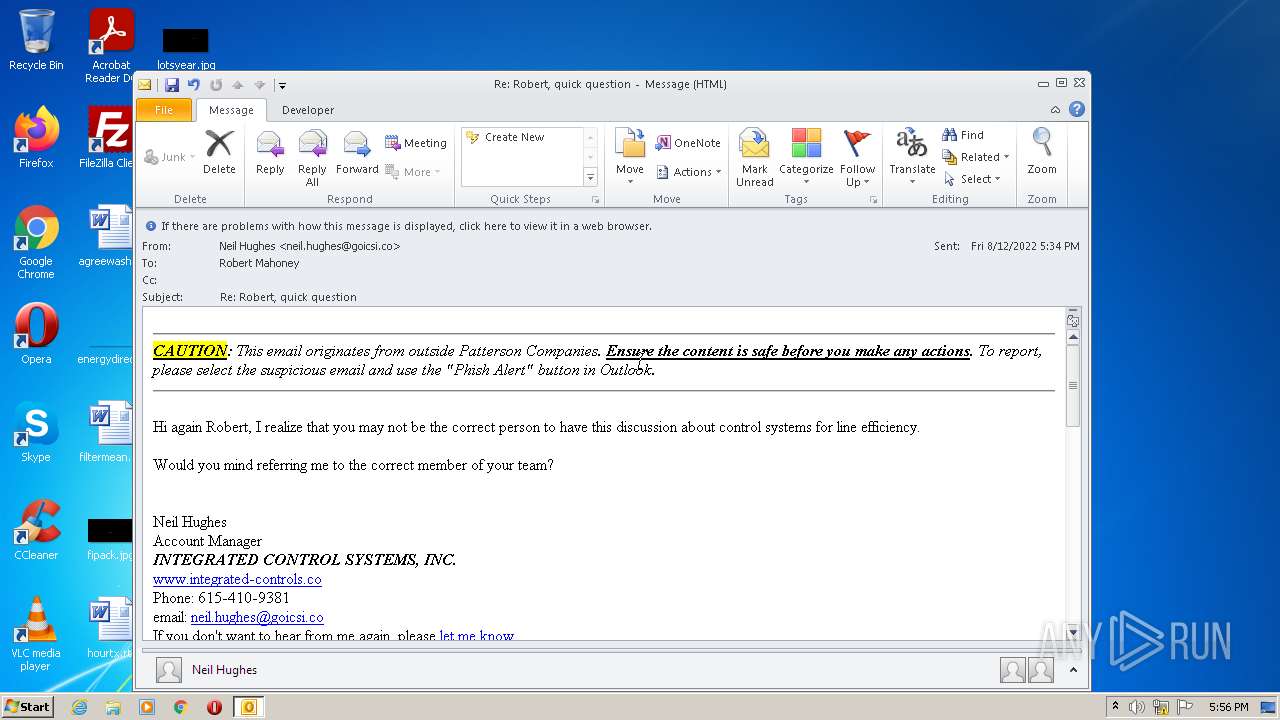
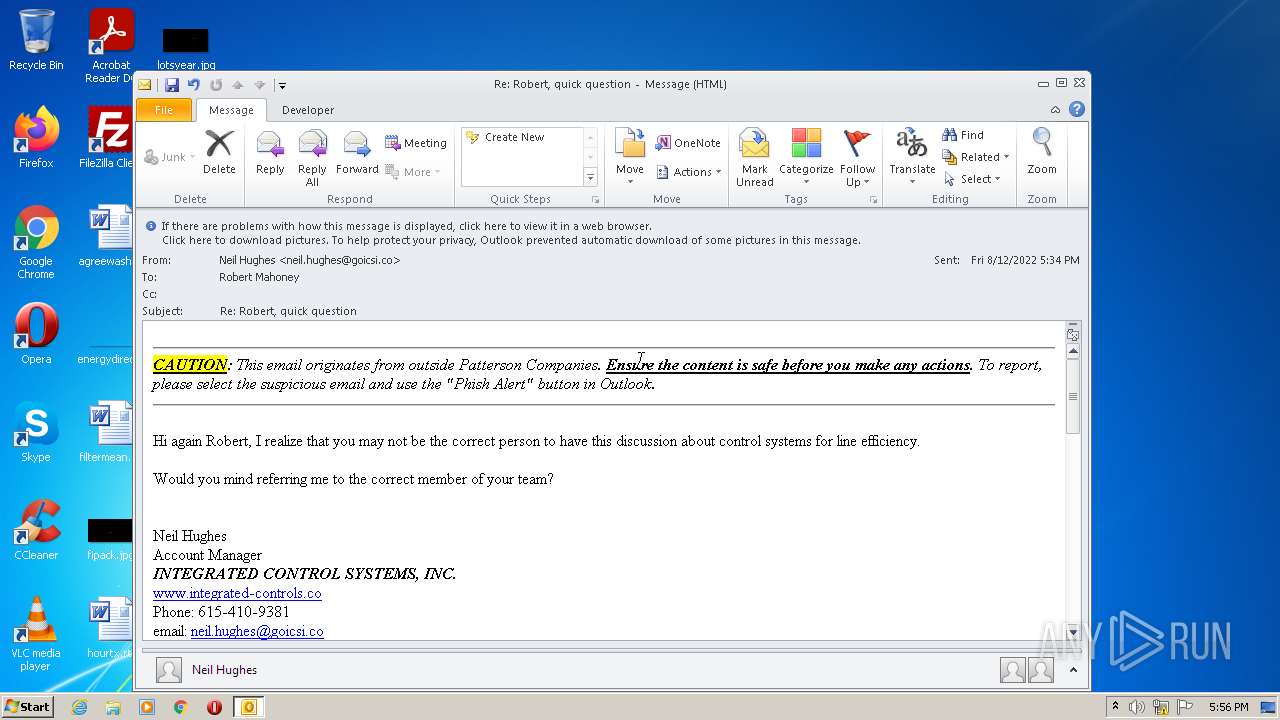
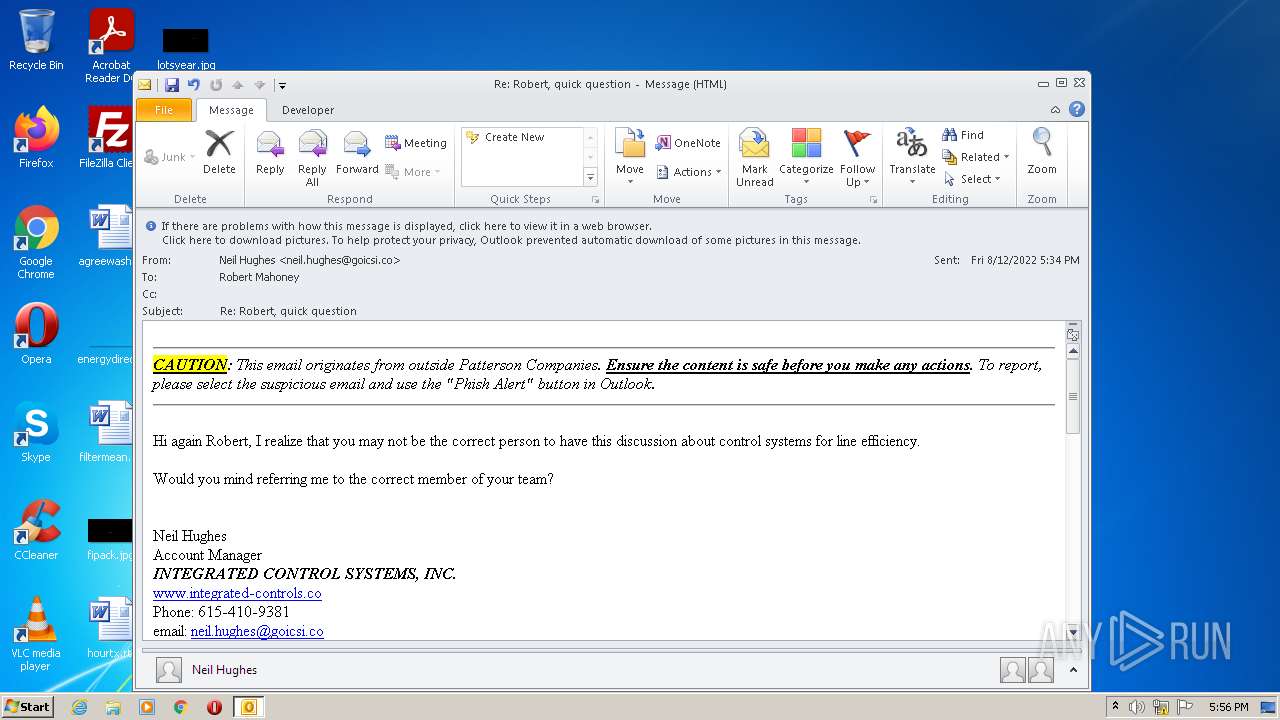
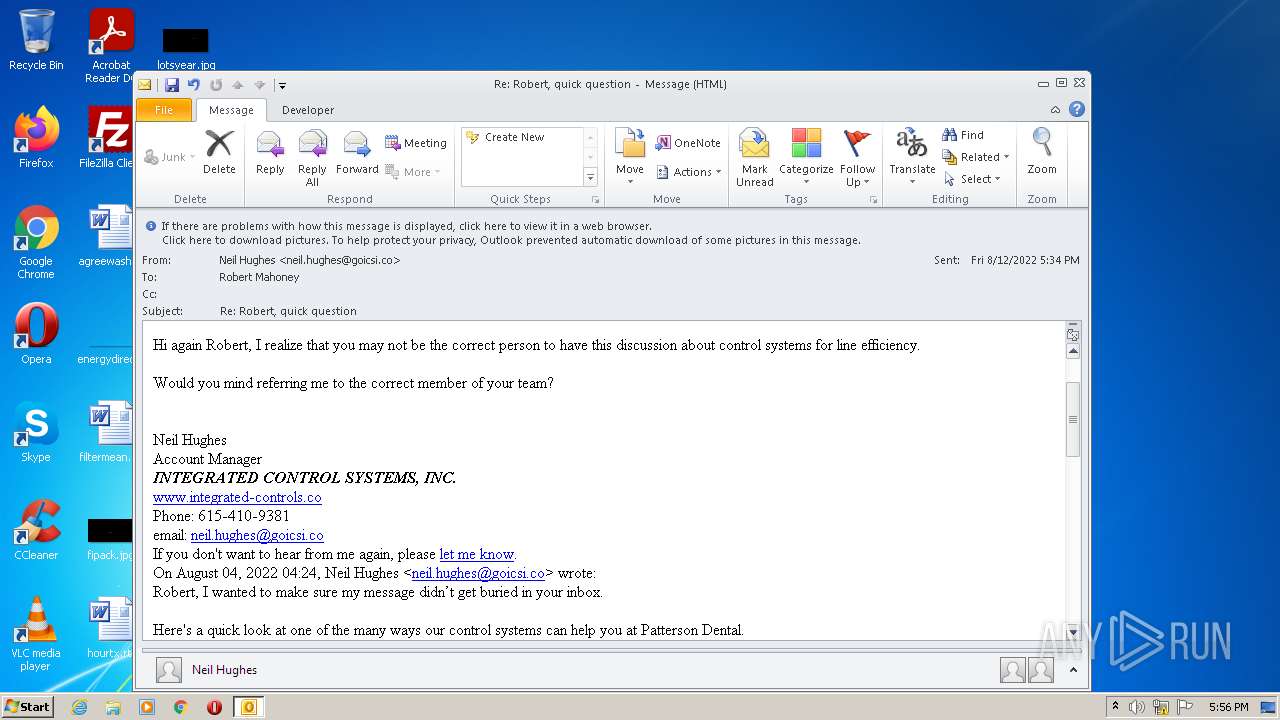
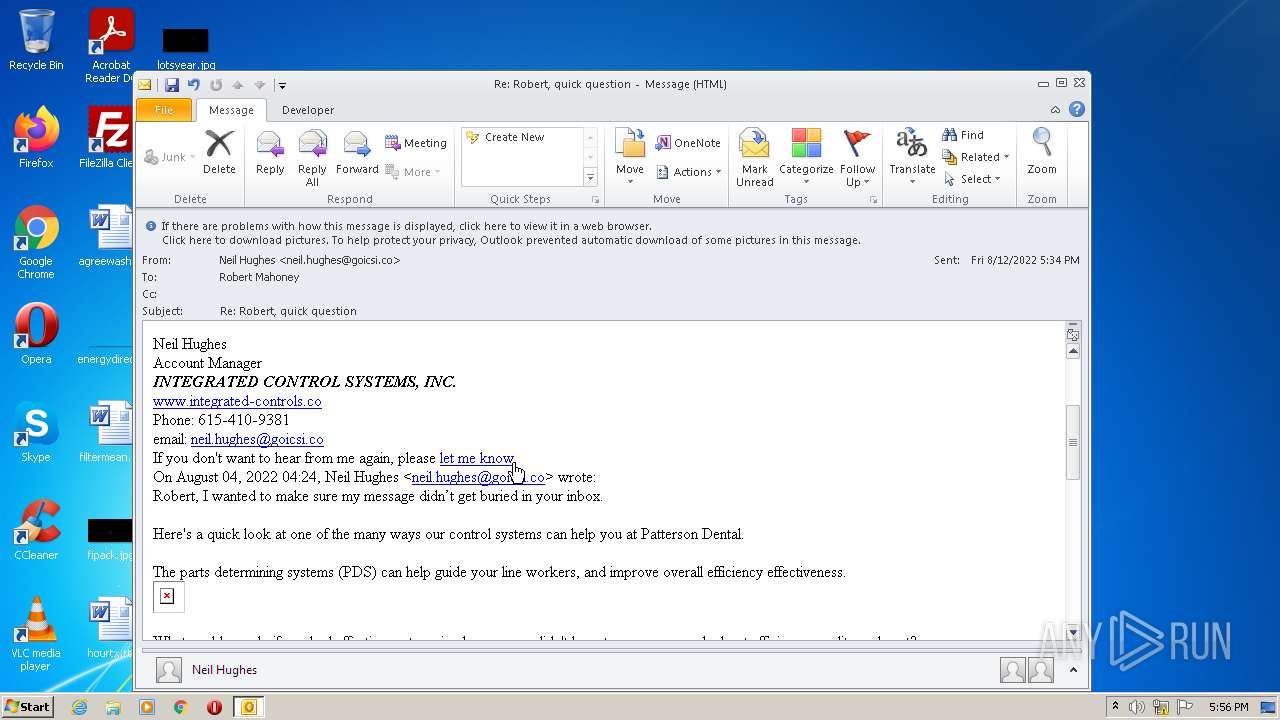
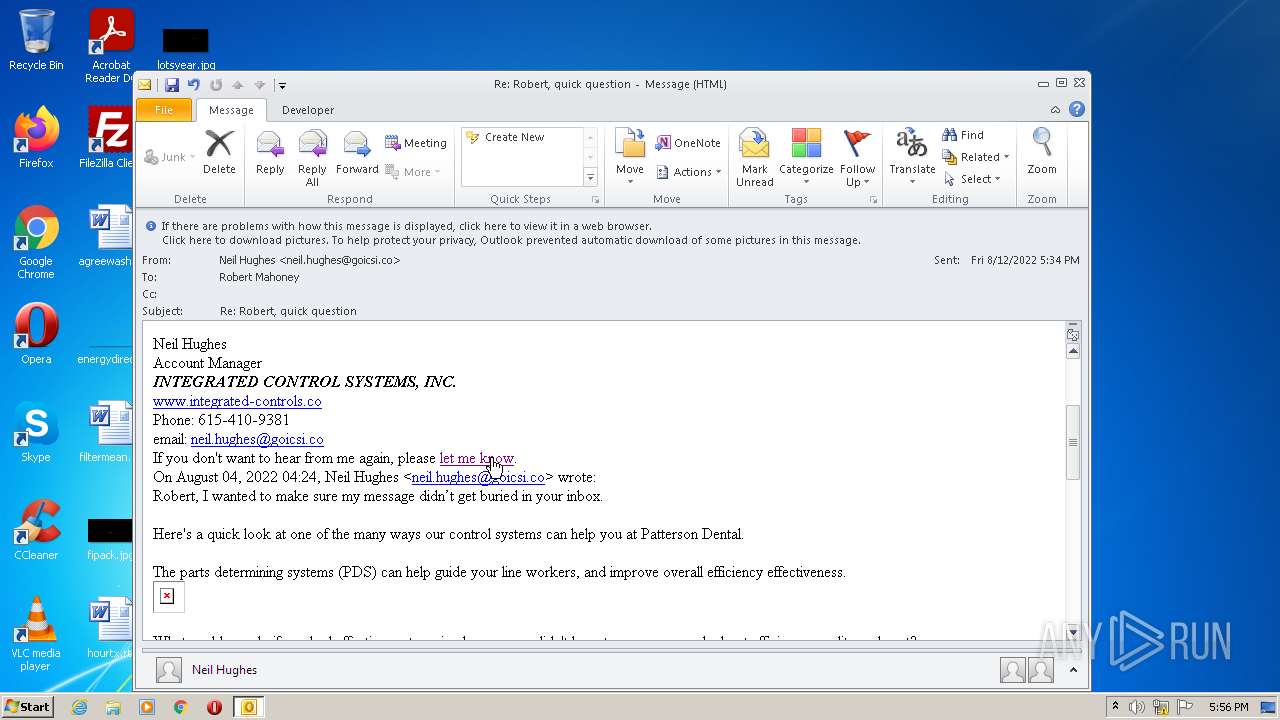
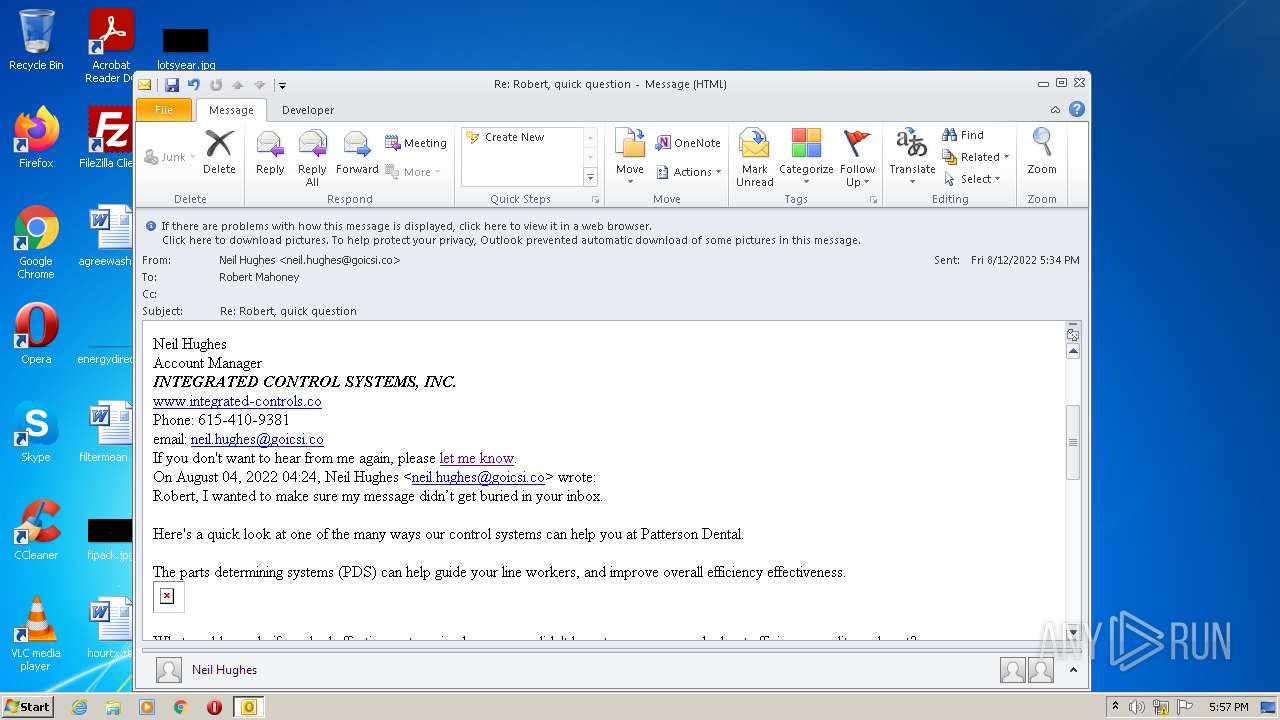
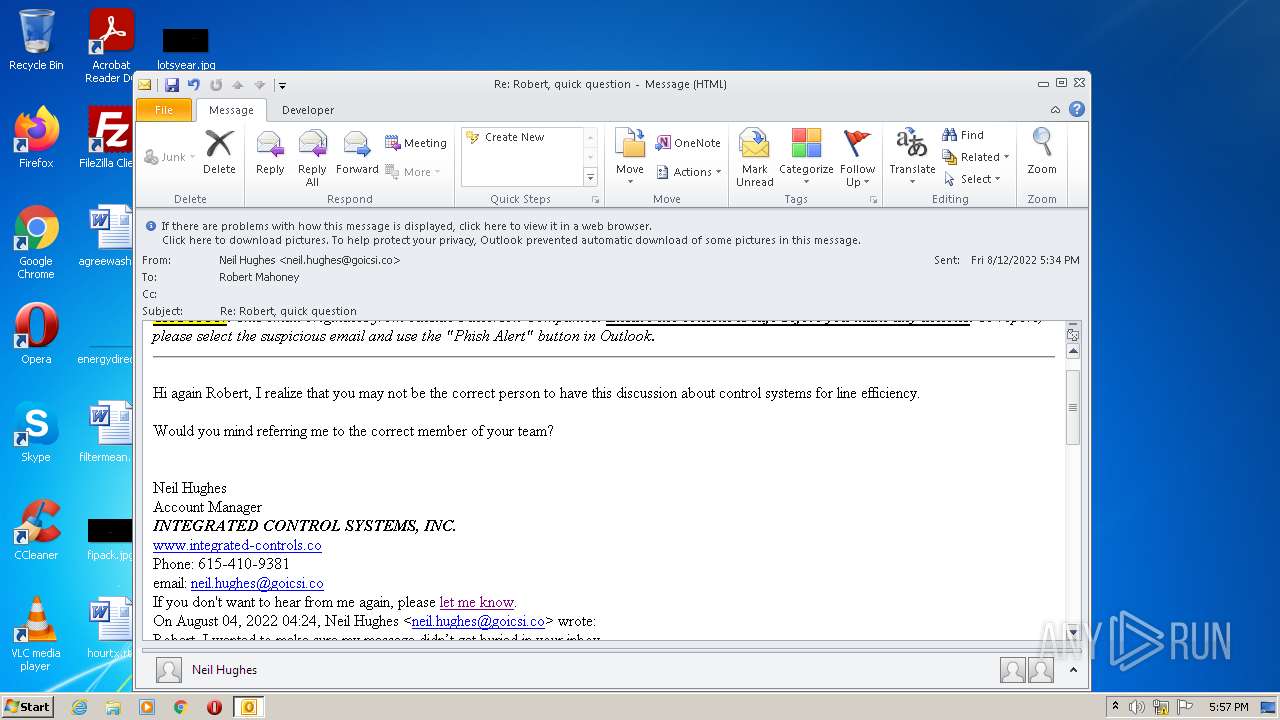
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/73d1d417-9fce-4267-9c48-dbad5feebfa1 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 16:56:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | D58AE978AD0562995113EE96B0E7A02D |
| SHA1: | 1E682DA700B26A528E64FDD27A8327F3E0D0E2A0 |
| SHA256: | 1654A114726B421486B31BD3F23F7806046A58247DB275B78CA66B10E7D2A9B9 |
| SSDEEP: | 384:A0Q/nXIhg88WdufWZSC6PQ+5z9bsdDWXoIxMRyt:wIeWdzZLX+5RbsdDWXo7Ryt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1520)
- iexplore.exe (PID: 3400)
Checks supported languages
- OUTLOOK.EXE (PID: 2544)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2984)
Searches for installed software
- OUTLOOK.EXE (PID: 2544)
Reads the computer name
- OUTLOOK.EXE (PID: 2544)
INFO
Checks supported languages
- iexplore.exe (PID: 1708)
- iexplore.exe (PID: 1520)
- iexplore.exe (PID: 1572)
- iexplore.exe (PID: 3400)
- chrome.exe (PID: 2984)
- chrome.exe (PID: 440)
- chrome.exe (PID: 2880)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 3464)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 2700)
- chrome.exe (PID: 1540)
- chrome.exe (PID: 3276)
- chrome.exe (PID: 828)
- chrome.exe (PID: 1120)
- chrome.exe (PID: 696)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 4028)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 3584)
- chrome.exe (PID: 2840)
- chrome.exe (PID: 2704)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 3396)
- chrome.exe (PID: 2940)
Reads settings of System Certificates
- iexplore.exe (PID: 1708)
- iexplore.exe (PID: 1520)
- iexplore.exe (PID: 1572)
- chrome.exe (PID: 2728)
Checks Windows Trust Settings
- iexplore.exe (PID: 1520)
- iexplore.exe (PID: 1708)
- iexplore.exe (PID: 1572)
Reads the date of Windows installation
- iexplore.exe (PID: 1708)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1708)
Reads internet explorer settings
- iexplore.exe (PID: 1520)
- iexplore.exe (PID: 3400)
Changes settings of System certificates
- iexplore.exe (PID: 1708)
Reads the computer name
- iexplore.exe (PID: 1572)
- iexplore.exe (PID: 3400)
- chrome.exe (PID: 2984)
- chrome.exe (PID: 2880)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 828)
- iexplore.exe (PID: 1708)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 3396)
- iexplore.exe (PID: 1520)
Application launched itself
- iexplore.exe (PID: 1572)
- chrome.exe (PID: 2984)
- iexplore.exe (PID: 1708)
Changes internet zones settings
- iexplore.exe (PID: 1572)
- iexplore.exe (PID: 1708)
Manual execution by user
- chrome.exe (PID: 2984)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
65
Monitored processes
26
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x67e2d988,0x67e2d998,0x67e2d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 696 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15862119321351132588,2861766345130604034,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3100 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1044,15862119321351132588,2861766345130604034,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2944 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15862119321351132588,2861766345130604034,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3320 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1708 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1044,15862119321351132588,2861766345130604034,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2816 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
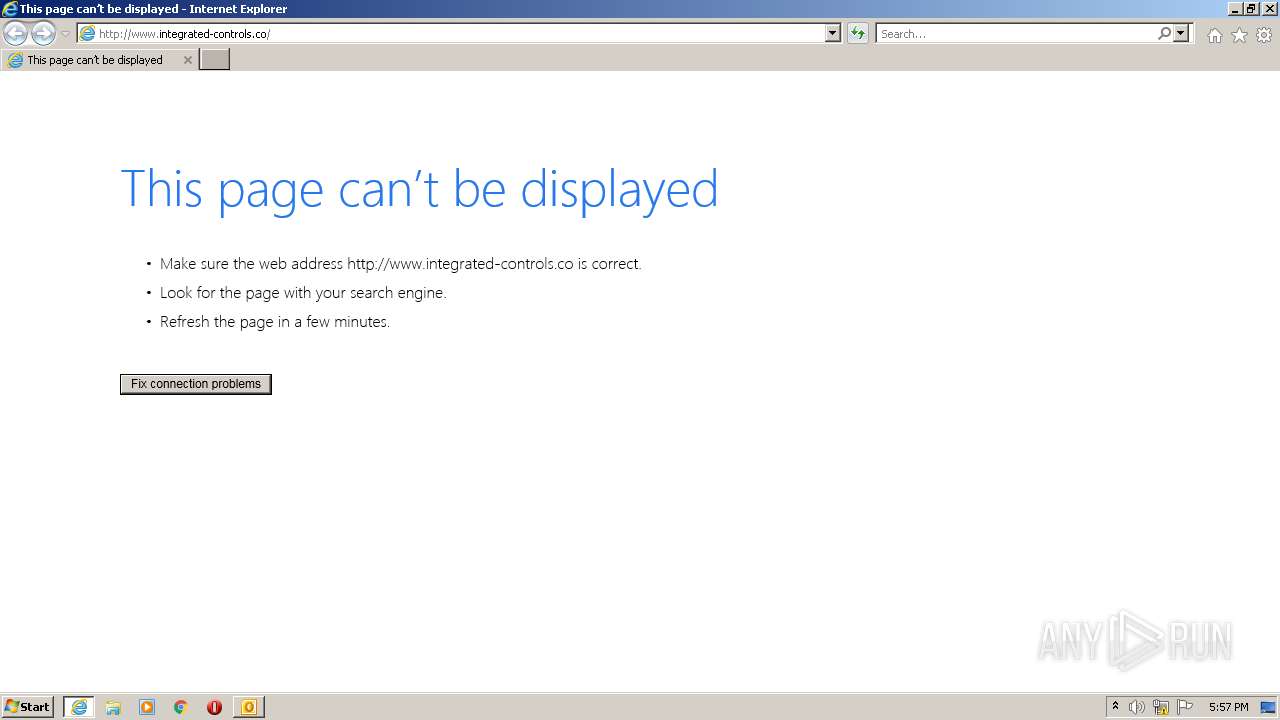
| 1572 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.integrated-controls.co/ | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
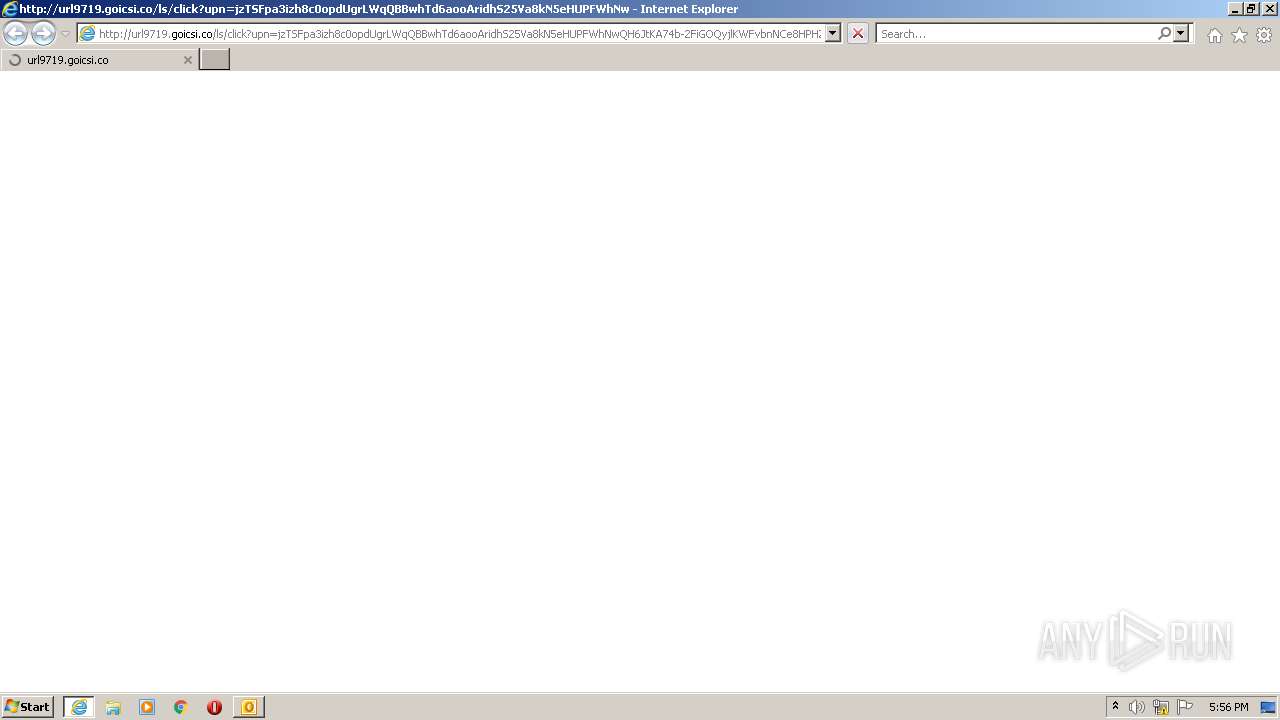
| 1708 | "C:\Program Files\Internet Explorer\iexplore.exe" http://url9719.goicsi.co/ls/click?upn=jzTSFpa3izh8c0opdUgrLWqQBBwhTd6aooAridhS25Va8kN5eHUPFWhNwQH6JtKA74b-2FiGOQyjlKWFvbnNCe8HPHZ5HfEkfwwVu-2BCR-2FRqWY-3DIcmT_62i4ZQidJAut2vx9TYnJ86vRZt2riAS8bWxQdi-2FOrCjKEBUdFJdEoXhzxWuyr4s1l8N-2FYWbaE7gS9FEFYs4jR7m9W53vCJHuY4g7026pKValZNBqu3vP1JwAxEPVb9ygNM8HyJJmE8DhHDs6cr6BJKSIgy5T7yLlejf9QK4or54zUpELD6ZXPdm9-2FgYd-2FtB-2F-2B3oroDHM-2BaOD6NOOXGac-2BEU25Y-2BgrqLfMK0FbPYXP9KU4G6ubb95Z-2FZYiCeXEgsy-2FtTjIZgmcyxW5vnkX1yJ6pXqObV6tSxTIx-2FACR5t0io9GRM2HwfTL5fJePm44lOCEhg80L0UMGcngltLGAtmqViPiZIH1-2B9yXoMMS2bOSGICla11tSJ9FQ91olmUAUL4ntUEtRxru7wCRsn7WdOpvNrLUVB49oq-2Ba7Tp-2Bgww4LCNXuIREQCLlXQXxWpwQrSh | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2544 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\phish_alert_sp2_2.0.0.0.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,15862119321351132588,2861766345130604034,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3440 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
36 298
Read events
35 389
Write events
883
Delete events
26
Modification events
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2544) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
157
Text files
126
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2544 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5C40.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2544 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2544 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2544 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA010.tmp | cat | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EC40F66EB1D092C00465FB5E347A57AC | der | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA00F.tmp | compressed | |
MD5:— | SHA256:— | |||
| 1520 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
63
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2544 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2728 | chrome.exe | GET | 301 | 198.12.227.3:80 | http://www.integrated-controls.com/ | US | — | — | unknown |
1520 | iexplore.exe | GET | 302 | 167.89.118.83:80 | http://url9719.goicsi.co/ls/click?upn=jzTSFpa3izh8c0opdUgrLWqQBBwhTd6aooAridhS25Va8kN5eHUPFWhNwQH6JtKA74b-2FiGOQyjlKWFvbnNCe8HPHZ5HfEkfwwVu-2BCR-2FRqWY-3DIcmT_62i4ZQidJAut2vx9TYnJ86vRZt2riAS8bWxQdi-2FOrCjKEBUdFJdEoXhzxWuyr4s1l8N-2FYWbaE7gS9FEFYs4jR7m9W53vCJHuY4g7026pKValZNBqu3vP1JwAxEPVb9ygNM8HyJJmE8DhHDs6cr6BJKSIgy5T7yLlejf9QK4or54zUpELD6ZXPdm9-2FgYd-2FtB-2F-2B3oroDHM-2BaOD6NOOXGac-2BEU25Y-2BgrqLfMK0FbPYXP9KU4G6ubb95Z-2FZYiCeXEgsy-2FtTjIZgmcyxW5vnkX1yJ6pXqObV6tSxTIx-2FACR5t0io9GRM2HwfTL5fJePm44lOCEhg80L0UMGcngltLGAtmqViPiZIH1-2B9yXoMMS2bOSGICla11tSJ9FQ91olmUAUL4ntUEtRxru7wCRsn7WdOpvNrLUVB49oq-2Ba7Tp-2Bgww4LCNXuIREQCLlXQXxWpwQrSh | US | html | 79 b | suspicious |
1520 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b7df5e784415a40e | US | compressed | 60.2 Kb | whitelisted |
1520 | iexplore.exe | GET | 200 | 2.16.186.19:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNUrtaAdpqYQo3ahNQJaw6Ilw%3D%3D | unknown | der | 503 b | shared |
1708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
1708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1520 | iexplore.exe | GET | 200 | 96.16.145.230:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
2728 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
1520 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?84f6925c03c96cc7 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2544 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1520 | iexplore.exe | 167.89.118.83:80 | url9719.goicsi.co | SendGrid, Inc. | US | suspicious |
1520 | iexplore.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
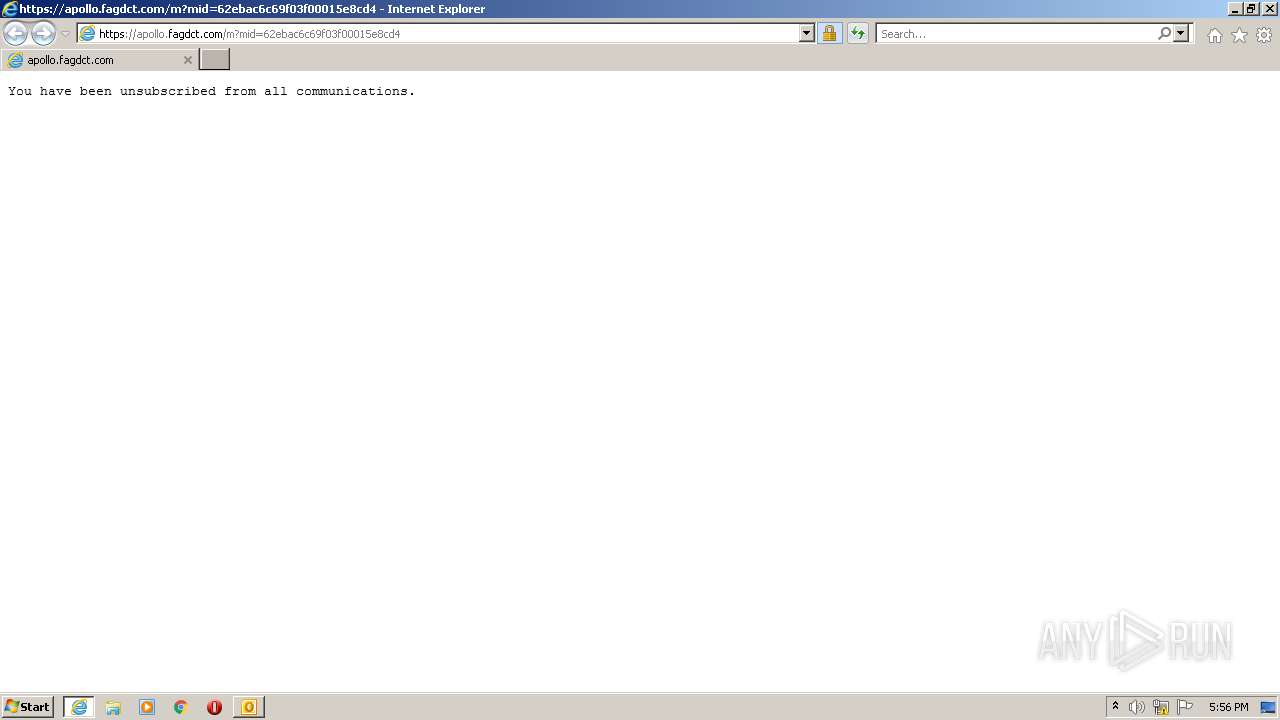
1520 | iexplore.exe | 34.122.213.224:443 | apollo.fagdct.com | — | US | suspicious |
1520 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
1708 | iexplore.exe | 34.122.213.224:443 | apollo.fagdct.com | — | US | suspicious |
1520 | iexplore.exe | 2.16.186.19:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
1708 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1708 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1572 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
url9719.goicsi.co |
| suspicious |
apollo.fagdct.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ocsp.digicert.com |
| whitelisted |
www.integrated-controls.co |
| unknown |