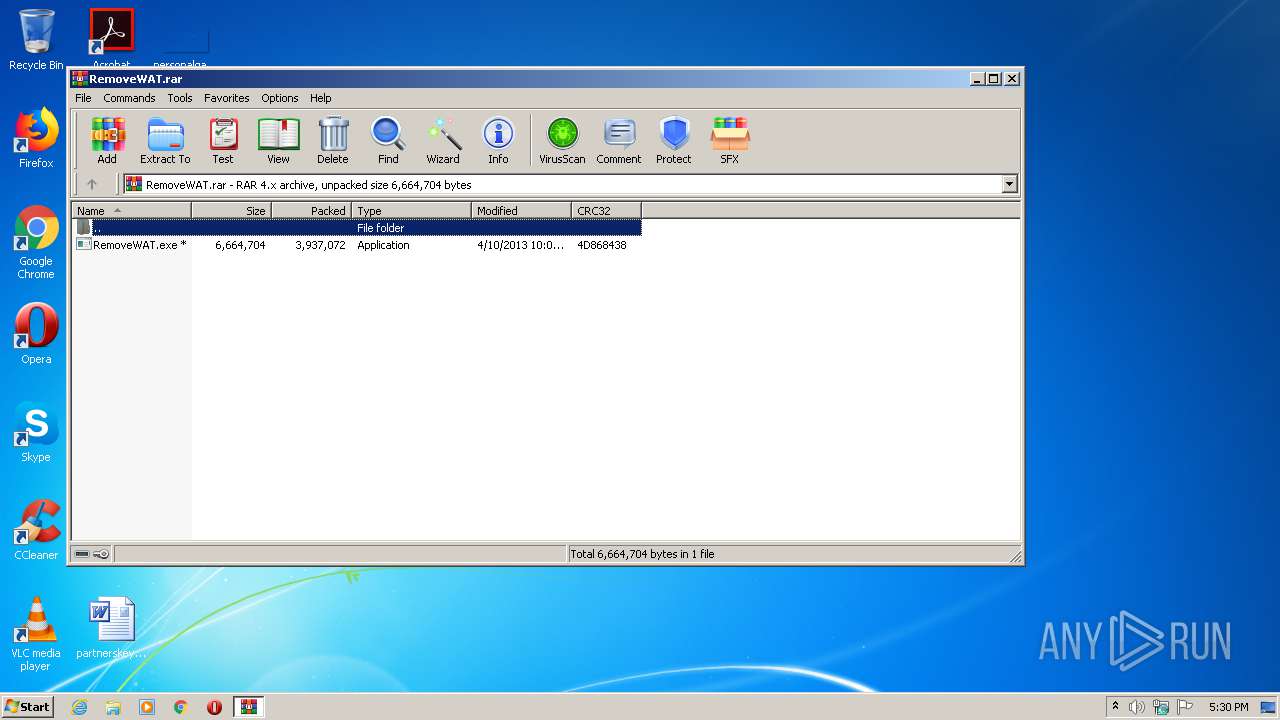
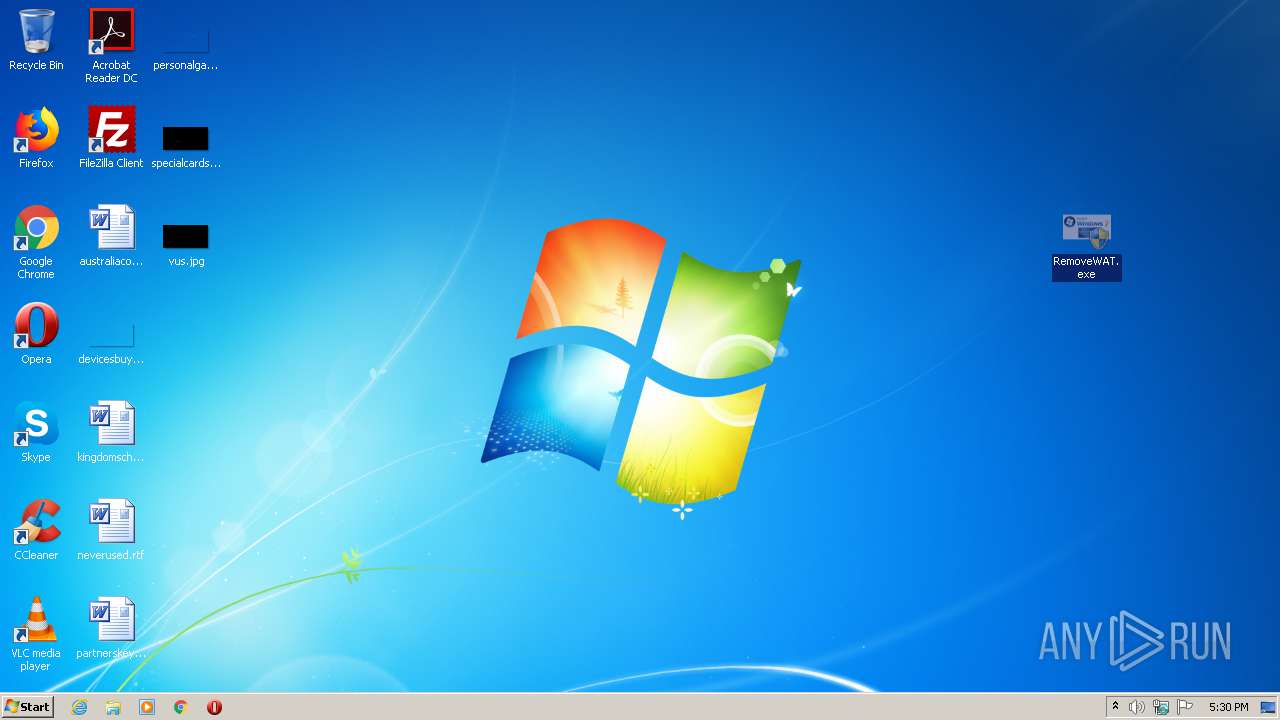
| File name: | RemoveWAT.rar |
| Full analysis: | https://app.any.run/tasks/8d10563d-6778-477c-a256-7fcf9a559425 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 16:30:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | CF99BEC65BE72BEA0D03D08B4B14A1F6 |
| SHA1: | BDB51F0D3DC9CEC90F6F4AABF5F1A2D71AD2953F |
| SHA256: | 170C725FE2B38199EA6A316386FD874E32C6930E40CCA6D4E9CF3F57ECF97AC6 |
| SSDEEP: | 98304:bw23yxOcCHuRsIpYjWBBBVyKTjavrMJ6tEAD:ZEzejAz/j7kEw |
MALICIOUS
Application was dropped or rewritten from another process
- RemoveWAT.exe (PID: 2192)
- RemoveWAT.exe (PID: 904)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2764)
- schtasks.exe (PID: 1896)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2468)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2256)
Uses TASKKILL.EXE to kill process
- RemoveWAT.exe (PID: 904)
- cmd.exe (PID: 3416)
Creates files in the Windows directory
- RemoveWAT.exe (PID: 904)
- wusa.exe (PID: 1756)
Removes files from Windows directory
- RemoveWAT.exe (PID: 904)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 1412)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 2532)
Executed as Windows Service
- vssvc.exe (PID: 1144)
Starts CMD.EXE for commands execution
- RemoveWAT.exe (PID: 904)
INFO
Manual execution by user
- RemoveWAT.exe (PID: 2192)
- RemoveWAT.exe (PID: 904)
Low-level read access rights to disk partition
- vssvc.exe (PID: 1144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 3937114 |
|---|---|
| UncompressedSize: | 6664704 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2013:04:10 22:09:05 |
| PackingMethod: | Normal |
| ArchivedFileName: | RemoveWAT.exe |
Total processes
69
Monitored processes
24
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | icacls "C:\Windows\System32\Wat\WatAdminSvc.exe" /deny *S-1-1-0:(X) | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | icacls "C:\Windows\System32\user32.dll" /grant *S-1-1-0:F | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
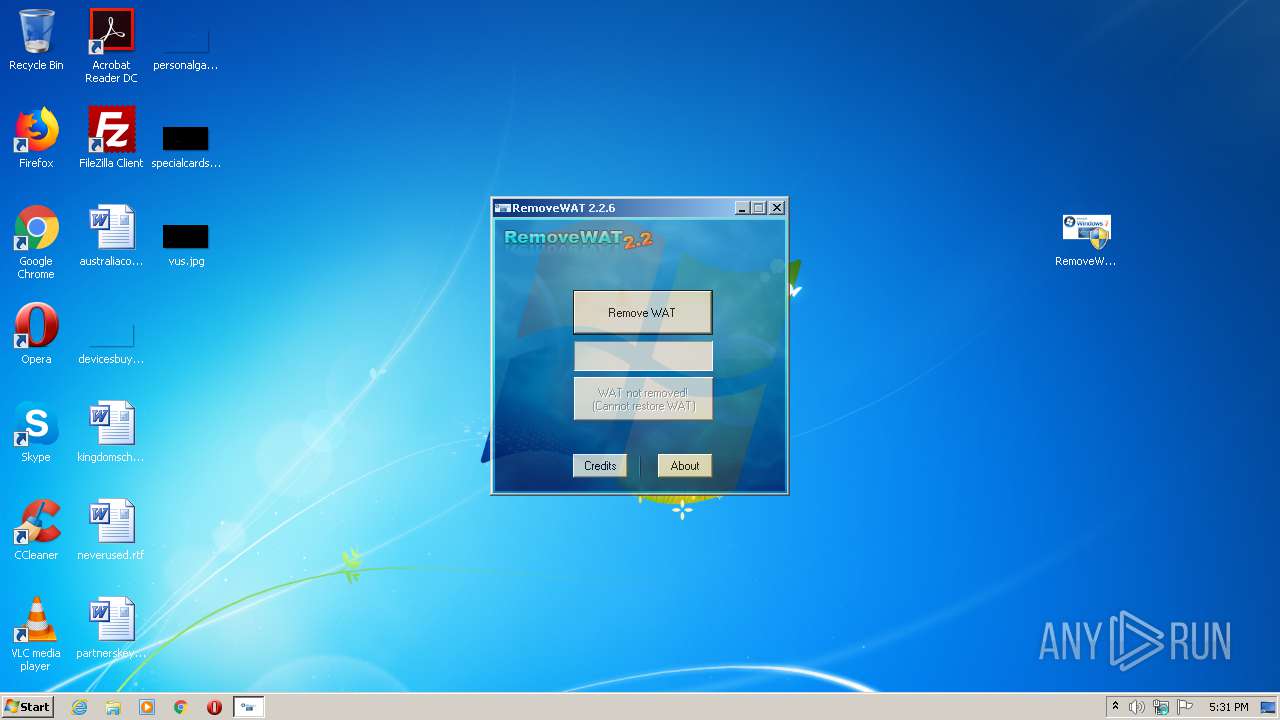
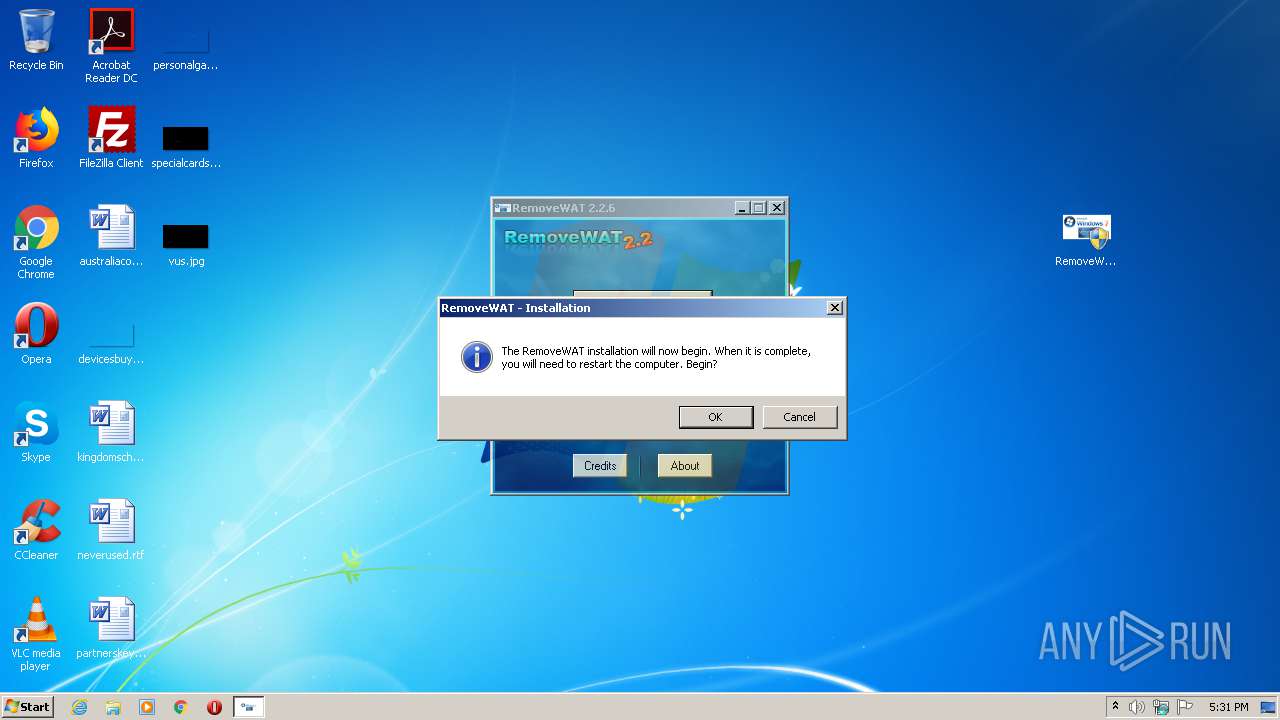
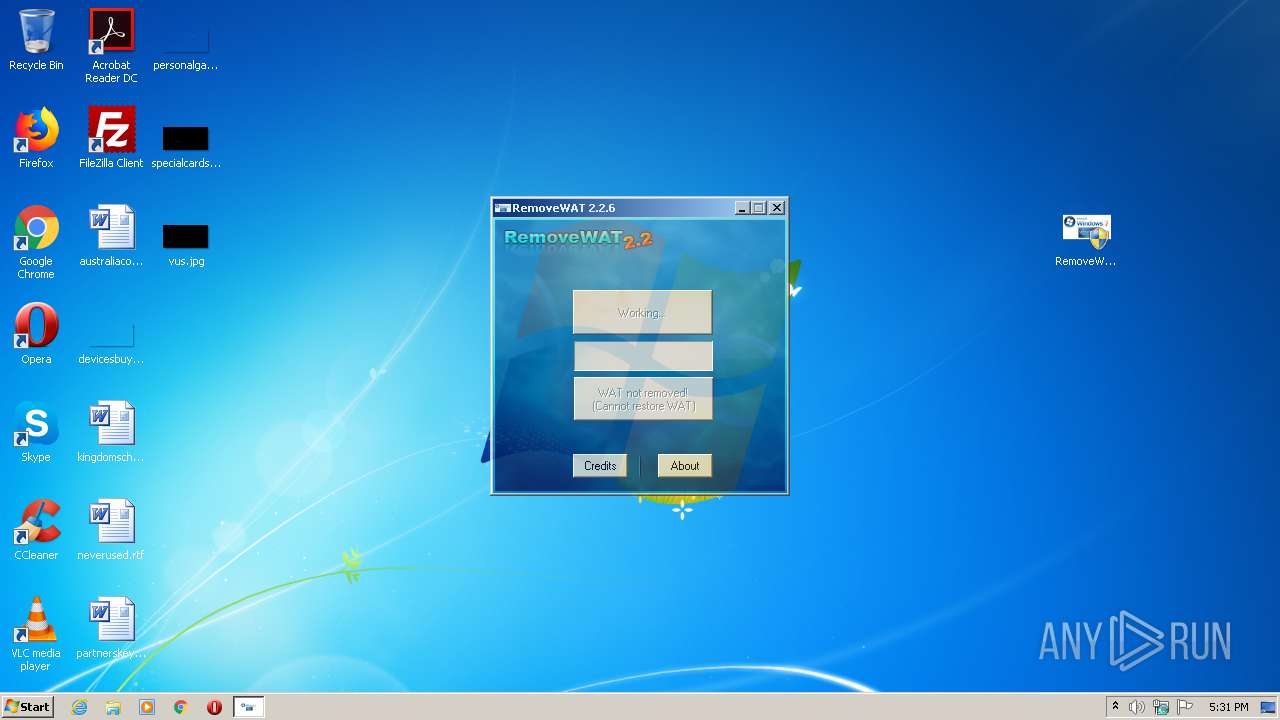
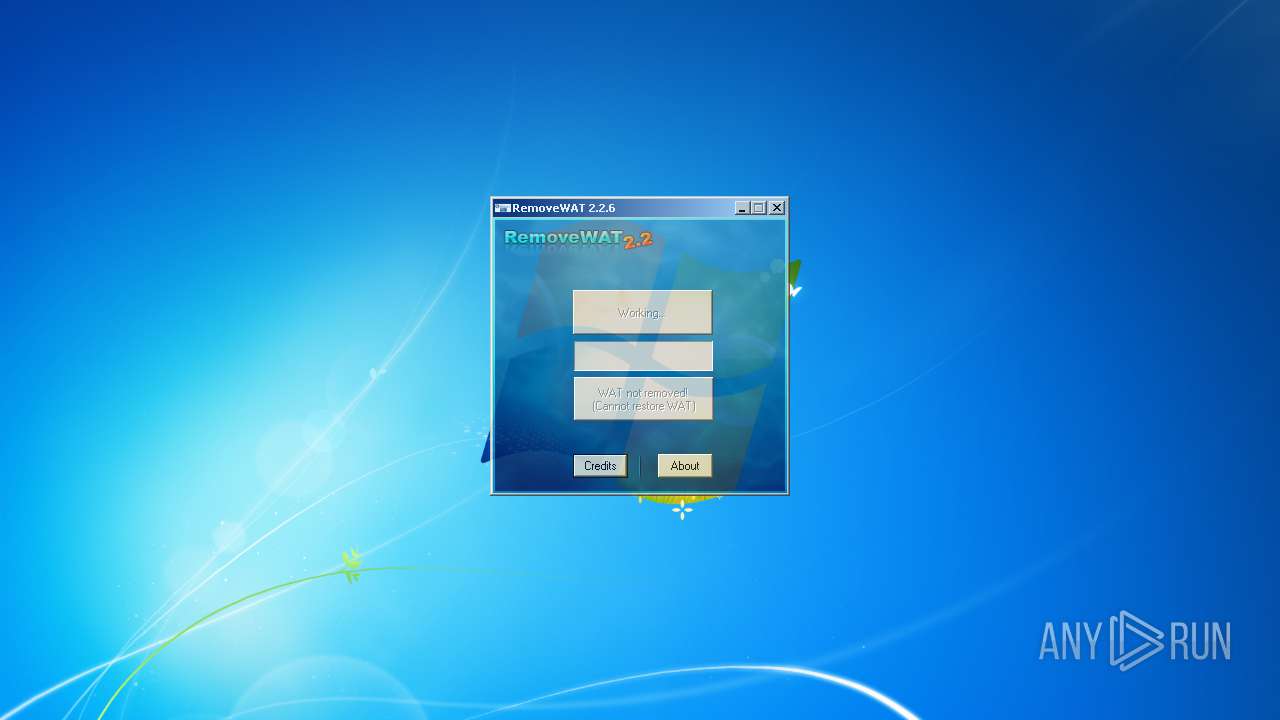
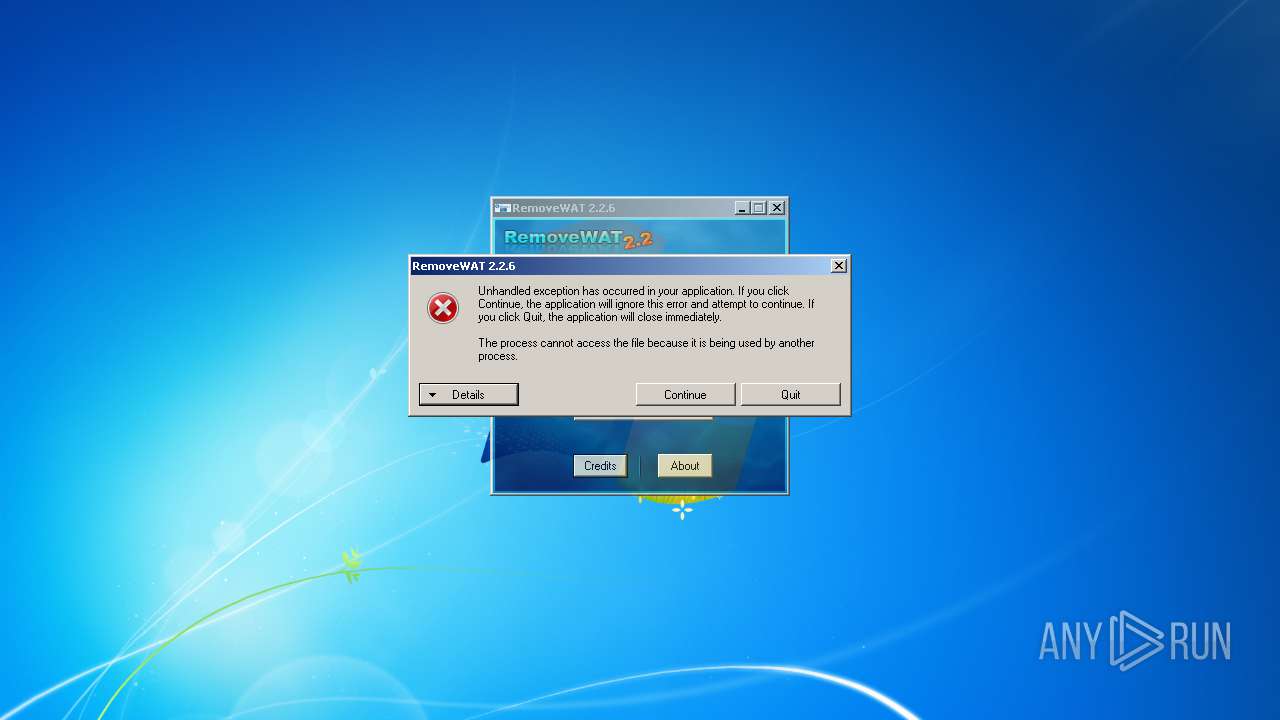
| 904 | "C:\Users\admin\Desktop\RemoveWAT.exe" | C:\Users\admin\Desktop\RemoveWAT.exe | explorer.exe | ||||||||||||
User: admin Company: Hazar & Co. Integrity Level: HIGH Description: RemoveWAT Exit code: 0 Version: 2.2.6.0 Modules
| |||||||||||||||
| 1144 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | "C:\Windows\System32\cmd.exe" /c takeown /f "C:\Windows\System32\Wat\WatUX.exe" & icacls "C:\Windows\System32\Wat\WatUX.exe" /reset & icacls "C:\Windows\System32\Wat\WatUX.exe" /deny *S-1-1-0:(X) | C:\Windows\System32\cmd.exe | — | RemoveWAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1756 | "C:\Windows\system32\wusa.exe" "C:\Windows\wat.MSU" /quiet | C:\Windows\system32\wusa.exe | — | RemoveWAT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Update Standalone Installer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1896 | schtasks /change /disable /tn "\Microsoft\Windows\Windows Activation Technologies\ValidationTaskDeadline" | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2032 | icacls "C:\Windows\System32\Wat\WatUX.exe" /reset | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | icacls "C:\Windows\System32\Wat\WatAdminSvc.exe" /reset | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | icacls "C:\Windows\System32\Wat\WatUX.exe" /deny *S-1-1-0:(X) | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
735
Read events
589
Write events
145
Delete events
1
Modification events
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RemoveWAT.rar | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
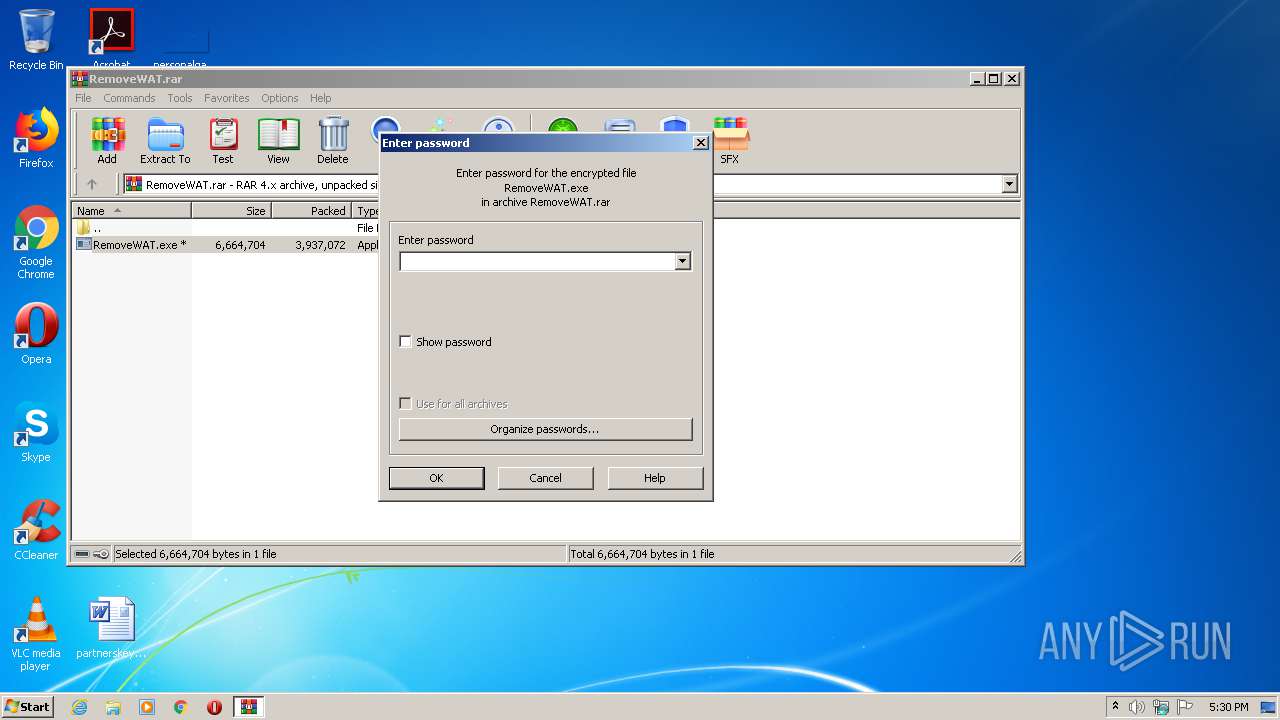
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
1
Suspicious files
2
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\$dpx$.tmp\2e8815f03a6b894faa149db07cee4892.tmp | — | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\$dpx$.tmp\a396e9d82fba75478943aaf1730a4603.tmp | — | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\$dpx$.tmp\ebd4de63fd6bed4ebd38421173b0bbbc.tmp | — | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\$dpx$.tmp\041c9aa9aa7bc14b9454cf7224538dd6.tmp | — | |
MD5:— | SHA256:— | |||
| 1144 | vssvc.exe | C: | — | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\Windows\Logs\DPX\setuperr.log | — | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\WSUSSCAN.cab | compressed | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\Windows6.1-KB971033-x86.xml | xml | |
MD5:— | SHA256:— | |||
| 904 | RemoveWAT.exe | C:\Windows\wat.MSU | msu | |
MD5:— | SHA256:— | |||
| 1756 | wusa.exe | C:\fd463ae46d285d6e2f45940546f3\Windows6.1-KB971033-x86-pkgProperties.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report