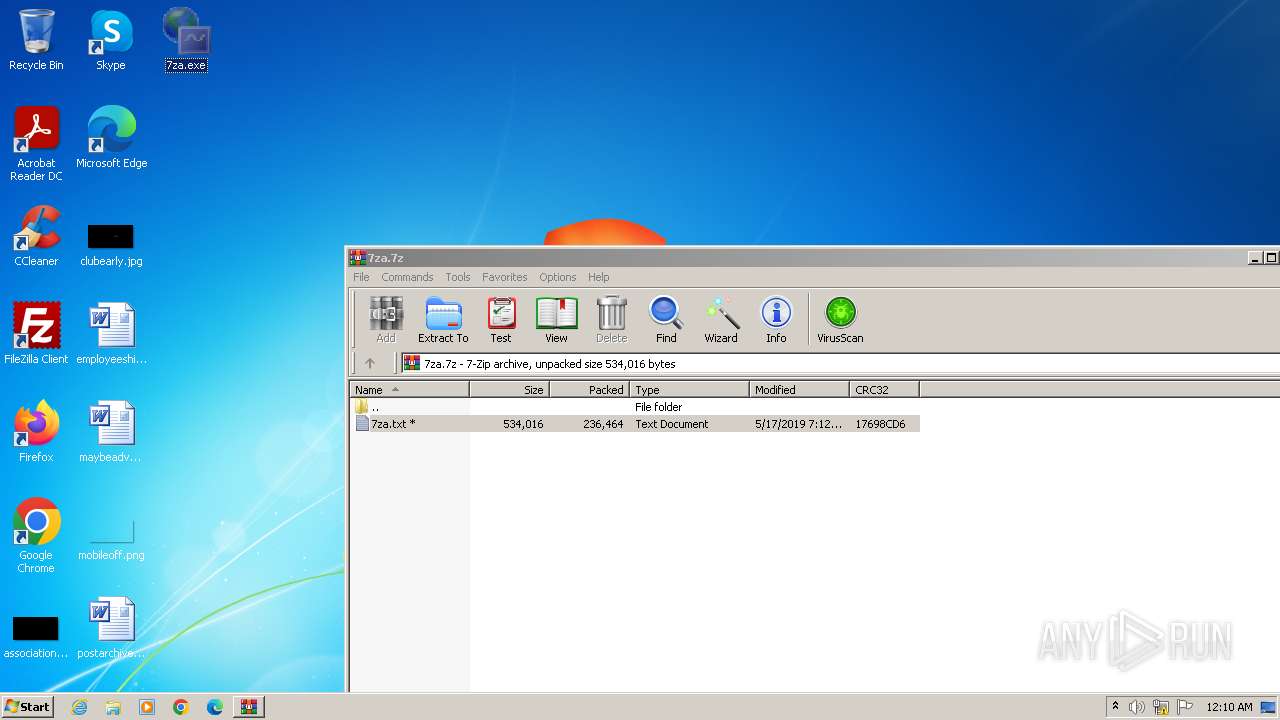
| File name: | 7za.7z |
| Full analysis: | https://app.any.run/tasks/a8b7fed2-d343-466a-8f6e-17f2fb55a8db |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2024, 23:08:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9EB56A77BE154F96FEDD3FC9BC1F8F92 |
| SHA1: | 1EF31708A0F85644388A4AD14418B570A59466BF |
| SHA256: | 176B08098EA5C592A7D78E3EA11752E8BA6E7CD5F8C7DE02C34FC863F6C3A6B1 |
| SSDEEP: | 6144:zRcyGh0+/PLXzkRLX1eaTSPz8QN9XSORwFUhYQdVwksbqlIx:zE0+XLXzGxeHBN9XkFU+QVJUdx |
MALICIOUS
Create files in the Startup directory
- 7za.exe (PID: 2040)
- 7za.exe (PID: 864)
- 7za.exe (PID: 1872)
- 7za.exe (PID: 1112)
- 7za.exe (PID: 1604)
- 7za.exe (PID: 1796)
- 7za.exe (PID: 1792)
- 7za.exe (PID: 2124)
- 7za.exe (PID: 2472)
- 7za.exe (PID: 1128)
Drops the executable file immediately after the start
- 7za.exe (PID: 1200)
- 7za.exe (PID: 1604)
SUSPICIOUS
Executable content was dropped or overwritten
- 7za.exe (PID: 1200)
- 7za.exe (PID: 1604)
Process drops legitimate windows executable
- 7za.exe (PID: 1604)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
Creates files or folders in the user directory
- 7za.exe (PID: 1200)
- 7za.exe (PID: 2040)
- 7za.exe (PID: 864)
- 7za.exe (PID: 1872)
- 7za.exe (PID: 1112)
- 7za.exe (PID: 1604)
- 7za.exe (PID: 1796)
- 7za.exe (PID: 1792)
- 7za.exe (PID: 2124)
- 7za.exe (PID: 2472)
- 7za.exe (PID: 1128)
Reads the computer name
- 7za.exe (PID: 864)
- 7za.exe (PID: 1200)
- 7za.exe (PID: 2040)
- 7za.exe (PID: 1872)
- 7za.exe (PID: 1112)
- 7za.exe (PID: 1604)
- 7za.exe (PID: 1796)
- 7za.exe (PID: 1792)
- 7za.exe (PID: 2124)
- 7za.exe (PID: 2472)
- 7za.exe (PID: 1128)
Checks supported languages
- 7za.exe (PID: 1200)
- 7za.exe (PID: 2040)
- 7za.exe (PID: 1872)
- 7za.exe (PID: 864)
- 7za.exe (PID: 1112)
- 7za.exe (PID: 1604)
- 7za.exe (PID: 2124)
- 7za.exe (PID: 2472)
- 7za.exe (PID: 1796)
- 7za.exe (PID: 1792)
- 7za.exe (PID: 1128)
Manual execution by a user
- 7za.exe (PID: 1872)
- 7za.exe (PID: 864)
- 7za.exe (PID: 1200)
- 7za.exe (PID: 2040)
- 7za.exe (PID: 1112)
- 7za.exe (PID: 1604)
- 7za.exe (PID: 2124)
- 7za.exe (PID: 2472)
- 7za.exe (PID: 1796)
- 7za.exe (PID: 1792)
- 7za.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
57
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1128 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1200 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1796 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\7za.exe" | C:\Users\admin\Desktop\7za.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
26 957
Read events
26 938
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7za.7z | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
24
Suspicious files
7
Text files
9
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\Desktop\7za.txt | executable | |
MD5:95E1B8930154783A112A8CF4BE312474 | SHA256:01E3E0ADB13D1074A76974B464904BD807D20DF27173DF57CE6952440037A1CF | |||
| 1200 | 7za.exe | C:\Users\admin\AppData\Roaming\Ground.exe | executable | |
MD5:95E1B8930154783A112A8CF4BE312474 | SHA256:01E3E0ADB13D1074A76974B464904BD807D20DF27173DF57CE6952440037A1CF | |||
| 864 | 7za.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | lnk | |
MD5:82B7F1C1C25D6DBE029E236B48825C01 | SHA256:2E3E6D71A31AD65E07B3351D2016834252A238E2F66D62934B3229FE2BB396C4 | |||
| 1604 | 7za.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | lnk | |
MD5:0DC77371F4694CDEE24E40DED1AC6AAE | SHA256:81346430E48E48BD5D813BE12F7734A2D62A42CA4F8DA3BFCC8413AE40BCF9BB | |||
| 2040 | 7za.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | binary | |
MD5:0DC77371F4694CDEE24E40DED1AC6AAE | SHA256:81346430E48E48BD5D813BE12F7734A2D62A42CA4F8DA3BFCC8413AE40BCF9BB | |||
| 1112 | 7za.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | lnk | |
MD5:0DC77371F4694CDEE24E40DED1AC6AAE | SHA256:81346430E48E48BD5D813BE12F7734A2D62A42CA4F8DA3BFCC8413AE40BCF9BB | |||
| 1872 | 7za.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Ground.lnk | lnk | |
MD5:0DC77371F4694CDEE24E40DED1AC6AAE | SHA256:81346430E48E48BD5D813BE12F7734A2D62A42CA4F8DA3BFCC8413AE40BCF9BB | |||
| 1604 | 7za.exe | C:\Windows\Alcrmv.exe | executable | |
MD5:95E1B8930154783A112A8CF4BE312474 | SHA256:01E3E0ADB13D1074A76974B464904BD807D20DF27173DF57CE6952440037A1CF | |||
| 1604 | 7za.exe | C:\Windows\RCX5F83.tmp | executable | |
MD5:907BC5065B8A016F4E6C7D438C889433 | SHA256:8EC670861B5F2B62AED0679EBCEFACF2C3D097810259C66124C221EB08713FCD | |||
| 1604 | 7za.exe | C:\Windows\Microsoft.NET\gNETFXRepair.ico | image | |
MD5:E3240ED5592A23428452A909E1CD3E06 | SHA256:C0BF9BDA3864898AED3E8F067970FB6E0A00FC90828384183489EE68245085B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |