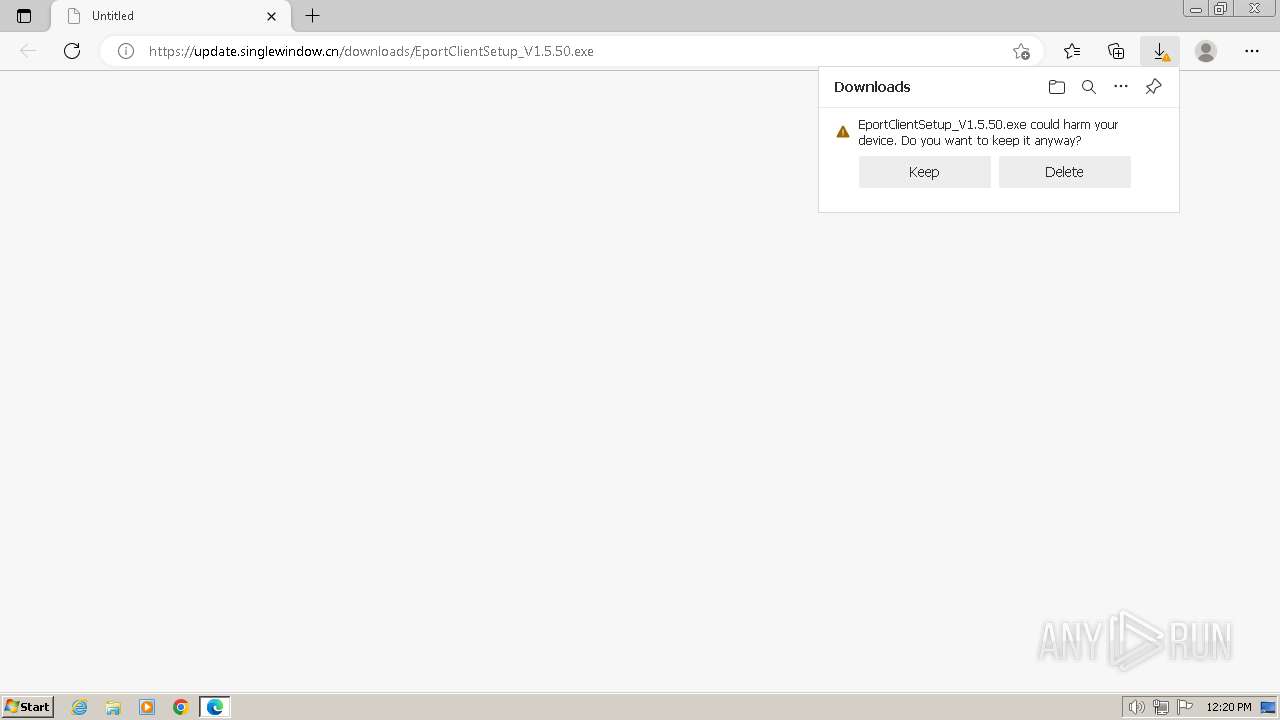
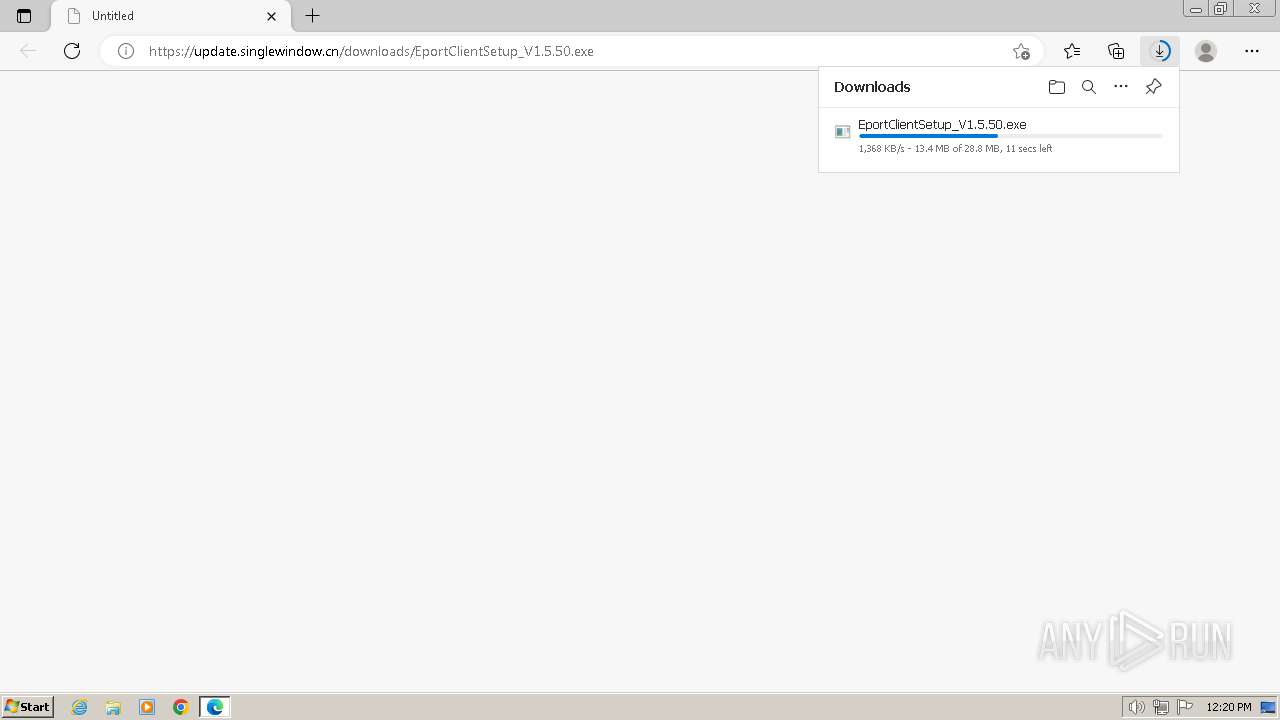
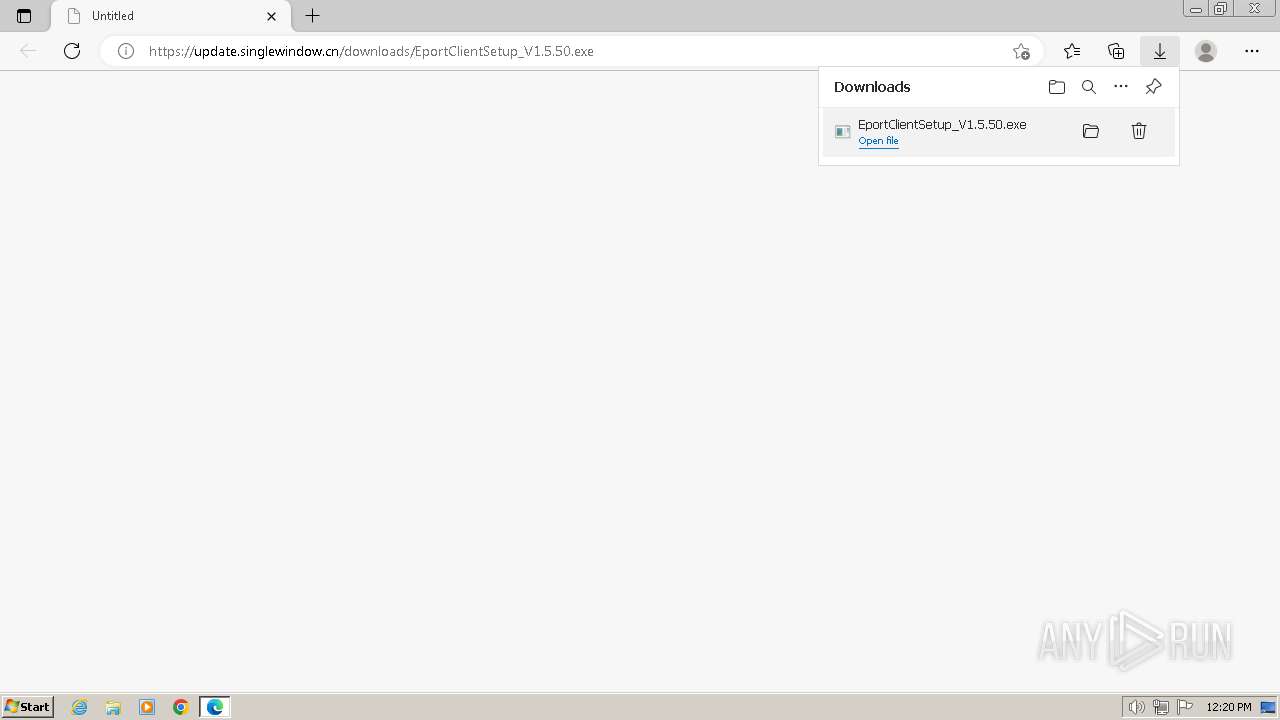
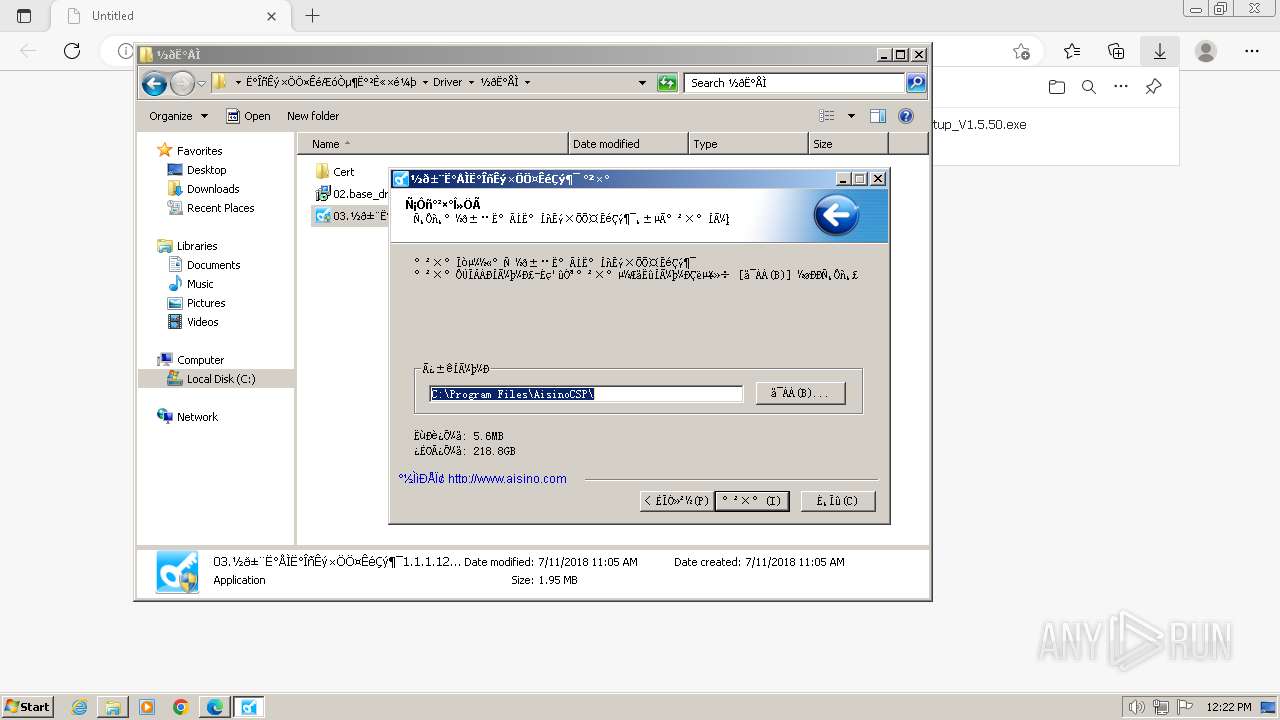
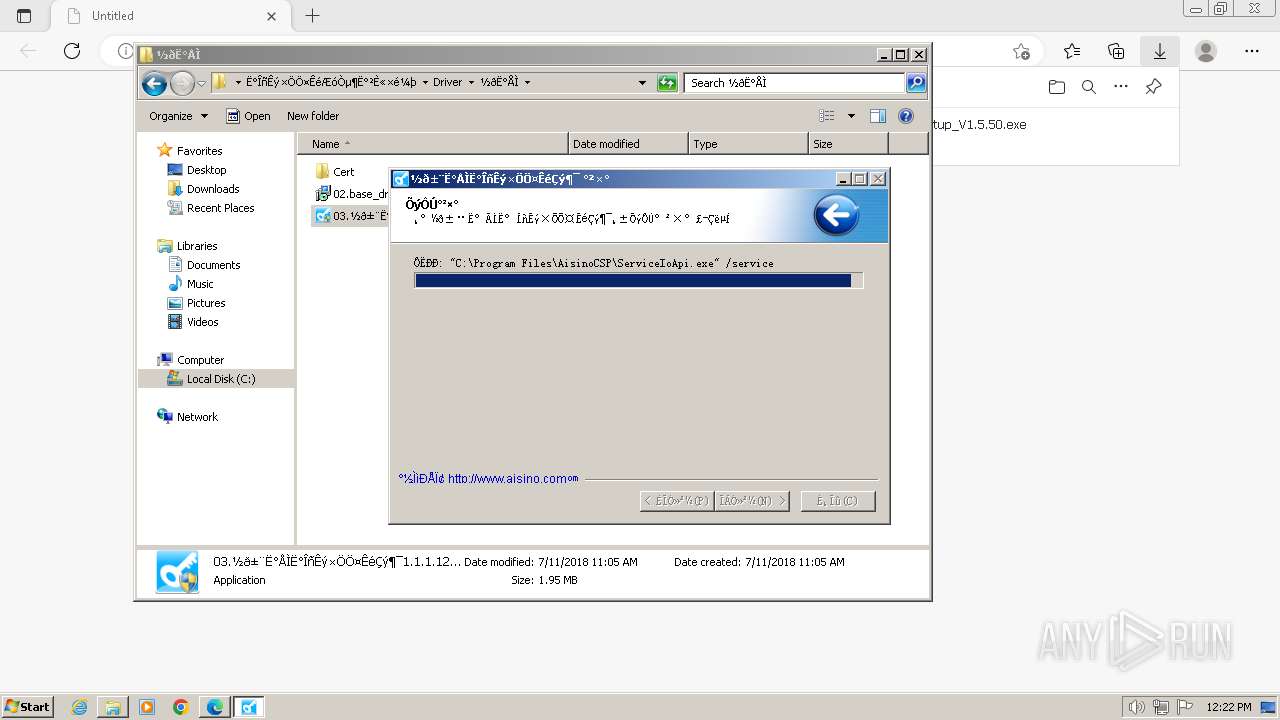
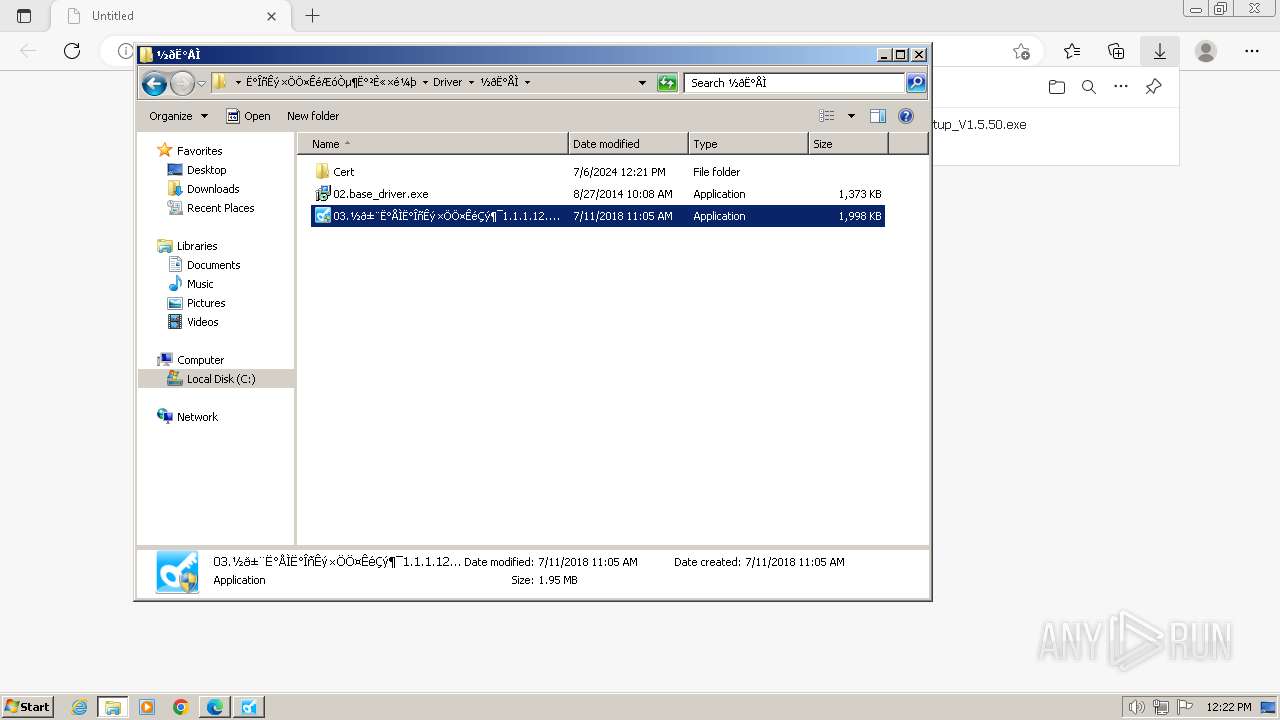
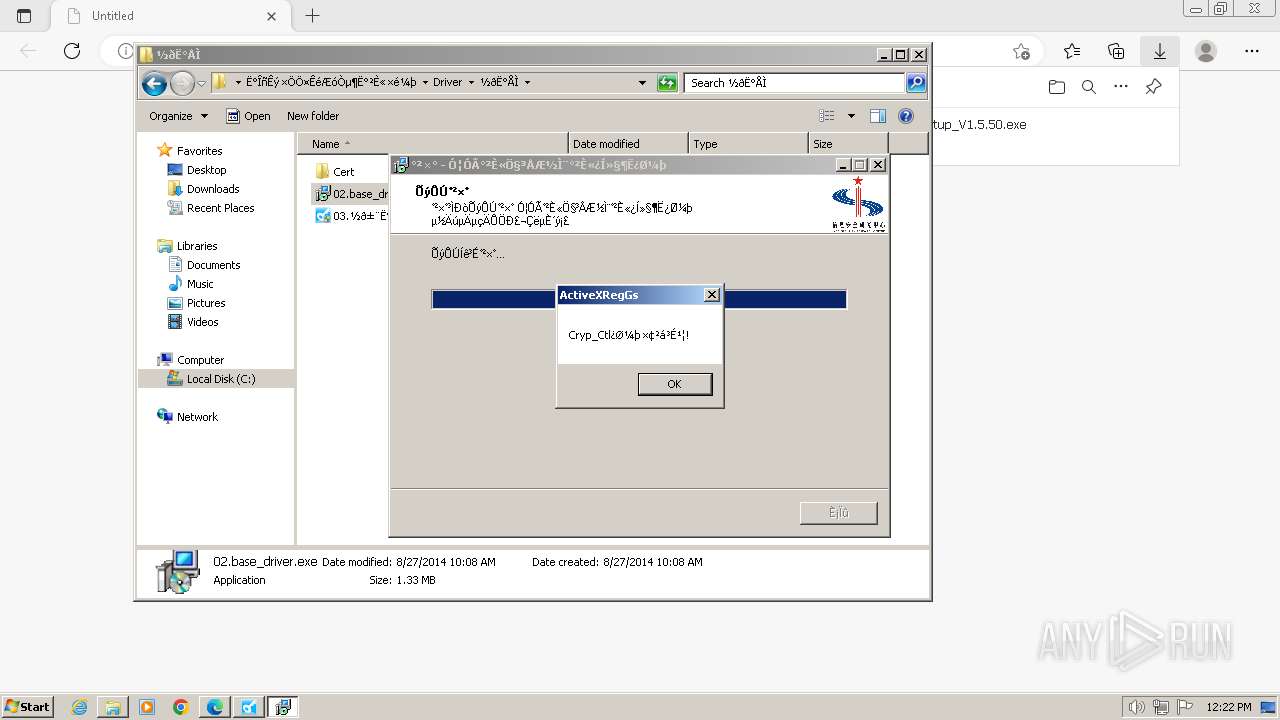
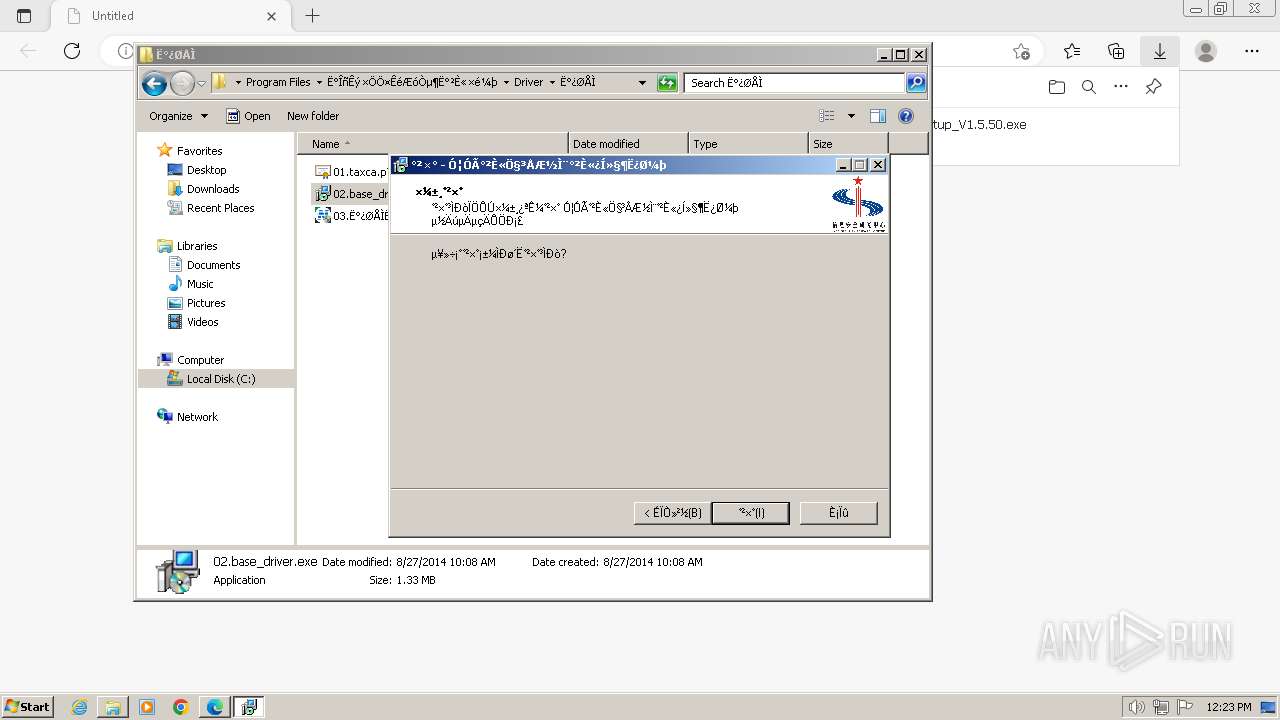
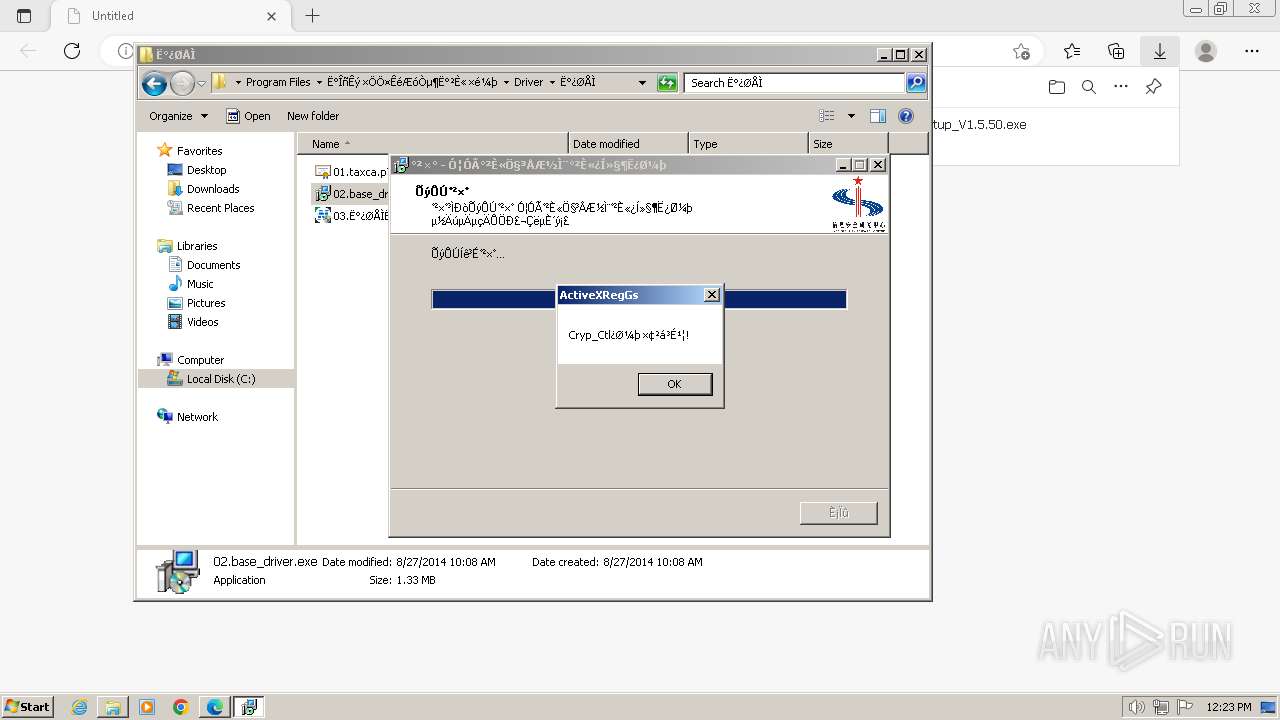
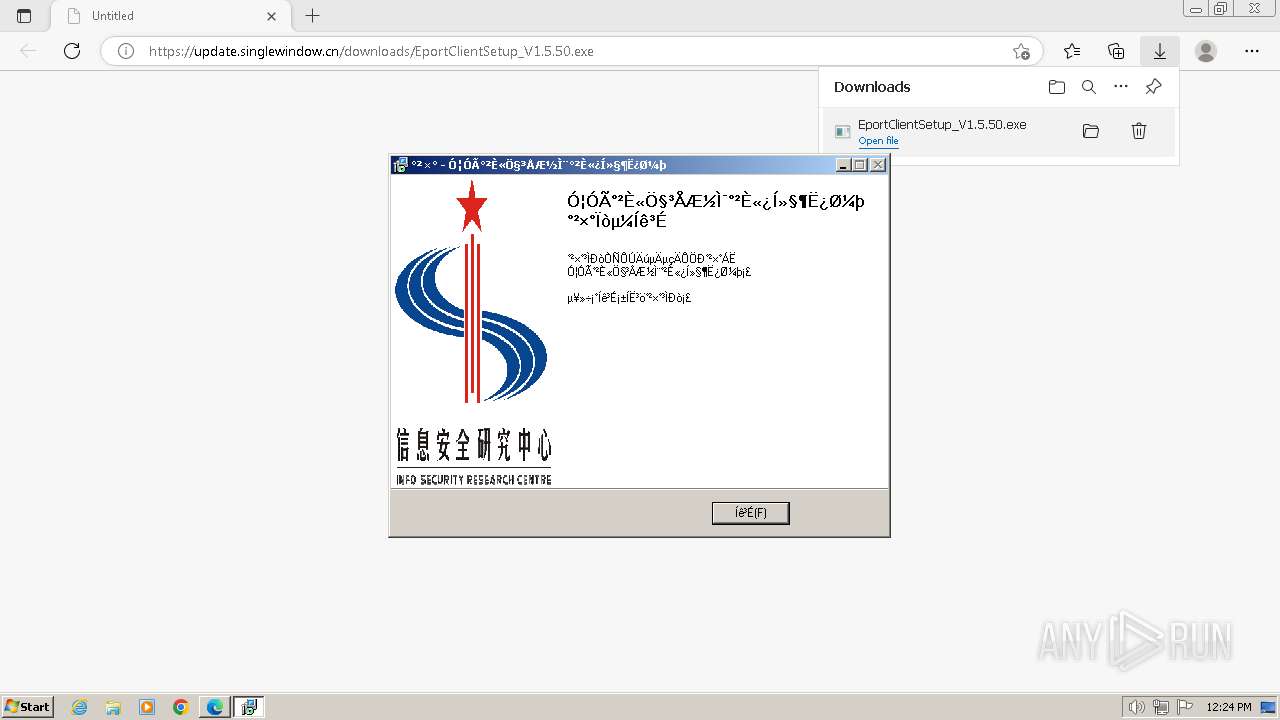
| URL: | https://update.singlewindow.cn/downloads/EportClientSetup_V1.5.50.exe |
| Full analysis: | https://app.any.run/tasks/62bf489a-49b8-482a-b0d8-e449339ab7e5 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2024, 11:19:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 94F22E3B9DC45AA7E9B4FB41449FBBF4 |
| SHA1: | F1CA92F602F084716C10707AD62CAB4DB6FC905D |
| SHA256: | 15F0510EB2DE763284951524BC530775B5085E95E2EA7911C996C138CE1FC1FB |
| SSDEEP: | 3:N8vRAv2JKa1KZss0QgLQWC:2v5ozZsPLQWC |
MALICIOUS
Creates a writable file in the system directory
- EportClientSetup_V1.5.50.exe (PID: 1832)
- drvinst.exe (PID: 3712)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 02.base_driver.tmp (PID: 1856)
- ActiveXRegGs.exe (PID: 3080)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- CnEport.Pub.WinService.exe (PID: 1280)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
Drops the executable file immediately after the start
- EportClientSetup_V1.5.50.exe (PID: 1832)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 02.base_driver.exe (PID: 524)
- 02.base_driver.tmp (PID: 1856)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- 02.base_driver.exe (PID: 3764)
- 02.base_driver.exe (PID: 3592)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.exe (PID: 1996)
- 02.base_driver.exe (PID: 1800)
- 02.base_driver.tmp (PID: 3864)
Uses Task Scheduler to autorun other applications
- nsD99A.tmp (PID: 3456)
Starts NET.EXE for service management
- nsDBD3.tmp (PID: 2388)
- net.exe (PID: 3184)
- ns262A.tmp (PID: 3324)
- net.exe (PID: 3900)
- net.exe (PID: 3924)
- ns2968.tmp (PID: 4092)
- net.exe (PID: 3736)
- nsFD40.tmp (PID: 4000)
- ns376D.tmp (PID: 2812)
- net.exe (PID: 2368)
Registers / Runs the DLL via REGSVR32.EXE
- 02.base_driver.tmp (PID: 1856)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
Changes the autorun value in the registry
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
SUSPICIOUS
Process drops legitimate windows executable
- EportClientSetup_V1.5.50.exe (PID: 1832)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- WDDriverR.exe (PID: 2112)
- 02.base_driver.tmp (PID: 1856)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
Malware-specific behavior (creating "System.dll" in Temp)
- EportClientSetup_V1.5.50.exe (PID: 1832)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
Creates/Modifies COM task schedule object
- EportClientSetup_V1.5.50.exe (PID: 1832)
- RegAsm.exe (PID: 1020)
- regsvr32.exe (PID: 2092)
- ActiveXRegGs.exe (PID: 3080)
- regsvr32.exe (PID: 3576)
- ActiveXRegGs.exe (PID: 2264)
- regsvr32.exe (PID: 3276)
- ActiveXRegGs.exe (PID: 3776)
Drops a system driver (possible attempt to evade defenses)
- EportClientSetup_V1.5.50.exe (PID: 1832)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- WDDriverR.exe (PID: 2112)
Executable content was dropped or overwritten
- EportClientSetup_V1.5.50.exe (PID: 1832)
- DPInst32.exe (PID: 2060)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- drvinst.exe (PID: 3712)
- TXRNSecurityCom.exe (PID: 3624)
- 02.base_driver.exe (PID: 524)
- 02.base_driver.tmp (PID: 1856)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- 02.base_driver.exe (PID: 3764)
- 02.base_driver.exe (PID: 3592)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.exe (PID: 1800)
- 02.base_driver.exe (PID: 1996)
- 02.base_driver.tmp (PID: 3864)
The process creates files with name similar to system file names
- EportClientSetup_V1.5.50.exe (PID: 1832)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
Starts application with an unusual extension
- EportClientSetup_V1.5.50.exe (PID: 1832)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
Reads security settings of Internet Explorer
- RegAsm.exe (PID: 1020)
- InstallUtil.exe (PID: 1392)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Reads settings of System Certificates
- RegAsm.exe (PID: 1020)
- InstallUtil.exe (PID: 1392)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Adds/modifies Windows certificates
- RegAsm.exe (PID: 1020)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WinService.exe (PID: 1280)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Checks Windows Trust Settings
- InstallUtil.exe (PID: 1392)
- drvinst.exe (PID: 3712)
- RegAsm.exe (PID: 1020)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WinService.exe (PID: 1280)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Executes as Windows Service
- HGBOT.exe (PID: 1944)
- WDTokenServerHaiGuan.exe (PID: 3408)
- WDDrvRpr_Share.exe (PID: 3888)
- ServiceIoApi.exe (PID: 2692)
- ServiceIoApi.exe (PID: 3800)
- CnEport.Pub.WinService.exe (PID: 1280)
Starts CMD.EXE for commands execution
- nsCBF5.tmp (PID: 2672)
- nsCC73.tmp (PID: 3356)
- nsCDAB.tmp (PID: 3080)
- nsCE29.tmp (PID: 3540)
- nsCFB1.tmp (PID: 2308)
- nsD550.tmp (PID: 3112)
- nsD5BE.tmp (PID: 3360)
- nsD62D.tmp (PID: 1196)
- nsD729.tmp (PID: 3804)
- nsD4E1.tmp (PID: 2868)
Starts SC.EXE for service management
- cmd.exe (PID: 3184)
- cmd.exe (PID: 3384)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 2740)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 2700)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 2016)
- cmd.exe (PID: 1000)
- nsD8AD.tmp (PID: 2472)
- nsDC51.tmp (PID: 1968)
- ns26A8.tmp (PID: 3904)
- ns792.tmp (PID: 3632)
Creates files in the driver directory
- drvinst.exe (PID: 3712)
Creates a software uninstall entry
- WDDriverR.exe (PID: 2112)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- EportClientSetup_V1.5.50.exe (PID: 1832)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 3592)
Uses powercfg.exe to modify the power settings
- nsDAF2.tmp (PID: 2268)
Reads the Windows owner or organization settings
- 02.base_driver.tmp (PID: 1856)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
Mutex name with non-standard characters
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
Reads the Internet Settings
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Uses REG/REGEDIT.EXE to modify registry
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
Uses RUNDLL32.EXE to load library
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
There is functionality for taking screenshot (YARA)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Searches for installed software
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
INFO
Drops the executable file immediately after the start
- msedge.exe (PID: 2076)
- msedge.exe (PID: 3392)
Application launched itself
- msedge.exe (PID: 3392)
Executable content was dropped or overwritten
- msedge.exe (PID: 2076)
- msedge.exe (PID: 3392)
The process uses the downloaded file
- msedge.exe (PID: 3392)
- msedge.exe (PID: 2120)
Checks supported languages
- EportClientSetup_V1.5.50.exe (PID: 1832)
- nsBD01.tmp (PID: 2332)
- RegAsm.exe (PID: 1020)
- InstallUtil.exe (PID: 1392)
- nsC157.tmp (PID: 2964)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- nsC466.tmp (PID: 2696)
- nsCA72.tmp (PID: 2996)
- HGBOT.exe (PID: 3620)
- HGBOT.exe (PID: 1944)
- nsCAF0.tmp (PID: 3752)
- WDDriverR.exe (PID: 2112)
- nsCC73.tmp (PID: 3356)
- WDTokenServerSetup.exe (PID: 3068)
- nsCDAB.tmp (PID: 3080)
- nsCE29.tmp (PID: 3540)
- nsCEC6.tmp (PID: 2640)
- WDTokenServerHaiGuan.exe (PID: 3948)
- nsCFB1.tmp (PID: 2308)
- WDTokenServerHaiGuan.exe (PID: 3408)
- nsD550.tmp (PID: 3112)
- nsD4E1.tmp (PID: 2868)
- nsD5BE.tmp (PID: 3360)
- nsD62D.tmp (PID: 1196)
- nsCBF5.tmp (PID: 2672)
- nsD6AB.tmp (PID: 1072)
- nsD729.tmp (PID: 3804)
- WDDrvRpr_Share.exe (PID: 3648)
- WDDrvRpr_Share.exe (PID: 3888)
- HDZB_USBKEY_2G_CEP_DevServer.exe (PID: 2400)
- nsD82F.tmp (PID: 2712)
- nsD8AD.tmp (PID: 2472)
- nsD92B.tmp (PID: 1920)
- nsDAF2.tmp (PID: 2268)
- TXRNSecurityCom.exe (PID: 3624)
- nsDBD3.tmp (PID: 2388)
- nsD99A.tmp (PID: 3456)
- nsDC51.tmp (PID: 1968)
- 02.base_driver.exe (PID: 524)
- 02.base_driver.tmp (PID: 1856)
- ActiveXRegGs.exe (PID: 3080)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ns262A.tmp (PID: 3324)
- ns26A8.tmp (PID: 3904)
- ServiceIoApi.exe (PID: 1744)
- nsD463.tmp (PID: 3632)
- registCCID.exe (PID: 2916)
- ns2968.tmp (PID: 4092)
- SetAccessControl.exe (PID: 3820)
- ServiceIoApi.exe (PID: 2692)
- ns4805.tmp (PID: 1284)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
- ns4DA4.tmp (PID: 3652)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- GFA_certd3003.exe (PID: 3824)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- nsFD40.tmp (PID: 4000)
- ns792.tmp (PID: 3632)
- ServiceIoApi.exe (PID: 3800)
- ns376D.tmp (PID: 2812)
- ServiceIoApi.exe (PID: 2412)
- CertManager.exe (PID: 2684)
- 02.base_driver.exe (PID: 3764)
- 02.base_driver.tmp (PID: 1672)
- 02.base_driver.exe (PID: 3592)
- 02.base_driver.tmp (PID: 3032)
- CertManageradmin.exe (PID: 3288)
- ActiveXRegGs.exe (PID: 2264)
- CertManageradmin.exe (PID: 2256)
- CnEport.Pub.WinService.exe (PID: 1280)
- CertManageradmin.exe (PID: 2000)
- 02.base_driver.exe (PID: 1800)
- 02.base_driver.tmp (PID: 680)
- 02.base_driver.exe (PID: 1996)
- CertManageradmin.exe (PID: 3880)
- 02.base_driver.tmp (PID: 3864)
- ActiveXRegGs.exe (PID: 3776)
Reads the computer name
- EportClientSetup_V1.5.50.exe (PID: 1832)
- RegAsm.exe (PID: 1020)
- InstallUtil.exe (PID: 1392)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- HGBOT.exe (PID: 3620)
- WDDriverR.exe (PID: 2112)
- HGBOT.exe (PID: 1944)
- WDTokenServerSetup.exe (PID: 3068)
- WDTokenServerHaiGuan.exe (PID: 3948)
- WDTokenServerHaiGuan.exe (PID: 3408)
- HDZB_USBKEY_2G_CEP_DevServer.exe (PID: 2400)
- WDDrvRpr_Share.exe (PID: 3888)
- TXRNSecurityCom.exe (PID: 3624)
- 02.base_driver.tmp (PID: 1856)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ServiceIoApi.exe (PID: 1744)
- WDDrvRpr_Share.exe (PID: 3648)
- ServiceIoApi.exe (PID: 2692)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WinService.exe (PID: 1280)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- GFA_certd3003.exe (PID: 3824)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- ServiceIoApi.exe (PID: 2412)
- ServiceIoApi.exe (PID: 3800)
- 02.base_driver.tmp (PID: 1672)
- CertManager.exe (PID: 2684)
- 02.base_driver.tmp (PID: 3032)
- CertManageradmin.exe (PID: 3288)
- CertManageradmin.exe (PID: 2000)
- 02.base_driver.tmp (PID: 680)
- CertManageradmin.exe (PID: 3880)
- 02.base_driver.tmp (PID: 3864)
- CertManageradmin.exe (PID: 2256)
Reads the machine GUID from the registry
- EportClientSetup_V1.5.50.exe (PID: 1832)
- InstallUtil.exe (PID: 1392)
- RegAsm.exe (PID: 1020)
- DPInst32.exe (PID: 2060)
- drvinst.exe (PID: 3712)
- WDDriverR.exe (PID: 2112)
- TXRNSecurityCom.exe (PID: 3624)
- ServiceIoApi.exe (PID: 2692)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
- CnEport.Pub.WinService.exe (PID: 1280)
- ServiceIoApi.exe (PID: 3800)
Reads the software policy settings
- RegAsm.exe (PID: 1020)
- InstallUtil.exe (PID: 1392)
- drvinst.exe (PID: 3712)
- SetAccessControl.exe (PID: 3820)
- CnEport.Pub.WinService.exe (PID: 1280)
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Create files in a temporary directory
- DPInst32.exe (PID: 2060)
- EportClientSetup_V1.5.50.exe (PID: 1832)
- WDDriverR.exe (PID: 2112)
- WDTokenServerSetup.exe (PID: 3068)
- TXRNSecurityCom.exe (PID: 3624)
- 02.base_driver.exe (PID: 524)
- 02.base_driver.tmp (PID: 1856)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- 02.base_driver.exe (PID: 3764)
- 02.base_driver.exe (PID: 3592)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.exe (PID: 1800)
- 02.base_driver.exe (PID: 1996)
- 02.base_driver.tmp (PID: 3864)
Creates files or folders in the user directory
- TXRNSecurityCom.exe (PID: 3624)
- EportClientSetup_V1.5.50.exe (PID: 1832)
Creates files in the program directory
- TXRNSecurityCom.exe (PID: 3624)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3864)
- ePass3003_SimpChinese_gfa.exe (PID: 3372)
Creates a software uninstall entry
- 02.base_driver.tmp (PID: 1856)
- 02.base_driver.tmp (PID: 3032)
- 02.base_driver.tmp (PID: 3864)
Manual execution by a user
- GFA_certd3003.exe (PID: 3824)
- explorer.exe (PID: 1672)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 1744)
- 03.½ð±¨Ë°ÅÌË°ÎñÊý×ÖÖ¤ÊéÇý¶¯1.1.1.12.exe (PID: 3208)
- 02.base_driver.exe (PID: 3764)
- CertManageradmin.exe (PID: 3288)
- CertManageradmin.exe (PID: 2256)
- CertManageradmin.exe (PID: 3880)
- CertManageradmin.exe (PID: 2000)
- 02.base_driver.exe (PID: 1800)
Disables trace logs
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Reads Environment values
- CnEport.Pub.WebSocketServer.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
231
Monitored processes
140
Malicious processes
27
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | sc config SCPolicySvc start= auto | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3764 --field-trial-handle=1340,i,5585361204244530832,14649098697131535303,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 524 | "C:\Program Files\Ë°ÎñÊý×ÖÖ¤ÊéÆóÒµ¶Ë°²È«×é¼þ\Driver\½ðË°ÅÌ\02.base_driver.exe" /sp- /silent /norestart | C:\Program Files\Ë°ÎñÊý×ÖÖ¤ÊéÆóÒµ¶Ë°²È«×é¼þ\Driver\½ðË°ÅÌ\02.base_driver.exe | TXRNSecurityCom.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: 应用安全支撑平台安全客户端控件 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Local\Temp\is-BOLRJ.tmp\02.base_driver.tmp" /SL5="$C01B0,1157836,52224,C:\Program Files\Ë°ÎñÊý×ÖÖ¤ÊéÆóÒµ¶Ë°²È«×é¼þ\Driver\Ë°¿ØÅÌ\02.base_driver.exe" | C:\Users\admin\AppData\Local\Temp\is-BOLRJ.tmp\02.base_driver.tmp | — | 02.base_driver.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 安装/卸载 Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
| 748 | sc start SCPolicySvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | cmd.exe /c sc start "WDDrvRpr_Share" | C:\Windows\System32\cmd.exe | — | nsD729.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | "C:\Öйúµç×Ó¿Ú°¶¿Í»§¶Ë¿Ø¼þ\tools\RegAsm.exe" /codebase "C:\Öйúµç×Ó¿Ú°¶¿Í»§¶Ë¿Ø¼þ\CnEport.Pub.WebSocket.ActiveX.dll" | C:\Öйúµç×Ó¿Ú°¶¿Í»§¶Ë¿Ø¼þ\tools\RegAsm.exe | — | nsBD01.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\nszCB39.tmp\nsD6AB.tmp" "C:\Windows\system32\WatchDataV5HaiGuan\Watchdata CSP v5.1 HaiGuan\ccid_driver\WDDrvRpr_Share.exe" /Service | C:\Users\admin\AppData\Local\Temp\nszCB39.tmp\nsD6AB.tmp | — | WDDriverR.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4332 --field-trial-handle=1340,i,5585361204244530832,14649098697131535303,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\AppData\Local\Temp\nszCB39.tmp\nsD62D.tmp" cmd.exe /c sc start SCPolicySvc | C:\Users\admin\AppData\Local\Temp\nszCB39.tmp\nsD62D.tmp | — | WDDriverR.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
74 072
Read events
71 362
Write events
2 653
Delete events
57
Modification events
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: B435E4A4287B2F00 | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (3392) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
277
Suspicious files
109
Text files
86
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF4e4ee.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF4e50d.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF4e54b.TMP | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\a39b4ae8-87af-492c-9f42-68affd221f39.tmp | binary | |
MD5:B9D3FF44ADE58B622EE7A54AA849ACEA | SHA256:11980933AF748910D01DB198497D6C9FB880C88BF1163716C62D154913EC87C5 | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Platform Notifications\LOG.old~RF4e5d8.TMP | text | |
MD5:93B76D13B273BF917AB2B451BC904403 | SHA256:4080C22F68EC4545FC075C08CD3C8AEF8946444329C307F7BA54C134F75E901A | |||
| 3392 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:599EE96A37069C802B2B7AF08E7A22FA | SHA256:496E41B4DB940FD3A078BD07EF2FA13C7F9E272A214AFD673E51502E7BCD63CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
26
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1280 | CnEport.Pub.WinService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
1280 | CnEport.Pub.WinService.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAj0a%2FGVPO1IO7x66TQNez8%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3392 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2076 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2076 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2076 | msedge.exe | 14.29.101.169:443 | update.singlewindow.cn | Chinanet | CN | unknown |
3392 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
update.singlewindow.cn |
| unknown |
edge.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CertManager.exe | SKF Process P11 Start |
CertManageradmin.exe | DeviceApi 23:12 pid=3288,tid=3428, g_isAdmin = 0 |
CertManageradmin.exe | DeviceApi 23:12 pid=3288,tid=3428, osversion.dwMajorVersion = 6 |
CertManageradmin.exe | DeviceApi 23:14 pid=2256,tid=2532, g_isAdmin = 0 |
CertManageradmin.exe | DeviceApi 23:14 pid=2256,tid=2532, osversion.dwMajorVersion = 6 |
CertManageradmin.exe | DeviceApi 23:16 pid=3880,tid=2620, g_isAdmin = 0 |
CertManageradmin.exe | DeviceApi 23:16 pid=3880,tid=2620, osversion.dwMajorVersion = 6 |
CertManageradmin.exe | DeviceApi 23:17 pid=2000,tid=3948, g_isAdmin = 0 |
CertManageradmin.exe | DeviceApi 23:17 pid=2000,tid=3948, osversion.dwMajorVersion = 6 |
CertManager.exe | SKF Process P11 |