| File name: | XWorm Crack.exe |
| Full analysis: | https://app.any.run/tasks/2be8942f-a770-4e1e-a679-cfecfa079932 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 05:11:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 7E1F59B346389C8DDE72670D941ACEB4 |
| SHA1: | D4FB968136618C58BE9992370329777A54C7136F |
| SHA256: | 1754EC70105B7E863D303D2256D836DB26DE03A63336A872AAC963ED0929D7B8 |
| SSDEEP: | 98304:RCYzBj4DbSb4Y6ZhkDQet54nHZUj0vU9XLDbenkuA83wpYp2twldaQ0EACheua5o:qp2z881mwH/kit496ikY |
MALICIOUS
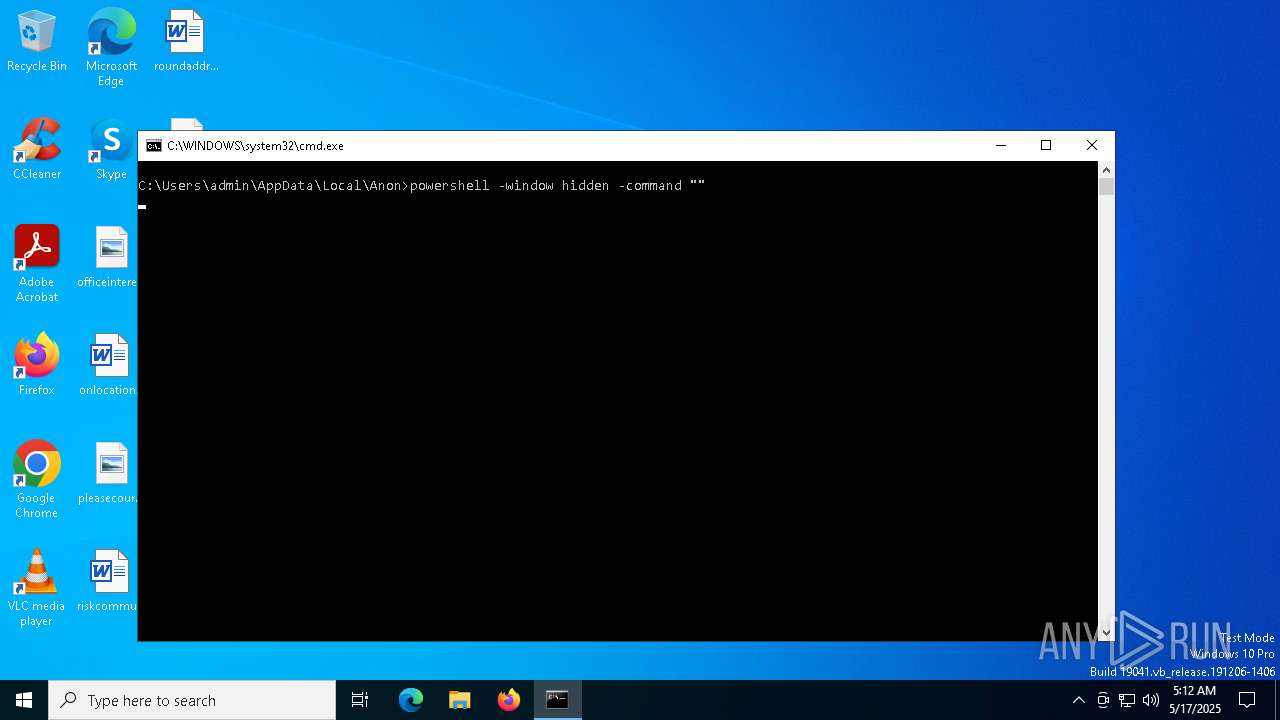
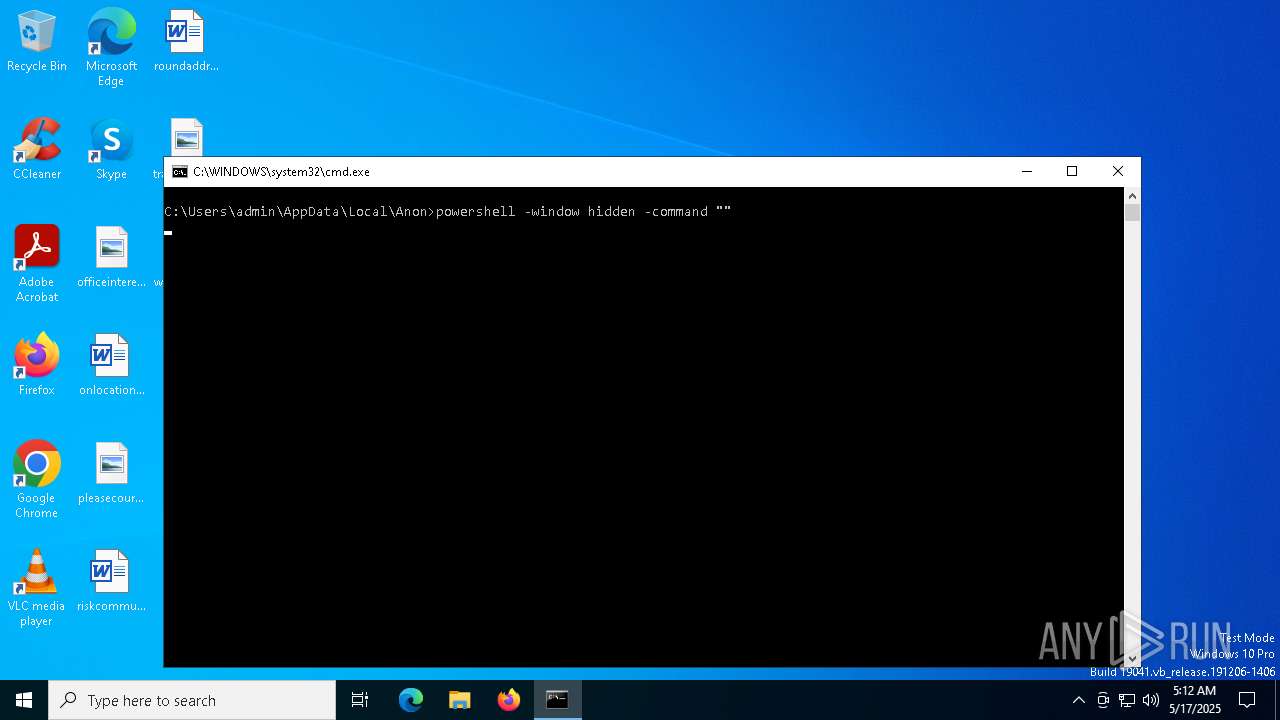
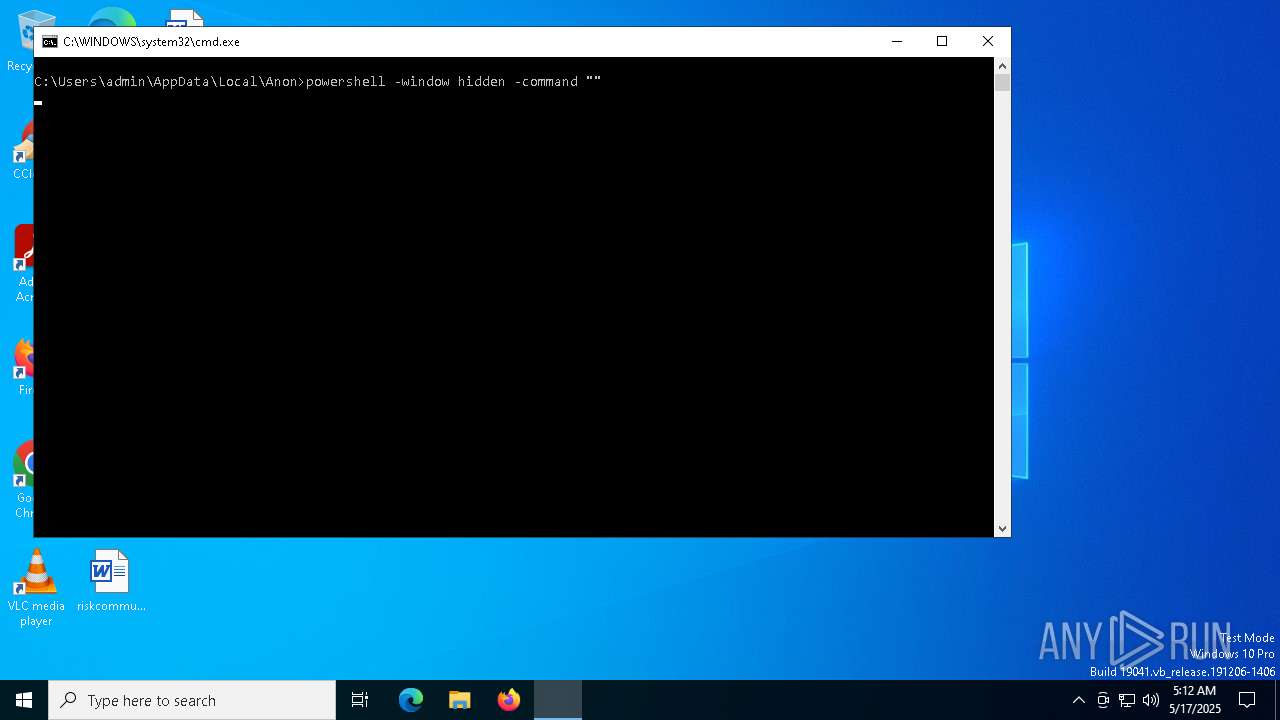
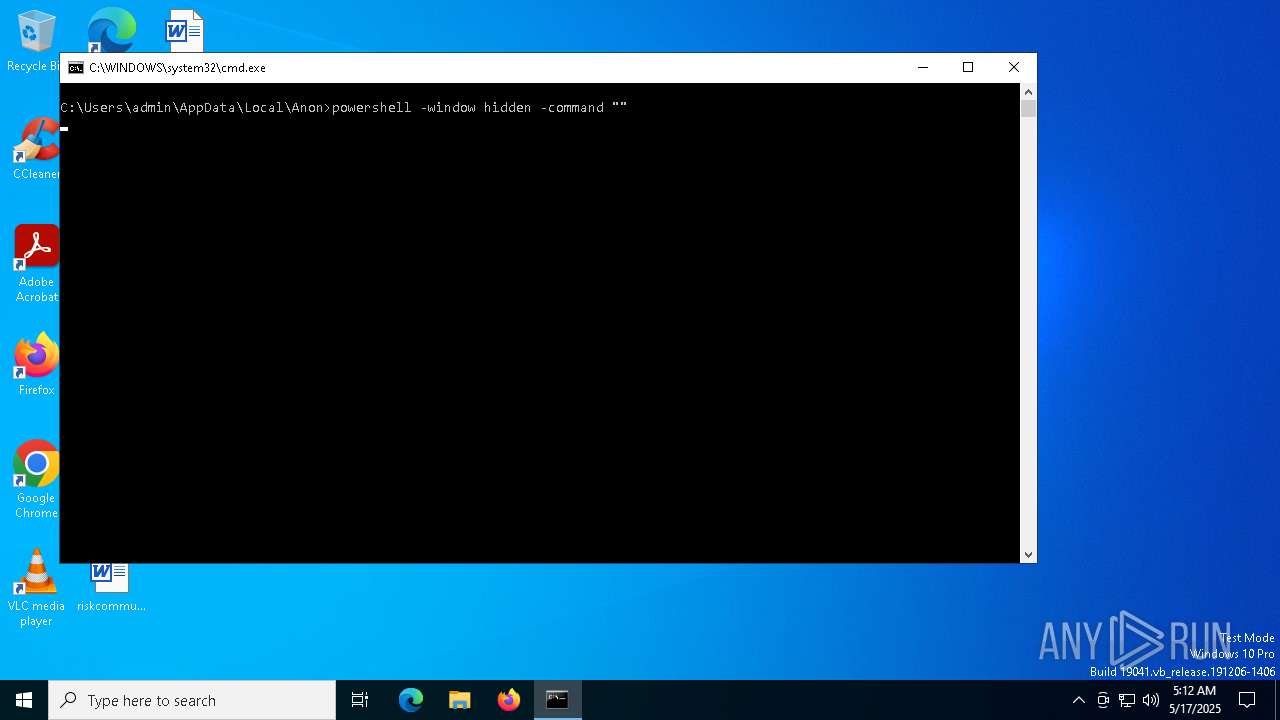
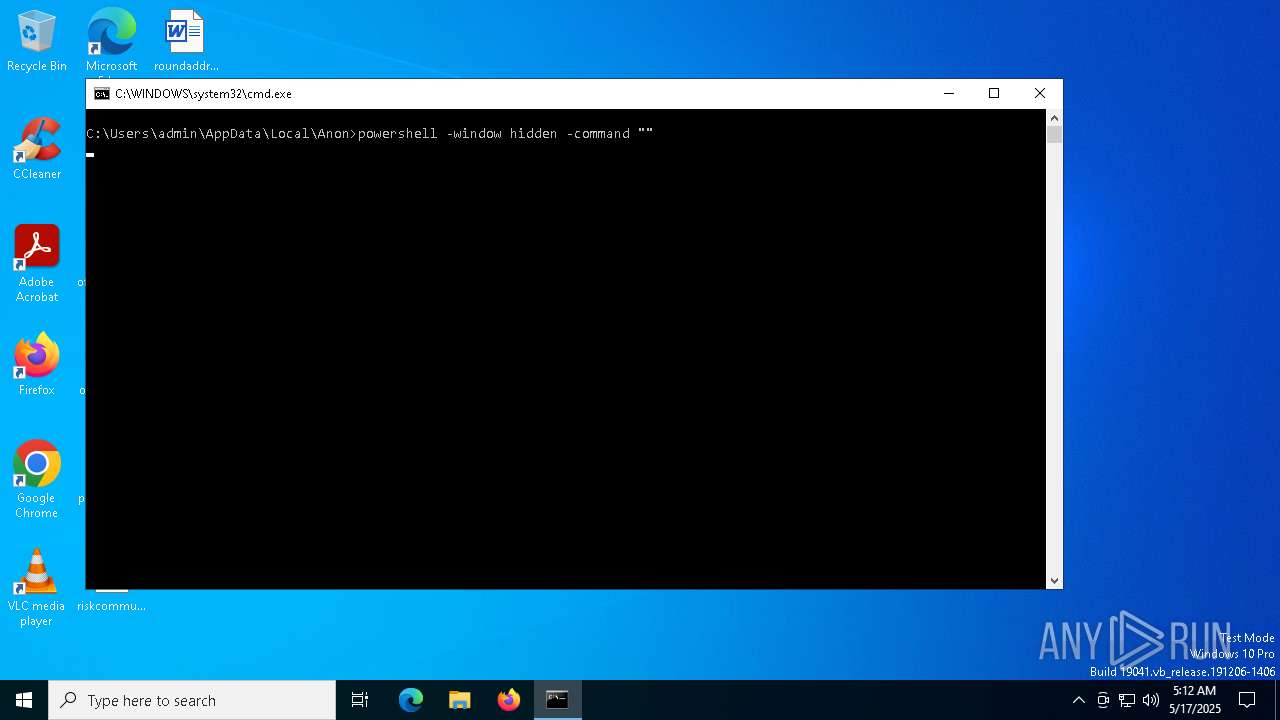
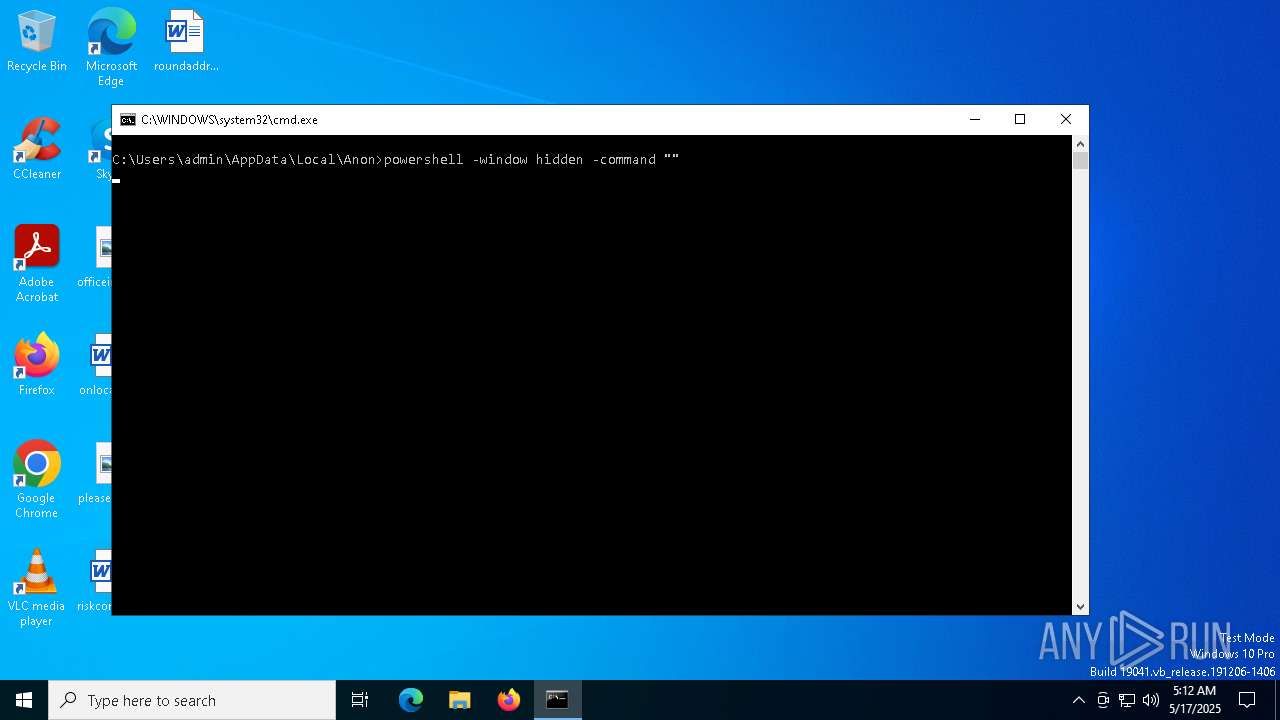
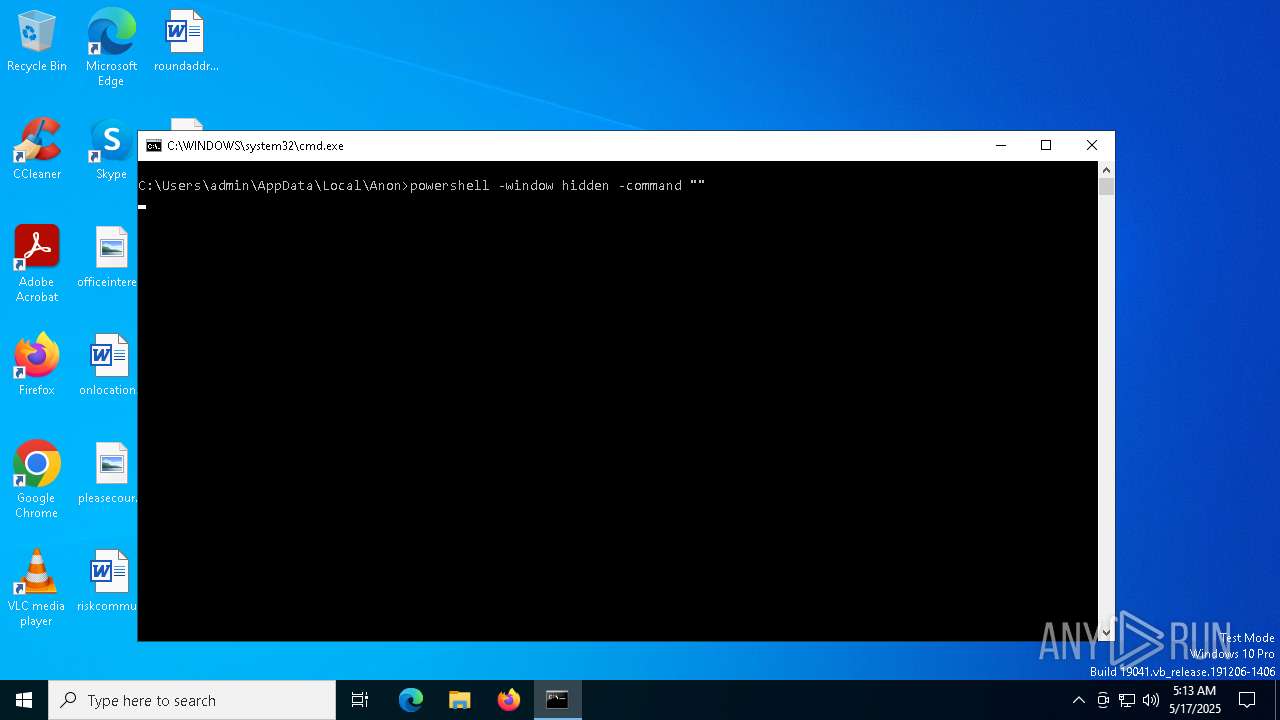
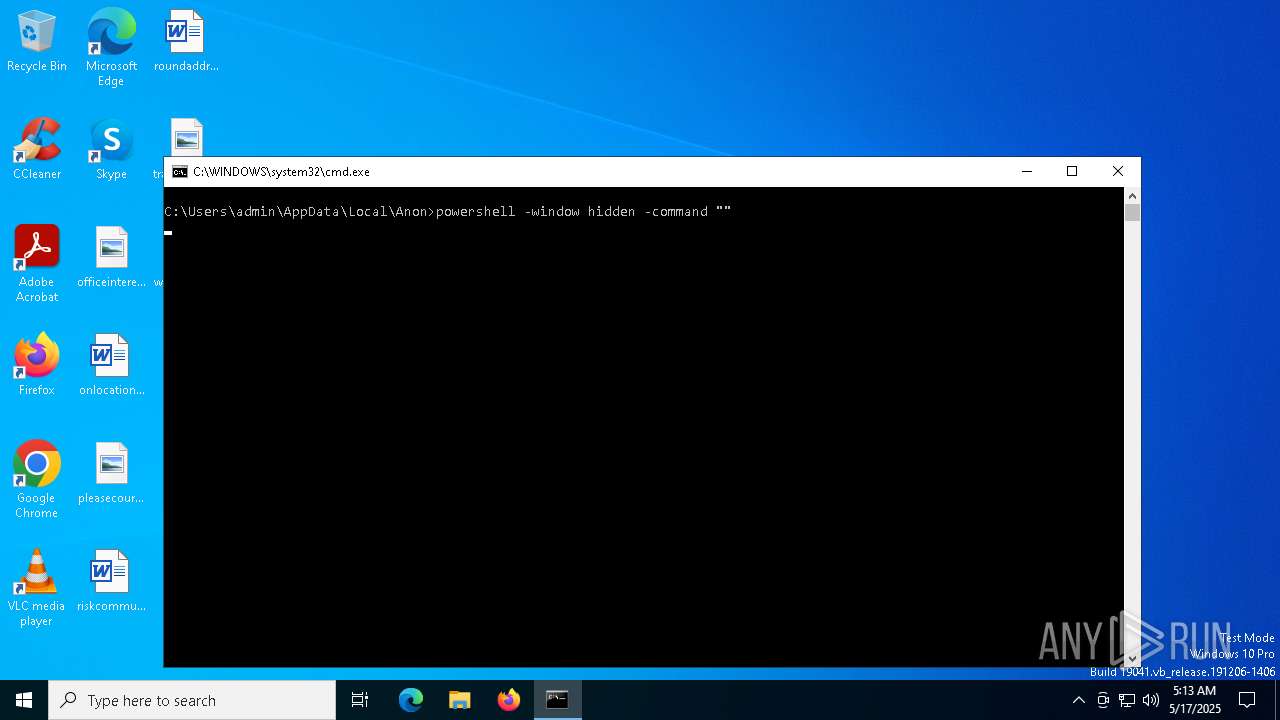
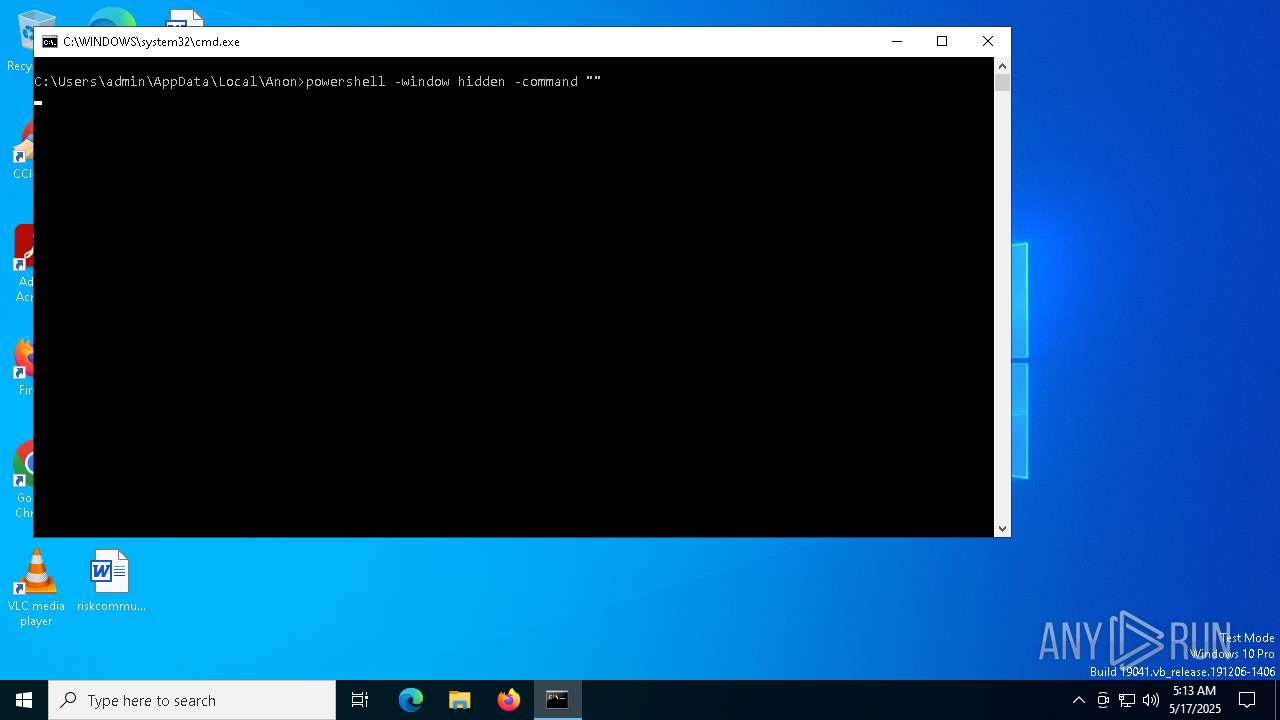
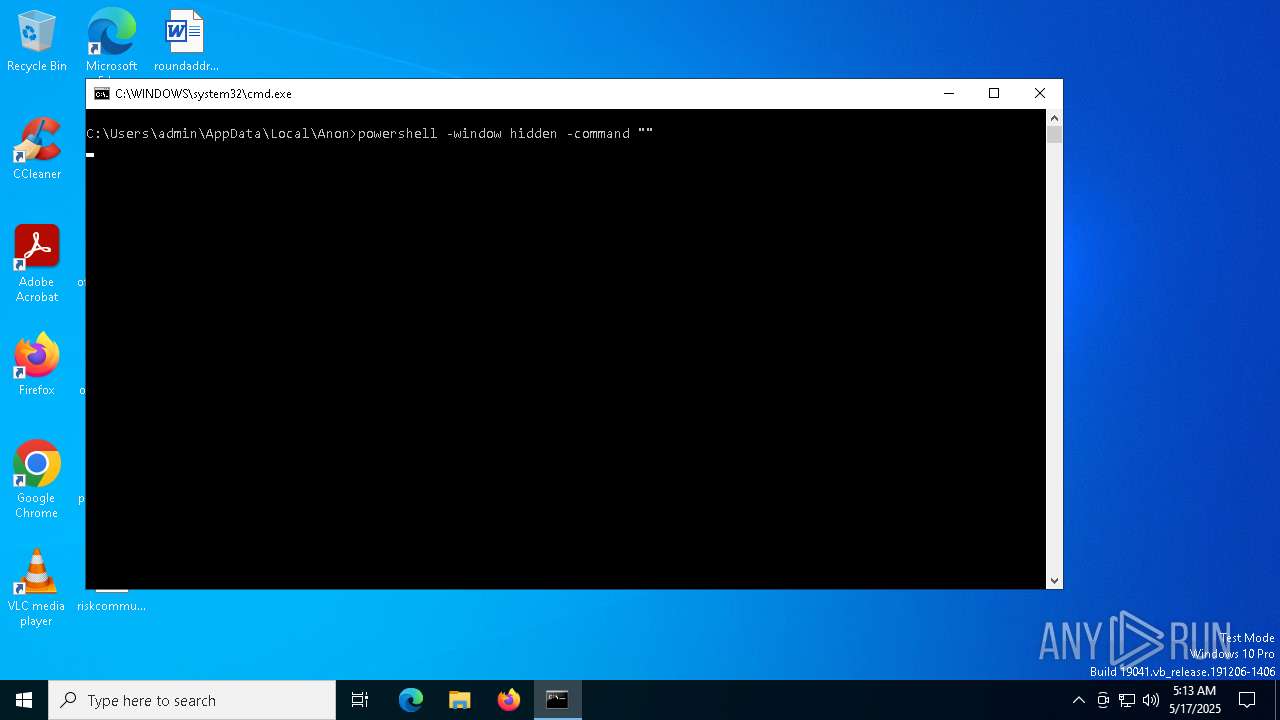
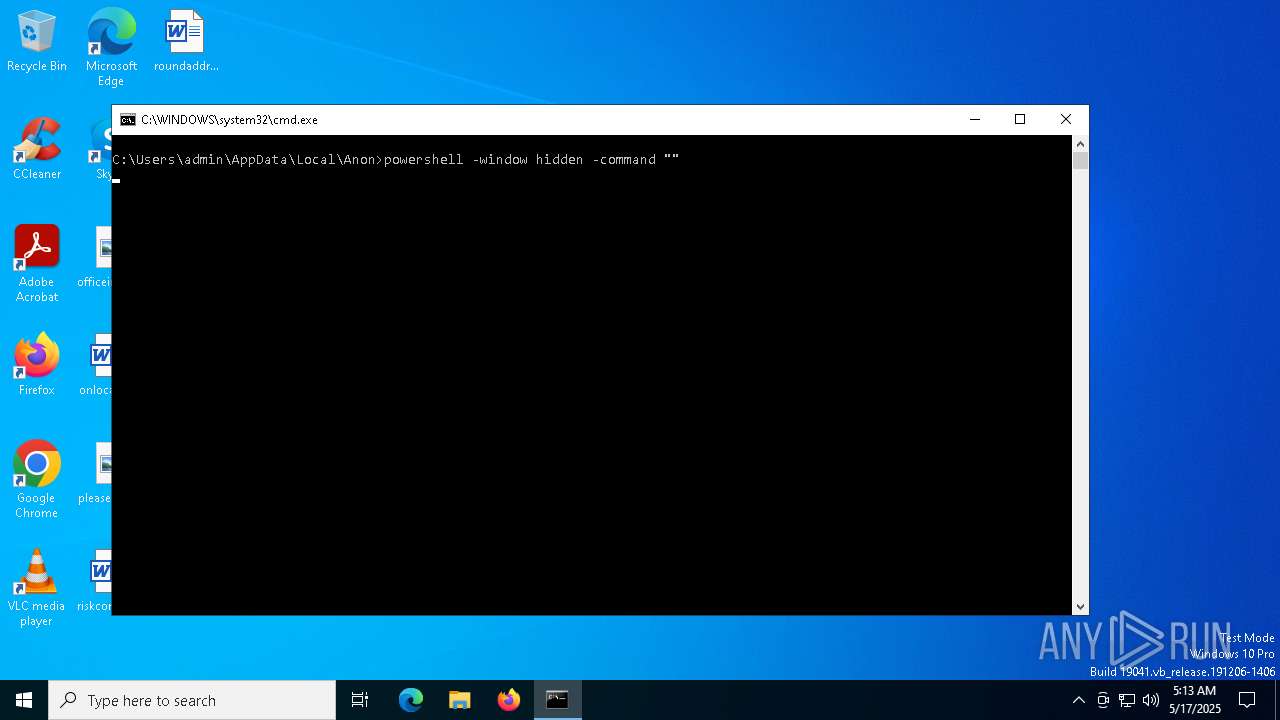
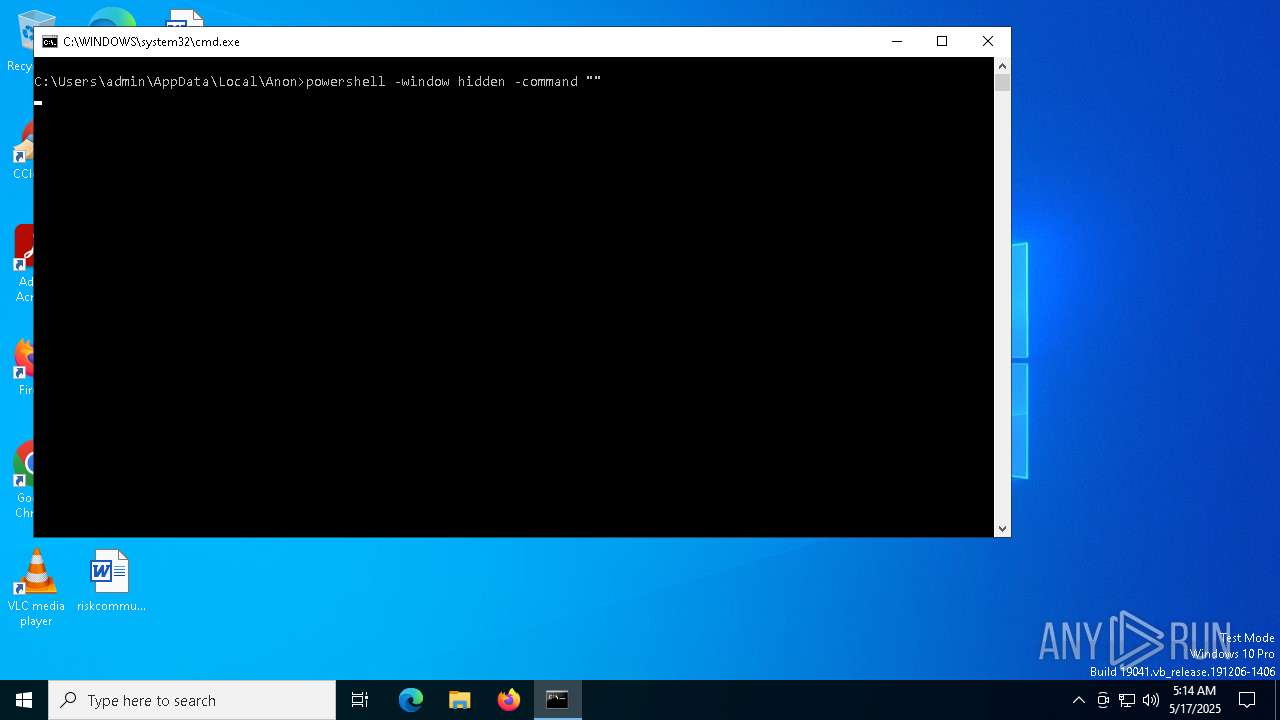
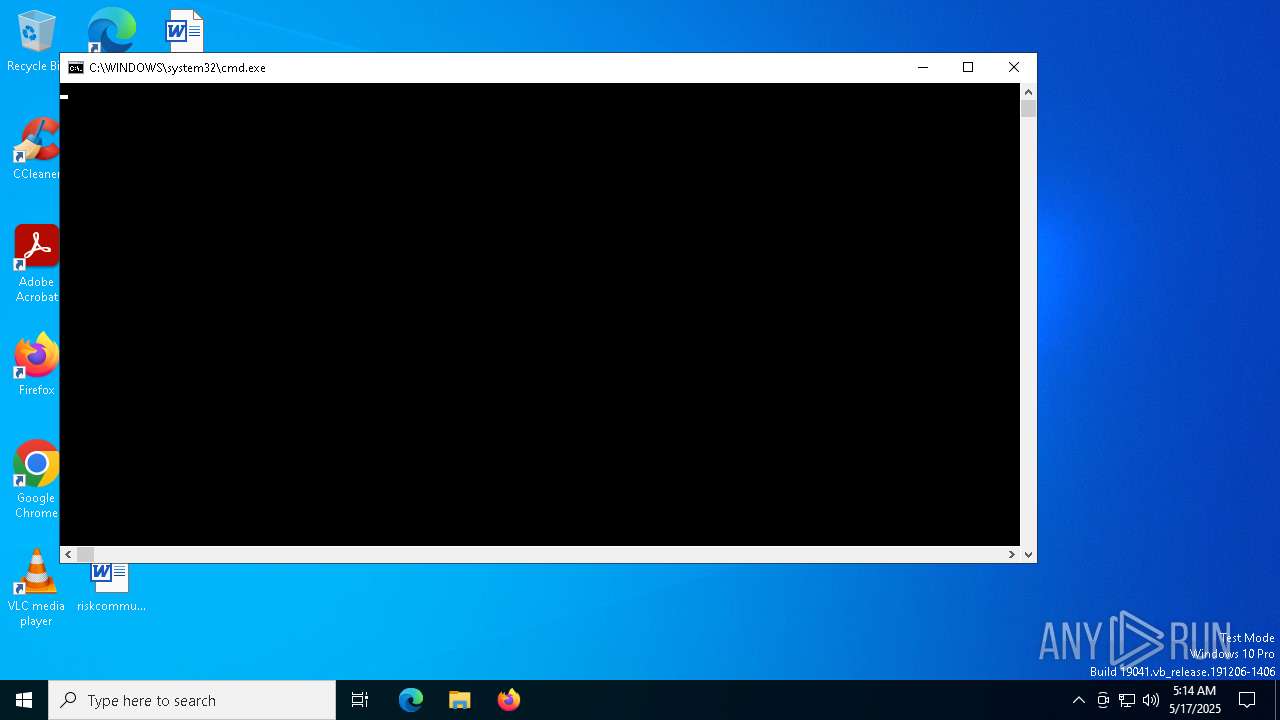
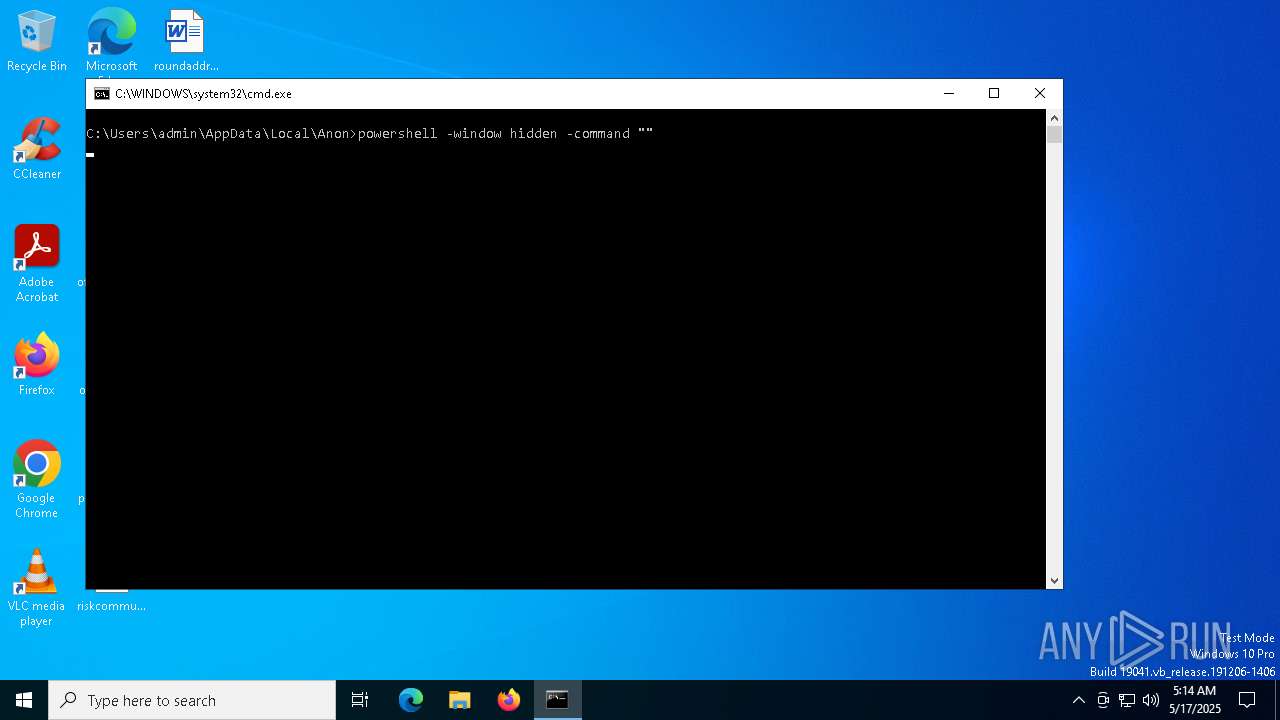
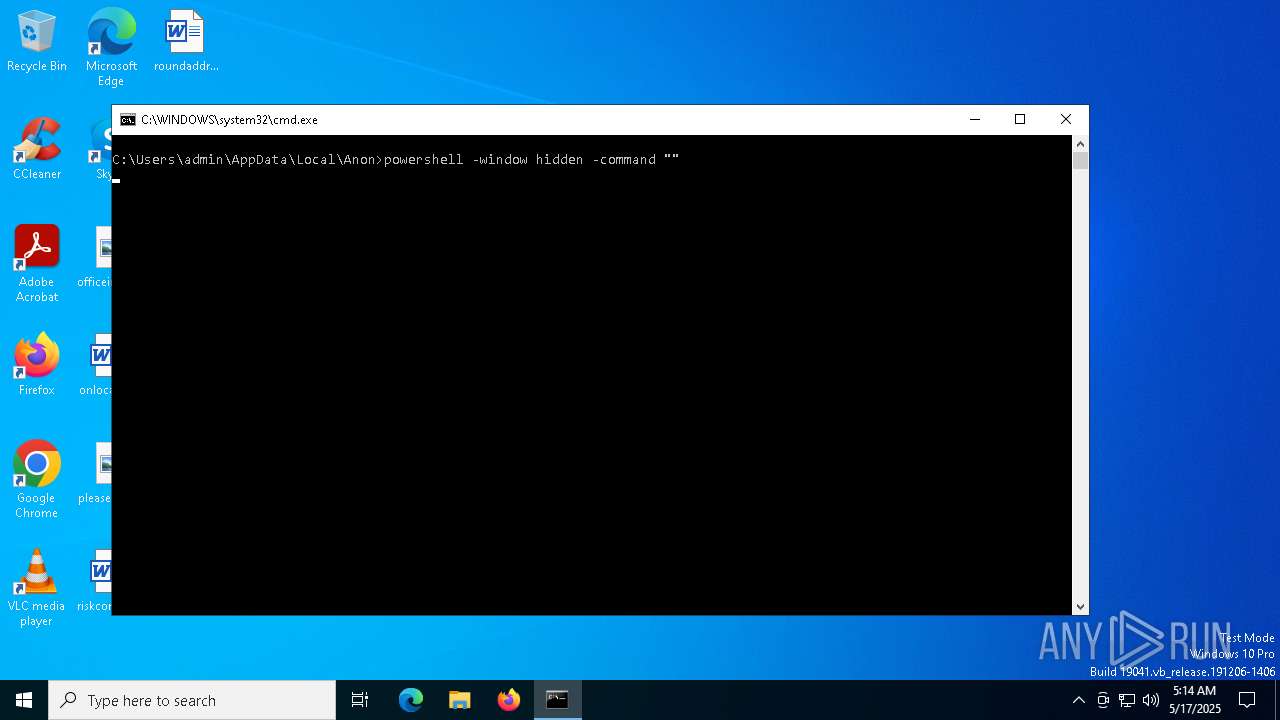
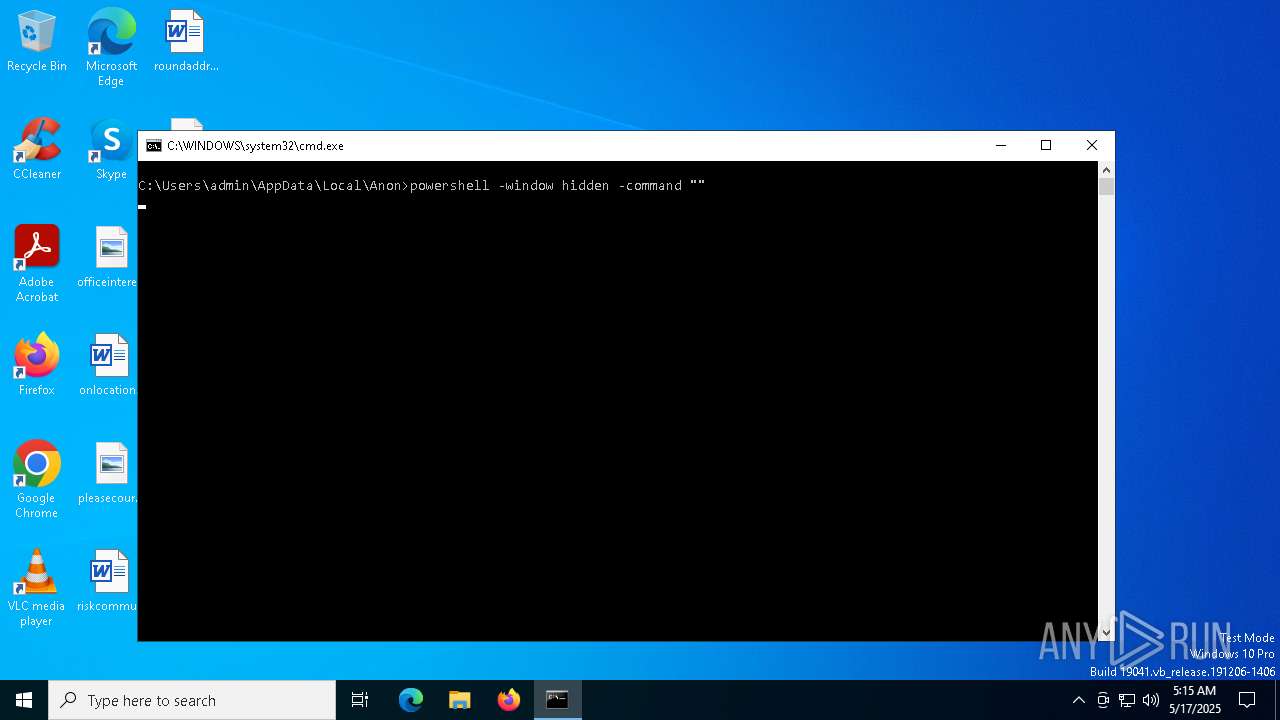
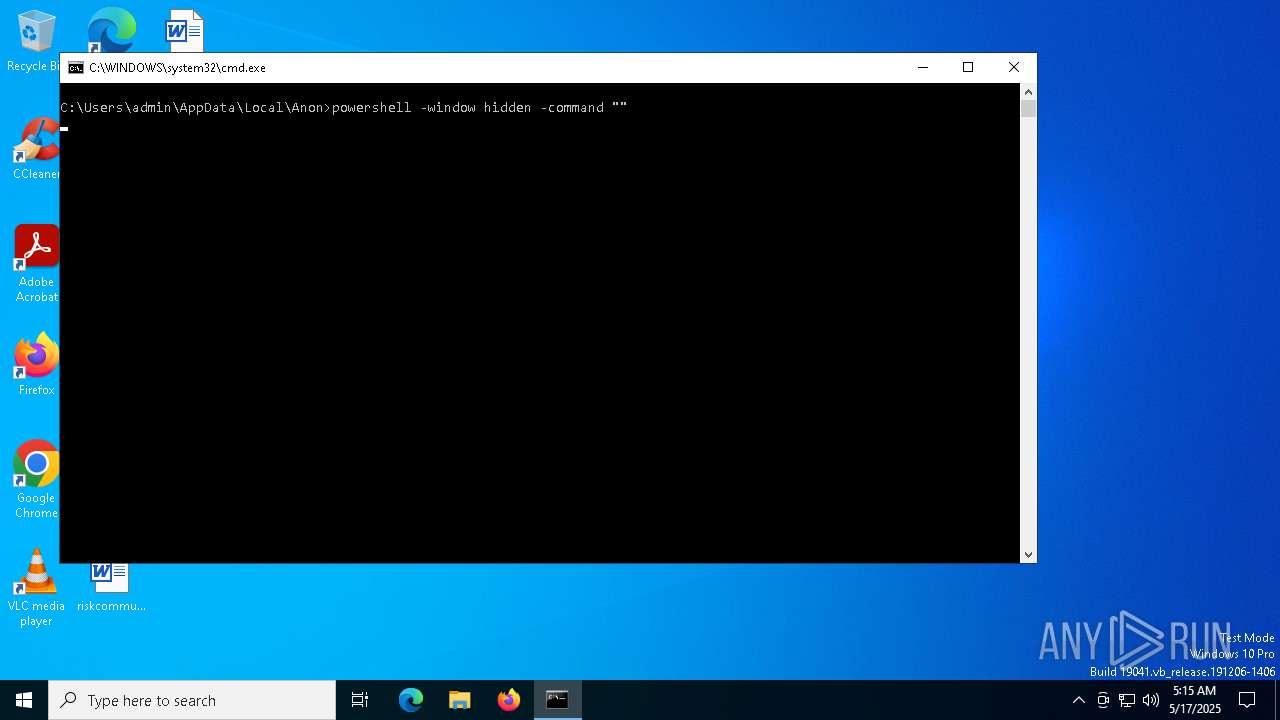
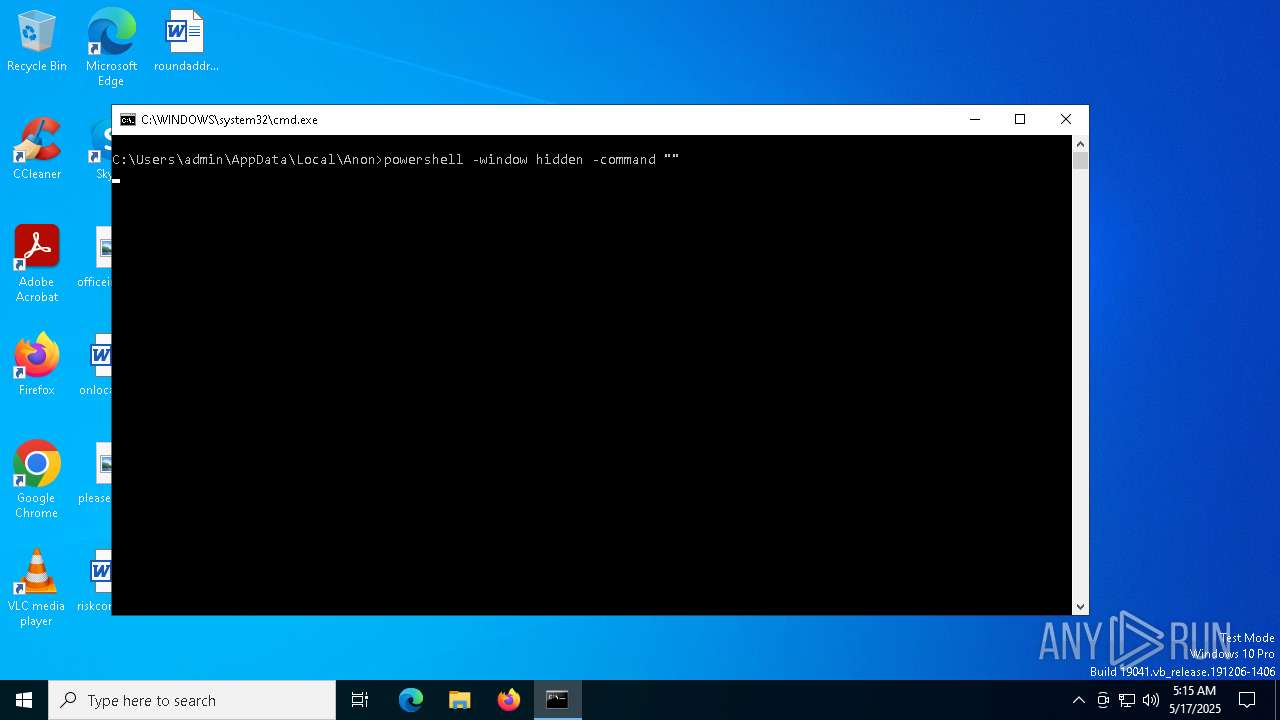
Run PowerShell with an invisible window
- powershell.exe (PID: 5008)
- powershell.exe (PID: 5072)
- powershell.exe (PID: 2516)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 1072)
- powershell.exe (PID: 5544)
- powershell.exe (PID: 5044)
- powershell.exe (PID: 3884)
- powershell.exe (PID: 3968)
- powershell.exe (PID: 1184)
- powershell.exe (PID: 4920)
- powershell.exe (PID: 6044)
- powershell.exe (PID: 720)
- powershell.exe (PID: 5008)
- powershell.exe (PID: 4572)
- powershell.exe (PID: 6040)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 1276)
- powershell.exe (PID: 644)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 2340)
- powershell.exe (PID: 6964)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 868)
- powershell.exe (PID: 232)
- powershell.exe (PID: 4056)
- powershell.exe (PID: 5204)
Changes Windows Defender settings
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 812)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4016)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 812)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 4016)
- cmd.exe (PID: 6908)
SUSPICIOUS
Process drops legitimate windows executable
- XWorm Crack.exe (PID: 2384)
- powershell.exe (PID: 1196)
Process drops python dynamic module
- XWorm Crack.exe (PID: 2384)
The process drops C-runtime libraries
- XWorm Crack.exe (PID: 2384)
Executable content was dropped or overwritten
- XWorm Crack.exe (PID: 2384)
- powershell.exe (PID: 1196)
- RuntimeBroker.exe (PID: 5008)
Application launched itself
- XWorm Crack.exe (PID: 2384)
Loads Python modules
- XWorm Crack.exe (PID: 6048)
Starts CMD.EXE for commands execution
- XWorm Crack.exe (PID: 6048)
- wscript.exe (PID: 1072)
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 5404)
- RuntimeBroker.exe (PID: 6136)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6456)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 1004)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 4696)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 6592)
- RuntimeBroker.exe (PID: 5308)
- RuntimeBroker.exe (PID: 5072)
- RuntimeBroker.exe (PID: 4304)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 5640)
- RuntimeBroker.exe (PID: 6876)
- RuntimeBroker.exe (PID: 6972)
- RuntimeBroker.exe (PID: 5600)
- RuntimeBroker.exe (PID: 5352)
- RuntimeBroker.exe (PID: 908)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 6512)
Executing commands from a ".bat" file
- XWorm Crack.exe (PID: 6048)
- wscript.exe (PID: 1072)
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 5404)
- RuntimeBroker.exe (PID: 6136)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6456)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 1004)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 4696)
- RuntimeBroker.exe (PID: 6592)
- RuntimeBroker.exe (PID: 5072)
- RuntimeBroker.exe (PID: 5308)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 4304)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 5640)
- RuntimeBroker.exe (PID: 6876)
- RuntimeBroker.exe (PID: 6972)
- RuntimeBroker.exe (PID: 5600)
- RuntimeBroker.exe (PID: 5352)
- RuntimeBroker.exe (PID: 908)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 6512)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5204)
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 812)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4016)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5204)
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 812)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 976)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4016)
- cmd.exe (PID: 3684)
The process executes VB scripts
- cmd.exe (PID: 5204)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1072)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 812)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 6908)
- cmd.exe (PID: 4016)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5736)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 2852)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 812)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 6244)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 7100)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 976)
- cmd.exe (PID: 1180)
- cmd.exe (PID: 5452)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 3192)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4016)
- cmd.exe (PID: 6908)
The executable file from the user directory is run by the CMD process
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 5404)
- RuntimeBroker.exe (PID: 6136)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 5064)
- RuntimeBroker.exe (PID: 6456)
- RuntimeBroker.exe (PID: 1004)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 5740)
- RuntimeBroker.exe (PID: 4696)
- RuntimeBroker.exe (PID: 6592)
- RuntimeBroker.exe (PID: 5308)
- RuntimeBroker.exe (PID: 5072)
- RuntimeBroker.exe (PID: 4304)
- RuntimeBroker.exe (PID: 6256)
- RuntimeBroker.exe (PID: 2896)
- RuntimeBroker.exe (PID: 5640)
- RuntimeBroker.exe (PID: 6876)
- RuntimeBroker.exe (PID: 6972)
- RuntimeBroker.exe (PID: 5600)
- RuntimeBroker.exe (PID: 5352)
- RuntimeBroker.exe (PID: 908)
- RuntimeBroker.exe (PID: 2084)
- RuntimeBroker.exe (PID: 7000)
- RuntimeBroker.exe (PID: 6512)
Reads security settings of Internet Explorer
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
Reads the date of Windows installation
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
Executes application which crashes
- XWorm V5.6 Crack.exe (PID: 1660)
- XWorm V5.6 Crack.exe (PID: 5216)
- XWorm V5.6 Crack.exe (PID: 1168)
- XWorm V5.6 Crack.exe (PID: 680)
- XWorm V5.6 Crack.exe (PID: 2896)
- XWorm V5.6 Crack.exe (PID: 132)
- XWorm V5.6 Crack.exe (PID: 5044)
- XWorm V5.6 Crack.exe (PID: 6040)
- XWorm V5.6 Crack.exe (PID: 2136)
- XWorm V5.6 Crack.exe (PID: 2152)
- XWorm V5.6 Crack.exe (PID: 6656)
- XWorm V5.6 Crack.exe (PID: 5772)
- XWorm V5.6 Crack.exe (PID: 5600)
- XWorm V5.6 Crack.exe (PID: 6228)
- XWorm V5.6 Crack.exe (PID: 6724)
- XWorm V5.6 Crack.exe (PID: 3888)
- XWorm V5.6 Crack.exe (PID: 3800)
- XWorm V5.6 Crack.exe (PID: 5680)
- XWorm V5.6 Crack.exe (PID: 1812)
- XWorm V5.6 Crack.exe (PID: 6820)
- XWorm V5.6 Crack.exe (PID: 3304)
- XWorm V5.6 Crack.exe (PID: 536)
- XWorm V5.6 Crack.exe (PID: 5360)
- XWorm V5.6 Crack.exe (PID: 1704)
- XWorm V5.6 Crack.exe (PID: 5796)
- XWorm V5.6 Crack.exe (PID: 6744)
INFO
Checks proxy server information
- XWorm Crack.exe (PID: 6048)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 1452)
Reads the computer name
- XWorm Crack.exe (PID: 2384)
- XWorm Crack.exe (PID: 6048)
- XWorm V5.6 Crack.exe (PID: 1660)
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
- XWorm V5.6 Crack.exe (PID: 5216)
Checks supported languages
- XWorm Crack.exe (PID: 2384)
- XWorm Crack.exe (PID: 6048)
- XWorm V5.6 Crack.exe (PID: 1660)
- RuntimeBroker.exe (PID: 5008)
- XWorm V5.6 Crack.exe (PID: 5216)
- RuntimeBroker.exe (PID: 5740)
The sample compiled with english language support
- XWorm Crack.exe (PID: 2384)
Create files in a temporary directory
- XWorm Crack.exe (PID: 2384)
- XWorm Crack.exe (PID: 6048)
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1660)
- powershell.exe (PID: 5680)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1660)
- powershell.exe (PID: 5680)
- powershell.exe (PID: 1452)
Disables trace logs
- powershell.exe (PID: 1196)
- powershell.exe (PID: 1452)
Process checks computer location settings
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
Reads the machine GUID from the registry
- XWorm V5.6 Crack.exe (PID: 1660)
- RuntimeBroker.exe (PID: 5008)
- RuntimeBroker.exe (PID: 5740)
- XWorm V5.6 Crack.exe (PID: 5216)
Creates files or folders in the user directory
- WerFault.exe (PID: 2344)
- WerFault.exe (PID: 736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:17 04:50:08+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 145408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
463
Monitored processes
307
Malicious processes
53
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Users\admin\AppData\Local\Temp\XWorm V5.6 Crack.exe" | C:\Users\admin\AppData\Local\Temp\XWorm V5.6 Crack.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: @ThreatCommunity Integrity Level: HIGH Description: XWorm by @ThreatCommunity Exit code: 3762504530 Version: 5.6.0.0 Modules
| |||||||||||||||
| 232 | powershell -window hidden -command "" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | "C:\Users\admin\AppData\Local\Temp\XWorm V5.6 Crack.exe" | C:\Users\admin\AppData\Local\Temp\XWorm V5.6 Crack.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: @ThreatCommunity Integrity Level: HIGH Description: XWorm by @ThreatCommunity Exit code: 3762504530 Version: 5.6.0.0 Modules
| |||||||||||||||
| 632 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | powershell -window hidden -command "" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | attrib +h "Anon" /s /d | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\WerFault.exe -u -p 6744 -s 936 | C:\Windows\System32\WerFault.exe | — | XWorm V5.6 Crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
450 125
Read events
449 949
Write events
98
Delete events
78
Modification events
| (PID) Process: | (5204) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | ProgramId |
Value: 00064ee32d88d6ce3eb386c7e88f7c8d705600000000 | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | FileId |
Value: 00003547dfaa6e524a367aff90b685bdb5e728c1bfeb | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\appdata\local\temp\xworm v5.6 crack.exe | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | LongPathHash |
Value: xworm v5.6 crack|b448236e62d20cab | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | Name |
Value: XWorm V5.6 Crack.exe | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | OriginalFileName |
Value: xworm.exe | |||
| (PID) Process: | (2344) WerFault.exe | Key: | \REGISTRY\A\{03126eeb-f701-fba6-2c26-de503fc66842}\Root\InventoryApplicationFile\xworm v5.6 crack|b448236e62d20cab |
| Operation: | write | Name: | Publisher |
Value: @threatcommunity | |||
Executable files
57
Suspicious files
55
Text files
193
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-fibers-l1-1-0.dll | executable | |
MD5:B5E2760C5A46DBEB8AE18C75F335707E | SHA256:91D249D7BC0E38EF6BCB17158B1FDC6DD8888DC086615C9B8B750B87E52A5FB3 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:9F746F4F7D845F063FEA3C37DCEBC27C | SHA256:88ACE577A9C51061CB7D1A36BABBBEFA48212FADC838FFDE98FDFFF60DE18386 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:8F8EB9CB9E78E3A611BC8ACAEC4399CB | SHA256:1BD81DFD19204B44662510D9054852FB77C9F25C1088D647881C9B976CC16818 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:C2F8C03ECCE9941492BFBE4B82F7D2D5 | SHA256:D56CE7B1CD76108AD6C137326EC694A14C99D48C3D7B0ACE8C3FF4D9BCEE3CE8 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:226A5983AE2CBBF0C1BDA85D65948ABC | SHA256:591358EB4D1531E9563EE0813E4301C552CE364C912CE684D16576EABF195DC3 | |||
| 2384 | XWorm Crack.exe | C:\Users\admin\AppData\Local\Temp\_MEI23842\api-ms-win-core-fibers-l1-1-1.dll | executable | |
MD5:050A30A687E7A2FA6F086A0DB89AA131 | SHA256:FC9D86CEC621383EAB636EBC87DDD3F5C19A3CB2A33D97BE112C051D0B275429 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
80
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.67.160.244:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2340 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2340 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6048 | XWorm Crack.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
6048 | XWorm Crack.exe | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.67.160.244:80 | ocsp.digicert.com | AKAMAI-AS | JP | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |