| download: | 26349f |
| Full analysis: | https://app.any.run/tasks/ded4de50-14fe-4ce7-a023-e4327b4f15d3 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 14:21:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
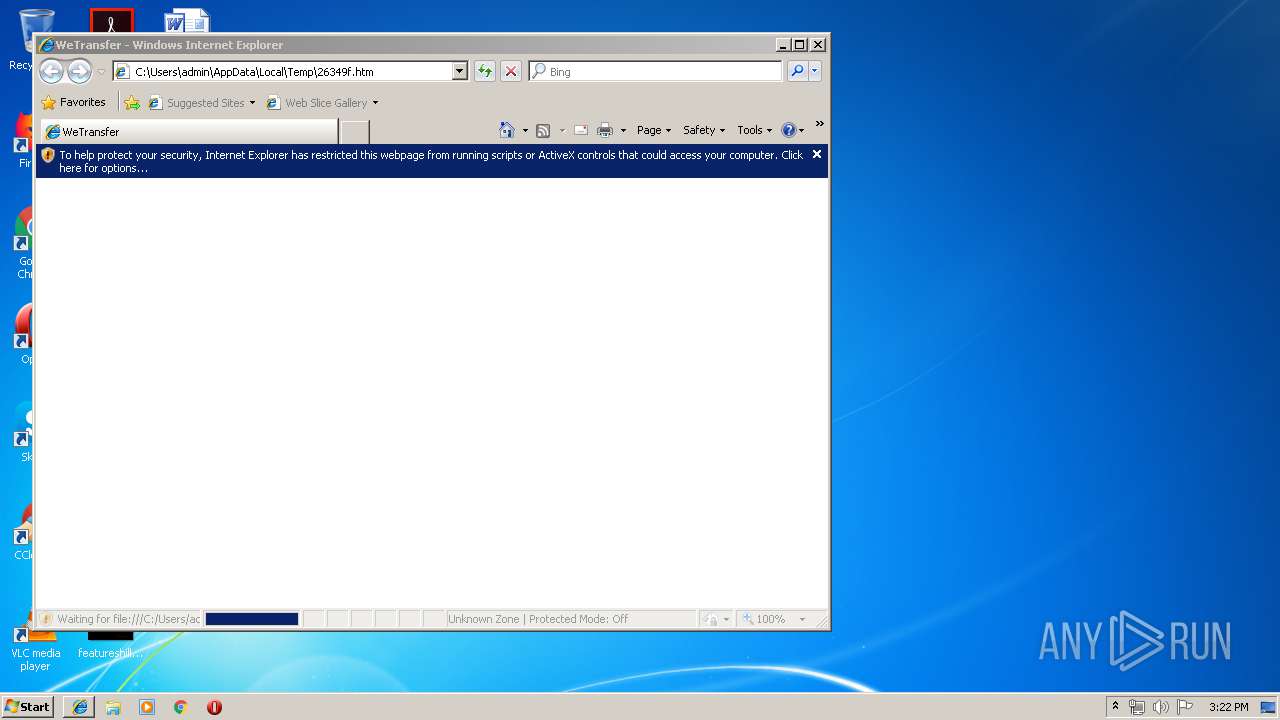
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines |
| MD5: | 99BB6FF120E654FB406D4471B9B2DB1F |
| SHA1: | CDA723A207B72AE596619985C0167CF2405C4E2C |
| SHA256: | 15B800C0EE3149074E5B2FD6215EE239FD178320A6A1C7BB5497DD0126E78D53 |
| SSDEEP: | 1536:UKEja2W7fazXBRIYeLbfCzbr2UdiUC3jP0BEih70TDuH:UKEjax7cdQbcrsP0BEihSDuH |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3544)
INFO
Application launched itself
- iexplore.exe (PID: 860)
- chrome.exe (PID: 3544)
Reads Internet Cache Settings
- iexplore.exe (PID: 3372)
Creates files in the user directory
- iexplore.exe (PID: 3372)
Reads internet explorer settings
- iexplore.exe (PID: 3372)
Changes settings of System certificates
- iexplore.exe (PID: 3372)
Manual execution by user
- chrome.exe (PID: 3544)
Changes internet zones settings
- iexplore.exe (PID: 860)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| HTTPEquivXUACompatible: | IE=edge |
|---|---|
| viewport: | width=device-width, minimum-scale=1, initial-scale=1, user-scalable=no |
| pinterest: | nopin |
| referrer: | origin |
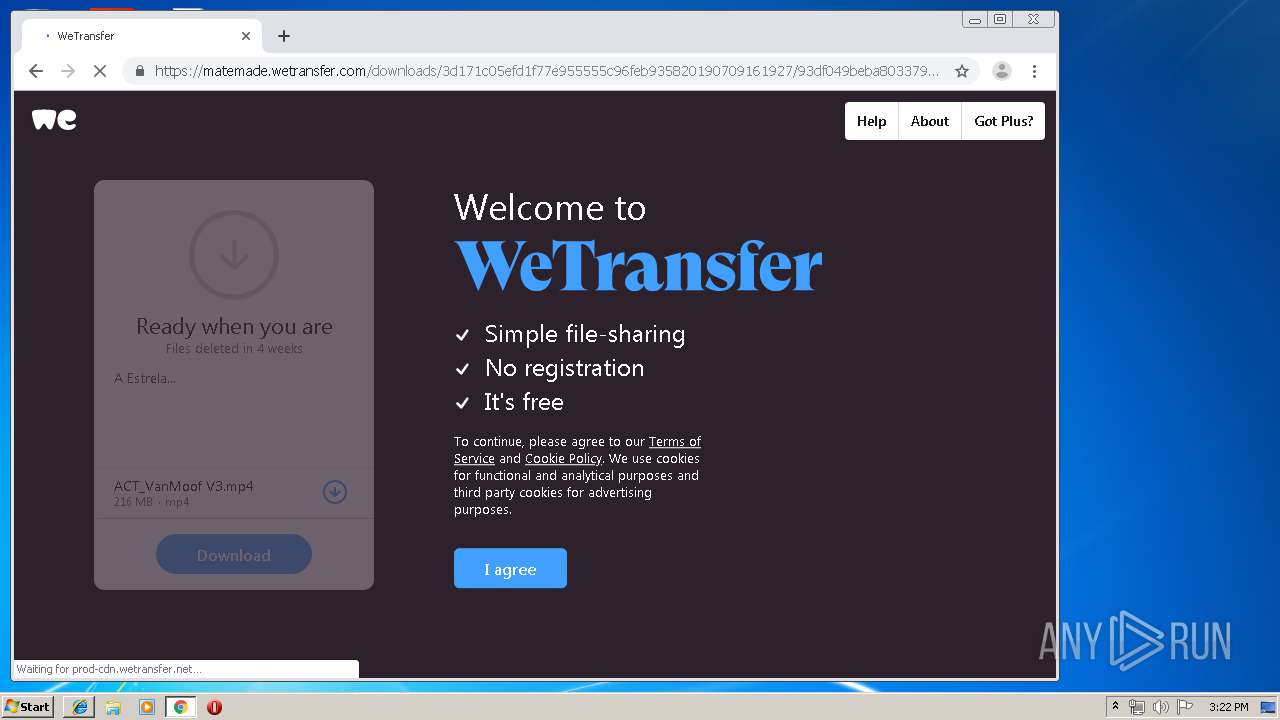
| Description: | WeTransfer is the simplest way to send your files around the world. Share large files up to 2GB for free. |
| Author: | WeTransfer |
| applicationName: | WeTransfer |
| csrfParam: | authenticity_token |
| csrfToken: | Bojk+v2M0ecOiBrUIX7jRa6aug3bB+O6djJt2p1vDIMaE3yisP1EBiBt84ON/7J9e1fgUBmkKL6Vbj3Q+fYfzw== |
| Title: | WeTransfer |
Total processes
67
Monitored processes
28
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2697331926286550129 --mojo-platform-channel-handle=3496 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 860 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\26349f.htm | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6bf1a9d0,0x6bf1a9e0,0x6bf1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13490069864605791028 --mojo-platform-channel-handle=3700 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4108654234673334570 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2148 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2503832246838963263 --mojo-platform-channel-handle=3620 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12600796830481013927 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2408 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=10987122387509094452 --mojo-platform-channel-handle=1580 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3336 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,9341188734794893758,17704999674763623341,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7298536172673452812 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2516 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 340
Read events
1 170
Write events
161
Delete events
9
Modification events
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E307070004000B000E00150037001E00 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | LoadTime |
Value: 8 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\iexplore |
| Operation: | write | Name: | Time |
Value: E307070004000B000E00150037002E00 | |||
| (PID) Process: | (860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (860) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
44
Text files
214
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 860 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 860 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabDE20.tmp | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarDE21.tmp | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabDE32.tmp | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarDE33.tmp | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabDF0F.tmp | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarDF10.tmp | — | |
MD5:— | SHA256:— | |||
| 3544 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
67
DNS requests
45
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2160 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3372 | iexplore.exe | GET | 200 | 2.16.186.89:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 56.3 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
2160 | chrome.exe | GET | 200 | 173.194.129.201:80 | http://r4---sn-aigzrn7s.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.217.117.45&mm=28&mn=sn-aigzrn7s&ms=nvh&mt=1562854886&mv=m&mvi=3&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3372 | iexplore.exe | OPTIONS | 400 | 172.217.18.168:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
860 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3372 | iexplore.exe | 13.224.196.31:443 | prod-cdn.wetransfer.net | — | US | unknown |
3372 | iexplore.exe | 13.224.197.19:80 | x.ss2.us | — | US | unknown |
4 | System | 172.217.18.168:139 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3372 | iexplore.exe | 2.16.186.89:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3372 | iexplore.exe | 172.217.18.168:80 | www.googletagmanager.com | Google Inc. | US | whitelisted |
4 | System | 172.217.18.168:445 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2160 | chrome.exe | 172.217.16.131:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2160 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2160 | chrome.exe | 172.217.16.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
prod-cdn.wetransfer.net |
| whitelisted |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
10 ETPRO signatures available at the full report