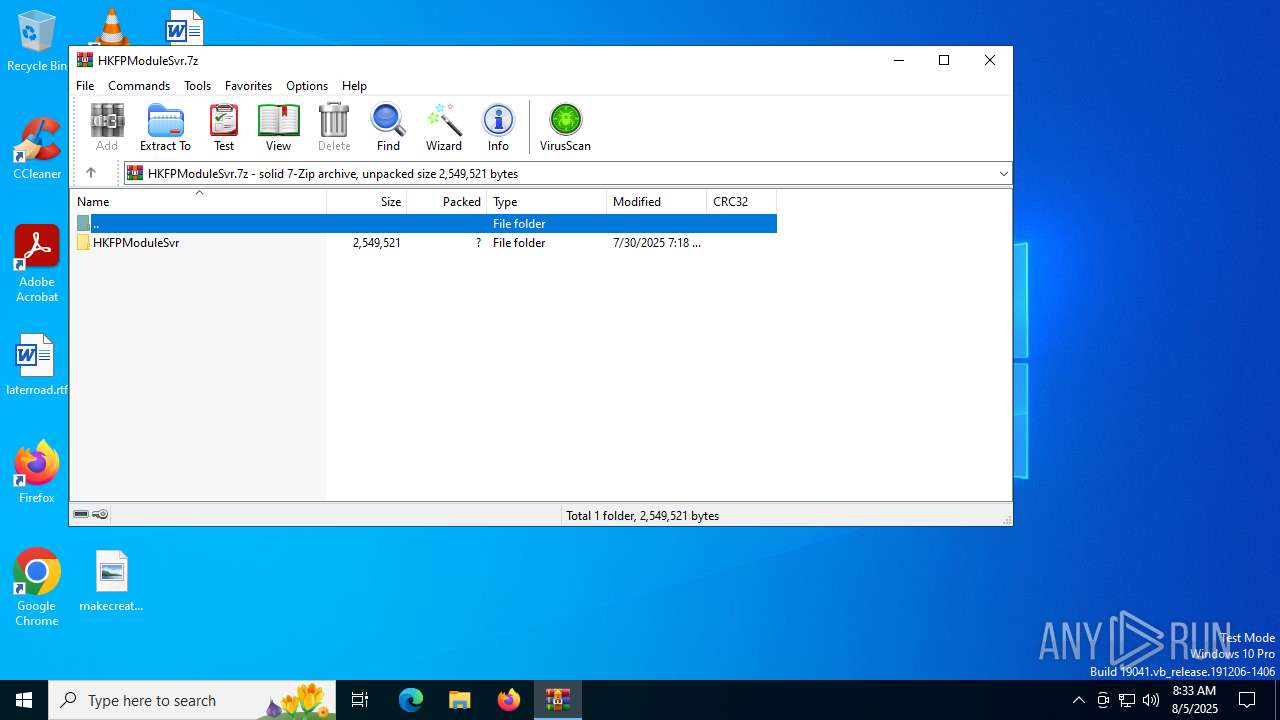
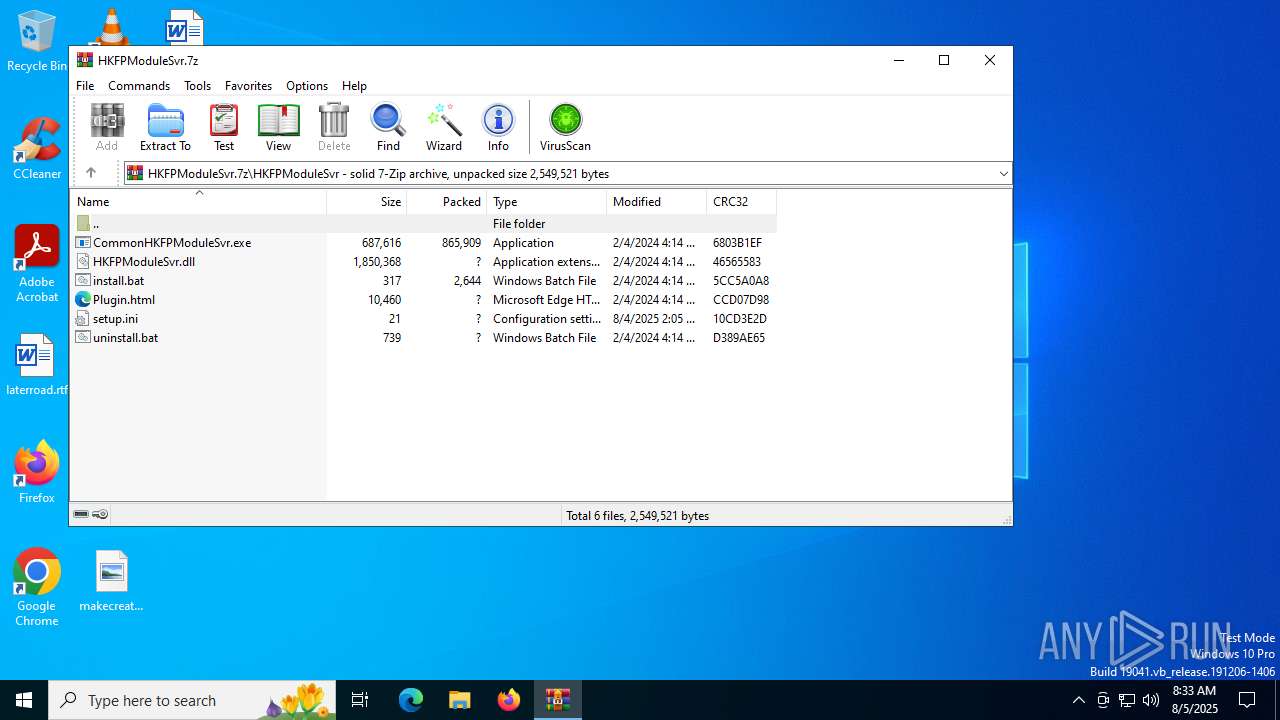
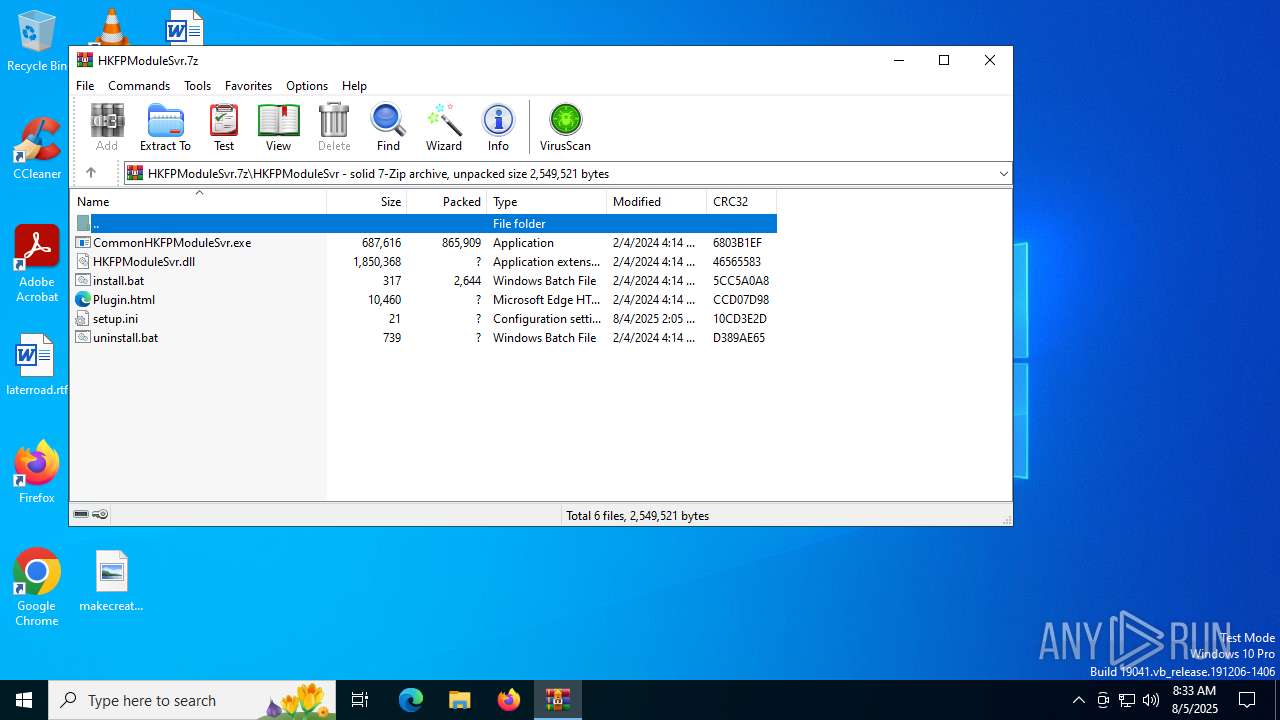
| File name: | HKFPModuleSvr.7z |
| Full analysis: | https://app.any.run/tasks/bf3d7830-5a59-4a68-bf23-0dc9a0179c16 |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2025, 08:32:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B11E38D9490F5D88A65A6A0970FF3755 |
| SHA1: | EB2D3AFB5B5B9077D100998AC43E209A0117AD03 |
| SHA256: | 170F4007FC5BA241F11EE451158841D2C90CB113D1D41C9A1595DC2B1B23C6A1 |
| SSDEEP: | 49152:uuB60VlHdz1aWjBJoeqalLEt06WtV/Ydwdskc4dlNQjVZOB7RovC80d+/xrOuopC:9B6kl9z1aWjBJ/E66WodmXQjVSj80d+J |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 5552)
- net.exe (PID: 1232)
Generic archive extractor
- WinRAR.exe (PID: 4072)
SUSPICIOUS
Restarts service on failure
- sc.exe (PID: 6584)
Sets the service to start on system boot
- sc.exe (PID: 1964)
Starts SC.EXE for service management
- cmd.exe (PID: 5552)
Creates a new Windows service
- sc.exe (PID: 3672)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4072)
Manual execution by a user
- cmd.exe (PID: 5552)
- CommonHKFPModuleSvr.exe (PID: 3740)
Checks supported languages
- CommonHKFPModuleSvr.exe (PID: 3740)
- mode.com (PID: 4168)
Checks proxy server information
- slui.exe (PID: 2216)
Reads the software policy settings
- slui.exe (PID: 2216)
Reads the computer name
- CommonHKFPModuleSvr.exe (PID: 3740)
The sample compiled with english language support
- WinRAR.exe (PID: 4072)
Starts MODE.COM to configure console settings
- mode.com (PID: 4168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:07:30 07:18:26+00:00 |
| ArchivedFileName: | HKFPModuleSvr |
Total processes
158
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1232 | net start "CommonHKFPModuleSvr" | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | C:\WINDOWS\system32\net1 start "CommonHKFPModuleSvr" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1964 | sc config "CommonHKFPModuleSvr" start= AUTO | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2216 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3672 | sc create "CommonHKFPModuleSvr" binPath= "\"C:\Users\admin\Desktop\CommonHKFPModuleSvr.exe\"" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | "C:\Users\admin\Desktop\CommonHKFPModuleSvr.exe" | C:\Users\admin\Desktop\CommonHKFPModuleSvr.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 20220114 Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 4072 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\HKFPModuleSvr.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4168 | mode con cols=50 lines=10 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5552 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 242
Read events
3 208
Write events
21
Delete events
13
Modification events
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HKFPModuleSvr.7z | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
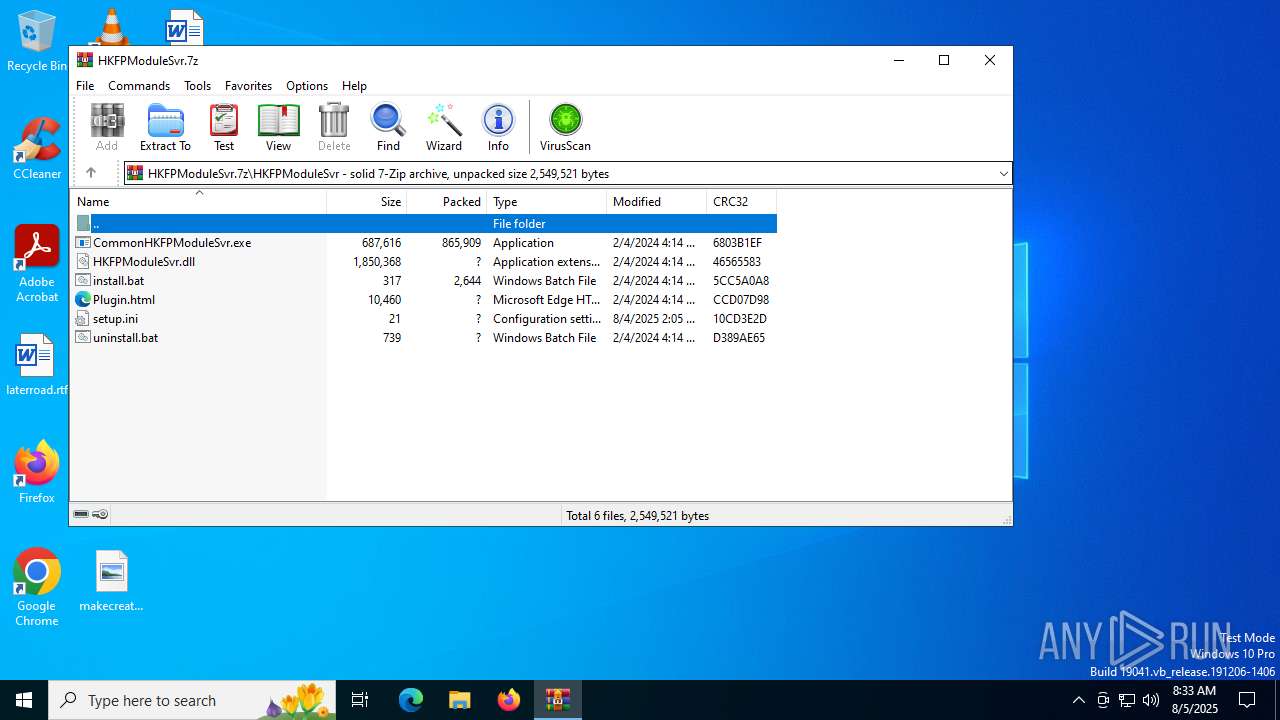
Executable files
2
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\CommonHKFPModuleSvr.exe | executable | |
MD5:C9C8094F292CECF355D917E506BFE650 | SHA256:1153AEFC313D0DC6C13181C5ACB4700F3DF1E291B66231996EE5C1D04DD091BD | |||
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\setup.ini | text | |
MD5:D0BA7DC58FB312547E949F4B2E77BDDF | SHA256:A39103279E9E57DB24605C679FE4B94BDFC8587C933390DB3779FF1BCDCFEED8 | |||
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\HKFPModuleSvr.dll | executable | |
MD5:26805E0D0B78B3D1E143EA3F6C4C25F0 | SHA256:1E6EABCA4C0FF075C6527B10D85733178508E879658D8EDB3482BCE345C29BC0 | |||
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\Plugin.html | html | |
MD5:B6137CDC0F9837AC7DAE47BEB75E0CEB | SHA256:2489852E608F6EE6E2638F33D806E5C9C71FCF1BF2FF5AB0B499813AA8BC2A8B | |||
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\install.bat | text | |
MD5:53C9535959C1D7A9D470CC918BF8B73C | SHA256:206E94B4D1936BBDAD3B07F4A399AB58ED4884C154CD857851A80C3D98D4CFA3 | |||
| 4072 | WinRAR.exe | C:\Users\admin\Desktop\uninstall.bat | text | |
MD5:6DA3636DB49F9AD663ADC36093CA9888 | SHA256:7AEB4B4C5025FA299070C47474FF34395130A58C19B9568969188877DA8E309D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
47
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4060 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2524 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
236 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4060 | svchost.exe | 20.190.151.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4060 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 2.16.241.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4196 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |