| URL: | client.zspeed-cdn.com |
| Full analysis: | https://app.any.run/tasks/f4c5fc08-4b83-40de-ae6c-c716e7e464bf |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2025, 12:57:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8F412ABE7AC76DB51DBB77171393C8F1 |
| SHA1: | FAEB6C5EC2E5551ADEFFD675AD2FB9F3A0C781F4 |
| SHA256: | 15A81314962C54F7D7FF4D09D856EE1100A670A99CAD0F50C819F7183C0E73B6 |
| SSDEEP: | 3:MIqA2Tn:MdA6 |
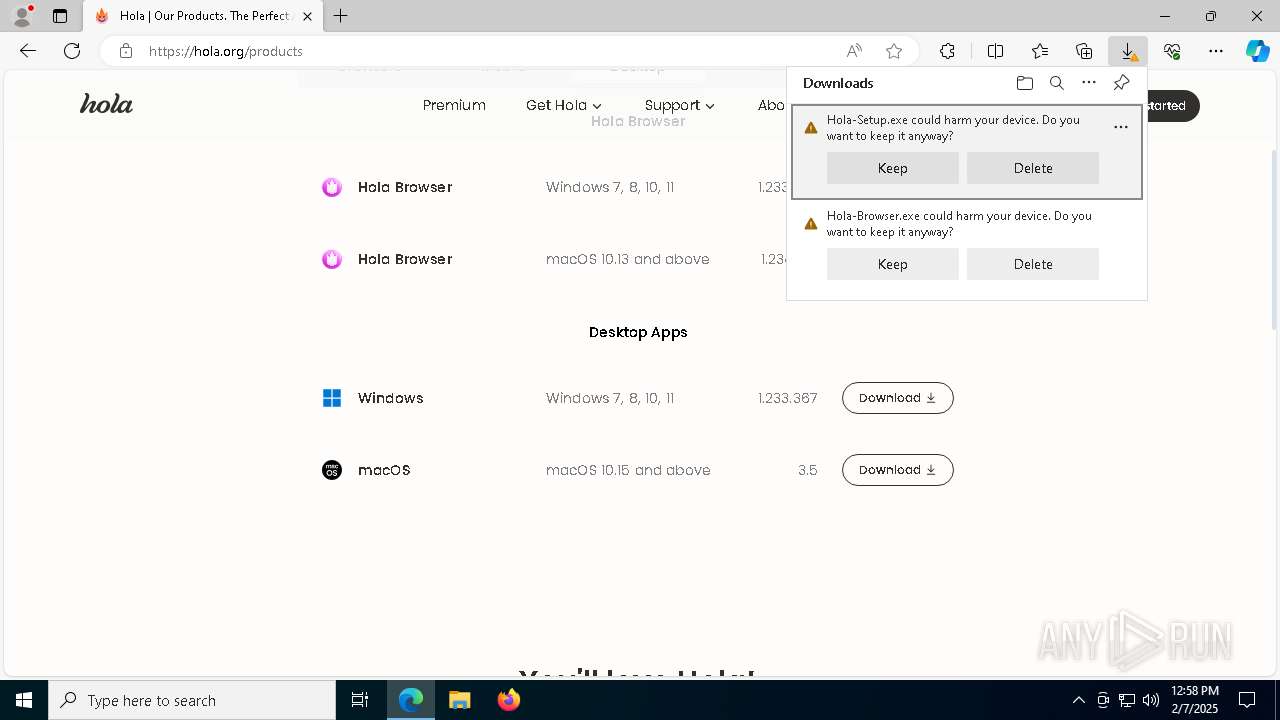
MALICIOUS
Changes the autorun value in the registry
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
SUSPICIOUS
Reads security settings of Internet Explorer
- Hola-Browser.exe (PID: 1156)
- Hola-Browser.exe (PID: 3876)
- net_updater64.exe (PID: 7188)
Executes application which crashes
- Hola-Setup.exe (PID: 5628)
- Hola-Browser.exe (PID: 4516)
- Hola-Setup.exe (PID: 4864)
Application launched itself
- Hola-Browser.exe (PID: 1156)
- Hola-Browser.exe (PID: 3876)
- hola_svc.exe (PID: 4244)
- hola_cr.exe (PID: 8668)
Executable content was dropped or overwritten
- Hola-Browser.exe (PID: 3876)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 4392)
- net_updater64.exe (PID: 7384)
- 7zr.exe (PID: 6156)
- Hola-Setup-x64-1.233.367.exe (PID: 8868)
Drops 7-zip archiver for unpacking
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
Creates a software uninstall entry
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
Executes as Windows Service
- net_updater64.exe (PID: 5304)
- hola_svc.exe (PID: 4244)
- WmiApSrv.exe (PID: 1348)
Checks Windows Trust Settings
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 7188)
The process drops C-runtime libraries
- net_updater64.exe (PID: 5304)
Process drops legitimate windows executable
- net_updater64.exe (PID: 5304)
Detected use of alternative data streams (AltDS)
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 4392)
- net_updater64.exe (PID: 7384)
Creates file in the systems drive root
- hola_svc.exe (PID: 4244)
Windows service management via SC.EXE
- sc.exe (PID: 7224)
- sc.exe (PID: 2572)
- sc.exe (PID: 2432)
- sc.exe (PID: 8132)
- sc.exe (PID: 7380)
- sc.exe (PID: 2008)
- sc.exe (PID: 6004)
- sc.exe (PID: 1460)
- sc.exe (PID: 7976)
- sc.exe (PID: 6056)
- sc.exe (PID: 2148)
- sc.exe (PID: 2072)
- sc.exe (PID: 1852)
- sc.exe (PID: 5200)
- sc.exe (PID: 3680)
- sc.exe (PID: 6272)
- sc.exe (PID: 4328)
- sc.exe (PID: 8)
- sc.exe (PID: 7572)
- sc.exe (PID: 7188)
- sc.exe (PID: 4816)
- sc.exe (PID: 7152)
- sc.exe (PID: 5936)
- sc.exe (PID: 7232)
- sc.exe (PID: 6444)
- sc.exe (PID: 5320)
- sc.exe (PID: 3984)
- sc.exe (PID: 7640)
- sc.exe (PID: 7300)
- sc.exe (PID: 5964)
- sc.exe (PID: 8032)
- sc.exe (PID: 2280)
- sc.exe (PID: 7532)
- sc.exe (PID: 7544)
- sc.exe (PID: 7904)
- sc.exe (PID: 7820)
- sc.exe (PID: 7004)
- sc.exe (PID: 4300)
- sc.exe (PID: 6664)
- sc.exe (PID: 5300)
- sc.exe (PID: 3796)
- sc.exe (PID: 1868)
- sc.exe (PID: 6852)
- sc.exe (PID: 6860)
- sc.exe (PID: 7632)
- sc.exe (PID: 7016)
- sc.exe (PID: 7388)
- sc.exe (PID: 1304)
- sc.exe (PID: 3920)
- sc.exe (PID: 6388)
- sc.exe (PID: 6360)
- sc.exe (PID: 4360)
- sc.exe (PID: 8328)
- sc.exe (PID: 8748)
- sc.exe (PID: 8756)
- sc.exe (PID: 8788)
- sc.exe (PID: 8764)
- sc.exe (PID: 8772)
- sc.exe (PID: 8780)
- sc.exe (PID: 8828)
- sc.exe (PID: 8804)
- sc.exe (PID: 4764)
- sc.exe (PID: 7124)
- sc.exe (PID: 8796)
Starts SC.EXE for service management
- hola_svc.exe (PID: 4244)
Checks for external IP
- net_updater64.exe (PID: 5304)
Connects to unusual port
- hola_svc.exe (PID: 4244)
The process checks if it is being run in the virtual environment
- net_updater64.exe (PID: 5304)
- hola_cr.exe (PID: 8668)
INFO
Reads Environment values
- identity_helper.exe (PID: 7652)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 4392)
- net_updater64.exe (PID: 7384)
Executable content was dropped or overwritten
- msedge.exe (PID: 6752)
- msedge.exe (PID: 6428)
- msedge.exe (PID: 7116)
Reads the computer name
- identity_helper.exe (PID: 7652)
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- Hola-Browser.exe (PID: 4516)
- Hola-Browser.exe (PID: 3876)
- Hola-Browser.exe (PID: 5536)
- Hola-Setup.exe (PID: 4864)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 5304)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 7188)
- hola_svc.exe (PID: 4244)
- net_updater64.exe (PID: 4392)
- idle_report.exe (PID: 2220)
- test_wpf.exe (PID: 7068)
- net_updater64.exe (PID: 7384)
- idle_report.exe (PID: 5496)
- test_wpf.exe (PID: 8096)
- hola_cr.exe (PID: 8644)
- Hola-Setup-x64-1.233.367.exe (PID: 9016)
Checks supported languages
- identity_helper.exe (PID: 7652)
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- Hola-Browser.exe (PID: 4516)
- Hola-Browser.exe (PID: 3876)
- Hola-Browser.exe (PID: 5536)
- Hola-Setup.exe (PID: 4864)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 5304)
- test_wpf.exe (PID: 1460)
- test_wpf.exe (PID: 6176)
- net_updater64.exe (PID: 7188)
- hola_svc.exe (PID: 4244)
- net_updater64.exe (PID: 4392)
- test_wpf.exe (PID: 7068)
- hola_svc.exe (PID: 6840)
- hola_svc.exe (PID: 7620)
- Hola-Setup-x64-1.233.367.exe (PID: 8868)
- net_updater64.exe (PID: 7384)
- idle_report.exe (PID: 5496)
- hola.exe (PID: 8664)
- hola_cr.exe (PID: 8616)
- hola_cr.exe (PID: 8644)
- hola_cr.exe (PID: 7460)
- hola_cr.exe (PID: 6176)
- hola_cr.exe (PID: 8728)
- Hola-Setup-x64-1.233.367.exe (PID: 9016)
- hola_cr.exe (PID: 6272)
- hola_cr.exe (PID: 7068)
- hola_cr.exe (PID: 6852)
- hola_cr.exe (PID: 8820)
- hola_cr.exe (PID: 8368)
- hola_cr.exe (PID: 7936)
- hola_cr.exe (PID: 7848)
- hola_cr.exe (PID: 3124)
- hola_cr.exe (PID: 8776)
- hola_cr.exe (PID: 5392)
- hola_cr.exe (PID: 7504)
Reads the machine GUID from the registry
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- Hola-Browser.exe (PID: 3876)
- Hola-Browser.exe (PID: 5536)
- Hola-Browser.exe (PID: 4516)
- Hola-Setup.exe (PID: 4864)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 5304)
- test_wpf.exe (PID: 6176)
- test_wpf.exe (PID: 1460)
- hola_svc.exe (PID: 4244)
- idle_report.exe (PID: 2220)
- net_updater64.exe (PID: 4392)
- test_wpf.exe (PID: 7068)
- net_updater64.exe (PID: 7384)
- test_wpf.exe (PID: 8096)
- idle_report.exe (PID: 5496)
Disables trace logs
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- Hola-Browser.exe (PID: 5536)
- Hola-Browser.exe (PID: 3876)
- net_updater64.exe (PID: 5304)
- hola_svc.exe (PID: 4244)
- rasdial.exe (PID: 7152)
- rasdial.exe (PID: 7340)
- rasdial.exe (PID: 2972)
- rasdial.exe (PID: 8592)
- rasdial.exe (PID: 5536)
- rasdial.exe (PID: 9196)
- rasdial.exe (PID: 7956)
- rasdial.exe (PID: 8596)
Checks proxy server information
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- WerFault.exe (PID: 5096)
- Hola-Browser.exe (PID: 5536)
- Hola-Browser.exe (PID: 3876)
- WerFault.exe (PID: 6032)
- WerFault.exe (PID: 2292)
- net_updater64.exe (PID: 7188)
- hola_cr.exe (PID: 8668)
Create files in a temporary directory
- Hola-Browser.exe (PID: 1156)
- Hola-Browser.exe (PID: 3876)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- Hola-Setup-x64-1.233.367.exe (PID: 8868)
- Hola-Setup-x64-1.233.367.exe (PID: 9016)
- hola_cr.exe (PID: 8668)
Reads the software policy settings
- Hola-Browser.exe (PID: 1156)
- Hola-Setup.exe (PID: 5628)
- WerFault.exe (PID: 5096)
- Hola-Browser.exe (PID: 5536)
- WerFault.exe (PID: 6032)
- WerFault.exe (PID: 2292)
- Hola-Browser.exe (PID: 3876)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 4392)
- net_updater64.exe (PID: 7384)
- Hola-Setup-x64-1.233.367.exe (PID: 9016)
- hola.exe (PID: 8664)
Application launched itself
- msedge.exe (PID: 6428)
Process checks computer location settings
- Hola-Browser.exe (PID: 1156)
- Hola-Browser.exe (PID: 3876)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 7384)
- hola_cr.exe (PID: 6272)
- hola_cr.exe (PID: 7068)
- hola_cr.exe (PID: 7936)
- hola_cr.exe (PID: 7848)
- hola_cr.exe (PID: 3124)
- hola_cr.exe (PID: 8368)
- hola_cr.exe (PID: 7504)
Creates files or folders in the user directory
- WerFault.exe (PID: 6032)
- WerFault.exe (PID: 2292)
- WerFault.exe (PID: 5096)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 7188)
- hola_cr.exe (PID: 8668)
- hola_cr.exe (PID: 8644)
The sample compiled with english language support
- Hola-Browser.exe (PID: 3876)
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 5304)
- 7zr.exe (PID: 6156)
- msedge.exe (PID: 7116)
- Hola-Setup-x64-1.233.367.exe (PID: 8868)
Creates files in the program directory
- Hola-Setup-x64-1.233.367.exe (PID: 5788)
- net_updater64.exe (PID: 5460)
- net_updater64.exe (PID: 7188)
- net_updater64.exe (PID: 5304)
- net_updater64.exe (PID: 4392)
- hola_svc.exe (PID: 4244)
- net_updater64.exe (PID: 7384)
- 7zr.exe (PID: 6156)
- Hola-Setup-x64-1.233.367.exe (PID: 8868)
- Hola-Setup-x64-1.233.367.exe (PID: 9016)
- hola.exe (PID: 8664)
Reads the time zone
- net_updater64.exe (PID: 5304)
Reads CPU info
- net_updater64.exe (PID: 5304)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7012)
- explorer.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
476
Monitored processes
334
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | sc query luminati_net_updater_win_hola_browser_and_vpn_hola_org | C:\Windows\System32\sc.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | rasdial | C:\Windows\System32\rasdial.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1144 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\Downloads\Hola-Browser.exe" | C:\Users\admin\Downloads\Hola-Browser.exe | msedge.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: MEDIUM Description: Hola Browser Setup Exit code: 0 Version: 1.227.226.0 Modules
| |||||||||||||||
| 1172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1220 | rasdial | C:\Windows\System32\rasdial.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1304 | sc query luminati_net_updater_win_hola_auto_sdk_hola_org | C:\Windows\System32\sc.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
69 352
Read events
69 159
Write events
191
Delete events
2
Modification events
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 95836330238C2F00 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 24F47830238C2F00 | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FB525747-267C-40EC-8B60-E0BC8FBF0F7B} | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9F1E8329-E881-47F1-89DA-52C1B9D25325} | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {2E120CD6-4E29-4E7E-970D-D592CCC47BCB} | |||
| (PID) Process: | (6428) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328530 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E4E80067-5D95-4E55-BA4E-2169D35B9B0B} | |||
Executable files
84
Suspicious files
791
Text files
101
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135799.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135799.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1357a9.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1357a9.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135799.TMP | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6428 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
71
TCP/UDP connections
326
DNS requests
261
Threats
58
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6348 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6428 | msedge.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAXrhBDPOQ2gaSPA09Ycq3A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.23:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6072 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6072 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
client.zspeed-cdn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
5304 | net_updater64.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
8644 | hola_cr.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
Process | Message |
|---|---|
hola_cr.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Roaming directory exists )
|