| File name: | hwi_764.exe |
| Full analysis: | https://app.any.run/tasks/50db6a16-7d4c-43e9-956c-0c7f9d9b9a43 |
| Verdict: | Malicious activity |
| Analysis date: | October 18, 2023, 21:48:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0702F46419FD200AC2BB499D501B7001 |
| SHA1: | E74B1FA64324817C28A34DAD05DE03D9DE477CAF |
| SHA256: | 15B6A49ABBCD040B8BD67FF1E7CF98E4C3F48DBF9973FD555BA247B3F30DA287 |
| SSDEEP: | 98304:chN0zuSU+HKouVEU1I+tv9S0jlaT2lRKtUXHJZLqIKfUHg9V5tJY2zM2hpJnzkiS:ZbjsdbBGdEiUSG312f5u |
MALICIOUS
Drops the executable file immediately after the start
- hwi_764.exe (PID: 556)
- hwi_764.exe (PID: 3824)
- hwi_764.tmp (PID: 1632)
- HWiNFO32.EXE (PID: 3472)
Loads dropped or rewritten executable
- hwi_764.tmp (PID: 1632)
Application was dropped or rewritten from another process
- HWiNFO32.EXE (PID: 3740)
- HWiNFO32.EXE (PID: 3472)
SUSPICIOUS
Process drops legitimate windows executable
- hwi_764.tmp (PID: 1632)
Reads the Windows owner or organization settings
- hwi_764.tmp (PID: 1632)
Reads the Internet Settings
- hwi_764.tmp (PID: 3708)
- HWiNFO32.EXE (PID: 3472)
Drops a system driver (possible attempt to evade defenses)
- HWiNFO32.EXE (PID: 3472)
Checks Windows Trust Settings
- HWiNFO32.EXE (PID: 3472)
Reads security settings of Internet Explorer
- HWiNFO32.EXE (PID: 3472)
Reads settings of System Certificates
- HWiNFO32.EXE (PID: 3472)
INFO
Checks supported languages
- hwi_764.exe (PID: 556)
- hwi_764.tmp (PID: 3708)
- hwi_764.exe (PID: 3824)
- hwi_764.tmp (PID: 1632)
- HWiNFO32.EXE (PID: 3472)
Reads the computer name
- hwi_764.tmp (PID: 3708)
- hwi_764.tmp (PID: 1632)
- HWiNFO32.EXE (PID: 3472)
Create files in a temporary directory
- hwi_764.exe (PID: 556)
- hwi_764.exe (PID: 3824)
- hwi_764.tmp (PID: 1632)
- HWiNFO32.EXE (PID: 3472)
Application was dropped or rewritten from another process
- hwi_764.tmp (PID: 3708)
- hwi_764.tmp (PID: 1632)
Creates files in the program directory
- hwi_764.tmp (PID: 1632)
- HWiNFO32.EXE (PID: 3472)
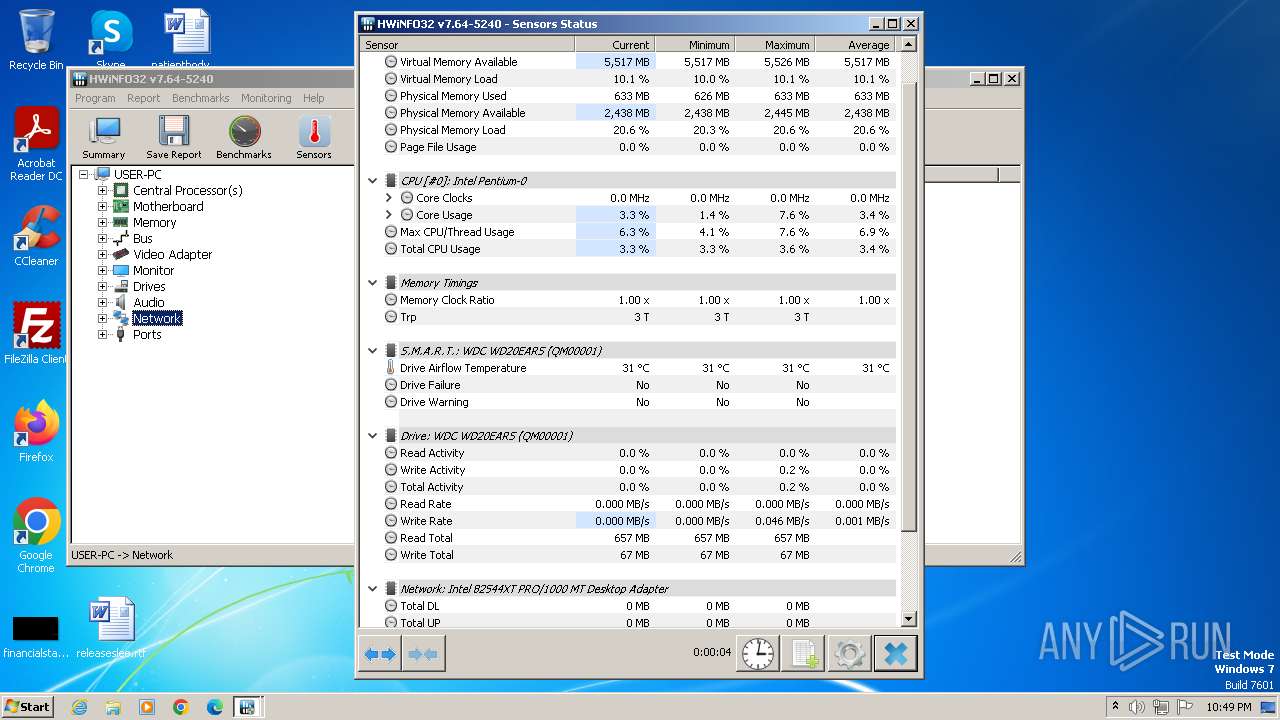
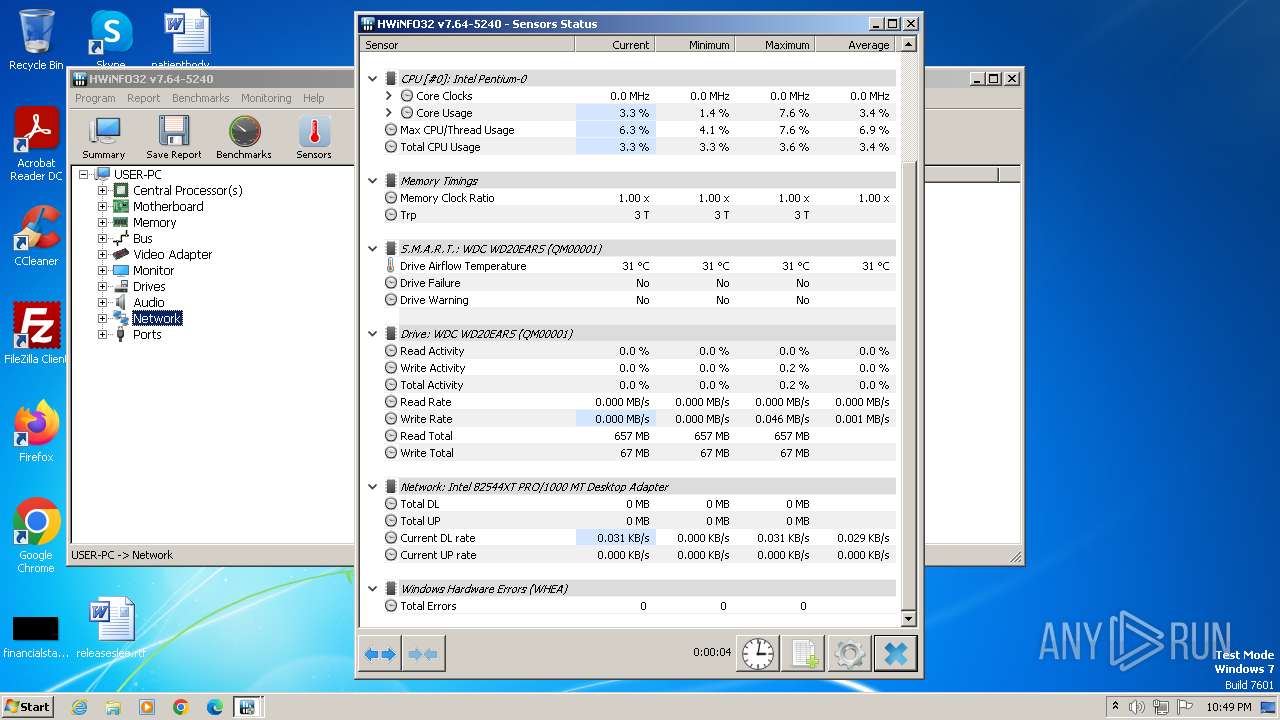
Reads CPU info
- HWiNFO32.EXE (PID: 3472)
Reads the machine GUID from the registry
- HWiNFO32.EXE (PID: 3472)
Checks proxy server information
- HWiNFO32.EXE (PID: 3472)
Creates files or folders in the user directory
- HWiNFO32.EXE (PID: 3472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.9) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (16.7) |
| .exe | | | Win32 Executable Delphi generic (8.7) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 84480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Martin Malik, REALiX s.r.o. |
| FileDescription: | |
| FileVersion: | |
| LegalCopyright: | Copyright ©1999-2023 Martin Malik, REALiX s.r.o. |
| ProductName: | |
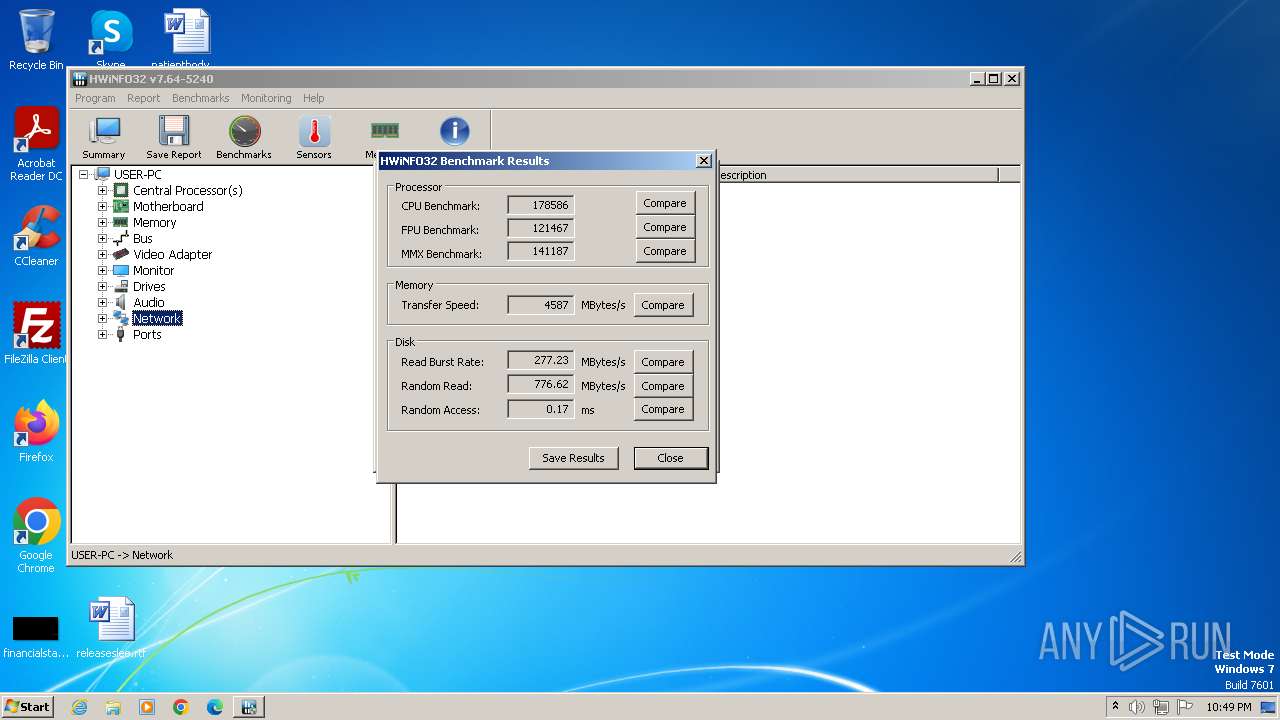
| ProductVersion: | 7.64 |
Total processes
49
Monitored processes
6
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Users\admin\AppData\Local\Temp\hwi_764.exe" | C:\Users\admin\AppData\Local\Temp\hwi_764.exe | — | explorer.exe | |||||||||||
User: admin Company: Martin Malik, REALiX s.r.o. Integrity Level: MEDIUM Description: Exit code: 0 Version: Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\AppData\Local\Temp\is-KAGG9.tmp\hwi_764.tmp" /SL5="$150220,11831683,123392,C:\Users\admin\AppData\Local\Temp\hwi_764.exe" /SPAWNWND=$4036C /NOTIFYWND=$602F8 | C:\Users\admin\AppData\Local\Temp\is-KAGG9.tmp\hwi_764.tmp | — | hwi_764.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3472 | "C:\Program Files\HWiNFO32\HWiNFO32.EXE" | C:\Program Files\HWiNFO32\HWiNFO32.EXE | hwi_764.tmp | ||||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: HIGH Description: HWiNFO32 Exit code: 0 Version: 7.64-5240 Modules
| |||||||||||||||
| 3708 | "C:\Users\admin\AppData\Local\Temp\is-F1NES.tmp\hwi_764.tmp" /SL5="$602F8,11831683,123392,C:\Users\admin\AppData\Local\Temp\hwi_764.exe" | C:\Users\admin\AppData\Local\Temp\is-F1NES.tmp\hwi_764.tmp | — | hwi_764.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3740 | "C:\Program Files\HWiNFO32\HWiNFO32.EXE" | C:\Program Files\HWiNFO32\HWiNFO32.EXE | — | hwi_764.tmp | |||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: MEDIUM Description: HWiNFO32 Exit code: 3221226540 Version: 7.64-5240 Modules
| |||||||||||||||
| 3824 | "C:\Users\admin\AppData\Local\Temp\hwi_764.exe" /SPAWNWND=$4036C /NOTIFYWND=$602F8 | C:\Users\admin\AppData\Local\Temp\hwi_764.exe | hwi_764.tmp | ||||||||||||
User: admin Company: Martin Malik, REALiX s.r.o. Integrity Level: HIGH Description: Exit code: 0 Version: Modules
| |||||||||||||||
Total events
6 815
Read events
6 726
Write events
46
Delete events
43
Modification events
| (PID) Process: | (3708) hwi_764.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3708) hwi_764.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3708) hwi_764.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3708) hwi_764.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3472) HWiNFO32.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
10
Suspicious files
8
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | hwi_764.exe | C:\Users\admin\AppData\Local\Temp\is-KAGG9.tmp\hwi_764.tmp | executable | |
MD5:751D4F1D0F96F1DF71F778391555E52B | SHA256:249A43F4202A145F53CB034C6AD9AB91A2F783621B4B172B89660F91A9285D1F | |||
| 3472 | HWiNFO32.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:AA683A53C531D8B0BFA9C61E10238CF6 | SHA256:270EFD03AAE8270E3FE57B5366CD38BBBDC24DB12C0363518245C2F170C26144 | |||
| 1632 | hwi_764.tmp | C:\Program Files\HWiNFO32\unins000.dat | binary | |
MD5:C0B07DBBEE70948B46EEAFB1D4D9C0A4 | SHA256:8DBD0C8A95129128F96A14B8144F1B916D73F945F4B2E6F0C894E650EC15524D | |||
| 1632 | hwi_764.tmp | C:\Program Files\HWiNFO32\is-6LHM4.tmp | executable | |
MD5:AC788D19BF96CA1108756D82355115E9 | SHA256:6B9CB8DC1574446ABB7ECF02ADF62529A0F1DA46C38725BDE5794600CE7ACF89 | |||
| 3472 | HWiNFO32.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:B4BE53FFEB16270E840162D95BEBF6C9 | SHA256:E6D2F02F91105FD282E943D149A7CC5CA20E1AAC307A92A67836D29A639599D2 | |||
| 3472 | HWiNFO32.EXE | C:\Users\admin\AppData\Local\Temp\HWiNFO32_187.SYS | executable | |
MD5:718937A3E7E00E752A44C6B093057D52 | SHA256:F78EA9EB1966A7CB9407F5EF0640EE1034E6E49EF820625BE55D7884D2B98475 | |||
| 1632 | hwi_764.tmp | C:\Program Files\HWiNFO32\HWiNFO32.EXE | executable | |
MD5:BA4545C2F4CE942A50445CF422A0F5DB | SHA256:B9E12BD6952186D303A79896C937FE8A58A4619092C6B1FC470E048F1D7A4FBA | |||
| 3472 | HWiNFO32.EXE | C:\Program Files\HWiNFO32\HWiNFO32.INI | text | |
MD5:31EA0D720B02F5BE9A0A8C843FA525B6 | SHA256:2B52116A161DB87EAD7FBA5329E113610A39EC5183D713A9D9A7222FE657C949 | |||
| 1632 | hwi_764.tmp | C:\Users\admin\AppData\Local\Temp\is-2KSJS.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 3472 | HWiNFO32.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:0D559A477BCE71E75257BB8389B787FA | SHA256:F9A632DEBB7A23BD3C67E5E568E442F177023641C7B0F9AF121710DAA3204D22 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3472 | HWiNFO32.EXE | GET | 200 | 8.248.147.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4cecca3696452d98 | unknown | compressed | 4.66 Kb | unknown |
3472 | HWiNFO32.EXE | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3472 | HWiNFO32.EXE | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3472 | HWiNFO32.EXE | 172.67.205.235:443 | www.hwinfo.com | CLOUDFLARENET | US | unknown |
3472 | HWiNFO32.EXE | 8.248.147.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3472 | HWiNFO32.EXE | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.hwinfo.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |