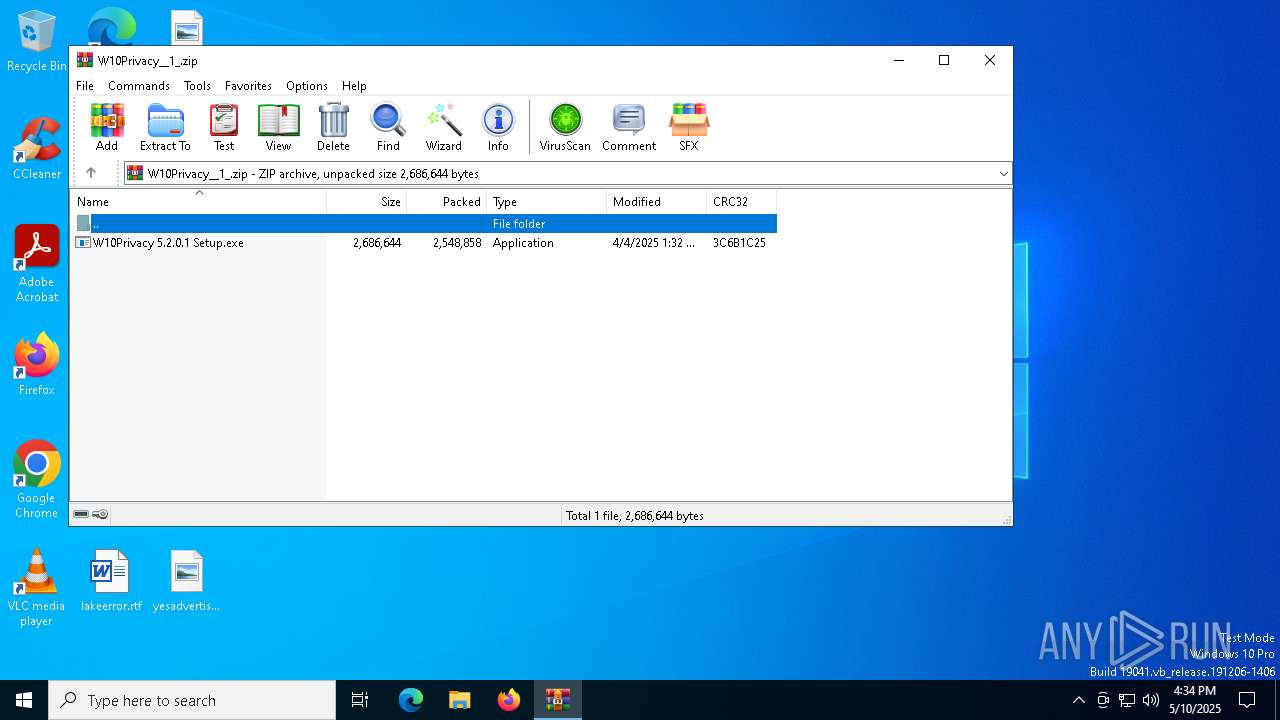
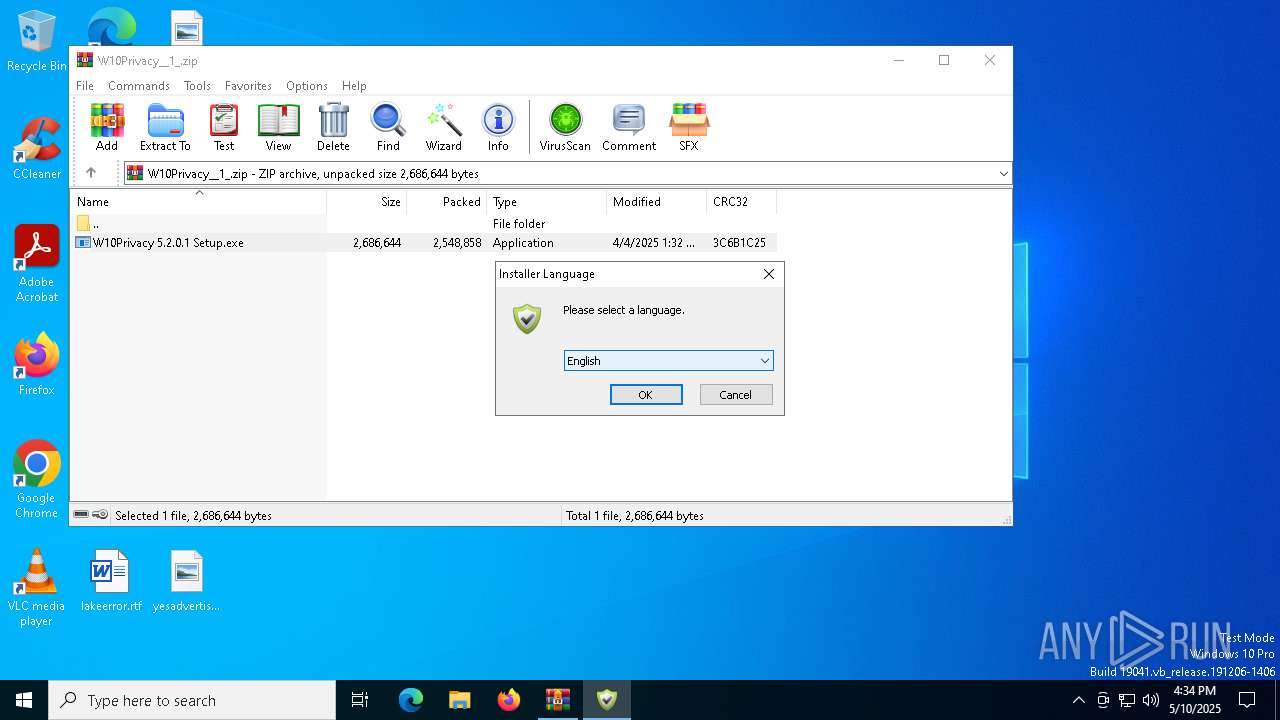
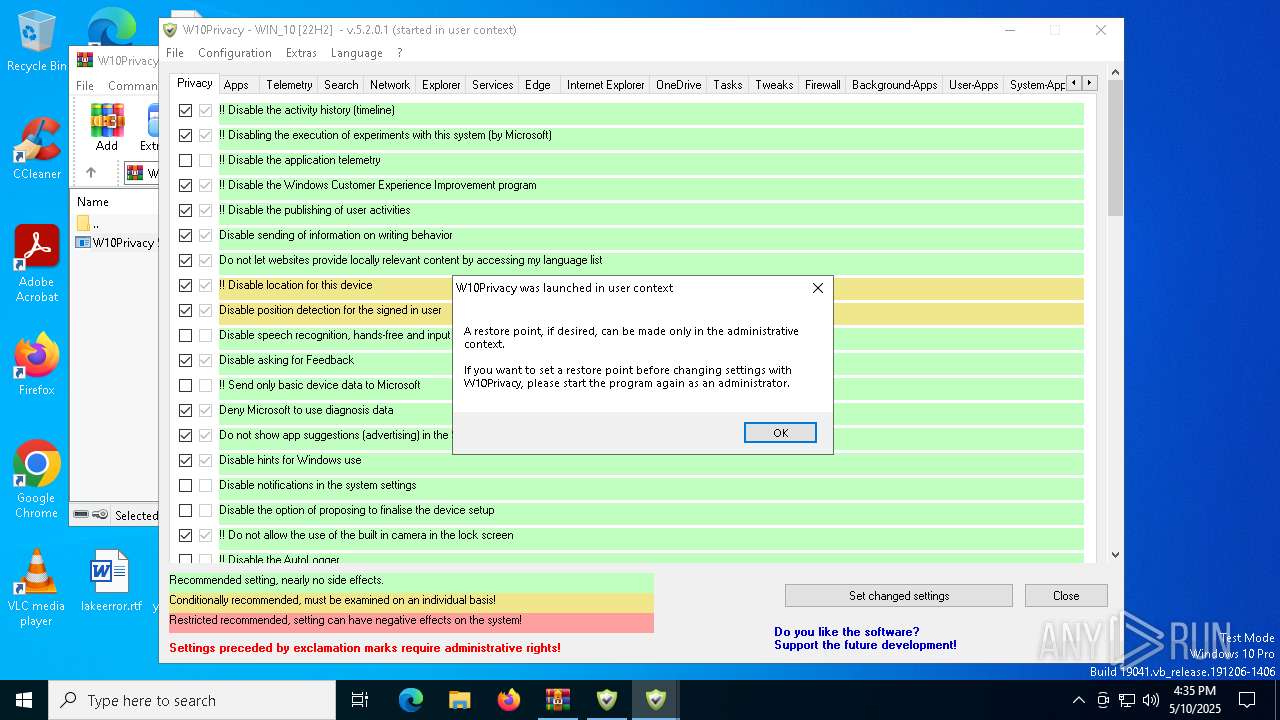
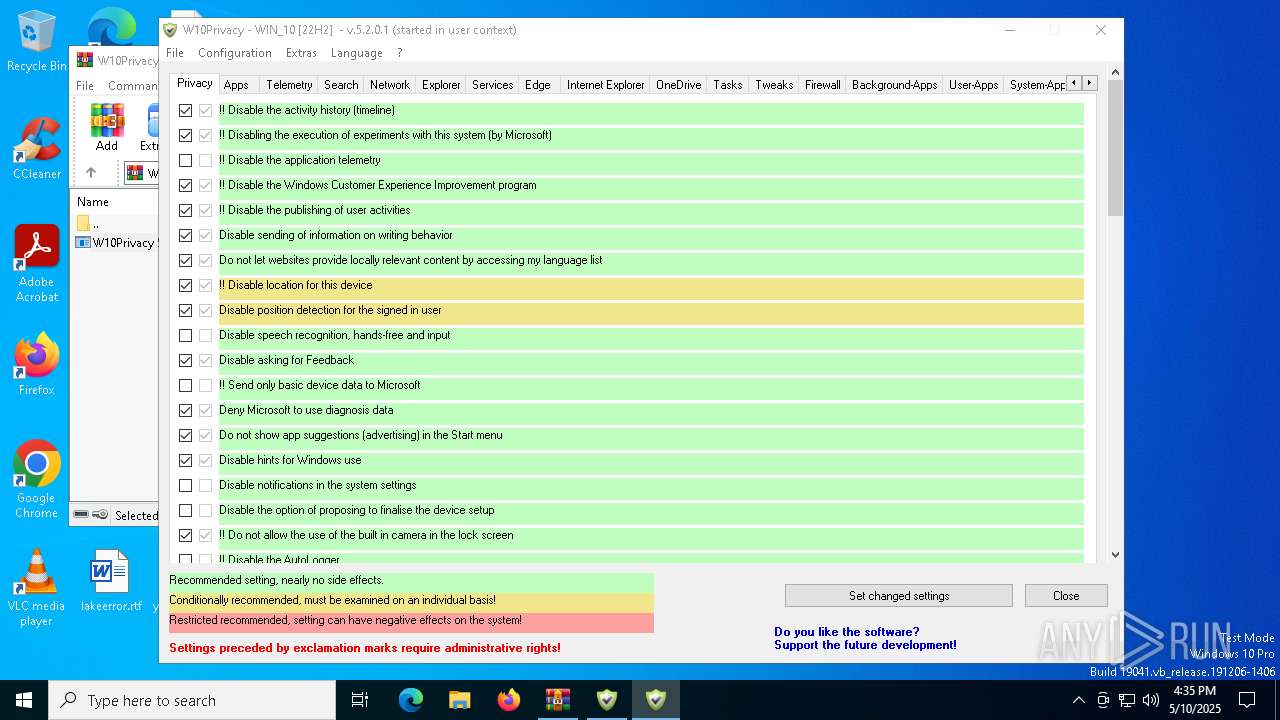
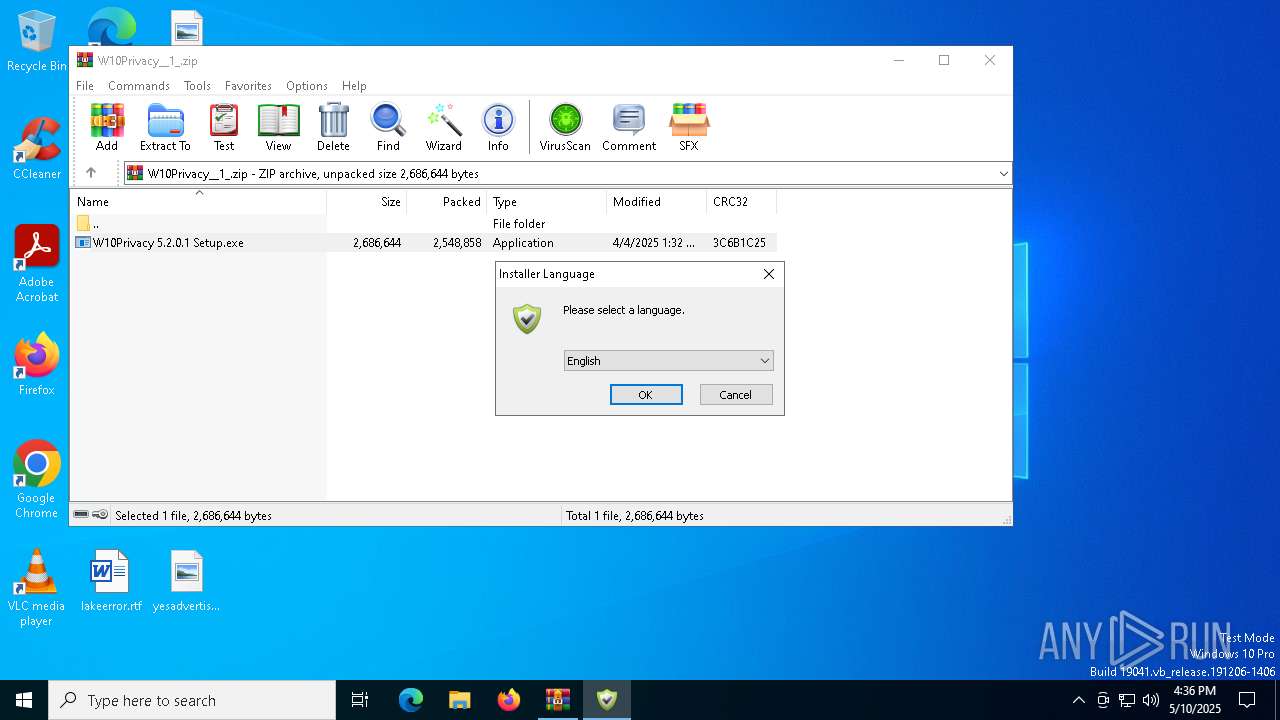
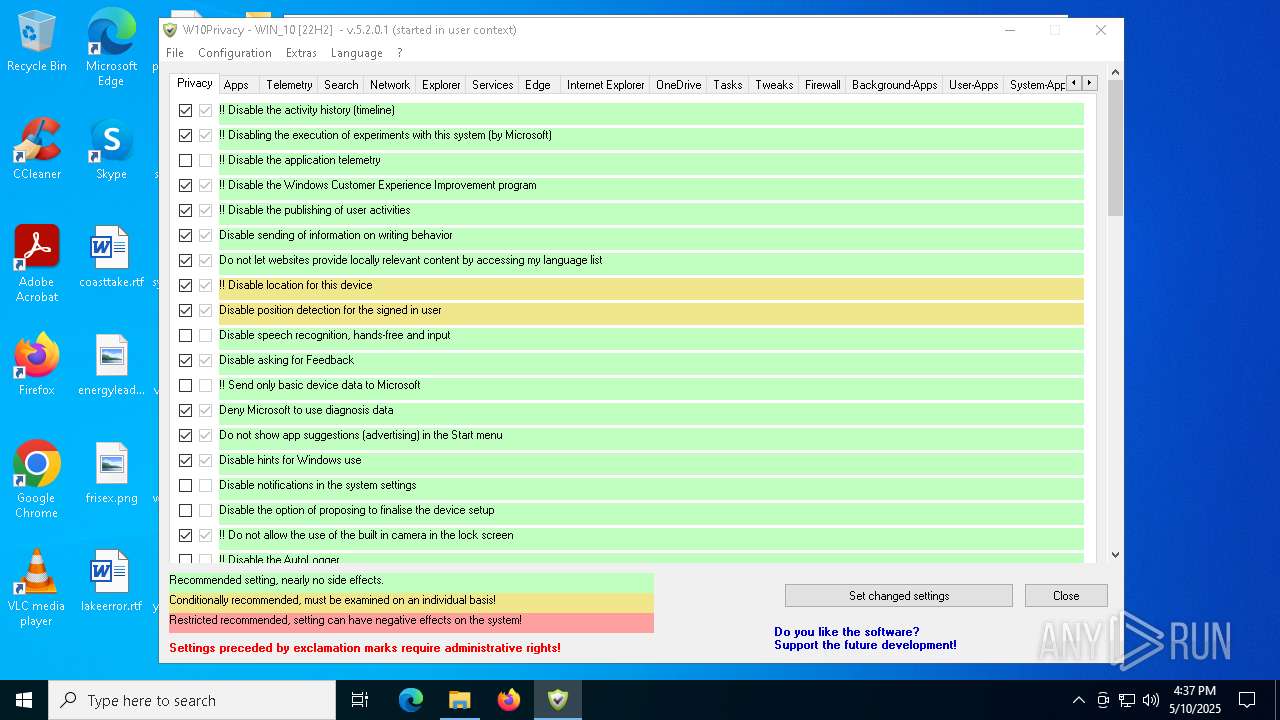
| File name: | W10Privacy__1_.zip |
| Full analysis: | https://app.any.run/tasks/9f9acb15-23f8-49c8-ba94-e2c02904a969 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 16:34:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5CE62E01543A539C1CC550E5BF5E62E5 |
| SHA1: | D3DB807BE1AD8A51A4860E1CD612BFD78F29E8FE |
| SHA256: | 16AB3EDE9FEF8237CFB892D3F98B55F6636F862BFCB40F56AEFC7BF3B3067408 |
| SSDEEP: | 98304:plu27FB+bRjsPR+/kGGlXLRGLIj331KtJX/fdXQi/WSqVfssltaYzNzHsrdxOoAy:HHgeBcT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1272)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1272)
Executable content was dropped or overwritten
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
The process creates files with name similar to system file names
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
Malware-specific behavior (creating "System.dll" in Temp)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
There is functionality for taking screenshot (YARA)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy.exe (PID: 2148)
- W10Privacy.exe (PID: 8084)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
Creates a software uninstall entry
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
Starts CMD.EXE for commands execution
- W10Privacy.exe (PID: 2148)
- W10Privacy.exe (PID: 8084)
Identifying current user with WHOAMI command
- cmd.exe (PID: 5324)
- cmd.exe (PID: 4996)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 6388)
- schtasks.exe (PID: 2504)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2284)
- cmd.exe (PID: 6372)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 7384)
- cmd.exe (PID: 8120)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1272)
Create files in a temporary directory
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
- W10Privacy.exe (PID: 2148)
Checks supported languages
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy.exe (PID: 2148)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
Reads the computer name
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
- W10Privacy.exe (PID: 2148)
The sample compiled with german language support
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy 5.2.0.1 Setup.exe (PID: 7728)
Creates files in the program directory
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
Creates files or folders in the user directory
- W10Privacy 5.2.0.1 Setup.exe (PID: 7732)
- W10Privacy.exe (PID: 2148)
Manual execution by a user
- W10Privacy.exe (PID: 2148)
- W10Privacy.exe (PID: 8084)
Reads the software policy settings
- slui.exe (PID: 7296)
Reads security settings of Internet Explorer
- netsh.exe (PID: 7444)
The process uses AutoIt
- W10Privacy.exe (PID: 2148)
- W10Privacy.exe (PID: 8084)
UPX packer has been detected
- W10Privacy.exe (PID: 2148)
- W10Privacy.exe (PID: 8084)
Reads mouse settings
- W10Privacy.exe (PID: 2148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:04 15:32:46 |
| ZipCRC: | 0x3c6b1c25 |
| ZipCompressedSize: | 2548858 |
| ZipUncompressedSize: | 2686644 |
| ZipFileName: | W10Privacy 5.2.0.1 Setup.exe |
Total processes
197
Monitored processes
59
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\W10Privacy__1_.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\cmd.exe /C del /s /q "C:\Users\admin\AppData\Local\Temp\tasks.txt" | C:\Windows\SysWOW64\cmd.exe | — | W10Privacy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\system32\cmd.exe /C del /s /q "C:\Users\admin\AppData\Local\Temp\whoami.txt" | C:\Windows\SysWOW64\cmd.exe | — | W10Privacy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Program Files (x86)\W10Privacy\W10Privacy.exe" | C:\Program Files (x86)\W10Privacy\W10Privacy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: W10Privacy Exit code: 0 Version: 5.2.0.1 Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\system32\cmd.exe /C C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe Get-AppxPackage > C:\Users\admin\AppData\Local\Temp\benutzerapps.txt | C:\Windows\System32\cmd.exe | — | W10Privacy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | netsh advfirewall firewall show rule name=all dir=out verbose | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | schtasks.exe /query /FO CSV | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 671
Read events
15 641
Write events
30
Delete events
0
Modification events
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\W10Privacy__1_.zip | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1272) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7732) W10Privacy 5.2.0.1 Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\W10Privacy |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\W10Privacy\Uninstall.exe | |||
| (PID) Process: | (7732) W10Privacy 5.2.0.1 Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\W10Privacy |
| Operation: | write | Name: | DisplayVersion |
Value: 5.2.0.1 | |||
Executable files
14
Suspicious files
20
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Users\admin\AppData\Local\Temp\nsaE969.tmp\modern-wizard.bmp | image | |
MD5:84198D368B12F7AE4B274C6DB32BC6FF | SHA256:C3D66F9E03723A893634FE4B9CF7DFBFEFBCE40A8651AADC55BB198585CBFE83 | |||
| 1272 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1272.20156\W10Privacy 5.2.0.1 Setup.exe | executable | |
MD5:830D971CC1583541748088B6342BFD93 | SHA256:6B0F812A9849441151056DD55A60D7BDAFF7A8C40EE4C2582728AD59E52F67FE | |||
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Program Files (x86)\W10Privacy\W10Privacy.exe | executable | |
MD5:E442ECDF3425E237F531745804489C2E | SHA256:1C9248C57B23A3A085B615B8134F39AAAF6E74DCDB5289D12A91DE1AC6C66C74 | |||
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Users\admin\AppData\Local\Temp\nsaE969.tmp\UserInfo.dll | executable | |
MD5:E6F30908ABFC6F53B7C3C36DAEC4586D | SHA256:E0DC3112796DBAA37F25AB54B7FAC2FBF791CBC6E36A84FC61C6423B84A3677B | |||
| 2148 | W10Privacy.exe | C:\Users\admin\AppData\Roaming\W10Privacy\W10Privacy.ini | text | |
MD5:A28367555FB661A98B03D27D943EF3E2 | SHA256:E9E9FC976264DA1D348B67AD496A8EB627888C4139E776DE16396C1E17F443AD | |||
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Program Files (x86)\W10Privacy\W10PrivacyTile150.png | image | |
MD5:C4DB1D83D8197E4E85A9A081FA6CE445 | SHA256:17EBB2699C33B62FF3FBA8E23A42FEDEA3E1078A2133696D7090E70C8709B458 | |||
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Program Files (x86)\W10Privacy\W10Privacy.VisualElementsManifest.xml | xml | |
MD5:98AC5354DC56BF21F057DDC3C6D9A2BC | SHA256:032C2BAE55810CBB1B59D43E45C91295205D830C5D9BA6186165AFA019CD8605 | |||
| 7732 | W10Privacy 5.2.0.1 Setup.exe | C:\Program Files (x86)\W10Privacy\Uninstall.exe | executable | |
MD5:DAE635DEF0F5765A2B50A7E08CD0FC38 | SHA256:B613FDA8543BA77E817B95558D424367735B17B689CC4022B5A2354E76581DF4 | |||
| 2148 | W10Privacy.exe | C:\Users\admin\AppData\Roaming\W10Privacy\Languages.ini | text | |
MD5:A4983BDA5611BB75961DC6353B7126F9 | SHA256:9502EFDB509132E8AF3DA3293AA31C1A6542D1ABECC00A5CB2BC416208F6991D | |||
| 2148 | W10Privacy.exe | C:\Users\admin\AppData\Local\Temp\aut3EBB.tmp | binary | |
MD5:FAEF0034D594C112D239D746AFD137A8 | SHA256:A6E60B0DE7B2FC431BB4DC9D8157B8C324FBE72C8EF9081E8C9F3EE2AE8C31A1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7952 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |