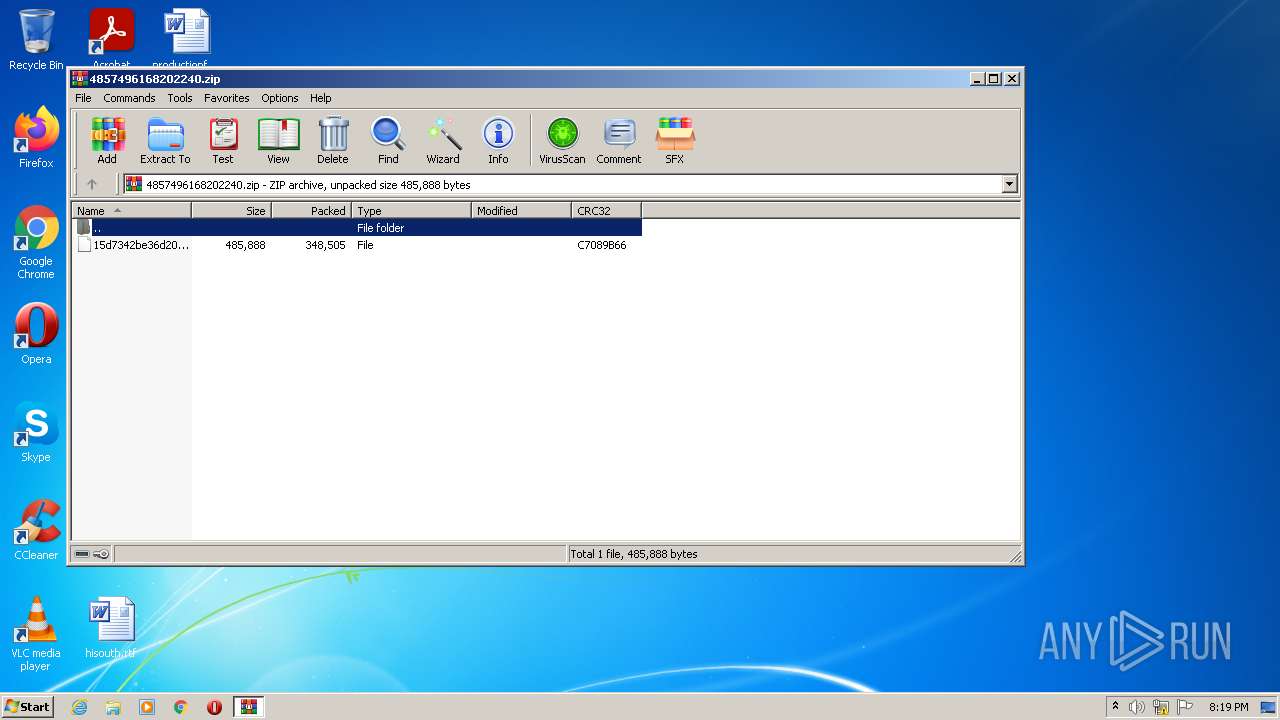
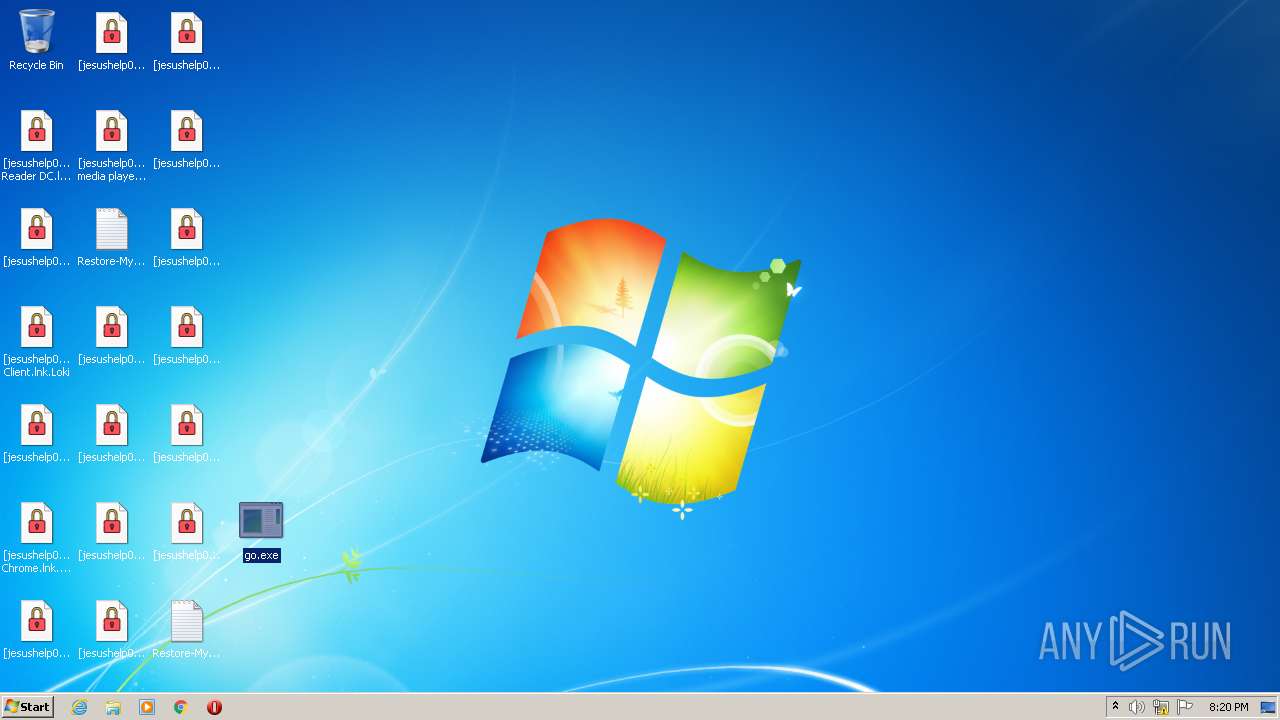
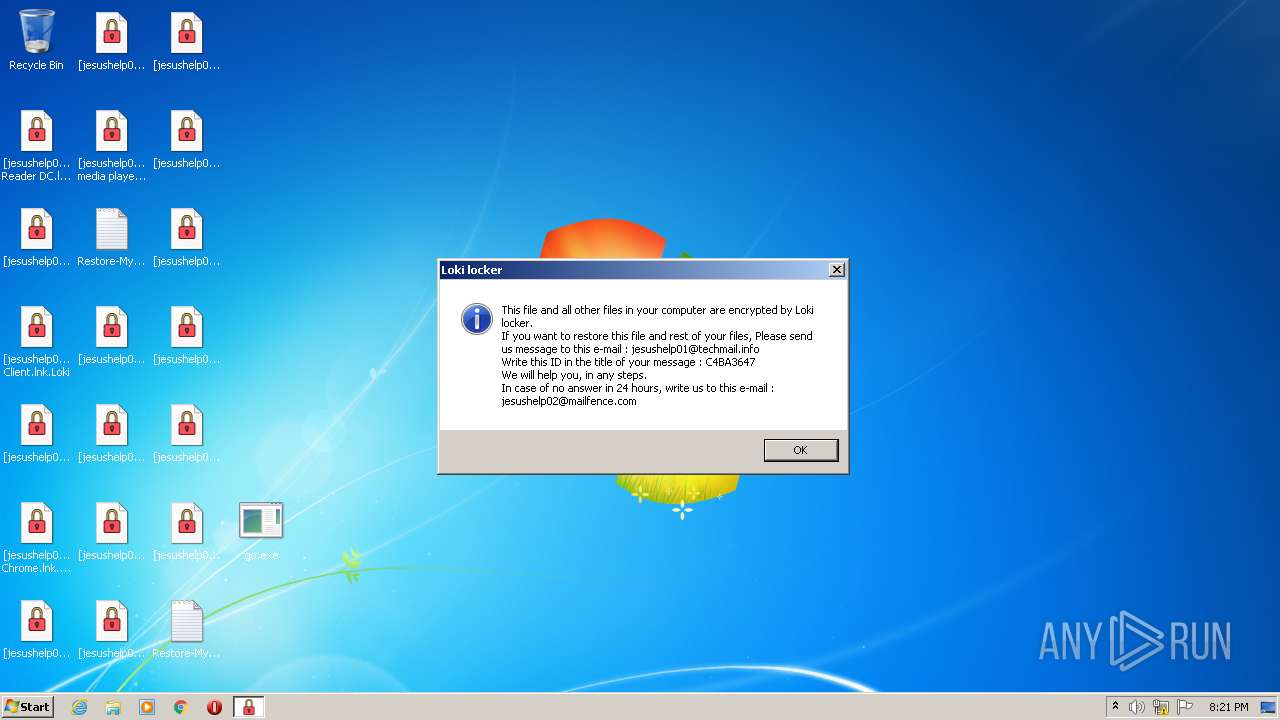
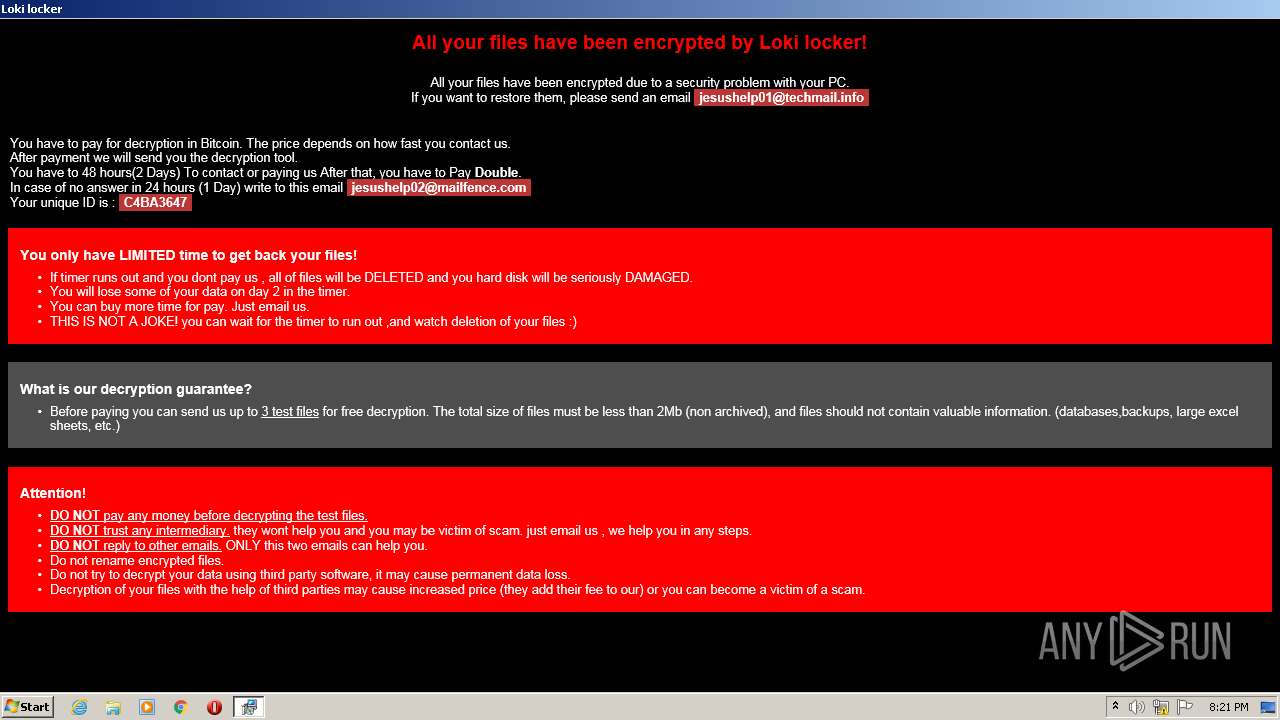
| File name: | 4857496168202240.zip |
| Full analysis: | https://app.any.run/tasks/30ed2dfa-466c-4f70-822e-7ddd5390d54f |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2022, 20:19:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 07C7911FEE7B10248C0581AB2B5CEA2C |
| SHA1: | DFE63284E426601E444693F1210DFAD769FE05EF |
| SHA256: | 15C502BD130BC27EB17DBD5506201B8F524C897CFB92CDC7574CF4C95620A721 |
| SSDEEP: | 6144:qB5u9bIp+MfhFB/SPYEslcFMU8nevGMjyTyejWY7jv5nSybYIkeWEjnirC9u+tOR:qU8pvfrBSPY7cFyTWYHgybR56D |
MALICIOUS
Application was dropped or rewritten from another process
- go.exe (PID: 3644)
- go.exe (PID: 1952)
- ovkf4nzt.exe (PID: 1512)
Writes to a start menu file
- go.exe (PID: 3644)
- go.exe (PID: 1952)
Changes the autorun value in the registry
- go.exe (PID: 3644)
- go.exe (PID: 1952)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 1432)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2140)
- wbengine.exe (PID: 3276)
Starts Visual C# compiler
- go.exe (PID: 3644)
- go.exe (PID: 1952)
Drops executable file immediately after starts
- csc.exe (PID: 452)
- csc.exe (PID: 328)
- go.exe (PID: 1952)
Application was injected by another process
- svchost.exe (PID: 332)
- svchost.exe (PID: 876)
- SearchIndexer.exe (PID: 2996)
Deletes shadow copies
- cmd.exe (PID: 1704)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 3484)
Runs injected code in another process
- wbadmin.exe (PID: 2844)
Starts BCDEDIT.EXE to disable recovery
- cmd.exe (PID: 3676)
Turns off the firewall via NETSH.EXE
- cmd.exe (PID: 1104)
Disables Windows Defender
- go.exe (PID: 1952)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3732)
- go.exe (PID: 3644)
- cvtres.exe (PID: 4056)
- csc.exe (PID: 452)
- cmd.exe (PID: 1432)
- csc.exe (PID: 328)
- cvtres.exe (PID: 4072)
- go.exe (PID: 1952)
- cmd.exe (PID: 3288)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 2408)
- WMIC.exe (PID: 2560)
- cmd.exe (PID: 3676)
- cmd.exe (PID: 1104)
- cmd.exe (PID: 2484)
- ovkf4nzt.exe (PID: 1512)
- mshta.exe (PID: 3616)
- cmd.exe (PID: 3484)
Reads the computer name
- WinRAR.exe (PID: 3732)
- go.exe (PID: 3644)
- go.exe (PID: 1952)
- WMIC.exe (PID: 2560)
- ovkf4nzt.exe (PID: 1512)
- mshta.exe (PID: 3616)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3732)
- go.exe (PID: 3644)
- csc.exe (PID: 452)
- go.exe (PID: 1952)
- csc.exe (PID: 328)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3732)
- go.exe (PID: 3644)
- csc.exe (PID: 452)
- go.exe (PID: 1952)
- csc.exe (PID: 328)
Creates files in the user directory
- go.exe (PID: 3644)
Starts CMD.EXE for commands execution
- go.exe (PID: 3644)
- go.exe (PID: 1952)
Creates files in the program directory
- go.exe (PID: 3644)
- csc.exe (PID: 452)
- csc.exe (PID: 328)
- go.exe (PID: 1952)
- SearchIndexer.exe (PID: 2996)
Creates files in the Windows directory
- svchost.exe (PID: 876)
- go.exe (PID: 1952)
- wbadmin.exe (PID: 2844)
Application launched itself
- go.exe (PID: 3644)
Changes default file association
- go.exe (PID: 1952)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 1104)
- cmd.exe (PID: 2484)
Executed as Windows Service
- vssvc.exe (PID: 3896)
- wbengine.exe (PID: 3276)
- vds.exe (PID: 3060)
Reads Environment values
- netsh.exe (PID: 2520)
- netsh.exe (PID: 2096)
Executed via COM
- DllHost.exe (PID: 3656)
- vdsldr.exe (PID: 3980)
Starts MSHTA.EXE for opening HTA or HTMLS files
- ovkf4nzt.exe (PID: 1512)
Writes to a desktop.ini file (may be used to cloak folders)
- go.exe (PID: 1952)
Reads Microsoft Outlook installation path
- mshta.exe (PID: 3616)
INFO
Manual execution by user
- go.exe (PID: 3644)
- ovkf4nzt.exe (PID: 1512)
Checks supported languages
- svchost.exe (PID: 876)
- schtasks.exe (PID: 2140)
- vssadmin.exe (PID: 3668)
- wbadmin.exe (PID: 2844)
- vssvc.exe (PID: 3896)
- bcdedit.exe (PID: 3224)
- netsh.exe (PID: 2520)
- wbengine.exe (PID: 3276)
- DllHost.exe (PID: 3656)
- bcdedit.exe (PID: 3236)
- netsh.exe (PID: 2096)
- wbadmin.exe (PID: 2608)
- vds.exe (PID: 3060)
- vdsldr.exe (PID: 3980)
Reads the computer name
- schtasks.exe (PID: 2140)
- wbadmin.exe (PID: 2844)
- wbadmin.exe (PID: 2608)
- vssvc.exe (PID: 3896)
- netsh.exe (PID: 2096)
- netsh.exe (PID: 2520)
- DllHost.exe (PID: 3656)
- vds.exe (PID: 3060)
- wbengine.exe (PID: 3276)
- vdsldr.exe (PID: 3980)
- vssadmin.exe (PID: 3668)
Reads internet explorer settings
- mshta.exe (PID: 3616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 15d7342be36d20ce615647fac9c2277f46b6d19aa54f3cf3d99e49d6ce0486d0 |
|---|---|
| ZipUncompressedSize: | 485888 |
| ZipCompressedSize: | 348505 |
| ZipCRC: | 0xc7089b66 |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
87
Monitored processes
35
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\i5sboeob.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | go.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 332 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\odptmeg3.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | go.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 876 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1104 | "C:\Windows\System32\cmd.exe" /C netsh advfirewall set currentprofile state off | C:\Windows\System32\cmd.exe | — | go.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | "C:\Windows\System32\cmd.exe" /C schtasks /CREATE /SC ONLOGON /TN Loki /TR C:\Users\admin\AppData\Roaming\winlogon.exe /RU SYSTEM /RL HIGHEST /F | C:\Windows\System32\cmd.exe | go.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
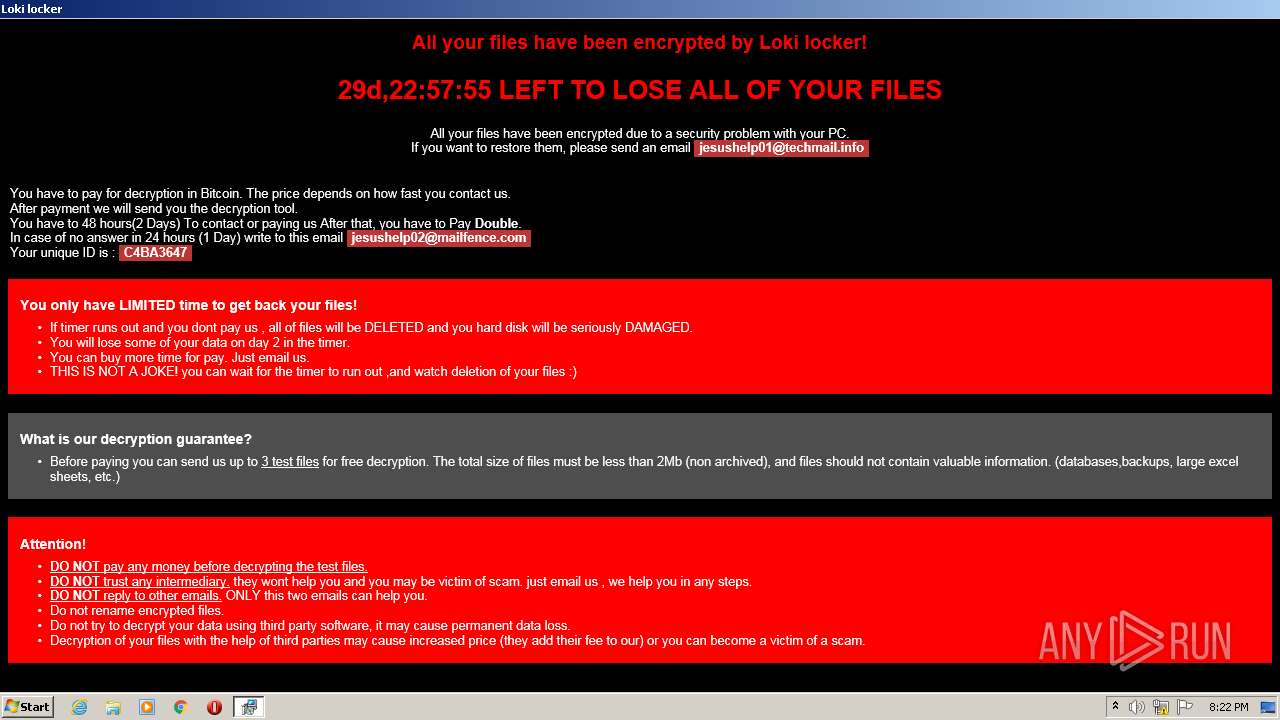
| 1512 | "C:\ProgramData\ovkf4nzt.exe" "C:\Users\admin\Desktop\[jesushelp01@techmail.info][C4BA3647]ratherbrown.jpg.Loki" | C:\ProgramData\ovkf4nzt.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1704 | "C:\Windows\System32\cmd.exe" /C wbadmin delete catalog -quiet | C:\Windows\System32\cmd.exe | — | go.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1952 | "C:\Users\admin\Desktop\go.exe" | C:\Users\admin\Desktop\go.exe | go.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: svchost Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2096 | netsh advfirewall set currentprofile state off | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 392
Read events
15 115
Write events
277
Delete events
0
Modification events
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\4857496168202240.zip | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3732) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
2 392
Text files
400
Unknown types
92
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 876 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 452 | csc.exe | C:\ProgramData\CSCF41E2E2A78C34658937750879B8021C0.TMP | res | |
MD5:— | SHA256:— | |||
| 876 | svchost.exe | C:\Windows\System32\Tasks\Loki | xml | |
MD5:— | SHA256:— | |||
| 3644 | go.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wvtymcow.bat | text | |
MD5:3FC537B642D3756646715325299C6367 | SHA256:708511C356493E41CA103DB51B8DF3FB57898DDB2BB7CF4F11560FACDE9425ED | |||
| 3644 | go.exe | C:\Users\admin\AppData\Roaming\winlogon.exe | executable | |
MD5:8AEA251877CB4F5EE6CF357831F8620C | SHA256:15D7342BE36D20CE615647FAC9C2277F46B6D19AA54F3CF3D99E49D6CE0486D0 | |||
| 3644 | go.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe | executable | |
MD5:8AEA251877CB4F5EE6CF357831F8620C | SHA256:15D7342BE36D20CE615647FAC9C2277F46B6D19AA54F3CF3D99E49D6CE0486D0 | |||
| 3732 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3732.14320\15d7342be36d20ce615647fac9c2277f46b6d19aa54f3cf3d99e49d6ce0486d0 | executable | |
MD5:8AEA251877CB4F5EE6CF357831F8620C | SHA256:15D7342BE36D20CE615647FAC9C2277F46B6D19AA54F3CF3D99E49D6CE0486D0 | |||
| 3644 | go.exe | C:\ProgramData\winlogon.exe | executable | |
MD5:8AEA251877CB4F5EE6CF357831F8620C | SHA256:15D7342BE36D20CE615647FAC9C2277F46B6D19AA54F3CF3D99E49D6CE0486D0 | |||
| 3644 | go.exe | C:\Users\admin\AppData\Local\Temp\y5hc1q4u.ico | image | |
MD5:DBC49B5F7714255217080C2E81F05A99 | SHA256:6D2F1F6164CBD331B9DC43B37948372E21B2EE45407AA99E199693835CDED09C | |||
| 3644 | go.exe | C:\Users\admin\AppData\Local\Temp\odptmeg3.0.cs | text | |
MD5:10B6718BE4F289FF55BA79E70761CD94 | SHA256:5A069E12E8222CC928722C39C6DAA871C23C977E3D43CF90CF8E46A05EC14494 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3644 | go.exe | POST | 200 | 91.223.82.6:80 | http://loki-locker.one/index.php | NL | binary | 601 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.1:445 | — | — | — | unknown |
— | — | 192.168.100.2:445 | — | — | — | whitelisted |
— | — | 192.168.100.1:139 | — | — | — | unknown |
3644 | go.exe | 91.223.82.6:80 | loki-locker.one | Iws Networks LLC | NL | malicious |
— | — | 192.168.100.2:139 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
loki-locker.one |
| malicious |