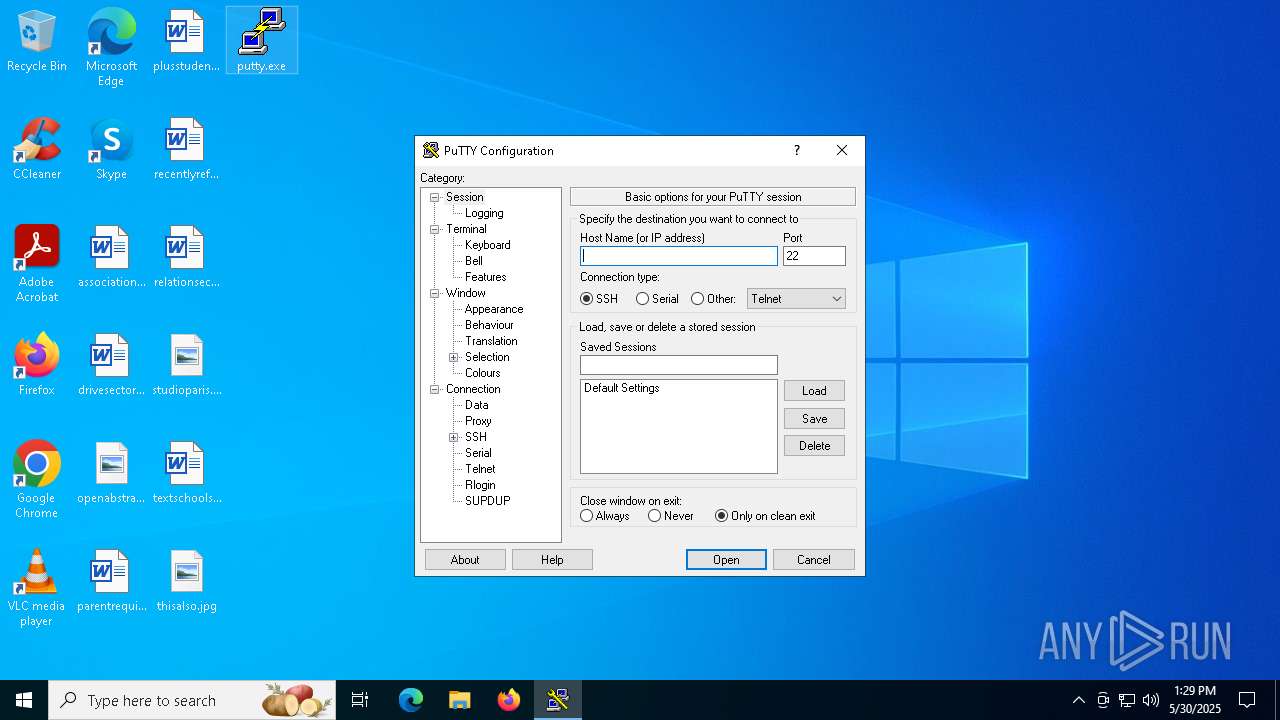
| File name: | putty.exe |
| Full analysis: | https://app.any.run/tasks/577e26cc-0787-4646-ab3e-3bc44df59181 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 13:25:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 10 sections |
| MD5: | 36E31F610EEF3223154E6E8FD074190F |
| SHA1: | 1F2800382CD71163C10E5CE0A32B60297489FBB5 |
| SHA256: | 16CBE40FB24CE2D422AFDDB5A90A5801CED32EF52C22C2FC77B25A90837F28AD |
| SSDEEP: | 49152:uEHBCJFkonGPavKwSDQYBvcgexU282Cdn8KpOEgn31trkHReASNkwDDOkRdu4uWi:3GSDQkr2D8n8KpOEeLr8RtSNkwDds4i |
MALICIOUS
No malicious indicators.SUSPICIOUS
PUTTY has been detected
- putty.exe (PID: 616)
- putty.exe (PID: 7396)
- putty.exe (PID: 2420)
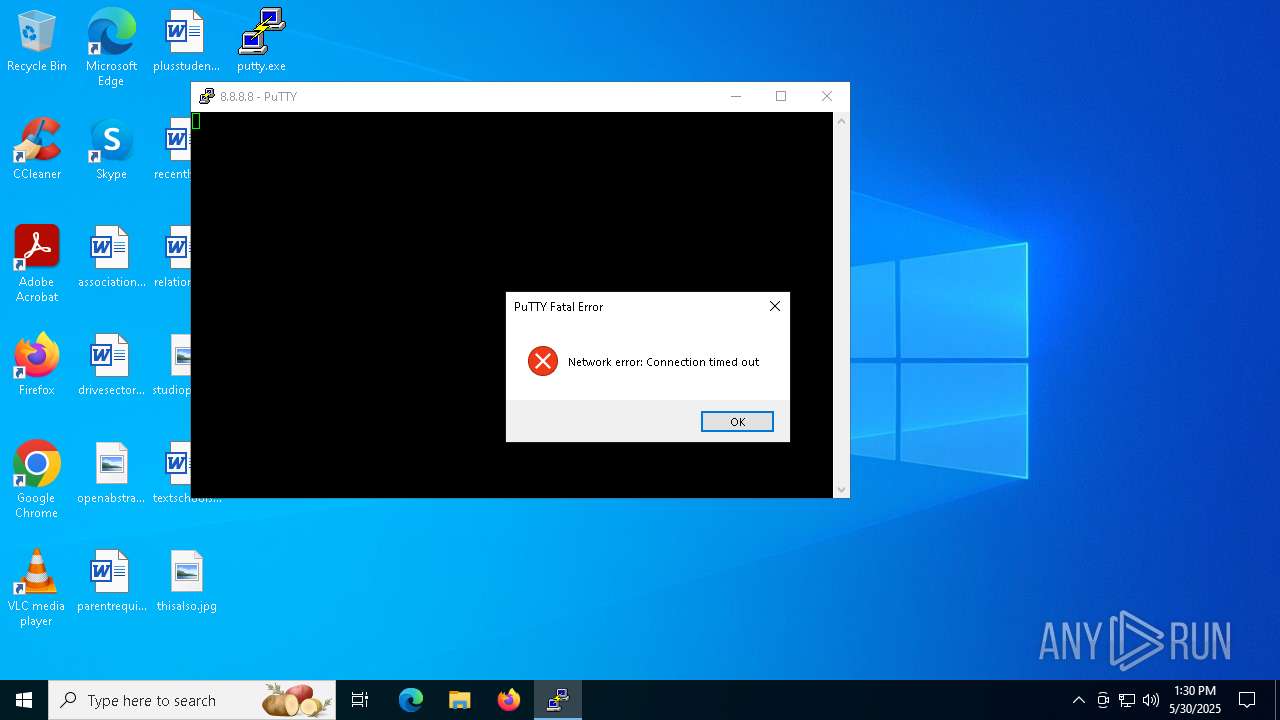
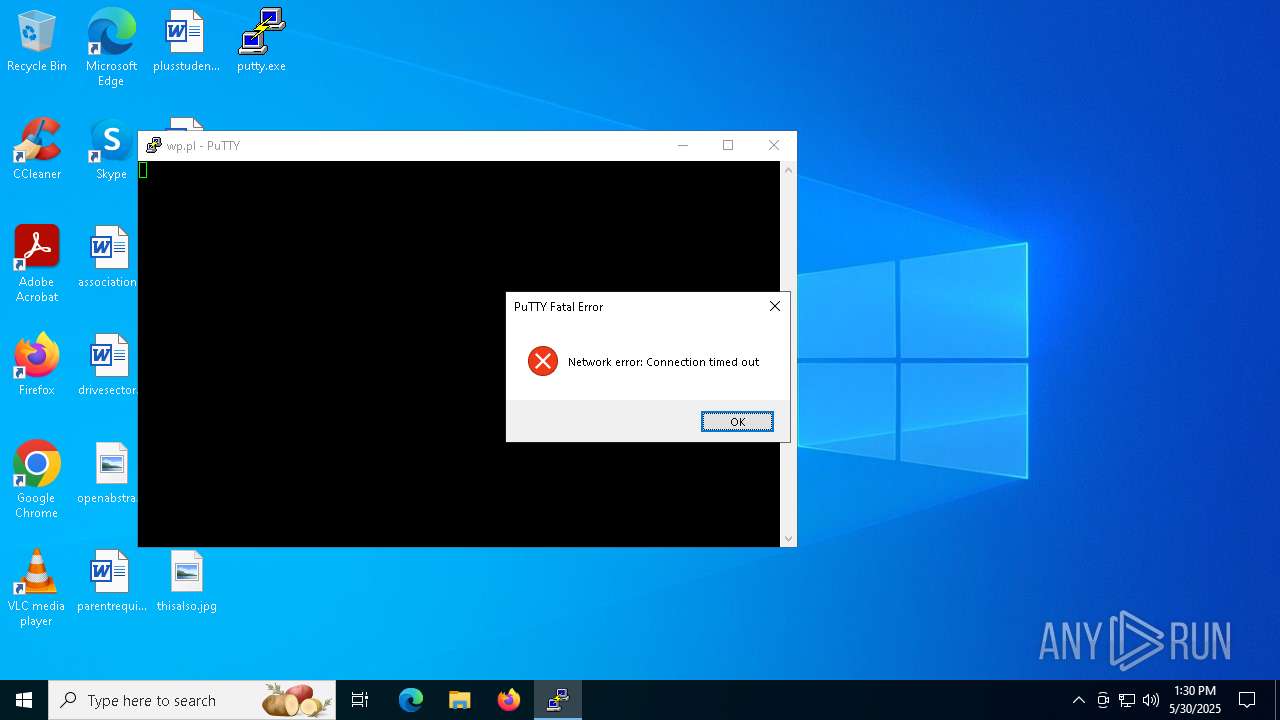
Connects to SSH
- putty.exe (PID: 616)
- putty.exe (PID: 7396)
- putty.exe (PID: 2420)
INFO
The sample compiled with english language support
- putty.exe (PID: 616)
Checks supported languages
- putty.exe (PID: 616)
Creates files or folders in the user directory
- putty.exe (PID: 616)
Reads the computer name
- putty.exe (PID: 616)
Reads the machine GUID from the registry
- putty.exe (PID: 616)
Checks proxy server information
- slui.exe (PID: 6480)
Reads the software policy settings
- slui.exe (PID: 6480)
Manual execution by a user
- putty.exe (PID: 7396)
- putty.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:01 11:27:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 966144 |
| InitializedDataSize: | 716288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xbe504 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.83.0.0 |
| ProductVersionNumber: | 0.83.0.0 |
| FileFlagsMask: | 0x000b |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | Simon Tatham |
| ProductName: | PuTTY suite |
| FileDescription: | SSH, Telnet, Rlogin, and SUPDUP client |
| InternalName: | PuTTY |
| OriginalFileName: | PuTTY |
| FileVersion: | Release 0.83 (with embedded help) |
| ProductVersion: | Release 0.83 |
| LegalCopyright: | Copyright © 1997-2025 Simon Tatham. |
Total processes
203
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Users\admin\AppData\Local\Temp\putty.exe" | C:\Users\admin\AppData\Local\Temp\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Exit code: 0 Version: Release 0.83 (with embedded help) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Desktop\putty.exe" | C:\Users\admin\Desktop\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Exit code: 0 Version: Release 0.83 (with embedded help) Modules
| |||||||||||||||
| 2560 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7396 | "C:\Users\admin\Desktop\putty.exe" | C:\Users\admin\Desktop\putty.exe | explorer.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Exit code: 0 Version: Release 0.83 (with embedded help) Modules
| |||||||||||||||
| 8148 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8156 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 706
Read events
3 678
Write events
26
Delete events
2
Modification events
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000004000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\3\Shell\{DE4F0660-FA10-4B8F-A494-068B20B22307} |
| Operation: | write | Name: | Rev |
Value: 0 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\3\Shell\{DE4F0660-FA10-4B8F-A494-068B20B22307} |
| Operation: | write | Name: | FFlags |
Value: 18874369 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\3\Shell\{DE4F0660-FA10-4B8F-A494-068B20B22307} |
| Operation: | write | Name: | Vid |
Value: {65F125E5-7BE1-4810-BA9D-D271C8432CE3} | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | WFlags |
Value: 0 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | ShowCmd |
Value: 1 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\Shell\Microsoft.Windows.ControlPanel |
| Operation: | write | Name: | HotKey |
Value: 0 | |||
| (PID) Process: | (8148) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\3\Shell\{DE4F0660-FA10-4B8F-A494-068B20B22307} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
Executable files
0
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 616 | putty.exe | C:\Users\admin\AppData\Local\PUTTY.RND | binary | |
MD5:3F5B903766F19A3725337116795C512B | SHA256:8103A67085033A036C66431020A3EB1EB96C934A9A9C818D9F5F56E93C9CCD31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
79
DNS requests
82
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7656 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2392 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b96d4ca8-86b5-4bcc-9b2f-8200e97368c2?P1=1749216198&P2=404&P3=2&P4=WDJSRhSj%2fKNBwAZWgADgE%2fThWE11IeCyxeiRhVdHNSKgbAdasL4vkXZJVZe3u2SbXScL4H7gSPCRVl6uWWvH6w%3d%3d | unknown | — | — | whitelisted |
2392 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/b96d4ca8-86b5-4bcc-9b2f-8200e97368c2?P1=1749216198&P2=404&P3=2&P4=WDJSRhSj%2fKNBwAZWgADgE%2fThWE11IeCyxeiRhVdHNSKgbAdasL4vkXZJVZe3u2SbXScL4H7gSPCRVl6uWWvH6w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | unknown |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
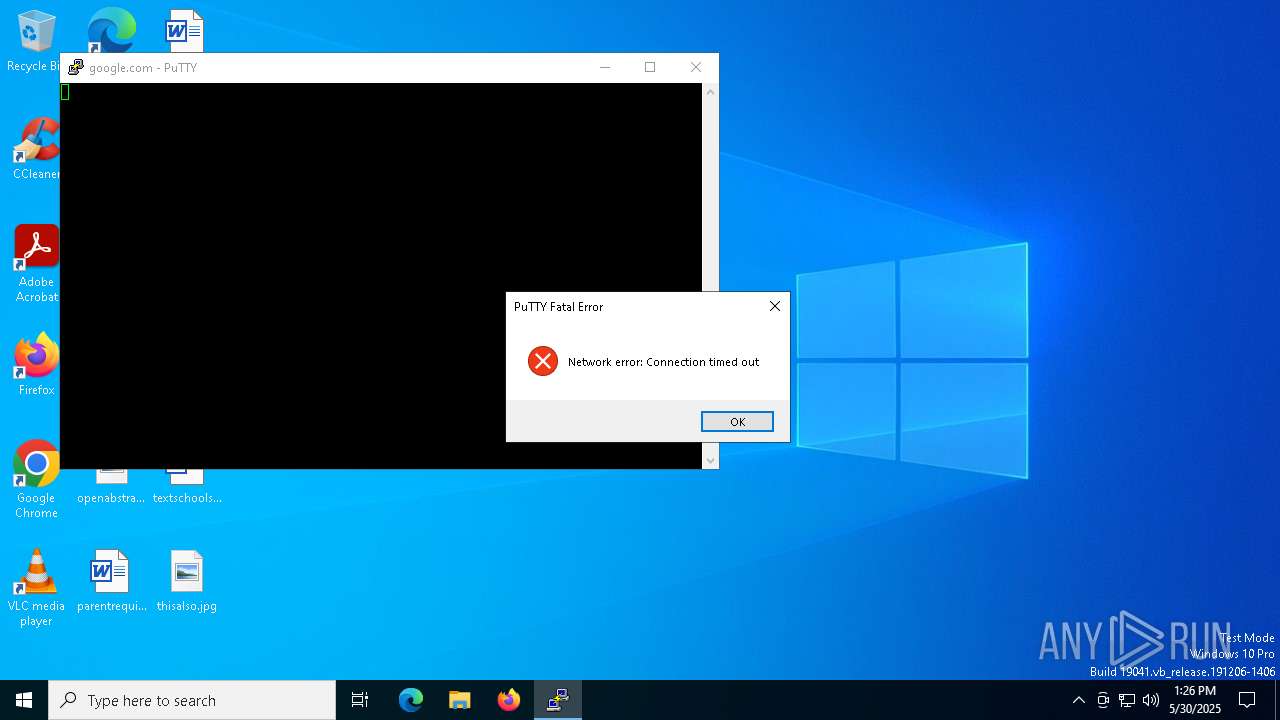
616 | putty.exe | 142.250.186.110:22 | google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
616 | putty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
7396 | putty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
2420 | putty.exe | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |