analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
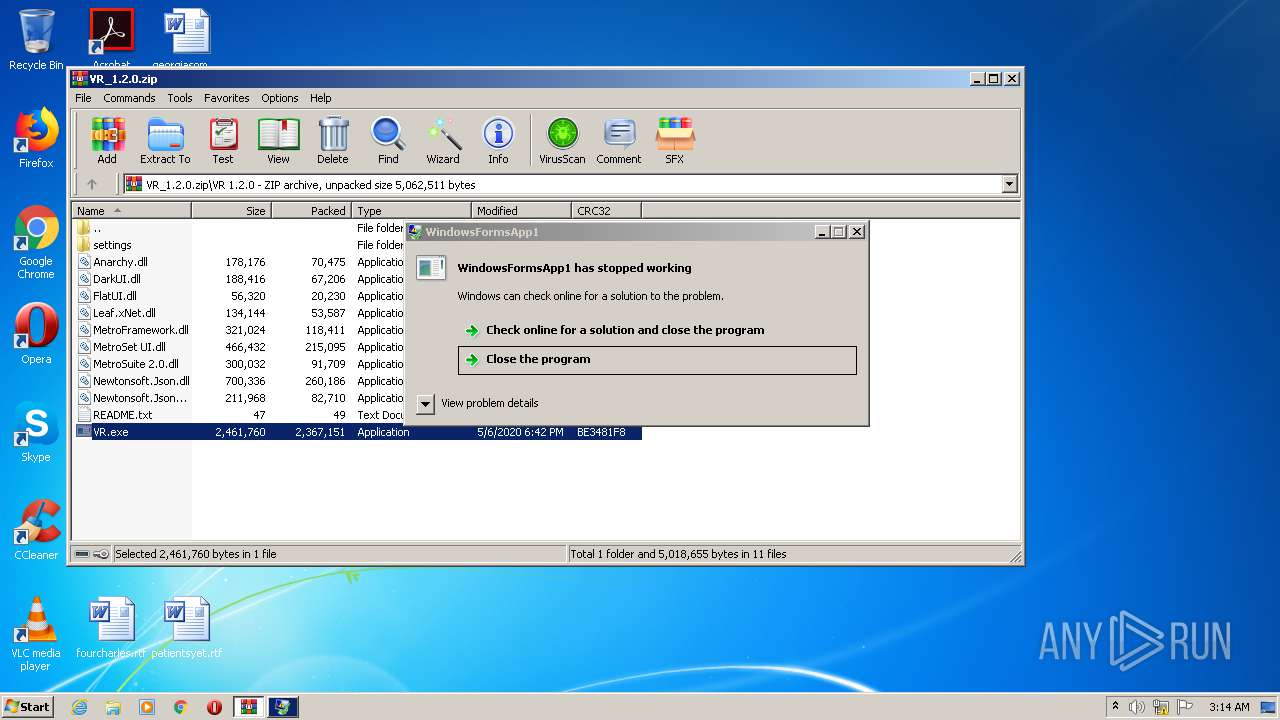
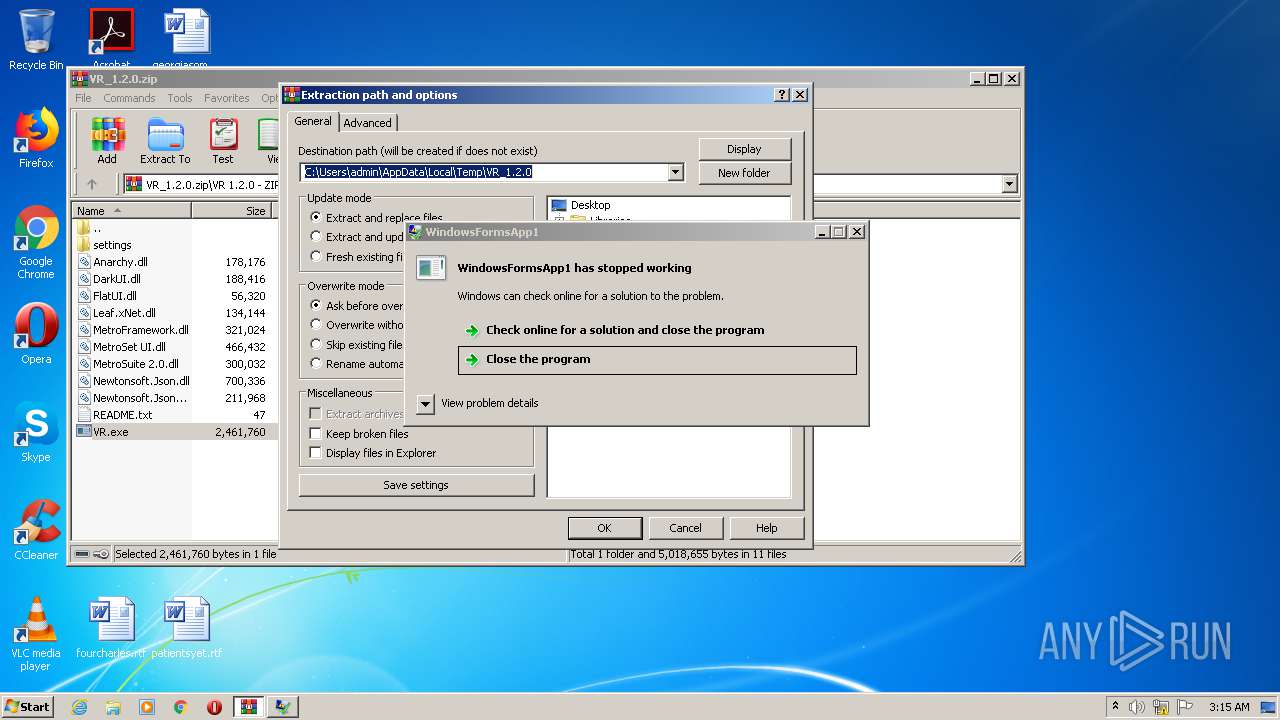
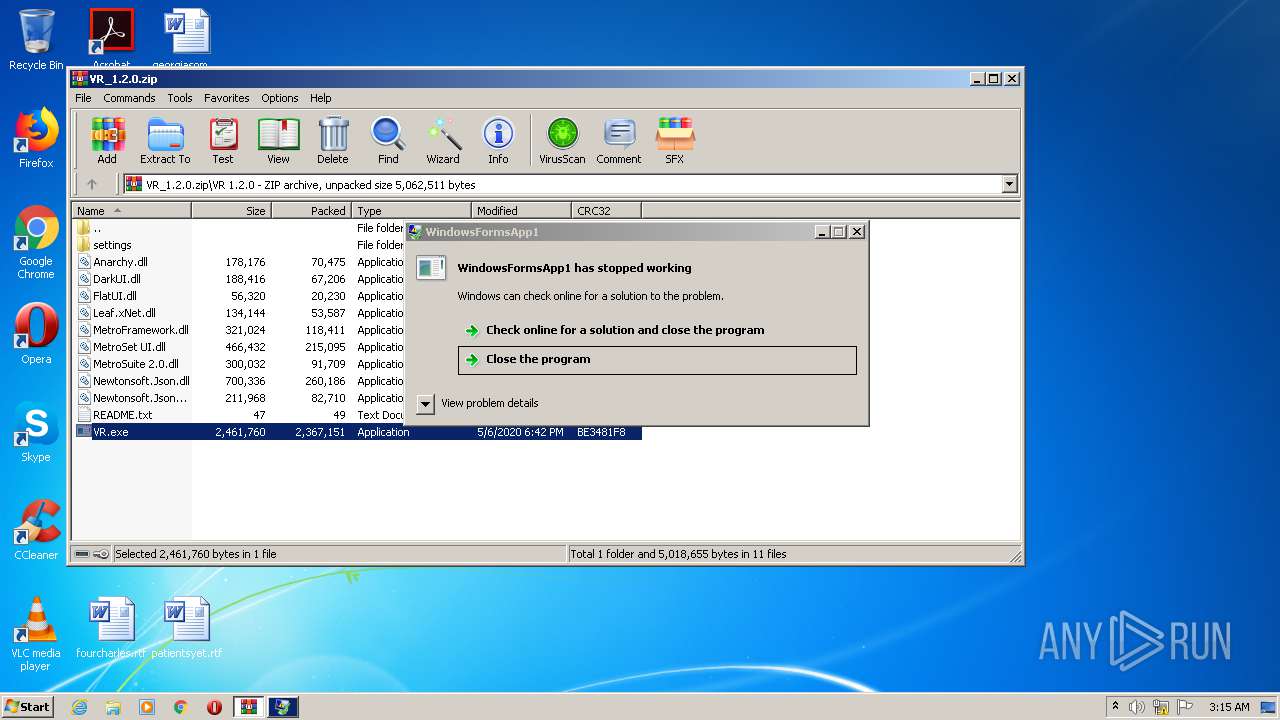
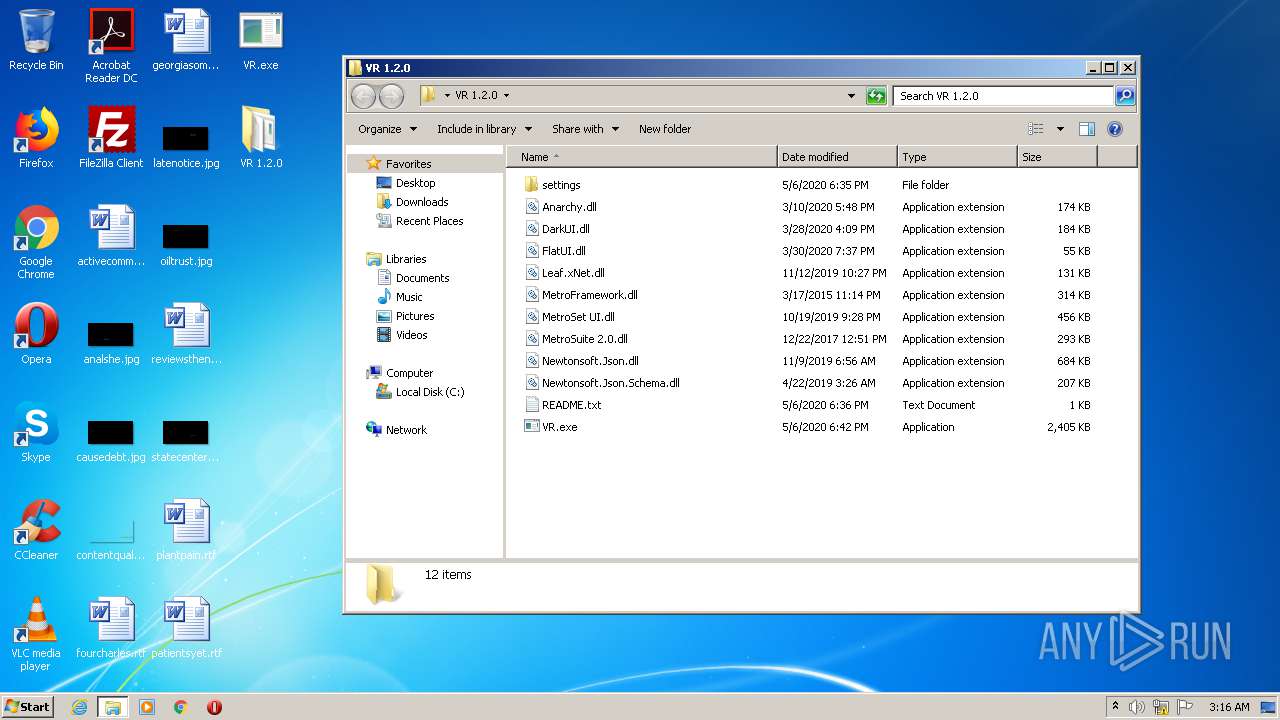
| File name: | VR_1.2.0.zip |
| Full analysis: | https://app.any.run/tasks/83a54e0f-88c2-45c2-96ee-57d210b235f7 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 02:14:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 775DEEDB30E5C52C90F708D7284FB85B |
| SHA1: | 87A724A186925326CD839BF48A2F545A14A6602C |
| SHA256: | 1645F945BF477252FE1B4D89EA31CA7A2A8E7B26A08855A35FD70ACE15C8ABA8 |
| SSDEEP: | 98304:mcOtX8surz4S1BnFzl4D3WPxAkqTzRFWhmN0N:HOtXsrcS1BnP47mxAPTSx |
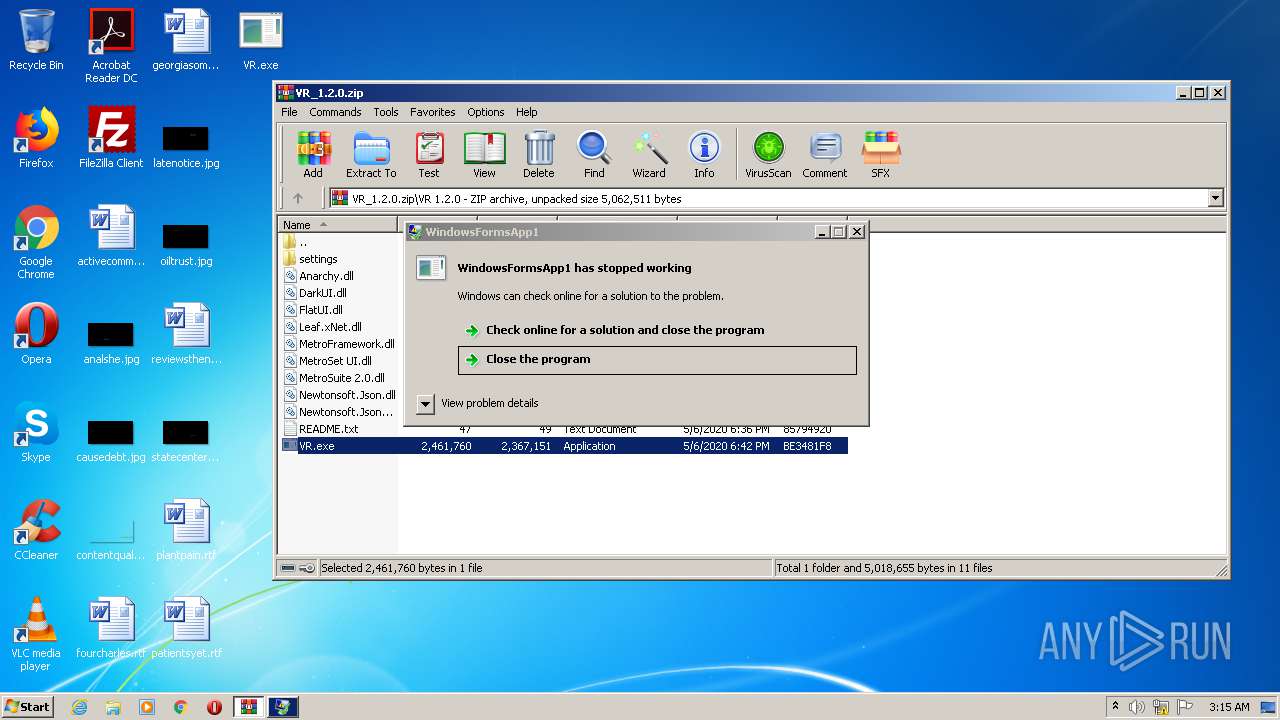
MALICIOUS
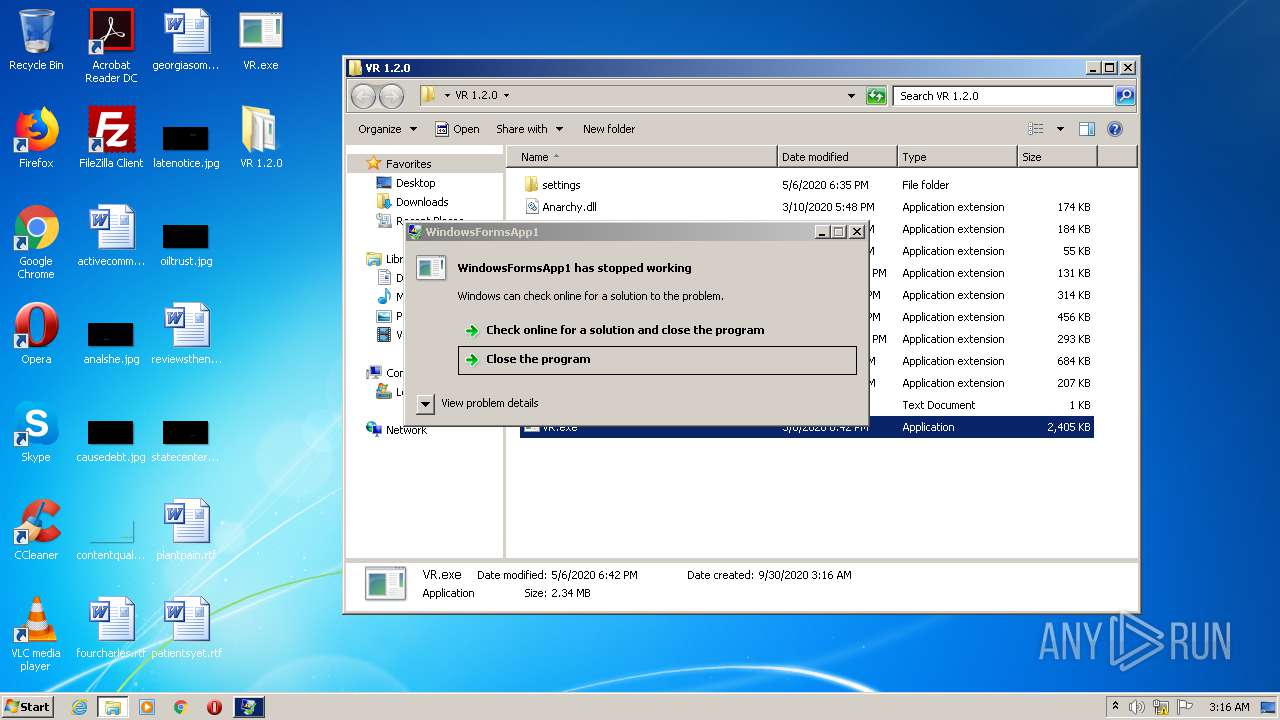
Application was dropped or rewritten from another process
- VR.exe (PID: 972)
- VR.exe (PID: 3180)
- VR.exe (PID: 2676)
- VR.exe (PID: 928)
- VR.exe (PID: 3536)
Loads dropped or rewritten executable
- VR.exe (PID: 3180)
- VR.exe (PID: 972)
- VR.exe (PID: 2676)
- SearchProtocolHost.exe (PID: 2468)
- VR.exe (PID: 928)
- VR.exe (PID: 3536)
SUSPICIOUS
Creates files in the user directory
- rundll32.exe (PID: 2308)
Reads Internet Cache Settings
- rundll32.exe (PID: 2308)
- rundll32.exe (PID: 3840)
- rundll32.exe (PID: 3088)
- rundll32.exe (PID: 3316)
- rundll32.exe (PID: 2208)
Uses RUNDLL32.EXE to load library
- VR.exe (PID: 3180)
- VR.exe (PID: 972)
- VR.exe (PID: 2676)
- VR.exe (PID: 928)
- VR.exe (PID: 3536)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3656)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 3480)
- VR.exe (PID: 928)
- VR.exe (PID: 3536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:05:06 19:38:13 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | VR 1.2.0/ |
Total processes
57
Monitored processes
13
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3656 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\VR_1.2.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | |
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 | ||||
| 3180 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\VR.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\VR.exe | WinRAR.exe | |
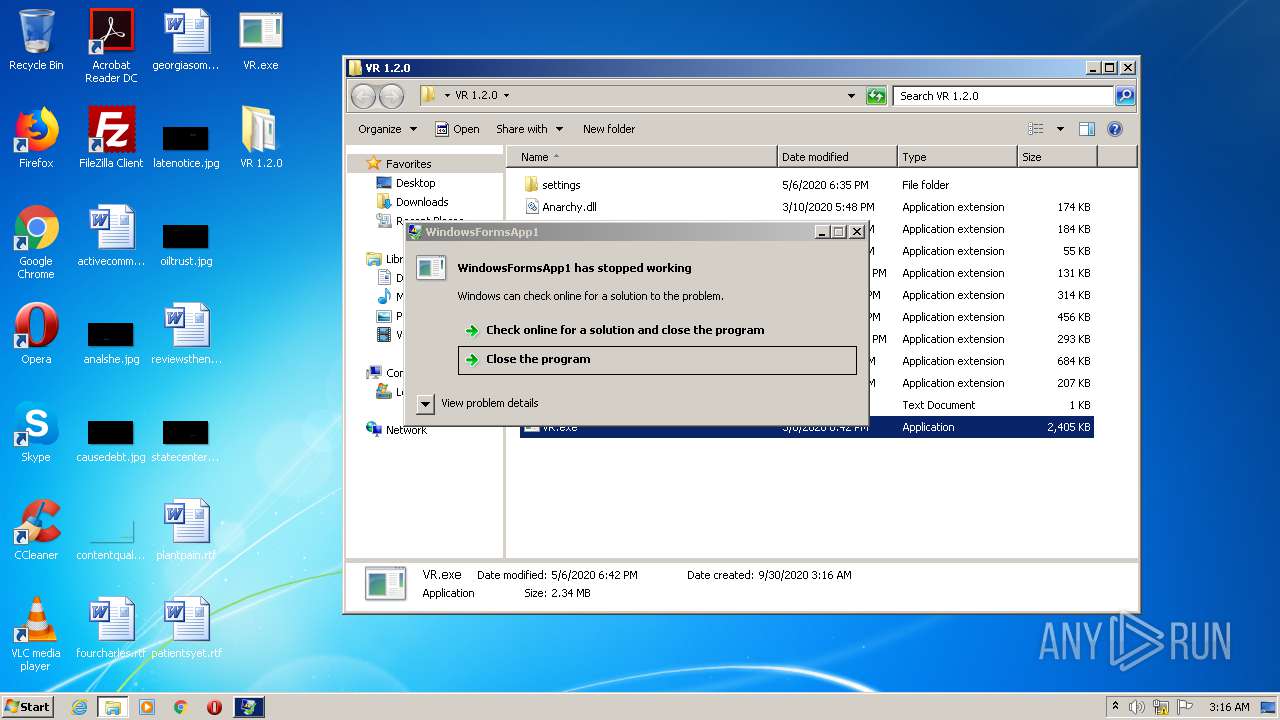
User: admin Integrity Level: MEDIUM Description: WindowsFormsApp1 Exit code: 3762504530 Version: 1.0.0.0 | ||||
| 2308 | C:\Windows\system32\rundll32.exe C:\Windows\system32\gameux.dll,GameUXShim {c69b7a85-0b83-401b-881a-3df6a3934000};C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\VR.exe;3180 | C:\Windows\system32\rundll32.exe | VR.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 972 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.43650\VR 1.2.0\VR.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.43650\VR 1.2.0\VR.exe | WinRAR.exe | |
User: admin Integrity Level: MEDIUM Description: WindowsFormsApp1 Exit code: 3762504530 Version: 1.0.0.0 | ||||
| 3088 | C:\Windows\system32\rundll32.exe C:\Windows\system32\gameux.dll,GameUXShim {c69b7a85-0b83-401b-881a-3df6a3934000};C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.43650\VR 1.2.0\VR.exe;972 | C:\Windows\system32\rundll32.exe | VR.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2676 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.47041\VR 1.2.0\VR.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.47041\VR 1.2.0\VR.exe | WinRAR.exe | |
User: admin Integrity Level: MEDIUM Description: WindowsFormsApp1 Exit code: 3762504530 Version: 1.0.0.0 | ||||
| 3840 | C:\Windows\system32\rundll32.exe C:\Windows\system32\gameux.dll,GameUXShim {c69b7a85-0b83-401b-881a-3df6a3934000};C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.47041\VR 1.2.0\VR.exe;2676 | C:\Windows\system32\rundll32.exe | VR.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2468 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Version: 7.00.7600.16385 (win7_rtm.090713-1255) | ||||
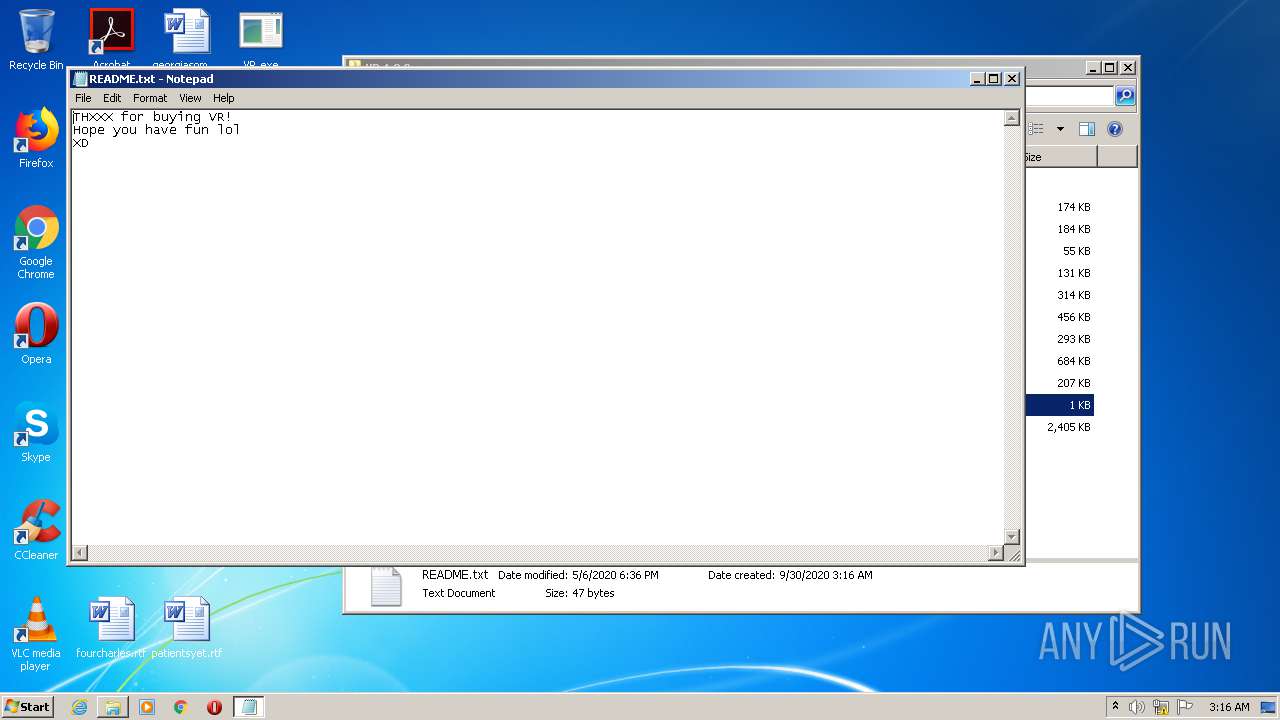
| 3480 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\VR 1.2.0\README.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 928 | "C:\Users\admin\Desktop\VR 1.2.0\VR.exe" | C:\Users\admin\Desktop\VR 1.2.0\VR.exe | explorer.exe | |
User: admin Integrity Level: MEDIUM Description: WindowsFormsApp1 Exit code: 3762504530 Version: 1.0.0.0 | ||||
Total events
2 438
Read events
2 358
Write events
0
Delete events
0
Modification events
Executable files
38
Suspicious files
0
Text files
8
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\Anarchy.dll | executable | |
MD5:8D5437EA6D950E82FBB8EEC088DE8D3E | SHA256:E6254AE1C6F7906C874897570DB4E8AEFF95091049056557AA304A1B4FC1E171 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.43650\VR 1.2.0\Anarchy.dll | executable | |
MD5:8D5437EA6D950E82FBB8EEC088DE8D3E | SHA256:E6254AE1C6F7906C874897570DB4E8AEFF95091049056557AA304A1B4FC1E171 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\MetroSuite 2.0.dll | executable | |
MD5:5EE9F67FE5FC7F5E12452CCC1F264388 | SHA256:00CEC7945BE290CF35A2DA6A9C5C3E3630D454D32EBC34B52D6EA2CB2F85DB66 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\settings\proxies.txt | text | |
MD5:E55C50FECB0B288E43B6EE4A23CAF191 | SHA256:D38AF3692CB065DCABD935EDC535BC6D3BF8041F924EF64AEBDBB451BD1E7F9D | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\README.txt | text | |
MD5:EDFDA6A3AFC9FD989046C777C5E198C0 | SHA256:505BD46C798D79BEC2B4C7131F383DDA8C0DABC5223D2C75FB8A328C8E624B7D | |||
| 2308 | rundll32.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\GameExplorer\{408E01D4-C485-4513-B73F-A647AE4071C4}\PlayTasks\0\Play.lnk | lnk | |
MD5:C9A1C7911E0F08B2E5B3377BE99B2DB1 | SHA256:6B4ED46F6540FC9BE946147AD31E2F8C22BFF71C230DD8C9ADB9D8D51149C025 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\DarkUI.dll | executable | |
MD5:B6B8464FF0134F035F0DBEF4130A36BB | SHA256:4A6CE472A481560F3004FD4FD19952F96E1F8F96078168166792450CA005EA33 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.43650\VR 1.2.0\MetroFramework.dll | executable | |
MD5:EADE3A0C93F4A4539CBFB7DA94632ABF | SHA256:FFBECA7CAF4AF85AD5A1245C6D91296EFC2B24A28CC95A5AF31DF1660FF9F895 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\MetroFramework.dll | executable | |
MD5:EADE3A0C93F4A4539CBFB7DA94632ABF | SHA256:FFBECA7CAF4AF85AD5A1245C6D91296EFC2B24A28CC95A5AF31DF1660FF9F895 | |||
| 3656 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3656.42328\VR 1.2.0\FlatUI.dll | executable | |
MD5:B63F5C816F8799857B9B8F95B6E2A9B0 | SHA256:058C926A8818479B06AB9402F2A6C85EB0F64626C2956102D6699AD413AFE2FB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
11
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3088 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
3840 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
2676 | VR.exe | GET | 404 | 145.14.145.228:80 | http://voidata.000webhostapp.com/voidraider/newestVersion | US | xml | 345 b | shared |
3840 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
3840 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
928 | VR.exe | GET | 404 | 145.14.145.134:80 | http://voidata.000webhostapp.com/voidraider/newestVersion | US | xml | 345 b | shared |
3316 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
3316 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
972 | VR.exe | GET | 404 | 145.14.145.228:80 | http://voidata.000webhostapp.com/voidraider/newestVersion | US | xml | 345 b | shared |
2208 | rundll32.exe | GET | 404 | 104.111.238.86:80 | http://go.microsoft.com/fwlink?linkid=30219&locale=en-US&clientType=VISTA_GAMES&clientVersion=6.1.2 | NL | xml | 345 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2308 | rundll32.exe | 104.111.238.86:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3088 | rundll32.exe | 104.111.238.86:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3840 | rundll32.exe | 104.111.238.86:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3180 | VR.exe | 145.14.145.228:80 | voidata.000webhostapp.com | Hostinger International Limited | US | shared |
2676 | VR.exe | 145.14.145.228:80 | voidata.000webhostapp.com | Hostinger International Limited | US | shared |
972 | VR.exe | 145.14.145.228:80 | voidata.000webhostapp.com | Hostinger International Limited | US | shared |
— | — | 104.111.238.86:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3316 | rundll32.exe | 104.111.238.86:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3996 | WerFault.exe | 52.184.220.162:80 | watson.microsoft.com | Microsoft Corporation | US | suspicious |
928 | VR.exe | 145.14.145.134:80 | voidata.000webhostapp.com | Hostinger International Limited | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
voidata.000webhostapp.com |
| shared |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
3996 | WerFault.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
3996 | WerFault.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |