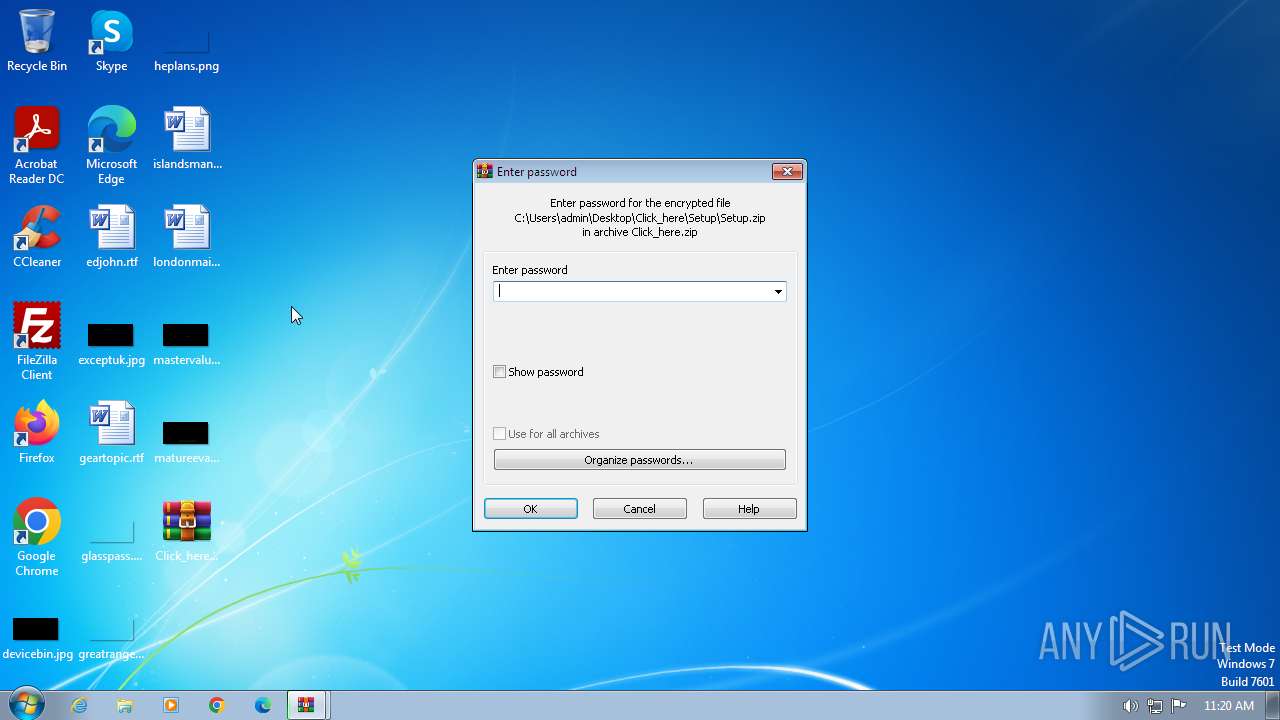
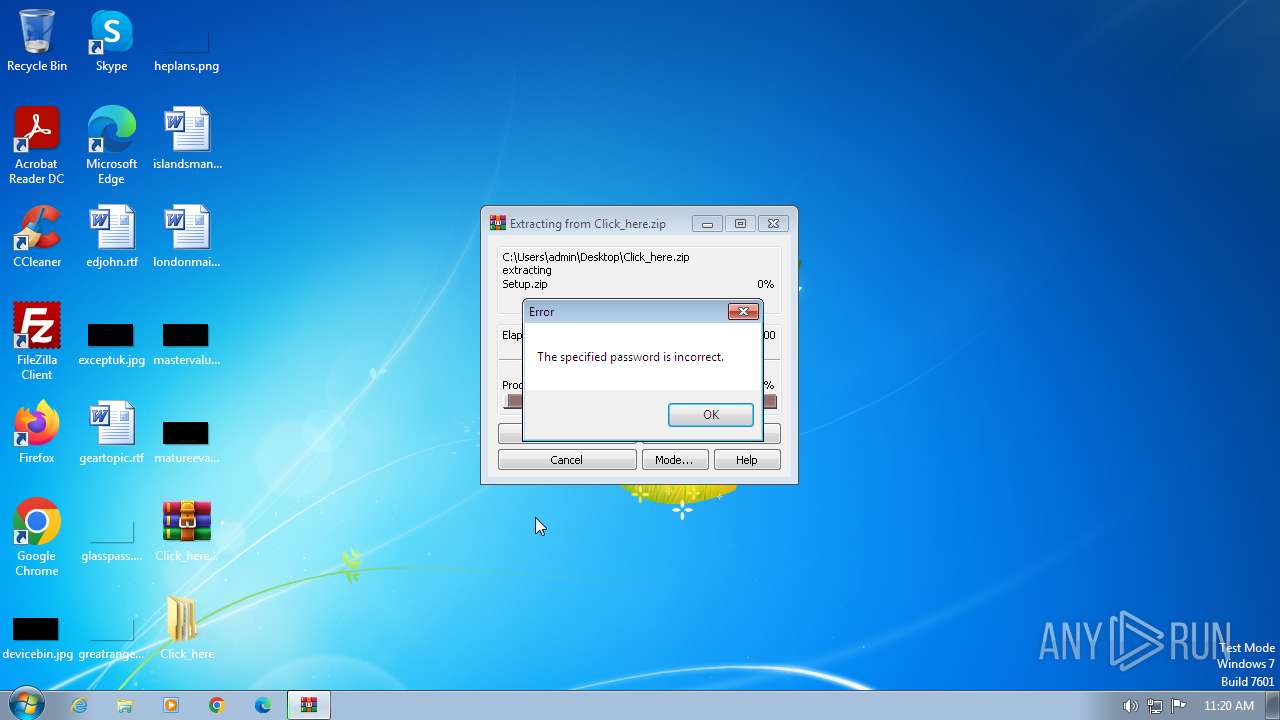
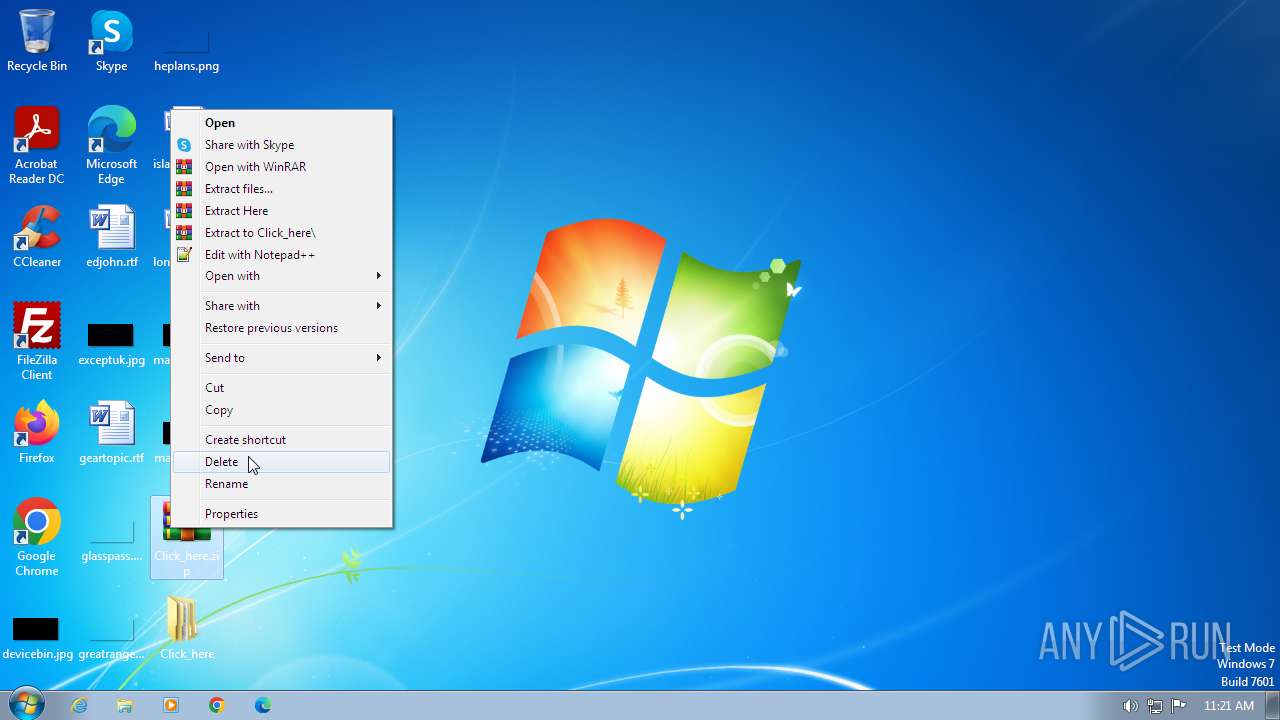
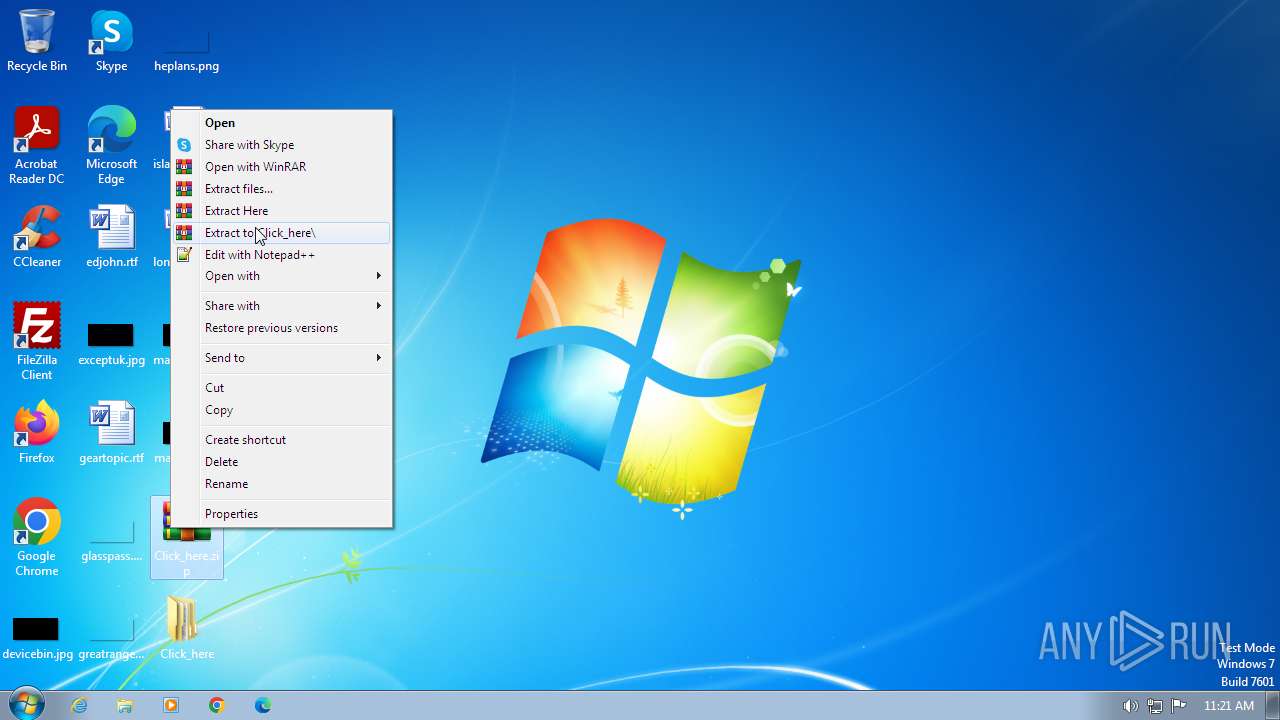
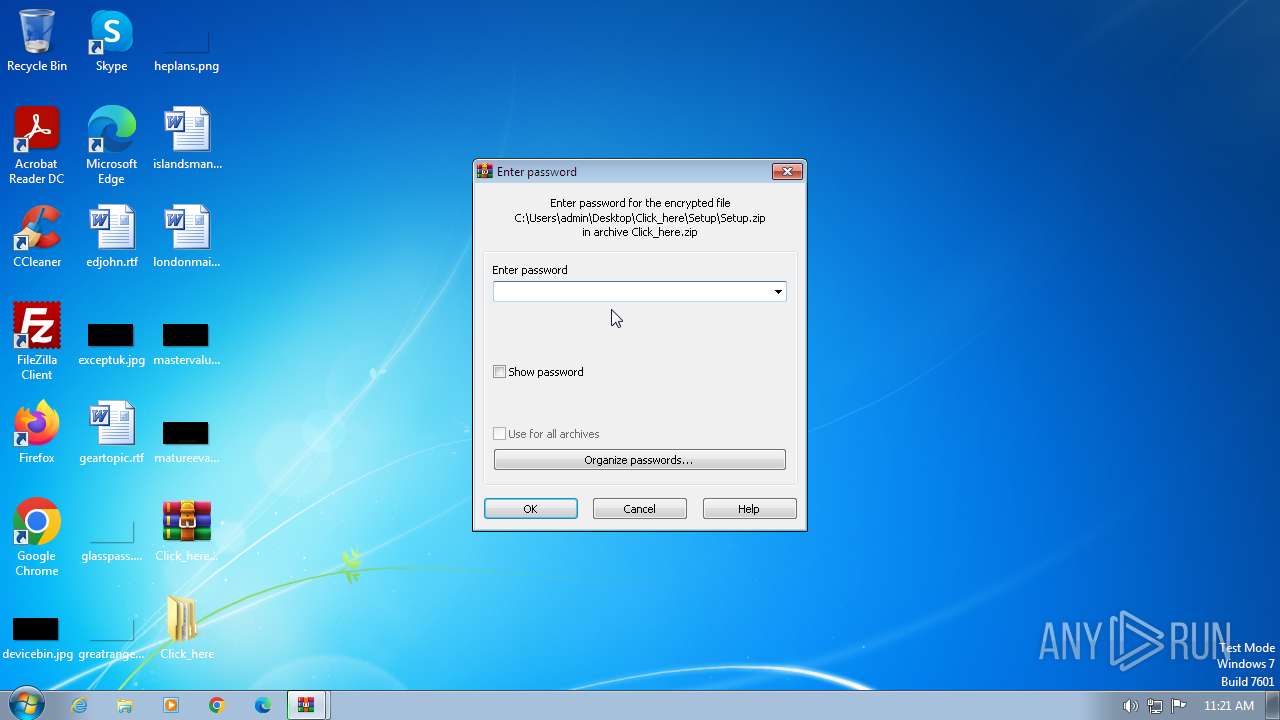
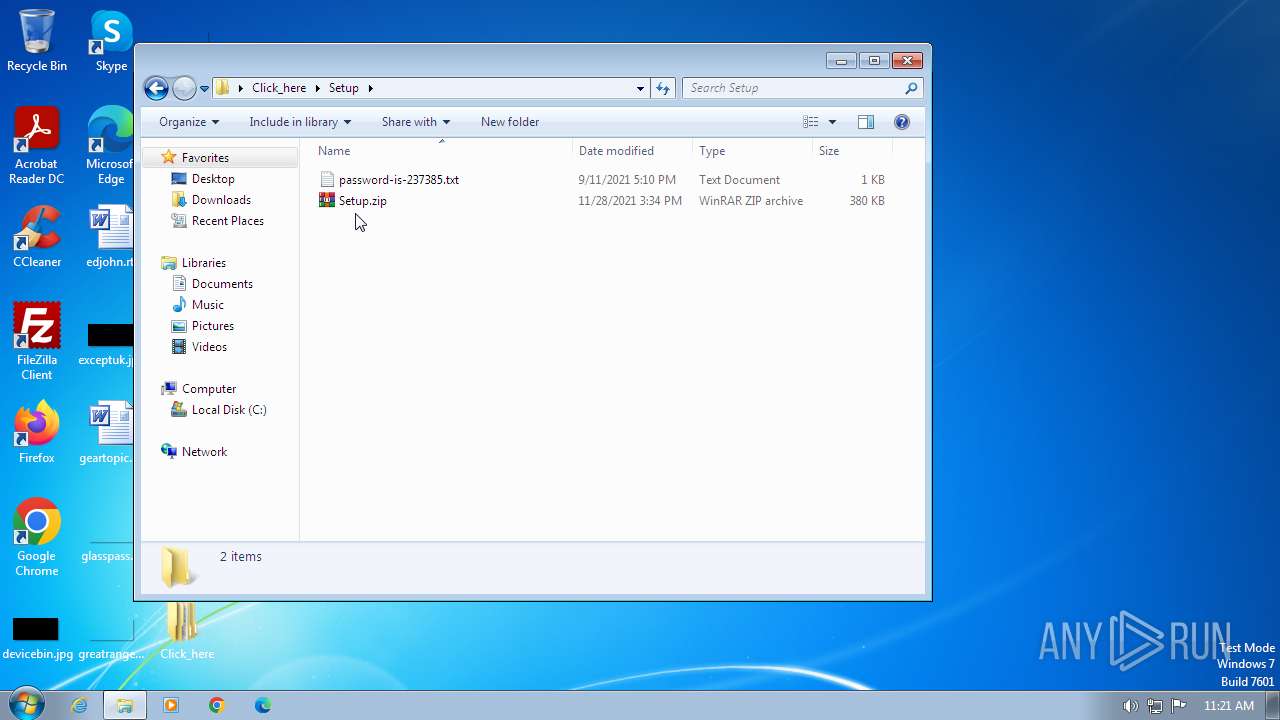
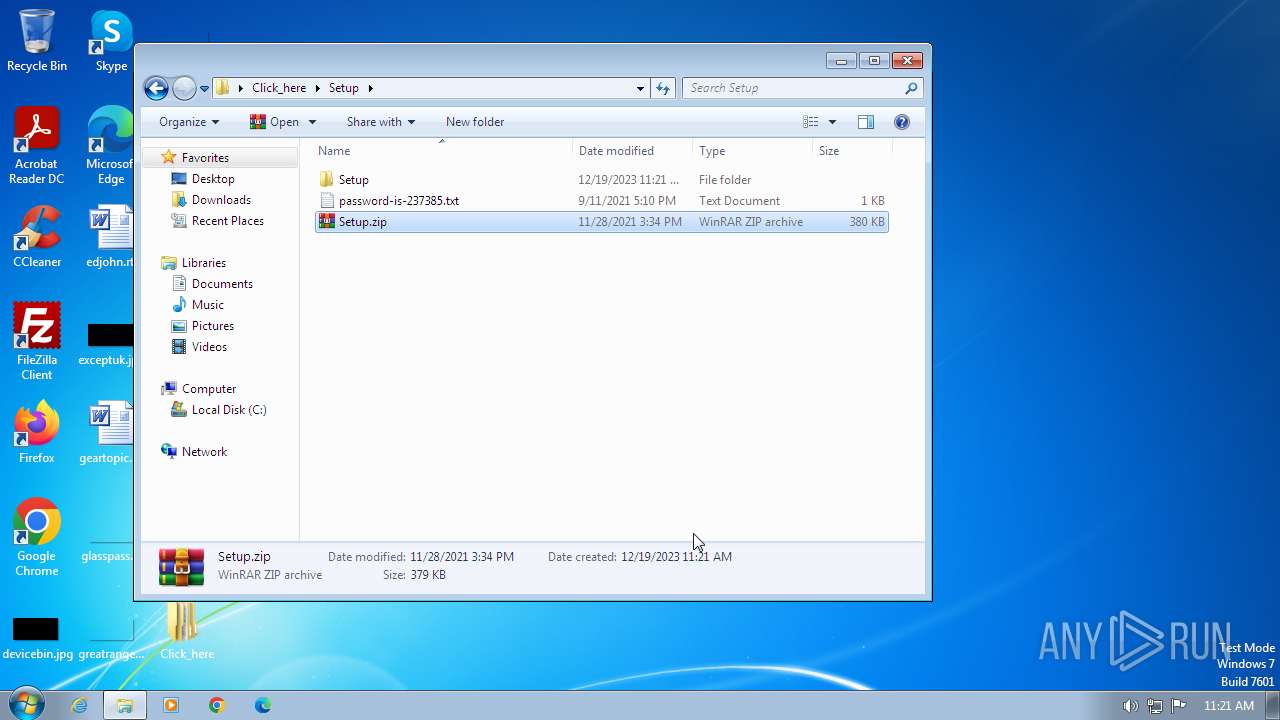
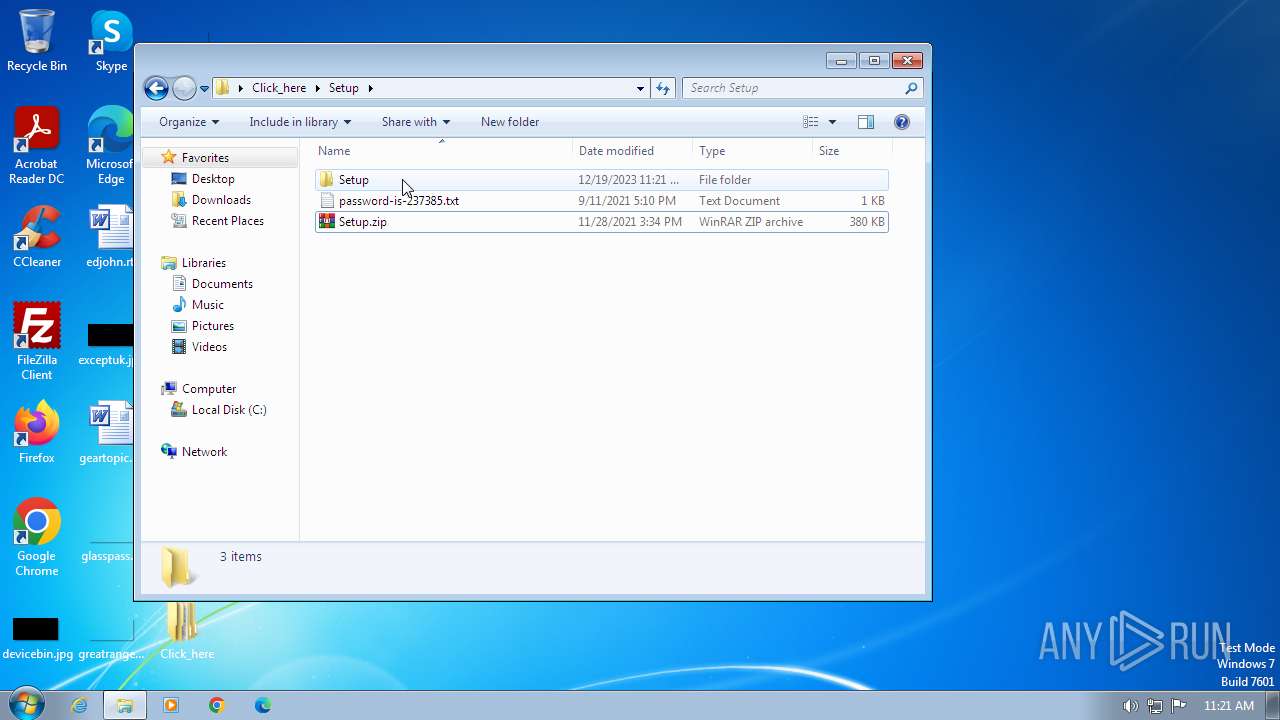
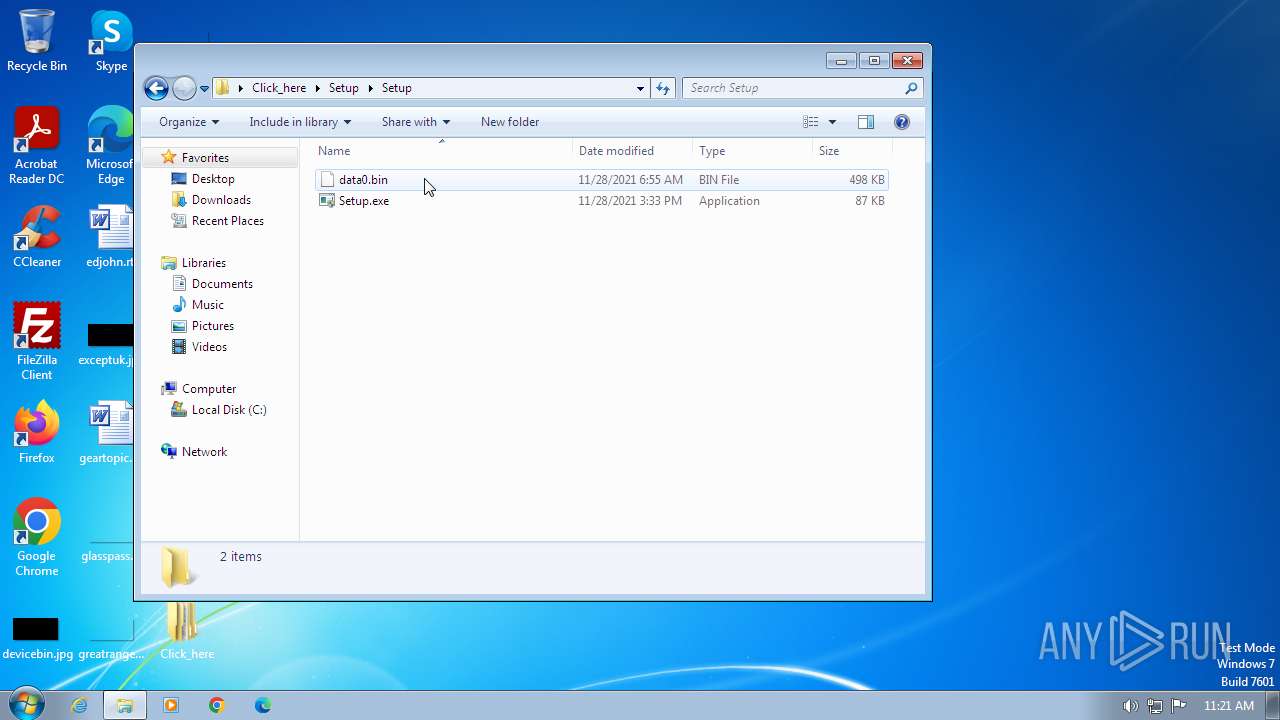
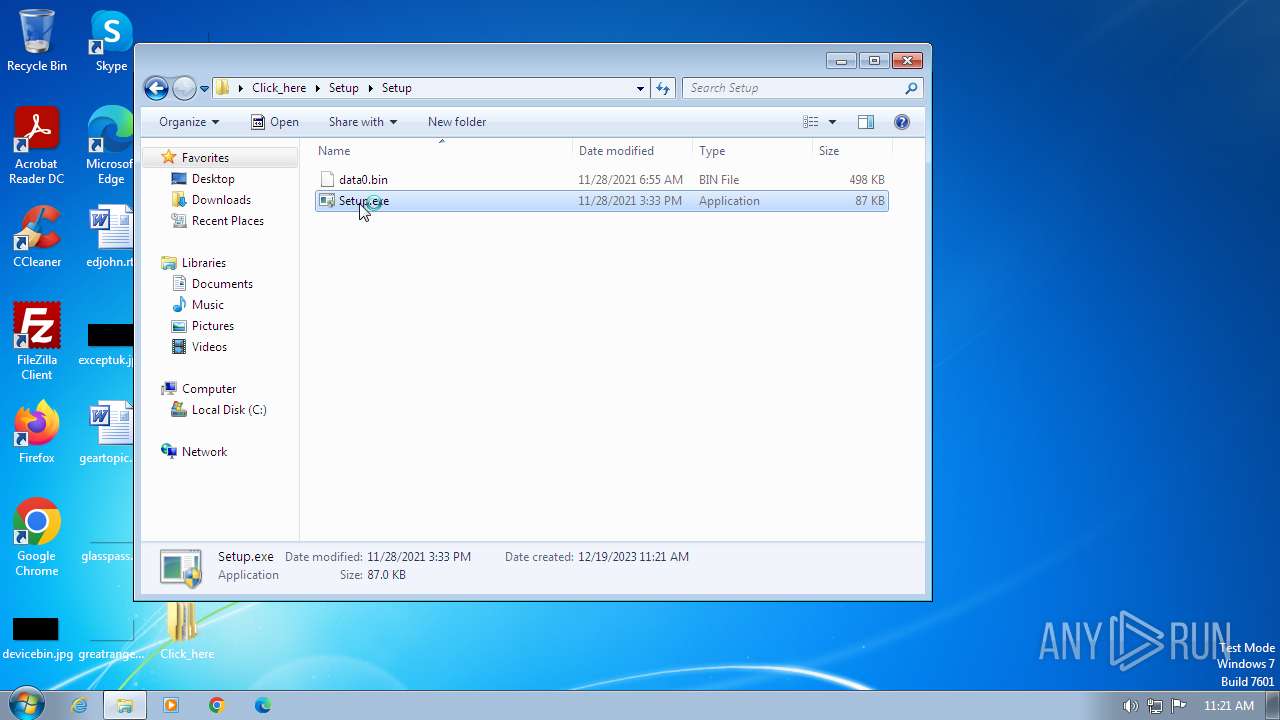
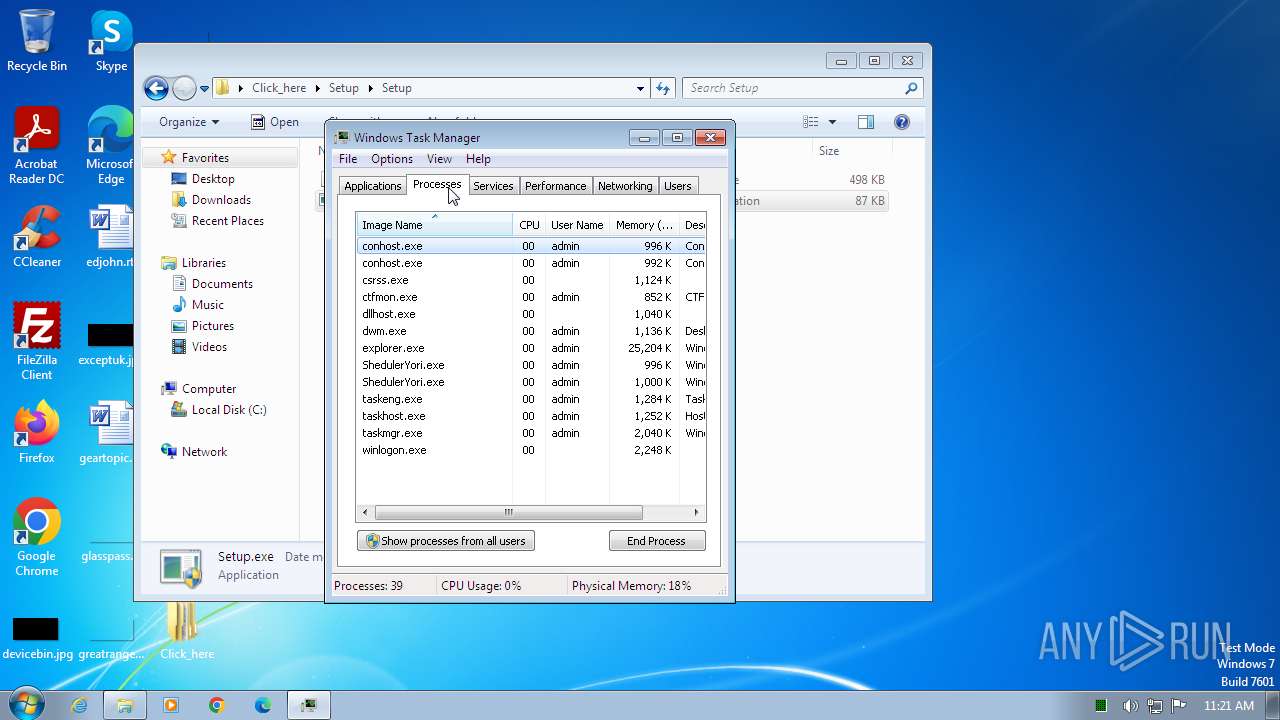
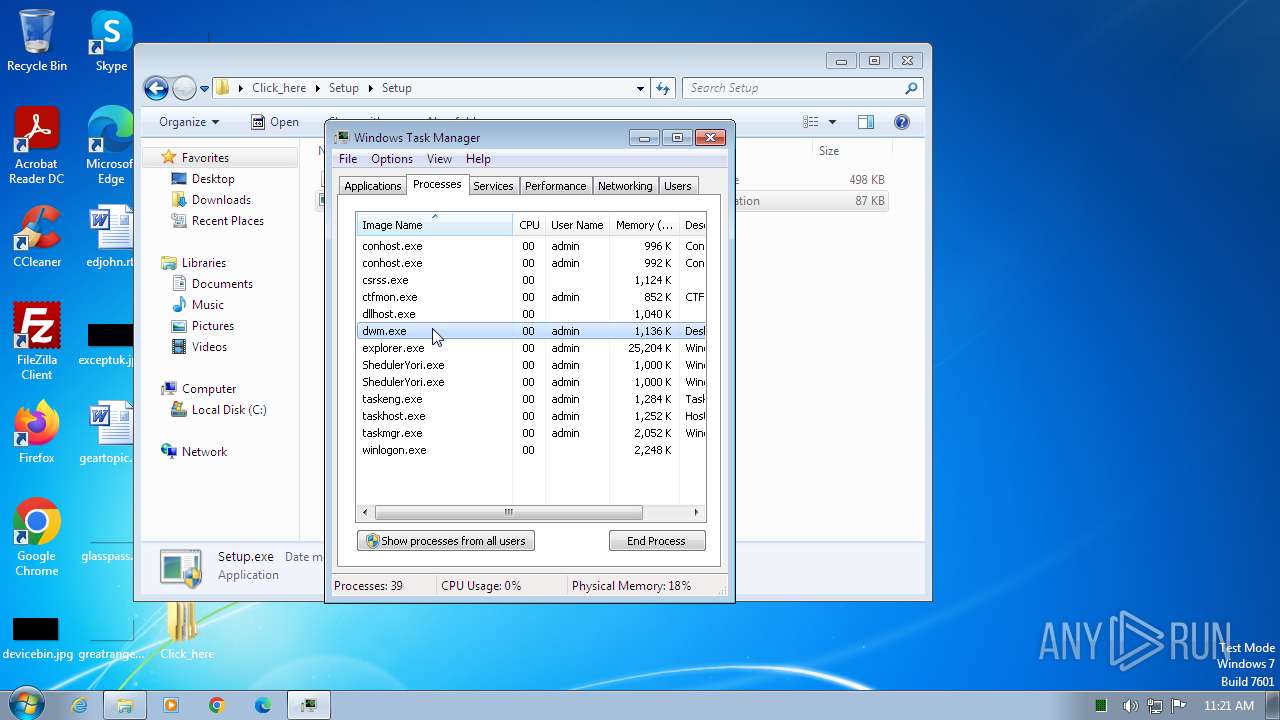
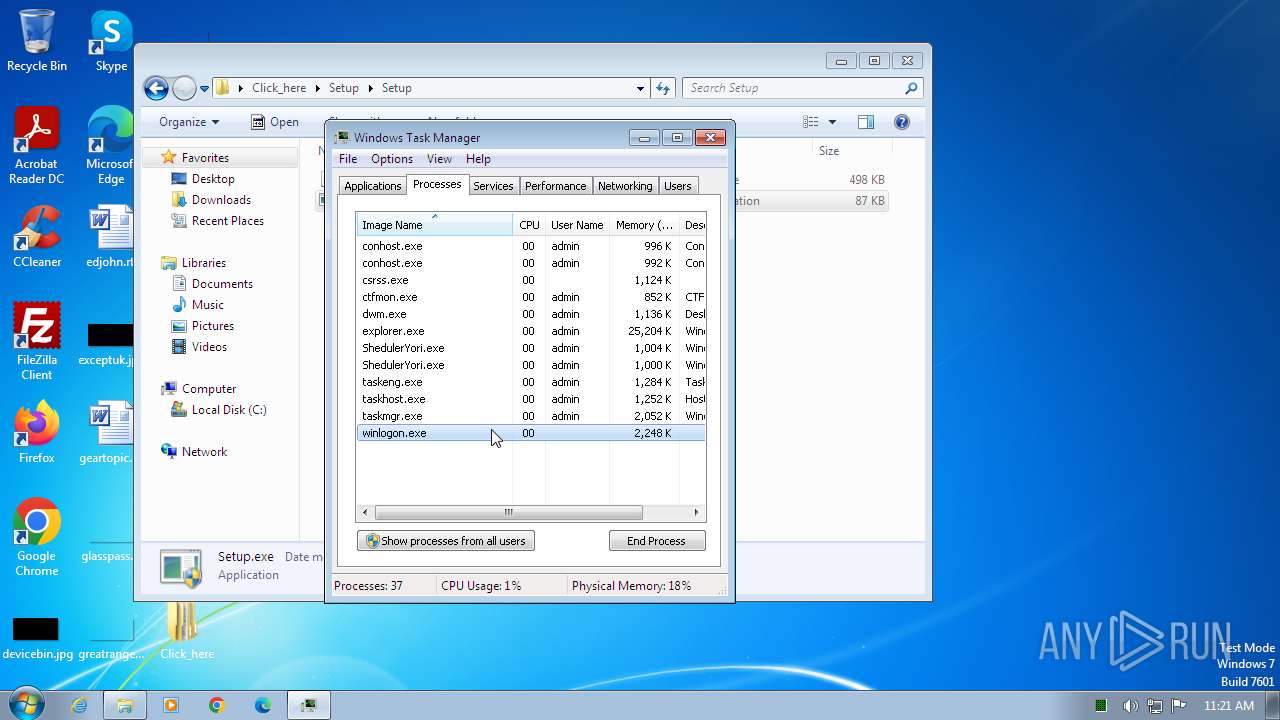
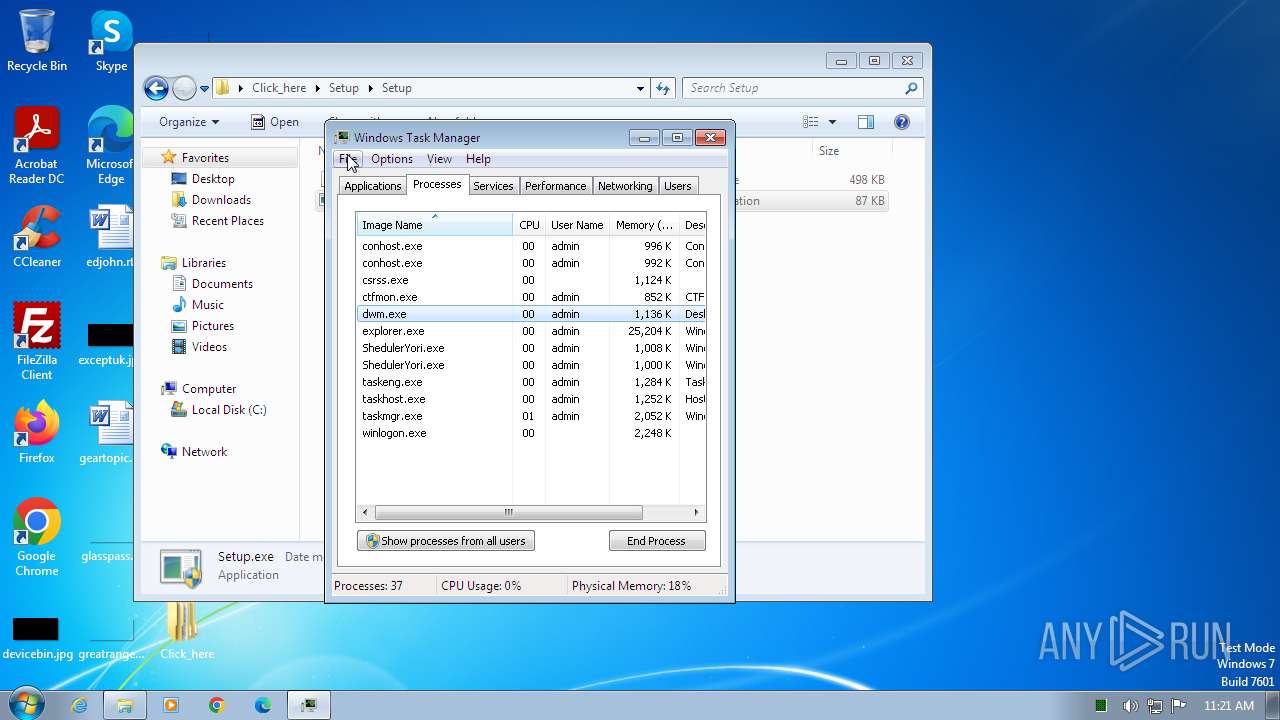
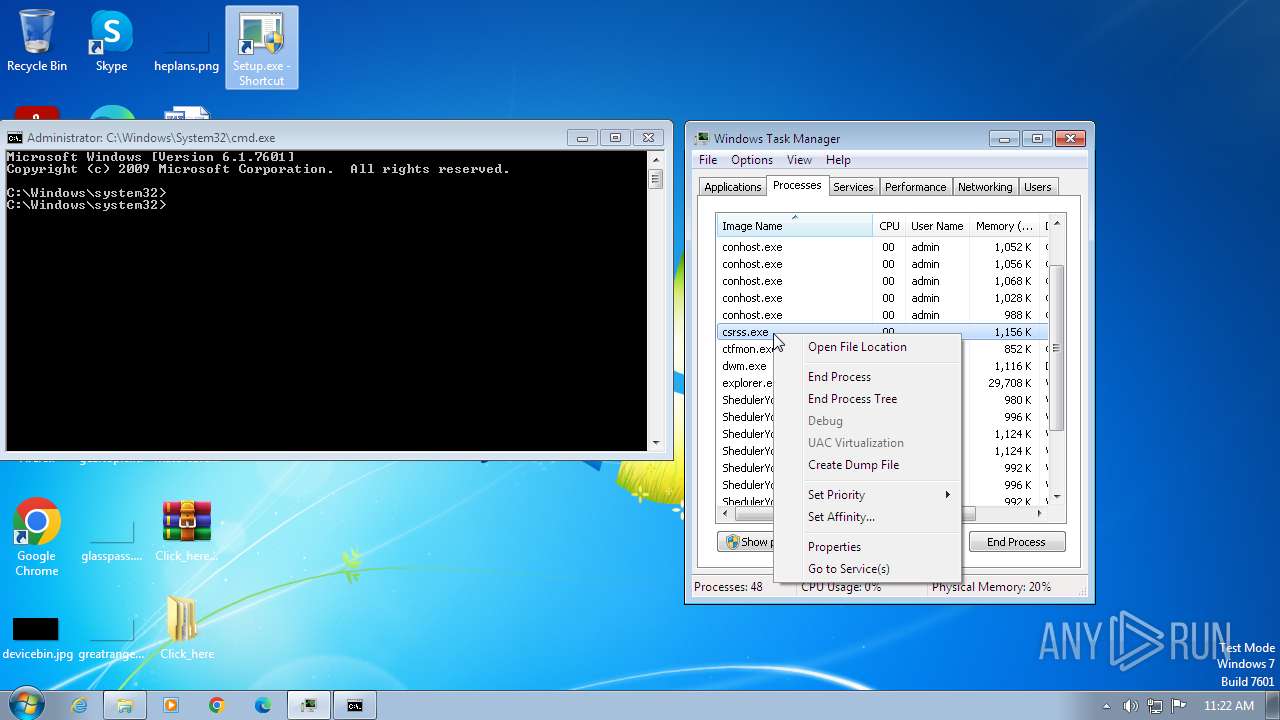
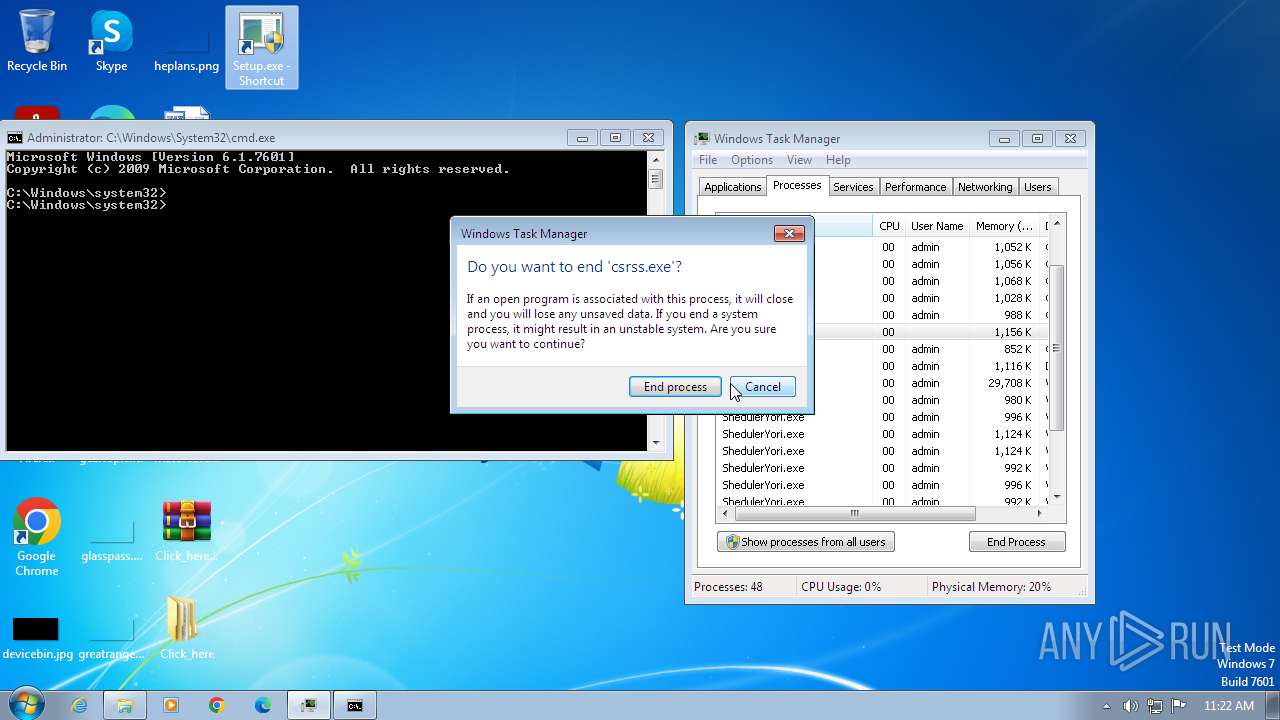
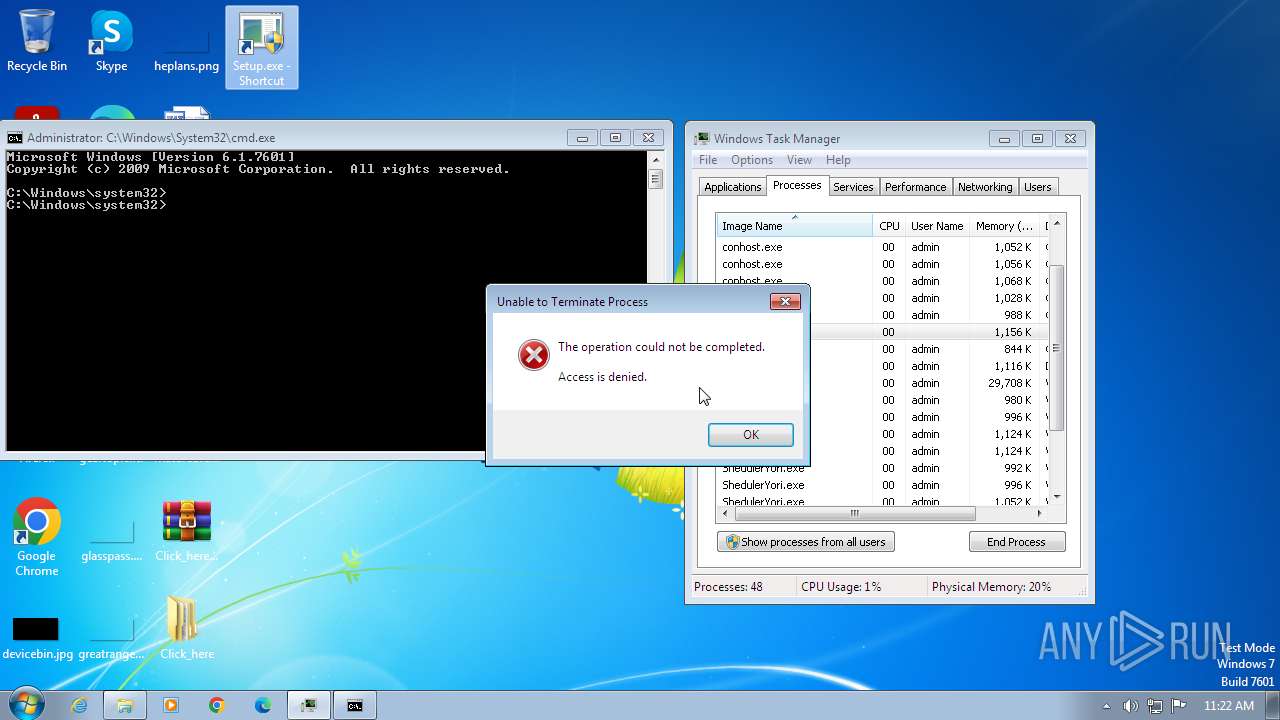
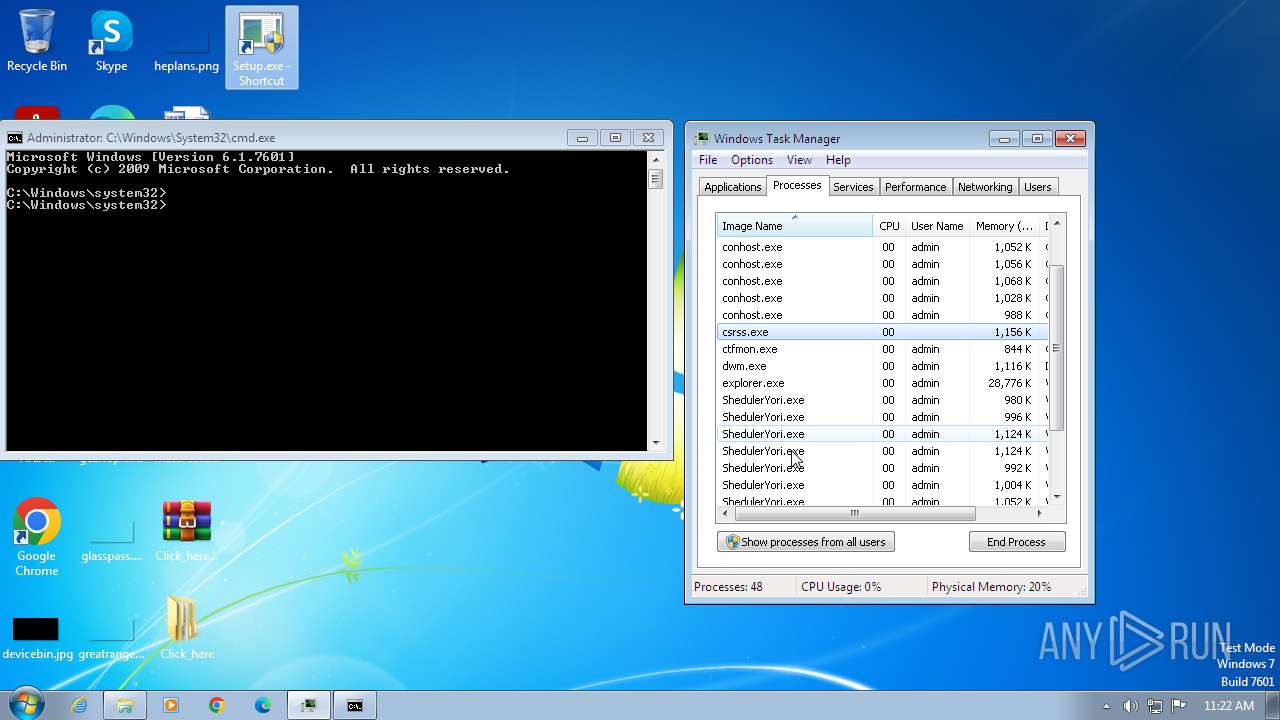
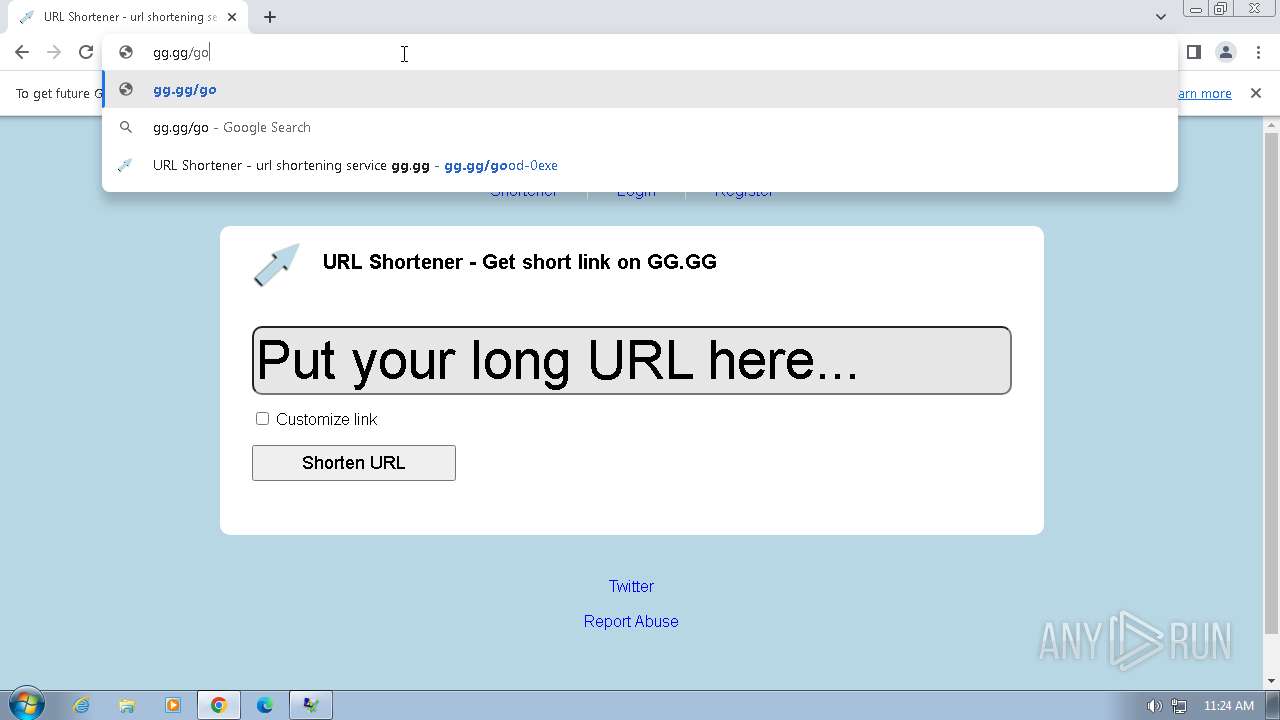
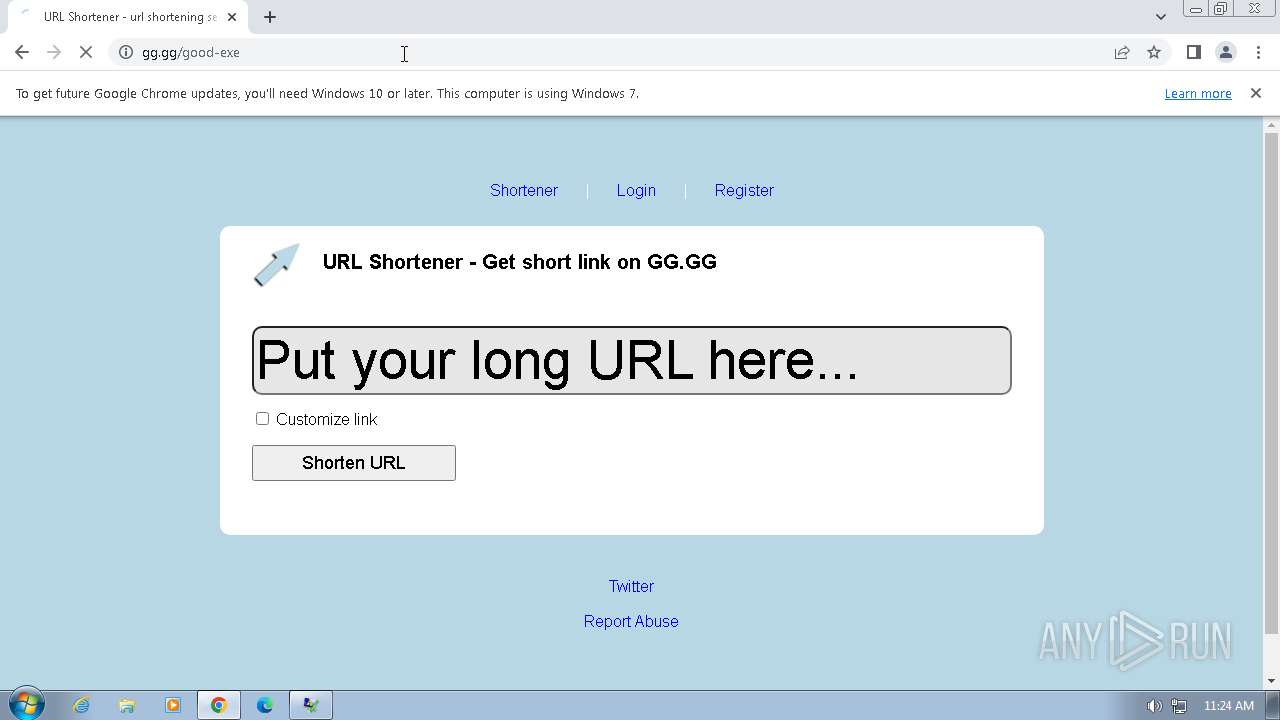
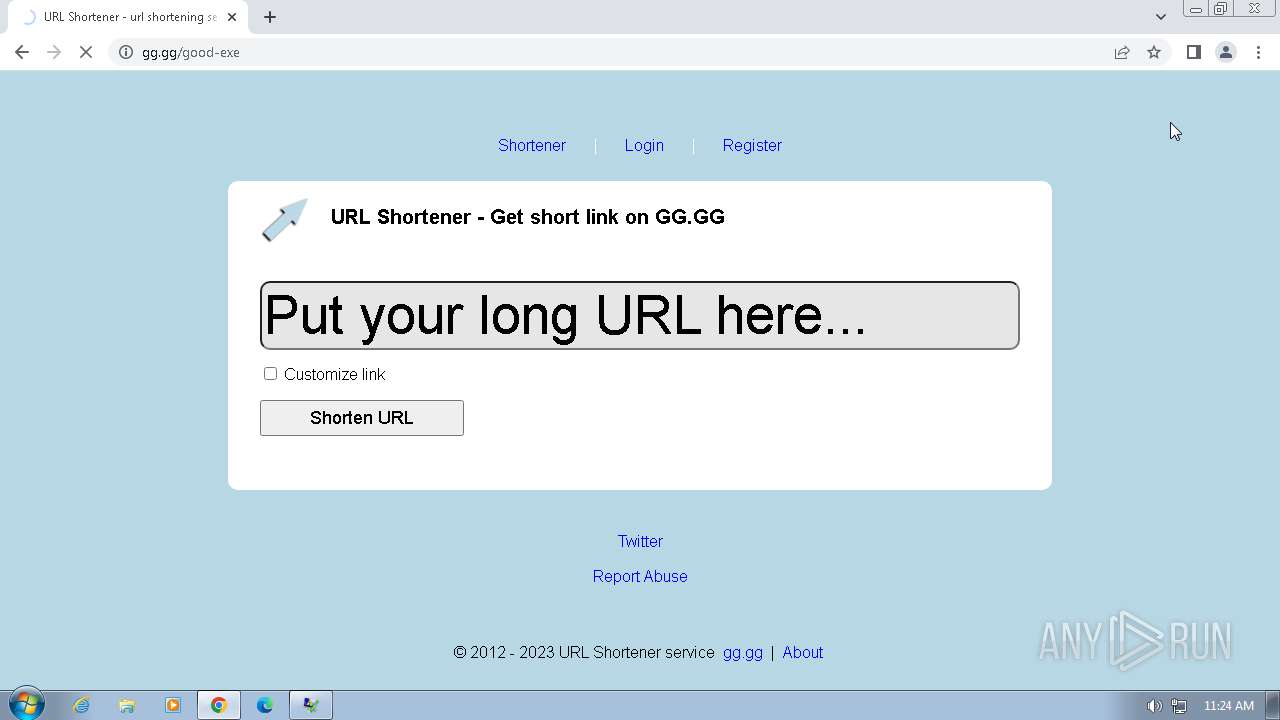
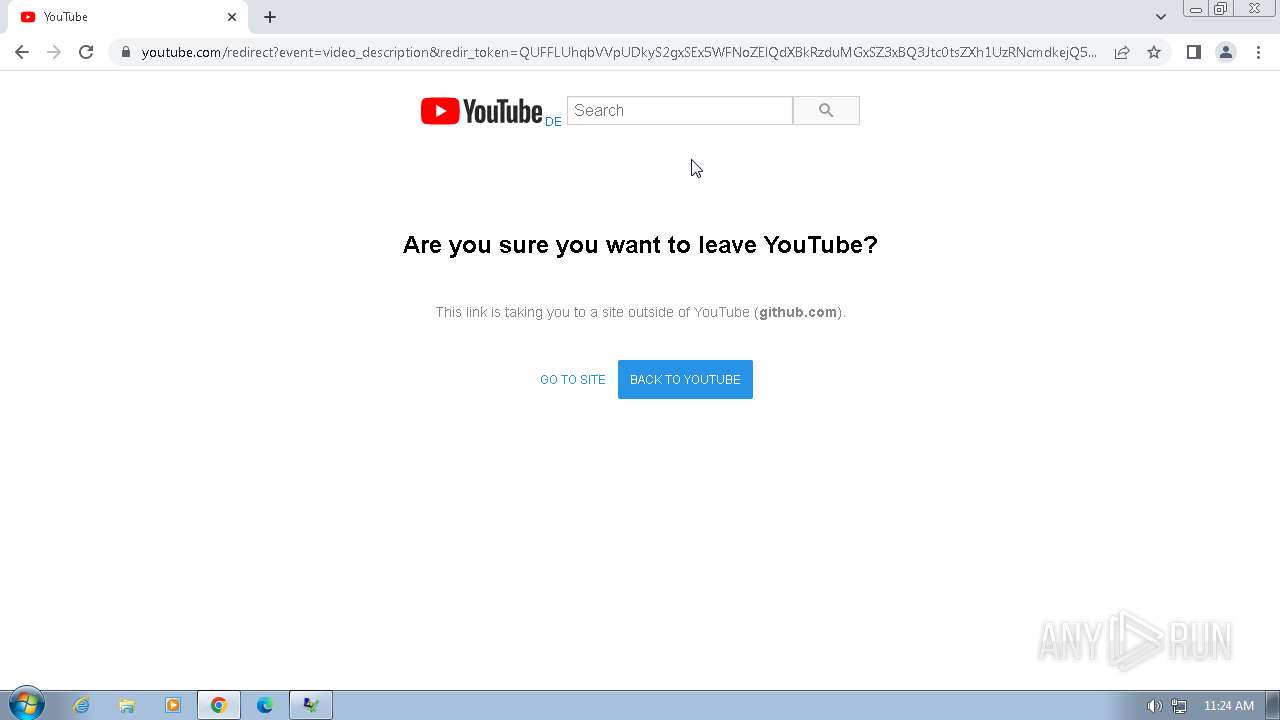
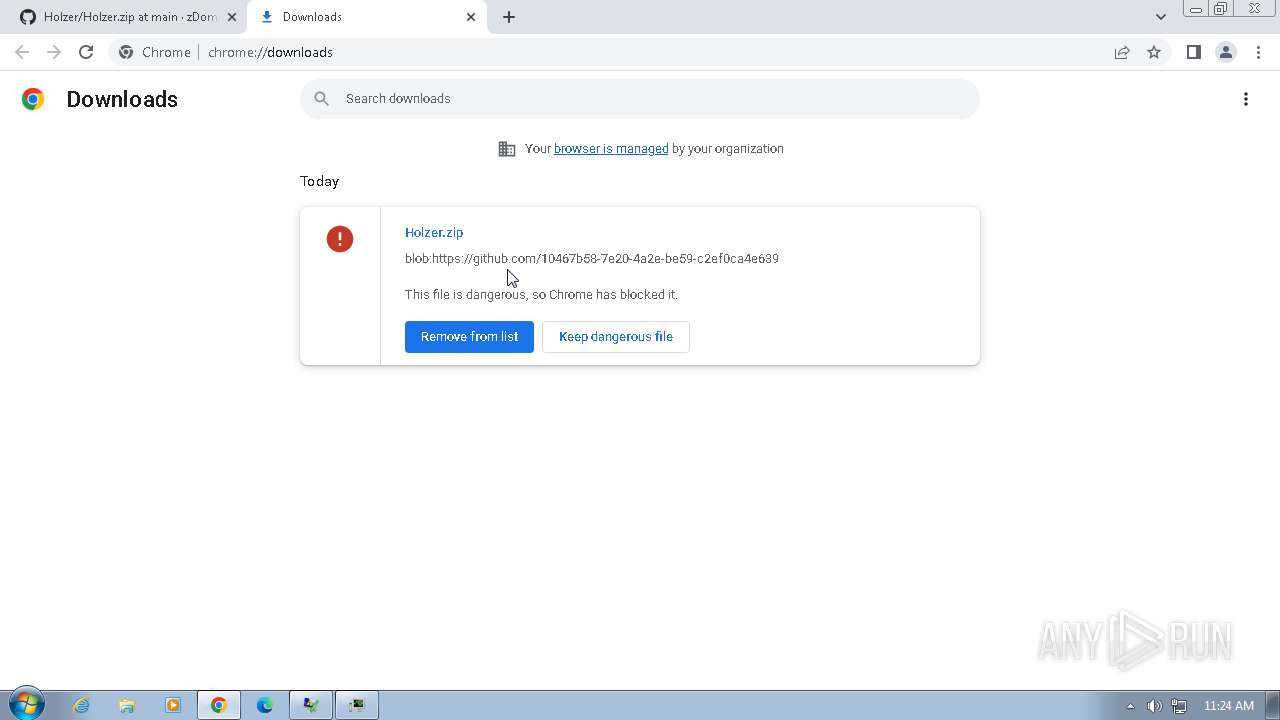
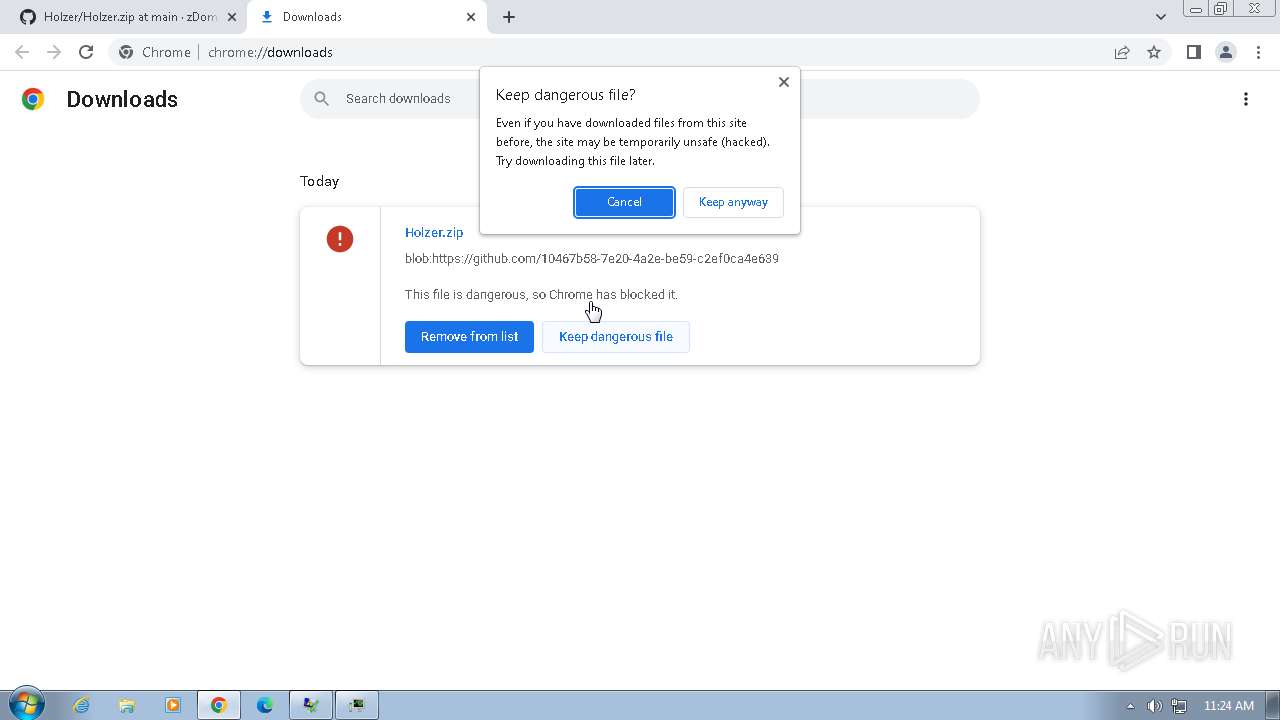
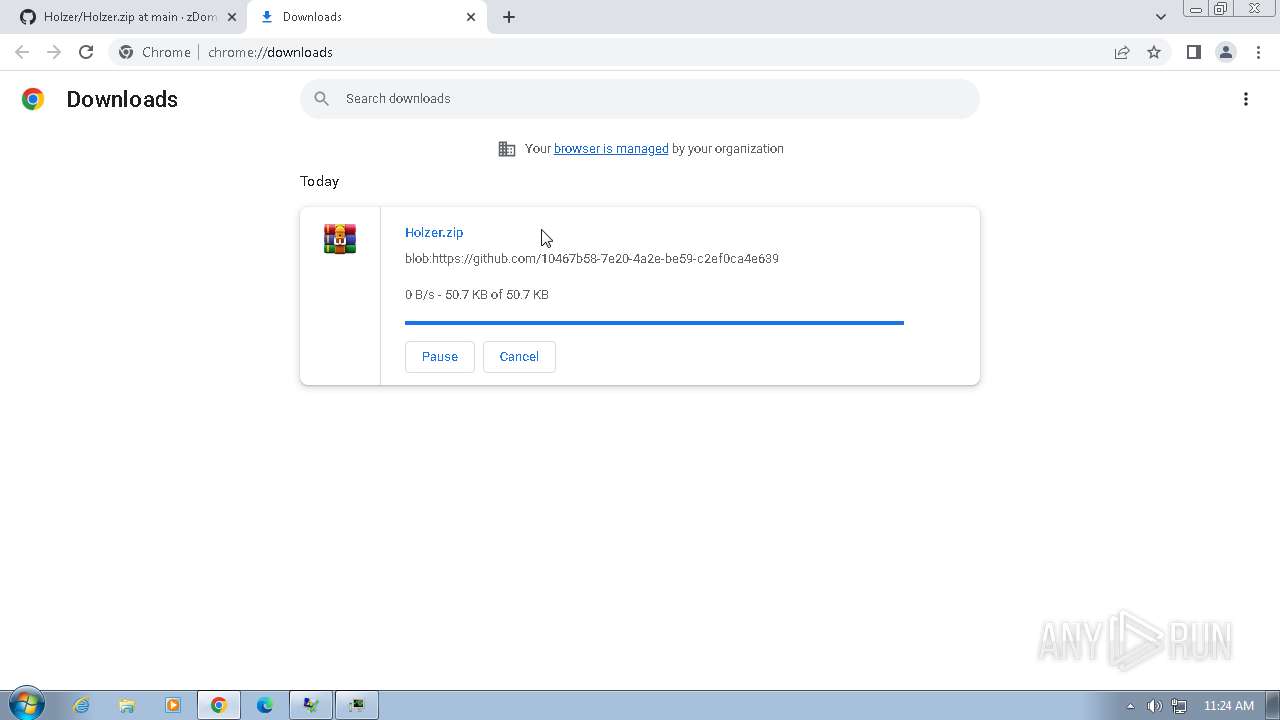
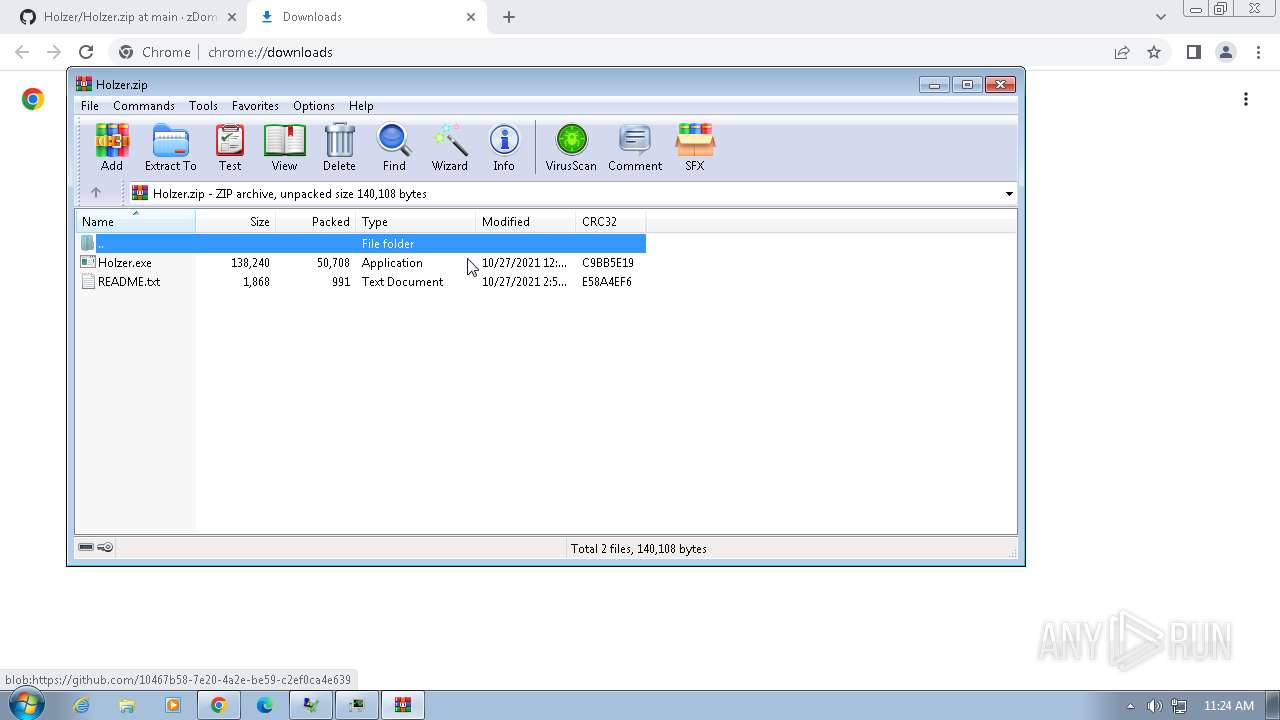
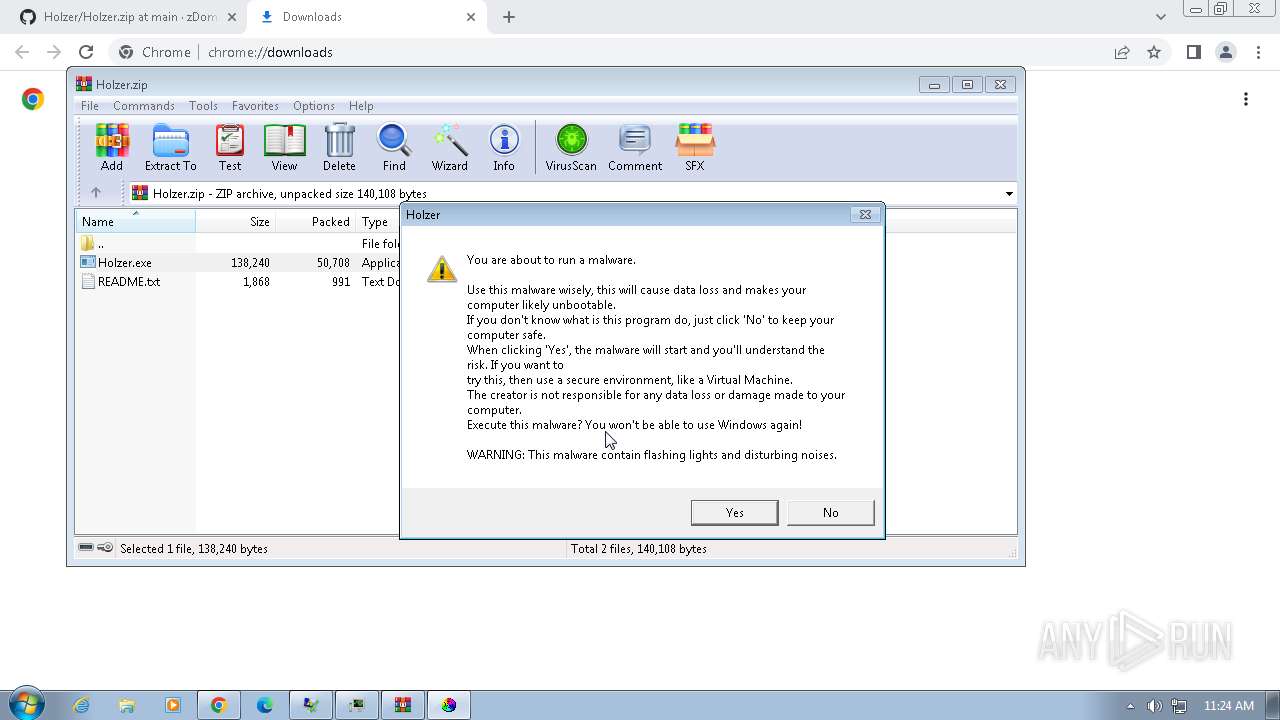
| File name: | Click_here.zip |
| Full analysis: | https://app.any.run/tasks/3315c535-1c8e-4cc3-af54-e74935625f13 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2023, 11:20:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | B4E9DDFA5DA9F2C7B0B1A0CEE0F6159C |
| SHA1: | 971FE6EC764342D31E0F2B10DD09C8763560426D |
| SHA256: | 15A6FC69CAE8D98C9AFA0A60D06B5FEE5940741490D28FB3C33A059008B91106 |
| SSDEEP: | 12288:STqLuovP1PKq58xRqb+IbK5HIFBWdErKXu5gILjWi:OqLumP1PKq5o8aIbKlIFuE4AgILD |
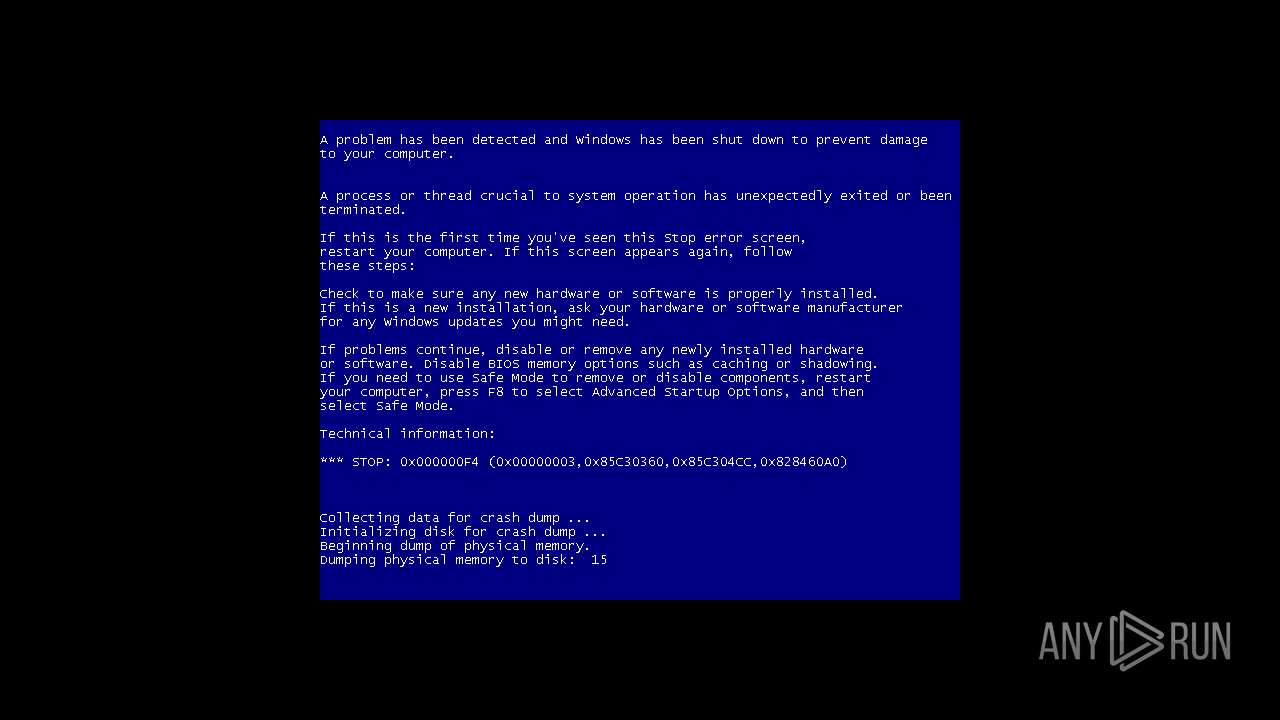
MALICIOUS
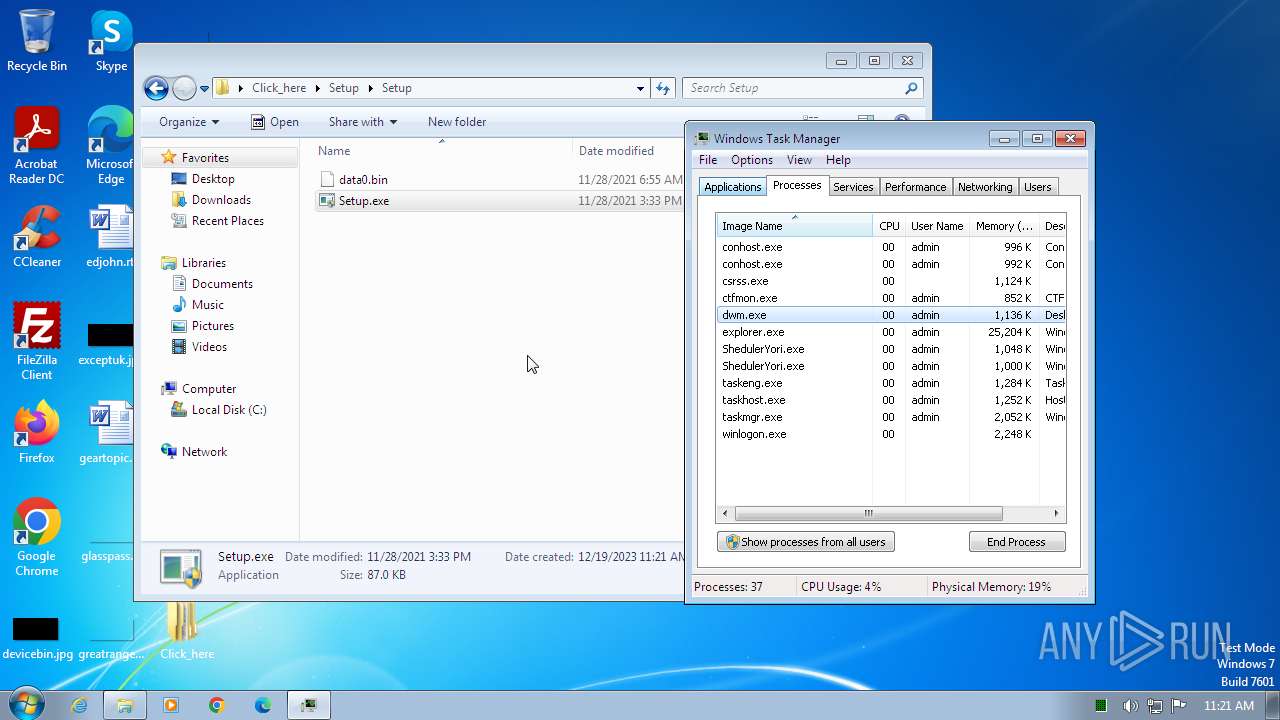
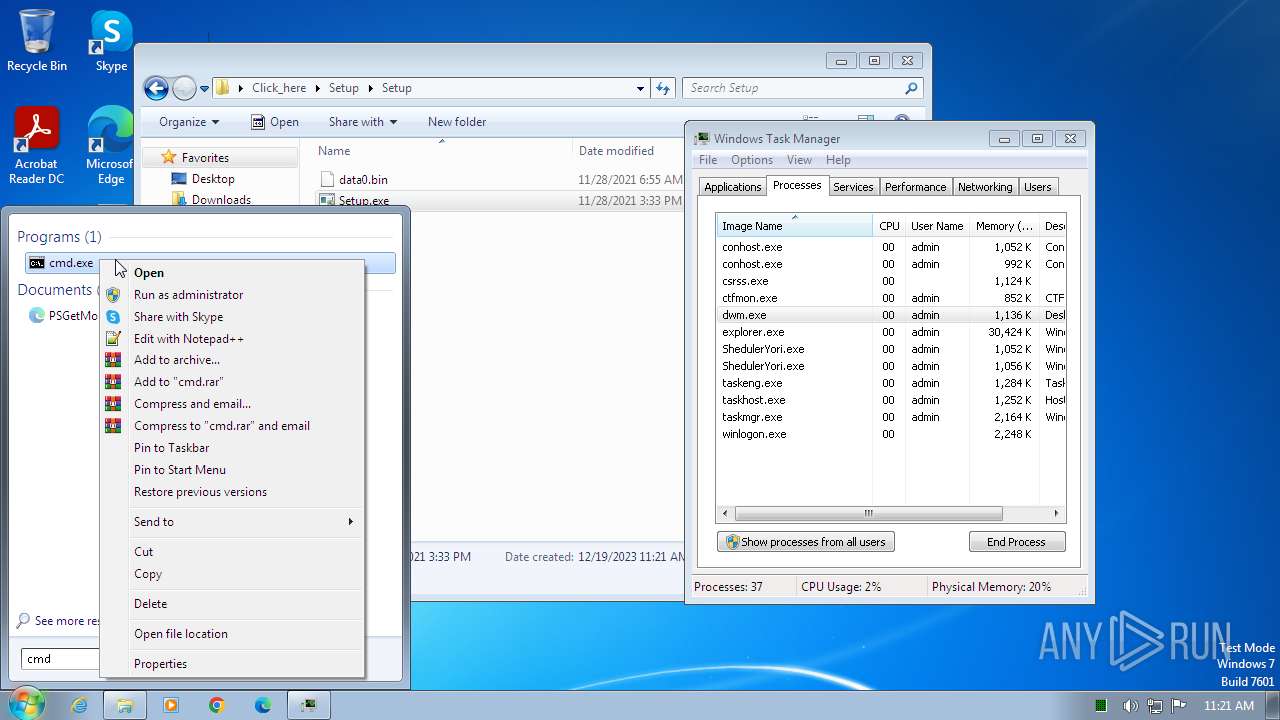
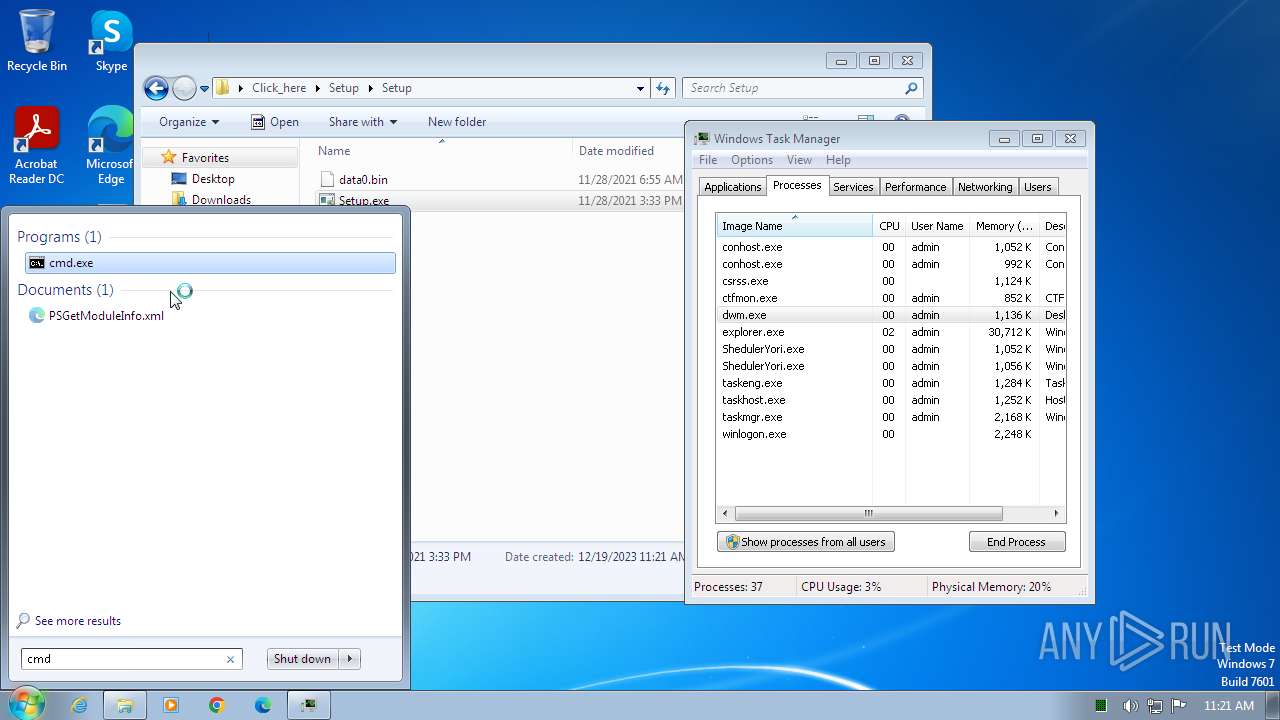
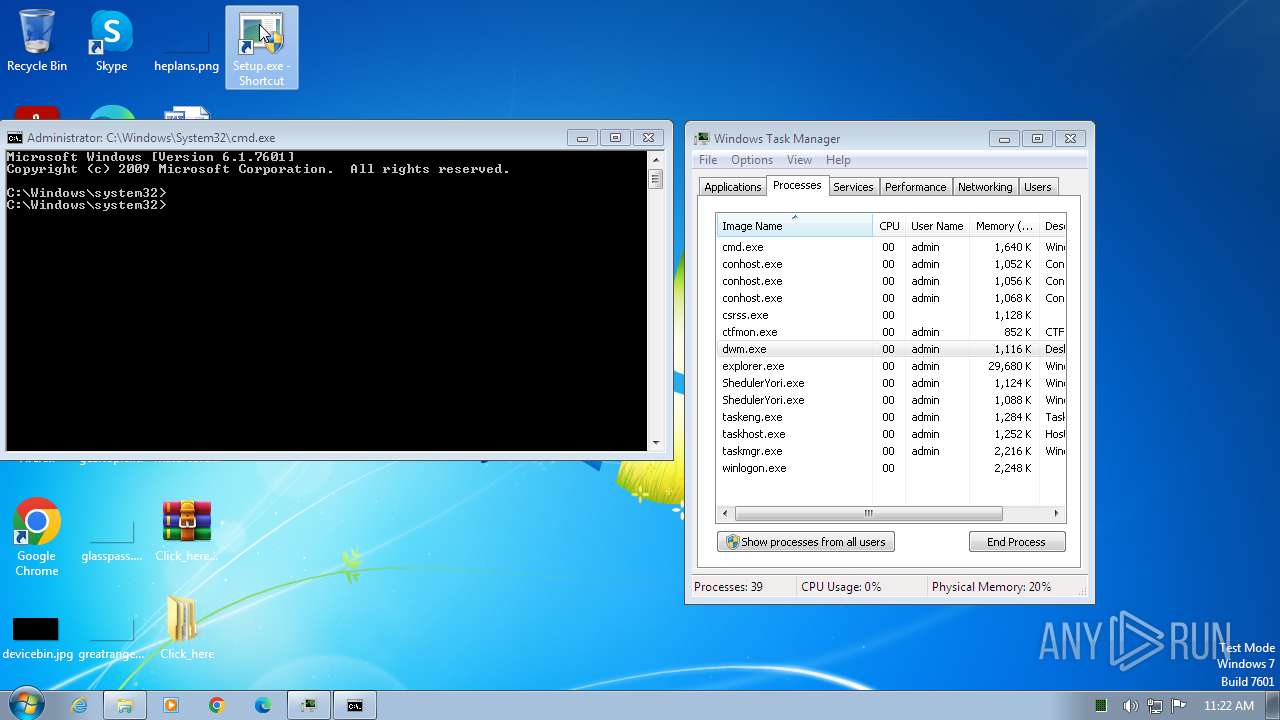
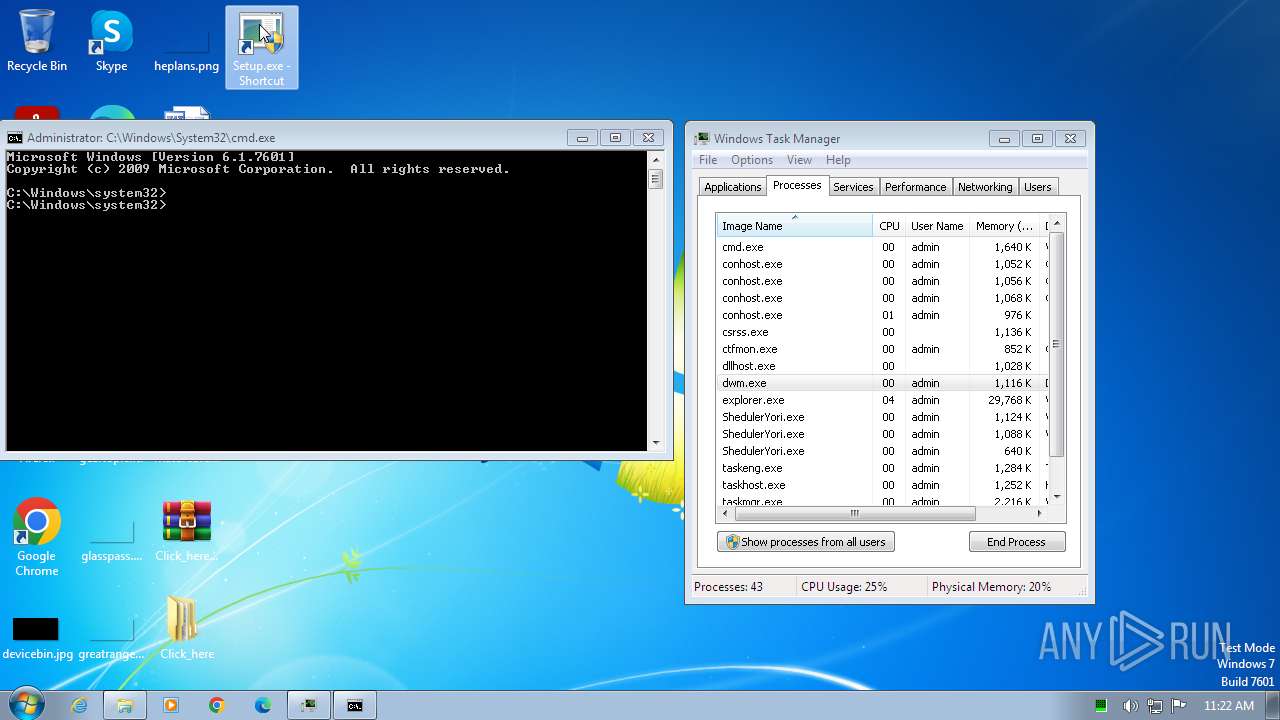
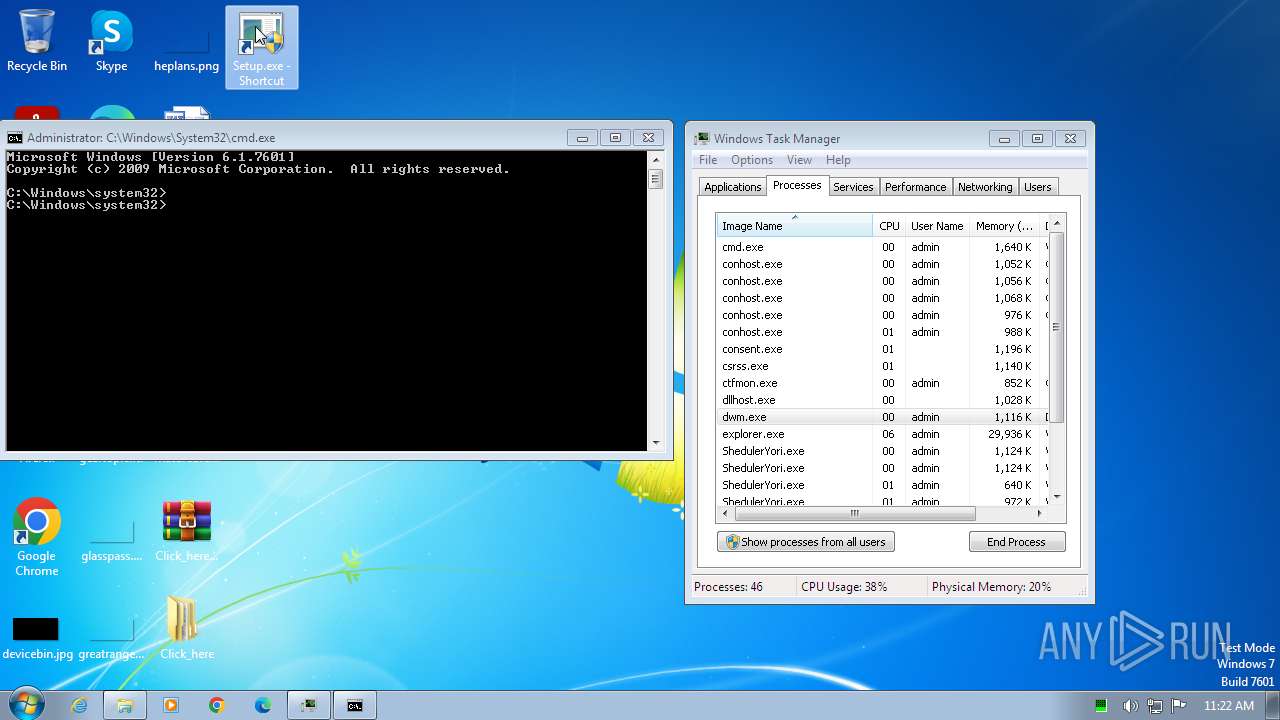
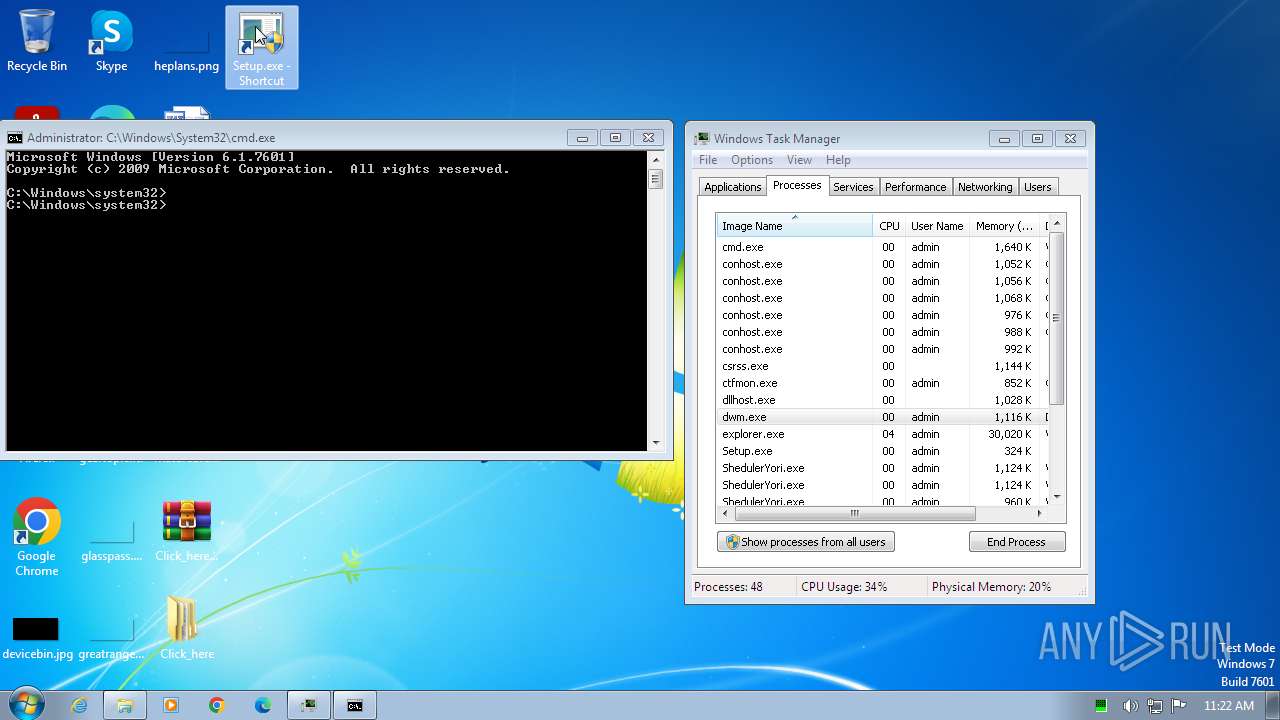
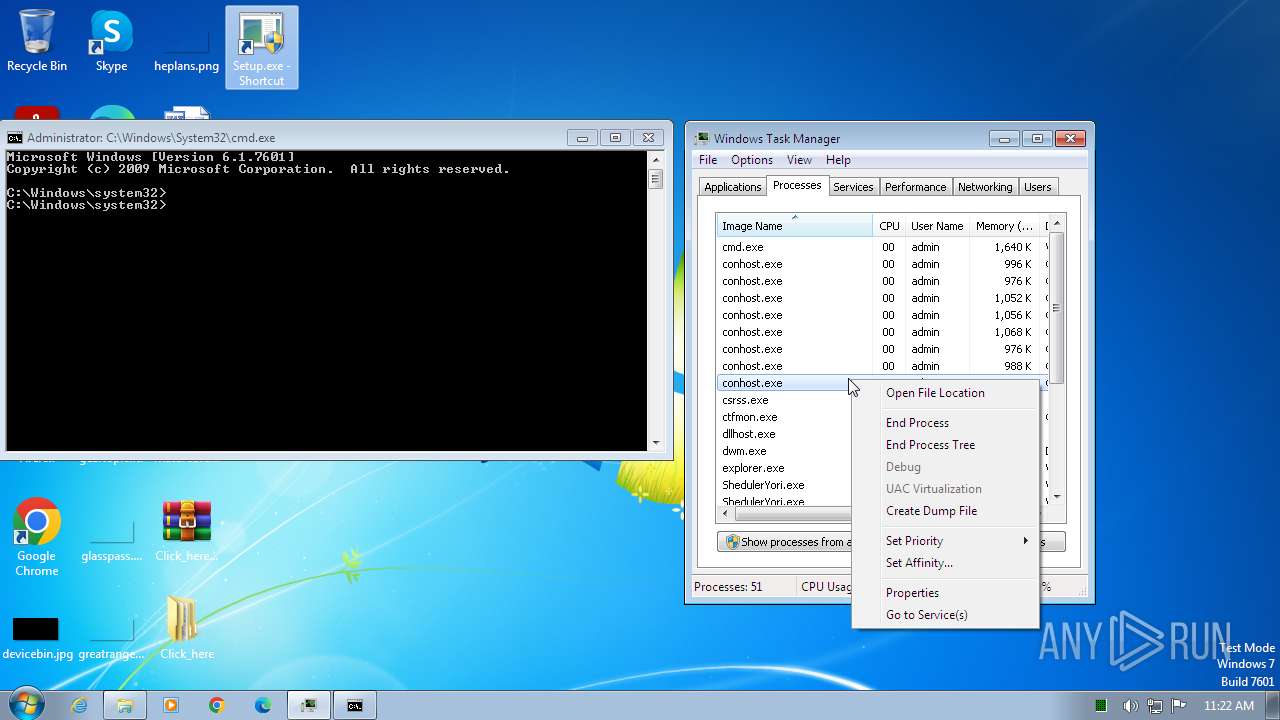
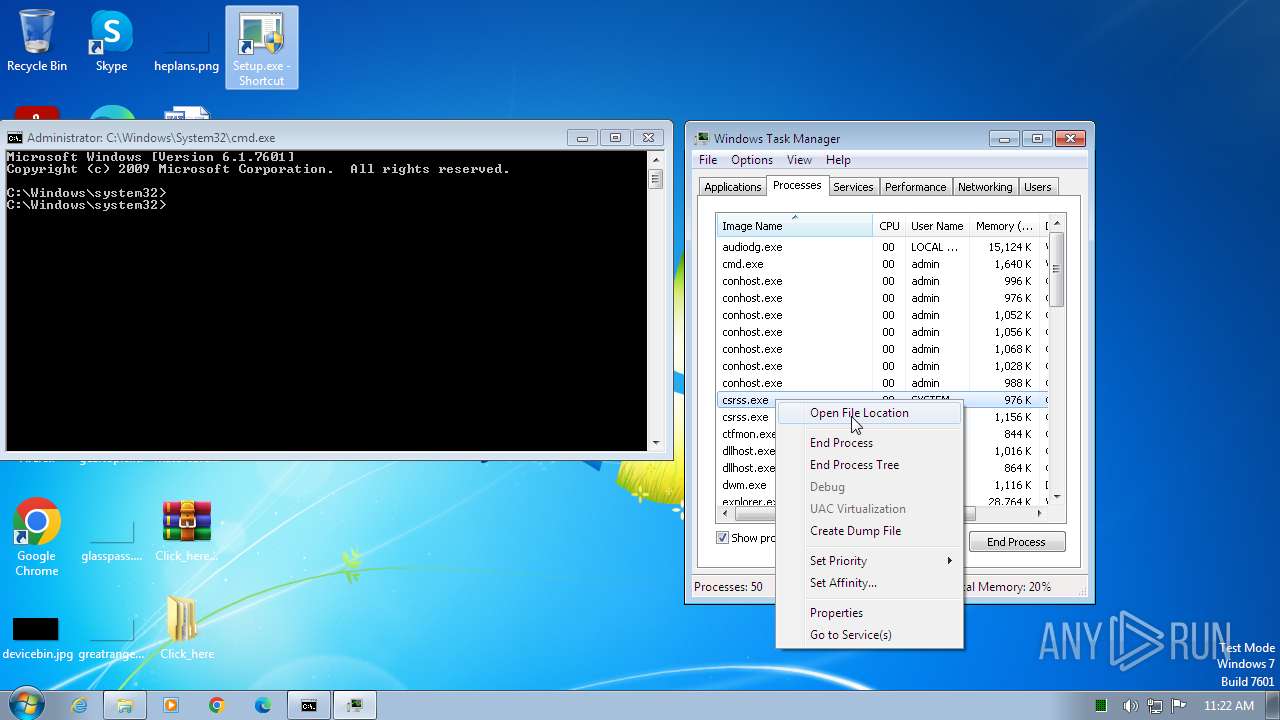
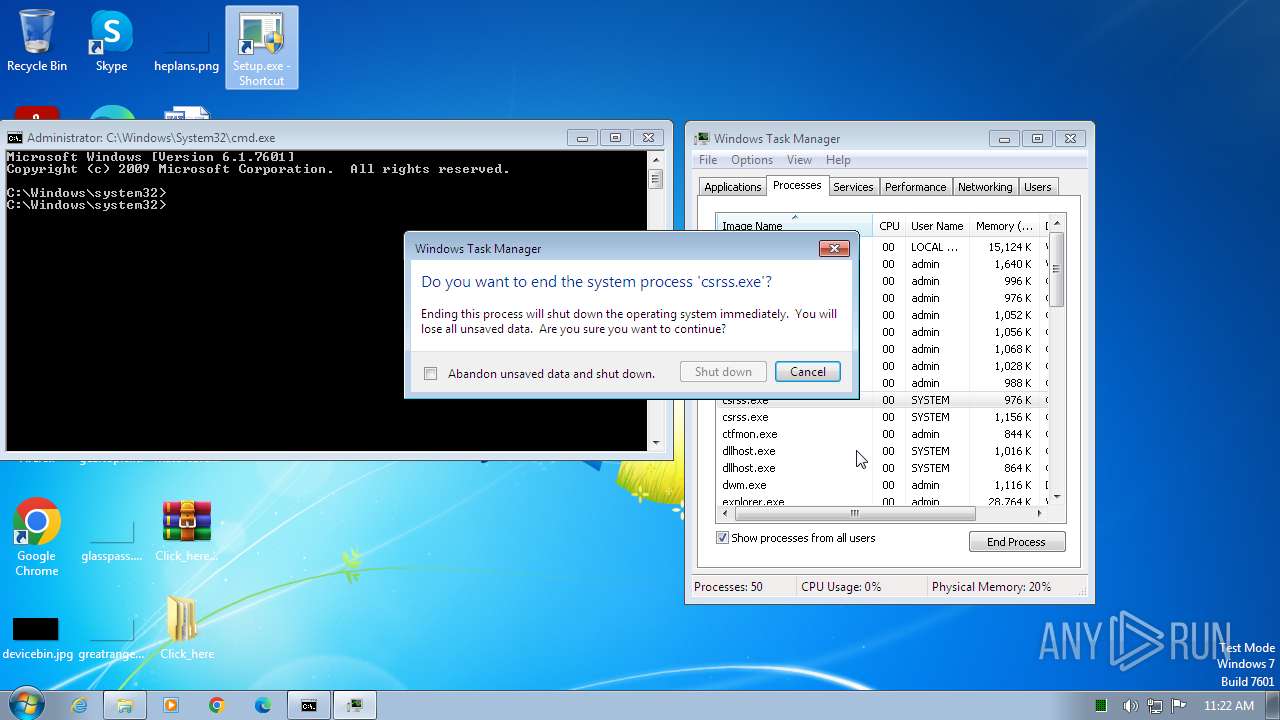
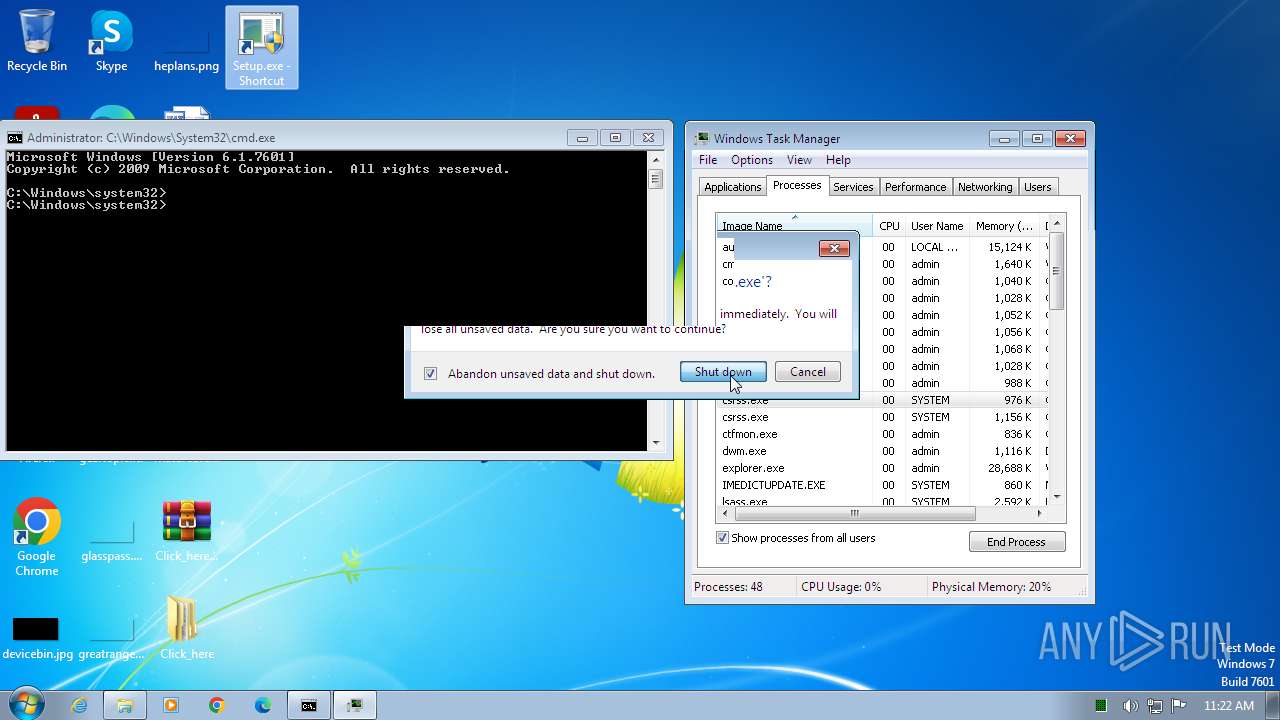
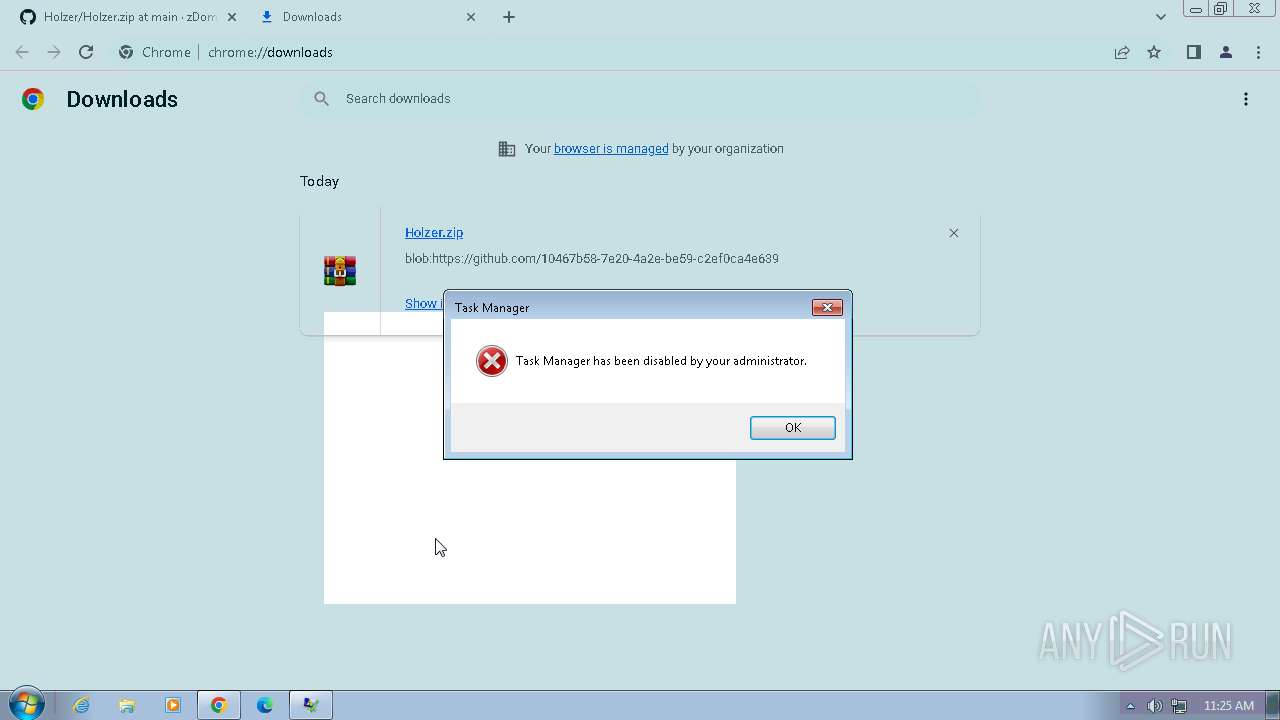
Drops the executable file immediately after the start
- Setup.exe (PID: 2544)
SUSPICIOUS
Reads the Internet Settings
- Setup.exe (PID: 2544)
- Setup.exe (PID: 3632)
- Setup.exe (PID: 3012)
- Setup.exe (PID: 4060)
- Setup.exe (PID: 324)
- Setup.exe (PID: 3828)
- Setup.exe (PID: 1576)
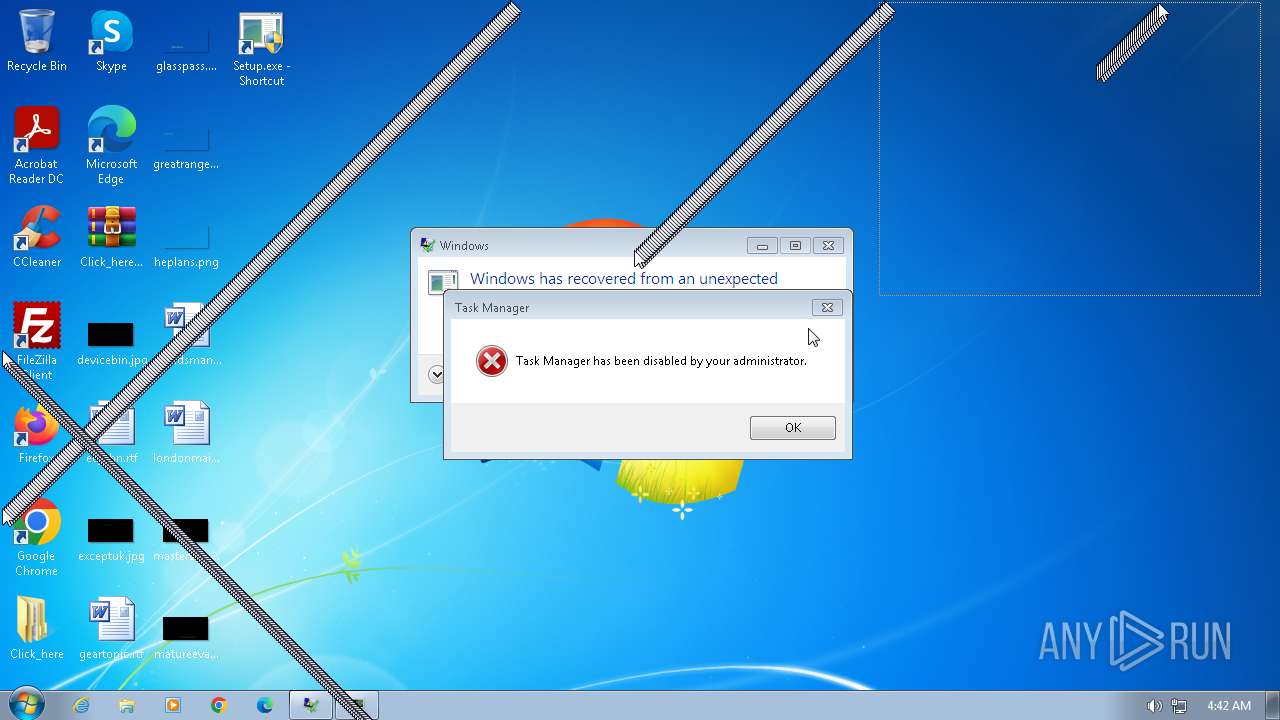
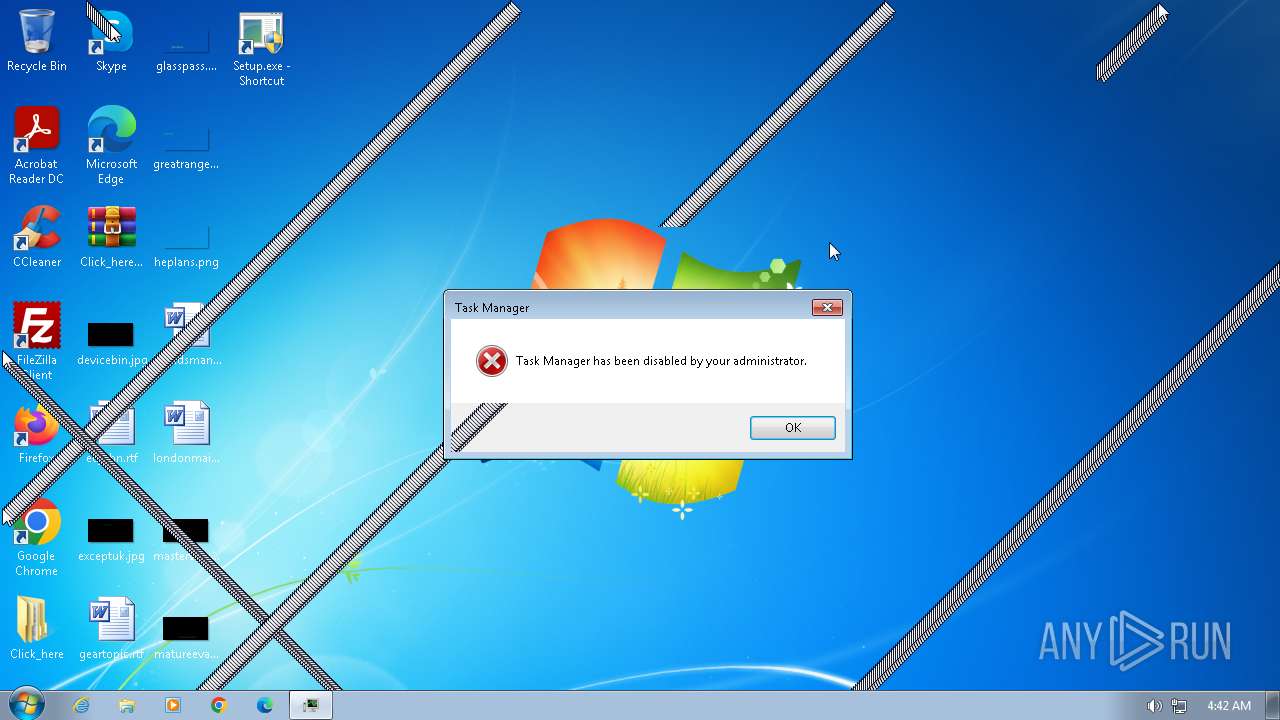
- taskmgr.exe (PID: 3112)
- sipnotify.exe (PID: 1792)
- runonce.exe (PID: 2036)
- taskmgr.exe (PID: 4076)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1792)
- ctfmon.exe (PID: 1664)
Application launched itself
- taskmgr.exe (PID: 3112)
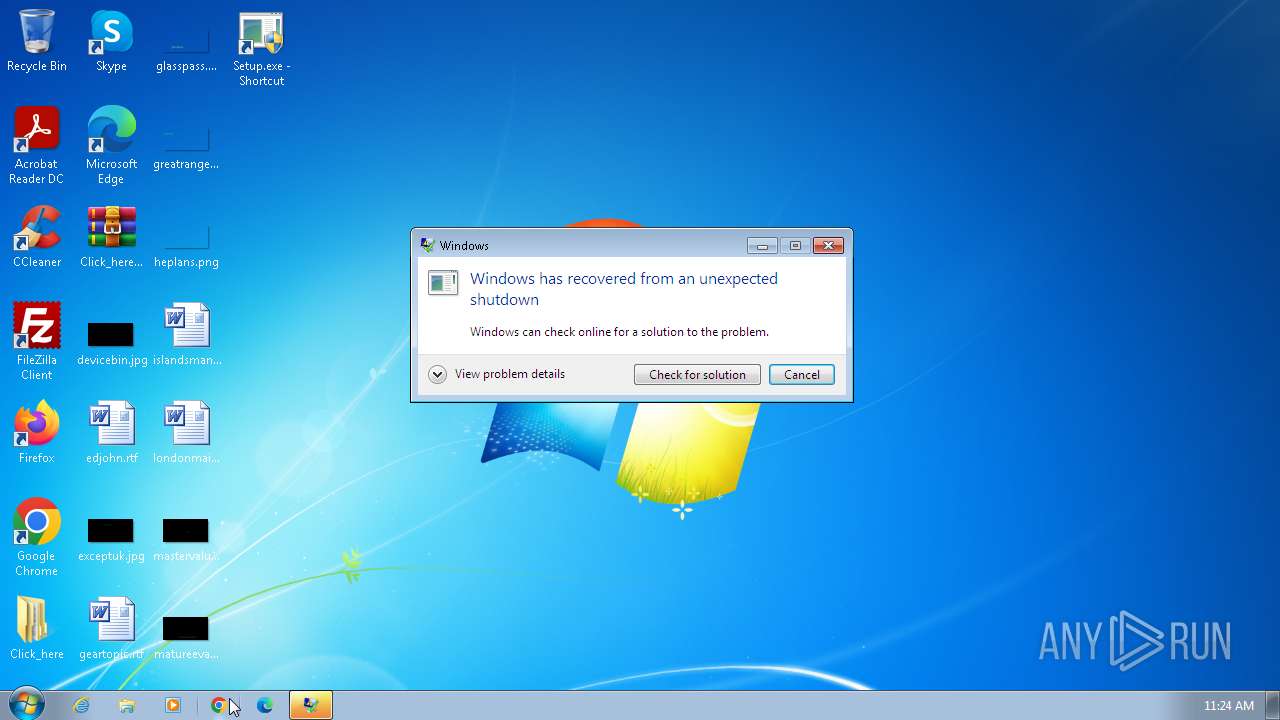
- WerFault.exe (PID: 348)
- taskmgr.exe (PID: 4076)
Reads settings of System Certificates
- sipnotify.exe (PID: 1792)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 2120)
- Setup.exe (PID: 2544)
- ShedulerYori.exe (PID: 2856)
- Setup.exe (PID: 3632)
- ShedulerYori.exe (PID: 4036)
- Setup.exe (PID: 3828)
- Setup.exe (PID: 3012)
- ShedulerYori.exe (PID: 3092)
- Setup.exe (PID: 4060)
- ShedulerYori.exe (PID: 4028)
- Setup.exe (PID: 324)
- ShedulerYori.exe (PID: 1596)
- ShedulerYori.exe (PID: 3872)
- ShedulerYori.exe (PID: 1972)
- Setup.exe (PID: 1576)
- IMEKLMG.EXE (PID: 2052)
- wmpnscfg.exe (PID: 2460)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2576)
- IMEKLMG.EXE (PID: 312)
- Holzer.exe (PID: 3396)
Reads the computer name
- wmpnscfg.exe (PID: 2120)
- Setup.exe (PID: 2544)
- ShedulerYori.exe (PID: 2856)
- ShedulerYori.exe (PID: 3092)
- Setup.exe (PID: 3632)
- Setup.exe (PID: 3012)
- Setup.exe (PID: 4060)
- Setup.exe (PID: 324)
- ShedulerYori.exe (PID: 3872)
- ShedulerYori.exe (PID: 4028)
- Setup.exe (PID: 3828)
- ShedulerYori.exe (PID: 4036)
- Setup.exe (PID: 1576)
- ShedulerYori.exe (PID: 1596)
- ShedulerYori.exe (PID: 1972)
- IMEKLMG.EXE (PID: 312)
- IMEKLMG.EXE (PID: 2052)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2460)
- wmpnscfg.exe (PID: 2576)
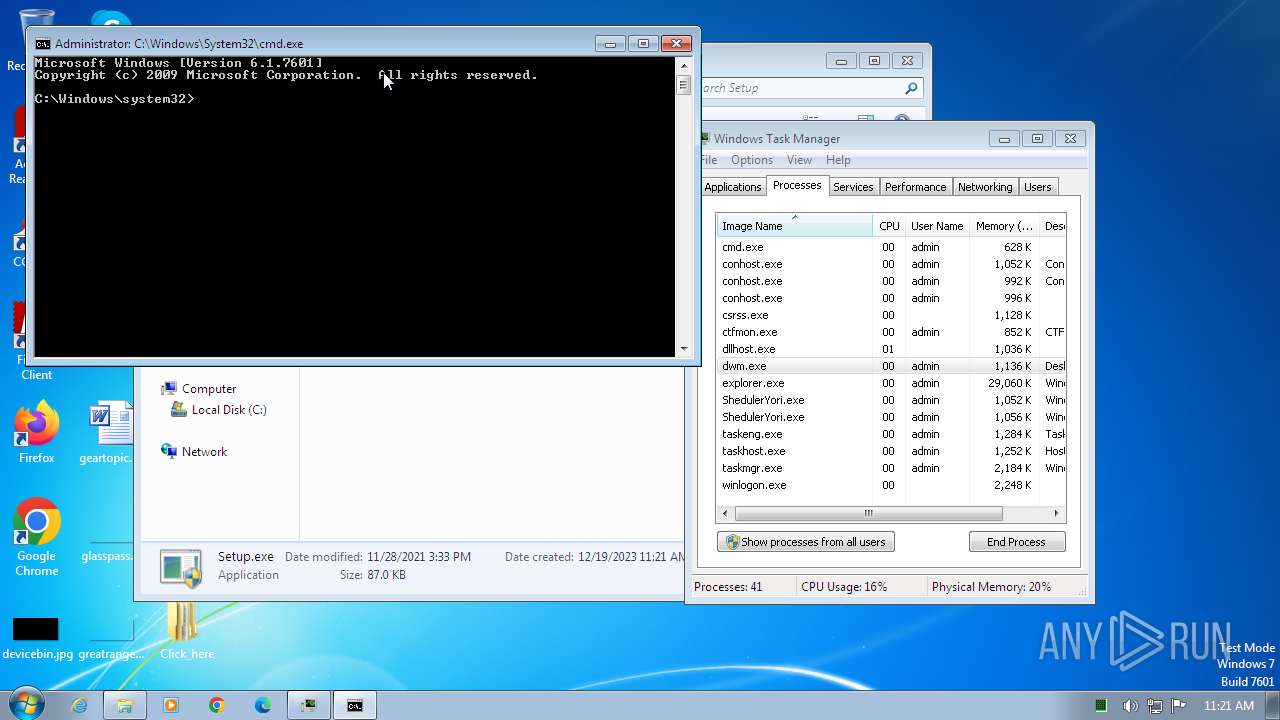
Manual execution by a user
- WinRAR.exe (PID: 1656)
- Setup.exe (PID: 2544)
- WinRAR.exe (PID: 2660)
- WinRAR.exe (PID: 1388)
- Setup.exe (PID: 1000)
- Setup.exe (PID: 3012)
- Setup.exe (PID: 3828)
- taskmgr.exe (PID: 3112)
- Setup.exe (PID: 3632)
- cmd.exe (PID: 3328)
- Setup.exe (PID: 3536)
- Setup.exe (PID: 2228)
- Setup.exe (PID: 4060)
- Setup.exe (PID: 324)
- Setup.exe (PID: 1772)
- Setup.exe (PID: 1576)
- Setup.exe (PID: 3780)
- Setup.exe (PID: 128)
- runonce.exe (PID: 2036)
- IMEKLMG.EXE (PID: 2052)
- IMEKLMG.EXE (PID: 312)
- wmpnscfg.exe (PID: 2576)
- wmpnscfg.exe (PID: 2388)
- wmpnscfg.exe (PID: 2460)
- chrome.exe (PID: 2596)
- taskmgr.exe (PID: 4076)
Create files in a temporary directory
- Setup.exe (PID: 2544)
- WerFault.exe (PID: 1436)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2660)
- chrome.exe (PID: 1016)
- WinRAR.exe (PID: 2560)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1792)
Reads the time zone
- runonce.exe (PID: 2036)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 312)
- IMEKLMG.EXE (PID: 2052)
The process uses the downloaded file
- chrome.exe (PID: 2140)
- WinRAR.exe (PID: 2560)
Application launched itself
- chrome.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:09:11 22:15:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
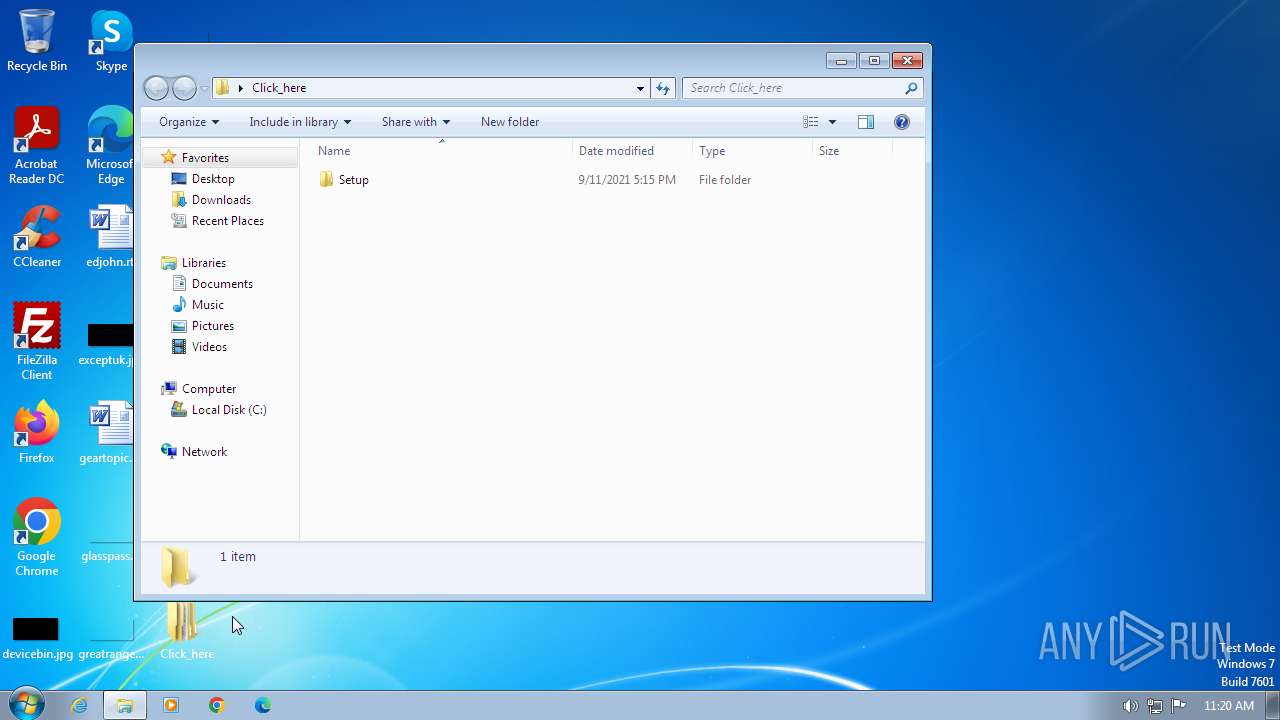
| ZipFileName: | Setup/ |
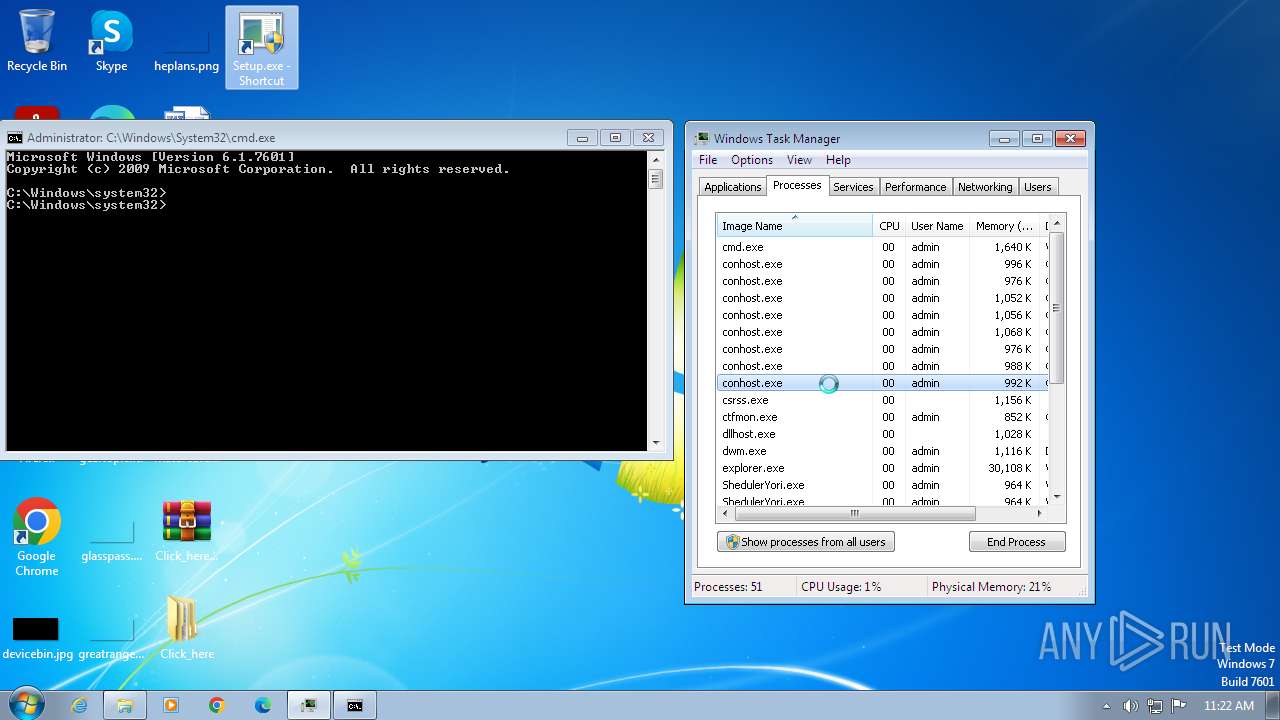
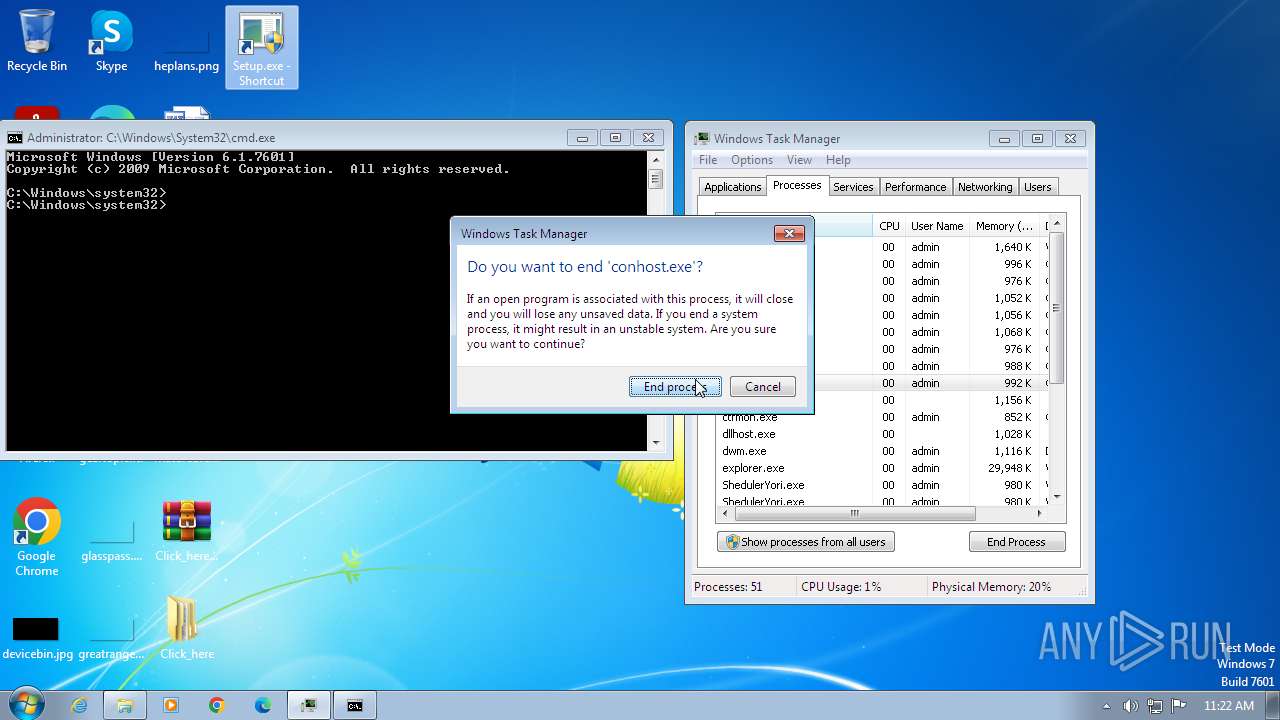
Total processes
189
Monitored processes
70
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,Control_RunDLL C:\Windows\system32\desk.cpl desk,@Themes /Action:OpenTheme /file:"C:\Windows\Resources\Themes\aero.theme" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | "C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe" | C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=4556 --field-trial-handle=1192,i,18043685965102614612,10326883054060425284,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 312 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 324 | "C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe" | C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 348 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | "C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe" | C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=4328 --field-trial-handle=1192,i,18043685965102614612,10326883054060425284,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Click_here.zip" C:\Users\admin\Desktop\Click_here\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1436 | C:\Windows\System32\WerFault.exe -k -q | C:\Windows\System32\WerFault.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 504
Read events
16 263
Write events
238
Delete events
3
Modification events
| (PID) Process: | (116) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1656) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
212
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2596 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF6225.TMP | — | |
MD5:— | SHA256:— | |||
| 2596 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1792 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\main.jpg | image | |
MD5:B342ACE63F77961249A084C61EABC884 | SHA256:E5067BBA2095B5DA7C3171EC116E9A92337E24E471339B0860A160076EFE49B9 | |||
| 2660 | WinRAR.exe | C:\Users\admin\Desktop\Click_here\Setup\Setup\data0.bin | binary | |
MD5:C50C58AA6FA1B3413623ADCC36894ECD | SHA256:C9ABFE1CC1021C116295001B862F6C5F4D00CA33E73262CC9AAE5CF20F669059 | |||
| 2544 | Setup.exe | C:\Users\admin\AppData\Local\Temp\ShedulerYori.exe | executable | |
MD5:B724E4BC22D5F782A6F991D67FB00FB6 | SHA256:627611F37A051DC649065489CF39E9666701B2C235AC3F8D43712DDD723DD710 | |||
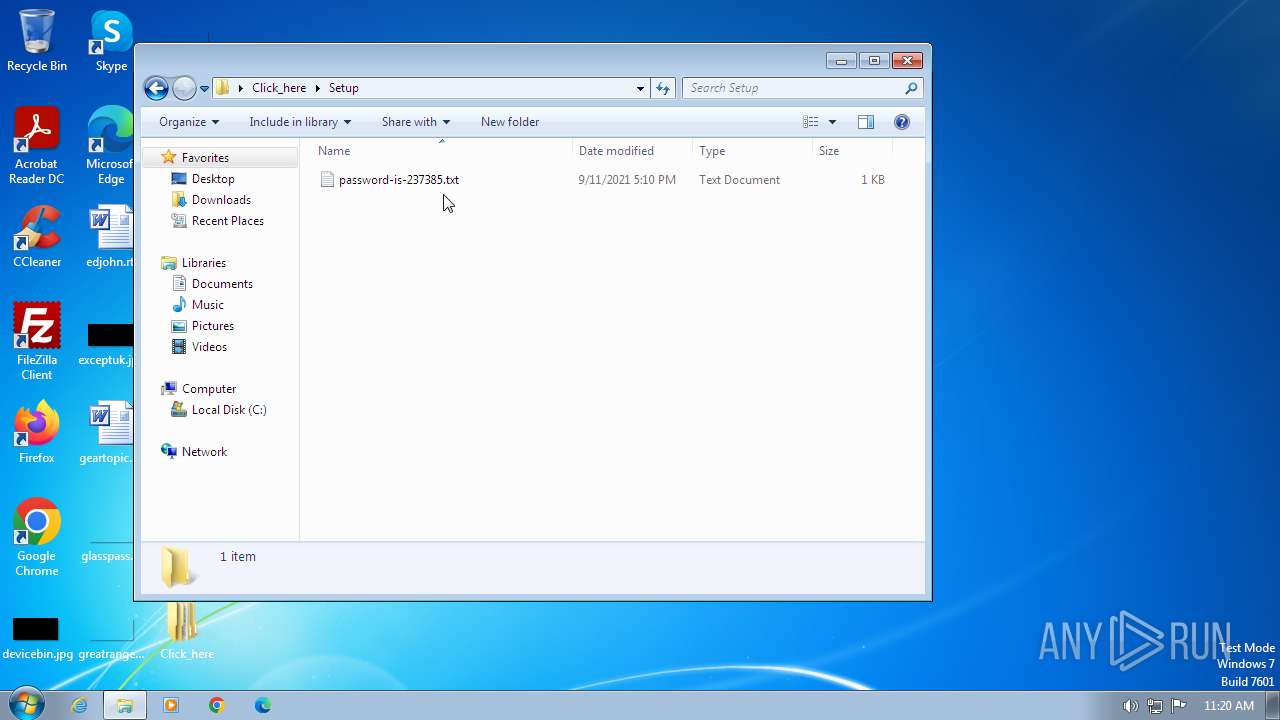
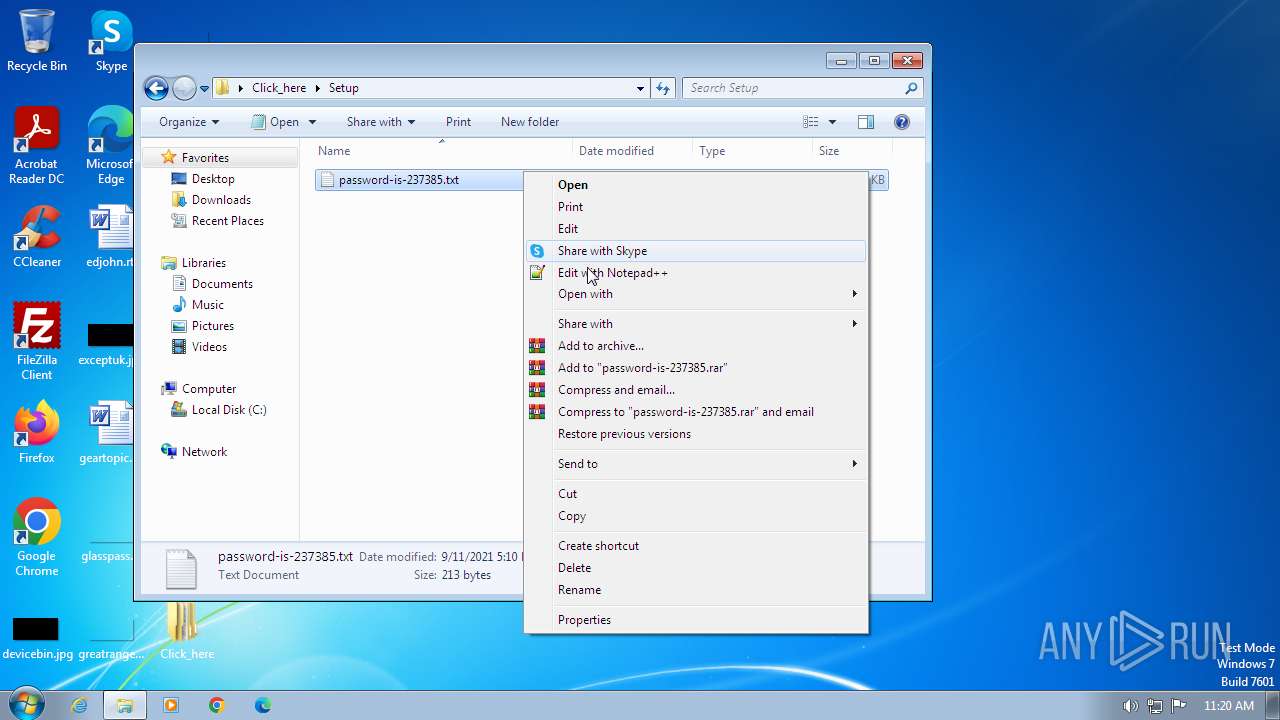
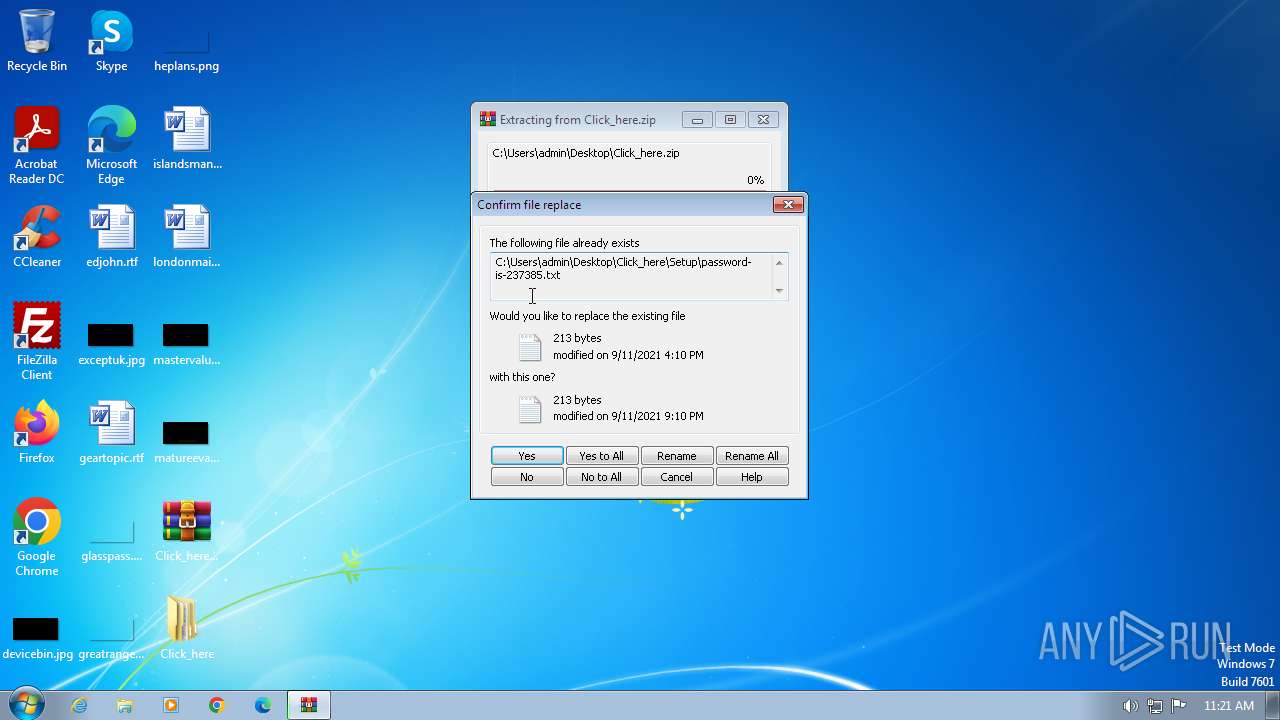
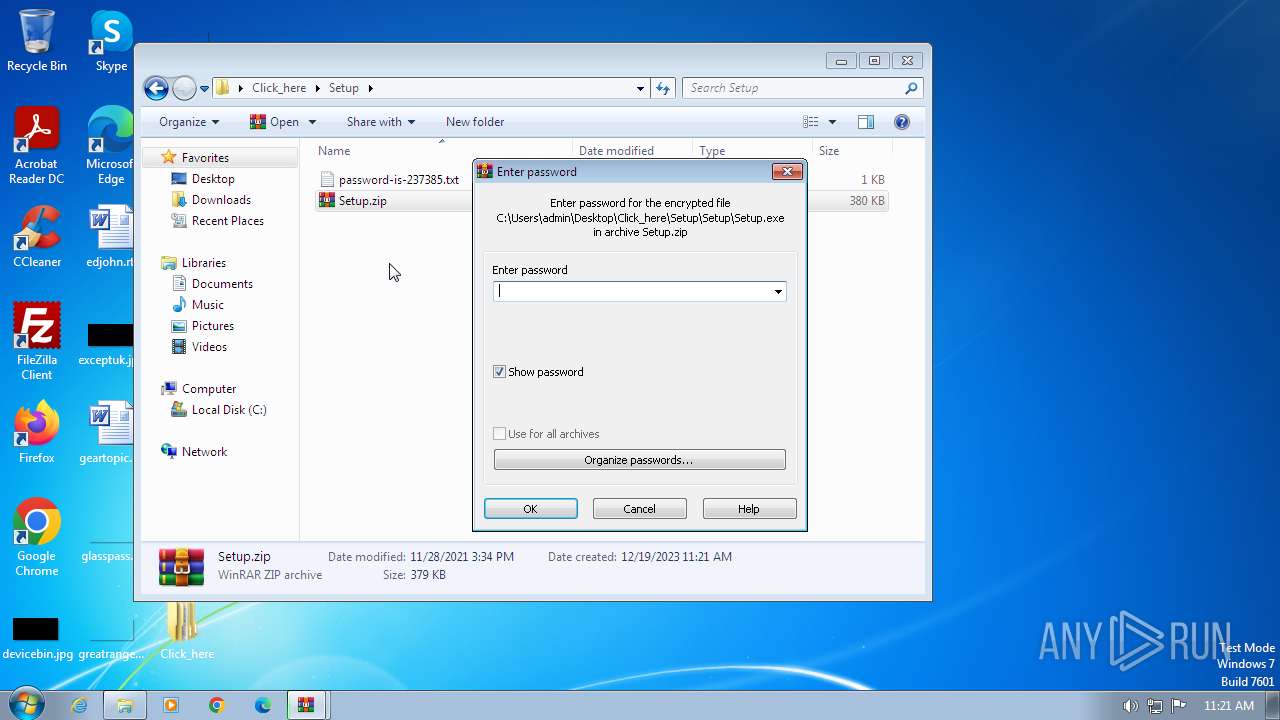
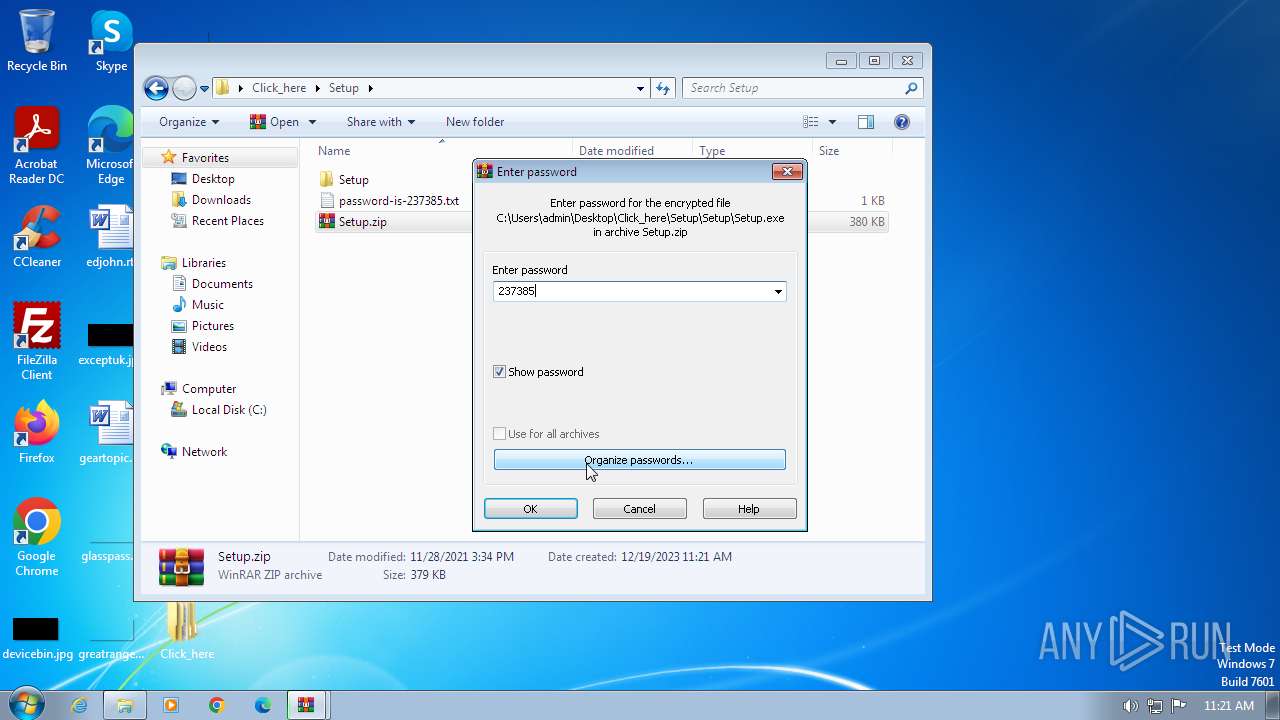
| 1656 | WinRAR.exe | C:\Users\admin\Desktop\Click_here\Setup\password-is-237385.txt | text | |
MD5:DF8BAFF7A3AB716B3D6C8F382A586868 | SHA256:CAC1789B0443E2FE0419BD302309CF28E55000EFEA404C5B51A9118650C1B80B | |||
| 1388 | WinRAR.exe | C:\Users\admin\Desktop\Click_here\Setup\Setup.zip | compressed | |
MD5:E12F9328357A5DCFC8336F9CB34C0B6F | SHA256:7921EF72016505300840FA04EA2180DD66FC4401428F71447376A55BC80235C0 | |||
| 2660 | WinRAR.exe | C:\Users\admin\Desktop\Click_here\Setup\Setup\Setup.exe | executable | |
MD5:5A435DBB34225EE123506EEFE5EF141D | SHA256:9543FF1AEC6FFF81E2A2EC65841864ACFDD71343FB88DA5B8F0575D41AFCB87C | |||
| 2036 | runonce.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Explorer\ExplorerStartupLog_RunOnce.etl | binary | |
MD5:6D1DA9DB986A5E19D4D764B0D6DC1C03 | SHA256:7FFA849896048F6C1592E9B09A67791AAB87062FD1A17CA071264BCDC8683F81 | |||
| 1436 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER-9562-0.sysdata.xml | xml | |
MD5:B7E38B5A83FC38998EEA25968B42554E | SHA256:5CB3B571D015C8DF84D1842C2D5E5F872829FBEF998EE36BC67C4A38342B95DF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
78
DNS requests
93
Threats
21
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1792 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133474586367650000 | unknown | — | — | unknown |
2764 | chrome.exe | GET | 200 | 91.215.42.31:80 | http://gg.gg/css/style.css | unknown | text | 1.39 Kb | unknown |
2764 | chrome.exe | GET | 200 | 91.215.42.31:80 | http://gg.gg/ | unknown | html | 1.78 Kb | unknown |
2764 | chrome.exe | GET | 200 | 91.215.42.31:80 | http://gg.gg/css/jquery.tagit.css | unknown | text | 452 b | unknown |
— | — | GET | 200 | 91.215.42.31:80 | http://gg.gg/css/smoothness/jquery-ui-1.8.21.custom.css | unknown | text | 5.91 Kb | unknown |
— | — | GET | 200 | 91.215.42.31:80 | http://gg.gg/js/jquery-1.7.2.min.js | unknown | html | 33.0 Kb | unknown |
2764 | chrome.exe | GET | 200 | 91.215.42.31:80 | http://gg.gg/js/jquery-ui-1.8.21.custom.min.js | unknown | text | 50.8 Kb | unknown |
— | — | GET | 200 | 91.215.42.31:80 | http://gg.gg/js/jquery.corners.min.js | unknown | text | 3.20 Kb | unknown |
— | — | GET | 200 | 91.215.42.31:80 | http://gg.gg/js/jquery.cookie.js | unknown | text | 837 b | unknown |
— | — | GET | 200 | 91.215.42.31:80 | http://gg.gg/js/jquery.zclip.min.js | unknown | text | 2.59 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2856 | ShedulerYori.exe | 212.193.30.45:80 | — | Delis LLC | CZ | unknown |
3092 | ShedulerYori.exe | 212.193.30.45:80 | — | Delis LLC | CZ | unknown |
2856 | ShedulerYori.exe | 212.193.30.29:80 | — | Delis LLC | CZ | unknown |
3092 | ShedulerYori.exe | 212.193.30.29:80 | — | Delis LLC | CZ | unknown |
4036 | ShedulerYori.exe | 212.193.30.45:80 | — | Delis LLC | CZ | unknown |
3872 | ShedulerYori.exe | 212.193.30.45:80 | — | Delis LLC | CZ | unknown |
4028 | ShedulerYori.exe | 212.193.30.45:80 | — | Delis LLC | CZ | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
query.prod.cms.rt.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
lh5.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2764 | chrome.exe | Misc activity | ET INFO GG Url Shortener Observed in DNS Query |
2764 | chrome.exe | Misc activity | ET INFO GG Url Shortener Observed in DNS Query |
2764 | chrome.exe | Misc activity | ET INFO GG Url Shortener Observed in DNS Query |
2764 | chrome.exe | Misc activity | ET INFO GG Url Shortener Observed in DNS Query |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |
2764 | chrome.exe | Potentially Bad Traffic | ET HUNTING DDoS-Guard Hosted Content |