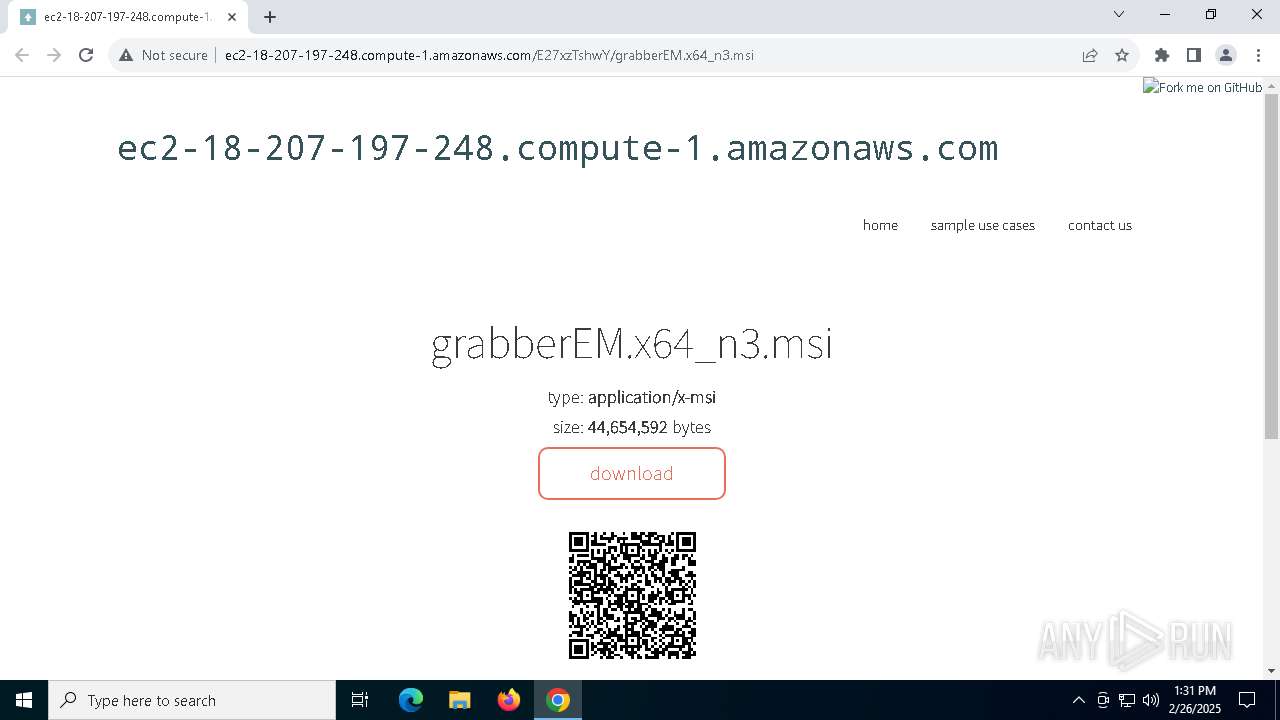
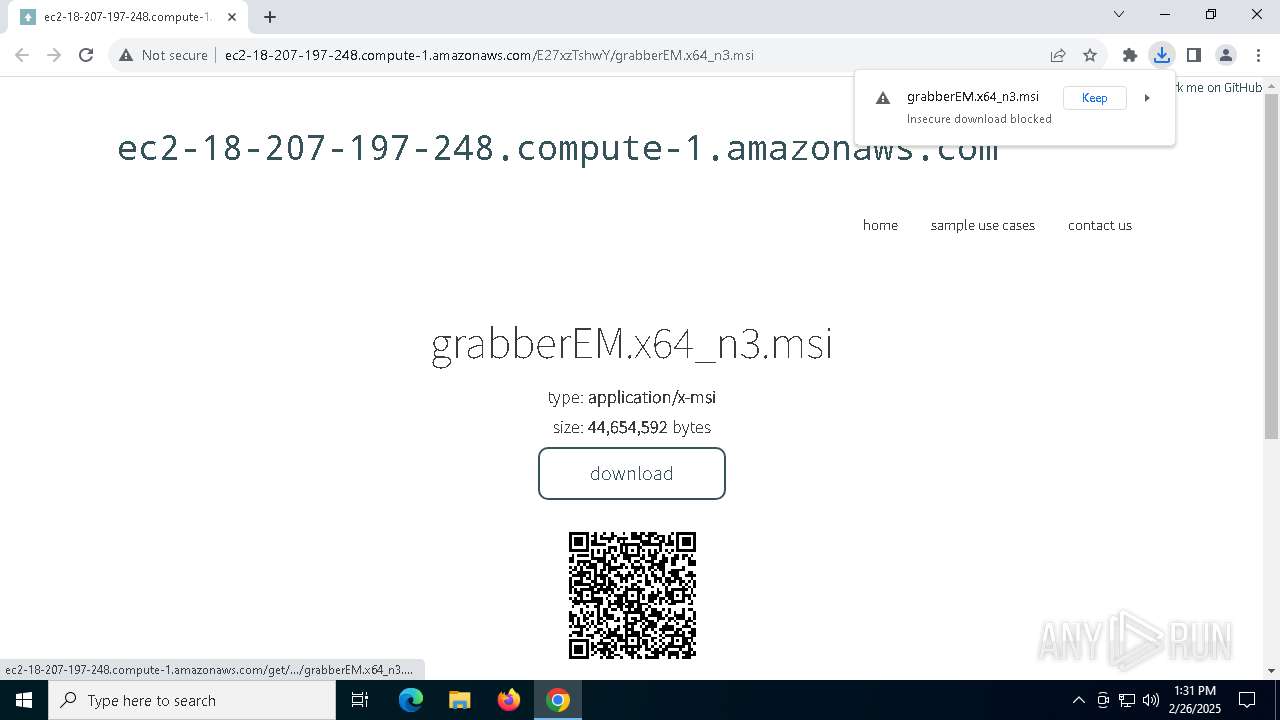
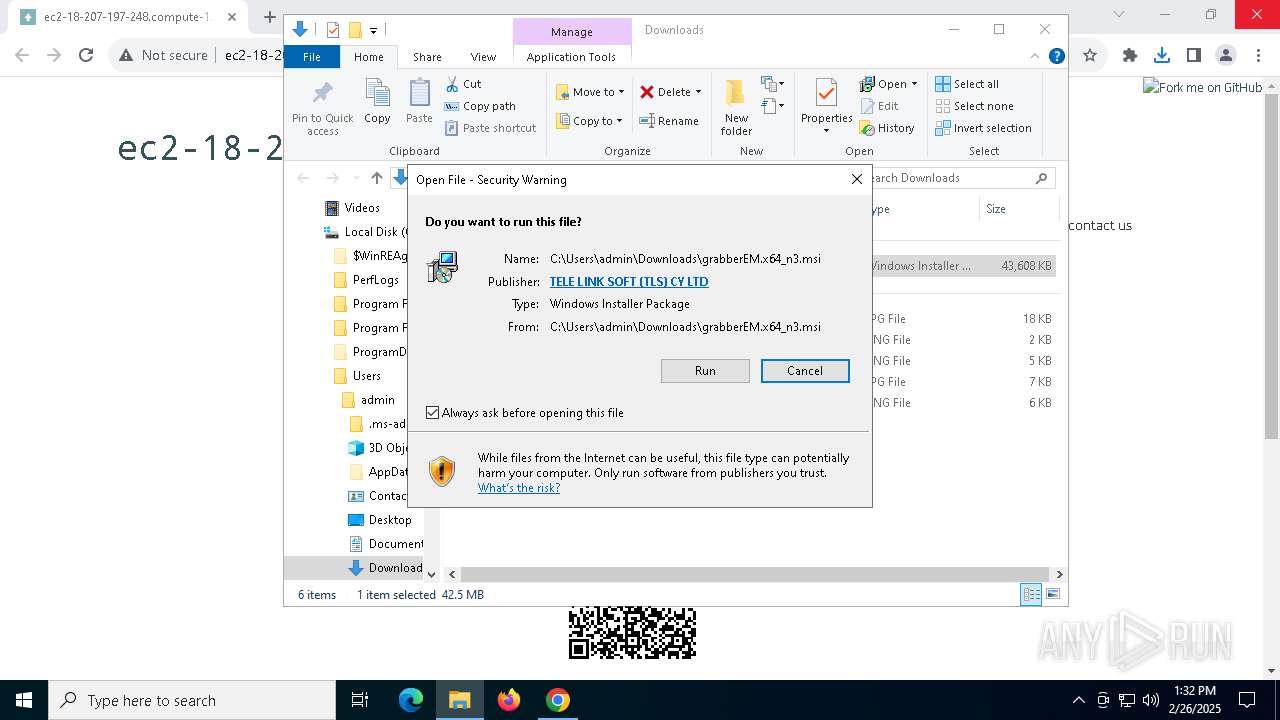
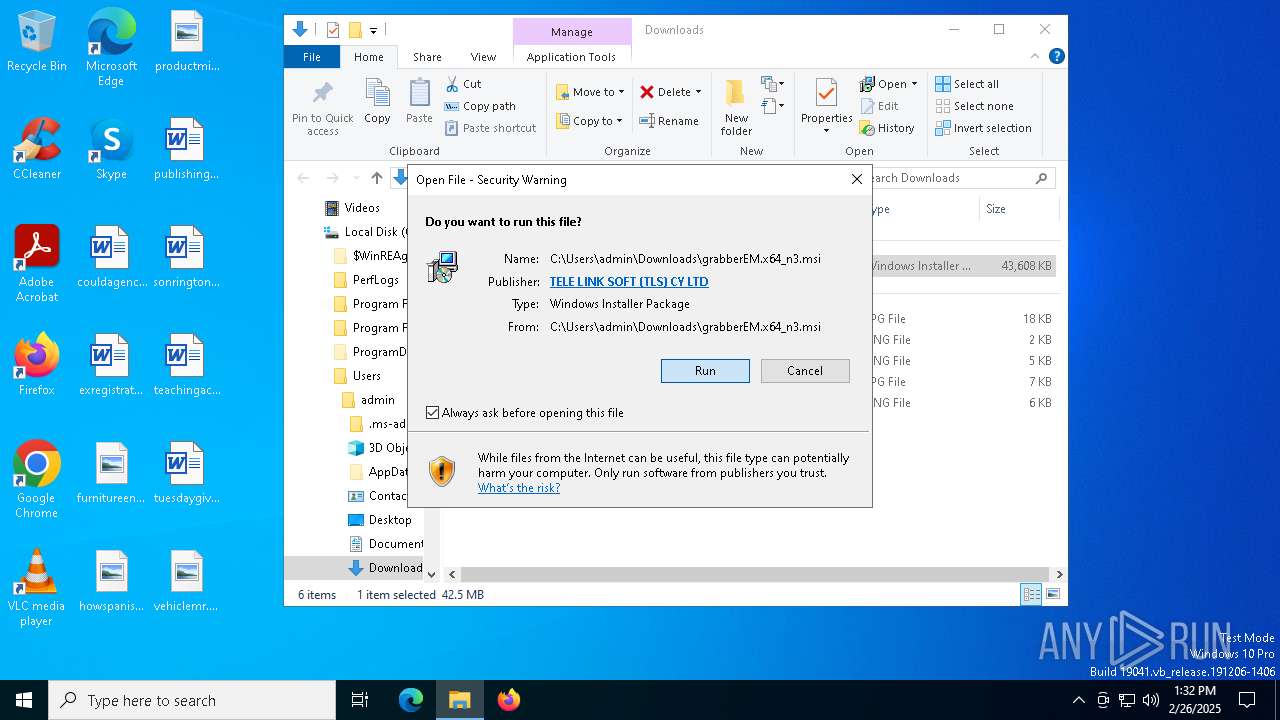
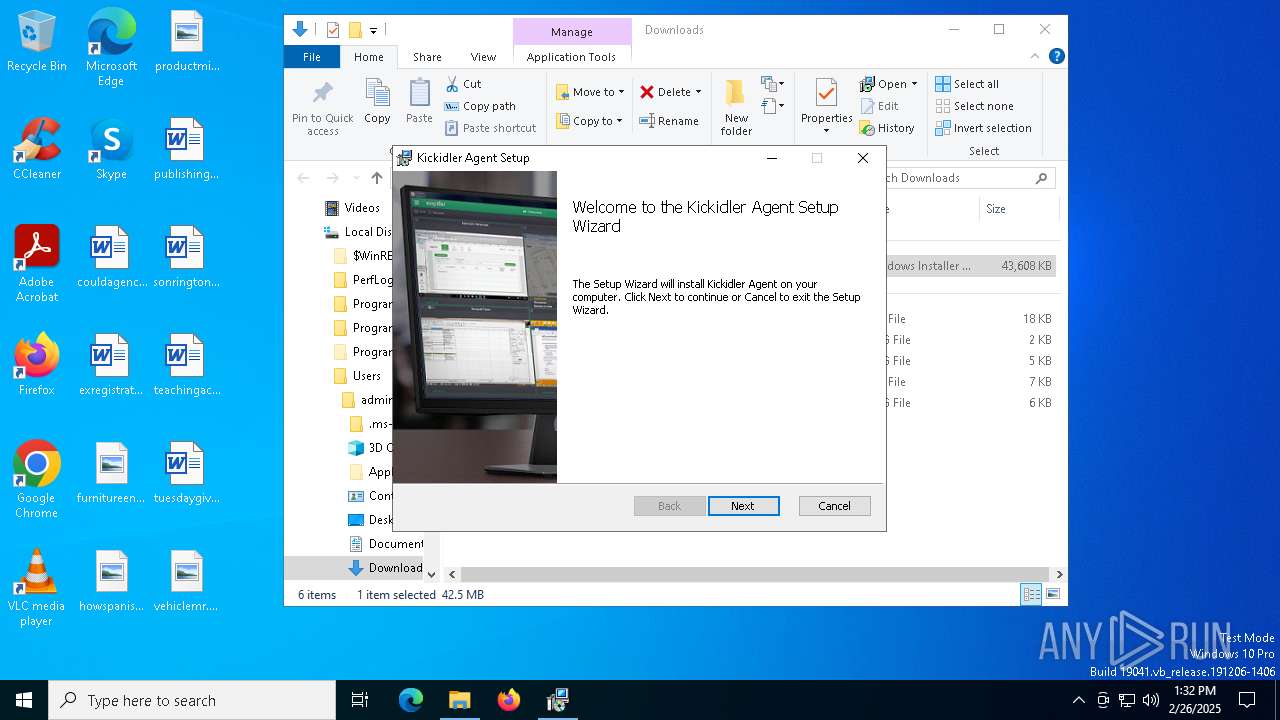
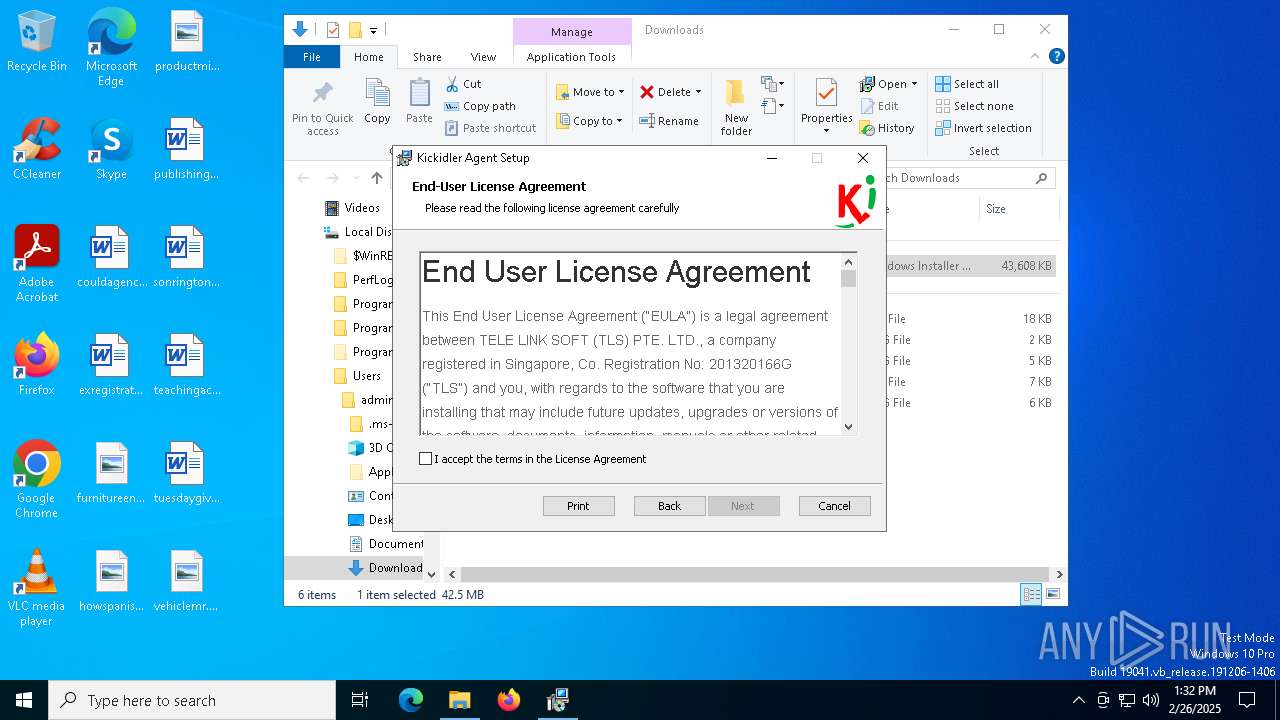
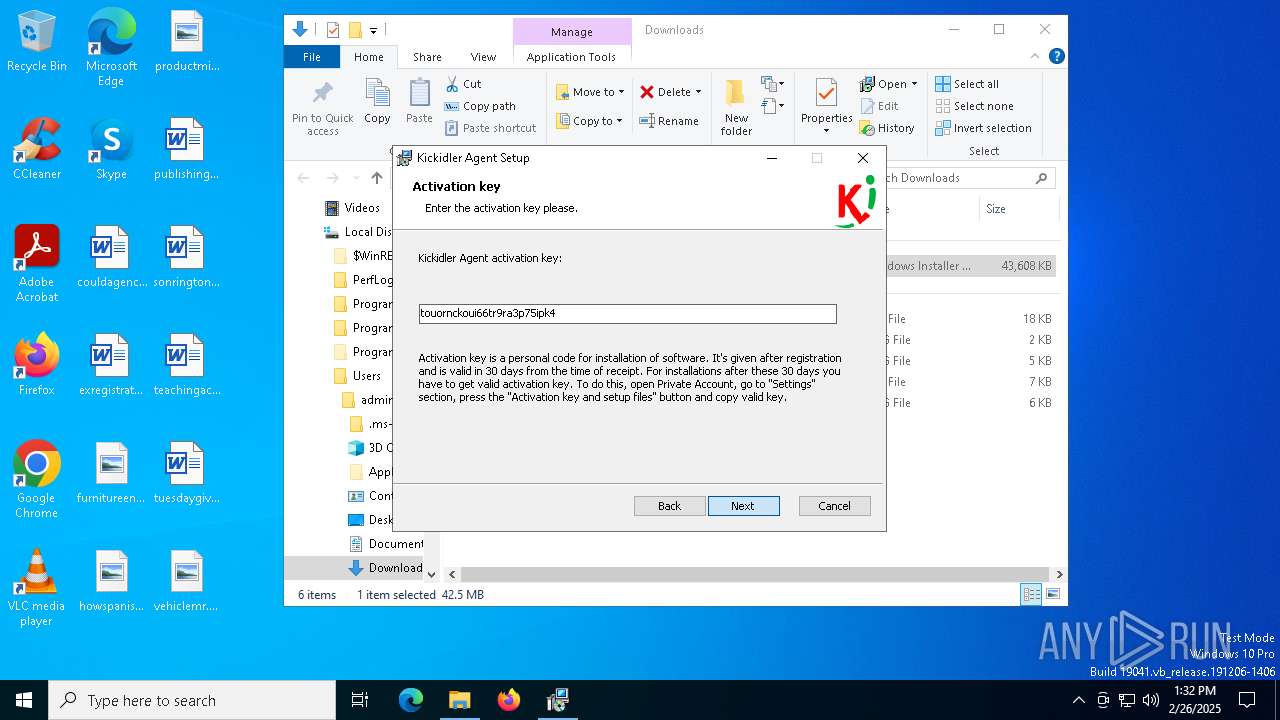
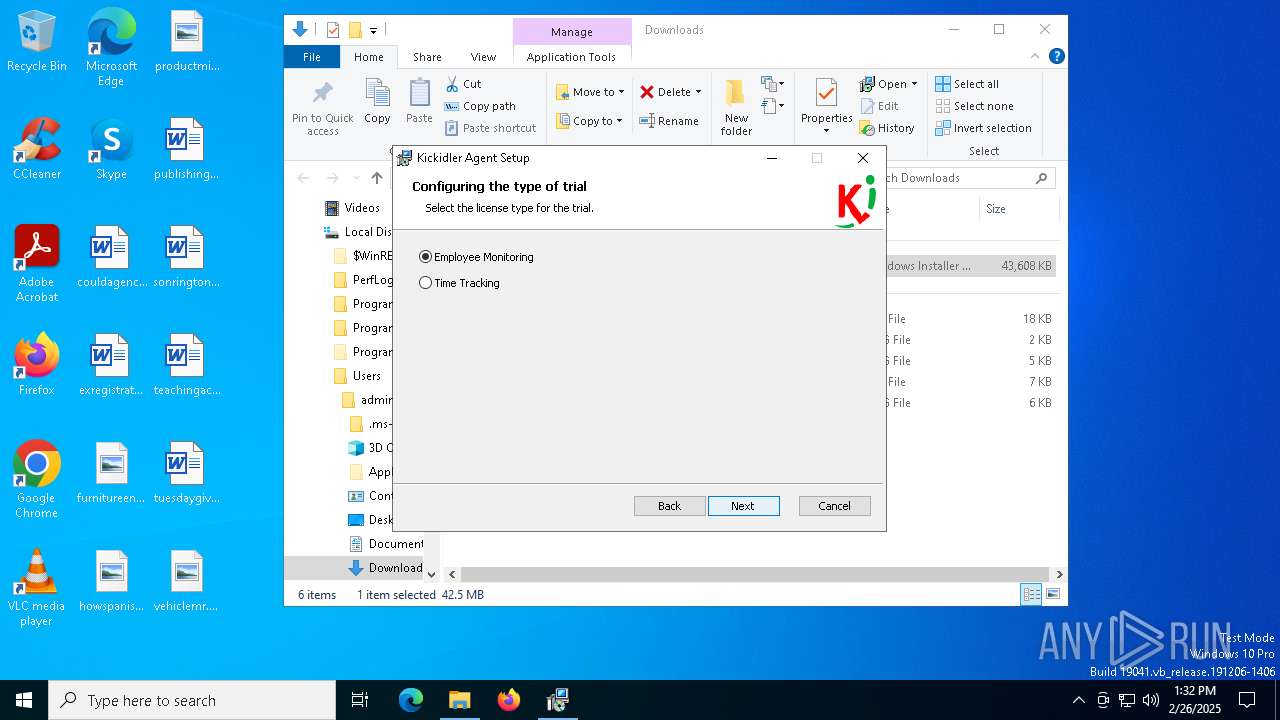
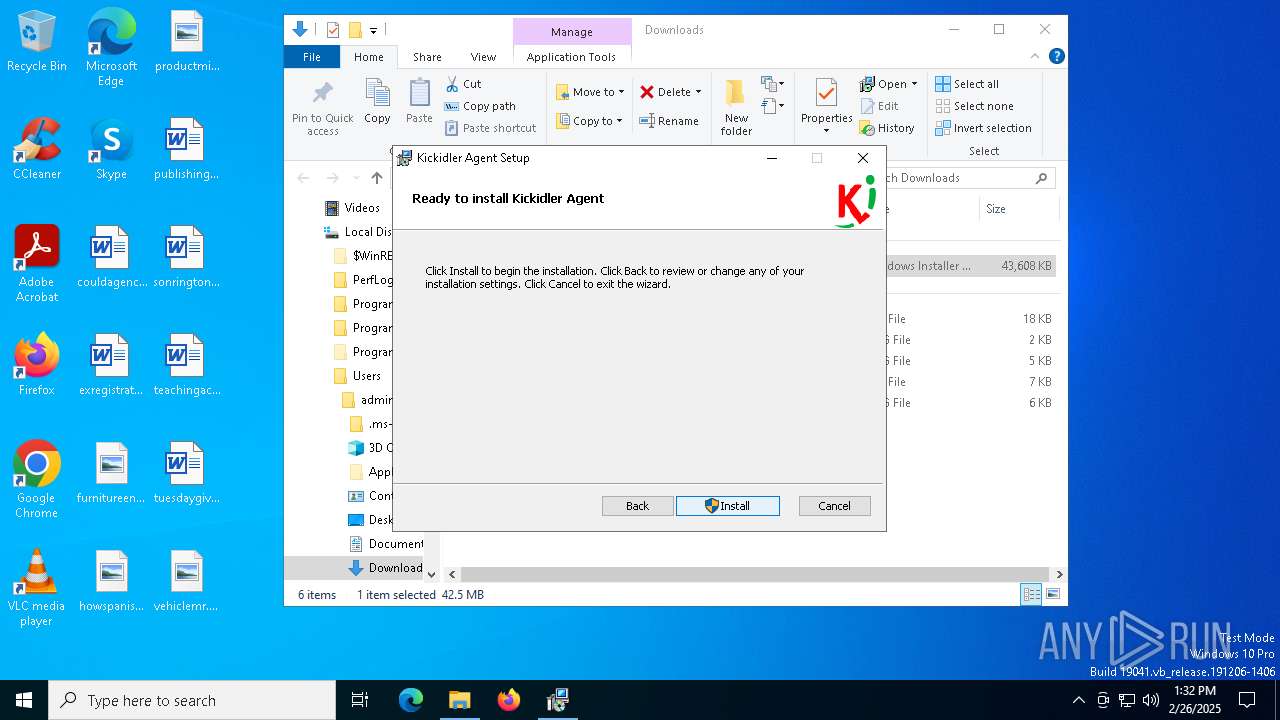
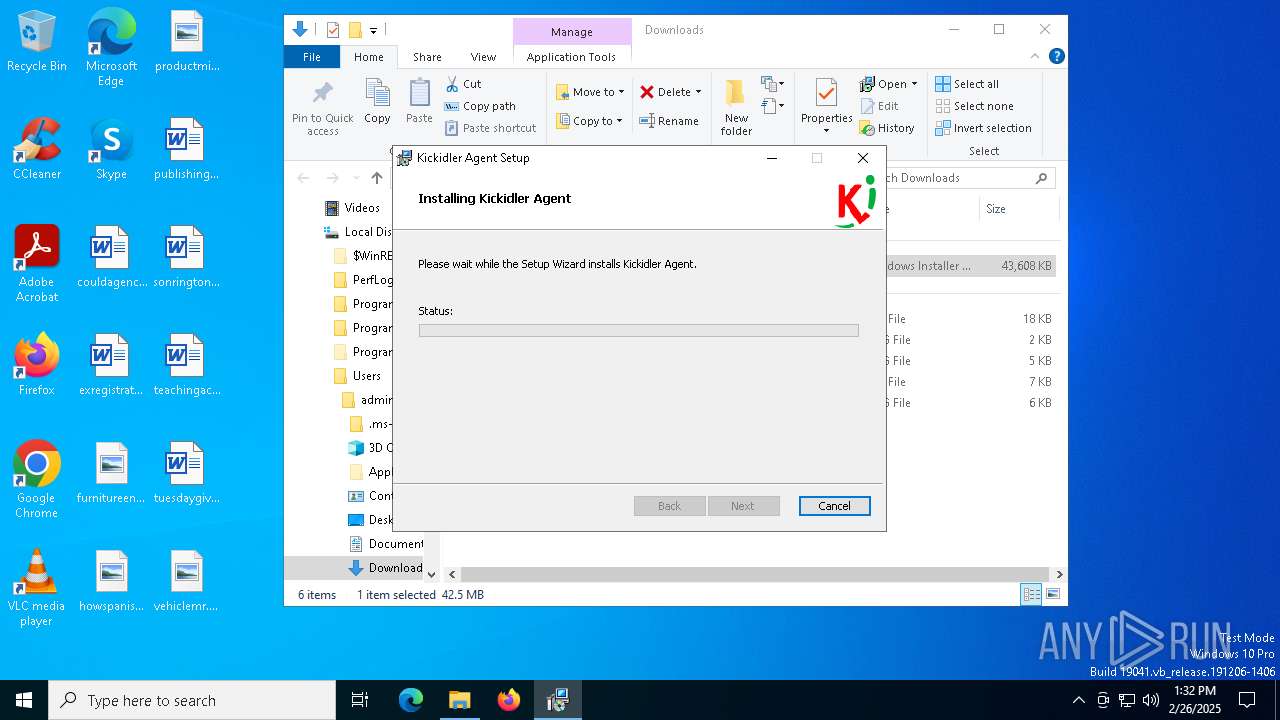
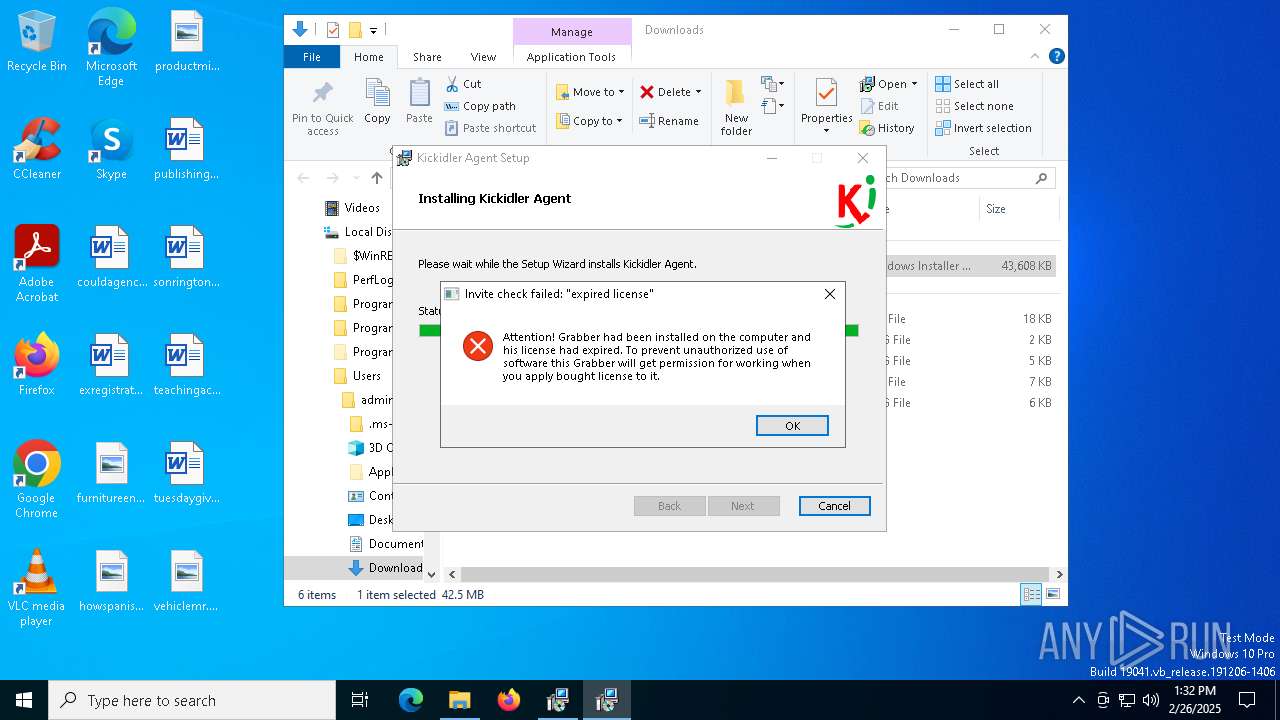
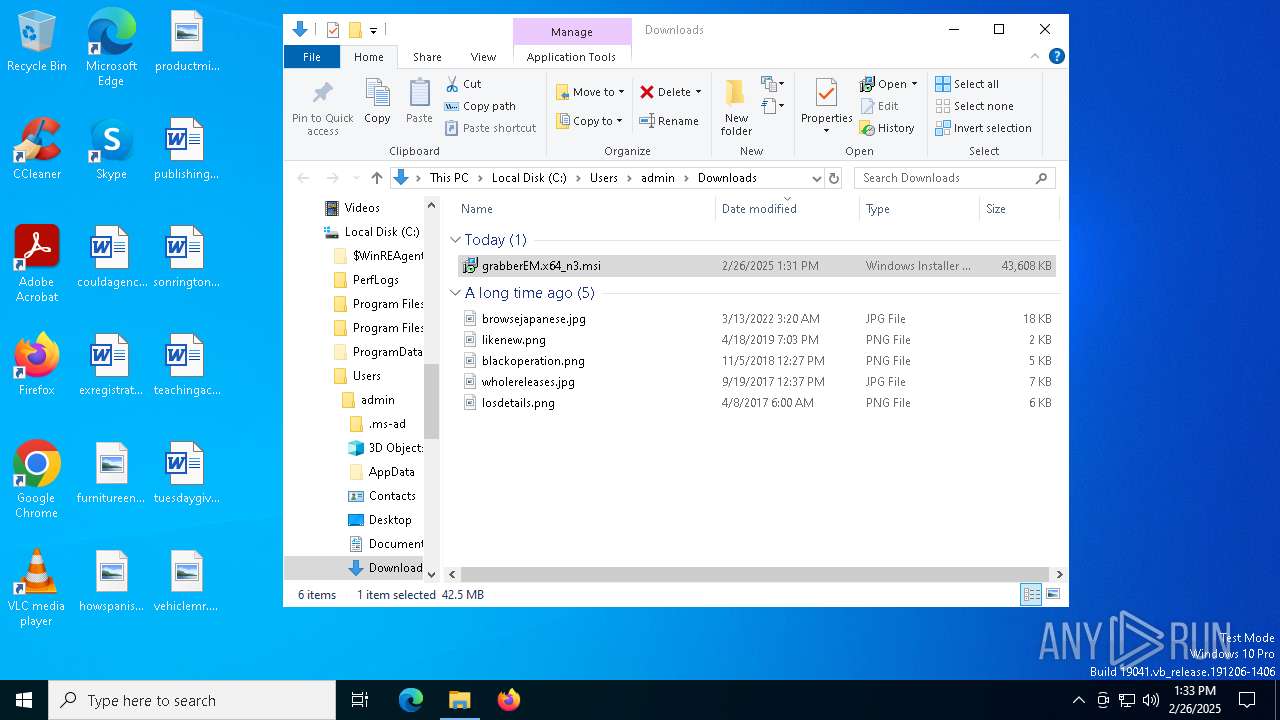
| URL: | http://ec2-18-207-197-248.compute-1.amazonaws.com/E27xzTshwY/grabberEM.x64_n3.msi |
| Full analysis: | https://app.any.run/tasks/08b93e61-f41a-495e-b534-494d8210c465 |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2025, 13:31:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | AE88E14E846A2264EF09EC85D16692EE |
| SHA1: | 35589C6F660CAB07608B8CDE4F72C45D741D0D2D |
| SHA256: | 1709E97B2F63614C2BAAC6A122BB7E899576375F1E6D7E74E78EFDF42F808EF1 |
| SSDEEP: | 3:N1KbmUSp0XR4rpmfQ7WtLZK7TR6orM:ClSpuBfQS2R4 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 5492)
Checks Windows Trust Settings
- msiexec.exe (PID: 5972)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 1088)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5972)
Process drops legitimate windows executable
- msiexec.exe (PID: 5972)
The process drops C-runtime libraries
- msiexec.exe (PID: 5972)
Reads the date of Windows installation
- msiexec.exe (PID: 1088)
Hides command output
- PING.EXE (PID: 7152)
- PING.EXE (PID: 7892)
- PING.EXE (PID: 4528)
- PING.EXE (PID: 7948)
- PING.EXE (PID: 7864)
- PING.EXE (PID: 6032)
- PING.EXE (PID: 7776)
- PING.EXE (PID: 7988)
- PING.EXE (PID: 7536)
- PING.EXE (PID: 7504)
- PING.EXE (PID: 7440)
- PING.EXE (PID: 8176)
- PING.EXE (PID: 2192)
- PING.EXE (PID: 4164)
- PING.EXE (PID: 5056)
- PING.EXE (PID: 6036)
- PING.EXE (PID: 6268)
- PING.EXE (PID: 976)
- PING.EXE (PID: 7700)
- PING.EXE (PID: 7172)
- PING.EXE (PID: 7852)
- PING.EXE (PID: 7956)
- PING.EXE (PID: 7696)
- PING.EXE (PID: 7560)
- PING.EXE (PID: 2084)
- PING.EXE (PID: 8184)
- PING.EXE (PID: 7576)
- PING.EXE (PID: 4844)
- PING.EXE (PID: 4688)
- PING.EXE (PID: 4180)
- PING.EXE (PID: 812)
- PING.EXE (PID: 7232)
- PING.EXE (PID: 7292)
- PING.EXE (PID: 1132)
- PING.EXE (PID: 3364)
- PING.EXE (PID: 6668)
- PING.EXE (PID: 5600)
- PING.EXE (PID: 7264)
- PING.EXE (PID: 7944)
- PING.EXE (PID: 7588)
- PING.EXE (PID: 7984)
- PING.EXE (PID: 7848)
- PING.EXE (PID: 6372)
- PING.EXE (PID: 8044)
- PING.EXE (PID: 7808)
- PING.EXE (PID: 4172)
- PING.EXE (PID: 1276)
- PING.EXE (PID: 780)
- PING.EXE (PID: 7144)
- PING.EXE (PID: 5136)
- PING.EXE (PID: 7208)
- PING.EXE (PID: 7640)
- PING.EXE (PID: 7444)
- PING.EXE (PID: 1300)
- PING.EXE (PID: 7908)
- PING.EXE (PID: 7800)
- PING.EXE (PID: 7676)
- PING.EXE (PID: 4756)
- PING.EXE (PID: 5544)
- PING.EXE (PID: 7624)
- PING.EXE (PID: 3968)
- PING.EXE (PID: 2236)
- PING.EXE (PID: 2416)
- PING.EXE (PID: 7940)
- PING.EXE (PID: 2516)
- PING.EXE (PID: 7992)
- PING.EXE (PID: 7976)
- PING.EXE (PID: 7472)
- PING.EXE (PID: 5304)
- PING.EXE (PID: 896)
- PING.EXE (PID: 7740)
- PING.EXE (PID: 7820)
- PING.EXE (PID: 7716)
- PING.EXE (PID: 7212)
- PING.EXE (PID: 8028)
- PING.EXE (PID: 7784)
- PING.EXE (PID: 5256)
- PING.EXE (PID: 1600)
- PING.EXE (PID: 7984)
- PING.EXE (PID: 5956)
- PING.EXE (PID: 8064)
- PING.EXE (PID: 6964)
- PING.EXE (PID: 7436)
- PING.EXE (PID: 1244)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1088)
Runs PING.EXE to delay simulation
- msiexec.exe (PID: 1088)
Connects to unusual port
- grabber.exe (PID: 8052)
- grabber.exe (PID: 7912)
- grabber.exe (PID: 1012)
Reads data from a binary Stream object (SCRIPT)
- msiexec.exe (PID: 1088)
Windows service management via SC.EXE
- sc.exe (PID: 5172)
Starts SC.EXE for service management
- msiexec.exe (PID: 1088)
Executes as Windows Service
- grabber.exe (PID: 1012)
INFO
Application launched itself
- chrome.exe (PID: 7400)
- msiexec.exe (PID: 5972)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- msiexec.exe (PID: 7520)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
Reads Environment values
- msiexec.exe (PID: 4880)
- msiexec.exe (PID: 1088)
Checks proxy server information
- explorer.exe (PID: 5492)
- slui.exe (PID: 2560)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Checks supported languages
- msiexec.exe (PID: 4880)
- msiexec.exe (PID: 5548)
- msiexec.exe (PID: 5972)
- msiexec.exe (PID: 6192)
- msiexec.exe (PID: 3900)
- msiexec.exe (PID: 6584)
- grabber.exe (PID: 8052)
- msiexec.exe (PID: 1088)
- grabber.exe (PID: 7912)
- grabber.exe (PID: 5280)
- grabber.exe (PID: 1012)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7520)
- msiexec.exe (PID: 5972)
Reads the computer name
- msiexec.exe (PID: 4880)
- msiexec.exe (PID: 5548)
- msiexec.exe (PID: 3900)
- msiexec.exe (PID: 6192)
- msiexec.exe (PID: 6584)
- msiexec.exe (PID: 1088)
- grabber.exe (PID: 8052)
- grabber.exe (PID: 7912)
- grabber.exe (PID: 5280)
- grabber.exe (PID: 1012)
- msiexec.exe (PID: 5972)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5972)
- grabber.exe (PID: 8052)
- grabber.exe (PID: 7912)
Reads the software policy settings
- msiexec.exe (PID: 7520)
- explorer.exe (PID: 5492)
- msiexec.exe (PID: 5972)
- grabber.exe (PID: 8052)
- grabber.exe (PID: 7912)
- slui.exe (PID: 8088)
- grabber.exe (PID: 1012)
The sample compiled with english language support
- msiexec.exe (PID: 5972)
Creates a software uninstall entry
- msiexec.exe (PID: 5972)
Creates files in the program directory
- grabber.exe (PID: 8052)
- grabber.exe (PID: 1012)
Process checks computer location settings
- msiexec.exe (PID: 1088)
- grabber.exe (PID: 7912)
Reads the time zone
- grabber.exe (PID: 7912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
334
Monitored processes
198
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PING.EXE | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\Windows\System32\PING.EXE" -n 2 127.0.0.1>nul | C:\Windows\System32\PING.EXE | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Windows\System32\PING.EXE" -n 2 127.0.0.1>nul | C:\Windows\System32\PING.EXE | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\Windows\System32\PING.EXE" -n 2 127.0.0.1>nul | C:\Windows\System32\PING.EXE | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | "C:\Windows\System32\PING.EXE" -n 2 127.0.0.1>nul | C:\Windows\System32\PING.EXE | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
69 035
Read events
68 506
Write events
502
Delete events
27
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000030240 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (7400) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7400) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7400) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7400) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7400) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (3240) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000C0A4B6CD5288DB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
Executable files
100
Suspicious files
373
Text files
247
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c6bd.TMP | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c6bd.TMP | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c6bd.TMP | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c6bd.TMP | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c6bd.TMP | — | |
MD5:— | SHA256:— | |||
| 7400 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
63
DNS requests
40
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/E27xzTshwY/grabberEM.x64_n3.msi | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/fonts/fonts.css?family=Source+Sans+Pro:100,200,300 | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/fonts/fonts.css?family=Droid+Sans+Mono | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/scripts/vendor/modernizr.js | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/styles/main.css | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/images/Logo-orange.png | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/scripts/main.js | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/fonts/source-sans-pro-300-normal-latin.woff2 | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/fonts/source-sans-pro-200-normal-latin.woff2 | unknown | — | — | shared |
7616 | chrome.exe | GET | 200 | 18.207.197.248:80 | http://ec2-18-207-197-248.compute-1.amazonaws.com/fonts/transfersh.woff | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7400 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7616 | chrome.exe | 18.207.197.248:80 | ec2-18-207-197-248.compute-1.amazonaws.com | AMAZON-AES | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ec2-18-207-197-248.compute-1.amazonaws.com |
| shared |
client.wns.windows.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
camo.githubusercontent.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |
7616 | chrome.exe | Misc activity | ET FILE_SHARING File Download from transfer .sh Service |