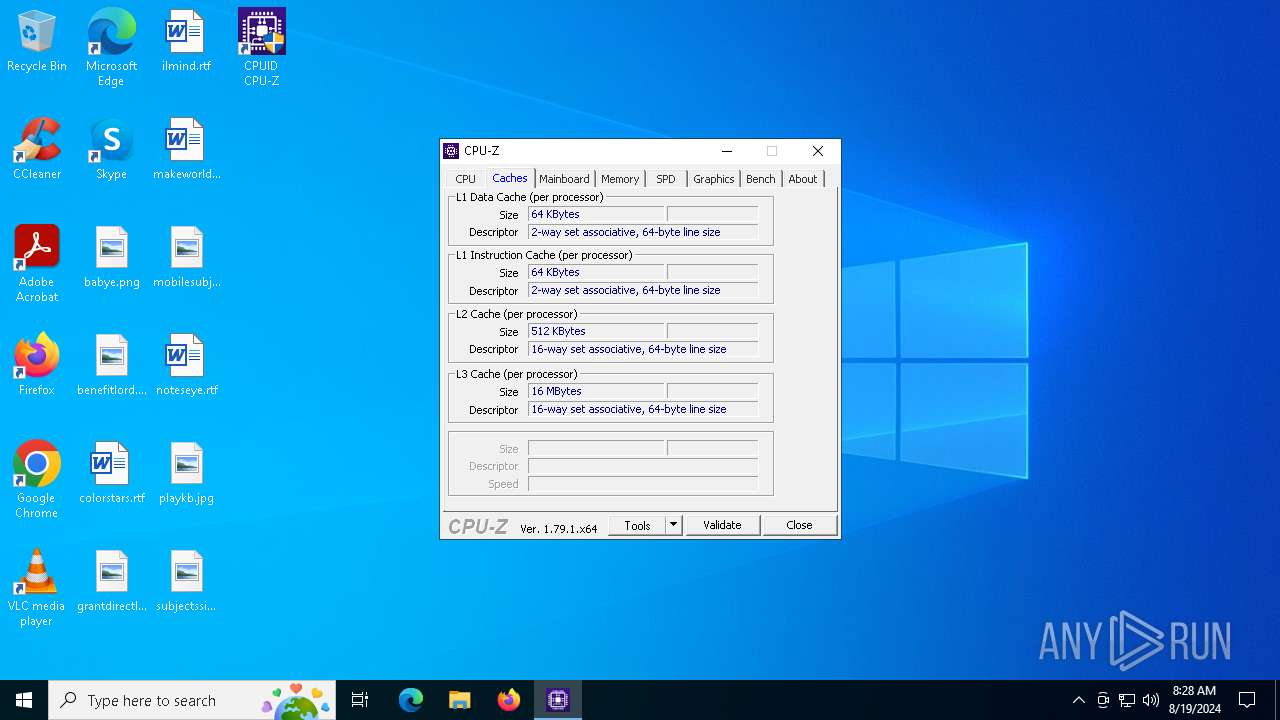
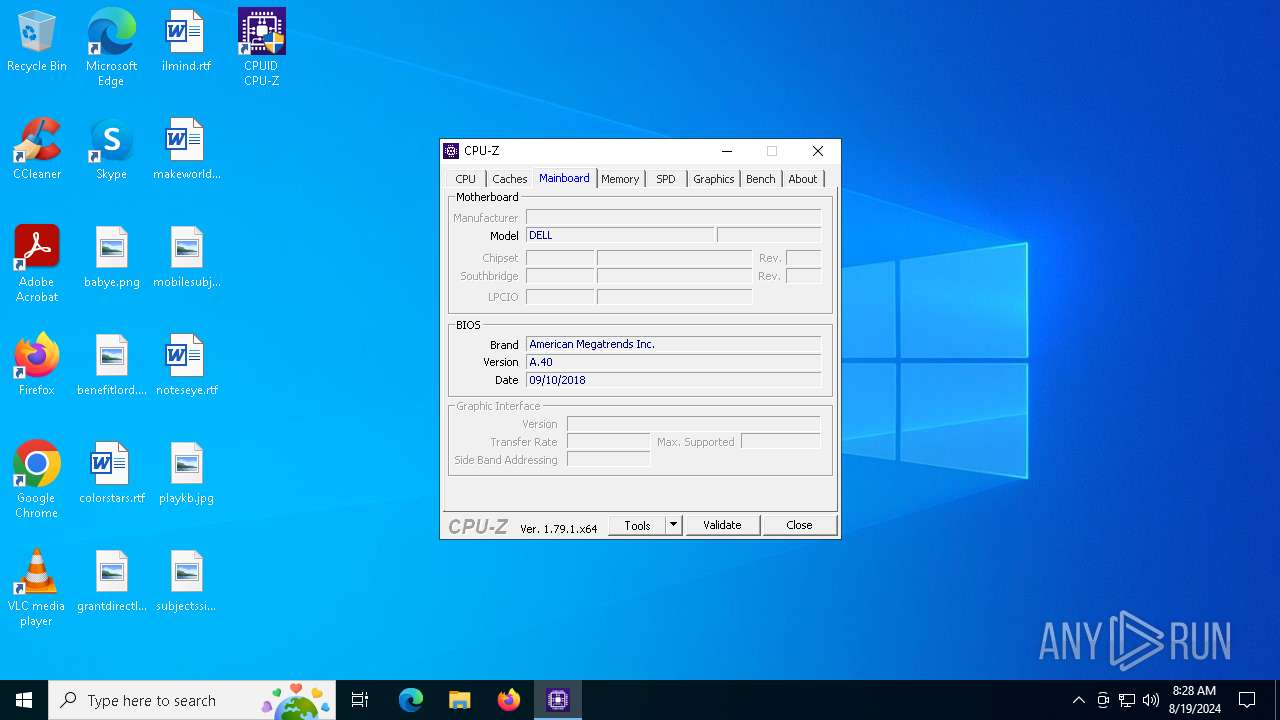
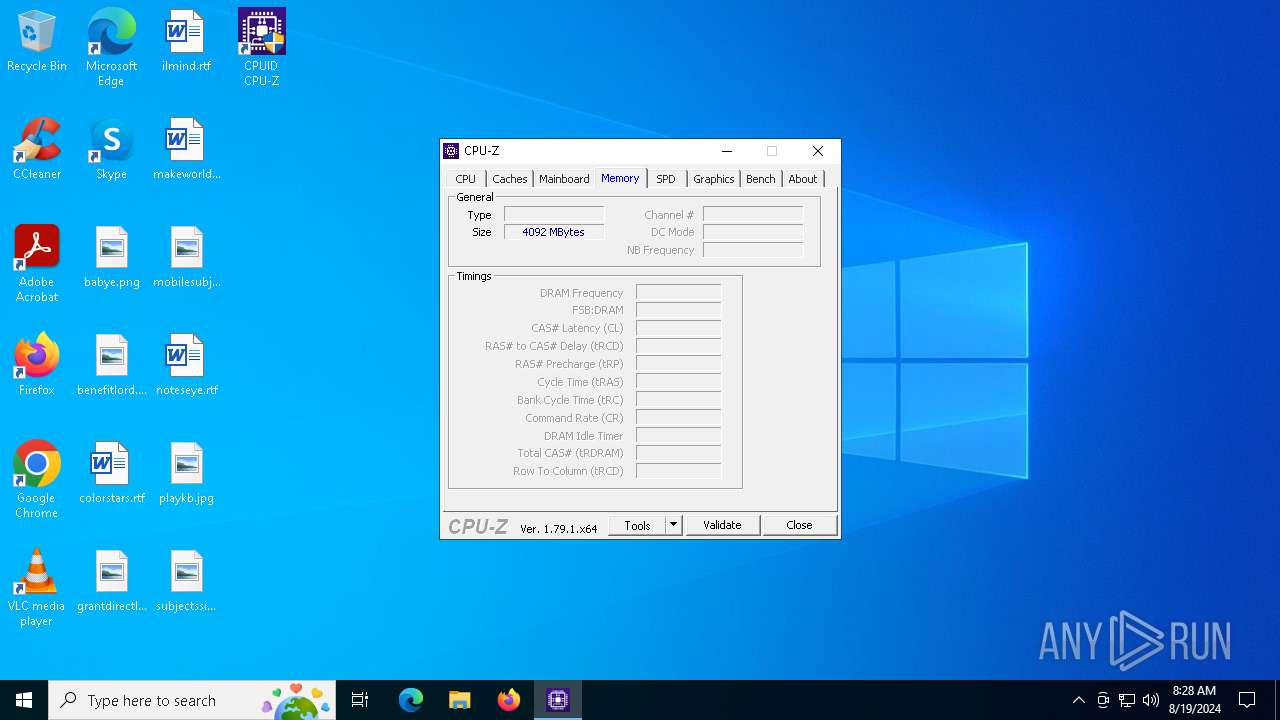
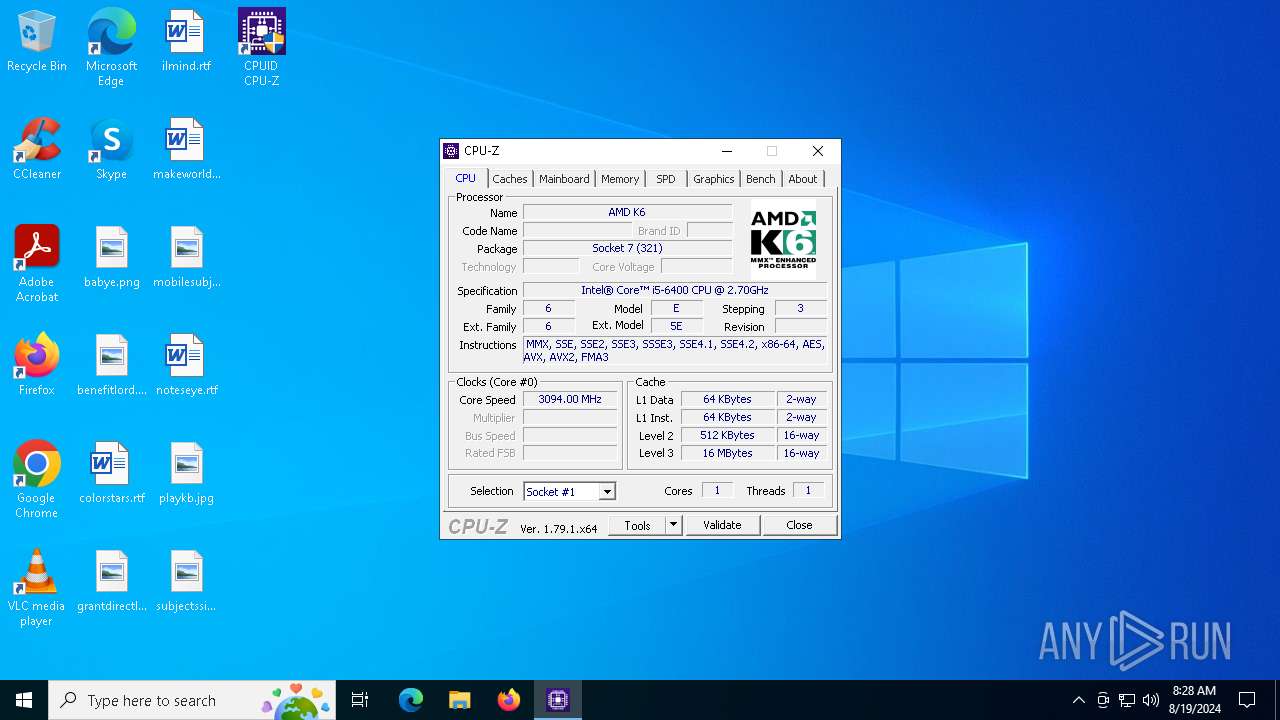
| File name: | cpu-z_1.79-en.exe |
| Full analysis: | https://app.any.run/tasks/4eaf5895-04ce-4056-a6a0-837a9dd80709 |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2024, 08:27:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F6DB452E6B1C905795DCCCC22FB6D84A |
| SHA1: | FAE363D27FC3CA83F69220717583F3614761146F |
| SHA256: | 170ADB03D00AC93DEC154BBC2EF925A74F8FF96CFDB7E8C0728DBC6376BC560E |
| SSDEEP: | 49152:z75+YryMHetWY9VMDlmnc8swaW/vc+sm8Yp:X5+yHecY7MMc8lao5Xp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- cpu-z_1.79-en.tmp (PID: 6432)
- cpuz.exe (PID: 1128)
Drops the executable file immediately after the start
- cpu-z_1.79-en.exe (PID: 6408)
- cpu-z_1.79-en.exe (PID: 6532)
- cpu-z_1.79-en.tmp (PID: 6580)
- cpuz.exe (PID: 1128)
Executable content was dropped or overwritten
- cpu-z_1.79-en.exe (PID: 6408)
- cpu-z_1.79-en.exe (PID: 6532)
- cpu-z_1.79-en.tmp (PID: 6580)
- cpuz.exe (PID: 1128)
Reads the date of Windows installation
- cpu-z_1.79-en.tmp (PID: 6432)
Start notepad (likely ransomware note)
- cpu-z_1.79-en.tmp (PID: 6432)
There is functionality for VM detection (VirtualBox)
- cpuz.exe (PID: 1128)
Checks Windows Trust Settings
- cpuz.exe (PID: 1128)
Reads the Windows owner or organization settings
- cpu-z_1.79-en.tmp (PID: 6580)
Drops a system driver (possible attempt to evade defenses)
- cpuz.exe (PID: 1128)
INFO
Checks supported languages
- cpu-z_1.79-en.tmp (PID: 6432)
- cpu-z_1.79-en.exe (PID: 6408)
- cpu-z_1.79-en.exe (PID: 6532)
- cpu-z_1.79-en.tmp (PID: 6580)
- cpuz.exe (PID: 1128)
Reads the computer name
- cpu-z_1.79-en.tmp (PID: 6432)
- cpu-z_1.79-en.tmp (PID: 6580)
- cpuz.exe (PID: 1128)
Create files in a temporary directory
- cpu-z_1.79-en.exe (PID: 6532)
- cpu-z_1.79-en.tmp (PID: 6580)
- cpuz.exe (PID: 1128)
- cpu-z_1.79-en.exe (PID: 6408)
Process checks computer location settings
- cpu-z_1.79-en.tmp (PID: 6432)
Creates a software uninstall entry
- cpu-z_1.79-en.tmp (PID: 6580)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6836)
Manual execution by a user
- cpuz.exe (PID: 5956)
- cpuz.exe (PID: 1128)
Reads Environment values
- cpuz.exe (PID: 1128)
Checks proxy server information
- cpuz.exe (PID: 1128)
Reads the machine GUID from the registry
- cpuz.exe (PID: 1128)
Creates files or folders in the user directory
- cpuz.exe (PID: 1128)
Reads the software policy settings
- cpuz.exe (PID: 1128)
Creates files in the program directory
- cpu-z_1.79-en.tmp (PID: 6580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
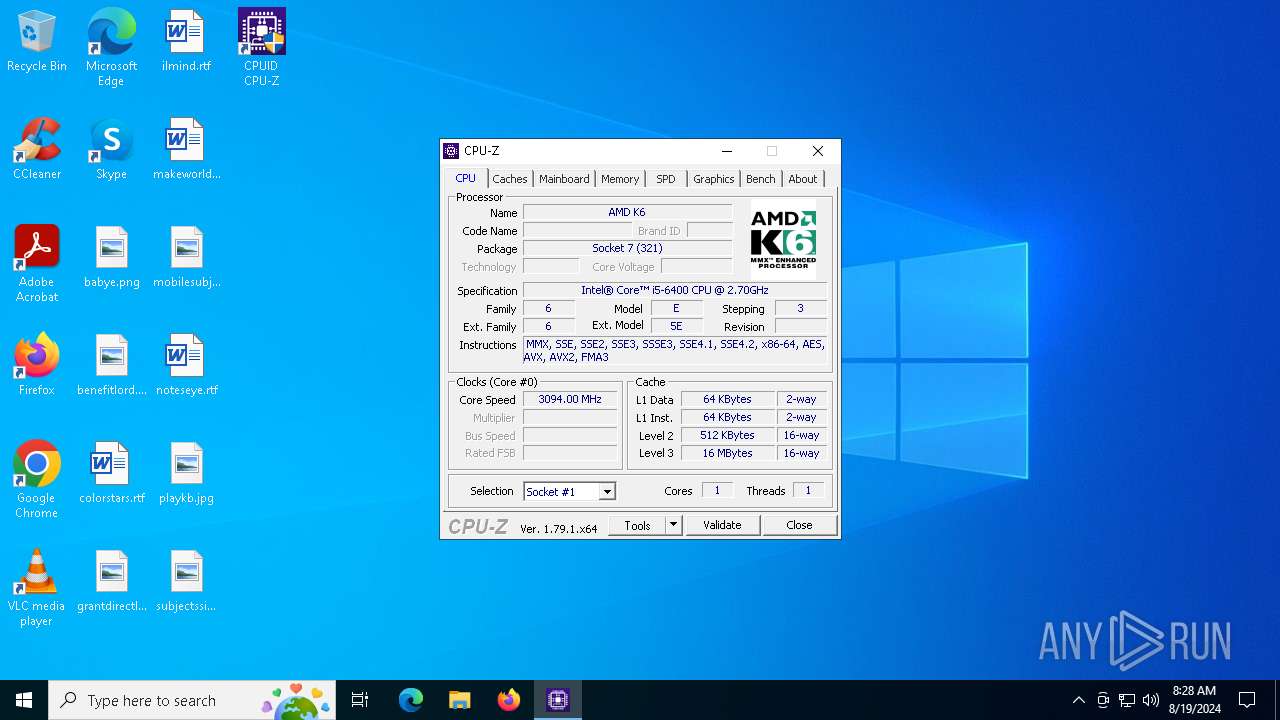
| FileDescription: | CPUID CPU-Z Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | CPUID CPU-Z |
| ProductVersion: |
Total processes
140
Monitored processes
7
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1128 | "C:\Program Files\CPUID\CPU-Z\cpuz.exe" | C:\Program Files\CPUID\CPU-Z\cpuz.exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: CPU-Z Application Version: 1, 7, 9, 1 Modules
| |||||||||||||||
| 5956 | "C:\Program Files\CPUID\CPU-Z\cpuz.exe" | C:\Program Files\CPUID\CPU-Z\cpuz.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Integrity Level: MEDIUM Description: CPU-Z Application Exit code: 3221226540 Version: 1, 7, 9, 1 Modules
| |||||||||||||||
| 6408 | "C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe" | C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: CPUID CPU-Z Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6432 | "C:\Users\admin\AppData\Local\Temp\is-3RFFE.tmp\cpu-z_1.79-en.tmp" /SL5="$40284,1452756,57856,C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe" | C:\Users\admin\AppData\Local\Temp\is-3RFFE.tmp\cpu-z_1.79-en.tmp | — | cpu-z_1.79-en.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 6532 | "C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe" /SPAWNWND=$302F0 /NOTIFYWND=$40284 | C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe | cpu-z_1.79-en.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: CPUID CPU-Z Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6580 | "C:\Users\admin\AppData\Local\Temp\is-45GVL.tmp\cpu-z_1.79-en.tmp" /SL5="$40306,1452756,57856,C:\Users\admin\AppData\Local\Temp\cpu-z_1.79-en.exe" /SPAWNWND=$302F0 /NOTIFYWND=$40284 | C:\Users\admin\AppData\Local\Temp\is-45GVL.tmp\cpu-z_1.79-en.tmp | cpu-z_1.79-en.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 6836 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Program Files\CPUID\CPU-Z\cpuz_readme.txt | C:\Windows\SysWOW64\notepad.exe | — | cpu-z_1.79-en.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 882
Read events
6 832
Write events
44
Delete events
6
Modification events
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: B419000048D03FA611F2DA01 | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: DD5189EBDE106A497160DDFB9F48918A04208F35CAA55FB1FD8363A80F180E13 | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\CPUID\CPU-Z\cpuz.exe | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: A70C604835B6B44306C74BB8F81B926D41D7BCE94F22EB0EDF59DFA9F02D3D56 | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CPUID\CPU-Z |
| Operation: | write | Name: | PATH |
Value: C:\Program Files\CPUID\CPU-Z | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CPUID\CPU-Z |
| Operation: | write | Name: | PRODUCT_NAME |
Value: CPUID CPU-Z | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CPUID\CPU-Z |
| Operation: | write | Name: | VERSION |
Value: 1.79.1 | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CPUID CPU-Z_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.9 (a) | |||
| (PID) Process: | (6580) cpu-z_1.79-en.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CPUID CPU-Z_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\CPUID\CPU-Z | |||
Executable files
8
Suspicious files
8
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6580 | cpu-z_1.79-en.tmp | C:\Program Files\CPUID\CPU-Z\unins000.exe | executable | |
MD5:524915B3F0BE32A55CF793F2846E6F8A | SHA256:1BB1BA50AEF2FDDCA4E9D831053E92359D25AD7437062DF5AFD220B91336E9F8 | |||
| 6408 | cpu-z_1.79-en.exe | C:\Users\admin\AppData\Local\Temp\is-3RFFE.tmp\cpu-z_1.79-en.tmp | executable | |
MD5:832DAB307E54AA08F4B6CDD9B9720361 | SHA256:CC783A04CCBCA4EDD06564F8EC88FE5A15F1E3BB26CEC7DE5E090313520D98F3 | |||
| 6580 | cpu-z_1.79-en.tmp | C:\Program Files\CPUID\CPU-Z\cpuz_eula.txt | text | |
MD5:DB9D65B0431BD586B9A5ED242A1A34BA | SHA256:81C9EA933B99826869079BE726FD2A0CE3A0BAFC30ED5CBDC57BADDD1DD118EB | |||
| 6580 | cpu-z_1.79-en.tmp | C:\Program Files\CPUID\CPU-Z\is-3AG7F.tmp | text | |
MD5:DB9D65B0431BD586B9A5ED242A1A34BA | SHA256:81C9EA933B99826869079BE726FD2A0CE3A0BAFC30ED5CBDC57BADDD1DD118EB | |||
| 6580 | cpu-z_1.79-en.tmp | C:\Users\admin\AppData\Local\Temp\is-HO9B3.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6580 | cpu-z_1.79-en.tmp | C:\Program Files\CPUID\CPU-Z\unins000.dat | binary | |
MD5:AFCEF446200573E87D691379022A5B2A | SHA256:72C6EF0FDF75C80D7C5732C4999EE0E21FB4EA102FAE40AB22799763E9DD2D70 | |||
| 1128 | cpuz.exe | C:\Users\admin\AppData\Local\Temp\cpuz_driver_1128.log | text | |
MD5:75AACBE3A6686DD19F729D39B97E899D | SHA256:138E2AFBE32EA57B7F2BF1753B97DA5316A96C598CF024171B3AFF46ABEABC85 | |||
| 6580 | cpu-z_1.79-en.tmp | C:\Program Files\CPUID\CPU-Z\is-VP5TJ.tmp | executable | |
MD5:85F281763127DF02D60B42AE353884D8 | SHA256:93CBEDB18D39A9F69CA9E8656994F0BA99FFBD2FD4ABD0A20AE817E52B9496BE | |||
| 6580 | cpu-z_1.79-en.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CPUID\CPU-Z\CPU-Z.lnk | binary | |
MD5:737B9CF120E438BE7DDB6E3B7B22CF41 | SHA256:08399781C18BED2EDDCDE4F255CEEFFC7E2E61C68C2B71925E5362FB41611B2A | |||
| 6580 | cpu-z_1.79-en.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CPUID\CPU-Z\Uninstall CPU-Z.lnk | binary | |
MD5:50921C20C530A67789DD8357A22E375A | SHA256:7687F82259AA6637F60047D80B098B2BEECA1C8902F8905B01A23414BA066327 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6904 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6480 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1128 | cpuz.exe | GET | 301 | 195.154.81.43:80 | http://download.cpuid.com/cpuid.ver | unknown | — | — | whitelisted |
1128 | cpuz.exe | GET | 200 | 184.24.77.65:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgSTi%2FCGxZ2Esn2oh5KTXh7Xlg%3D%3D | unknown | — | — | whitelisted |
1948 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4060 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1292 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1948 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1948 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
download.cpuid.com |
| whitelisted |
r11.o.lencr.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |