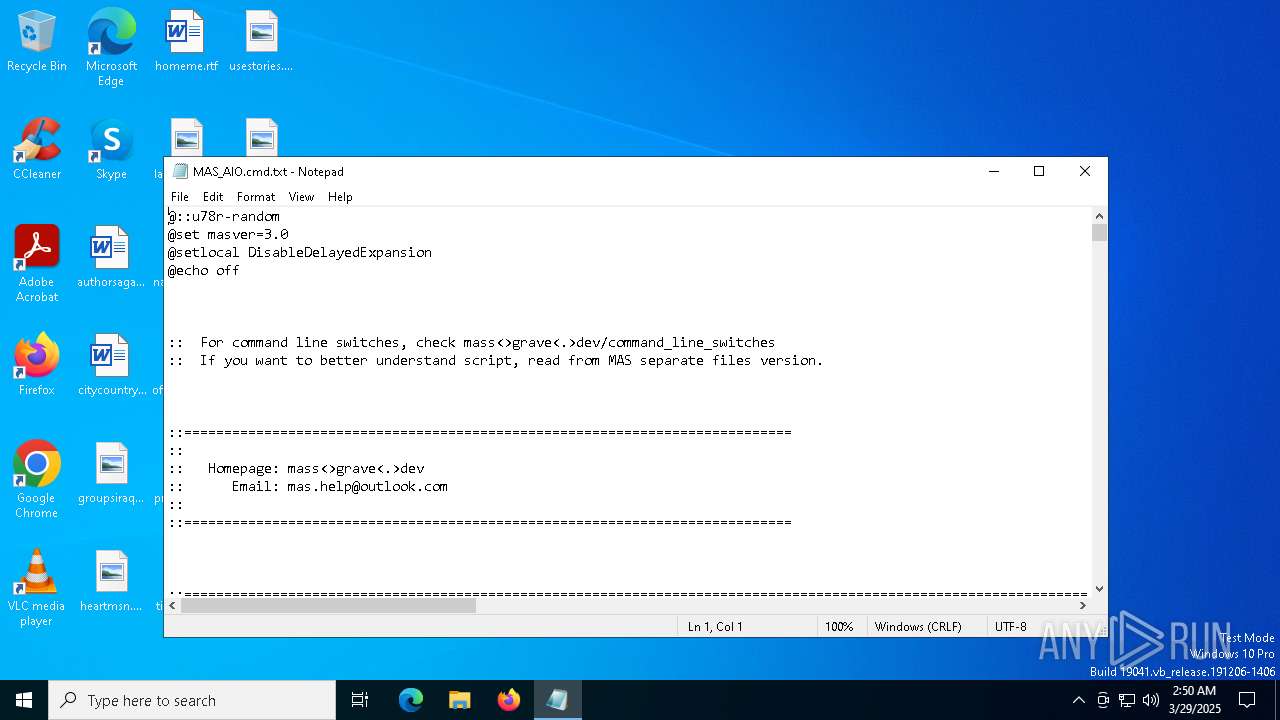
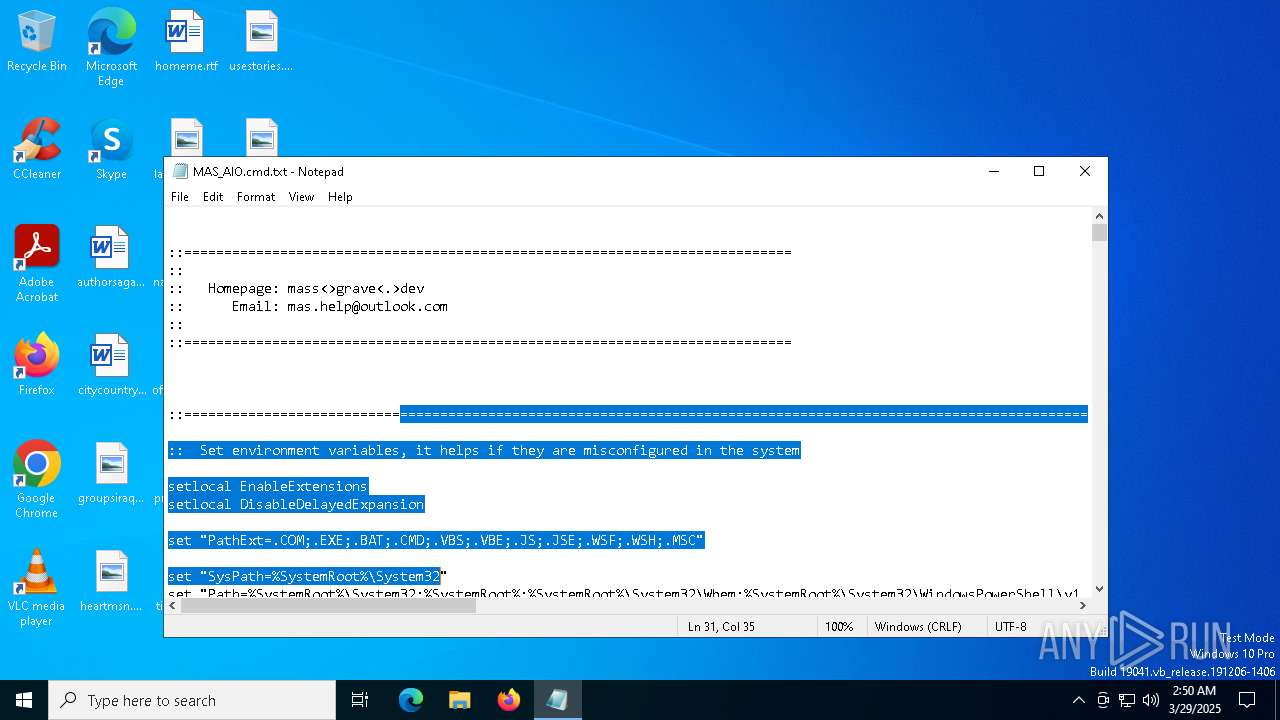
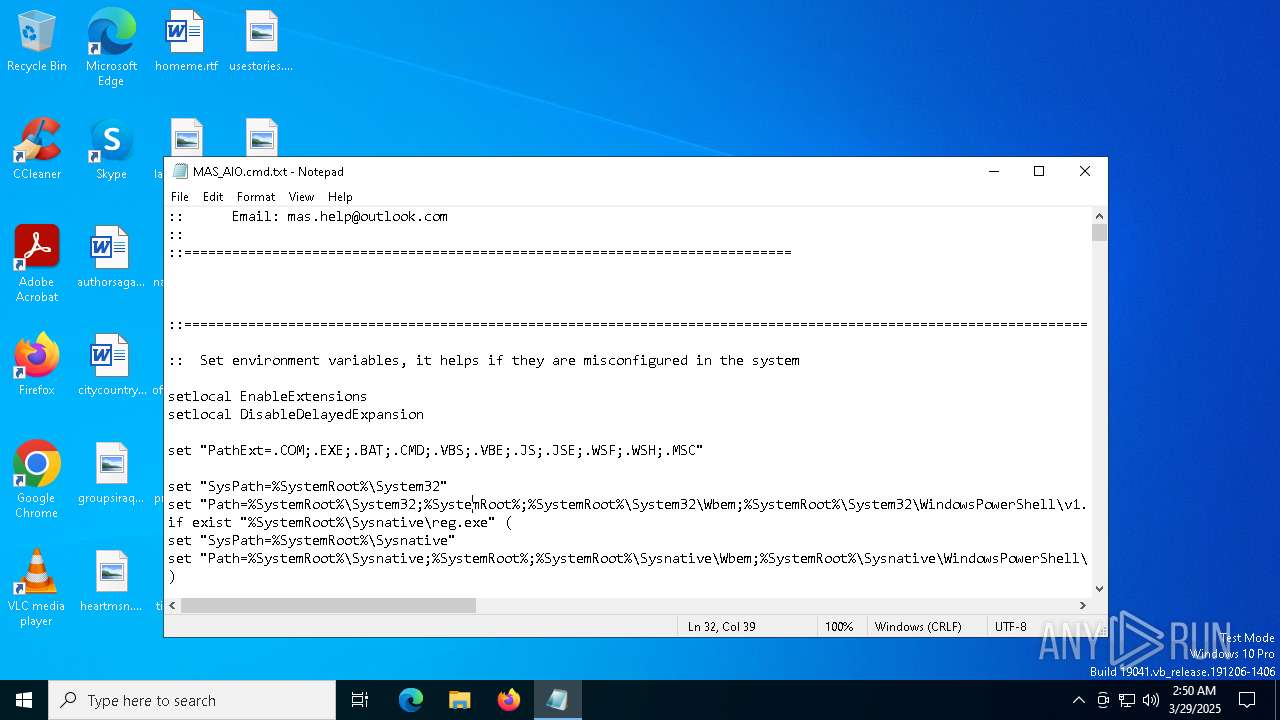
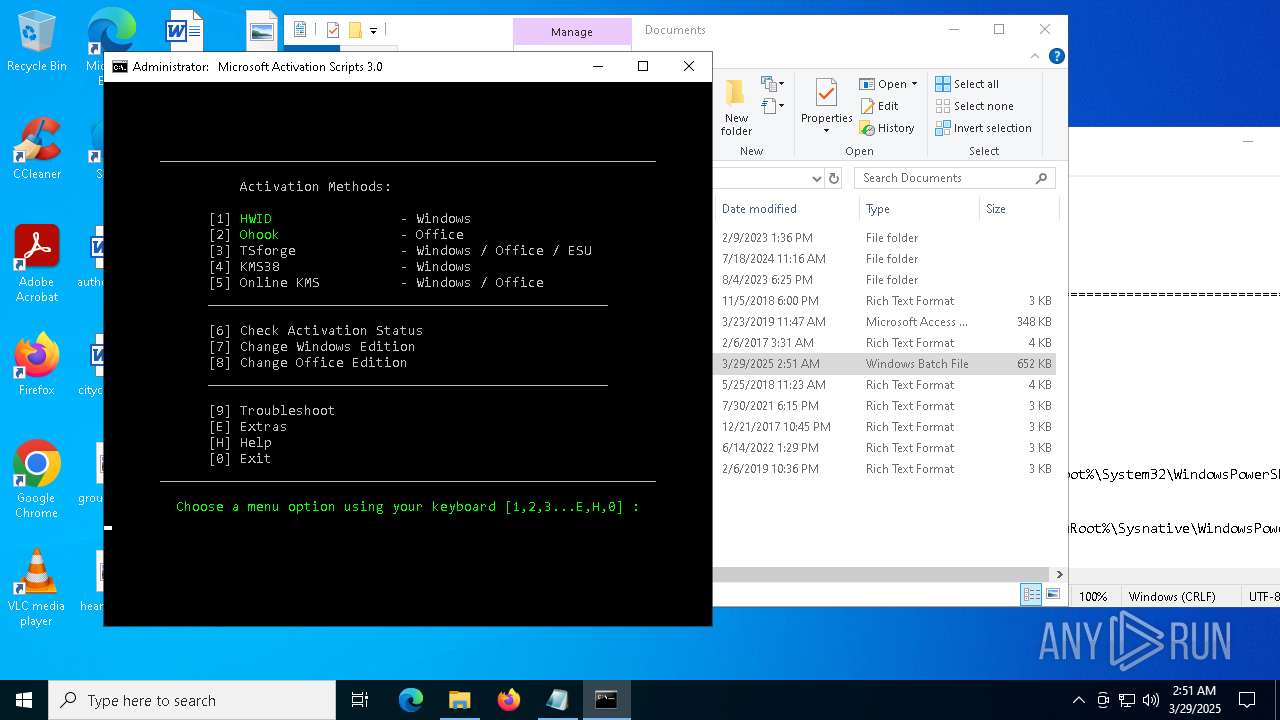
| File name: | MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/545689c2-3e2f-43c6-81f5-1330a84dd2ff |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2025, 02:50:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (348), with CRLF line terminators |
| MD5: | 5B9A3CF1F44FACE6C7BA60B2F729A2D3 |
| SHA1: | 253041DFB0D8F58E0A2D9480C69830CB0484B86E |
| SHA256: | 16F0FFCDD242A0D514B9D96AE1535F48A2E2811D45A8094E98BB0A26EA2FEBBA |
| SSDEEP: | 6144:5oIjH+imAc5g+9YCMD0a9g7nc/4IsK0ykpBwuI:5oIjHOAWYCMDF0c/psK0ykpBm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Windows service management via SC.EXE
- sc.exe (PID: 8164)
- sc.exe (PID: 7716)
- sc.exe (PID: 6388)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7456)
Starts SC.EXE for service management
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7456)
Application launched itself
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7828)
- cmd.exe (PID: 7456)
- cmd.exe (PID: 7500)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7828)
- powershell.exe (PID: 7740)
- cmd.exe (PID: 7456)
- cmd.exe (PID: 7500)
Executing commands from ".cmd" file
- cmd.exe (PID: 8100)
- powershell.exe (PID: 7740)
- cmd.exe (PID: 7456)
Executing commands from a ".bat" file
- cmd.exe (PID: 8100)
- powershell.exe (PID: 7740)
- cmd.exe (PID: 7456)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4300)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 7456)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4300)
- cmd.exe (PID: 8100)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 7456)
- cmd.exe (PID: 2152)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4300)
- cmd.exe (PID: 4408)
- cmd.exe (PID: 7456)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6476)
Hides command output
- cmd.exe (PID: 7052)
- cmd.exe (PID: 7548)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7548)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7456)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6944)
- BackgroundTransferHost.exe (PID: 5776)
- BackgroundTransferHost.exe (PID: 8008)
- BackgroundTransferHost.exe (PID: 5392)
- BackgroundTransferHost.exe (PID: 5376)
- BackgroundTransferHost.exe (PID: 7400)
- WMIC.exe (PID: 1628)
- WMIC.exe (PID: 7744)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5776)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5776)
Manual execution by a user
- cmd.exe (PID: 8100)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5776)
Checks operating system version
- cmd.exe (PID: 8100)
- cmd.exe (PID: 7456)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 5304)
- powershell.exe (PID: 4000)
- powershell.exe (PID: 4172)
Starts MODE.COM to configure console settings
- mode.com (PID: 8028)
- mode.com (PID: 8040)
Checks supported languages
- mode.com (PID: 8040)
- mode.com (PID: 8028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
219
Monitored processes
86
Malicious processes
3
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | ping -4 -n 1 activated.win | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | find /i "/" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-el -qedit" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | wmic path Win32_ComputerSystem get CreationClassName /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | choice /C:123456789EH0 /N | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | find /i "FullLanguage" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\System32\cmd.exe /c "powershell.exe $AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1); $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule(2, $False); $TypeBuilder = $ModuleBuilder.DefineType(0); [void]$TypeBuilder.DefinePInvokeMethod('SLGetWindowsInformationDWORD', 'slc.dll', 'Public, Static', 1, [int], @([String], [int].MakeByRefType()), 1, 3); $Sku = 0; [void]$TypeBuilder.CreateType()::SLGetWindowsInformationDWORD('Kernel-BrandingInfo', [ref]$Sku); $Sku" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | C:\WINDOWS\System32\cmd.exe /c ping -4 -n 1 activated.win | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | powershell.exe "$TB = [AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1).DefineDynamicModule(2, $False).DefineType(0); [void]$TB.DefinePInvokeMethod('GetConsoleWindow', 'kernel32.dll', 22, 1, [IntPtr], @(), 1, 3).SetImplementationFlags(128); [void]$TB.DefinePInvokeMethod('SendMessageW', 'user32.dll', 22, 1, [IntPtr], @([IntPtr], [UInt32], [IntPtr], [IntPtr]), 1, 3).SetImplementationFlags(128); $hIcon = $TB.CreateType(); $hWnd = $hIcon::GetConsoleWindow(); echo $($hIcon::SendMessageW($hWnd, 127, 0, 0) -ne [IntPtr]::Zero);" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
42 231
Read events
42 158
Write events
70
Delete events
3
Modification events
| (PID) Process: | (8008) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8008) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8008) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5776) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5776) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5776) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6944) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6944) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6944) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6944) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
Executable files
0
Suspicious files
6
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5776 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\036d83ef-e731-46de-9273-a465643ddae9.down_data | — | |
MD5:— | SHA256:— | |||
| 7740 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4ltlgzwk.ir3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cazpdgzu.prz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6944 | notepad.exe | C:\Users\admin\Documents\MAS_AIO.cmd.bat | text | |
MD5:5B9A3CF1F44FACE6C7BA60B2F729A2D3 | SHA256:16F0FFCDD242A0D514B9D96AE1535F48A2E2811D45A8094E98BB0A26EA2FEBBA | |||
| 5776 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\5cfbfc24-81f2-43f2-b41a-ebbd43509d4a.up_meta_secure | binary | |
MD5:29BAB119B91C5AC56E1A2C61E4C7FB85 | SHA256:D0057DBF8F9D5364445AA11C92337854DC228ACDCB7F3FD6CB05CE5C73F54799 | |||
| 5304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_moqtjpoq.q3w.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5776 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4A53E41FCD6E6B79D6020C4864FBF864 | SHA256:33B10A6E4980B101741EF005965EAFD852298EE591230B4E326B6FD20B6D63D0 | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0bvvy2at.4gd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5776 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\5cfbfc24-81f2-43f2-b41a-ebbd43509d4a.9793816a-e906-4ba8-9940-5b1fc4378b34.down_meta | binary | |
MD5:ACD8A118DCF5B41FE77E545BB65C16F3 | SHA256:C7D3BD83A2B713B998E85EADDF41EF10A69648EFFF560062DE9ABDE25704574B | |||
| 5776 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\036d83ef-e731-46de-9273-a465643ddae9.9793816a-e906-4ba8-9940-5b1fc4378b34.down_meta | binary | |
MD5:ACD8A118DCF5B41FE77E545BB65C16F3 | SHA256:C7D3BD83A2B713B998E85EADDF41EF10A69648EFFF560062DE9ABDE25704574B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
24
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7348 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5776 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.172.255.217:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7348 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7348 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5776 | BackgroundTransferHost.exe | 2.16.241.201:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5776 | BackgroundTransferHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |