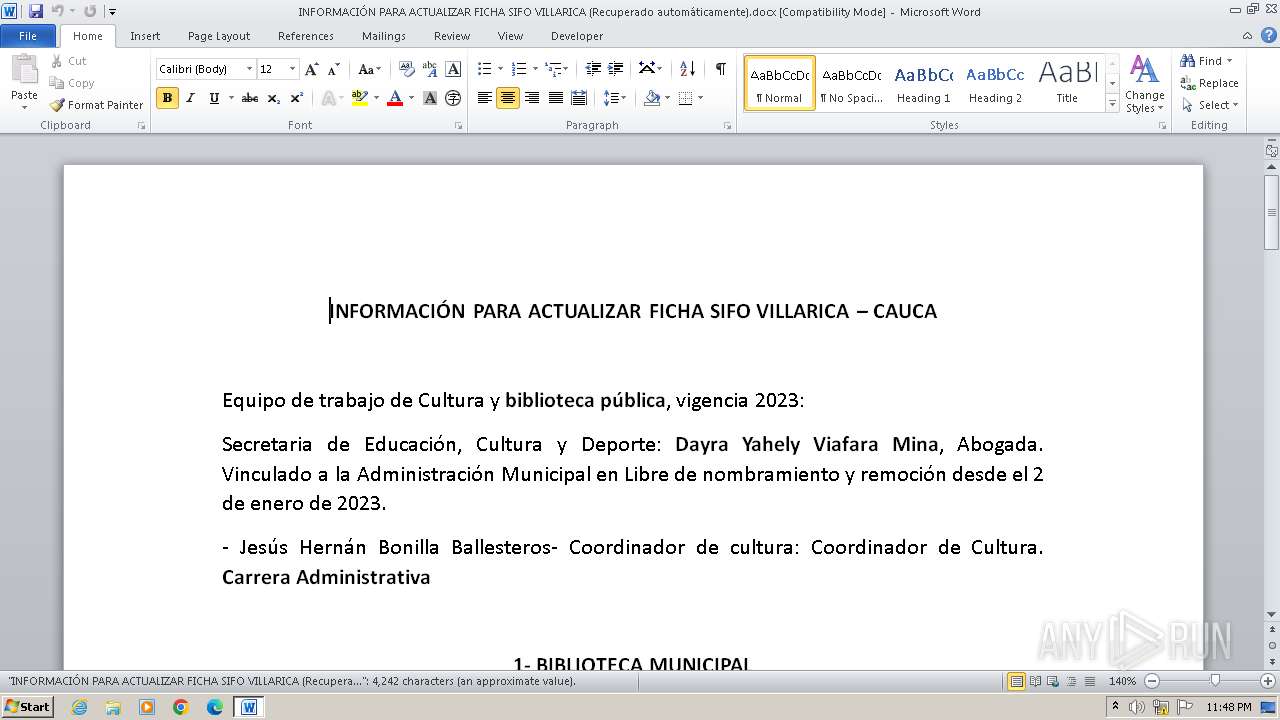
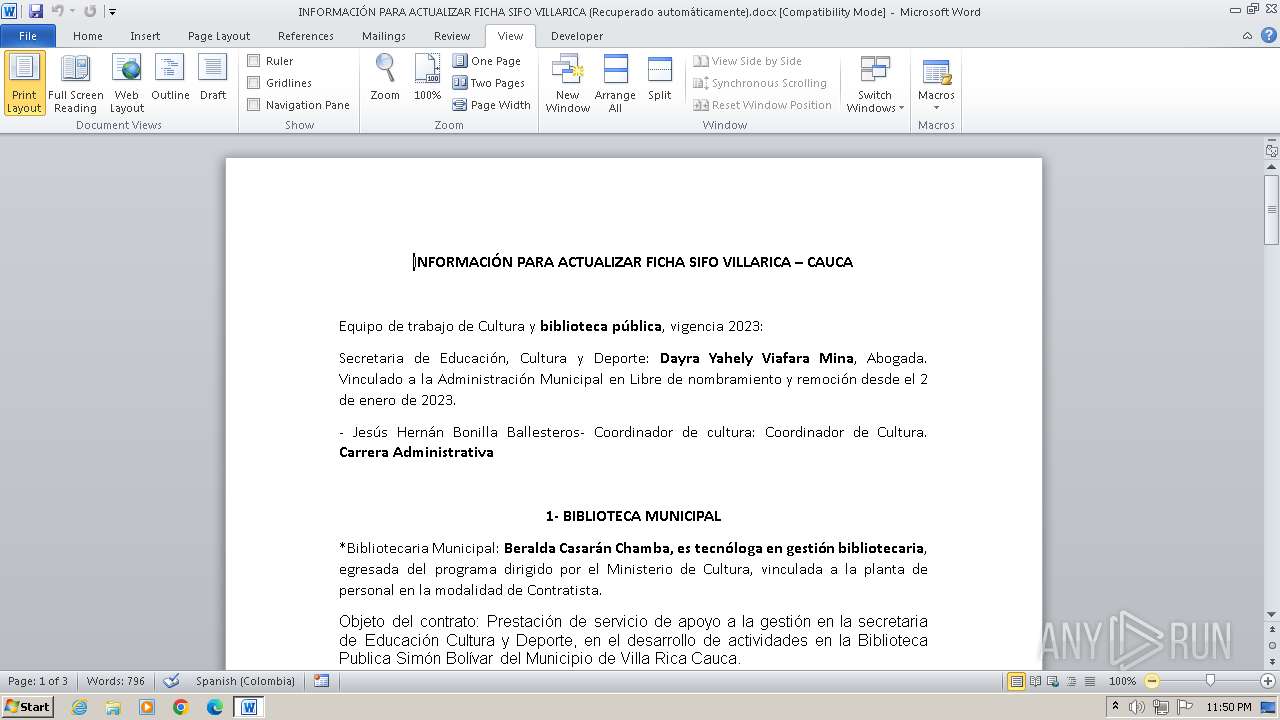
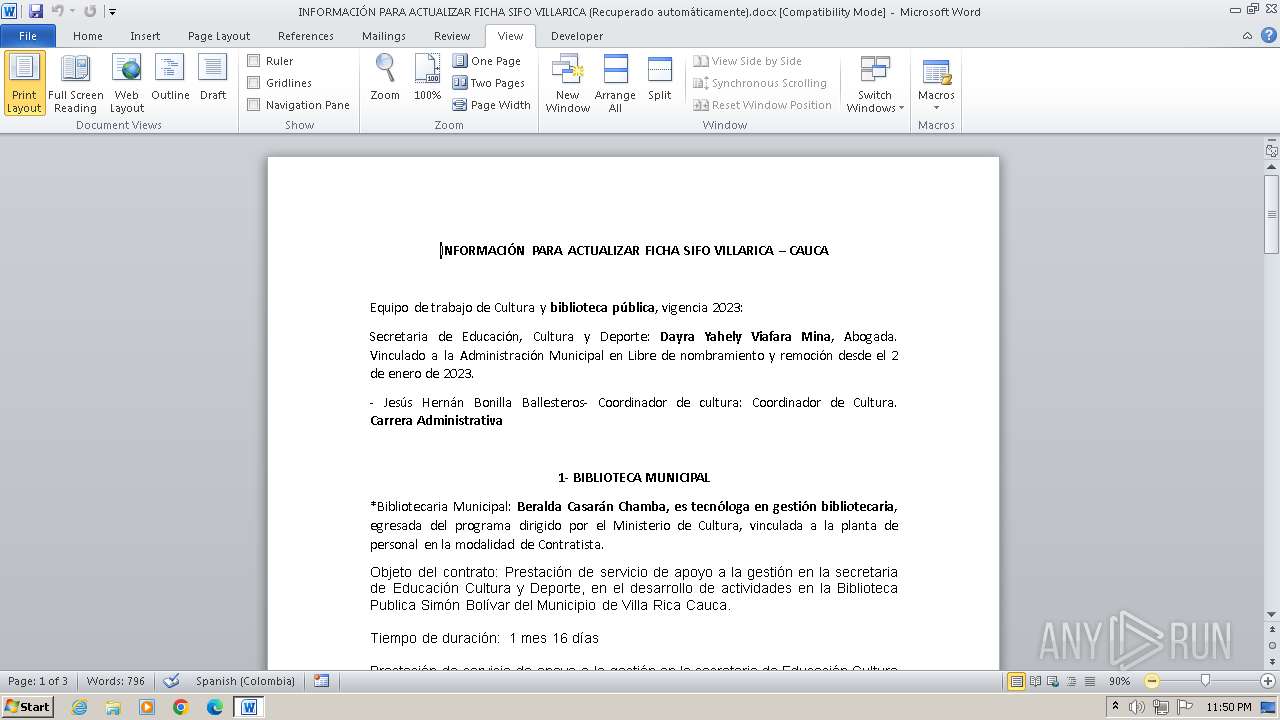
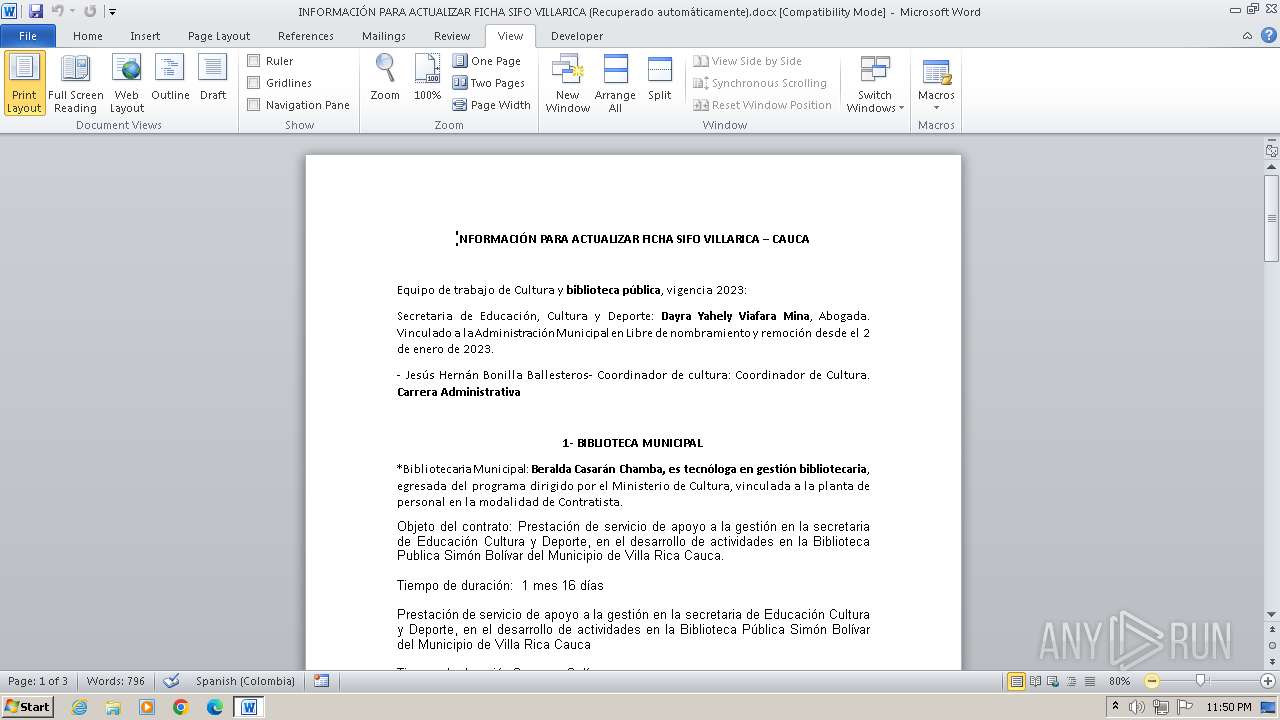
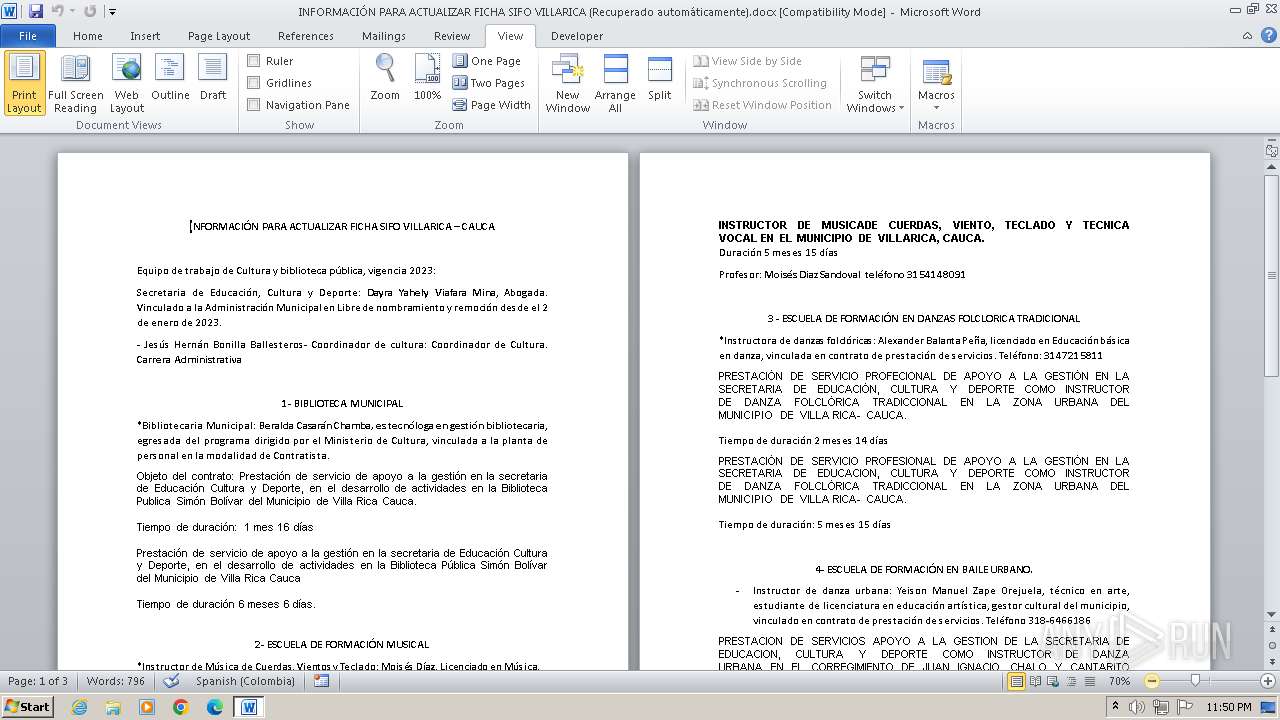
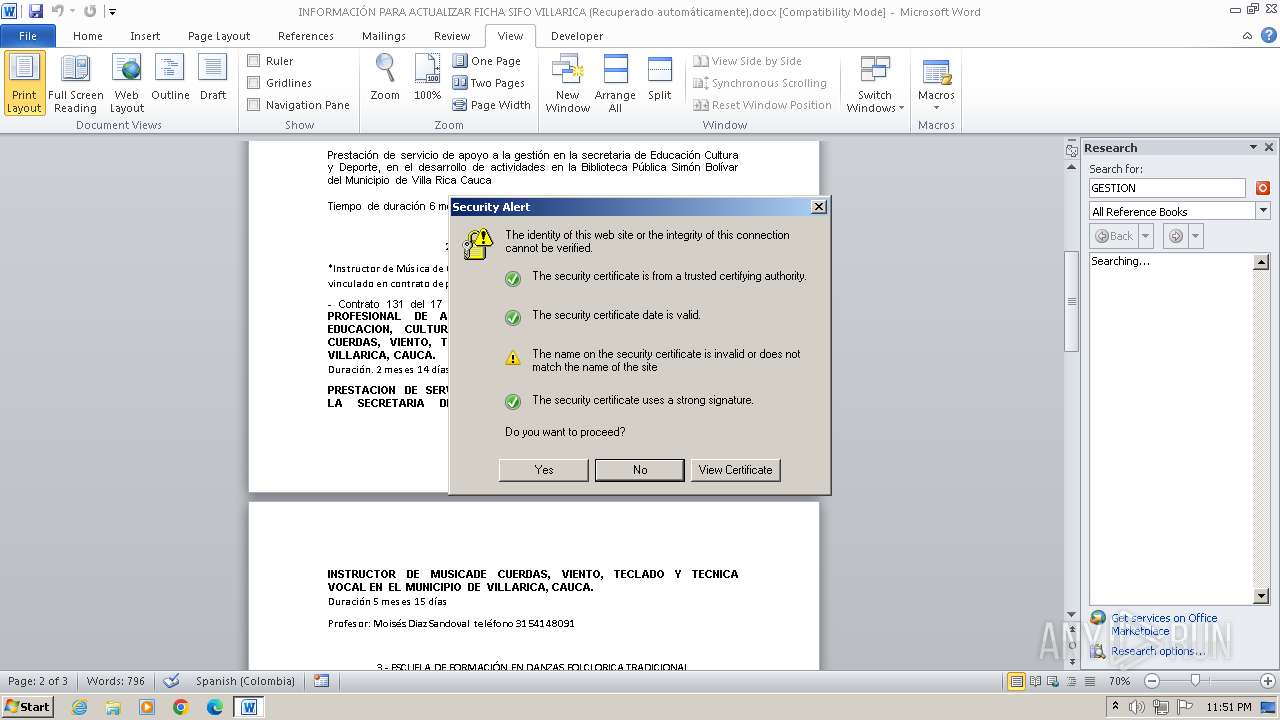
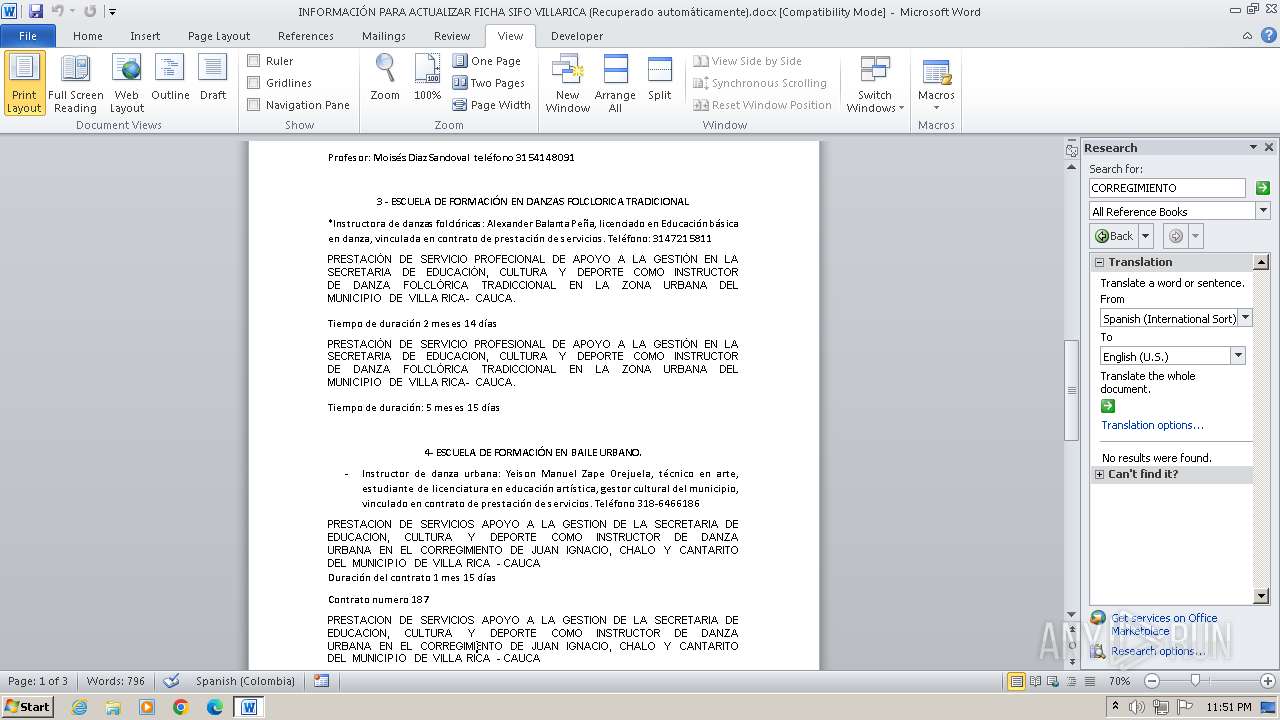
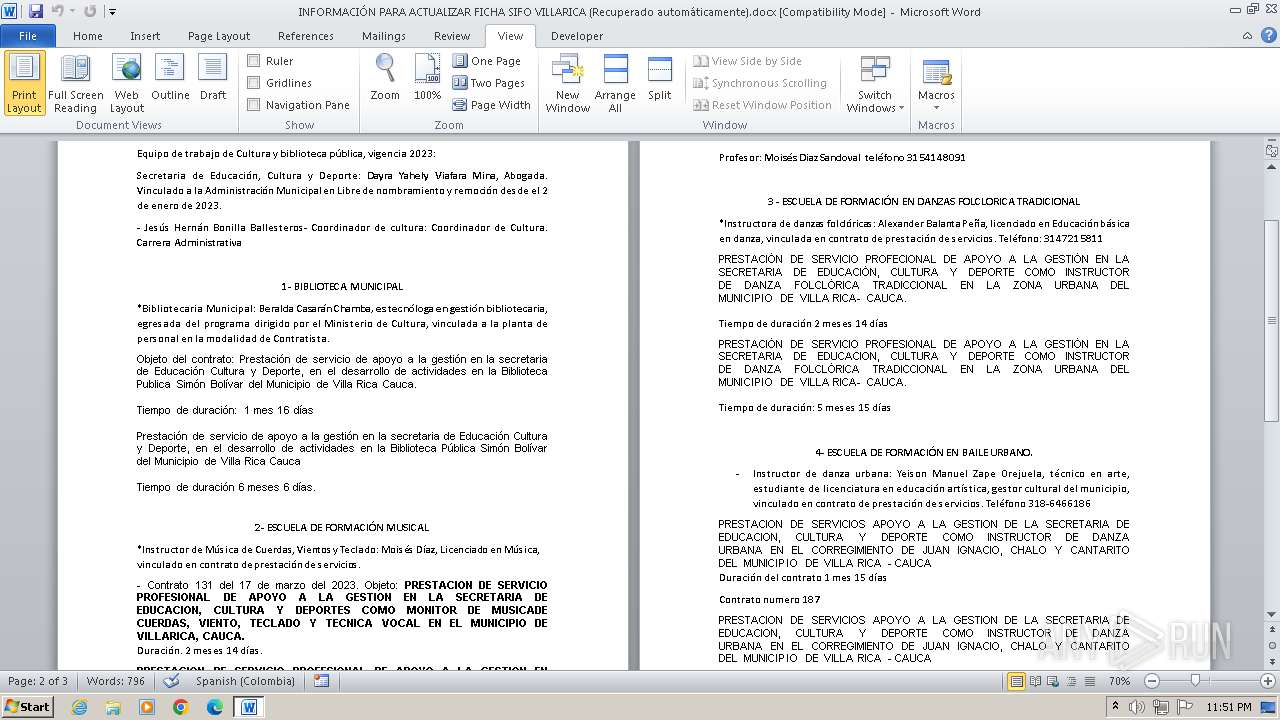
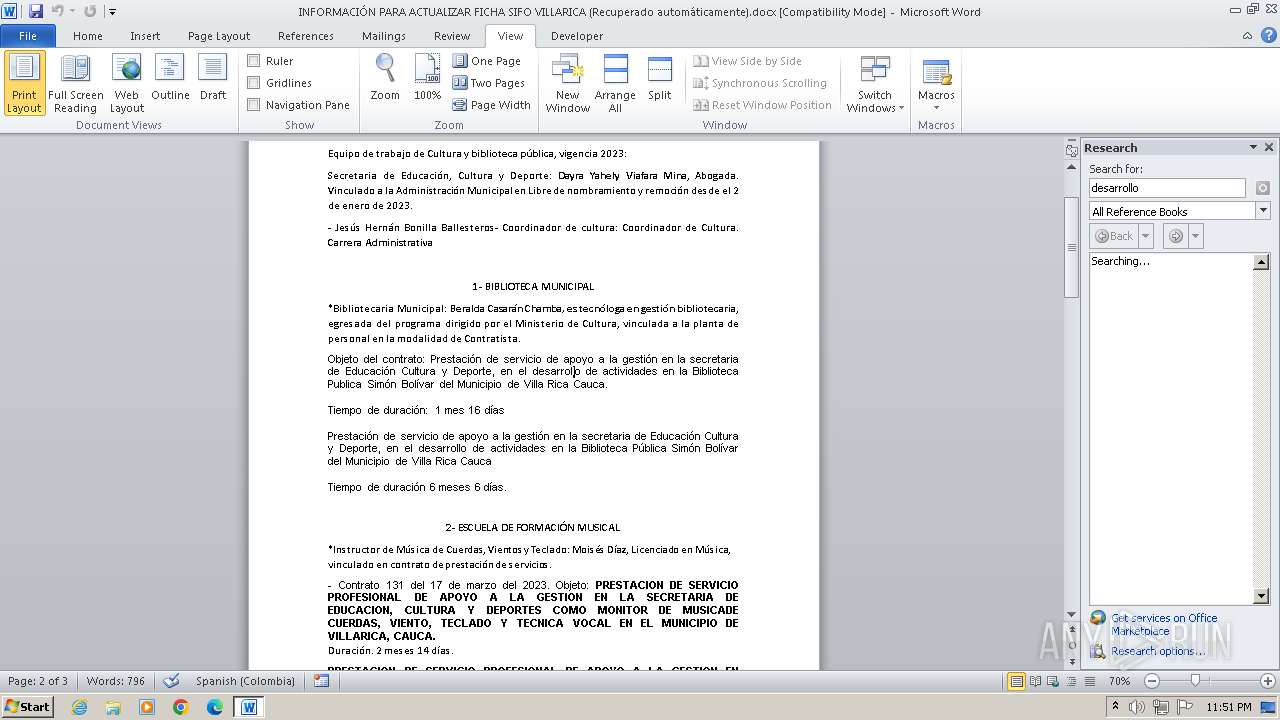
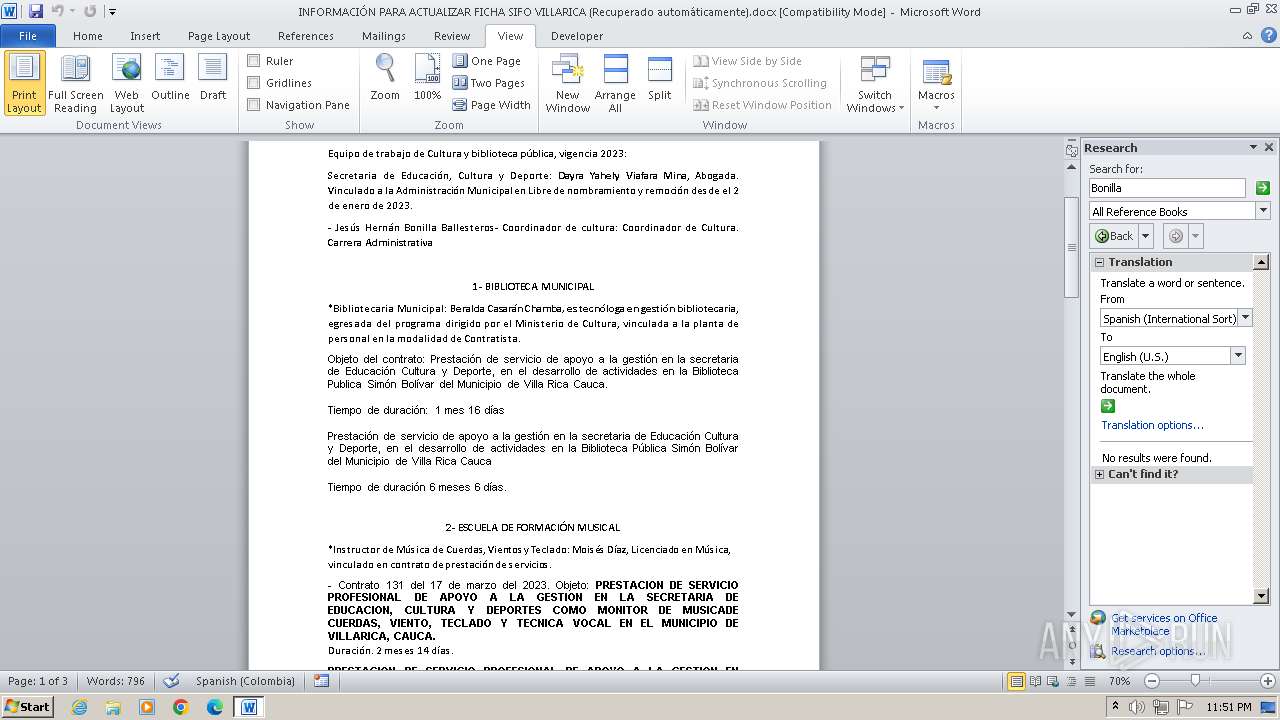
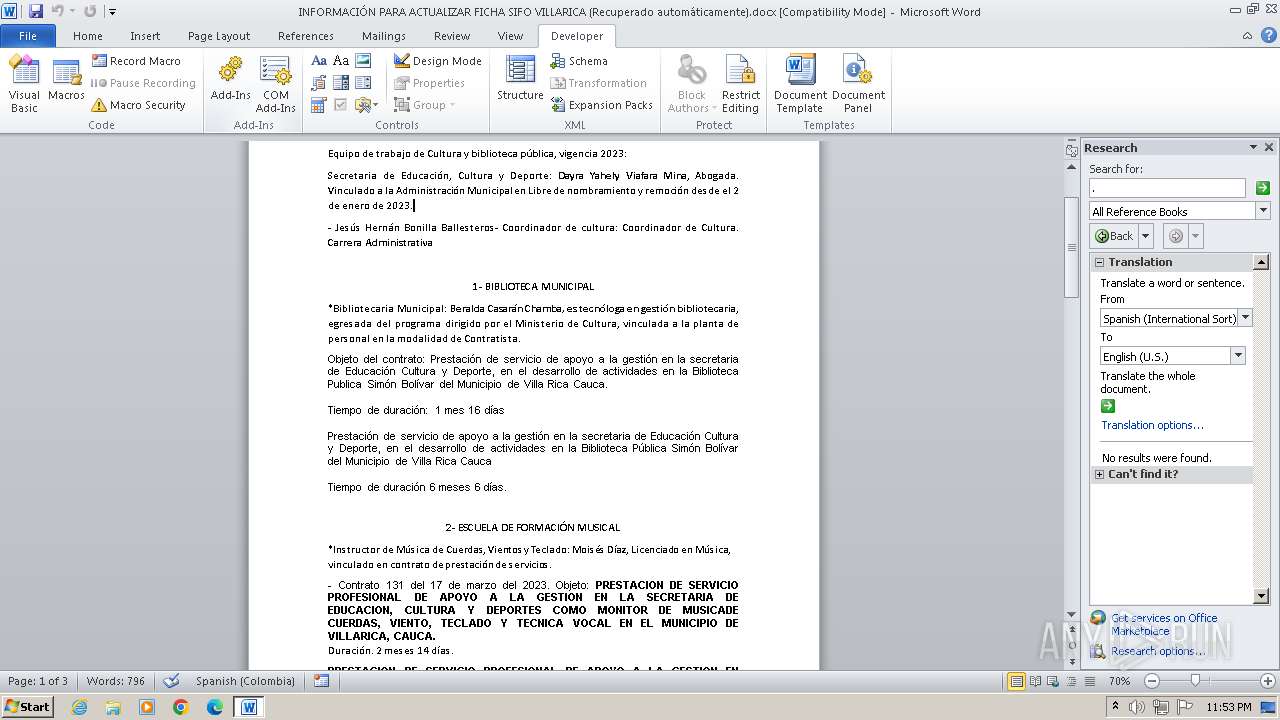
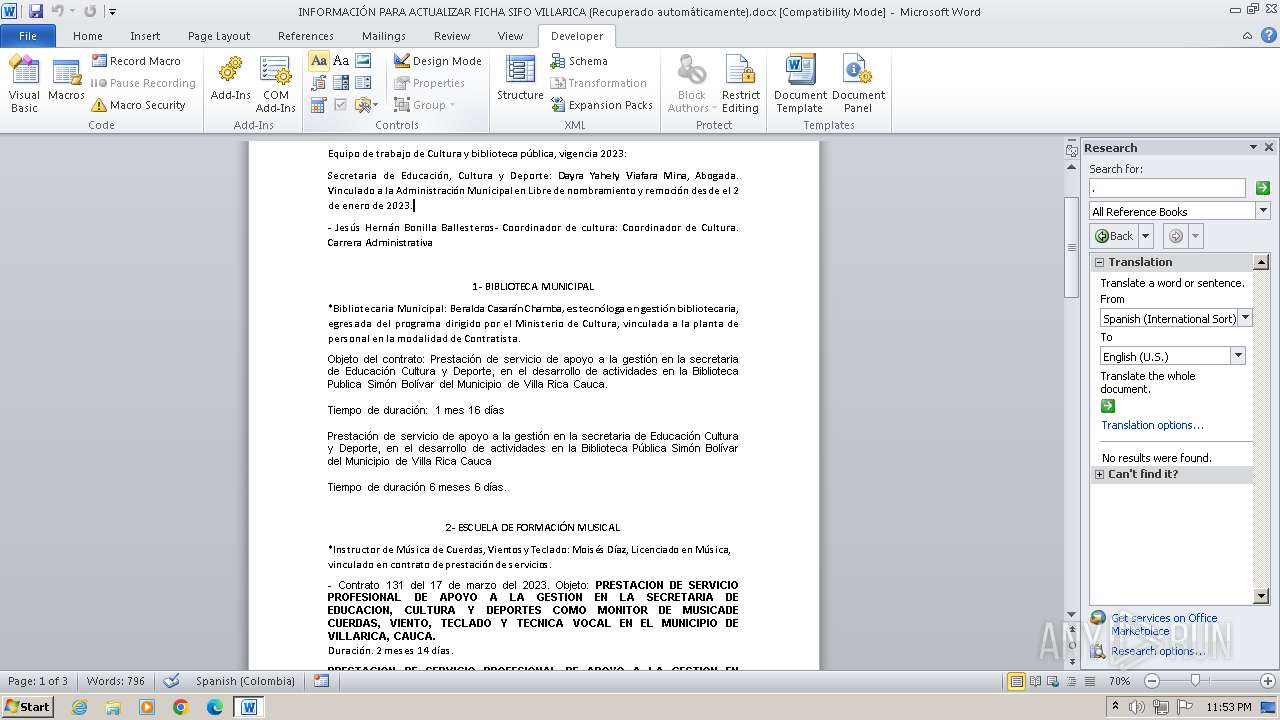
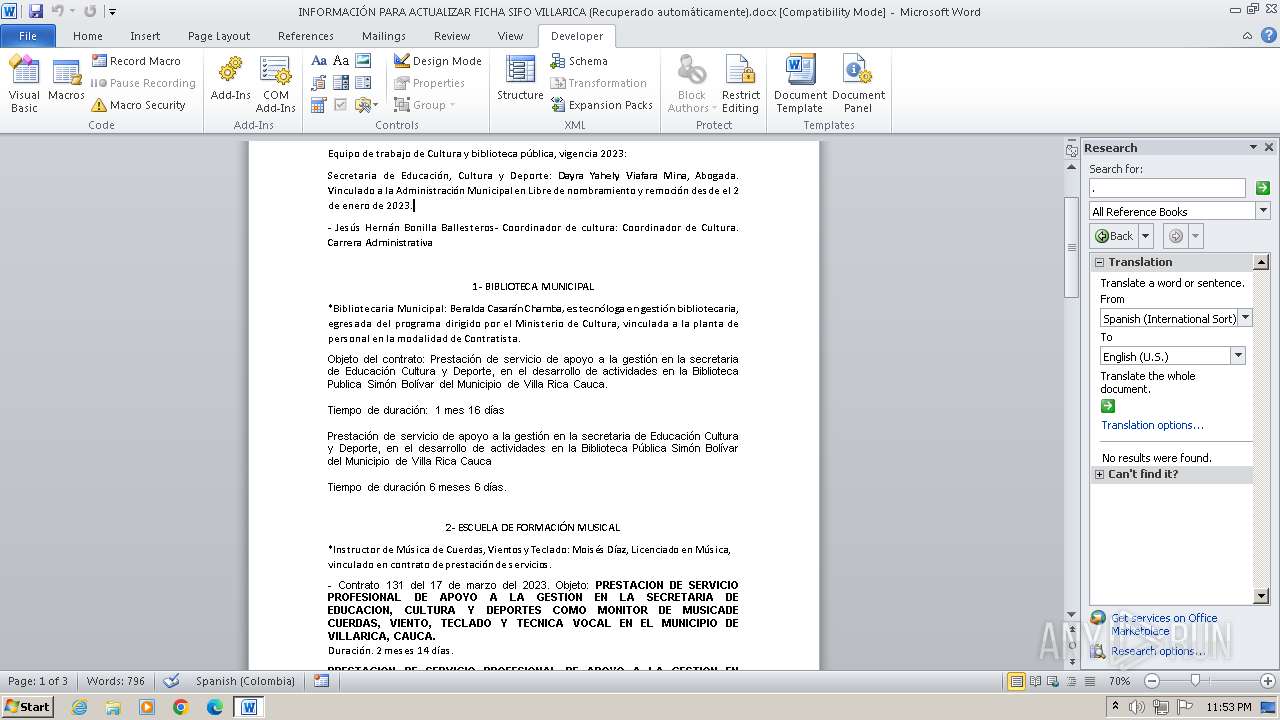
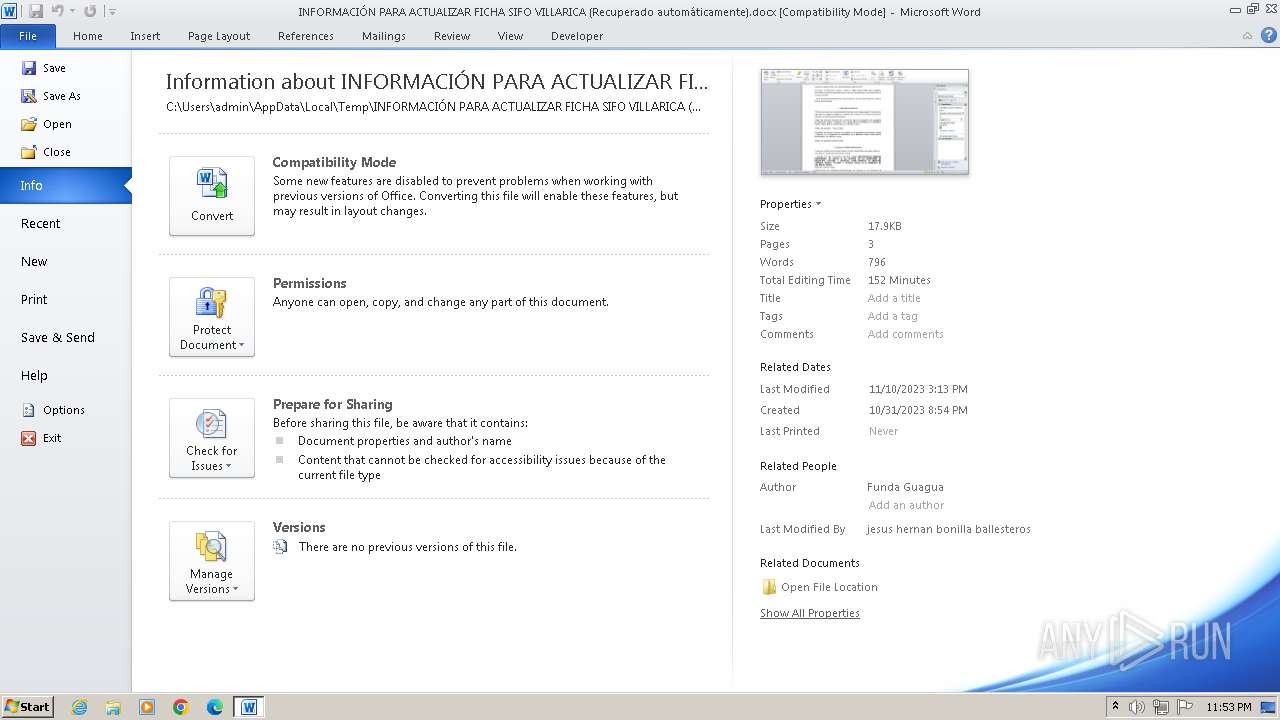
| File name: | INFORMACIÓN PARA ACTUALIZAR FICHA SIFO VILLARICA (Recuperado automáticamente).docx |
| Full analysis: | https://app.any.run/tasks/1d21070a-189a-4abd-83e2-5fa8009bdb74 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2023, 23:48:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | DEC7284CACB44BF7C26E63CAA4F250A4 |
| SHA1: | 7C1E48DE9DAF3CE26472E5726A6572A6892CE8FE |
| SHA256: | 162F41F2D17AF452E8E06CB6EF3E5A4693E7DF123785E64B37D22928764B4E10 |
| SSDEEP: | 384:MN/Vd5AV1fVJiZcjybkfdxOODcghXgNI/J9Jj7xXYZRflq8hnk3d:MvAV1VUcybkeGtAIXJjdCzNn0 |
MALICIOUS
Connection from MS Office application
- WINWORD.EXE (PID: 3432)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3564)
Reads the computer name
- wmpnscfg.exe (PID: 3564)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3564)
Checks supported languages
- wmpnscfg.exe (PID: 3564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x576f9132 |
| ZipCompressedSize: | 358 |
| ZipUncompressedSize: | 1445 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | Funda Guagua |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | jesus hernan bonilla ballesteros |
| RevisionNumber: | 14 |
| CreateDate: | 2023:10:31 20:54:00Z |
| ModifyDate: | 2023:11:10 15:13:00Z |
| Template: | Normal |
| TotalEditTime: | 2.5 hours |
| Pages: | 1 |
| Words: | 791 |
| Characters: | 4354 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 36 |
| Paragraphs: | 10 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 5135 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3432 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\INFORMACIÓN PARA ACTUALIZAR FICHA SIFO VILLARICA (Recuperado automáticamente).docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3564 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
35 905
Read events
25 595
Write events
9 940
Delete events
370
Modification events
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3432) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
10
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR95BD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:636C65E424BA58A532AD1F236D570A08 | SHA256:2C1DF1AAB8E4C91C0C5211DE6C378C31BEE95A1DC016BE09413E02F57D992F1F | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$FORMACIÓN PARA ACTUALIZAR FICHA SIFO VILLARICA (Recuperado automáticamente).docx | binary | |
MD5:93C3C92FCD0563E128AA3EE2E3C9D183 | SHA256:D8582134C1FCDC76EBFF31171A5EFDB4CA5EA3AF955BE7ACC5230D09AF282FBF | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\config14[1].xml | xml | |
MD5:889B45B8077DE0965A059AEC47A3E7F3 | SHA256:1BC7B982F5467259DDA94DBF55D2ACEDE827168E2F73B276F62044DF6E549E17 | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryES240a.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\ONetConfig\b6419f5bc3093b5f22142ce454e02407.xml | xml | |
MD5:889B45B8077DE0965A059AEC47A3E7F3 | SHA256:1BC7B982F5467259DDA94DBF55D2ACEDE827168E2F73B276F62044DF6E549E17 | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso9977.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{7CA09E82-435E-44B0-AC98-6FAE7409560B}.tmp | binary | |
MD5:E5ED068DC43F7E74CDA22C46BCBFA918 | SHA256:CD5BACF5083F7C7A46E248D005362DAF250C9CE309A276CDD553B0D6E230BF6E | |||
| 3432 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\Word14.customUI | compressed | |
MD5:2708920706D645A7A9C0F8584C97289A | SHA256:15B3426F48393612BF91D1A04981D37CA41A4727BED15DBC2FD0C1715F40C9EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
21
DNS requests
4
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3432 | WINWORD.EXE | GET | 200 | 52.109.32.97:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | unknown | xml | 1.97 Kb | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
3432 | WINWORD.EXE | GET | 200 | 8.253.204.120:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?eab7494215071a9b | unknown | compressed | 4.66 Kb | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
3432 | WINWORD.EXE | POST | — | 52.109.124.67:443 | http://rr.office.microsoft.com:443/Research/query.asmx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 192.168.100.2:53 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
3432 | WINWORD.EXE | 52.109.32.97:80 | office14client.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
3432 | WINWORD.EXE | 52.109.124.67:443 | rr.office.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
3432 | WINWORD.EXE | 8.253.204.120:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| unknown |
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3432 | WINWORD.EXE | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
1 ETPRO signatures available at the full report