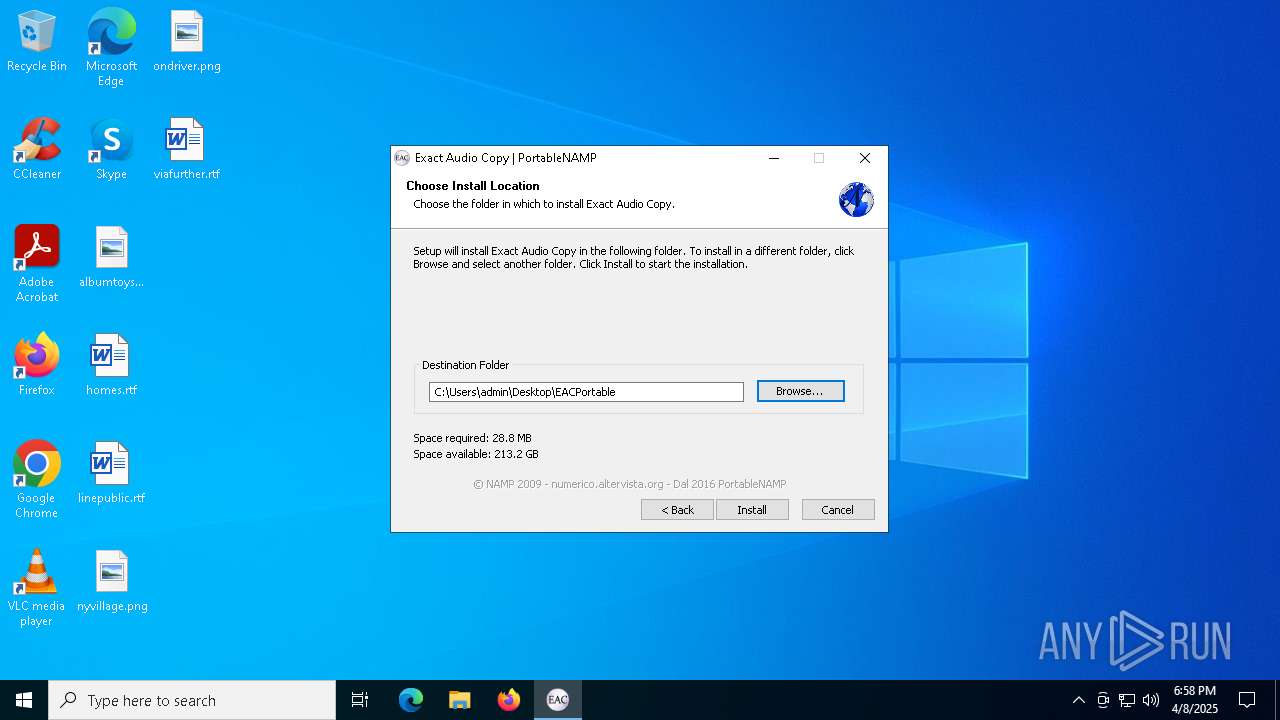
| File name: | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5 |
| Full analysis: | https://app.any.run/tasks/5863ff36-b32c-457c-882d-40940b41f389 |
| Verdict: | Malicious activity |
| Analysis date: | April 08, 2025, 18:57:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | E23541652C3470A6182DBFB3F89829E8 |
| SHA1: | D0C4A5188352E1197E5A256923378FC9F564F62D |
| SHA256: | 162128C311F79BAE11DED8D07828D11FD78B01D5284026668A26B479E46ABAD5 |
| SSDEEP: | 98304:XiHgSzNv0LScUoKffAcY3MH4NwTHTIR0uSQeCUr7hEGV6XQiaQryaRiiMLgvqtZ5:C6Ig5Mq0CNjXt+MJlw1B |
MALICIOUS
Detects Cygwin installation
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
SUSPICIOUS
Executable content was dropped or overwritten
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
- EACPortable.exe (PID: 632)
There is functionality for taking screenshot (YARA)
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
- EACPortable.exe (PID: 632)
- EAC.exe (PID: 6244)
Malware-specific behavior (creating "System.dll" in Temp)
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
- EACPortable.exe (PID: 632)
Process drops legitimate windows executable
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
The process creates files with name similar to system file names
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
- EACPortable.exe (PID: 632)
The process drops C-runtime libraries
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
Reads security settings of Internet Explorer
- EACPortable.exe (PID: 632)
- EAC.exe (PID: 6244)
SQL CE related mutex has been found
- EAC.exe (PID: 6244)
INFO
The sample compiled with english language support
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
Reads the computer name
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
- EACPortable.exe (PID: 632)
- EAC.exe (PID: 6244)
- cdrdao.exe (PID: 1240)
- cdrdao.exe (PID: 2908)
Reads the software policy settings
- slui.exe (PID: 5668)
- slui.exe (PID: 4300)
Checks supported languages
- EACPortable.exe (PID: 632)
- EAC.exe (PID: 6244)
- cdrdao.exe (PID: 1240)
- cdrdao.exe (PID: 2908)
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
Create files in a temporary directory
- EACPortable.exe (PID: 632)
- 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe (PID: 4776)
Creates files or folders in the user directory
- EAC.exe (PID: 6244)
Reads the machine GUID from the registry
- EAC.exe (PID: 6244)
Checks proxy server information
- slui.exe (PID: 4300)
UPX packer has been detected
- EAC.exe (PID: 6244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:07:24 22:31:33+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x35d8 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.6.0.0 |
| ProductVersionNumber: | 1.6.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | For additional details, visit PortableApps.com |
| CompanyName: | numerico.altervista.org |
| FileDescription: | Exact Audio Copy |
| FileVersion: | 1.6.0.0 |
| InternalName: | Exact Audio Copy |
| LegalCopyright: | 2007-2021 PortableApps.com, PortableApps.com Installer 3.5.21.0 |
| LegalTrademarks: | PortableApps.com is a registered trademark of Rare Ideas, LLC. |
| OriginalFileName: | EACPortable_1.6.0.paf.exe |
| PortableAppscomAppID: | EACPortable |
| PortableAppscomFormatVersion: | 3.5.21 |
| PortableAppscomInstallerVersion: | 3.5.21.0 |
| ProductName: | Exact Audio Copy |
| ProductVersion: | 1.6.0.0 |
Total processes
139
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Users\admin\Desktop\EACPortable\EACPortable.exe" | C:\Users\admin\Desktop\EACPortable\EACPortable.exe | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | ||||||||||||
User: admin Company: Portable Creata Da NAMP Integrity Level: MEDIUM Description: Exact Audio Copy Version: 2.2.2.0 Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\Desktop\EACPortable\App\EAC\cdrdao\cdrdao.exe" | C:\Users\admin\Desktop\EACPortable\App\EAC\CDRDAO\cdrdao.exe | — | EAC.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\Desktop\EACPortable\App\EAC\cdrdao\cdrdao.exe" scanbus | C:\Users\admin\Desktop\EACPortable\App\EAC\CDRDAO\cdrdao.exe | — | EAC.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4776 | "C:\Users\admin\AppData\Local\Temp\162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe" | C:\Users\admin\AppData\Local\Temp\162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | explorer.exe | ||||||||||||
User: admin Company: numerico.altervista.org Integrity Level: MEDIUM Description: Exact Audio Copy Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 5668 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6244 | "C:\Users\admin\Desktop\EACPortable\App\EAC\EAC.exe" | C:\Users\admin\Desktop\EACPortable\App\EAC\EAC.exe | — | EACPortable.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 089
Read events
2 822
Write events
267
Delete events
0
Modification events
| (PID) Process: | (4776) 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (4776) 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: CC71F56700000000 | |||
| (PID) Process: | (4776) 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
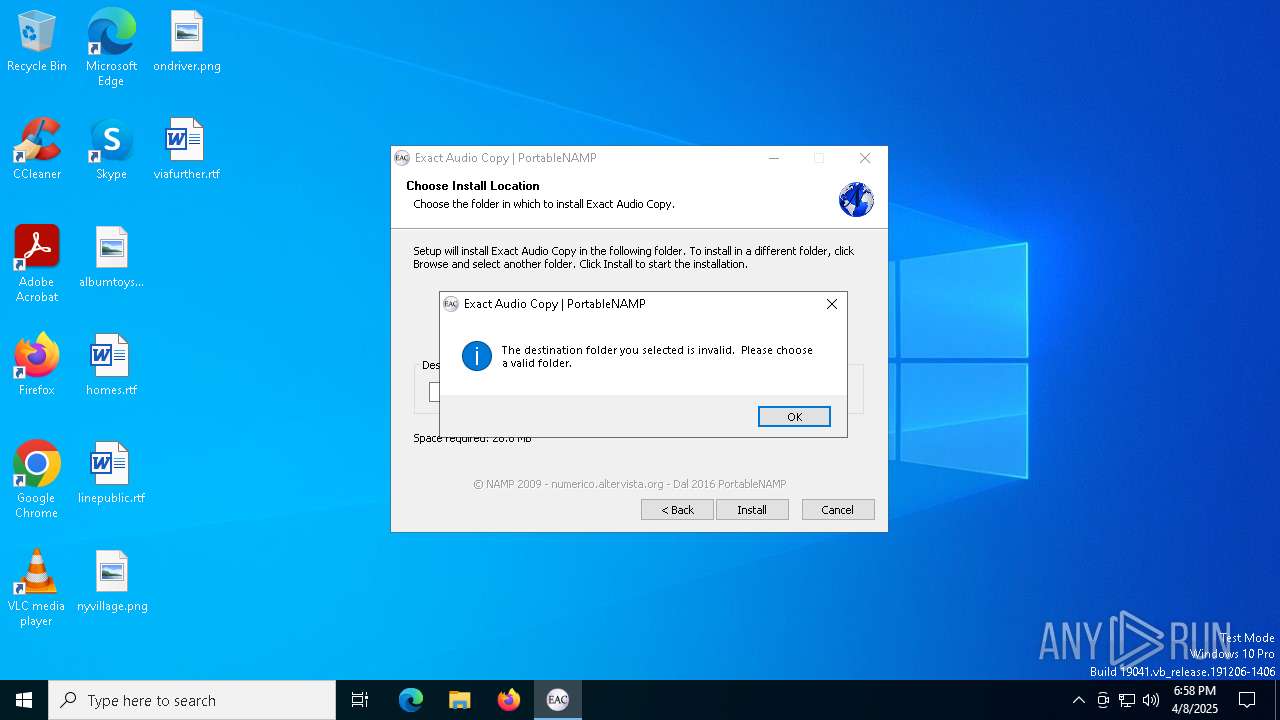
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (4776) 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\MarineCat\GOGO_DLL |
| Operation: | write | Name: | INSTPATH |
Value: C:\Users\admin\Desktop\EACPortable\App\EAC\GOGO.DLL | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\MarineCat\GOGO_DLL |
| Operation: | write | Name: | INSTPATH_VB |
Value: C:\Users\admin\Desktop\EACPortable\App\EAC\GOGO.DLL | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.imaadpcm |
| Operation: | write | Name: | fdwSupport |
Value: 1 | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.imaadpcm |
| Operation: | write | Name: | cFormatTags |
Value: 2 | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.imaadpcm |
| Operation: | write | Name: | aFormatTagCache |
Value: 01000000100000001100000014000000 | |||
| (PID) Process: | (6244) EAC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\AudioCompressionManager\DriverCache\msacm.imaadpcm |
| Operation: | write | Name: | cFilterTags |
Value: 0 | |||
Executable files
64
Suspicious files
10
Text files
103
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\AppData\Local\Temp\nsrBAF7.tmp\System.dll | executable | |
MD5:6E55A6E7C3FDBD244042EB15CB1EC739 | SHA256:ACF90AB6F4EDC687E94AAF604D05E16E6CFB5E35873783B50C66F307A35C6506 | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\appicon_16.png | binary | |
MD5:A44619E3343F3DEAFF0C221A238FBAE3 | SHA256:0601CEC9809C2F5FDCE04CB198D674B2C75C1BC0AE27B3AE478603C147CA264E | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\appicon_128.png | image | |
MD5:D5192C82AE79010C2E57AD02D7CFA382 | SHA256:7DC673D83E1A6DF7011373D70069A5C386DAF5EBC3E81E799522B599801D4C0D | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\AppData\Local\Temp\nsrBAF7.tmp\modern-header.bmp | image | |
MD5:ED5996417B7C0E2A389B9F8B4782BA2D | SHA256:0C948A7AA4DEDD0A2813D30798C26926ACE651C4153AF5AD85B356AA6118B44C | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\AppData\Local\Temp\nsrBAF7.tmp\nsDialogs.dll | executable | |
MD5:CA5BB0EE2B698869C41C087C9854487C | SHA256:C719697D5CED17D97BBC48662327339CCEC7E03F6552AA1D5C248F6FA5F16324 | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\appicon_32.png | binary | |
MD5:AFDF187377D81FAE0A69E47944A1560F | SHA256:AD9B7C06D014E70BA21E4972A58899439668397C4A983761C8838A1FABF1AB9B | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\appicon_256.png | binary | |
MD5:55733DE5A7FAC18733858FBA3234B6BF | SHA256:8D6AE713A13D7C26CC78318FBB9F29B41B3F051C449C1F5DCA193949CD1A415D | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\EACPortable.exe | executable | |
MD5:E4854F690485FCEB7D06F16E60E50DA4 | SHA256:21E33355B633ECEE0DE9B6A0D64AD637CF39668E3EF4FCB75565F9884B356B3E | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\appicon_48.png | binary | |
MD5:24B47E2FC807AF42BB166353CD062050 | SHA256:61F7B6C75A41543FC9F5761F892FE56FEFE294A3F539D49E9D08F3120D5C2F68 | |||
| 4776 | 162128c311f79bae11ded8d07828d11fd78b01d5284026668a26b479e46abad5.exe | C:\Users\admin\Desktop\EACPortable\App\AppInfo\EULA.txt | text | |
MD5:F5E0E49F30C9429C8D49D9D525688CD1 | SHA256:320B4289A0ECF21F956A53924A51D4A2D728785BD363645B31D8087E9AD762F0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4988 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4988 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |