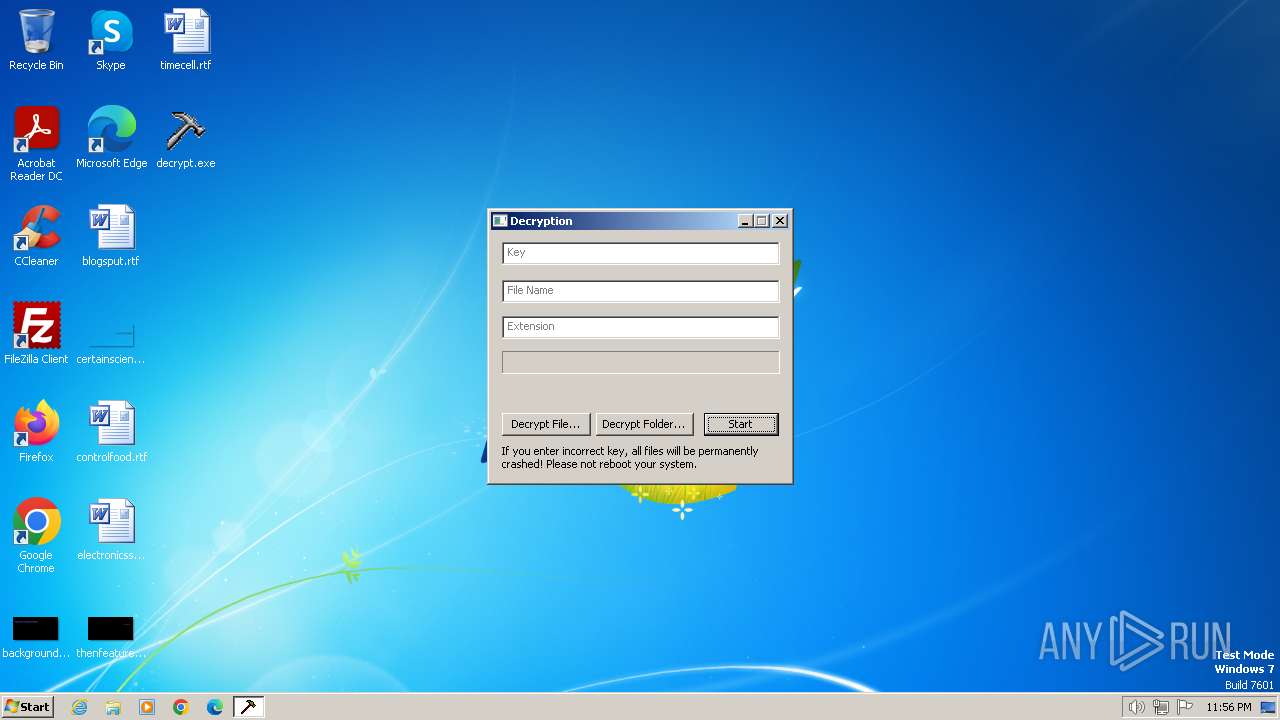
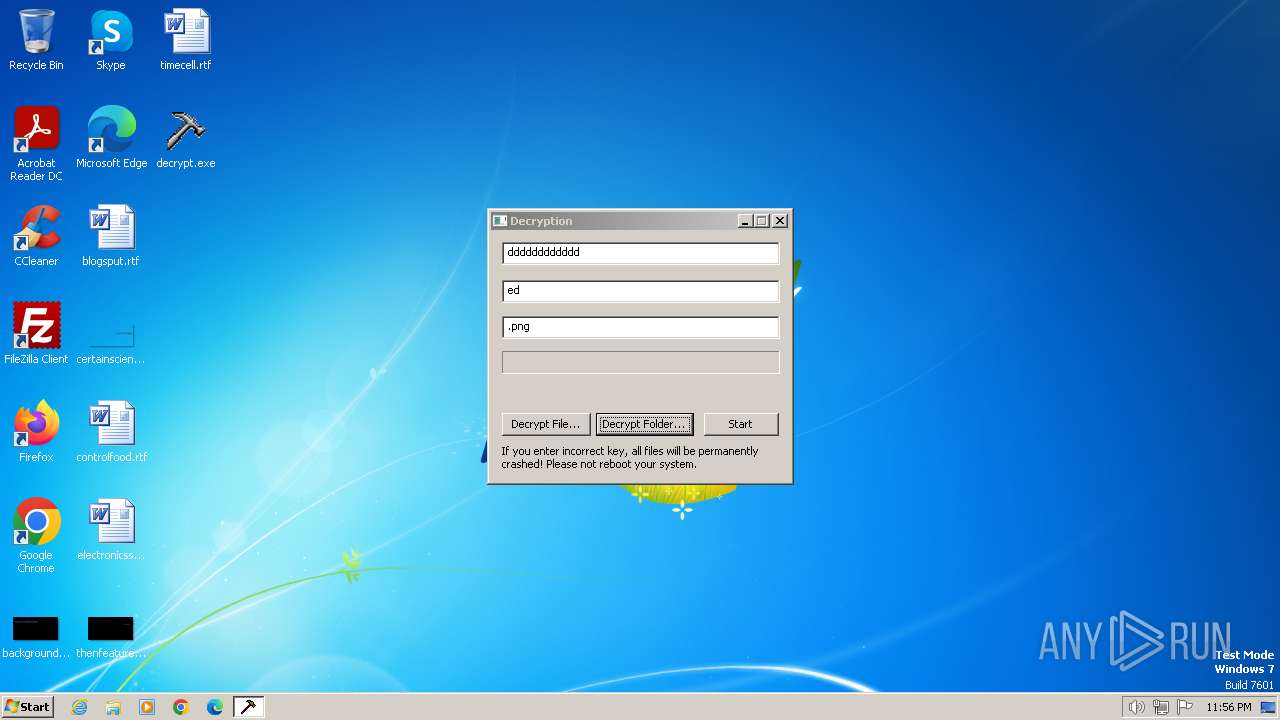
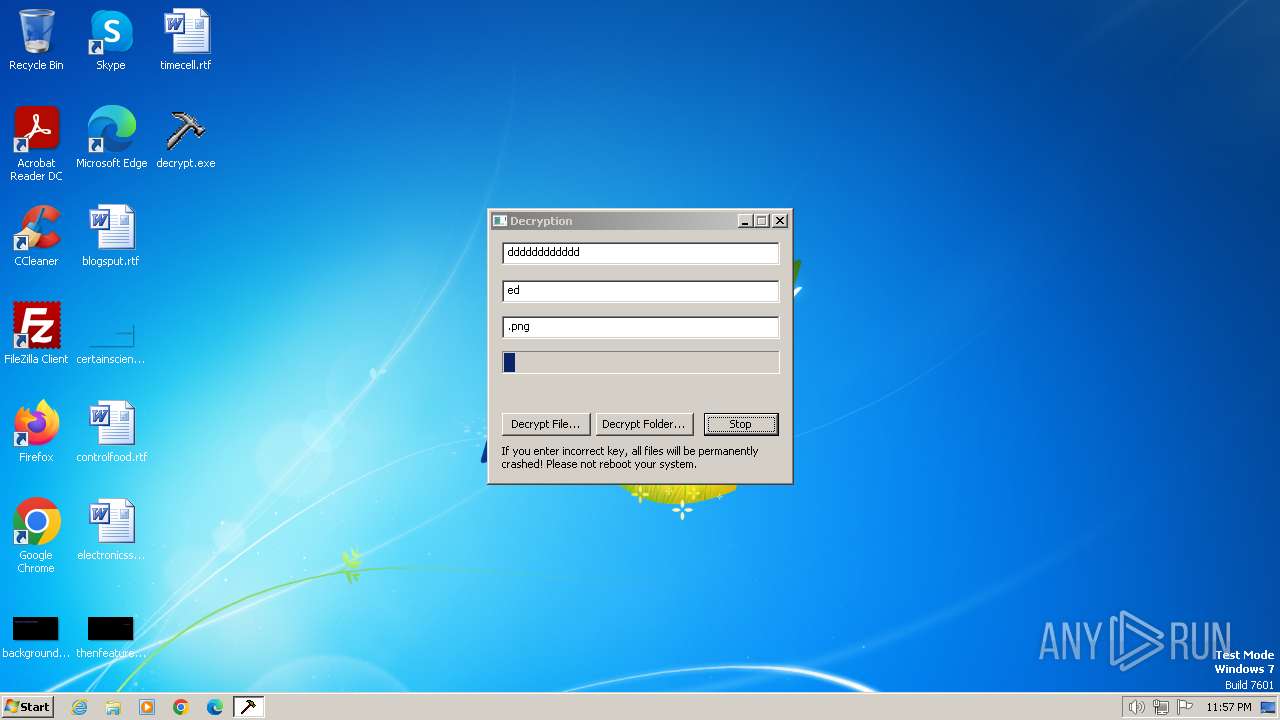
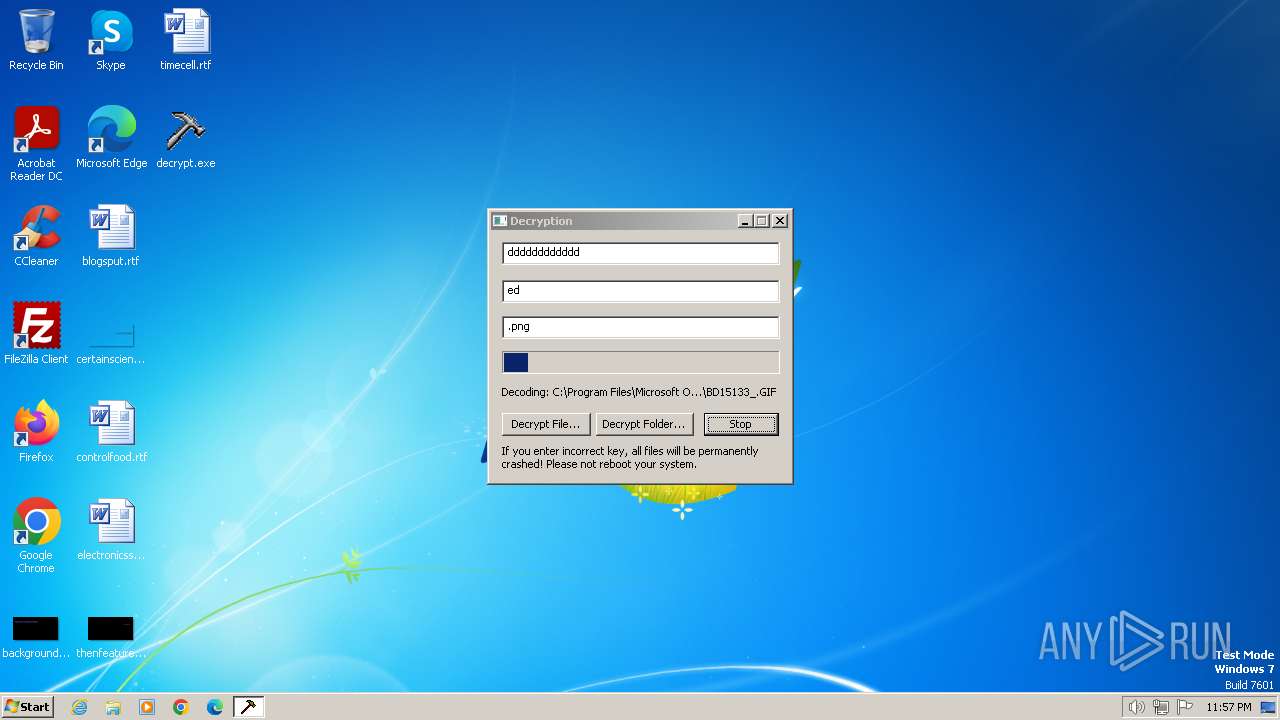
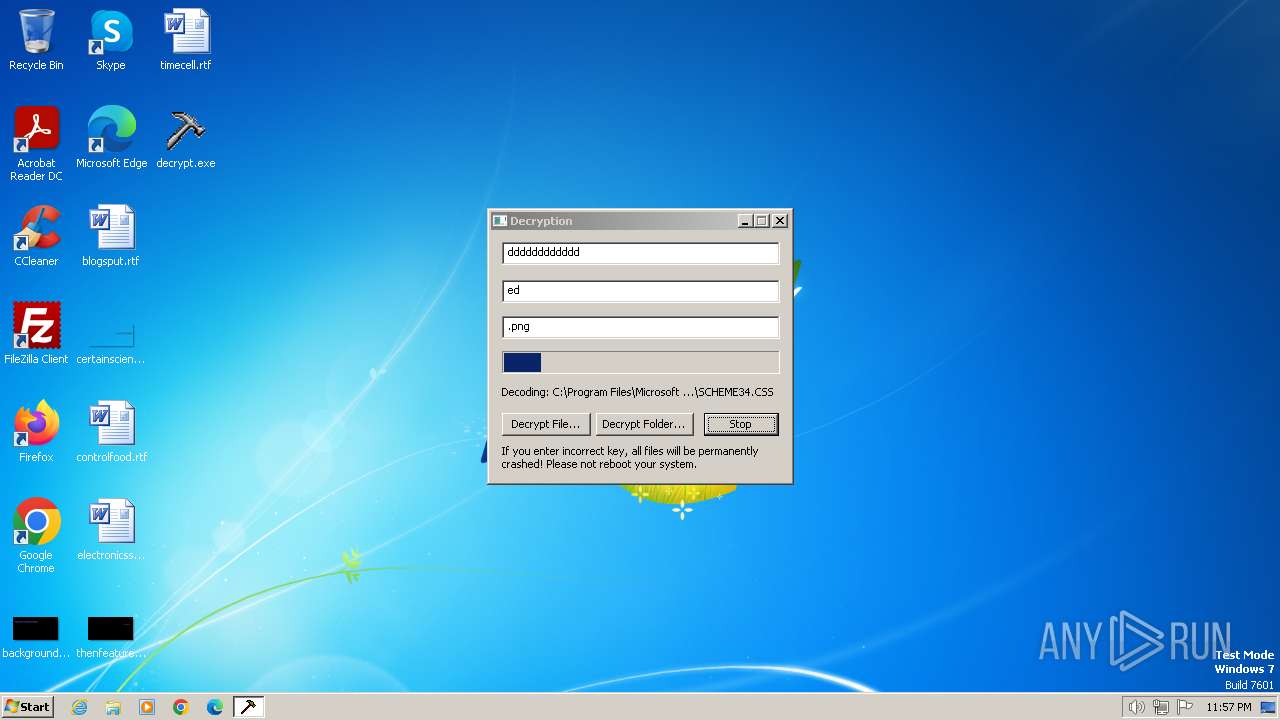
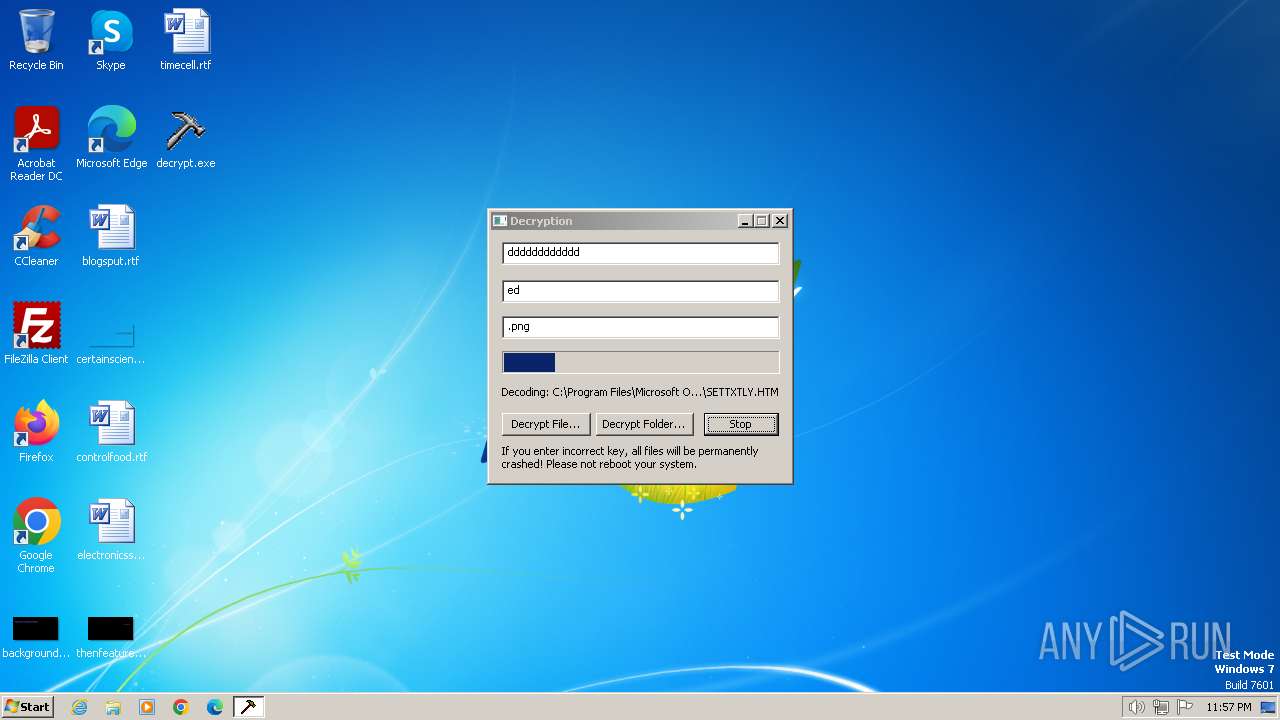
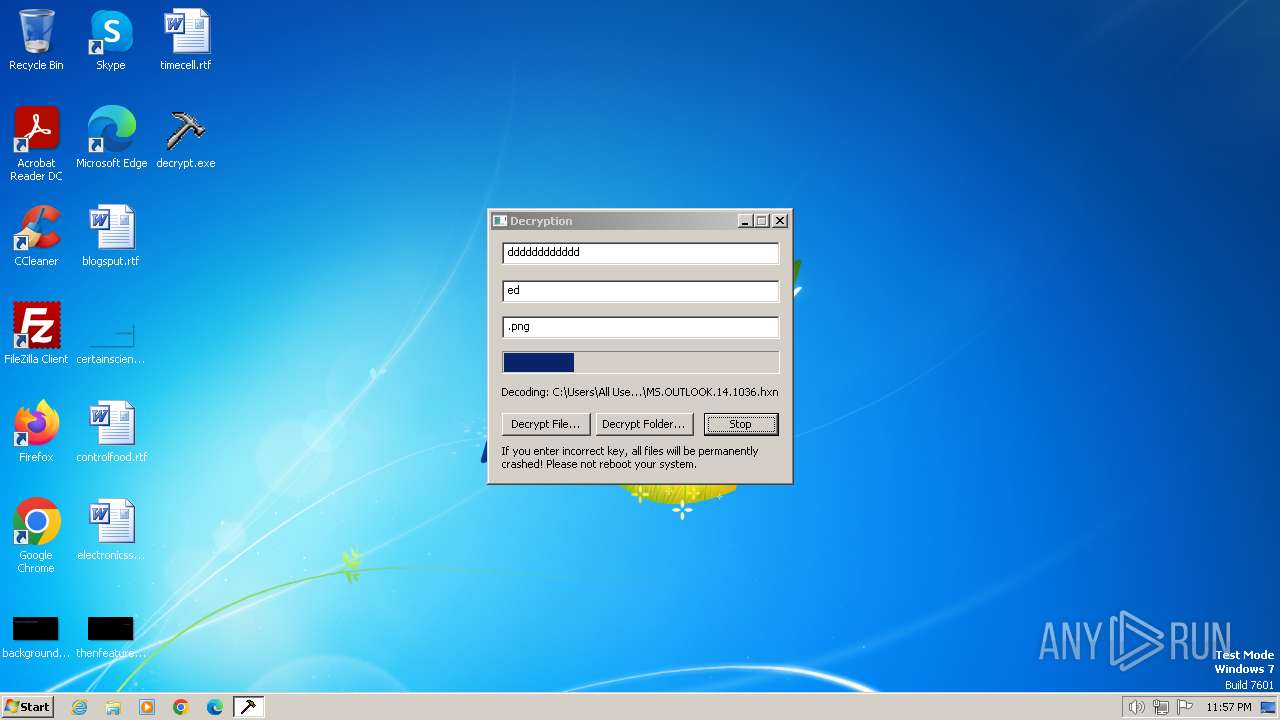
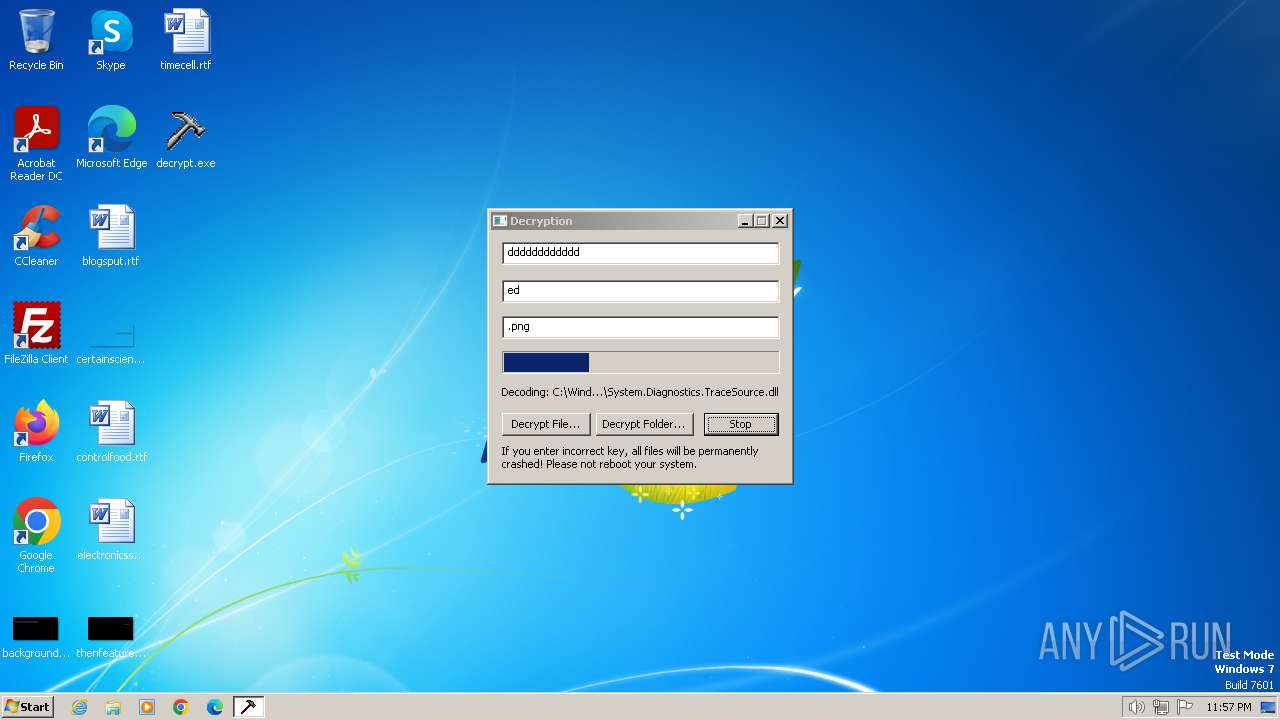
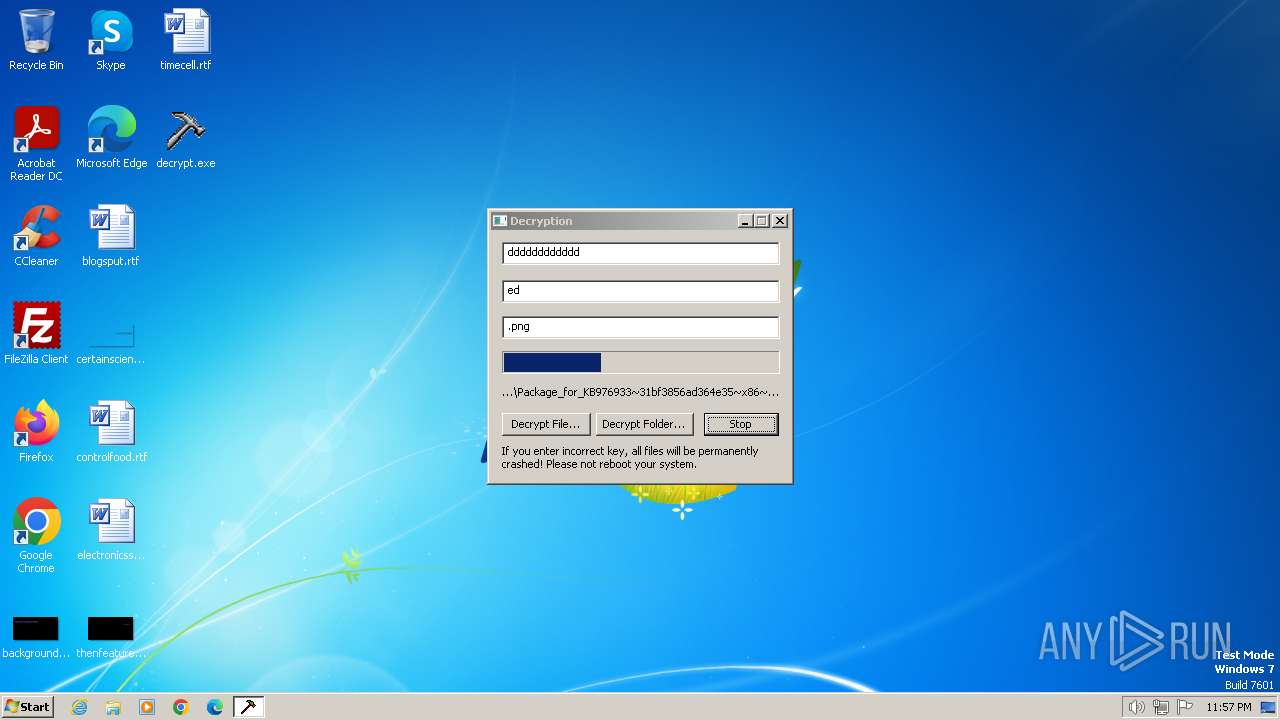
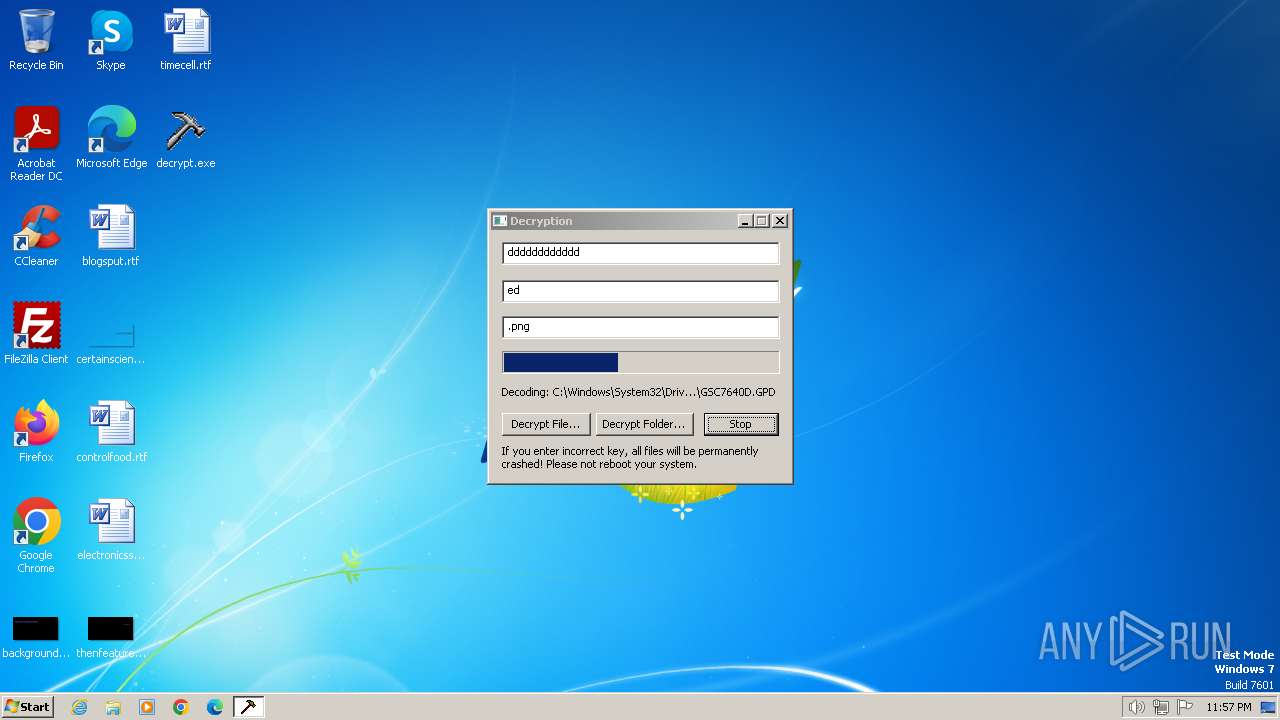
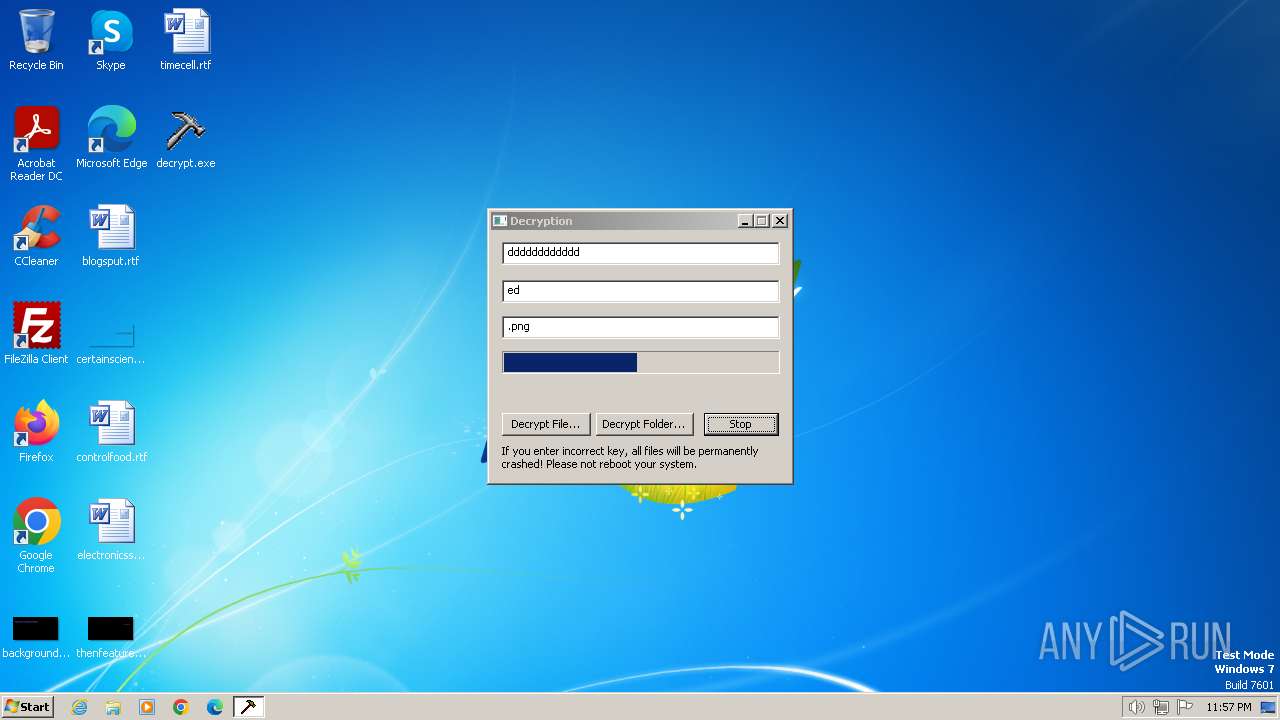
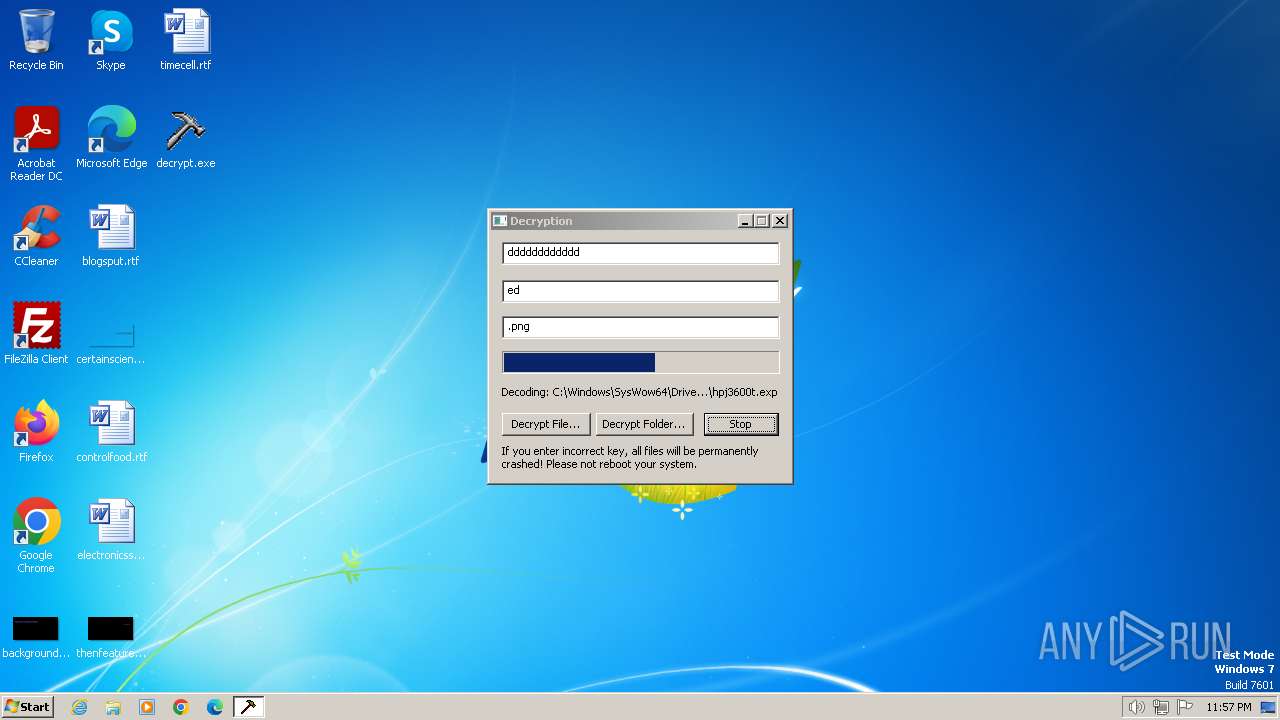
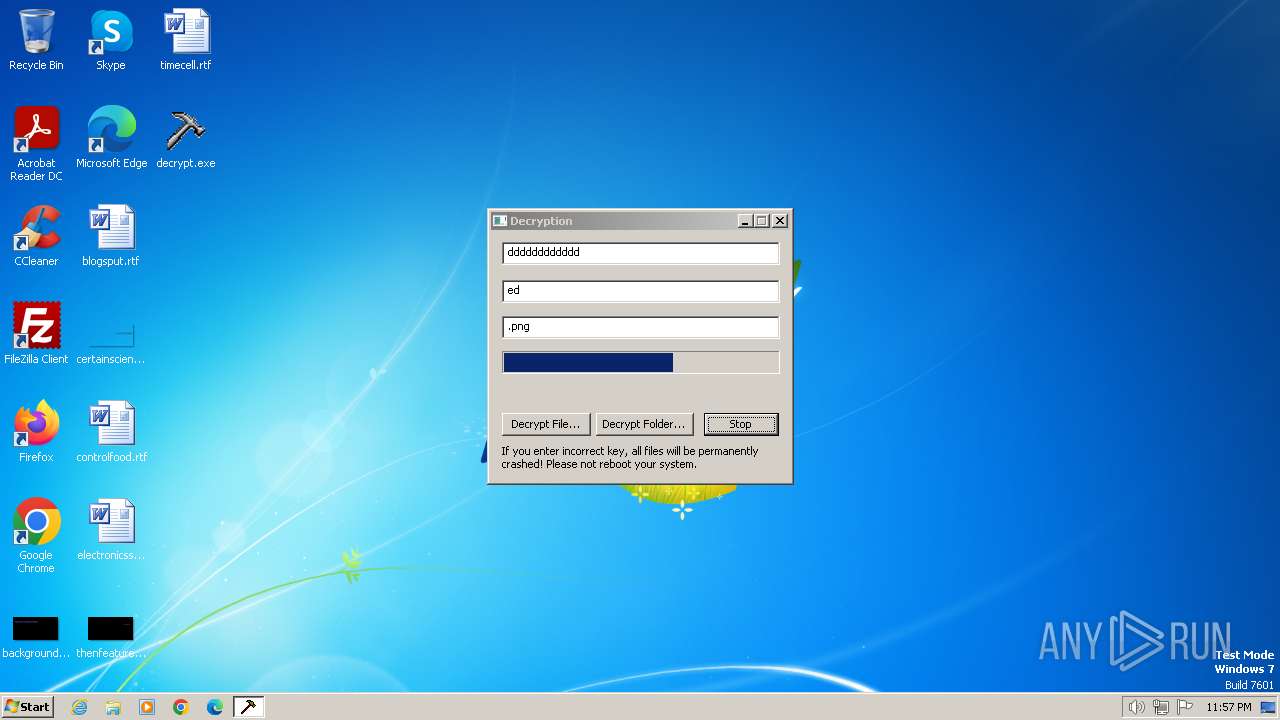
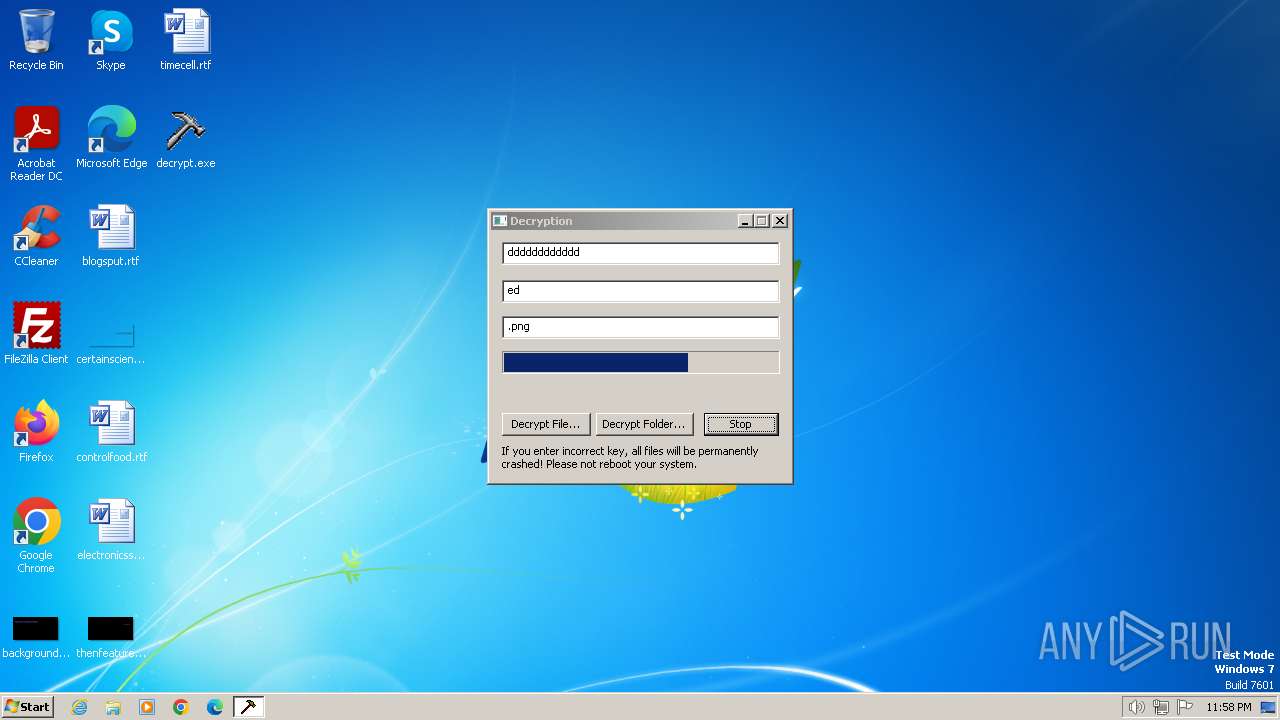
| File name: | decrypt.exe |
| Full analysis: | https://app.any.run/tasks/66f9de20-bbf2-4b7c-91ab-741e7f1eae93 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2024, 23:56:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4098EC223AF471E2C282344C588D2DBB |
| SHA1: | BF2C88797965AEB8EFB405D6FD976678D30F02BA |
| SHA256: | 16E145968BF8B5C3D1079DF39298D11BB80CCE936995C1AFA3F824C192B33151 |
| SSDEEP: | 98304:cBRWPFEL70jOUvI89hA5ahWWzNiTgAGJdFLOAkGkzdnEVomFHKnPBIy:ccfVhYWzSgAGJdFLOyomFHKnPb |
MALICIOUS
Steals credentials from Web Browsers
- decrypt.exe (PID: 2184)
Actions looks like stealing of personal data
- decrypt.exe (PID: 2184)
SUSPICIOUS
Reads browser cookies
- decrypt.exe (PID: 2184)
INFO
Reads the computer name
- decrypt.exe (PID: 2184)
Reads the machine GUID from the registry
- decrypt.exe (PID: 2184)
Checks supported languages
- decrypt.exe (PID: 2184)
Drops the executable file immediately after the start
- decrypt.exe (PID: 2184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:02 22:05:41+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 1859584 |
| InitializedDataSize: | 2053632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1398cf |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
35
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2184 | "C:\Users\admin\Desktop\decrypt.exe" | C:\Users\admin\Desktop\decrypt.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 543
Read events
1 492
Write events
50
Delete events
1
Modification events
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 06000000000000000B0000000100000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000006000000000000000B00000001000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2184) decrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
4
Suspicious files
154
Text files
103
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | decrypt.exe | C:\ProgramData\Microsoft\User Account Pictures\admin.dat | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\UpdateLock-308046B0AF4A39CB | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Adobe\AcroCef\DC\Acrobat\Cookie\Cookies-journal | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\CEF\User Data\Crashpad\metadata | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\metadata | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Affiliation Database-journal | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOCK | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | decrypt.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOCK | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |