| File name: | jargon.vbs |
| Full analysis: | https://app.any.run/tasks/f5386e97-c5d2-4858-a554-f6074dfd0654 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2019, 16:34:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 524D38B7488A490C0A93A2D248CA05C3 |
| SHA1: | 3C4CC4519601C041B9403D3B2DB9F0B763C65BD3 |
| SHA256: | 15A7F28FD3E63122D328F8057CBD57FF82125A24F66C7D6A32DC267558D0A0E1 |
| SSDEEP: | 48:aA+OkuYnQ32DikIqF9u5wiUqAOyCy0AIu0iRl/RlKRlJSTutk/:aAFkXbGb+A5OD0hiRtRgRDSTutC |
MALICIOUS
Changes the autorun value in the registry
- WScript.exe (PID: 2508)
- WScript.exe (PID: 2156)
SUSPICIOUS
Application launched itself
- WScript.exe (PID: 2156)
Executes scripts
- WScript.exe (PID: 2156)
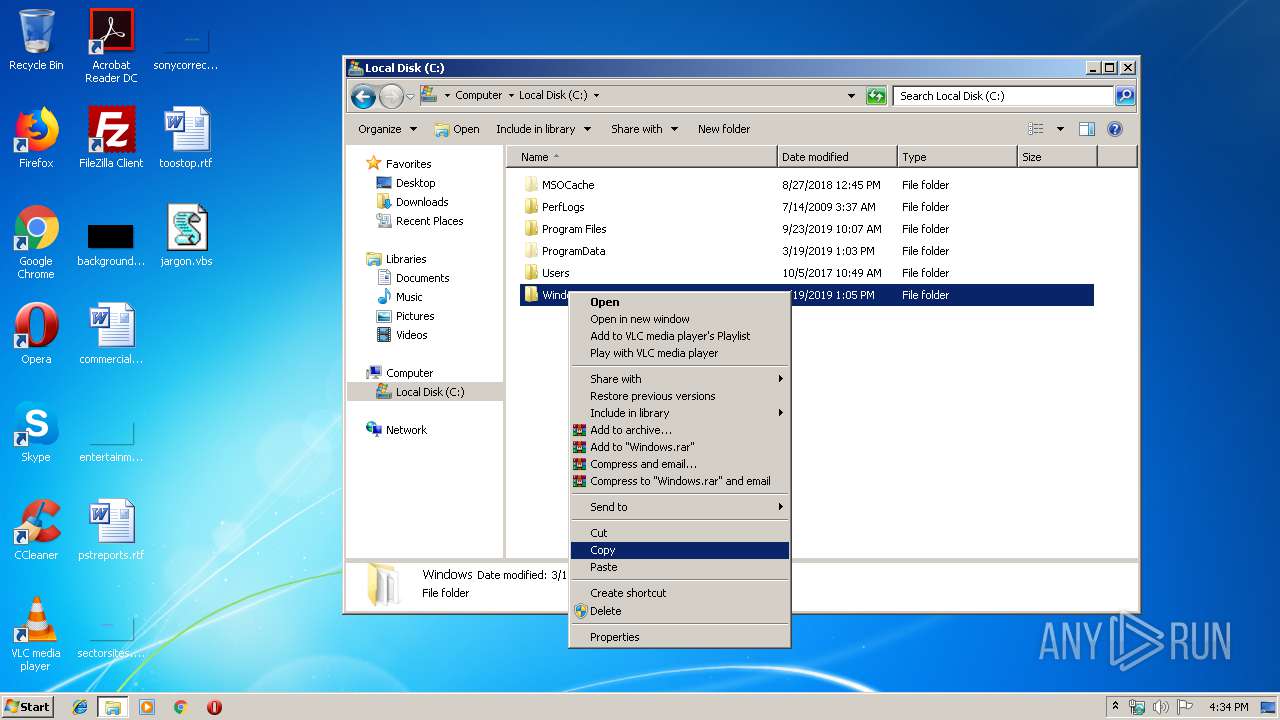
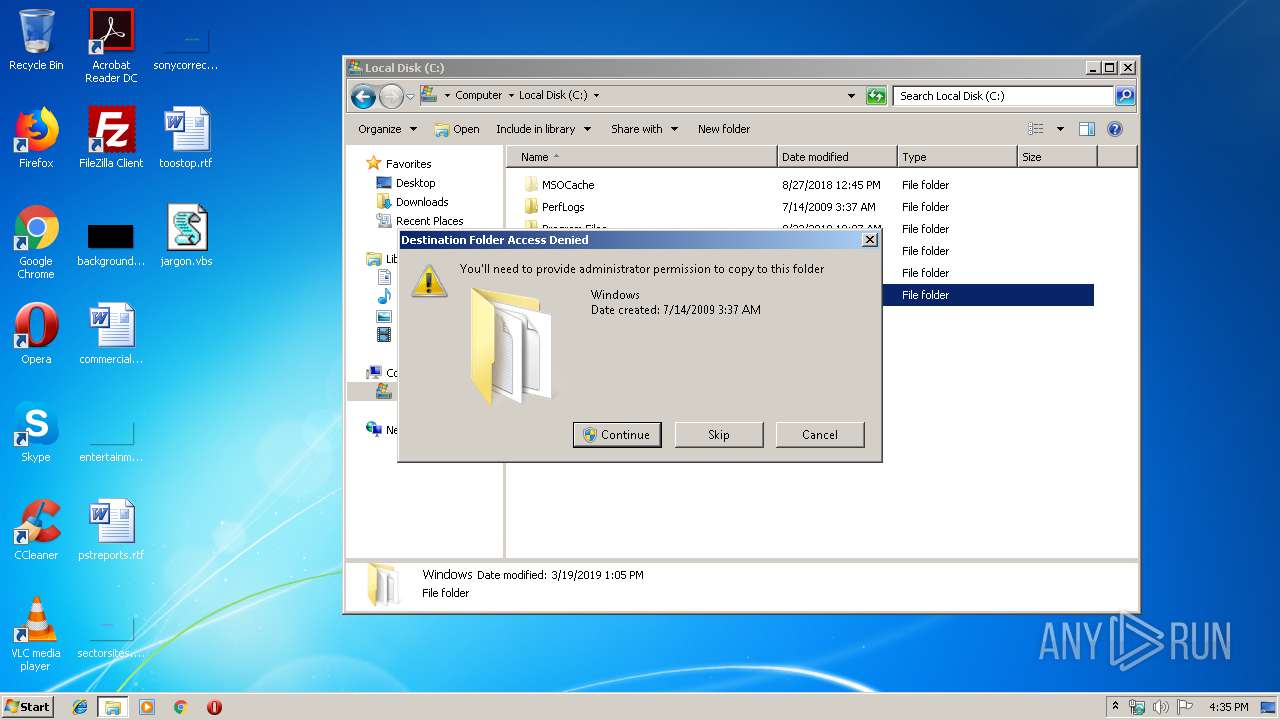
Creates files in the Windows directory
- DllHost.exe (PID: 2764)
Executed via COM
- DllHost.exe (PID: 2764)
INFO
Manual execution by user
- WScript.exe (PID: 2508)
- explorer.exe (PID: 2992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Windows\System32\wscript.exe" "C:\Windows\jargon.vbs" | C:\Windows\System32\wscript.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2156 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\jargon.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2508 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\jargon.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2764 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2992 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
164
Read events
156
Write events
6
Delete events
2
Modification events
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | autoMe |
Value: wscript.exe "C:\Windows\jargon.vbs" | |||
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | delete value | Name: | Hidden |
Value: 1 | |||
| (PID) Process: | (2156) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | delete value | Name: | HideFileExt |
Value: 0 | |||
| (PID) Process: | (2508) WScript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | autoMe |
Value: wscript.exe "C:\Windows\jargon.vbs" | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | DllHost.exe | C:\Windows\jargon.vbs | text | |
MD5:524D38B7488A490C0A93A2D248CA05C3 | SHA256:15A7F28FD3E63122D328F8057CBD57FF82125A24F66C7D6A32DC267558D0A0E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report