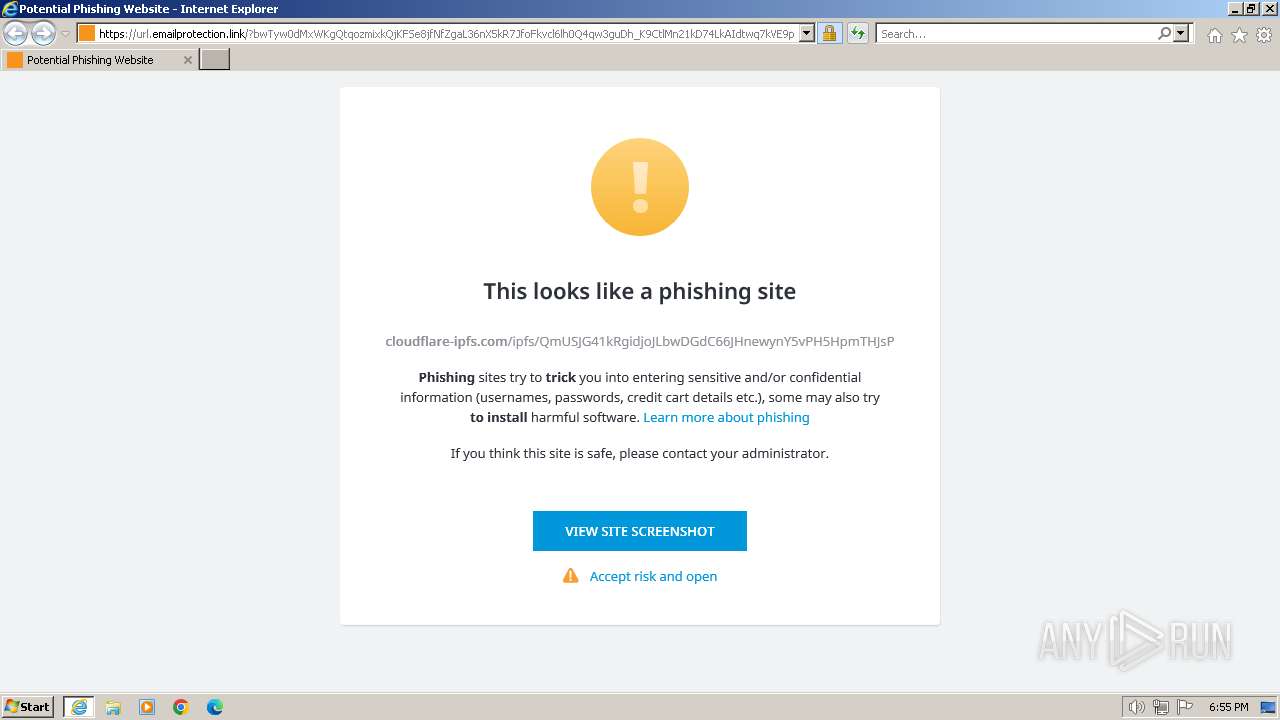
| URL: | https://url.emailprotection.link/?bwTyw0dMxWKgQtqozmixkQjKFSe8jfNfZgaL36nX5kR7JfoFkvcl6lh0Q4qw3guDh_K9CtlMn21kD74LkAIdtwq7kVE9pyyUQzQ1vjNECh_U7ItX1BjsM6Ov6tLkvshxlBu-DIgqSibJgd4mVQ4Mi8bQScun6sOndRK1lDuntS2U~ |
| Full analysis: | https://app.any.run/tasks/47b84099-dad7-49f5-ba55-f1ae7d3f3971 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2024, 18:55:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AF9D0484F7AB2FC2665769D61D583296 |
| SHA1: | 7FD9130706AD43E25096DEA53485D465D42CA65E |
| SHA256: | 15F31056E368666C8957AA36303BE842AF125B8426933ED85D8134E46B4059B6 |
| SSDEEP: | 6:2UfGRVg81WSyW1e2wXwO1SgwDKtS76OwVi:2UfqgMWSv9cJJSuOwVi |
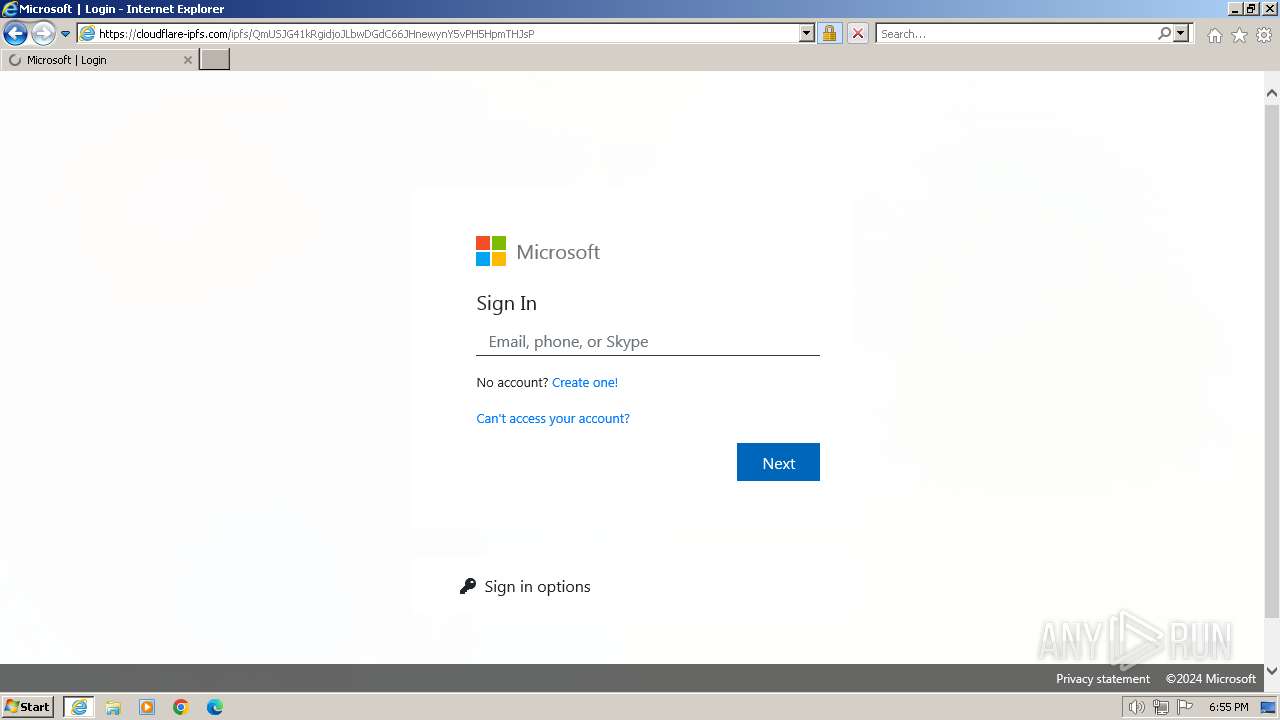
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 1604)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://url.emailprotection.link/?bwTyw0dMxWKgQtqozmixkQjKFSe8jfNfZgaL36nX5kR7JfoFkvcl6lh0Q4qw3guDh_K9CtlMn21kD74LkAIdtwq7kVE9pyyUQzQ1vjNECh_U7ItX1BjsM6Ov6tLkvshxlBu-DIgqSibJgd4mVQ4Mi8bQScun6sOndRK1lDuntS2U~" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:532 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 433
Read events
17 342
Write events
83
Delete events
8
Modification events
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (532) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
40
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\064D75DF60A1456F63CEF9F347BAA00B_FCE3E6607BCDA0B24C530EA53CB69E26 | binary | |
MD5:E9EC1735310826E8A075502D021A3C1E | SHA256:D9ED98DA7D1CB41D70A40F90474ED9E219491D6C76F9314ABDB1B016DDC92253 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\new_screenshot[1].js | text | |
MD5:4C183AA2B2518F5F6206EC12BF68B104 | SHA256:C92B1AECE38D5BAE7BFB72E26A5070D5663D40774C7ACEB973631025D6E6E592 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\064D75DF60A1456F63CEF9F347BAA00B_FCE3E6607BCDA0B24C530EA53CB69E26 | binary | |
MD5:CED53D152AB8B18B3F066EDD40ADD658 | SHA256:1F99A9B02F4C5259B8ECEA34EFE9D9E353985E071EC88123504A9294652DAF71 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\new_style[1].css | text | |
MD5:05B57D35B482EB0FA09C84E57C5CA68C | SHA256:8BE2E88F4BEED8E6D7C70115A1B71FA50C5DA67ABBC6E7F393A4960613079069 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ZQPS0YVW.htm | html | |
MD5:41322D2DF092F491E80A268C50C53B1C | SHA256:C4B828C5FE6DCC183A8006BA99701095AAFC92D581D7816C1A7C11861F2143F3 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_430EA0912164D1B129D6E1DC07C63959 | binary | |
MD5:79FF9C69EF68931E03EA05C3E20B0AA5 | SHA256:063175116A2CCCCCDFE1D9ED216AAC46E5680B816AC508972F8CC6B3FAD1C85B | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\tooltipster[1].css | text | |
MD5:FCBBBB9722DBDD355FA1F1FC7FCF49EF | SHA256:CA8178A737BDD4E6D2394E6C5609D1CA001254667458BB9CD1130BACEA58CB86 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_430EA0912164D1B129D6E1DC07C63959 | binary | |
MD5:DBAC57AC11A32211B1351D77A88CA29B | SHA256:13590C7A8B0E9E91436A3B3C09C0AA617C9FF02B16FB43BA69786879DAD7D811 | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9D4C30ABFD832BBF7FB85861282B25D6 | SHA256:44B17076477347455ACEFDDDF23051038907F08B4BC009C9049EB2B370C08BCC | |||
| 1604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\notosans-regular[1].ttf | binary | |
MD5:21F6235482ECDF67217DFA18483F7716 | SHA256:C8CFF31FCAE0EDC0E4FFD3628F36361DFC24D71CC5B9793E5FFAD8E76E6F182B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
50
DNS requests
25
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1604 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?58b09451c6662268 | unknown | — | — | unknown |
1604 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?83c23cd8118a42bc | unknown | — | — | unknown |
1604 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA0HeCoTP8b5pXKW4TH%2F0Xk%3D | unknown | binary | 471 b | unknown |
1604 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS6FKmrgWTGr7Q8nSk4Oub50ler6QQUlE%2FUXYvkpOKmgP792PkA76O%2BAlcCEA1XXOC77tS0eA%2Fb%2B7VLZ9A%3D | unknown | binary | 471 b | unknown |
532 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5565915fab5f2bac | unknown | — | — | unknown |
532 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2f21ede4db813e6d | unknown | — | — | unknown |
532 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
1604 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a53f9281f27ec170 | unknown | compressed | 65.2 Kb | unknown |
1604 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?035b8faa9f109581 | unknown | compressed | 65.2 Kb | unknown |
1604 | iexplore.exe | GET | 200 | 23.192.153.142:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1604 | iexplore.exe | 185.64.213.245:443 | url.emailprotection.link | Intermedia Technologies Company Limited | GB | unknown |
1604 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1604 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
532 | iexplore.exe | 185.64.213.245:443 | url.emailprotection.link | Intermedia Technologies Company Limited | GB | unknown |
532 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
532 | iexplore.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | unknown |
532 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
url.emailprotection.link |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
cloudflare-ipfs.com |
| malicious |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Peer to Peer File Sharing Service in DNS Lookup (cloudflare-ipfs .com) |
1604 | iexplore.exe | Misc activity | ET INFO Peer to Peer File Sharing Service Domain in TLS SNI (cloudflare-ipfs .com) |
1604 | iexplore.exe | Misc activity | ET INFO Peer to Peer File Sharing Service Domain in TLS SNI (cloudflare-ipfs .com) |
1604 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (ipfsquery) |
1604 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
1080 | svchost.exe | Misc activity | ET INFO Peer to Peer File Sharing Service in DNS Lookup (cloudflare-ipfs .com) |
532 | iexplore.exe | Misc activity | ET INFO Peer to Peer File Sharing Service Domain in TLS SNI (cloudflare-ipfs .com) |
532 | iexplore.exe | Misc activity | ET INFO Peer to Peer File Sharing Service Domain in TLS SNI (cloudflare-ipfs .com) |